| File name: | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3 |
| Full analysis: | https://app.any.run/tasks/789aaa8f-9ae8-4f78-ae94-f929a4bf5461 |
| Verdict: | Malicious activity |
| Analysis date: | December 30, 2024, 02:55:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | AEC33041AF622A85921E76632B6C4C1A |
| SHA1: | 5BCC77EB484D527A1F6F8EDF695A126D761AA263 |
| SHA256: | 1592CC653E3394A1D3717FF7B80B6816709C8443793EE74A398C30401FDD30C3 |
| SSDEEP: | 196608:XM4sYQJQCufw8tacNkfm/0RK07+8DTSIk:XYYcQXfycNf/8Rk |
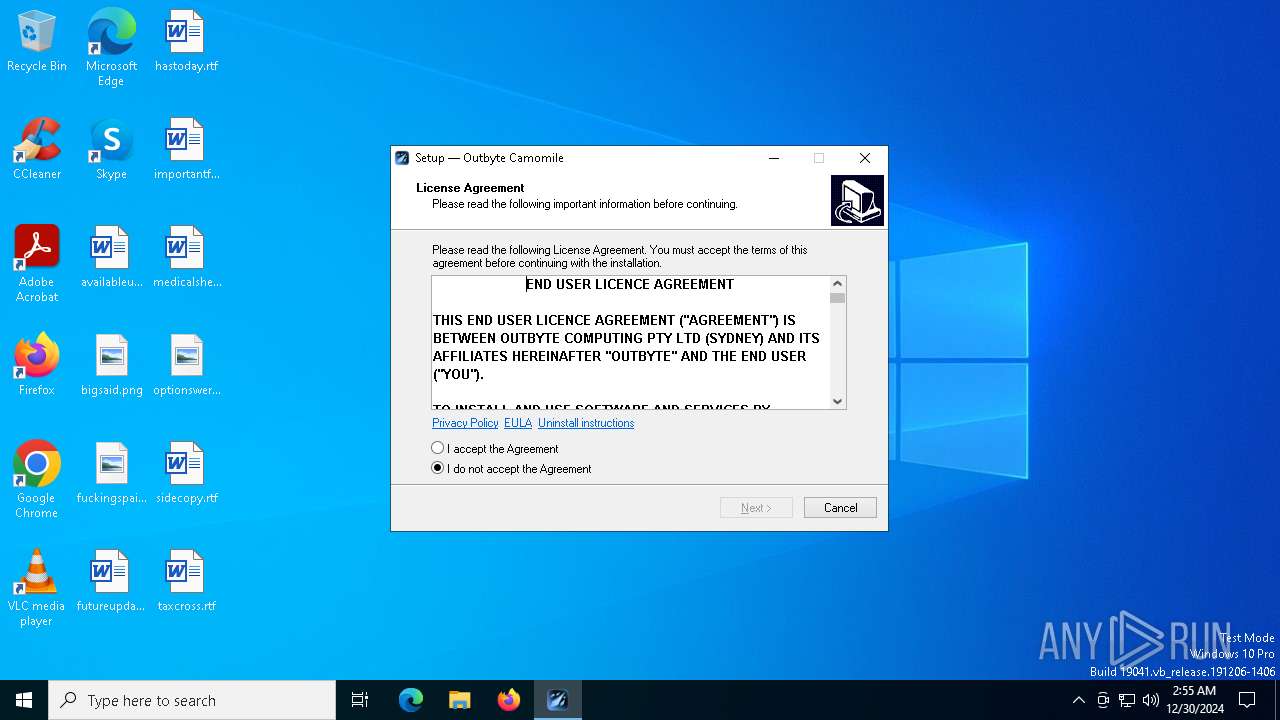
MALICIOUS
Executing a file with an untrusted certificate
- Installer.exe (PID: 6224)
SUSPICIOUS
Executable content was dropped or overwritten
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
Process drops SQLite DLL files
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
Reads security settings of Internet Explorer
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
Checks Windows Trust Settings
- Installer.exe (PID: 6224)
Reads the BIOS version
- Installer.exe (PID: 6224)
Reads the Windows owner or organization settings
- Installer.exe (PID: 6224)
There is functionality for communication over UDP network (YARA)
- Installer.exe (PID: 6224)
INFO
Process checks computer location settings
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
Checks supported languages
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
Reads Environment values
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
The sample compiled with english language support
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
Reads the computer name
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
Create files in a temporary directory
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
Checks proxy server information
- 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe (PID: 7124)
- Installer.exe (PID: 6224)
Reads the machine GUID from the registry
- Installer.exe (PID: 6224)
Creates files or folders in the user directory
- Installer.exe (PID: 6224)
Creates files in the program directory
- Installer.exe (PID: 6224)
Reads the software policy settings
- Installer.exe (PID: 6224)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (79.7) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (8.6) |
| .exe | | | Win16/32 Executable Delphi generic (3.9) |
| .exe | | | Generic Win/DOS Executable (3.8) |
| .exe | | | DOS Executable Generic (3.8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:04:17 20:12:32+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 143872 |
| InitializedDataSize: | 414208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x24530 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.3.4.32565 |
| ProductVersionNumber: | 1.3.4.32565 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Camomile |
| CompanyName: | Outbyte |
| FileDescription: | Outbyte Camomile Installation File |
| FileVersion: | 1.3.4.32565 |
| LegalCopyright: | Copyright © 2016-2024 Outbyte Computing Pty Ltd |
| OriginalFileName: | Outbyte-camomile-setup.exe |
| ProductName: | Camomile |
| ProductVersion: | 1.x |
Total processes
123
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6224 | "C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\Installer.exe" /spid:7124 /splha:37790528 | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\Installer.exe | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | ||||||||||||
User: admin Company: Outbyte Integrity Level: HIGH Description: Installer Version: 1.3.4.32565 Modules
| |||||||||||||||
| 6924 | "C:\Users\admin\AppData\Local\Temp\1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe" | C:\Users\admin\AppData\Local\Temp\1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | — | explorer.exe | |||||||||||
User: admin Company: Outbyte Integrity Level: MEDIUM Description: Outbyte Camomile Installation File Exit code: 3221226540 Version: 1.3.4.32565 Modules
| |||||||||||||||
| 7124 | "C:\Users\admin\AppData\Local\Temp\1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe" | C:\Users\admin\AppData\Local\Temp\1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | explorer.exe | ||||||||||||
User: admin Company: Outbyte Integrity Level: HIGH Description: Outbyte Camomile Installation File Version: 1.3.4.32565 Modules
| |||||||||||||||
Total events
4 578
Read events
4 558
Write events
20
Delete events
0
Modification events
| (PID) Process: | (7124) 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.URLClientId |
Value: 1036007967.121677488423 | |||
| (PID) Process: | (7124) 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (7124) 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (7124) 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (7124) 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.CustomClientId |
Value: 1036007967.121677488423 | |||
| (PID) Process: | (6224) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6D484312-2A78-96B5-2103-981509CE347B}\Version |
| Operation: | write | Name: | Assembly |
Value: 8154EB4F6364B3D88624301B9F3A3E9D8154EB4F6364B3D88624301B9F3A3E9D88AD8CBB5ED3F66B83A8A2CDF194269C890BB34AEBD806E41A50D3BD9C0B4765219909F09E75DEC0927FF4E8152284CD219909F09E75DEC0927FF4E8152284CD59B5414605BAE21E9735786EB516D3F8DE1283C2AFF9BF99D33ED2740C86BBD2F8157495FE950FA4A01046BB55F00DAD0F20AA1B1ADFE602954529934D03147D | |||
| (PID) Process: | (6224) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | Application.GAIV.FunnelDate |
Value: DCA031E5034BE640 | |||
| (PID) Process: | (6224) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.Language |
Value: ENU | |||
| (PID) Process: | (6224) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.TrackingIV.CID |
Value: 2349397750.1735527317 | |||
| (PID) Process: | (6224) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Outbyte\Camomile\1.x\Settings |
| Operation: | write | Name: | General.TrackingIV.SID |
Value: Au8Ds7NZIr | |||
Executable files
14
Suspicious files
20
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\Installer.exe | odttf | |
MD5:095966560F3C819896BECE49676BCA65 | SHA256:AF3E5CD95E429D04AB62C8B35EED0C50C46573F53ED4F39019E7A8046C1458F8 | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\vcl250.bpl | executable | |
MD5:FEBEE79A34BFF20E384E3FCAE2B51B61 | SHA256:37671E12042AE347EECE39F10AF9B643CE9D05F490300359460D3FEA0835F448 | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\InstallerUtils.dll | executable | |
MD5:A581166BAA47DB98D0D1B3C203487205 | SHA256:5C6F0AC164B27A89FA803EE697C6417C9D8FBDBA1BCB885CEE60C8B57EE071BE | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\SetupHelper.dll | executable | |
MD5:70CC462BB6933E4EF78626E27CC72F8C | SHA256:ACF4CD594E472C4DD1FD6AC0E8C6841EC942E0B27E3FC5C52FC345F4EC817FBB | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\vclimg250.bpl | executable | |
MD5:BF438764B3EB1A322CFD3E0651498E35 | SHA256:69E90153DC3BAC2FF178E69DEA862AAD7A4D02EE4BACDCDE26E3D481082081C0 | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\rtl250.bpl | executable | |
MD5:92ECCB295667552C32396F5AC3C5CA6D | SHA256:9CF666D79A944005674FF70C6E6605212CCA8F65E62602300B60CEA075DAB221 | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\Camomile.exe | binary | |
MD5:BFB7AC762F442CF17811AFA44CCBFD79 | SHA256:2C3C0E0F50A3B0CBCEF83623ECEF181DFD917A00083F39CA29BC3D6740FE6657 | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\OxComponentsRTL.bpl | executable | |
MD5:A51AADCBF50DF28CFAC595729DC0E180 | SHA256:8B7AD1974EF91F87D7AC2361F40E263FDA7F72CBF5B6D32A5E3E15E7E228CC28 | |||
| 6224 | Installer.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | der | |
MD5:8CDD66D52CA2F372E4DA4A46B336D7EE | SHA256:14115735E08562ECF04251D722EEB632F0EF2D0AC037BC017D208BC7D9A13BB6 | |||
| 7124 | 1592cc653e3394a1d3717ff7b80b6816709c8443793ee74a398c30401fdd30c3.exe | C:\Users\admin\AppData\Local\Temp\is-9755741.tmp\CFAHelper.dll | executable | |
MD5:D6925B8CCFC038AB6DB312E740E3F662 | SHA256:B1D1E265392ED2F2663203DB3D4DB7A140B80255DDA0A0FC62466FFCF99FFC3F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
38
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6224 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6224 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAwfypkv9EfKYa1bFvWpvwk%3D | unknown | — | — | whitelisted |
6224 | Installer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
6224 | Installer.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
6224 | Installer.exe | GET | 200 | 142.250.185.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
6224 | Installer.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | whitelisted |
6224 | Installer.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQD3gdqA6Jg5hrTz8KU5%2Blzk | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | unknown |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1176 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
outbyte.com |
| unknown |
ocsp.usertrust.com |
| whitelisted |