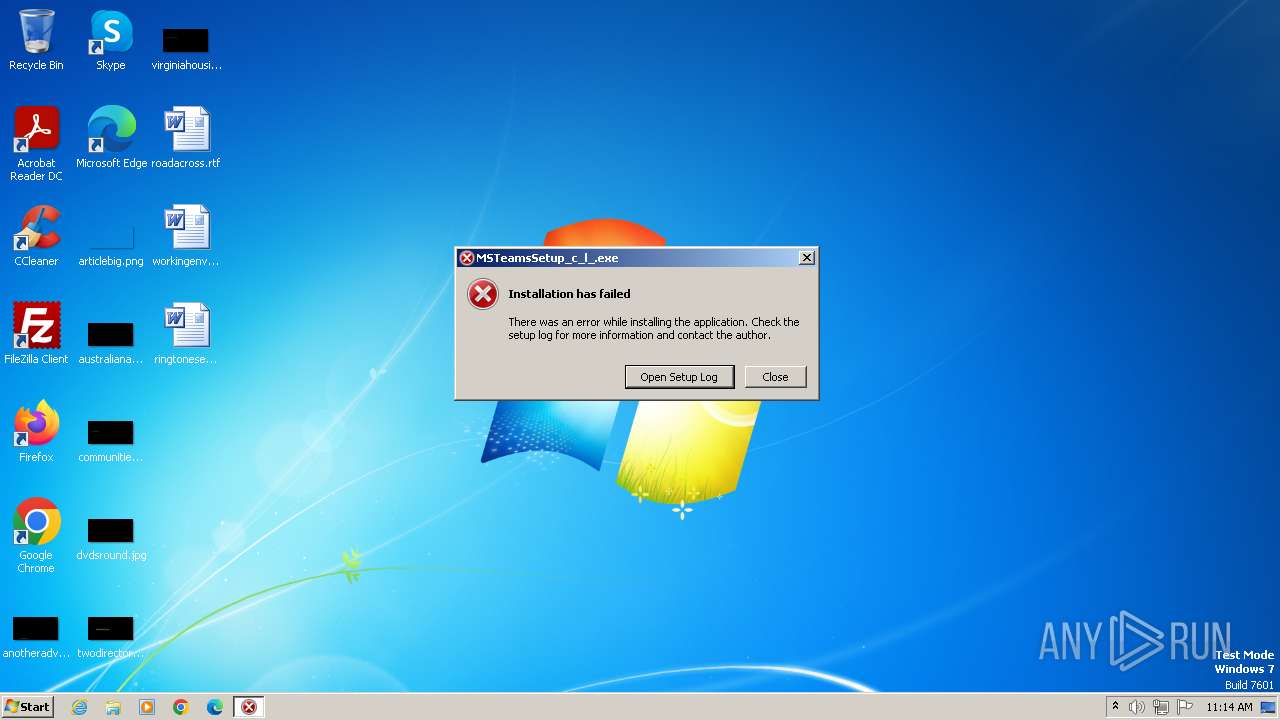
| File name: | MSTeamsSetup_c_l_.exe |
| Full analysis: | https://app.any.run/tasks/aa582dc9-936a-4502-b849-5776188329be |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2023, 11:14:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 092BFF0405AB418FE22C565E231BE2BA |
| SHA1: | 8AEF2B7D83B3D5AE55B24F25AB6621BB2DEA9287 |
| SHA256: | 156CAFA6DA98A57E481AAB74EF748726BD4DCE2912536FB59E65D9A57A3AE7A7 |
| SSDEEP: | 24576:4NYuPOTryV7OXRiYZgJw2K9KS74fVyhfP0dhyaz/PxSbQOUP8oSf37Z3/UyD:MOX6743ZvFKS74Nwfahyazx0LZ3jD |
MALICIOUS
Application was dropped or rewritten from another process
- Update.exe (PID: 3612)
Drops the executable file immediately after the start
- MSTeamsSetup_c_l_.exe (PID: 3628)
SUSPICIOUS
Reads the Internet Settings
- Update.exe (PID: 3612)
Reads settings of System Certificates
- Update.exe (PID: 3612)
Process drops legitimate windows executable
- MSTeamsSetup_c_l_.exe (PID: 3628)
INFO
Checks supported languages
- MSTeamsSetup_c_l_.exe (PID: 3628)
- Update.exe (PID: 3612)
Creates files or folders in the user directory
- MSTeamsSetup_c_l_.exe (PID: 3628)
- Update.exe (PID: 3612)
Reads the machine GUID from the registry
- Update.exe (PID: 3612)
Reads Microsoft Office registry keys
- Update.exe (PID: 3612)
Reads Environment values
- Update.exe (PID: 3612)
Reads the computer name
- Update.exe (PID: 3612)
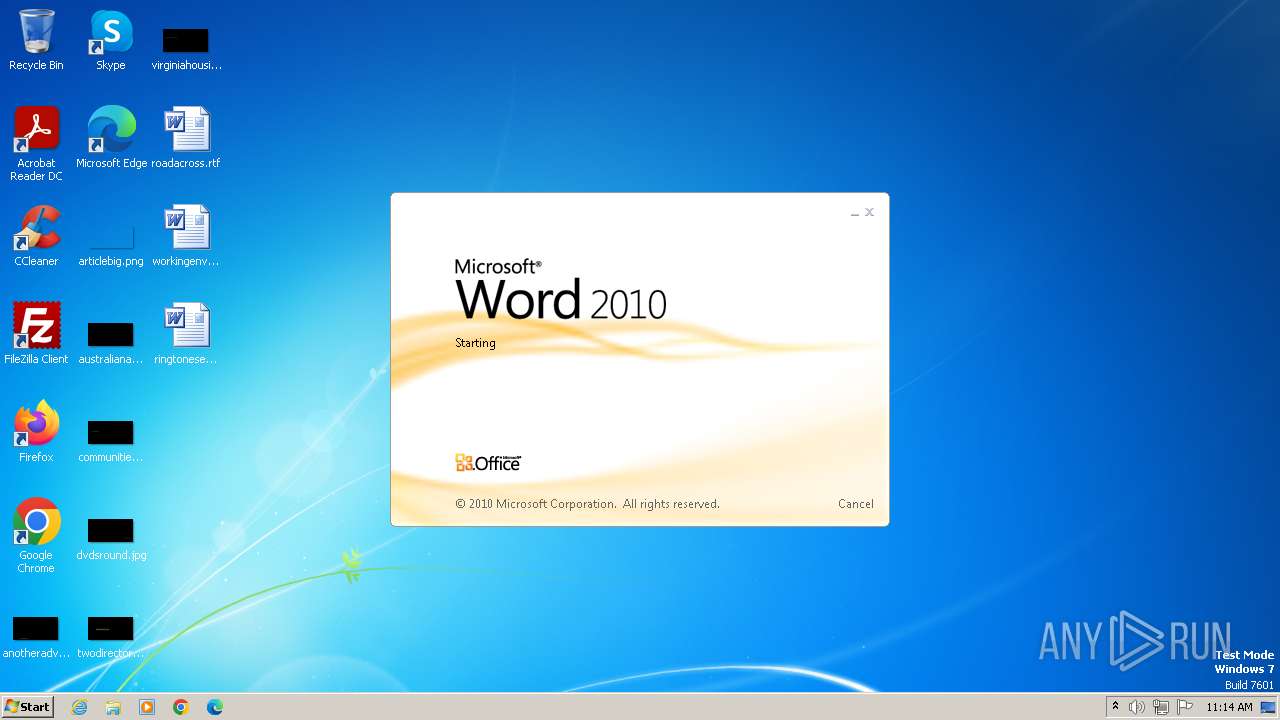
Manual execution by a user
- WINWORD.EXE (PID: 3824)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:04:20 00:24:16+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 215040 |
| InitializedDataSize: | 1187840 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14510 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.4.4.0 |
| ProductVersionNumber: | 1.4.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Installer for Squirrel-based applications |
| FileVersion: | 1.4.4.0 |
| InternalName: | Setup.exe |
| LegalCopyright: | Copyright (C) 2014 |
| OriginalFileName: | Setup.exe |
| ProductName: | Squirrel-based application |
| ProductVersion: | 1.4.4.0 |
| SquirrelAwareVersion: | 1 |
Total processes
41
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3612 | "C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe" --install . --exeName=MSTeamsSetup_c_l_.exe --bootstrapperMode | C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe | MSTeamsSetup_c_l_.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams Exit code: 4294967295 Version: 3.1.2.0 Modules
| |||||||||||||||
| 3628 | "C:\Users\admin\AppData\Local\Temp\MSTeamsSetup_c_l_.exe" | C:\Users\admin\AppData\Local\Temp\MSTeamsSetup_c_l_.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Installer for Squirrel-based applications Exit code: 4294967295 Version: 1.4.4.0 Modules
| |||||||||||||||
| 3824 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\ringtoneseasy.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
4 660
Read events
4 198
Write events
329
Delete events
133
Modification events
| (PID) Process: | (3612) Update.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (3824) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
Executable files
2
Suspicious files
4
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3824 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR12B6.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3628 | MSTeamsSetup_c_l_.exe | C:\Users\admin\AppData\Local\SquirrelTemp\downloading.gif | image | |
MD5:3488A1749B859E969C01BA981036FAB6 | SHA256:C3FA333FDBCE95D504AEE31912993DC17AB31324428F557AC774F7E98B049B99 | |||
| 3612 | Update.exe | C:\Users\admin\AppData\Local\SquirrelTemp\SquirrelSetup.log | text | |
MD5:222622EC046F6E8171095735629262AF | SHA256:0D9291371F4EF89B2217BFC59389E2CF97EA51AC67981FDB2C977E01A1772811 | |||
| 3824 | WINWORD.EXE | C:\Users\admin\Desktop\~$ngtoneseasy.rtf | binary | |
MD5:C7FC54923404814FC93C5601CCCEBAC6 | SHA256:D51B7C1089F4D7F5A83A5FC4A3E00E4FF20576559A7E9CA21E044F3070ADE9FB | |||
| 3824 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:7576C567772497D975560D6CE889FEEF | SHA256:98FFF8AEAE677BFDBFDCEA79CB29C105C1CCD6DCC9B96A51FABF94BA5561802D | |||
| 3628 | MSTeamsSetup_c_l_.exe | C:\Users\admin\AppData\Local\SquirrelTemp\endpoint.json | binary | |
MD5:677CAB9A8B50AD026CFA7625A35DD2D7 | SHA256:07890DDA20815E1E57DCA9553F5DFCFF1B85F4A4369685D4991599E2618978F0 | |||
| 3628 | MSTeamsSetup_c_l_.exe | C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe | executable | |
MD5:55D2BE3EA0DC1DCAEEFDDD7ED12C05E9 | SHA256:5CACCD37E4DF62DCF709605DE3F79664DE7190534B56CD69BCC96BDF0F939437 | |||
| 3824 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\ringtoneseasy.rtf.LNK | binary | |
MD5:C8E2F2BF3223395CC454D366EAA9FEC8 | SHA256:BD2CF47EE9200978AFFE61CD6FF2B2CEC0CD2BFFF3F203D3797B1BDA75BD8BBB | |||
| 3628 | MSTeamsSetup_c_l_.exe | C:\Users\admin\AppData\Local\SquirrelTemp\background.gif | image | |
MD5:FF1F29DCA0451246C3CA6CB7B023434F | SHA256:753D7D351E427246E2B6CC86C45E21F952939E306C3EB2FDB1BD7D67842C64B8 | |||
| 3824 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:421BC6E1857997AFBD664C8D0A030F86 | SHA256:1553A5FE24761173966BC494FF0FF6B26A0580C997E3D65C446B5440595A0F74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3612 | Update.exe | 20.189.173.6:443 | mobile.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mobile.pipe.aria.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Update.exe | Starting TelemetryManager constructor
|
Update.exe | Update.exe Information: 0 : |
Update.exe | Update.exe Information: 0 : |
Update.exe | TelemetryManagerImpl creation started
|
Update.exe | Update.exe Information: 0 : |
Update.exe | Performance counters are disabled. Skipping creation of counters category.
|
Update.exe | RecordBatcherTask with ID 4 started.
|
Update.exe | Update.exe Information: 0 : |
Update.exe | Update.exe Information: 0 : |
Update.exe | DataPackageSender with UserAgent name: AST-exe-C#, version: 3.1.2.0, [Ast_Default_Source]
|