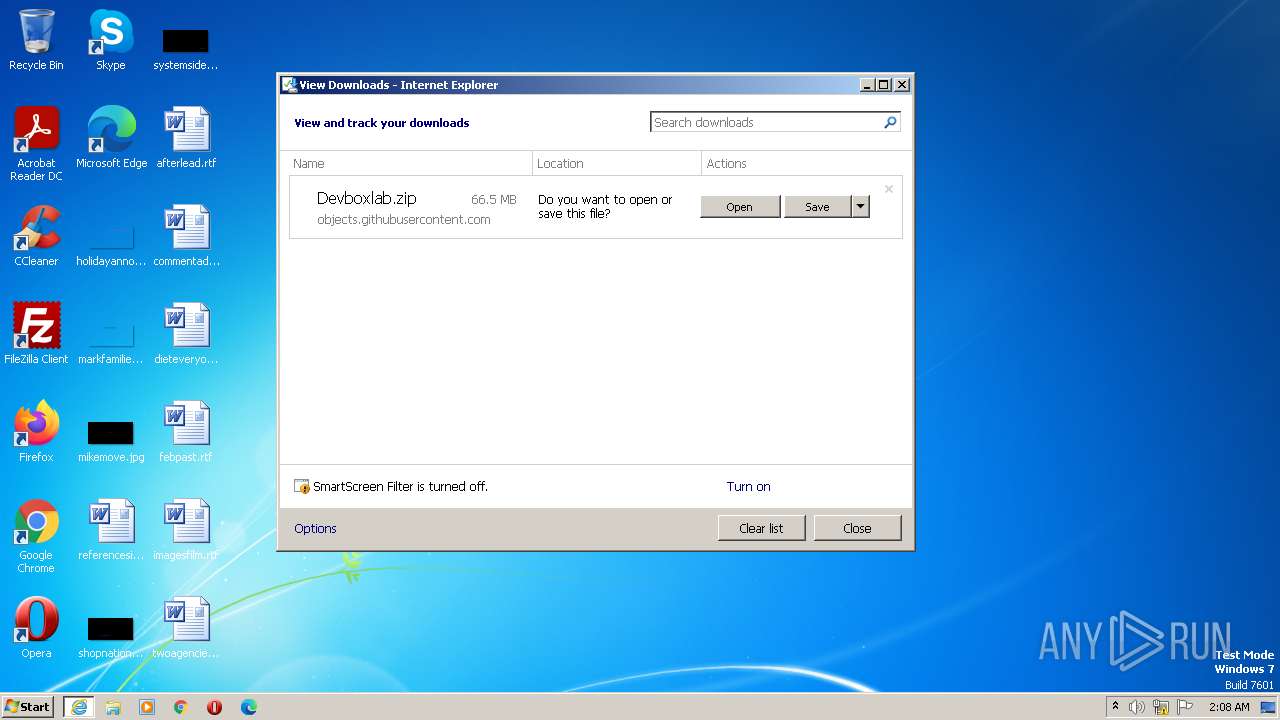
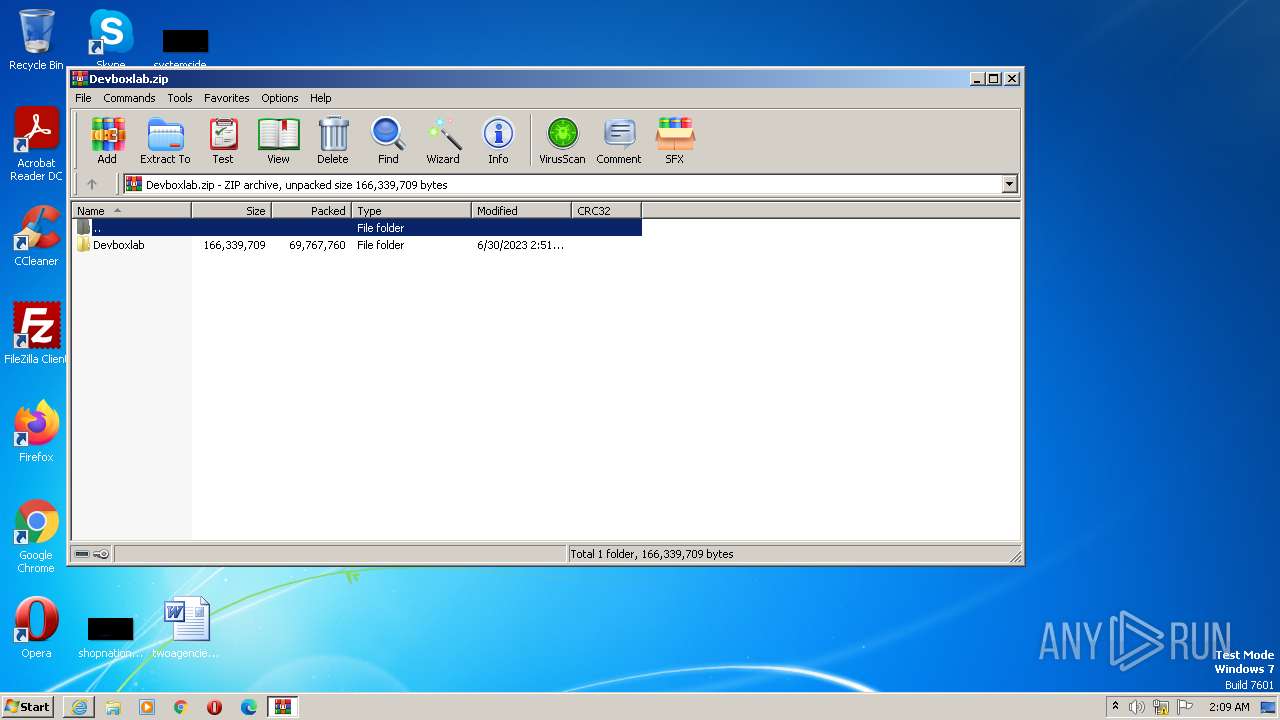
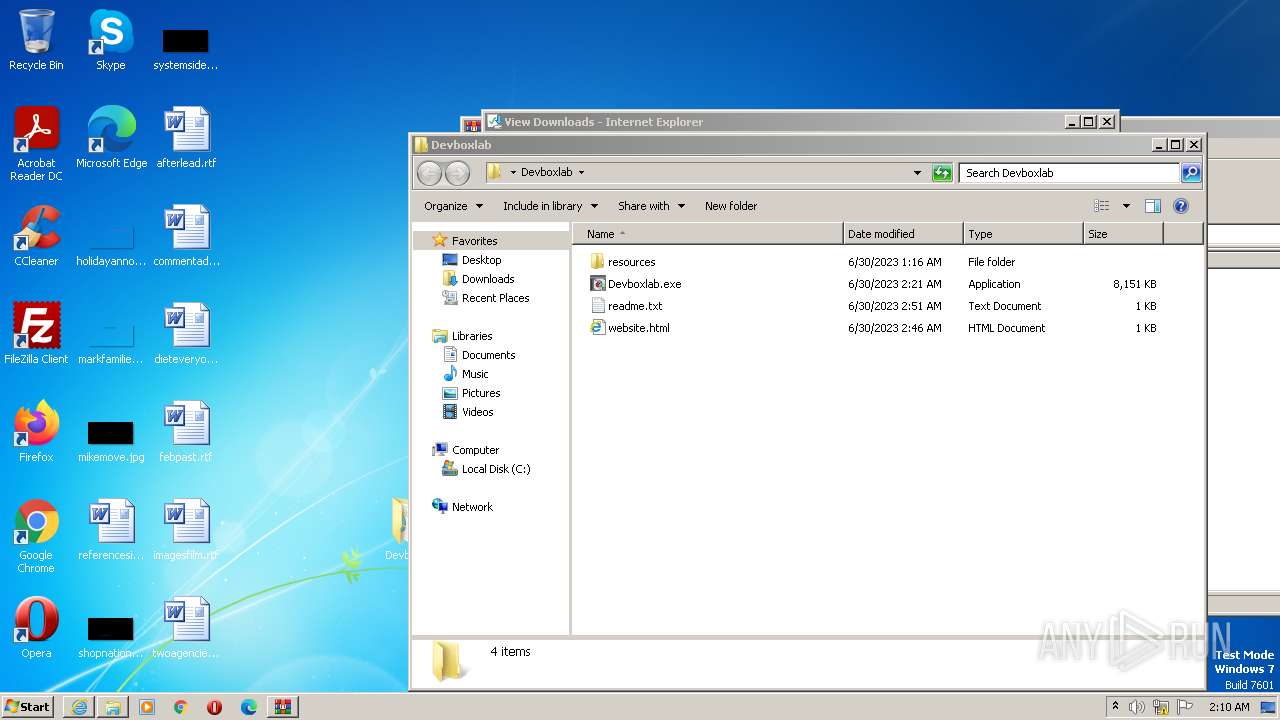
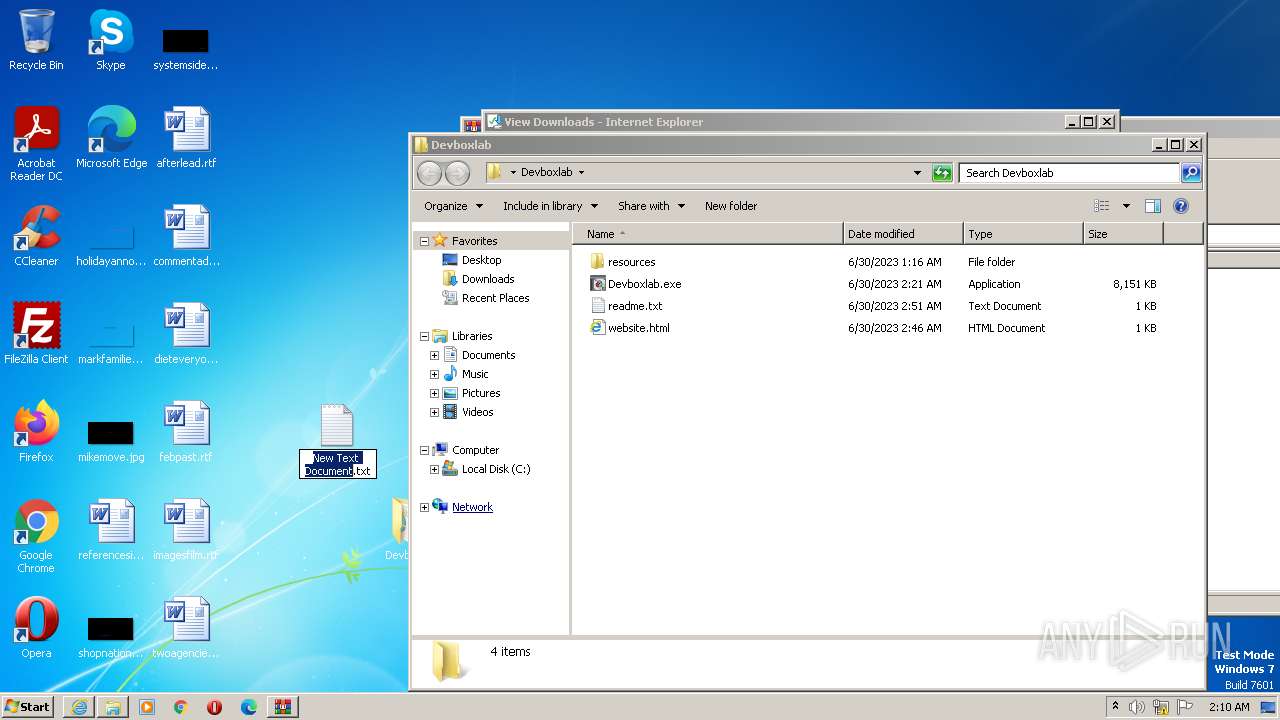
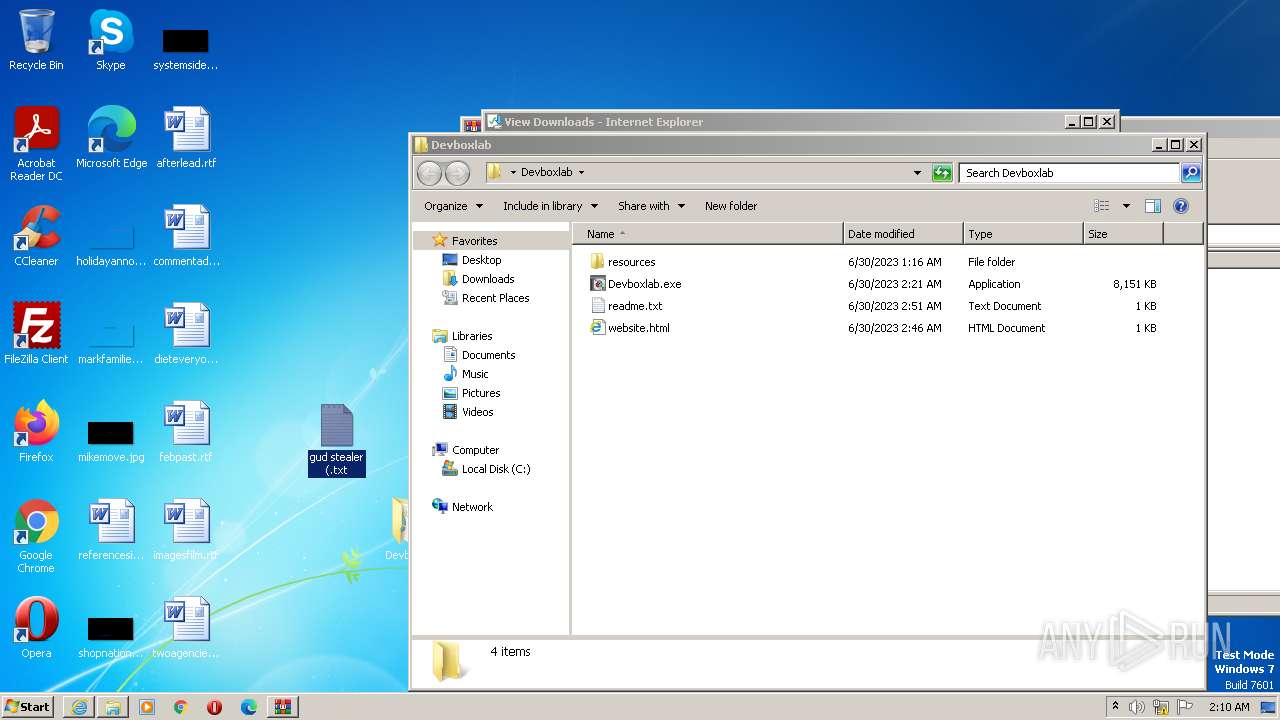
| URL: | https://objects.githubusercontent.com/github-production-release-asset-2e65be/660441027/3bd754fa-af38-43ae-af5d-118b6e11c629?X-Amz-Algorithm=AWS4-HMAC-SHA256&X-Amz-Credential=AKIAIWNJYAX4CSVEH53A%2F20230715%2Fus-east-1%2Fs3%2Faws4_request&X-Amz-Date=20230715T010751Z&X-Amz-Expires=300&X-Amz-Signature=56f57e54d28f69c91c3328916be79ea4ce859fc2616cb8c139319265951e9a8f&X-Amz-SignedHeaders=host&actor_id=0&key_id=0&repo_id=660441027&response-content-disposition=attachment%3B%20filename%3DDevboxlab.zip&response-content-type=application%2Foctet-stream |
| Full analysis: | https://app.any.run/tasks/a44e3cca-57f1-4966-8f58-009df17f513c |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2023, 01:08:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 84EA01025A7A1888E7E862C8FBCF0D54 |
| SHA1: | 2304E806F4D8A725643F7AF2F8F749BA8E7965D7 |
| SHA256: | 1552C1E143FBD50E8CE9FE6DE30CB41CB2A381E3124B5484733E6833773636F9 |
| SSDEEP: | 12:28aMGmbk9Lvttsq9AA4BRNcSJ3TAFReOIZoX9TUF/LVnAIn:23MGmoJt9HuR/UFRTXUF/xAIn |
MALICIOUS
Application was dropped or rewritten from another process
- Devboxlab.exe (PID: 1388)
- javaw.exe (PID: 696)
- Devboxlab.exe (PID: 2412)
- Devboxlab.exe (PID: 1364)
- javaw.exe (PID: 2252)
- Devboxlab.exe (PID: 1912)
Loads dropped or rewritten executable
- Devboxlab.exe (PID: 2412)
- javaw.exe (PID: 696)
- Devboxlab.exe (PID: 1912)
- javaw.exe (PID: 2252)
SUSPICIOUS
Starts CMD.EXE for commands execution
- javaw.exe (PID: 696)
- javaw.exe (PID: 2252)
Starts application with an unusual extension
- cmd.exe (PID: 1376)
- cmd.exe (PID: 2144)
- cmd.exe (PID: 2664)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 3524)
- cmd.exe (PID: 3500)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 1376)
- cmd.exe (PID: 3500)
Reads the Internet Settings
- WMIC.exe (PID: 4072)
- WMIC.exe (PID: 288)
- WMIC.exe (PID: 2716)
- WMIC.exe (PID: 3720)
Uses WMIC.EXE to obtain Sound Devices data
- cmd.exe (PID: 2664)
- cmd.exe (PID: 3524)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3348)
- WinRAR.exe (PID: 1148)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1148)
Create files in a temporary directory
- javaw.exe (PID: 696)
- javaw.exe (PID: 2252)
Application launched itself
- iexplore.exe (PID: 3348)
- msedge.exe (PID: 1228)
The process checks LSA protection
- javaw.exe (PID: 696)
- SearchProtocolHost.exe (PID: 3112)
- WMIC.exe (PID: 4072)
- javaw.exe (PID: 2252)
- WMIC.exe (PID: 288)
- WMIC.exe (PID: 3720)
- WMIC.exe (PID: 2716)
Manual execution by a user
- Devboxlab.exe (PID: 2412)
- Devboxlab.exe (PID: 1388)
- Devboxlab.exe (PID: 1364)
- Devboxlab.exe (PID: 1912)
Checks supported languages
- Devboxlab.exe (PID: 2412)
- javaw.exe (PID: 696)
- chcp.com (PID: 1364)
- chcp.com (PID: 3968)
- more.com (PID: 4076)
- chcp.com (PID: 2948)
- more.com (PID: 444)
- Devboxlab.exe (PID: 1912)
- chcp.com (PID: 1576)
- javaw.exe (PID: 2252)
- chcp.com (PID: 2524)
- more.com (PID: 2576)
- chcp.com (PID: 2512)
- more.com (PID: 1916)
Reads the machine GUID from the registry
- javaw.exe (PID: 696)
- javaw.exe (PID: 2252)
Reads the computer name
- javaw.exe (PID: 696)
- javaw.exe (PID: 2252)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
96
Monitored processes
43
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 288 | C:\Windows\System32\wbem\wmic.exe Sounddev Get /Format:List | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 444 | C:\Windows\System32\more.com | C:\Windows\System32\more.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: More Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | "C:\Users\admin\Desktop\Devboxlab\.\resources\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Devboxlab\Devboxlab.exe" | C:\Users\admin\Desktop\Devboxlab\resources\bin\javaw.exe | — | Devboxlab.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1010.13 Modules
| |||||||||||||||
| 1148 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\Devboxlab.zip" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1228 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --from-ie-to-edge=3 --ie-frame-hwnd=20138 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | ie_to_edge_stub.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1364 | C:\Windows\System32\chcp.com 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
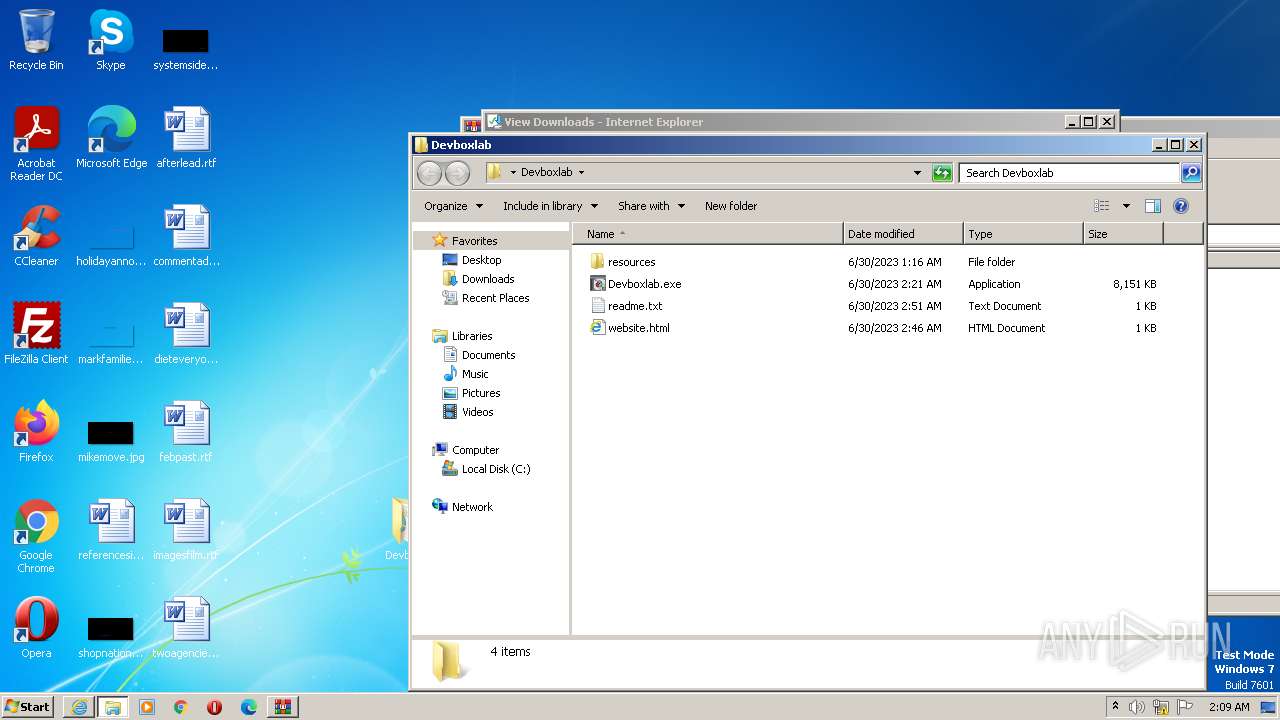
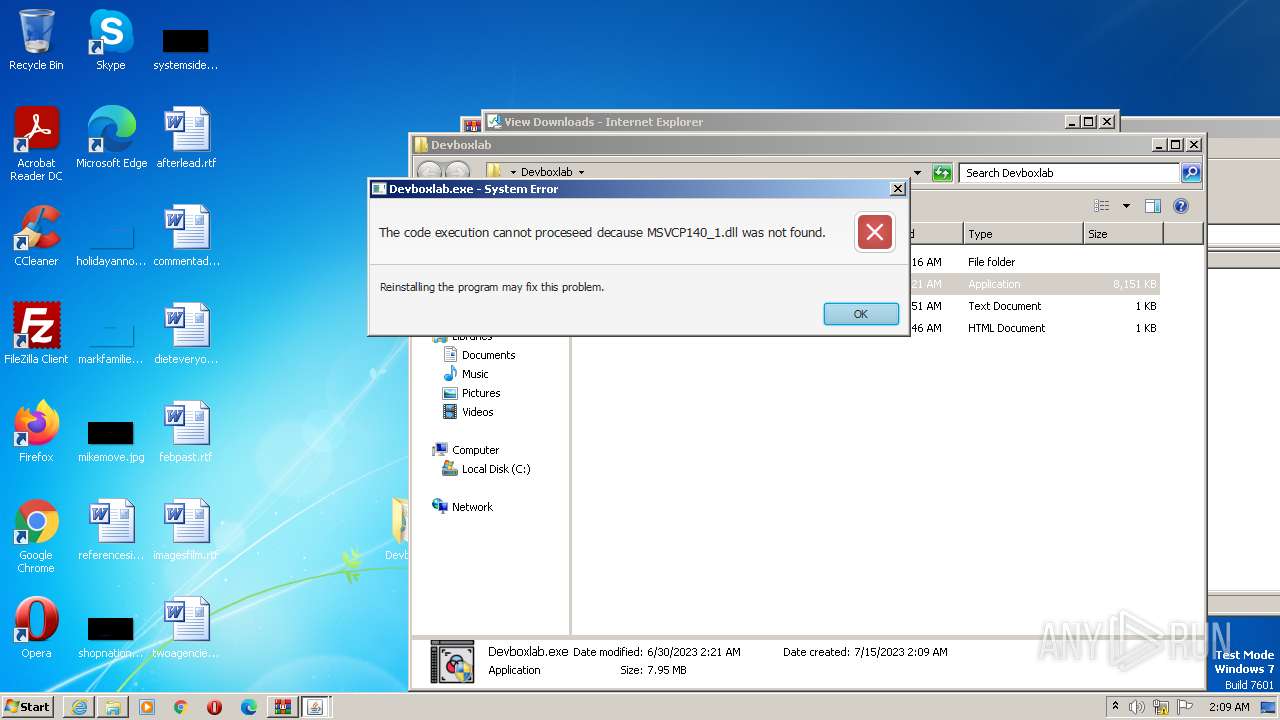
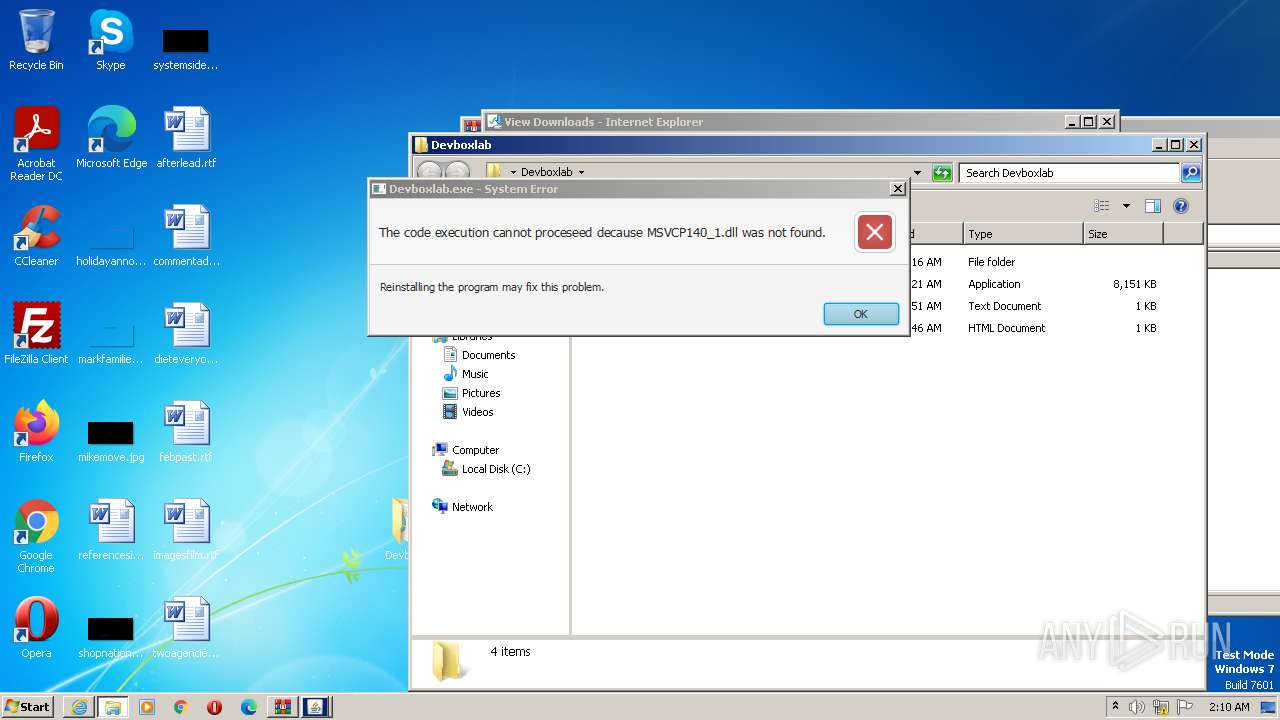
| 1364 | "C:\Users\admin\Desktop\Devboxlab\Devboxlab.exe" | C:\Users\admin\Desktop\Devboxlab\Devboxlab.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DevBoxLab: Downloading programs Exit code: 3221226540 Version: 1.1.0.6 Modules
| |||||||||||||||
| 1376 | C:\Windows\System32\cmd.exe /c "C:\Windows\System32\chcp.com 866>nul & C:\Windows\System32\wbem\wmic.exe Path Win32_VideoController Get AdapterRAM /Format:List | C:\Windows\System32\more.com" | C:\Windows\System32\cmd.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1388 | "C:\Users\admin\Desktop\Devboxlab\Devboxlab.exe" | C:\Users\admin\Desktop\Devboxlab\Devboxlab.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: DevBoxLab: Downloading programs Exit code: 3221226540 Version: 1.1.0.6 Modules
| |||||||||||||||
| 1392 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6d60f598,0x6d60f5a8,0x6d60f5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
22 003
Read events
21 890
Write events
112
Delete events
1
Modification events
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3348) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
111
Suspicious files
53
Text files
130
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF21f1a2.TMP | — | |
MD5:— | SHA256:— | |||
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF21f1d1.TMP | — | |
MD5:— | SHA256:— | |||
| 3368 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:E5DD2C64F76BF6FC010BB34002D4258F | SHA256:47506FDB2C76517ACCE7320150411FAB1775C8265B7E7EFB227073A93B93A1A1 | |||
| 3368 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Extension Scripts\LOG.old | text | |
MD5:54021011E3F52282B7E79DBE1D027290 | SHA256:BFFC56978F0ED331C5336EA385980D36B7AC755FED4318D2CC51510CBF3FF77D | |||
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Extension State\LOG.old | text | |
MD5:B86505018B5717632709F5A80576787C | SHA256:471ADF7C52778DF74BA2C8A1D8F142E4690208AC74A82A63192D211570E16D0D | |||
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:757B3624EA3EFB5BA4F0EDC237DDAE45 | SHA256:328A7CACFF96F4AC2209B5168EF0B0B58F562C376D4EEC286E89D4FF6DBA09CD | |||
| 1228 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad\settings.dat | binary | |
MD5:A2B913D3BC9B6344C76B056712064197 | SHA256:CC7E7F39A2B36FFD7D6EC45A4AA70BFB8DBEBC58EEB784D08218B0036D3AD564 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
46
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3348 | iexplore.exe | GET | 304 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?086bb8379a1b162b | US | — | — | whitelisted |
3348 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
3368 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
3368 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7a2ddfa7854568a4 | US | compressed | 4.70 Kb | whitelisted |
3348 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3368 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?522ea457cb308c1a | US | compressed | 4.70 Kb | whitelisted |
3348 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | binary | 471 b | whitelisted |
3368 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?023cb48ad2f34464 | US | compressed | 4.70 Kb | whitelisted |
3368 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0a258cf158d0b170 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1068 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3368 | iexplore.exe | 185.199.108.133:443 | — | FASTLY | US | malicious |
3368 | iexplore.exe | 23.56.204.161:443 | go.microsoft.com | AKAMAI-AS | GB | unknown |
3348 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3368 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3368 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1228 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| malicious |
edge.microsoft.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |