| download: | loader.zip |
| Full analysis: | https://app.any.run/tasks/c6749845-4a67-44aa-8c10-070d68649804 |
| Verdict: | Malicious activity |
| Analysis date: | July 18, 2019, 09:16:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 65CB72A3C2670D1944C84D46D5929969 |
| SHA1: | 0AF292EB3AF41EF3B5E051EF09D03185B1359224 |
| SHA256: | 154573E4BEA70F11BA39669931A413FAFC876CCB1559EF27369D4FEE68EC7264 |
| SSDEEP: | 98304:sEbxZ0TFbheOUW1NP71Xolw69n6e/5F4rDfLijJvKVY56TMudN9QDXfTC4N5jyw6:sonSeOX3P7holw6dxF4Hf8h1KBcDXfFc |
MALICIOUS
Loads dropped or rewritten executable
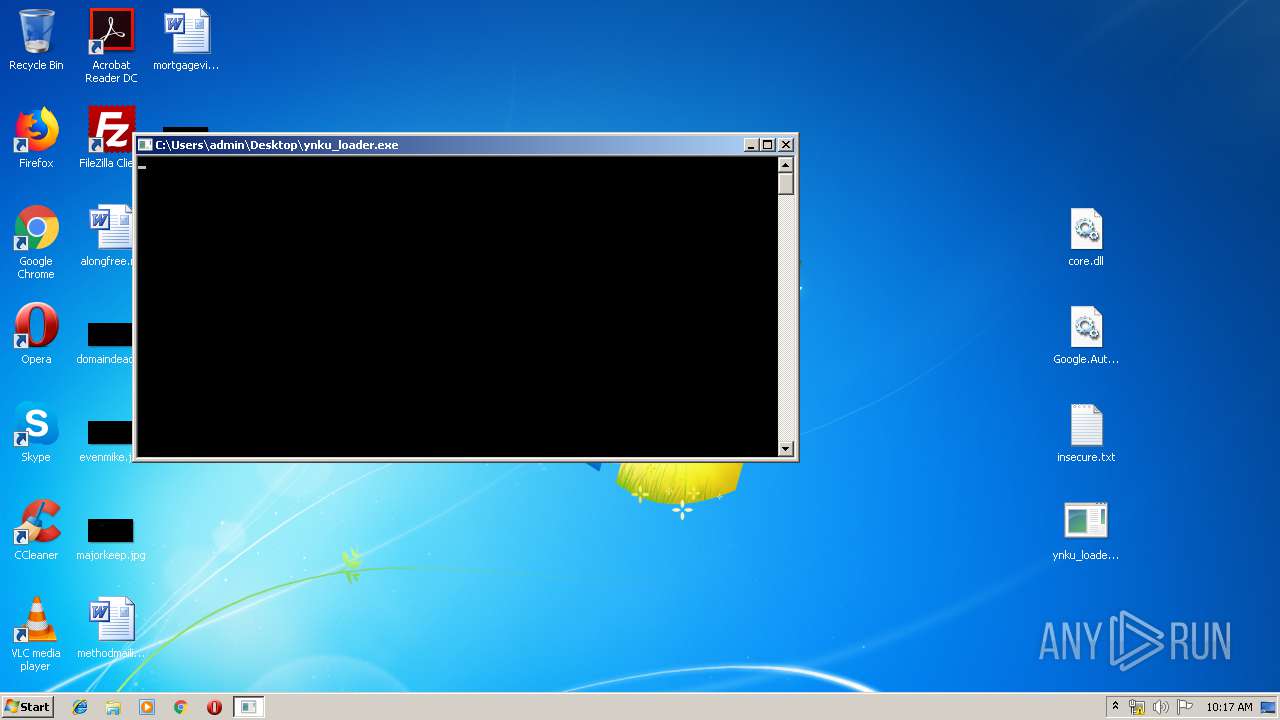
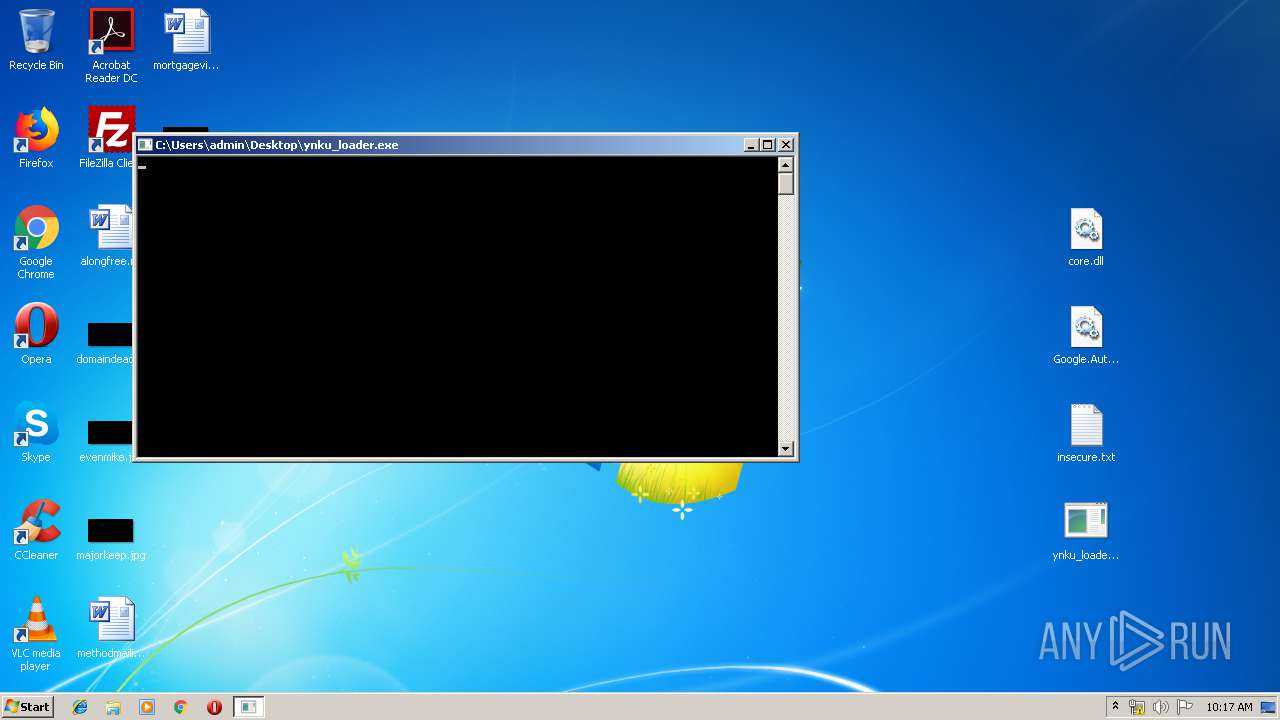
- ynku_loader.exe (PID: 544)
- SearchProtocolHost.exe (PID: 2552)
- WerFault.exe (PID: 3996)
- ynku_loader.exe (PID: 2852)
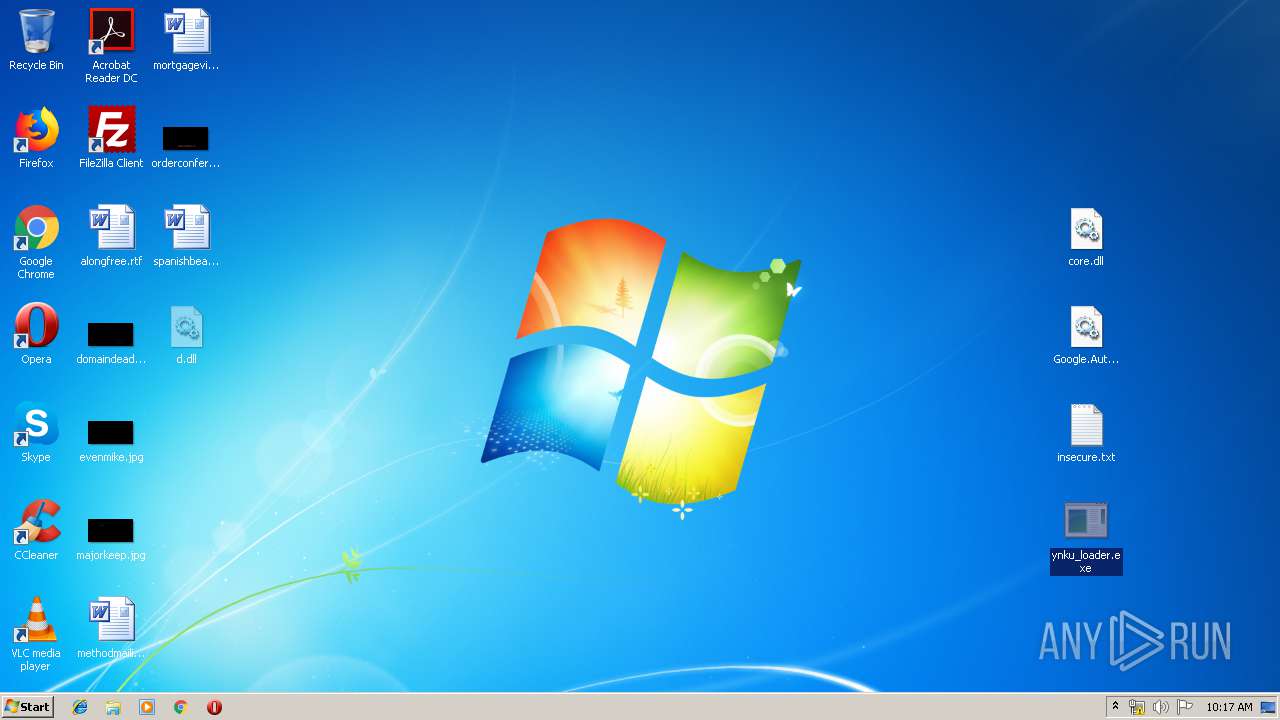
Application was dropped or rewritten from another process
- ynku_loader.exe (PID: 544)
- ynku_loader.exe (PID: 2852)
SUSPICIOUS
Executable content was dropped or overwritten
- ynku_loader.exe (PID: 2852)
- ynku_loader.exe (PID: 544)
INFO
Manual execution by user
- ynku_loader.exe (PID: 2852)
- ynku_loader.exe (PID: 544)
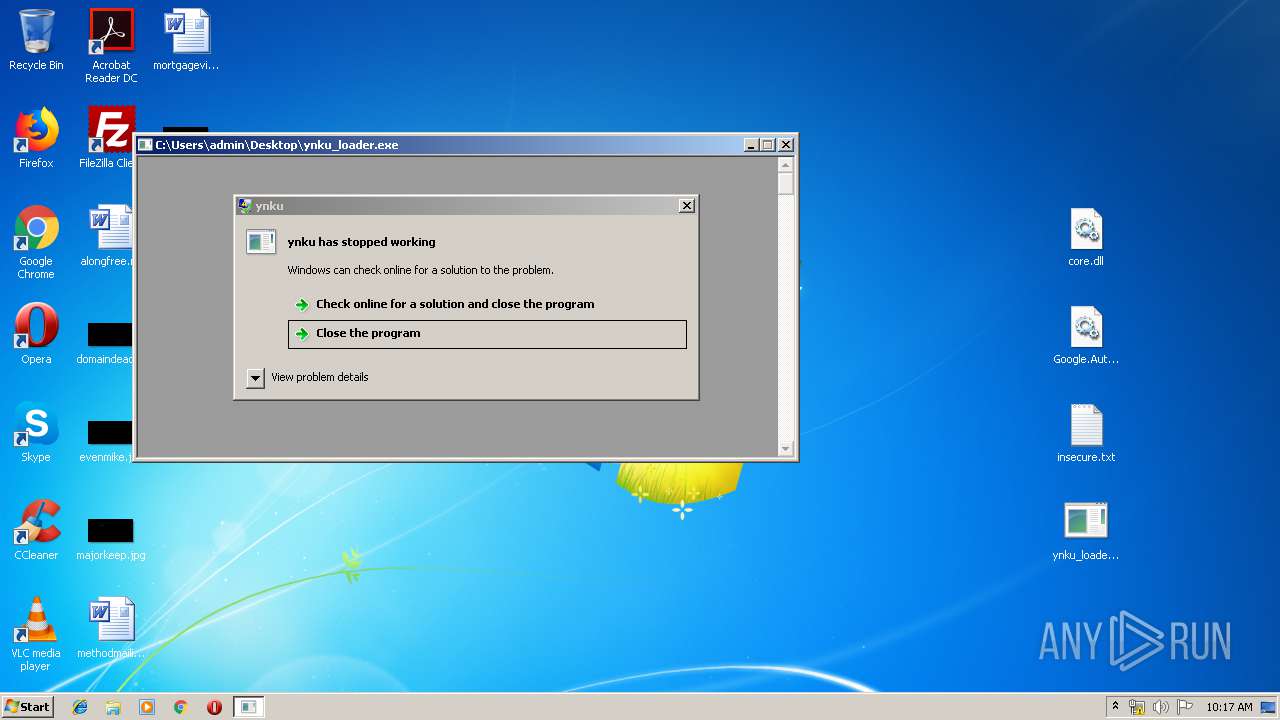
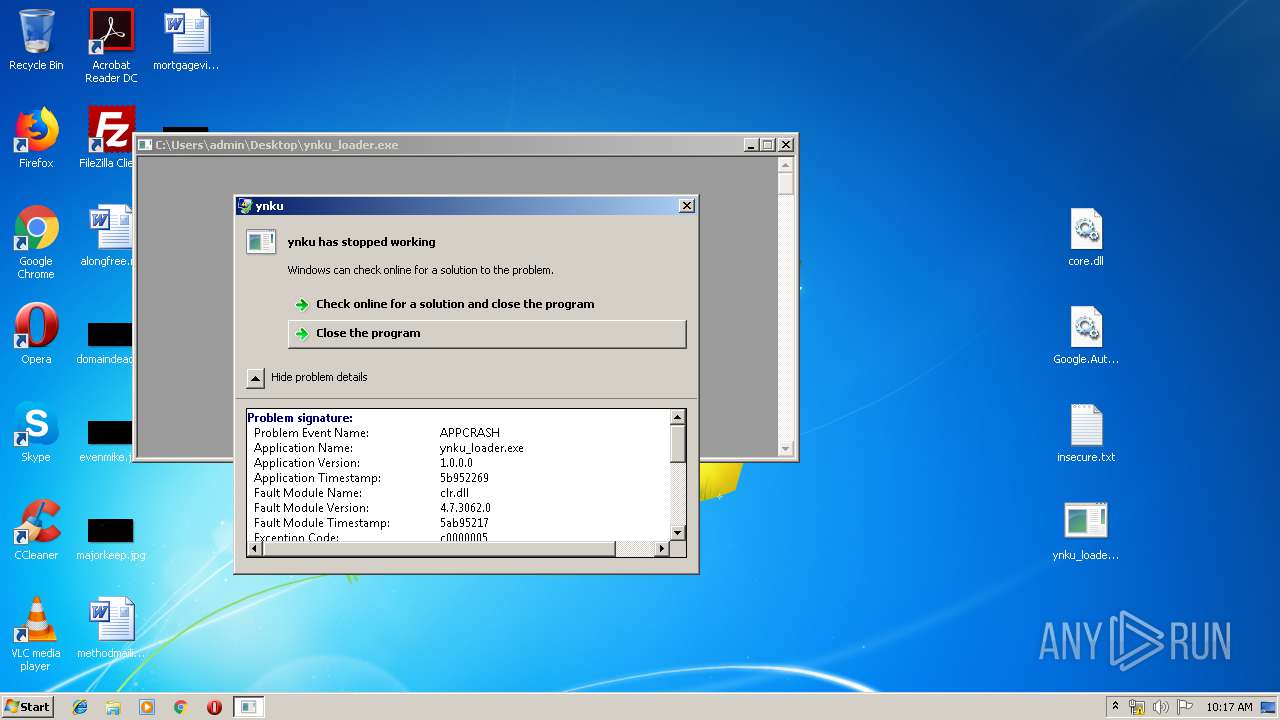
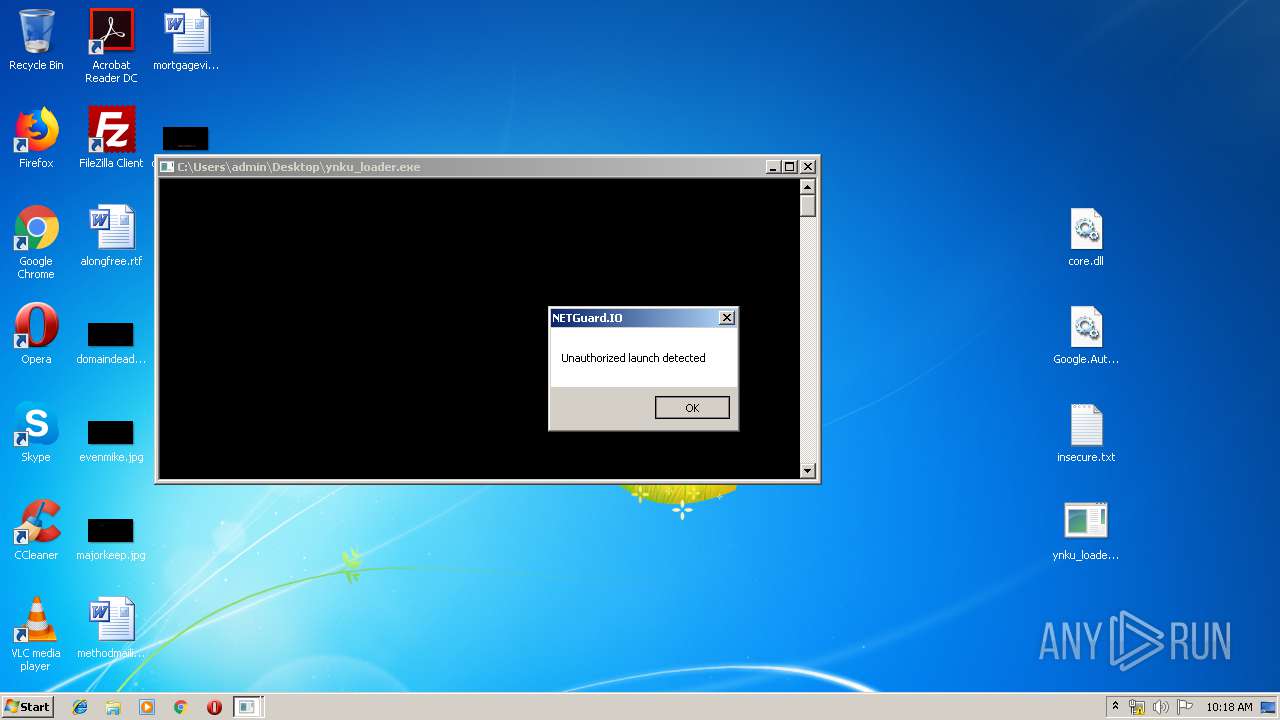
Application was crashed
- ynku_loader.exe (PID: 544)
- ynku_loader.exe (PID: 2852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (60) |
|---|---|---|
| .zip | | | ZIP compressed archive (40) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:07:16 19:32:21 |
| ZipCRC: | 0xf7729651 |
| ZipCompressedSize: | 2265630 |
| ZipUncompressedSize: | 2366976 |
| ZipFileName: | core.dll |
Total processes
44
Monitored processes
5
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\Users\admin\Desktop\ynku_loader.exe" | C:\Users\admin\Desktop\ynku_loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ynku Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2552 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\ynku_loader.exe" | C:\Users\admin\Desktop\ynku_loader.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ynku Exit code: 3221225477 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3488 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\loader.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3996 | C:\Windows\system32\WerFault.exe -u -p 544 -s 720 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
450
Read events
428
Write events
22
Delete events
0
Modification events
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\loader.zip | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3488) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2552) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2552) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
2
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3488.44155\core.dll | — | |
MD5:— | SHA256:— | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3488.44155\Google.Authenticator.dll | — | |
MD5:— | SHA256:— | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3488.44155\insecure.txt | — | |
MD5:— | SHA256:— | |||
| 3488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3488.44155\ynku_loader.exe | — | |
MD5:— | SHA256:— | |||
| 3996 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\ynku_loader.exe.544.dmp | — | |
MD5:— | SHA256:— | |||
| 544 | ynku_loader.exe | C:\Users\admin\Desktop\d.dll | executable | |
MD5:— | SHA256:— | |||
| 2852 | ynku_loader.exe | C:\Users\admin\Desktop\d.dll | executable | |
MD5:— | SHA256:— | |||
| 3996 | WerFault.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\WER\ReportArchive\AppCrash_ynku_loader.exe_8f2f2caf19af9b16e86677b4e2e54b5b256875b4_0f926925\Report.wer | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report