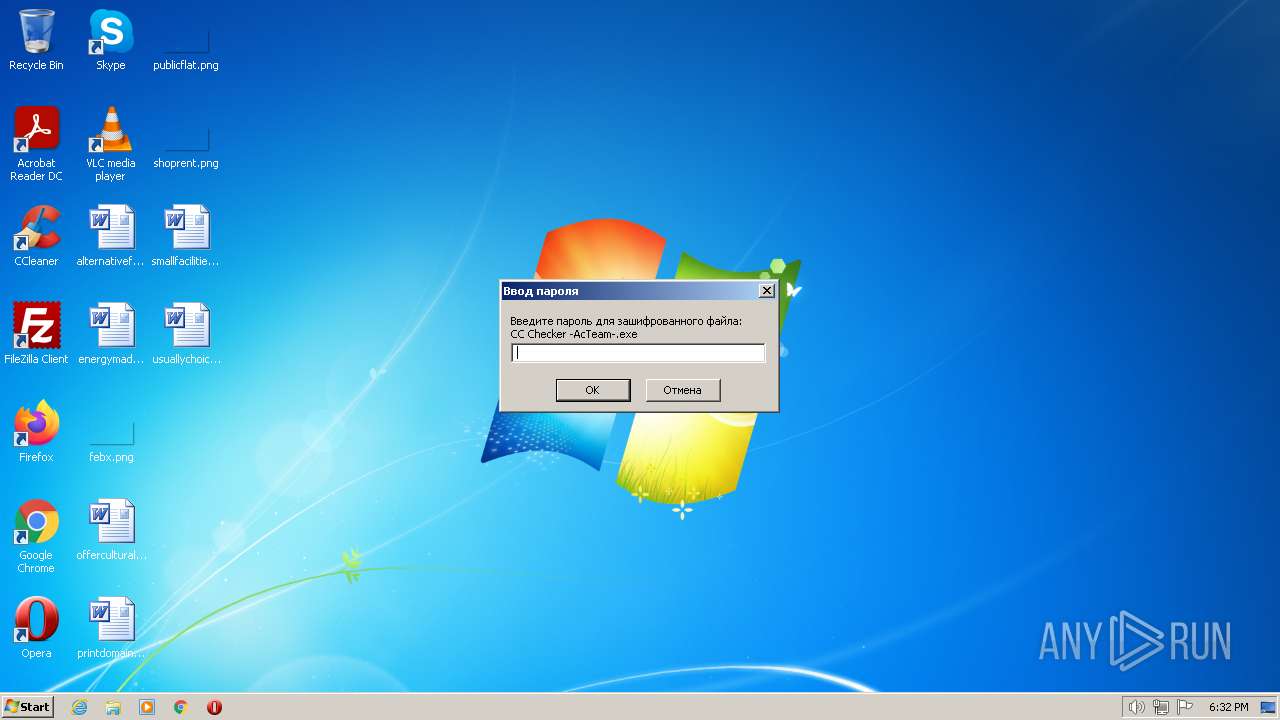
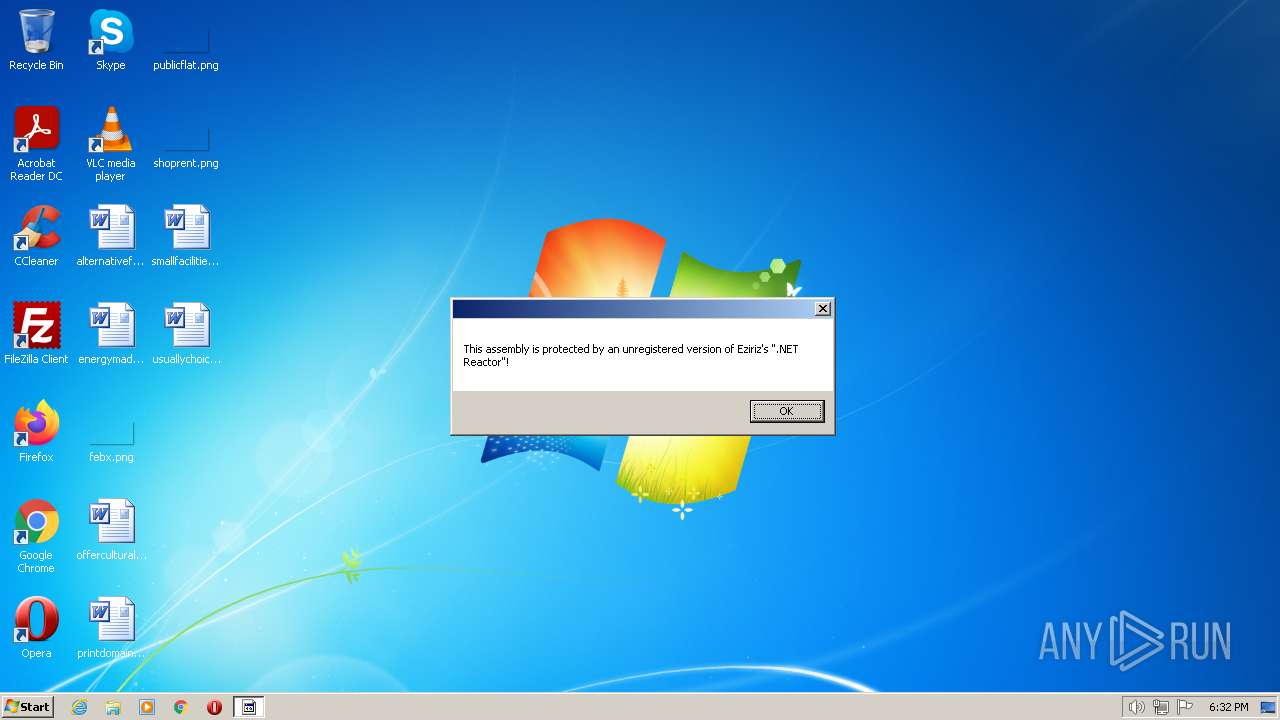
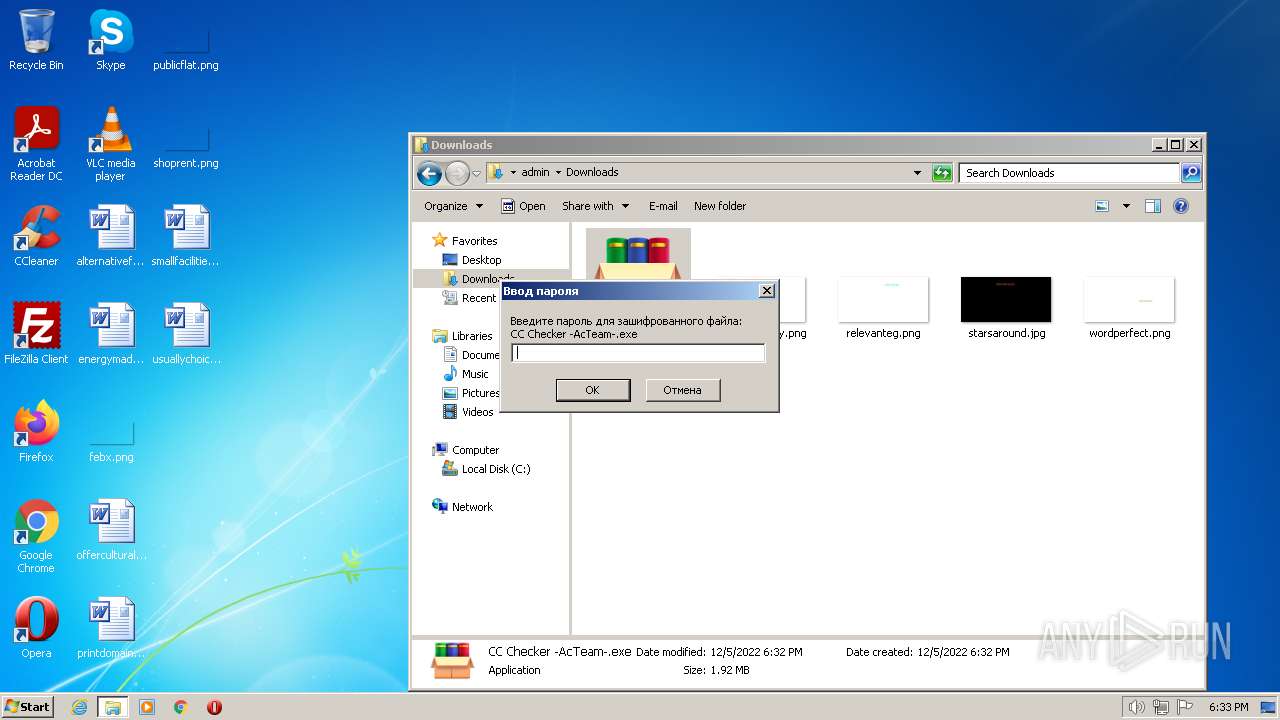
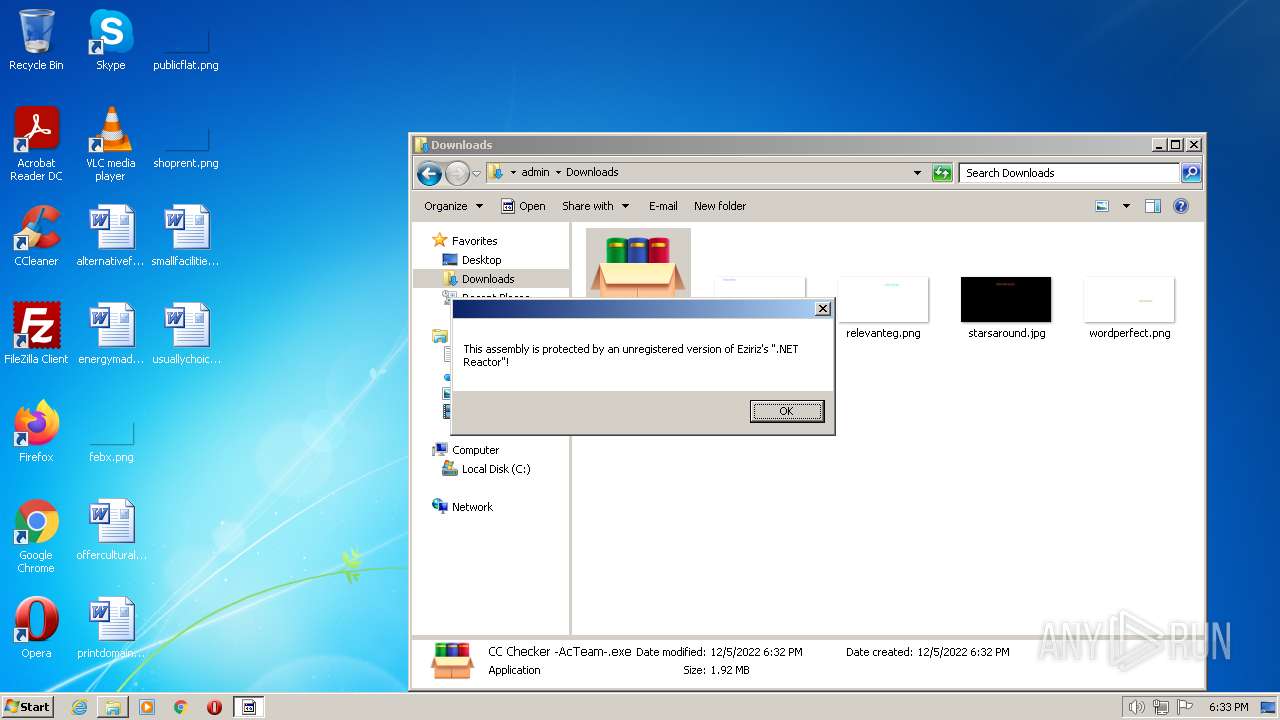
| File name: | CC Checker -AcTeam-.exe |
| Full analysis: | https://app.any.run/tasks/e4643c34-749a-40e2-b331-29c143fbd329 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 18:32:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F045688821C95892F36B1F1FB81C3DAD |
| SHA1: | E4FB3608A2ABAB3A79AE92557C63147ACFC5B195 |
| SHA256: | 151CEEA1A97415F8CE6BA897FB80E72B11B1C8BEF9D48968BBEFBD34199859AC |
| SSDEEP: | 49152:ABRNlVlypZAz25Vq3pYsq6wZKbbW5Etx6TbxEsPAdZkdqc:a/lgAz25V+qpZKGuX6T9jskdqc |
MALICIOUS
Application was dropped or rewritten from another process
- CC Checker -AcTeam-.exe (PID: 1248)
- CC_Checker -AcTeam-.exe (PID: 1920)
- CC Checker -AcTeam-.exe (PID: 1472)
Stealerium is detected
- CC Checker -AcTeam-.exe (PID: 1248)
Steals credentials from Web Browsers
- CC Checker -AcTeam-.exe (PID: 1248)
Writes to the Start menu file
- CC_Checker -AcTeam-.exe (PID: 1920)
Drops the executable file immediately after the start
- CC_Checker -AcTeam-.exe (PID: 1920)
- CC Checker -AcTeam-.exe (PID: 3632)
SUSPICIOUS
Reads the Internet Settings
- CC Checker -AcTeam-.exe (PID: 1752)
- CC Checker -AcTeam-.exe (PID: 1248)
- CC Checker -AcTeam-.exe (PID: 3632)
- CC Checker -AcTeam-.exe (PID: 1472)
Reads settings of System Certificates
- CC Checker -AcTeam-.exe (PID: 1248)
Reads browser cookies
- CC Checker -AcTeam-.exe (PID: 1248)
Loads DLL from Mozilla Firefox
- CC Checker -AcTeam-.exe (PID: 1248)
Executable content was dropped or overwritten
- CC_Checker -AcTeam-.exe (PID: 1920)
- CC Checker -AcTeam-.exe (PID: 3632)
INFO
Checks supported languages
- CC Checker -AcTeam-.exe (PID: 1752)
- CC Checker -AcTeam-.exe (PID: 1248)
- chcp.com (PID: 2548)
- chcp.com (PID: 3460)
- CC_Checker -AcTeam-.exe (PID: 1920)
- CC Checker -AcTeam-.exe (PID: 3632)
- CC Checker -AcTeam-.exe (PID: 1472)
Reads the computer name
- CC Checker -AcTeam-.exe (PID: 1248)
- CC Checker -AcTeam-.exe (PID: 1752)
- CC_Checker -AcTeam-.exe (PID: 1920)
- CC Checker -AcTeam-.exe (PID: 3632)
- CC Checker -AcTeam-.exe (PID: 1472)
Reads Environment values
- CC Checker -AcTeam-.exe (PID: 1248)
- CC Checker -AcTeam-.exe (PID: 1472)
Starts application with an unusual extension
- cmd.exe (PID: 2348)
- cmd.exe (PID: 3316)
Manual execution by a user
- explorer.exe (PID: 3820)
- CC Checker -AcTeam-.exe (PID: 3632)
Drops a file that was compiled in debug mode
- CC_Checker -AcTeam-.exe (PID: 1920)
- CC Checker -AcTeam-.exe (PID: 3632)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2022-Mar-03 13:15:57 |
| Debug artifacts: |
|
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 272 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 6 |
| TimeDateStamp: | 2022-Mar-03 13:15:57 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 203740 | 203776 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.71296 |
.rdata | 208896 | 44736 | 45056 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.26161 |
.data | 253952 | 149280 | 4096 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.38746 |
.didat | 405504 | 400 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.33273 |
.rsrc | 409600 | 57424 | 57856 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.80217 |
.reloc | 471040 | 9020 | 9216 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.62301 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.97409 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
2 | 5.10026 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 5.25868 | 3752 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 5.02609 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 5.18109 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 5.04307 | 9640 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 7.94547 | 15729 | Latin 1 / Western European | UNKNOWN | RT_ICON |
8 | 3.71728 | 582 | Latin 1 / Western European | UNKNOWN | RT_STRING |
9 | 3.73856 | 422 | Latin 1 / Western European | UNKNOWN | RT_STRING |
10 | 3.55807 | 220 | Latin 1 / Western European | UNKNOWN | RT_STRING |
Imports
KERNEL32.dll |
OLEAUT32.dll |
USER32.dll (delay-loaded) |
gdiplus.dll |
Total processes
56
Monitored processes
14
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1244 | netsh wlan show profile | C:\Windows\system32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
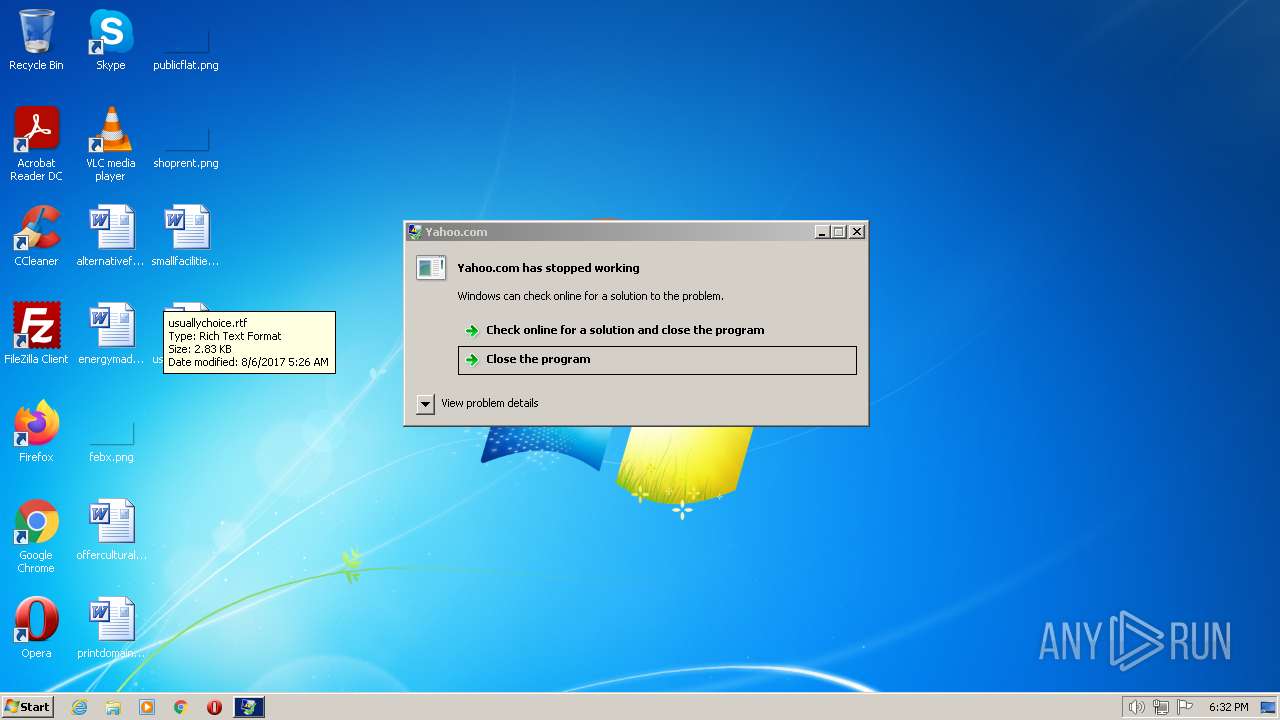
| 1248 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\CC Checker -AcTeam-.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\CC Checker -AcTeam-.exe | CC Checker -AcTeam-.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Yahoo.com Exit code: 0 Version: 1.4.1.2 Modules
| |||||||||||||||
| 1472 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\CC Checker -AcTeam-.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\CC Checker -AcTeam-.exe | CC Checker -AcTeam-.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Yahoo.com Exit code: 0 Version: 1.4.1.2 Modules
| |||||||||||||||
| 1752 | "C:\Users\admin\Downloads\CC Checker -AcTeam-.exe" | C:\Users\admin\Downloads\CC Checker -AcTeam-.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1872 | findstr All | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1920 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\CC_Checker -AcTeam-.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\CC_Checker -AcTeam-.exe | CC Checker -AcTeam-.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Google Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2348 | "cmd.exe" /C chcp 65001 && netsh wlan show profile | findstr All | C:\Windows\system32\cmd.exe | — | CC Checker -AcTeam-.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2548 | chcp 65001 | C:\Windows\system32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2688 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3316 | "cmd.exe" /C chcp 65001 && netsh wlan show networks mode=bssid | C:\Windows\system32\cmd.exe | — | CC Checker -AcTeam-.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
6 356
Read events
6 206
Write events
150
Delete events
0
Modification events
| (PID) Process: | (1752) CC Checker -AcTeam-.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1752) CC Checker -AcTeam-.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1752) CC Checker -AcTeam-.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1752) CC Checker -AcTeam-.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1248) CC Checker -AcTeam-.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CC Checker -AcTeam-_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (1248) CC Checker -AcTeam-.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CC Checker -AcTeam-_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (1248) CC Checker -AcTeam-.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CC Checker -AcTeam-_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (1248) CC Checker -AcTeam-.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CC Checker -AcTeam-_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (1248) CC Checker -AcTeam-.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CC Checker -AcTeam-_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (1248) CC Checker -AcTeam-.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\CC Checker -AcTeam-_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
Executable files
5
Suspicious files
4
Text files
35
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\Temp\tmp41DC.tmp.dat | — | |
MD5:— | SHA256:— | |||
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\dc2815bdebaeab526eaa882516445489\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Pictures\appearfriday.png | image | |
MD5:— | SHA256:— | |||
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\Temp\Stealerium-Latest.log | text | |
MD5:— | SHA256:— | |||
| 1752 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\CC Checker -AcTeam-.exe | executable | |
MD5:— | SHA256:— | |||
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\dc2815bdebaeab526eaa882516445489\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Documents\environmentbox.rtf | text | |
MD5:— | SHA256:— | |||
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\dc2815bdebaeab526eaa882516445489\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Desktop\energymade.rtf | text | |
MD5:— | SHA256:— | |||
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\dc2815bdebaeab526eaa882516445489\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Downloads\relevanteg.png | image | |
MD5:— | SHA256:— | |||
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\dc2815bdebaeab526eaa882516445489\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Desktop\alternativeflash.rtf | text | |
MD5:— | SHA256:— | |||
| 1248 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\dc2815bdebaeab526eaa882516445489\admin@USER-PC_en-US\Grabber\DRIVE-C\Users\admin\Pictures\includesv.png | image | |
MD5:— | SHA256:— | |||
| 1752 | CC Checker -AcTeam-.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\CC_Checker -AcTeam-.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
3
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1248 | CC Checker -AcTeam-.exe | 162.159.136.232:443 | discord.com | CLOUDFLARENET | — | shared |
1248 | CC Checker -AcTeam-.exe | 104.18.115.97:80 | icanhazip.com | CLOUDFLARENET | — | malicious |
1472 | CC Checker -AcTeam-.exe | 162.159.136.232:443 | discord.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discord.com |
| whitelisted |
icanhazip.com |
| shared |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
1248 | CC Checker -AcTeam-.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |