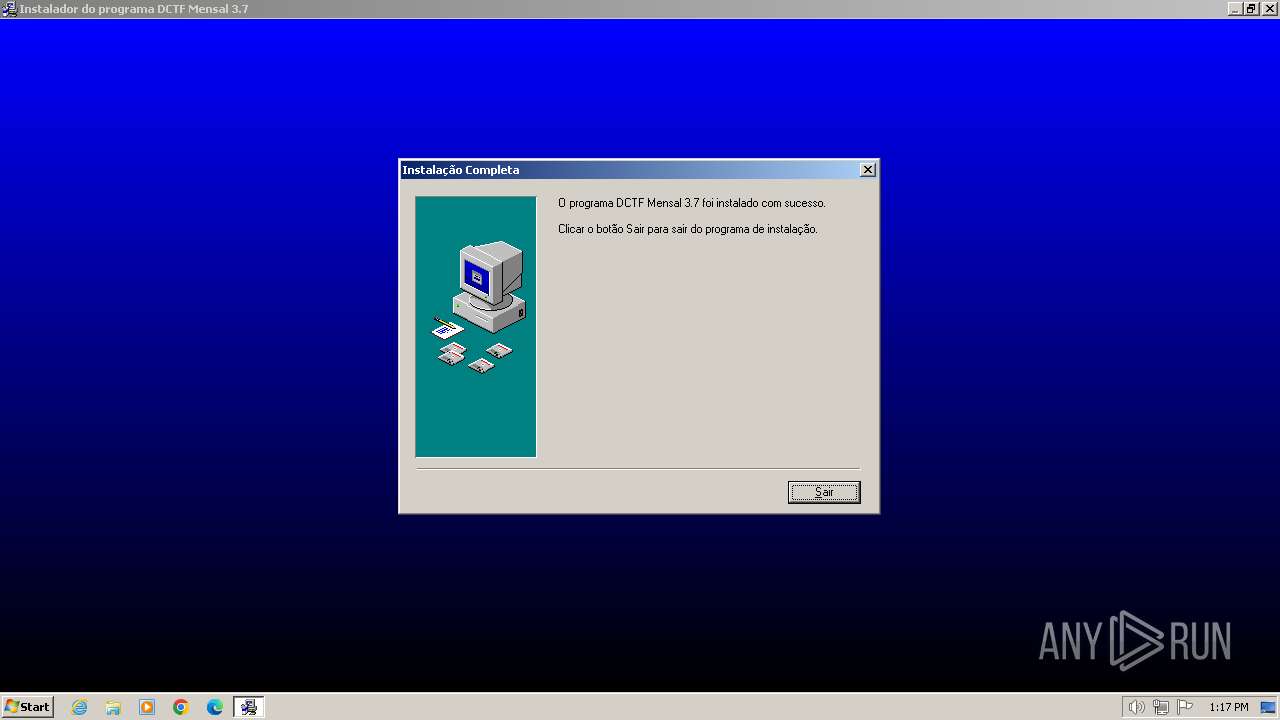
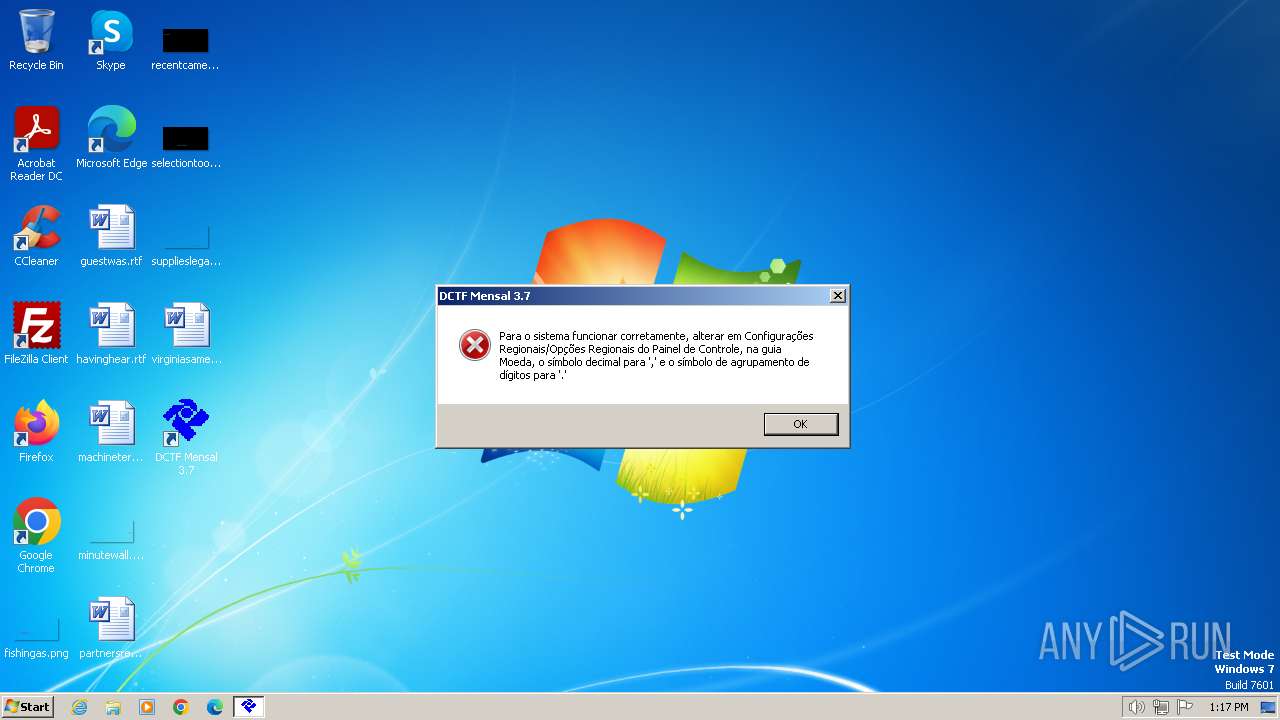
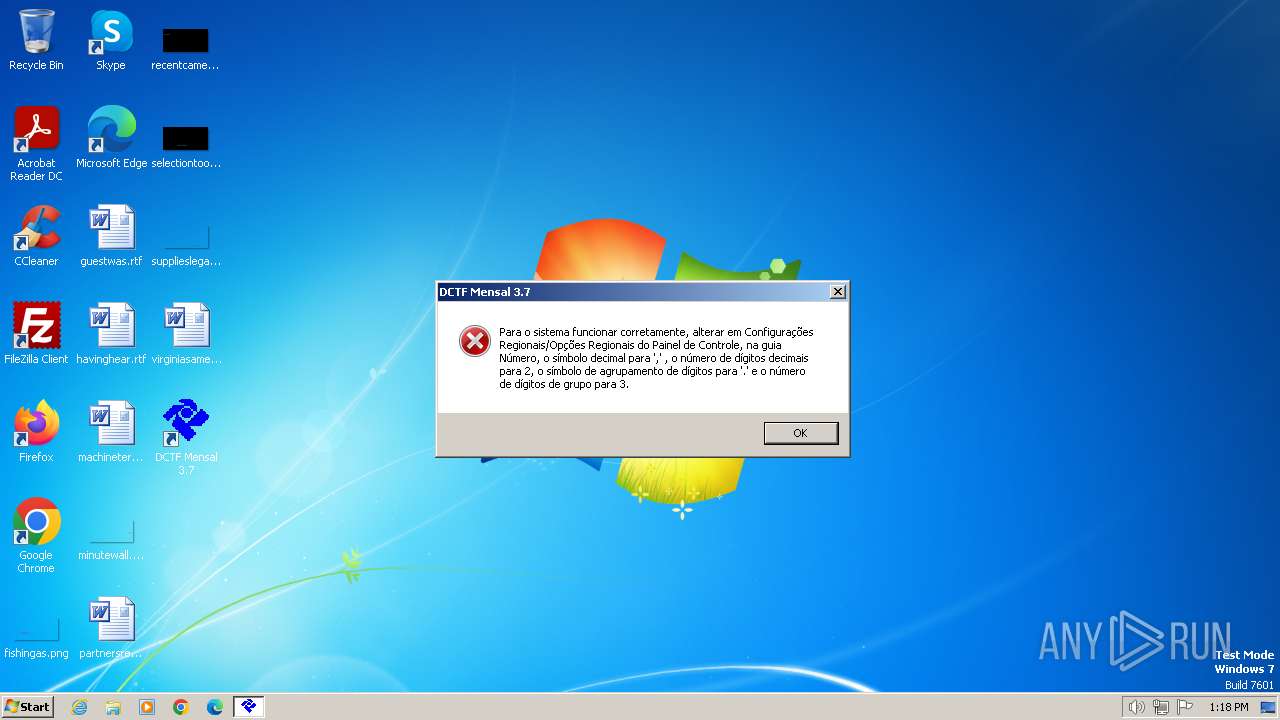
| File name: | dctfmensalv3-7.exe |
| Full analysis: | https://app.any.run/tasks/abdcf51f-357a-4d04-9e89-3339fe1d614d |
| Verdict: | Malicious activity |
| Analysis date: | March 01, 2024, 13:17:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 05F42D77E0B6115F3C3517BED2E557F1 |
| SHA1: | B85D004343FAAC509B7A4EBCE4C09AB67CC02934 |
| SHA256: | 1504CEBAE3AE60D4E780D43A383357AF13718002F5476B8E6288B86E405BF410 |
| SSDEEP: | 98304:RpgNCSp0+JopWSMi4IBnQW+BtXU/0vK9GPxUd/hwXZFR7+Sa2S8gic1xvvukKvIZ:yuJma1xQ6yJwDNSK |
MALICIOUS
Creates a writable file in the system directory
- dctfmensalv3-7.exe (PID: 3660)
Drops the executable file immediately after the start
- dctfmensalv3-7.exe (PID: 3660)
SUSPICIOUS
Process drops legitimate windows executable
- dctfmensalv3-7.exe (PID: 3660)
Creates/Modifies COM task schedule object
- GLJFA3F.tmp (PID: 3428)
- GLJFA3F.tmp (PID: 3992)
- GLJFA3F.tmp (PID: 1836)
- GLJFA3F.tmp (PID: 2580)
- GLJFA3F.tmp (PID: 2232)
- GLJFA3F.tmp (PID: 3276)
- GLJFA3F.tmp (PID: 4004)
- GLJFA3F.tmp (PID: 4044)
- GLJFA3F.tmp (PID: 2892)
- GLJFA3F.tmp (PID: 2208)
- GLJFA3F.tmp (PID: 2184)
- GLJFA3F.tmp (PID: 3684)
Executable content was dropped or overwritten
- dctfmensalv3-7.exe (PID: 3660)
The process drops C-runtime libraries
- dctfmensalv3-7.exe (PID: 3660)
Starts application with an unusual extension
- dctfmensalv3-7.exe (PID: 3660)
INFO
Checks supported languages
- dctfmensalv3-7.exe (PID: 3660)
- GLJFA3F.tmp (PID: 3992)
- GLJFA3F.tmp (PID: 2120)
- GLJFA3F.tmp (PID: 1836)
- GLJFA3F.tmp (PID: 2580)
- GLJFA3F.tmp (PID: 3276)
- GLJFA3F.tmp (PID: 2232)
- GLJFA3F.tmp (PID: 4000)
- GLJFA3F.tmp (PID: 4004)
- GLJFA3F.tmp (PID: 4044)
- GLJFA3F.tmp (PID: 2892)
- GLJFA3F.tmp (PID: 2208)
- GLJFA3F.tmp (PID: 3488)
- GLJFA3F.tmp (PID: 1972)
- GLJFA3F.tmp (PID: 1348)
- GLJFA3F.tmp (PID: 1824)
- GLJFA3F.tmp (PID: 1928)
- GLJFA3F.tmp (PID: 3724)
- GLJFA3F.tmp (PID: 2168)
- GLJFA3F.tmp (PID: 3164)
- GLJFA3F.tmp (PID: 3684)
- GLJFA3F.tmp (PID: 2420)
- GLJFA3F.tmp (PID: 2072)
- GLJFA3F.tmp (PID: 2184)
- DCTFMensal37.exe (PID: 1572)
- DCTFMensal37.exe (PID: 1576)
- GLJFA3F.tmp (PID: 3304)
- GLJFA3F.tmp (PID: 1876)
- GLJFA3F.tmp (PID: 1492)
- GLJFA3F.tmp (PID: 2624)
- GLJFA3F.tmp (PID: 1040)
- GLJFA3F.tmp (PID: 3428)
Reads the computer name
- GLJFA3F.tmp (PID: 3428)
- dctfmensalv3-7.exe (PID: 3660)
- GLJFA3F.tmp (PID: 3992)
- GLJFA3F.tmp (PID: 1836)
- GLJFA3F.tmp (PID: 2120)
- GLJFA3F.tmp (PID: 4044)
- GLJFA3F.tmp (PID: 3684)
- GLJFA3F.tmp (PID: 2184)
Reads mouse settings
- GLJFA3F.tmp (PID: 3992)
Create files in a temporary directory
- dctfmensalv3-7.exe (PID: 3660)
Creates files in the program directory
- dctfmensalv3-7.exe (PID: 3660)
Manual execution by a user
- DCTFMensal37.exe (PID: 1572)
- DCTFMensal37.exe (PID: 1576)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Wise Installer executable (91.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (5.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2001:10:25 19:47:11+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, Removable run from swap |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 8704 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21af |
| OSVersion: | 4 |
| ImageVersion: | 4 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.7.0.0 |
| ProductVersionNumber: | 3.7.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | SERPRO |
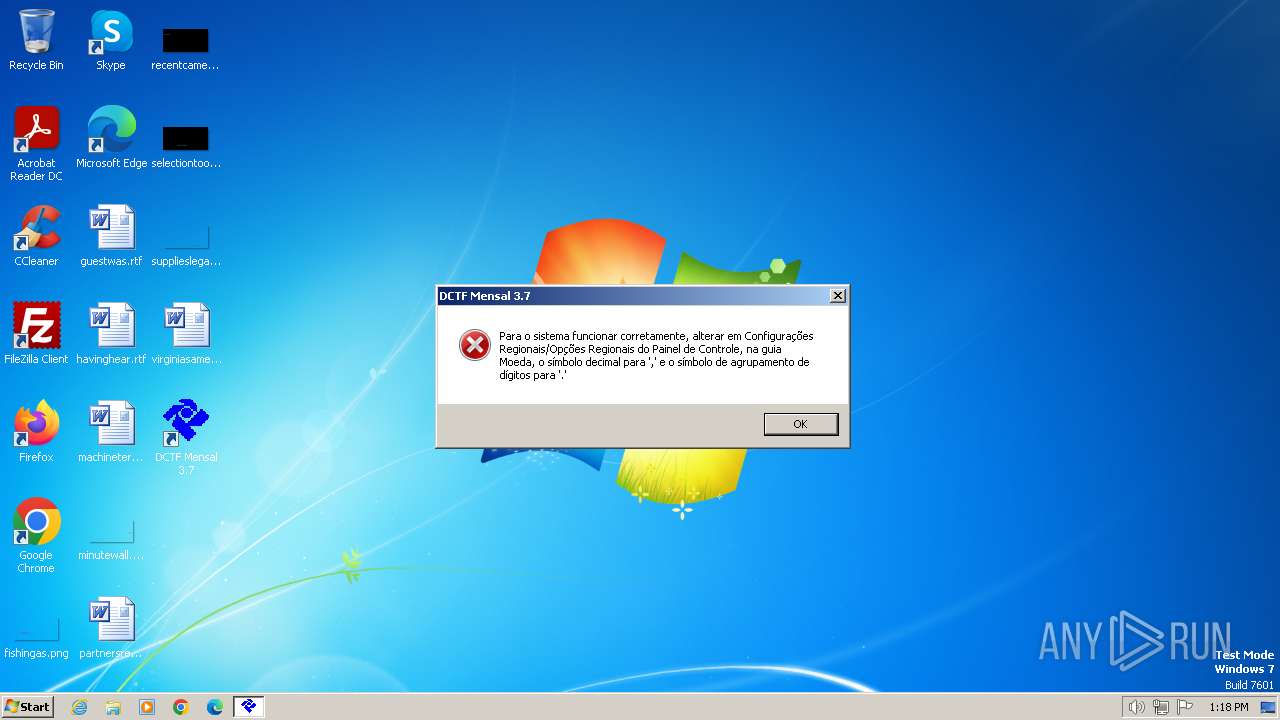
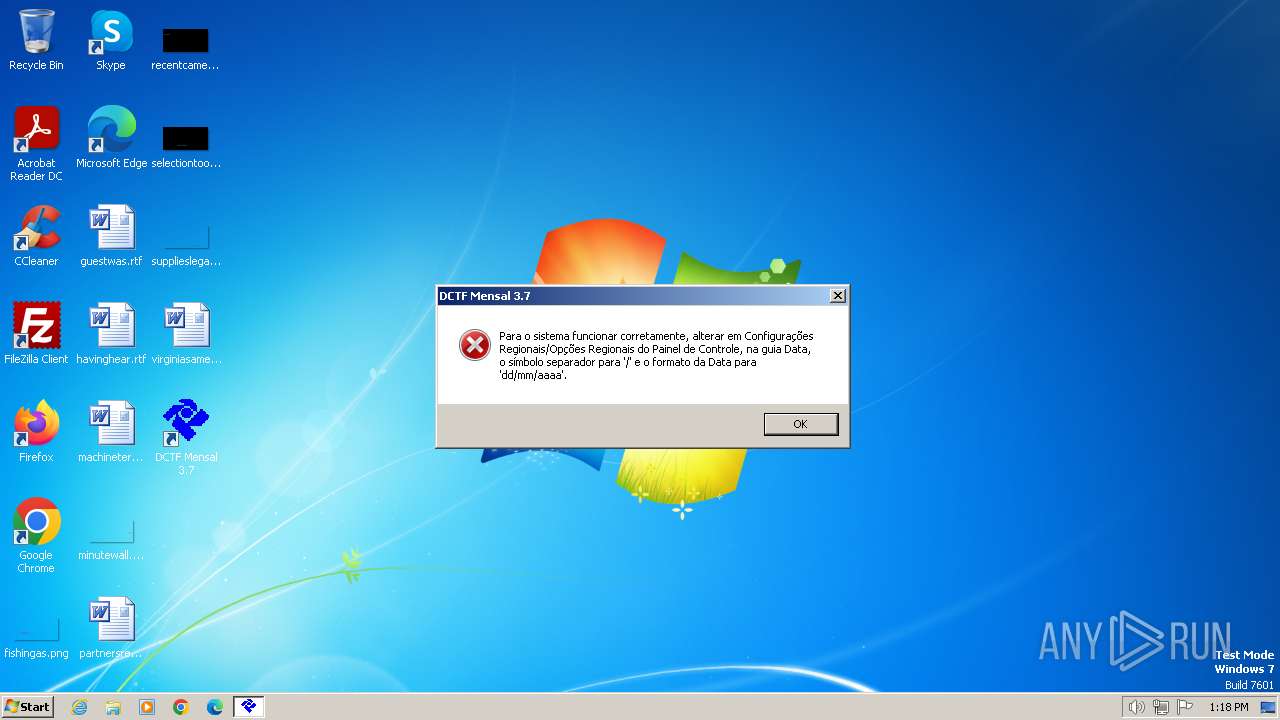
| FileDescription: | PGD DCTF Mensal 3.7 |
| FileVersion: | 3.7 |
| LegalCopyright: | Receita Federal do Brasil (RFB) |
Total processes
72
Monitored processes
33
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1040 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\oleaut32.dll | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\Msrepl35.dll | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1492 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\msvcrt40.dll | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1572 | "C:\Arquivos de Programas RFB\DCTF Mensal 3.7\DCTFMensal37.exe" | C:\Arquivos de Programas RFB\DCTF Mensal 3.7\DCTFMensal37.exe | — | explorer.exe | |||||||||||
User: admin Company: SERPRO Integrity Level: MEDIUM Exit code: 0 Version: 3.07 Modules
| |||||||||||||||
| 1576 | "C:\Arquivos de Programas RFB\DCTF Mensal 3.7\DCTFMensal37.exe" | C:\Arquivos de Programas RFB\DCTF Mensal 3.7\DCTFMensal37.exe | — | explorer.exe | |||||||||||
User: admin Company: SERPRO Integrity Level: MEDIUM Exit code: 0 Version: 3.07 Modules
| |||||||||||||||
| 1824 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\Msrd2x35.dll | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1836 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\Dblist32.ocx | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1876 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\comcat.dll | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1928 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\Msjint35.dll | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1972 | "C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp" C:\Windows\System32\expsrv.dll | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | — | dctfmensalv3-7.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
9 193
Read events
5 861
Write events
3 244
Delete events
88
Modification events
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\comcat.dll |
Value: 2 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\msvcrt40.dll |
Value: 2 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\olepro32.dll |
Value: 2 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\oleaut32.dll |
Value: 2 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\msvbvm60.dll |
Value: 2 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\ComDlg32.ocx |
Value: 1 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\MSCOMCTL.OCX |
Value: 2 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\hhctrl.ocx |
Value: 2 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\Dblist32.ocx |
Value: 1 | |||
| (PID) Process: | (3660) dctfmensalv3-7.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\SharedDLLs |
| Operation: | write | Name: | C:\Windows\System32\Tinumb6.ocx |
Value: 1 | |||
Executable files
103
Suspicious files
11
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3660 | dctfmensalv3-7.exe | C:\Users\admin\AppData\Local\Temp\GLKFC34.tmp | executable | |
MD5:3DF61E5730883B2D338ADDD7ACBE4BC4 | SHA256:2EFE9A54C8EB878711D9B6CD18F276838645AFF52FE69D8A864376CB258EC616 | |||
| 3660 | dctfmensalv3-7.exe | C:\Users\admin\AppData\Local\Temp\GLJFA3F.tmp | executable | |
MD5:6F608D264503796BEBD7CD66B687BE92 | SHA256:49833D2820AFB1D7409DFBD916480F2CDF5787D2E2D94166725BEB9064922D5D | |||
| 3660 | dctfmensalv3-7.exe | C:\Users\admin\AppData\Local\Temp\GLCFA2F.tmp | executable | |
MD5:8C97D8BB1470C6498E47B12C5A03CE39 | SHA256:A87F19F9FEE475D2B2E82ACFB4589BE6D816B613064CD06826E1D4C147BEB50A | |||
| 3660 | dctfmensalv3-7.exe | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | executable | |
MD5:3B2E23D259394C701050486E642D14FA | SHA256:166D7156142F3EE09FA69EB617DD22E4FD248AA80A1AC08767DB6AD99A2705C1 | |||
| 3660 | dctfmensalv3-7.exe | C:\Windows\system32\~GLH0002.TMP | executable | |
MD5:350FCB4ED44AF46F28CFAAFA37543E3E | SHA256:CBA6240BF4359E9FB72517C0BB69F8ADDF3F524D98D75A3BC81223A6CC08ED3B | |||
| 3660 | dctfmensalv3-7.exe | C:\Windows\System32\WiseDLL.dll | executable | |
MD5:5664566021FD53758A9AE087C3A29485 | SHA256:5FCFC480B3C7BC2DC18E39667CF4A3313575C6A5A614EBDCCB71AF664C19739D | |||
| 3660 | dctfmensalv3-7.exe | C:\Users\admin\AppData\Local\Temp\GLF1F.tmp | executable | |
MD5:3B2E23D259394C701050486E642D14FA | SHA256:166D7156142F3EE09FA69EB617DD22E4FD248AA80A1AC08767DB6AD99A2705C1 | |||
| 3660 | dctfmensalv3-7.exe | C:\Windows\system32\~GLH0001.TMP | executable | |
MD5:5664566021FD53758A9AE087C3A29485 | SHA256:5FCFC480B3C7BC2DC18E39667CF4A3313575C6A5A614EBDCCB71AF664C19739D | |||
| 3660 | dctfmensalv3-7.exe | C:\Windows\system32\temp.005 | executable | |
MD5:D76F0EAB36F83A31D411AEAF70DA7396 | SHA256:46F4FDB12C30742FF4607876D2F36CF432CDC7EC3D2C99097011448FC57E997C | |||
| 3660 | dctfmensalv3-7.exe | C:\Windows\system32\temp.003 | executable | |
MD5:0D303488CCE054204C323C37657AFA34 | SHA256:B34A300B2DD2B8A2946A451549202E8F9705AA38C19A4E2D73AB684CD93736C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |