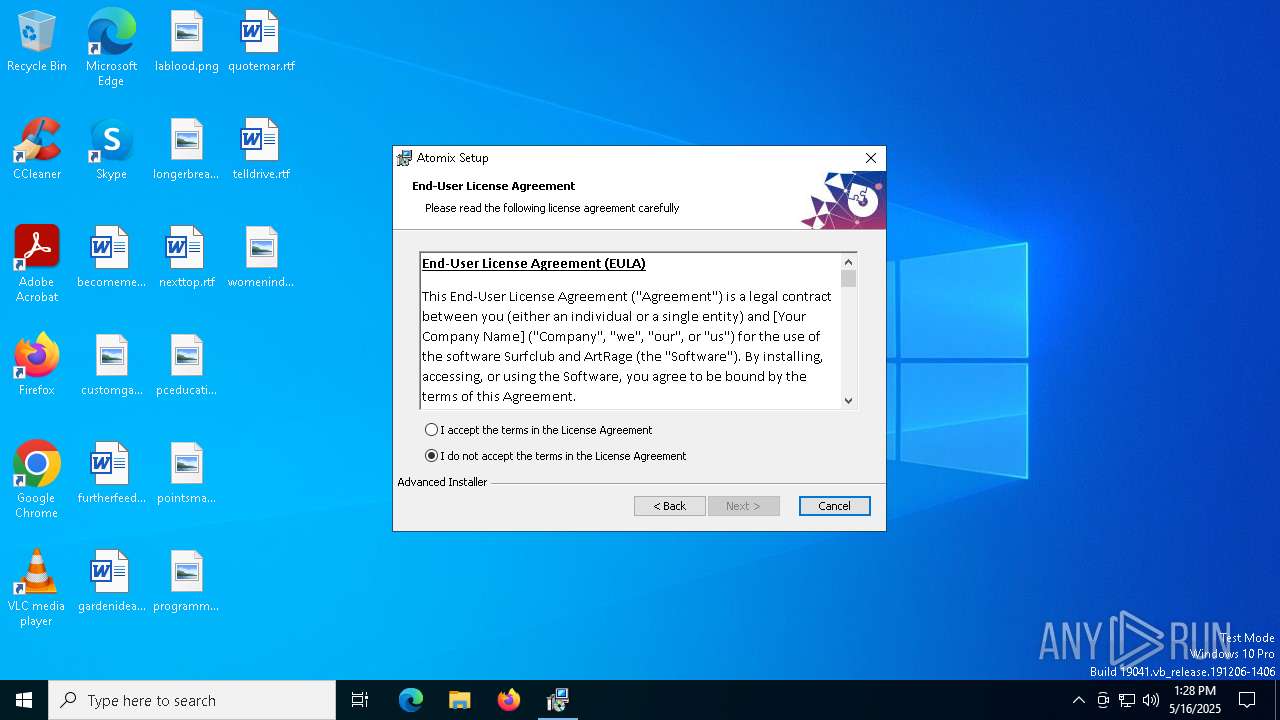
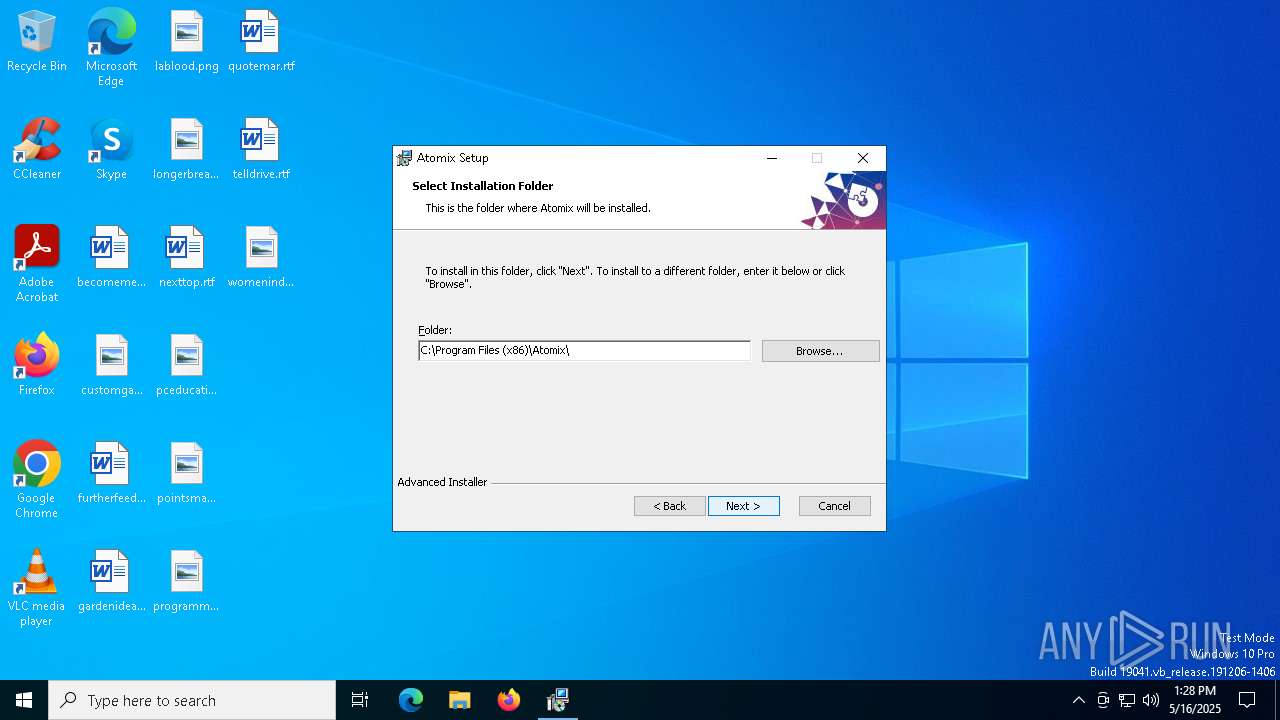
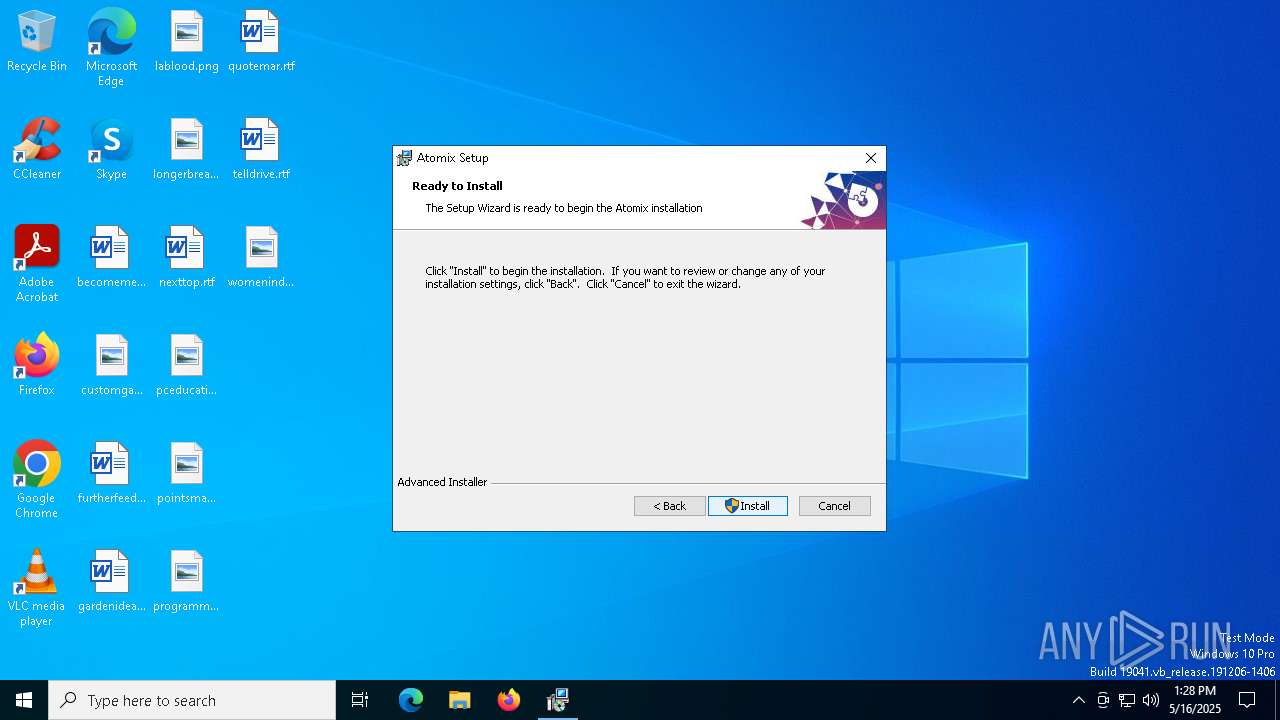
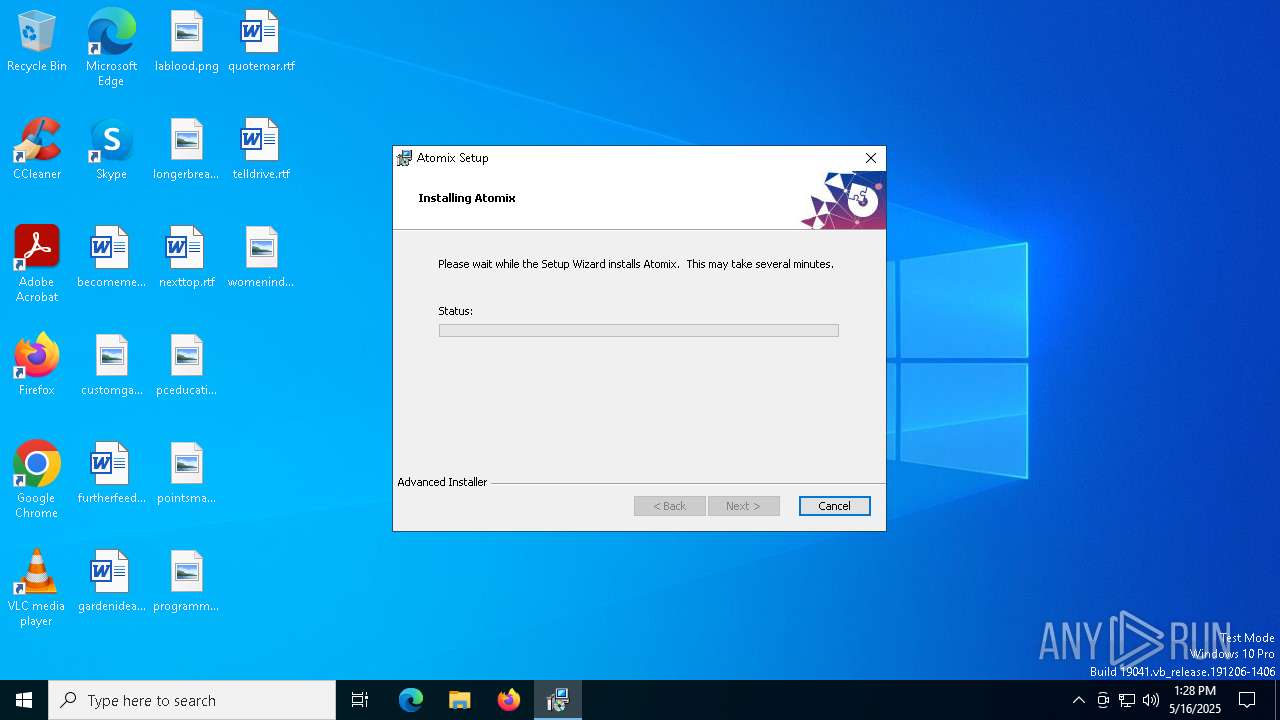
| File name: | 14d9d56bc4c17a971a9d69b41a4663ab7eb2ca5b52d860f9613823101f072c31 |
| Full analysis: | https://app.any.run/tasks/f7992366-a1f9-49dc-9619-2c2a464e99dd |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 13:28:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
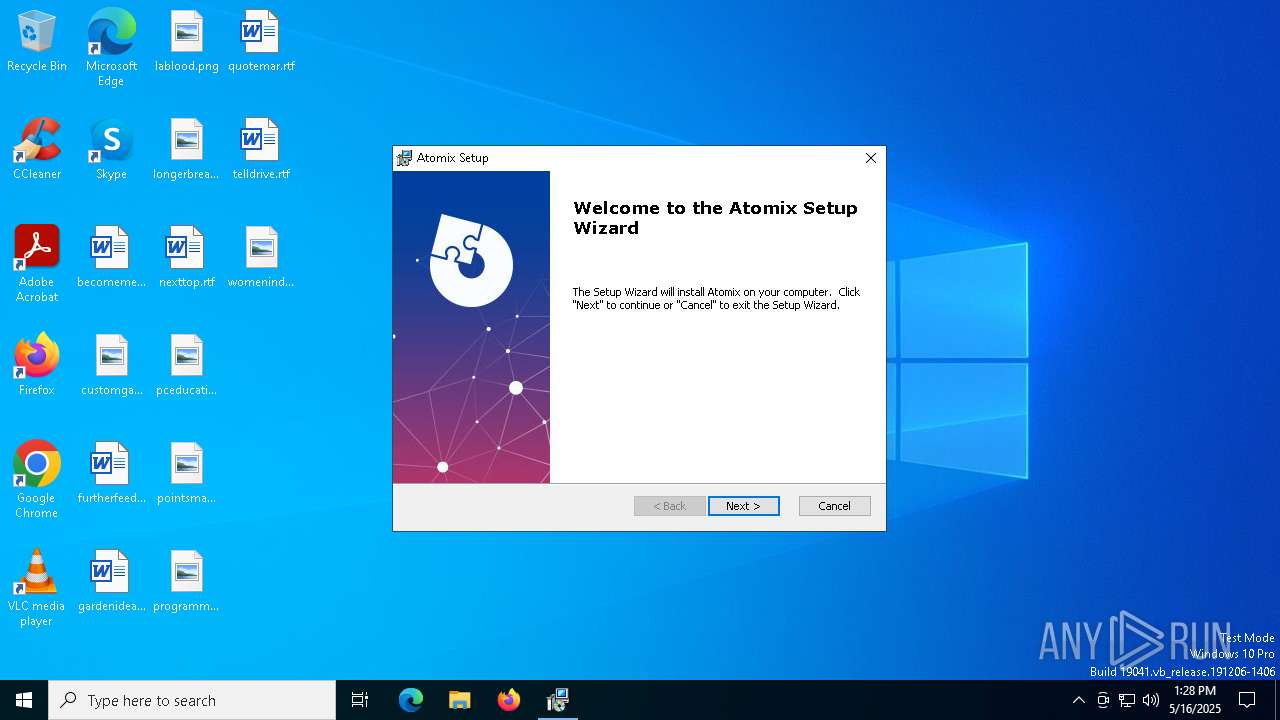
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Security: 0, Code page: 1252, Revision Number: {9A706C44-BD0E-4E97-AE6A-89AC19189097}, Number of Words: 2, Subject: Atomix, Author: Atomix, Name of Creating Application: Atomix, Template: ;1033, Comments: This installer database contains the logic and data required to install Atomix., Title: Installation Database, Keywords: Installer, MSI, Database, Create Time/Date: Wed Feb 19 13:22:37 2025, Last Saved Time/Date: Wed Feb 19 13:22:37 2025, Last Printed: Wed Feb 19 13:22:37 2025, Number of Pages: 450 |
| MD5: | 40BA7AFD12CBB907C004CD8629120846 |
| SHA1: | 63D403ABACA8A375055CFB2F314A003459A15BDF |
| SHA256: | 14D9D56BC4C17A971A9D69B41A4663AB7EB2CA5B52D860F9613823101F072C31 |
| SSDEEP: | 98304:t9I7oox4Cb+BgRGS/h6Q8RzVcp5ECoaF5jiGfXGACYHrvpXfSzbvug8Zla3Fz/xH:4n5w/Wtg39RBVvd9cB |
MALICIOUS
GENERIC has been found (auto)
- msiexec.exe (PID: 1164)
SUSPICIOUS
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6516)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 1164)
Executes as Windows Service
- VSSVC.exe (PID: 2420)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1164)
An automatically generated document
- msiexec.exe (PID: 1164)
Creates files or folders in the user directory
- msiexec.exe (PID: 1164)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6516)
- msiexec.exe (PID: 1164)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6516)
The sample compiled with english language support
- msiexec.exe (PID: 6516)
- msiexec.exe (PID: 1164)
Reads the software policy settings
- msiexec.exe (PID: 6516)
- msiexec.exe (PID: 1164)
Reads the computer name
- msiexec.exe (PID: 6516)
- msiexec.exe (PID: 1056)
Create files in a temporary directory
- msiexec.exe (PID: 6516)
Reads Environment values
- msiexec.exe (PID: 6516)
Checks supported languages
- msiexec.exe (PID: 1056)
- msiexec.exe (PID: 6516)
Checks proxy server information
- msiexec.exe (PID: 1164)
Manages system restore points
- SrTasks.exe (PID: 456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {9A706C44-BD0E-4E97-AE6A-89AC19189097} |
| Words: | 2 |
| Subject: | Atomix |
| Author: | Atomix |
| LastModifiedBy: | - |
| Software: | Atomix |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Atomix. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2025:02:19 13:22:37 |
| ModifyDate: | 2025:02:19 13:22:37 |
| LastPrinted: | 2025:02:19 13:22:37 |
| Pages: | 450 |
Total processes
132
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\14d9d56bc4c17a971a9d69b41a4663ab7eb2ca5b52d860f9613823101f072c31.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3024 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6516 | C:\Windows\syswow64\MsiExec.exe -Embedding 65875CA333CC7E1C205DDCF9A47B161F C | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 331
Read events
11 167
Write events
155
Delete events
9
Modification events
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000BC58D07466C6DB012004000030050000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000BC58D07466C6DB012004000030050000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000004DB1107566C6DB012004000030050000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000004DB1107566C6DB012004000030050000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000ADDC177566C6DB012004000030050000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000C715137566C6DB012004000030050000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000015EA877566C6DB0120040000B0190000E8030000010000000000000000000000B4C8041978A119458254AD2B90755C5200000000000000000000000000000000 | |||
| (PID) Process: | (2420) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000D1BC9F7566C6DB017409000048040000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (1056) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 48000000000000003E87857566C6DB012004000030050000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
9
Suspicious files
6
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1056 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1056 | msiexec.exe | C:\Windows\Installer\11978a.msi | — | |
MD5:— | SHA256:— | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FE17BEC2A573BC9AE36869D0274FFA19_6DA81F04C5F9EAD2CD0268808FCE61E1 | binary | |
MD5:7E5E9912DE7A985FF6257B5E3005DE2C | SHA256:EC0BDEA0FCC54BE0A302CAC5A2513186CCD5A9E1BD9DE7C8DD81CE1773141571 | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\248DDD9FCF61002E219645695E3FFC98_0FE2052DB4D07F373F2A573D5B9CE634 | binary | |
MD5:1050CB30CCBAE80D0317D8AF483F84B8 | SHA256:D4220F5D9441A778489E6C6465ACC521795EAA3AC2790AE19F9BA2807E1DFAEF | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSICA76.tmp | executable | |
MD5:0606E1A2FE0D72593405CAFEB945C740 | SHA256:E19A895AD4025EFF45AB03AA31A0916A6BA1E4F06DF5D6385B8C40924DC10890 | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FE17BEC2A573BC9AE36869D0274FFA19_6DA81F04C5F9EAD2CD0268808FCE61E1 | binary | |
MD5:5E32B38EF0CF3277B0988BBC3ADDEFC6 | SHA256:426A62DDD7CBFB37769E69311DD8A59C74A4FF0C89F09E8DDD919260D16CB294 | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSICFF8.tmp | executable | |
MD5:0606E1A2FE0D72593405CAFEB945C740 | SHA256:E19A895AD4025EFF45AB03AA31A0916A6BA1E4F06DF5D6385B8C40924DC10890 | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSICE31.tmp | executable | |
MD5:0606E1A2FE0D72593405CAFEB945C740 | SHA256:E19A895AD4025EFF45AB03AA31A0916A6BA1E4F06DF5D6385B8C40924DC10890 | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSID018.tmp | executable | |
MD5:0606E1A2FE0D72593405CAFEB945C740 | SHA256:E19A895AD4025EFF45AB03AA31A0916A6BA1E4F06DF5D6385B8C40924DC10890 | |||
| 1164 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSICFB9.tmp | executable | |
MD5:0606E1A2FE0D72593405CAFEB945C740 | SHA256:E19A895AD4025EFF45AB03AA31A0916A6BA1E4F06DF5D6385B8C40924DC10890 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
28
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.148:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1164 | msiexec.exe | GET | 200 | 18.173.205.113:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEEJLalPOx2YUHCpjsaUcQQQ%3D | unknown | — | — | whitelisted |
1164 | msiexec.exe | GET | 200 | 18.173.205.113:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSoEwb5tith0jIBy9frSyNGB1lsAAQUNr1J%2FzEs669qQP6ZwBbtuvxI3V8CEDQ8fFAr3OBsnzxlUcnQpFE%3D | unknown | — | — | whitelisted |
1672 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1672 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.148:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1164 | msiexec.exe | 18.173.205.113:80 | ocsps.ssl.com | — | US | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsps.ssl.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |