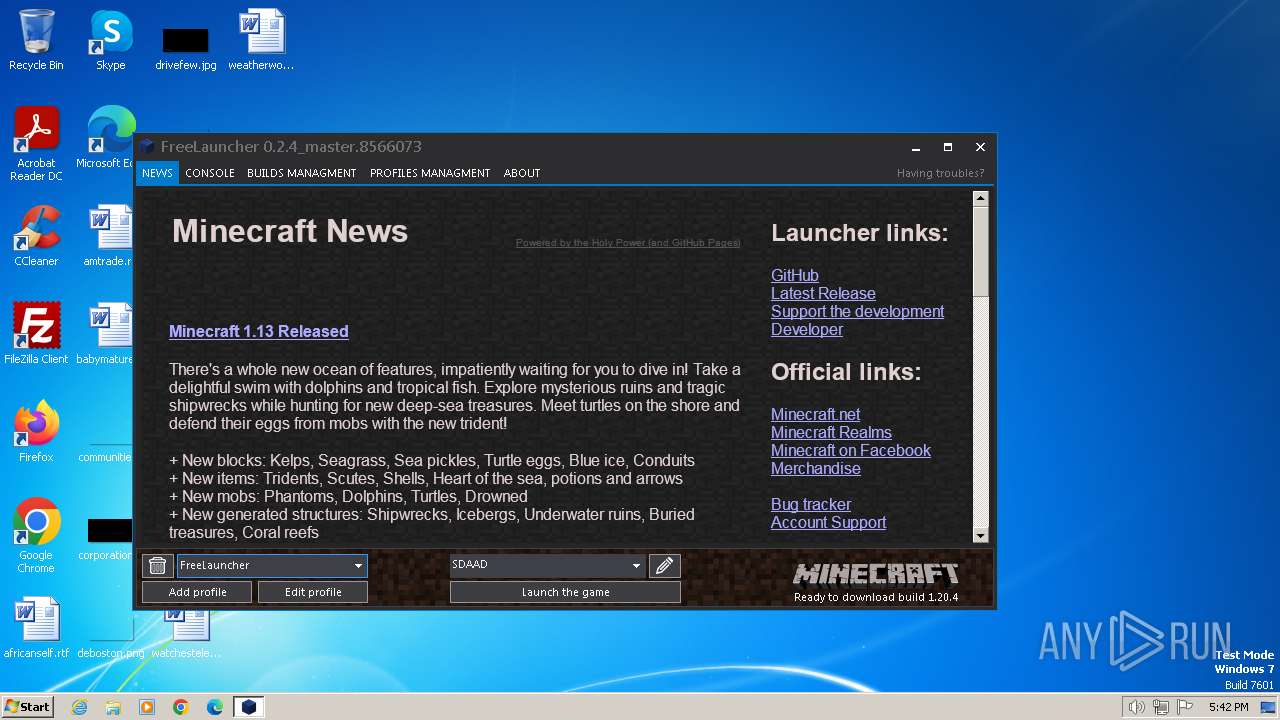
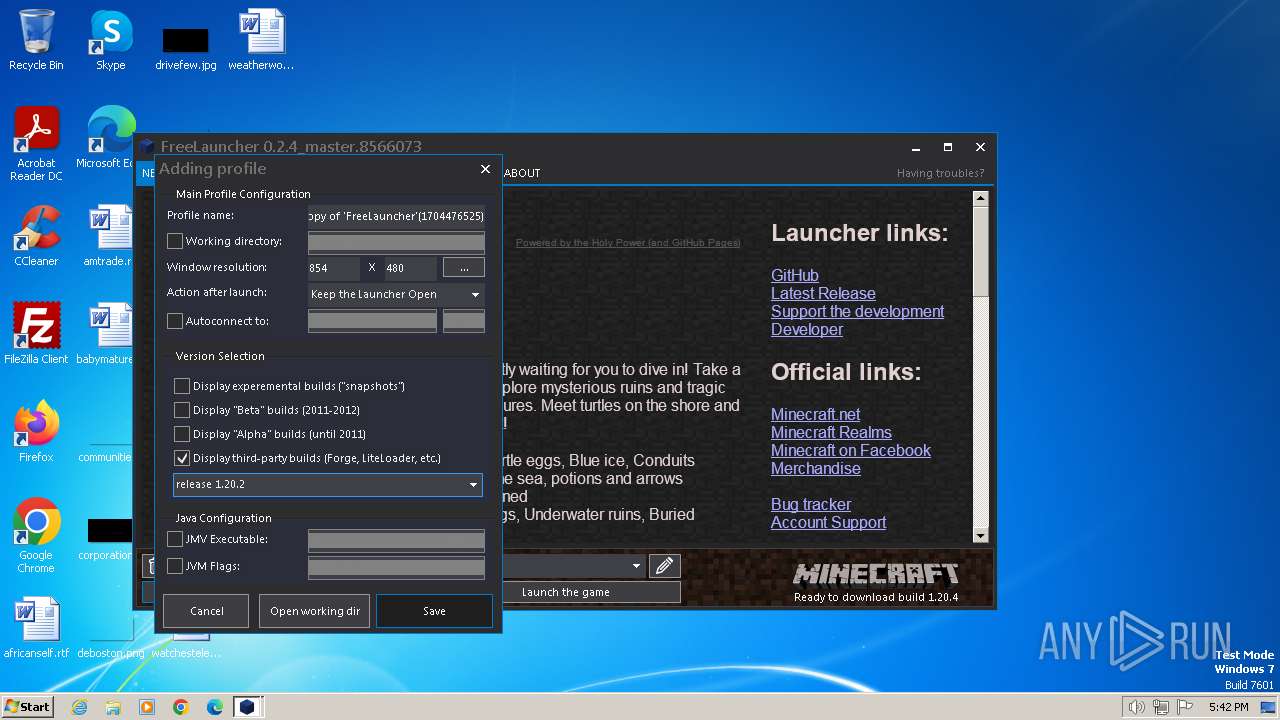
| File name: | FreeLauncher.exe |
| Full analysis: | https://app.any.run/tasks/960952d8-3c9d-4c6b-ad8c-7fb1f0382e4a |
| Verdict: | Malicious activity |
| Analysis date: | January 05, 2024, 17:41:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | C9A805B68752C2D20179BB055AAB492F |
| SHA1: | 8A7BEEE2BEAEB22049CFDE60B787A3FD4347BF0C |
| SHA256: | 14D51F64349F46AFB39030ECE25A32690AD82F3DA9AF198E18122CAB5AF807FE |
| SSDEEP: | 98304:M/4f1xQGBQU/y/qBQ2fsxwi4MqFnj6qVN+rZtBDzIO/c0Jz9GOGznbIkXVC52P0j:MAKcez/H5Cr |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- FreeLauncher.exe (PID: 2040)
Checks for Java to be installed
- FreeLauncher.exe (PID: 2040)
Reads the Internet Settings
- FreeLauncher.exe (PID: 2040)
Reads settings of System Certificates
- FreeLauncher.exe (PID: 2040)
Reads Internet Explorer settings
- FreeLauncher.exe (PID: 2040)
INFO
Drops the executable file immediately after the start
- FreeLauncher.exe (PID: 2040)
Reads the computer name
- FreeLauncher.exe (PID: 2040)
- wmpnscfg.exe (PID: 1784)
Checks supported languages
- FreeLauncher.exe (PID: 2040)
- wmpnscfg.exe (PID: 1784)
Creates files or folders in the user directory
- FreeLauncher.exe (PID: 2040)
Reads Environment values
- FreeLauncher.exe (PID: 2040)
Reads the machine GUID from the registry
- FreeLauncher.exe (PID: 2040)
Checks proxy server information
- FreeLauncher.exe (PID: 2040)
Manual execution by a user
- wmpnscfg.exe (PID: 1784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (56.7) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21.3) |
| .scr | | | Windows screen saver (10.1) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:08:22 18:00:51+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 4914176 |
| InitializedDataSize: | 38400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x4b1b0e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.2.4.1799 |
| ProductVersionNumber: | 0.2.4.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Open Source Minecraft launcher |
| CompanyName: | Igor Popov |
| FileDescription: | FreeLauncher |
| FileVersion: | 0.2.4.1799 |
| InternalName: | FreeLauncher.exe |
| LegalCopyright: | Copyright Igor Popov© 2015-2018 |
| LegalTrademarks: | - |
| OriginalFileName: | FreeLauncher.exe |
| ProductName: | FreeLauncher |
| ProductVersion: | 0.2.4_master.8566073 |
| AssemblyVersion: | 0.2.4.1799 |
Total processes
36
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1784 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\FreeLauncher.exe" | C:\Users\admin\AppData\Local\Temp\FreeLauncher.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Popov Integrity Level: MEDIUM Description: FreeLauncher Exit code: 0 Version: 0.2.4.1799 Modules
| |||||||||||||||
Total events
3 847
Read events
3 811
Write events
36
Delete events
0
Modification events
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2040) FreeLauncher.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
Executable files
38
Suspicious files
31
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\FreeLauncher[1].htm | html | |
MD5:4F8E702CC244EC5D4DE32740C0ECBD97 | SHA256:9E17CB15DD75BBBD5DBB984EDA674863C3B10AB72613CF8A39A00C3E11A8492A | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Roaming\.minecraft\versions\1.20.2\1.20.2.jar | compressed | |
MD5:3648233841690C8C4F9F8A0CF63A0DCD | SHA256:FA1A19BE56A506426308ABBC1CAD85F299A7FC6DAE4335559351BA0246713FDA | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\guava\guava\32.1.2-jre\guava-32.1.2-jre.jar | java | |
MD5:5FE031B3B35ED56182478811A931D617 | SHA256:BC65DEA7CFD9E4DACF8419D8AF0E741655857D27885BB35D943D7187FC3A8FCE | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\ibm\icu\icu4j\73.2\icu4j-73.2.jar | java | |
MD5:23A23DE561DD4F83E13D46E7273A35DE | SHA256:29280822F4B0796ACEF1F79B90B1D0C1EDD86C10E876A848E04B8A6298A16BF9 | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\blocklist\1.0.10\blocklist-1.0.10.jar | compressed | |
MD5:FC1420E3182DD32B4DF9933F810EBEBB | SHA256:830BFD639C8DB49236BBD8E45D3A2B8C96C56FF654A10118654958A6235D4C44 | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\code\gson\gson\2.10.1\gson-2.10.1.jar | compressed | |
MD5:DF6097815738CB31FC56391553210843 | SHA256:4241C14A7727C34FEEA6507EC801318A3D4A90F070E4525681079FB94EE4C593 | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\mojang\brigadier\1.1.8\brigadier-1.1.8.jar | compressed | |
MD5:34F54DAE241296B633655353219F8E06 | SHA256:CF65AFA612FFFBE4DC976115DAC0312F48B9C84B3DDAF58BEC8018A9454440D7 | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\bg_main[1].png | image | |
MD5:F1596E0654794B9A0DD94FA78DDD7D17 | SHA256:181A1E60BA5EE57497C0F97F5C6BCD49751DC6C4EC7355332C74056A02946D0C | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Roaming\.minecraft\libraries\com\google\guava\failureaccess\1.0.1\failureaccess-1.0.1.jar | java | |
MD5:091883993EF5BFA91DA01DCC8FC52236 | SHA256:A171EE4C734DD2DA837E4B16BE9DF4661AFAB72A41ADAF31EB84DFDAF936CA26 | |||
| 2040 | FreeLauncher.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\stylesheet[1].css | text | |
MD5:CC2B6EDA03A6EC209C8040BC74507A92 | SHA256:0C075EF6D8BD3985F8D49C9FCFEEC241BB1A65F636D8CD786EA49F8F6F925AD2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
68
TCP/UDP connections
15
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2040 | FreeLauncher.exe | GET | 200 | 185.199.108.153:80 | http://dedepete.github.io/FreeLauncher/ | unknown | html | 2.71 Kb | unknown |
2040 | FreeLauncher.exe | GET | 200 | 185.199.108.153:80 | http://dedepete.github.io/FreeLauncher/stylesheet.css | unknown | text | 660 b | unknown |
2040 | FreeLauncher.exe | GET | 200 | 185.199.108.153:80 | http://dedepete.github.io/FreeLauncher/bg_main.png | unknown | image | 434 b | unknown |
2040 | FreeLauncher.exe | GET | 400 | 13.107.246.45:80 | http://resources.download.minecraft.net/5f/5ff04807c356f1beed0b86ccf659b44b9983e3fa | unknown | xml | 289 b | unknown |
2040 | FreeLauncher.exe | GET | 400 | 13.107.246.45:80 | http://resources.download.minecraft.net/b6/b62ca8ec10d07e6bf5ac8dae0c8c1d2e6a1e3356 | unknown | xml | 289 b | unknown |
2040 | FreeLauncher.exe | GET | 400 | 13.107.246.45:80 | http://resources.download.minecraft.net/af/af96f55a90eaf11b327f1b5f8834a051027dc506 | unknown | xml | 289 b | unknown |
2040 | FreeLauncher.exe | GET | 400 | 13.107.246.45:80 | http://resources.download.minecraft.net/f0/f00657542252858a721e715a2e888a9226404e35 | unknown | xml | 289 b | unknown |
2040 | FreeLauncher.exe | GET | 400 | 13.107.246.45:80 | http://resources.download.minecraft.net/95/958d57021d8009de55d6e9e19957a72545e3c30c | unknown | xml | 289 b | unknown |
2040 | FreeLauncher.exe | GET | 400 | 13.107.246.45:80 | http://resources.download.minecraft.net/94/949afe72d4d3d785dab52d8baaefeb0e38b3c067 | unknown | xml | 289 b | unknown |
2040 | FreeLauncher.exe | GET | 400 | 13.107.246.45:80 | http://resources.download.minecraft.net/df/df274fe57c49ef1af6d218703d805db76a5c8af9 | unknown | xml | 289 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2040 | FreeLauncher.exe | 17.253.57.195:443 | captive.apple.com | APPLE-AUSTIN | DE | unknown |
2040 | FreeLauncher.exe | 140.82.121.5:443 | api.github.com | GITHUB | US | unknown |
2040 | FreeLauncher.exe | 185.199.108.153:80 | dedepete.github.io | FASTLY | US | shared |
2040 | FreeLauncher.exe | 13.107.213.63:443 | launchermeta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2040 | FreeLauncher.exe | 13.107.246.63:443 | launchermeta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2040 | FreeLauncher.exe | 13.107.246.45:80 | resources.download.minecraft.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
captive.apple.com |
| whitelisted |
api.github.com |
| whitelisted |
dedepete.github.io |
| unknown |
launchermeta.mojang.com |
| whitelisted |
piston-meta.mojang.com |
| unknown |
piston-data.mojang.com |
| unknown |
libraries.minecraft.net |
| shared |
resources.download.minecraft.net |
| shared |