| File name: | lua.exe |
| Full analysis: | https://app.any.run/tasks/ffda043a-607c-4e9f-9057-bb42ff252b90 |
| Verdict: | Malicious activity |
| Analysis date: | March 29, 2025, 20:19:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 9B511D21129DD10EC89077C4673FD078 |
| SHA1: | 0BE3D945799AD2582136C00EBB03100ACCB7C19B |
| SHA256: | 14CF8B9B5A40DA306472AF47095DDAE9741D543C9EA1C33CCAD089EA4E0F65EC |
| SSDEEP: | 49152:Xg/q1q56N/+X1YQ/Lbv8quQ6+IIgg4KgVjiZHMwmG9x:Sq1q560Xh/LWQ6VIgg2V8 |
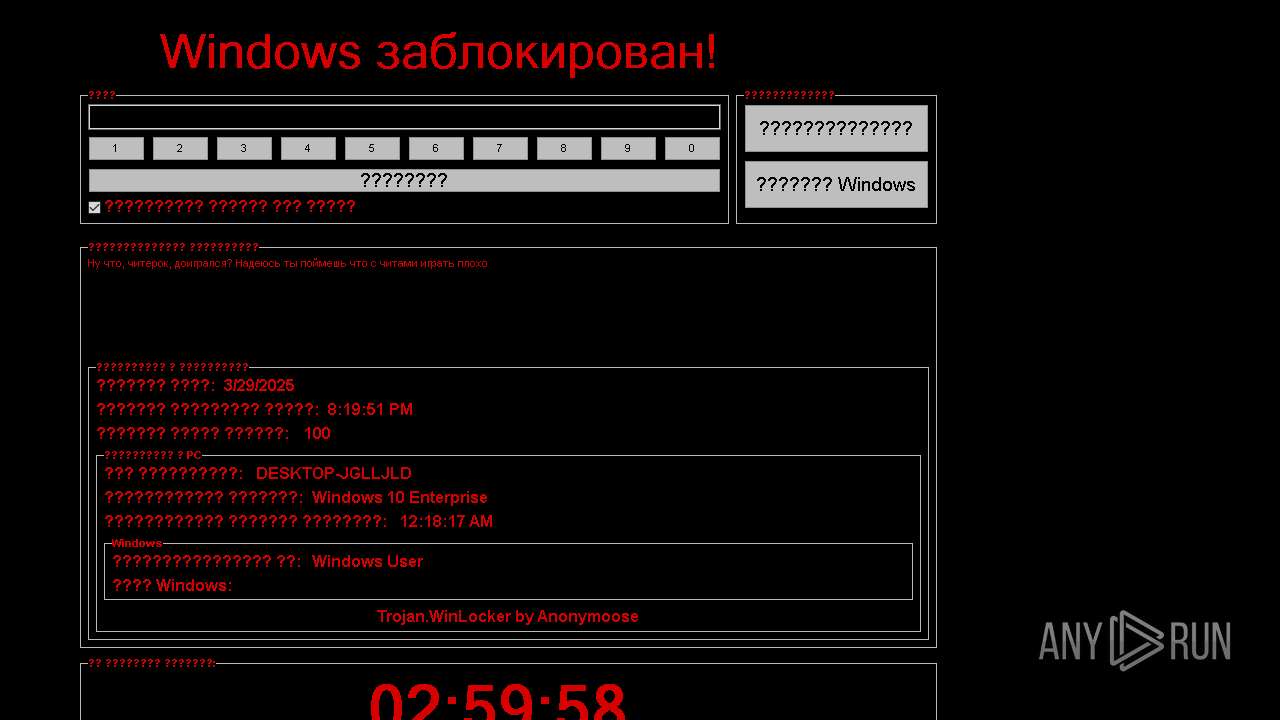
MALICIOUS
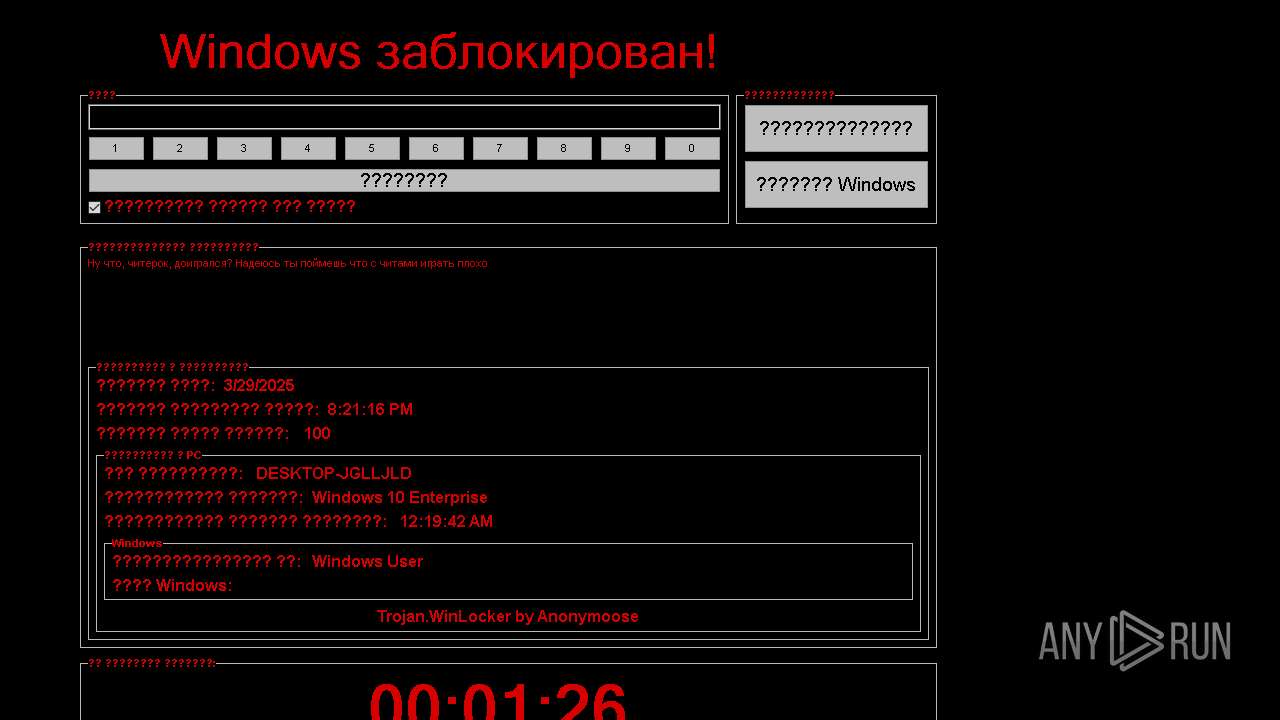
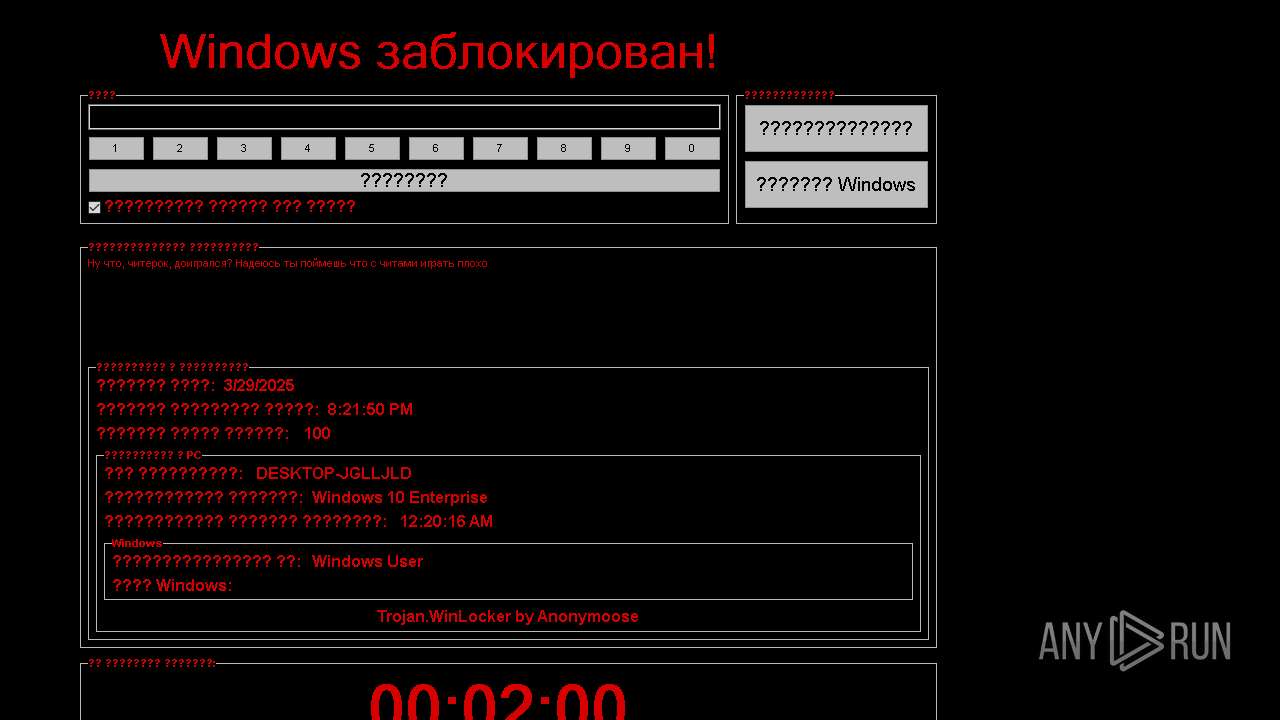
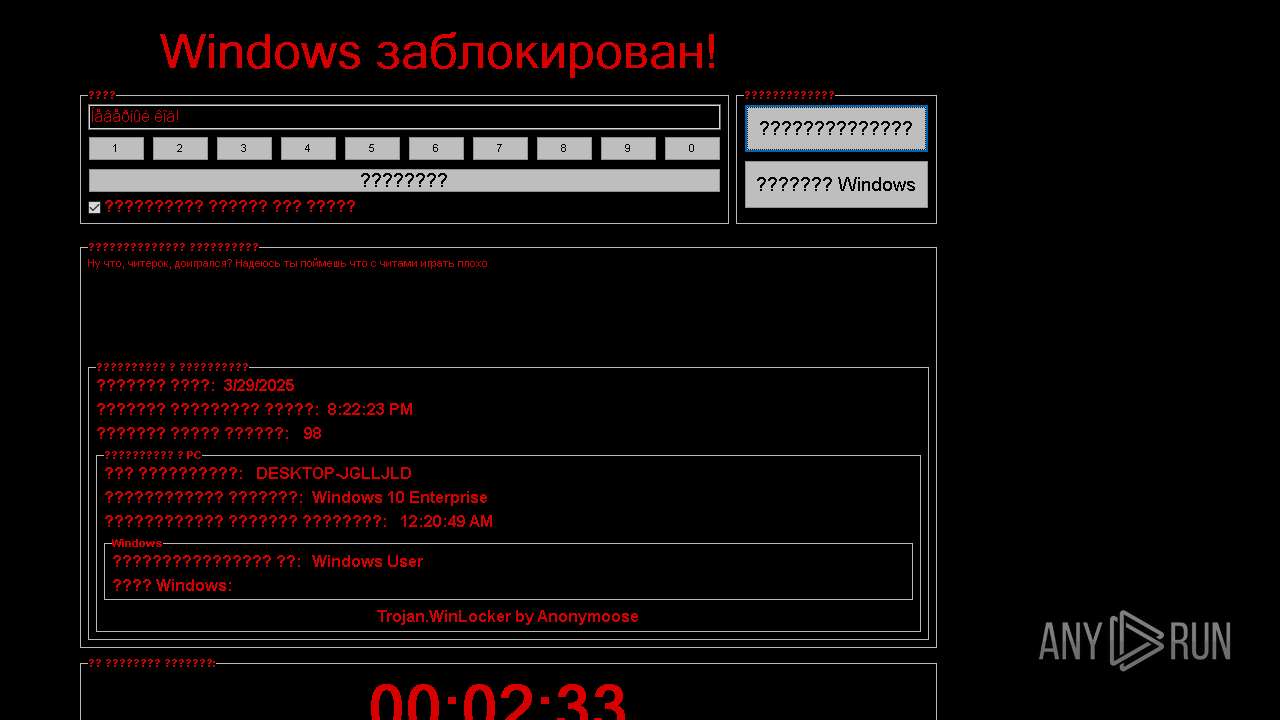
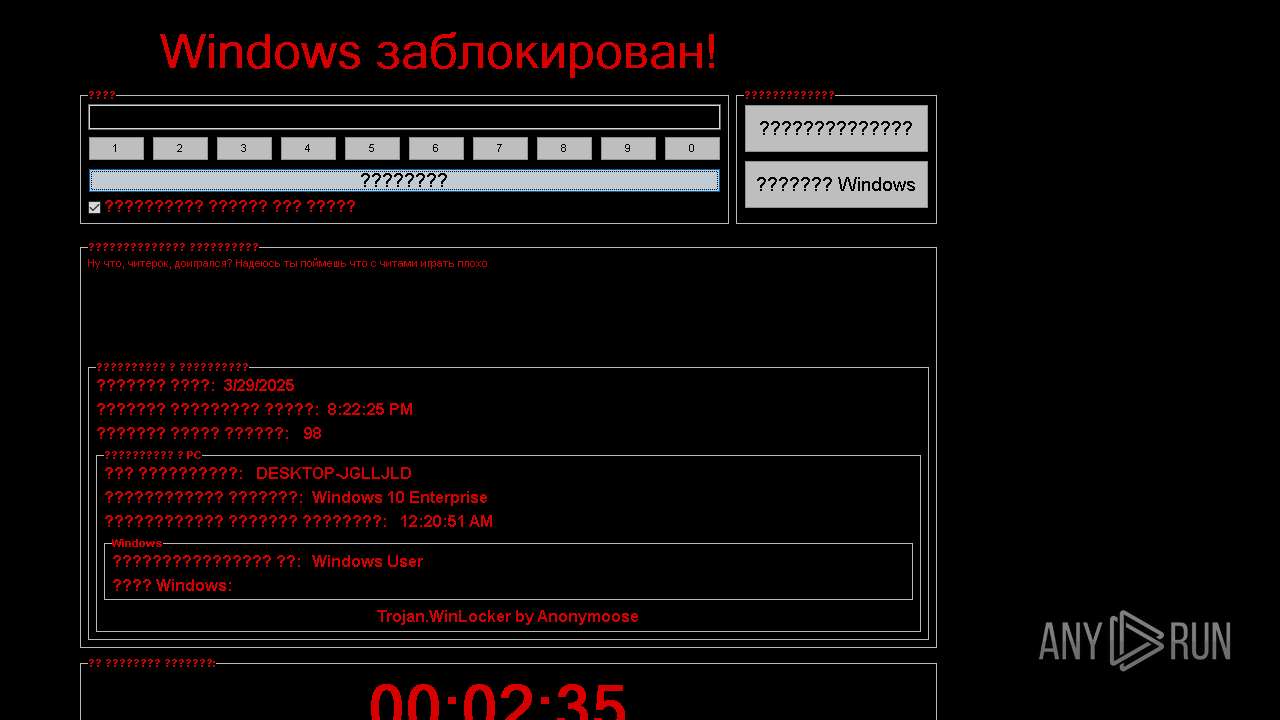
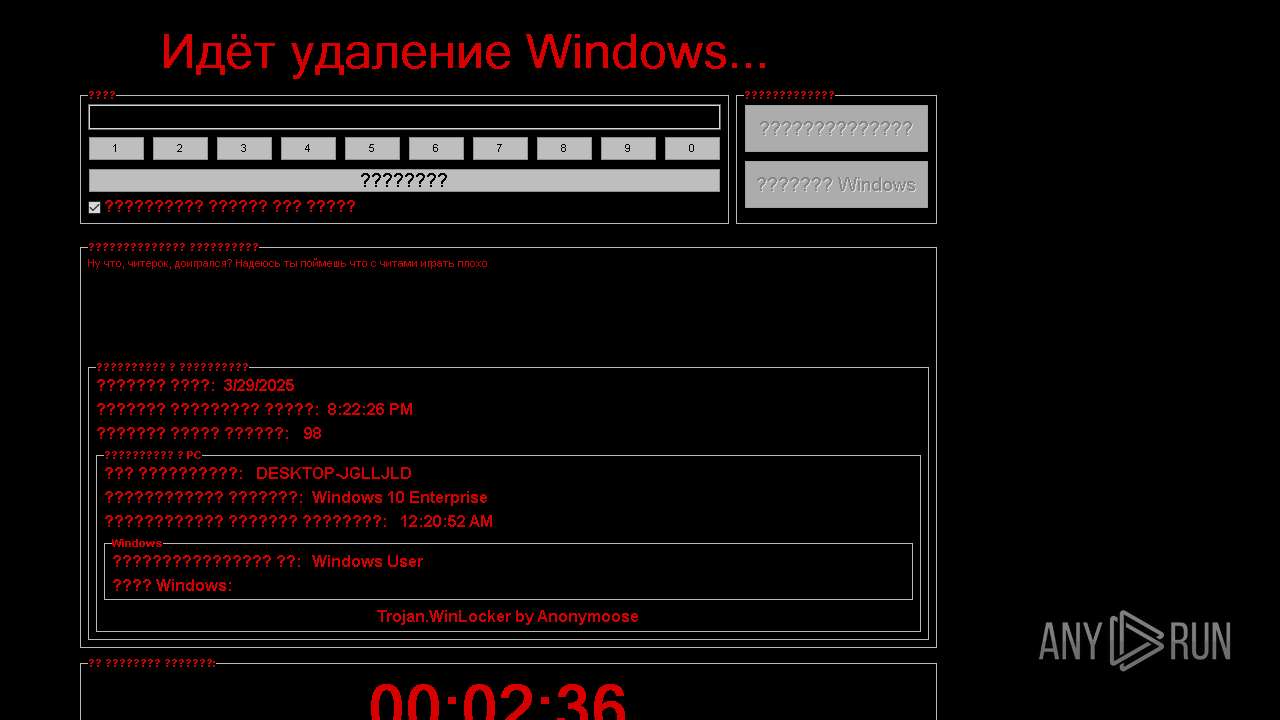
FRAGTOR mutex has been found
- lua.exe (PID: 7780)
Adds path to the Windows Defender exclusion list
- lua.exe (PID: 7780)
Disables Windows Defender
- lua.exe (PID: 7780)
Changes Windows Defender settings
- lua.exe (PID: 7780)
Changes the autorun value in the registry
- lua.exe (PID: 7780)
UAC/LUA settings modification
- lua.exe (PID: 7780)
Disables the Find the Start menu
- lua.exe (PID: 7780)
Changes image file execution options
- lua.exe (PID: 7780)
Disables the Run the Start menu
- lua.exe (PID: 7780)
Disables the Shutdown in the Start menu
- lua.exe (PID: 7780)
Disables the LogOff the Start menu
- lua.exe (PID: 7780)
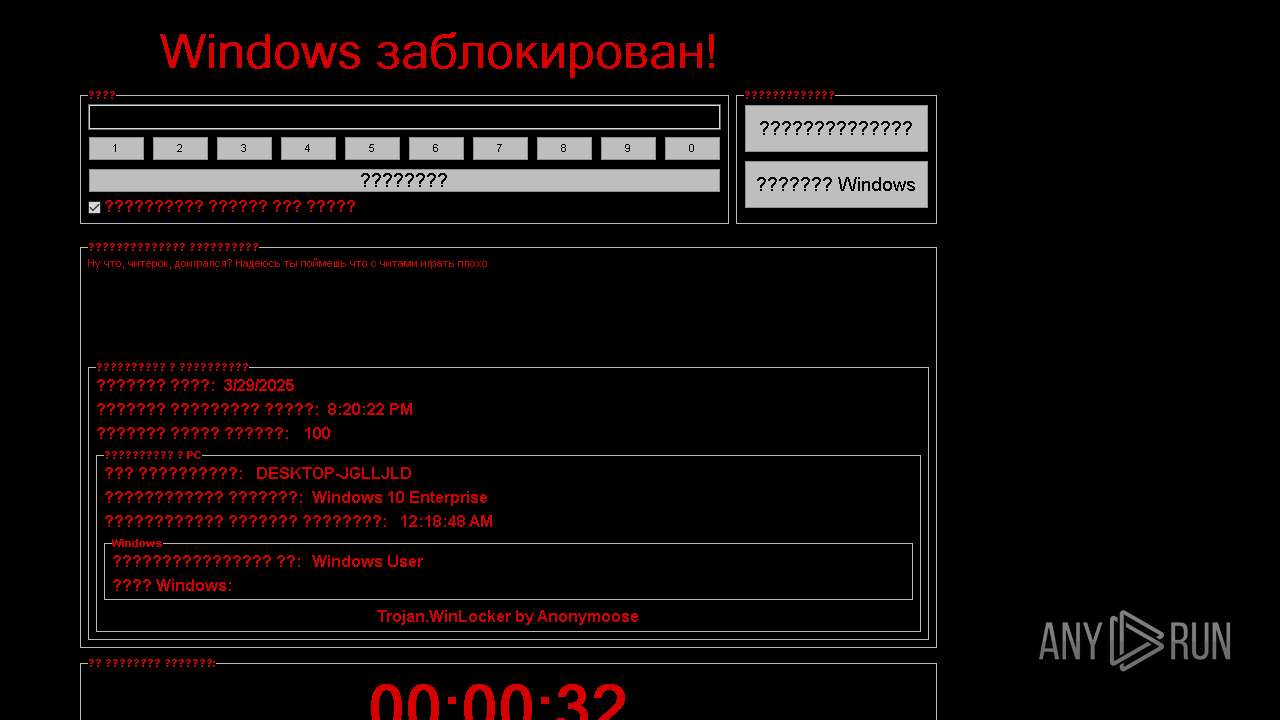
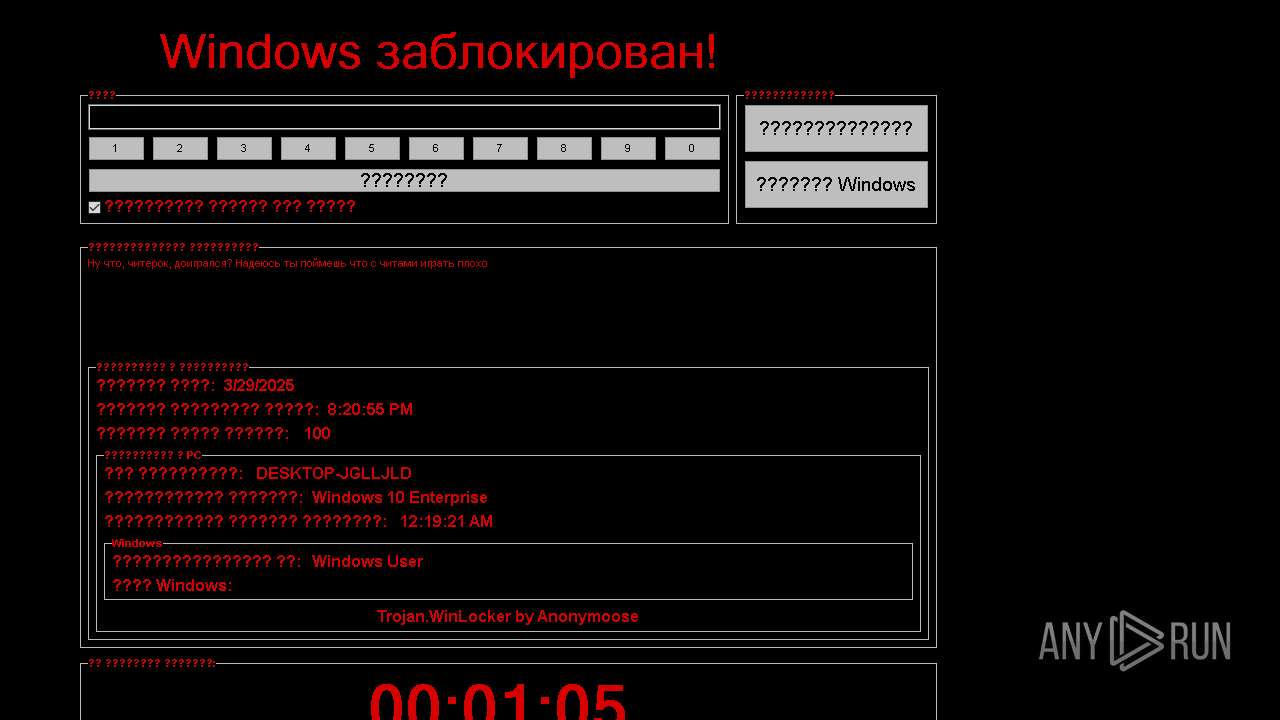
WINLOCKER has been detected (YARA)
- lua.exe (PID: 7780)
SUSPICIOUS
Starts POWERSHELL.EXE for commands execution
- lua.exe (PID: 7780)
Starts CMD.EXE for commands execution
- lua.exe (PID: 7780)
Script adds exclusion path to Windows Defender
- lua.exe (PID: 7780)
Reads security settings of Internet Explorer
- lua.exe (PID: 7780)
There is functionality for taking screenshot (YARA)
- lua.exe (PID: 7780)
Creates file in the systems drive root
- lua.exe (PID: 7780)
There is functionality for VM detection VMWare (YARA)
- lua.exe (PID: 7780)
There is functionality for VM detection VirtualBox (YARA)
- lua.exe (PID: 7780)
INFO
Checks supported languages
- lua.exe (PID: 7780)
Process checks computer location settings
- lua.exe (PID: 7780)
Reads the computer name
- lua.exe (PID: 7780)
Create files in a temporary directory
- lua.exe (PID: 7780)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7932)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7932)
Compiled with Borland Delphi (YARA)
- lua.exe (PID: 7780)
- slui.exe (PID: 7276)
Checks proxy server information
- slui.exe (PID: 7276)
Reads the software policy settings
- slui.exe (PID: 7276)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (94.6) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (2) |
| .scr | | | Windows screen saver (1.8) |
| .exe | | | Win32 Executable (generic) (0.6) |
| .exe | | | Win16/32 Executable Delphi generic (0.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1172992 |
| InitializedDataSize: | 184832 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x11f5b8 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
136
Monitored processes
8
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7276 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7388 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 2147945463 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7624 | "C:\Users\admin\AppData\Local\Temp\lua.exe" | C:\Users\admin\AppData\Local\Temp\lua.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 7780 | "C:\Users\admin\AppData\Local\Temp\lua.exe" | C:\Users\admin\AppData\Local\Temp\lua.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 7888 | "C:\Windows\System32\cmd.exe" /c schtasks /create /tn "GoogleUpdateTaskMachineUK" /sc MINUTE /mo 1 /tr "C:\Users\admin\AppData\Local\Temp\lua.exe" /rl HIGHEST /f | C:\Windows\System32\cmd.exe | — | lua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7896 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7932 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -Command "Add-MpPreference -ExclusionPath 'C:\Users\admin\AppData\Local\Temp\lua.exe'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | lua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7944 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 060
Read events
11 026
Write events
34
Delete events
0
Modification events
| (PID) Process: | (7780) lua.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\System |
| Operation: | write | Name: | DisableCMD |
Value: 2 | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 0 | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | Qwe |
Value: C:\Users\admin\AppData\Local\Temp\lua.exe | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\lua.exe | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\taskmgr.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\lua.exe | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\utilman.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\lua.exe | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\lua.exe | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\reg.exe |
| Operation: | write | Name: | Debugger |
Value: C:\Users\admin\AppData\Local\Temp\lua.exe | |||
| (PID) Process: | (7780) lua.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmd.exe |
| Operation: | write | Name: | Debugger |
Value: "cmd.exe","C:\Users\admin\AppData\Local\Temp\lua.exe" | |||
Executable files
0
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7780 | lua.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 7932 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cxcannq3.cv0.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7932 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_gouqthug.xos.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7780 | lua.exe | C:\Users\admin\AppData\Local\Temp\Time.ini | text | |
MD5:EB13B7EAF7F30D348E471F0907B31AAC | SHA256:94BA214735774FB4E68BE906C3E181D29C71DBBCD10540E70BA7021FCF5EA3AA | |||
| 7932 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:5F0ED4BBBA12272DCC437A7E47DD8C07 | SHA256:7610C9991B0BA6F5046CEB2D8C75D51AE3C0DB4C672F3658EB3F14B262383612 | |||
| 7780 | lua.exe | C:\Windows\appcompat\Programs\Amcache.hve.LOG1 | binary | |
MD5:BCE94E1C0D92EC8C88F5851E5B8B1F78 | SHA256:4139440928846EB0CF78C3CF416DE512E0116E6028306E37A241122F3A160CA7 | |||
| 7780 | lua.exe | C:\Users\admin\AppData\Local\Temp\Time2.ini | text | |
MD5:1281E7CD37295F4793D7C2A89768C0DC | SHA256:1FA21D9E19BF83DD68505165FEC38E46263B582FF8E3D582ADD57C756210B8FA | |||
| 7780 | lua.exe | C:\RestInPiss.dll | text | |
MD5:7BD75571D3A08F413BB0727D7ECBAF7A | SHA256:5EDC53221D1A70D8238CBF9A557F1C52B166A94A9364E24AB92525B9F4F81E43 | |||
| 7780 | lua.exe | C:\Windows\Logs\waasmedic\waasmedic.20250329_202147_728.etl | binary | |
MD5:B02E2ED5BAA2417AC8E5029F9E29B0E4 | SHA256:386E0E0A671243E94CBB3944A8221D06406770CE3082CF282211C938AD132C2D | |||
| 7780 | lua.exe | C:\Windows\Logs\waasmediccapsule\WaasRemediation.001.etl | binary | |
MD5:44CB3A81495A4F03B71F581D0F3F501E | SHA256:471440EC5FF7A658F48011DF3AF0F14C9B621B685EA4E00ED735E22AE458682B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
24
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7616 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7276 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |