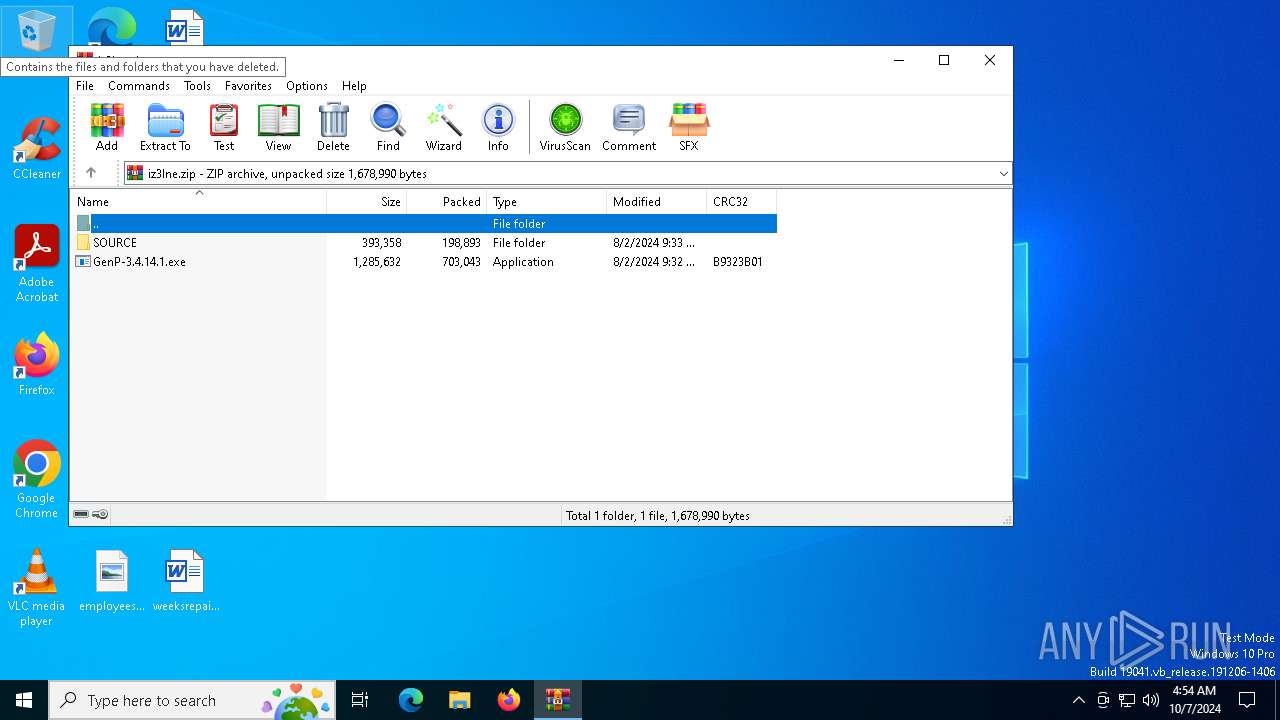
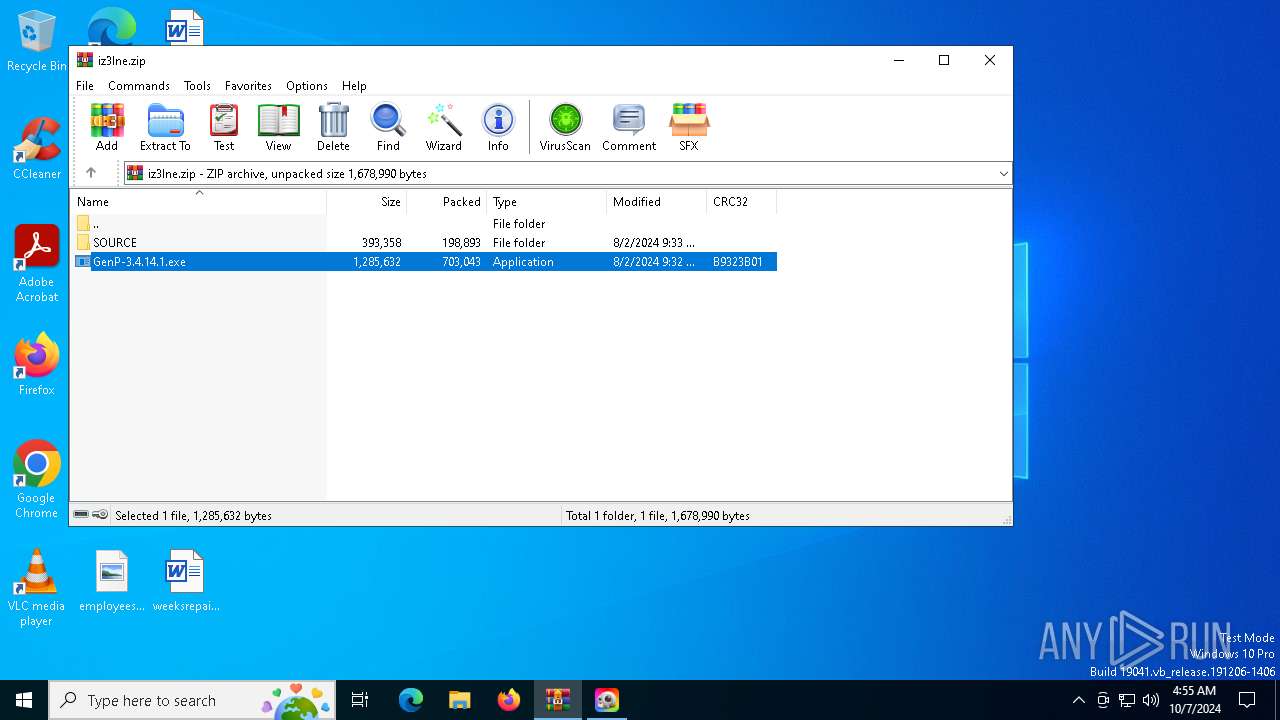
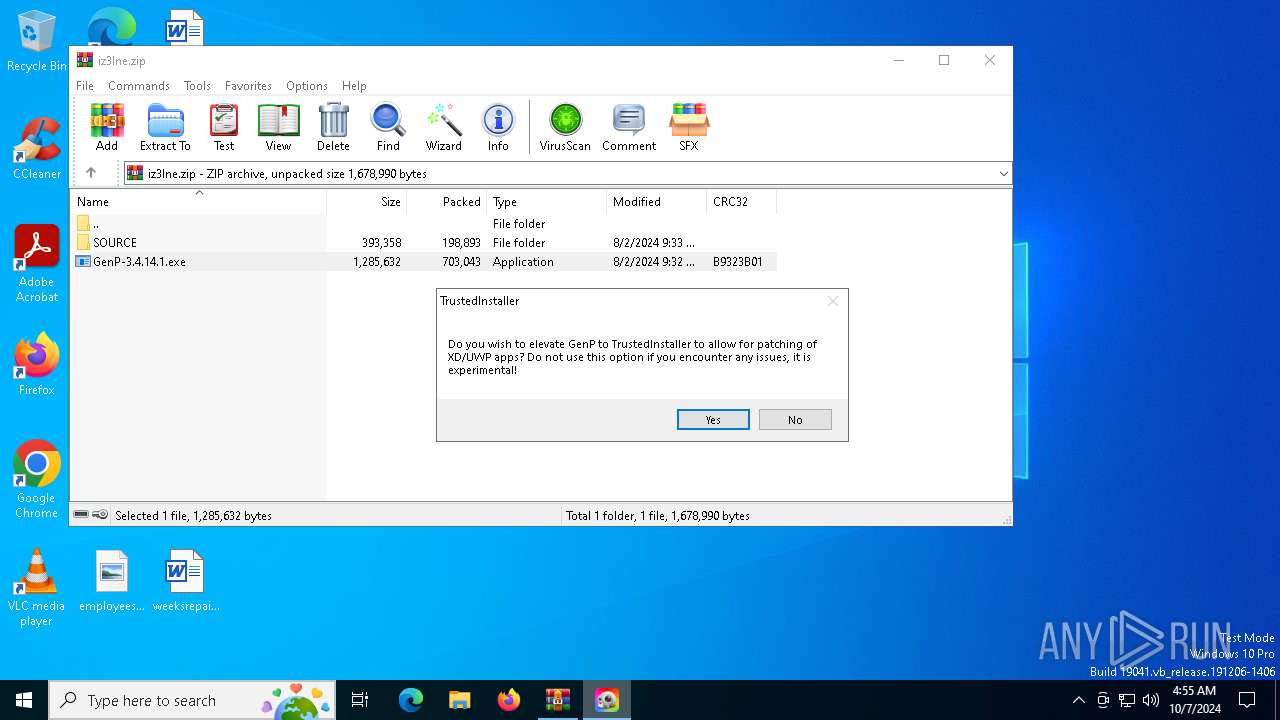
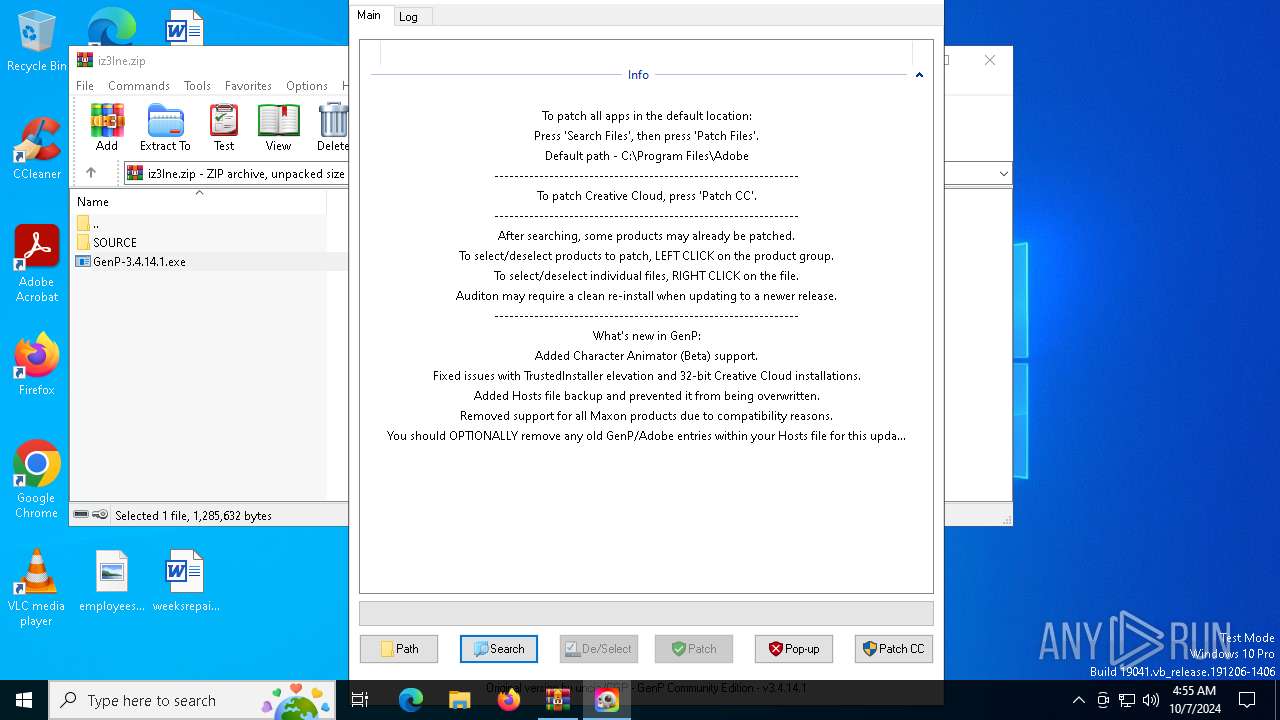
| File name: | iz3lne.zip |
| Full analysis: | https://app.any.run/tasks/deacba65-d35d-4b95-8eee-d5662204c325 |
| Verdict: | Malicious activity |
| Analysis date: | October 07, 2024, 04:54:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6B104BA9DEB749A6B6CE88B9C6997DAE |
| SHA1: | 19D9B52477606B78BDCE568235C0ACB9321C1BC4 |
| SHA256: | 14CE93AE01D50B9D2FF3C36C3EDD574A9F8BCEC56451F3A865FCC210C617A77B |
| SSDEEP: | 49152:vaAW1JvfJzxpH5gntvVxsO/vXYoFA1N4VrBBXYt621Vrmt7a7wWn7/YmO:vaAWnN2lnvXXFFA1N4VG6GVrmt7a7zBO |
MALICIOUS
No malicious indicators.SUSPICIOUS
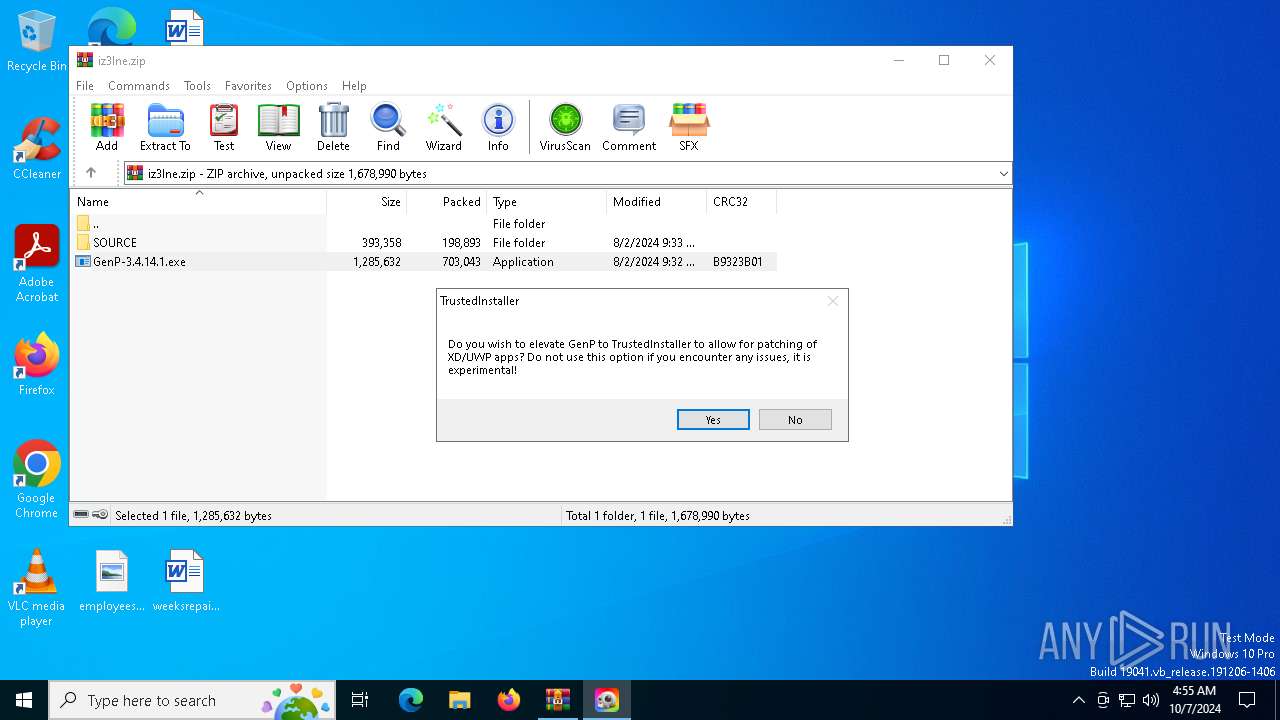
Application launched itself
- GenP-3.4.14.1.exe (PID: 5072)
- GenP-3.4.14.1.exe (PID: 4004)
- GenP-3.4.14.1.exe (PID: 2132)
- GenP-3.4.14.1.exe (PID: 3924)
- GenP-3.4.14.1.exe (PID: 1492)
- GenP-3.4.14.1.exe (PID: 796)
- GenP-3.4.14.1.exe (PID: 4840)
- GenP-3.4.14.1.exe (PID: 5388)
- GenP-3.4.14.1.exe (PID: 6352)
Executable content was dropped or overwritten
- GenP-3.4.14.1.exe (PID: 4840)
- GenP-3.4.14.1.exe (PID: 6948)
- GenP-3.4.14.1.exe (PID: 4196)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:08:02 14:32:54 |
| ZipCRC: | 0xb9323b01 |
| ZipCompressedSize: | 703043 |
| ZipUncompressedSize: | 1285632 |
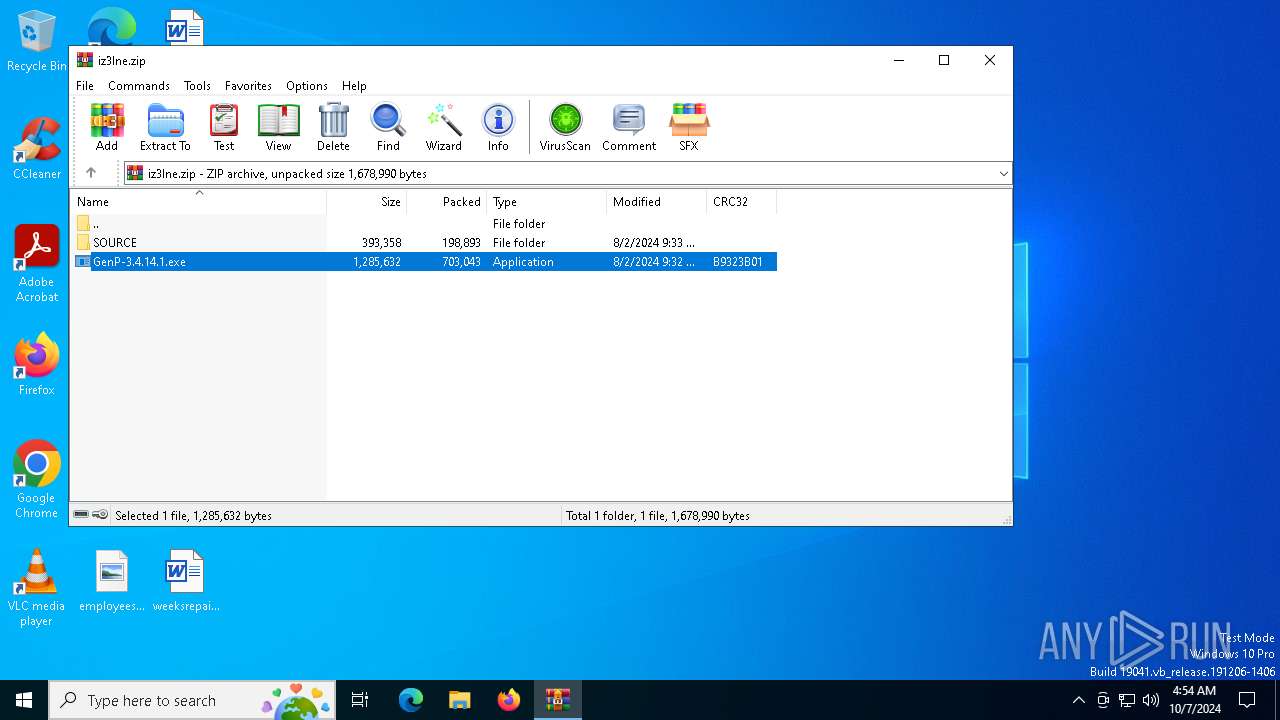
| ZipFileName: | GenP-3.4.14.1.exe |
Total processes
167
Monitored processes
24
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 796 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.21824\GenP-3.4.14.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.21824\GenP-3.4.14.1.exe | — | WinRAR.exe | |||||||||||
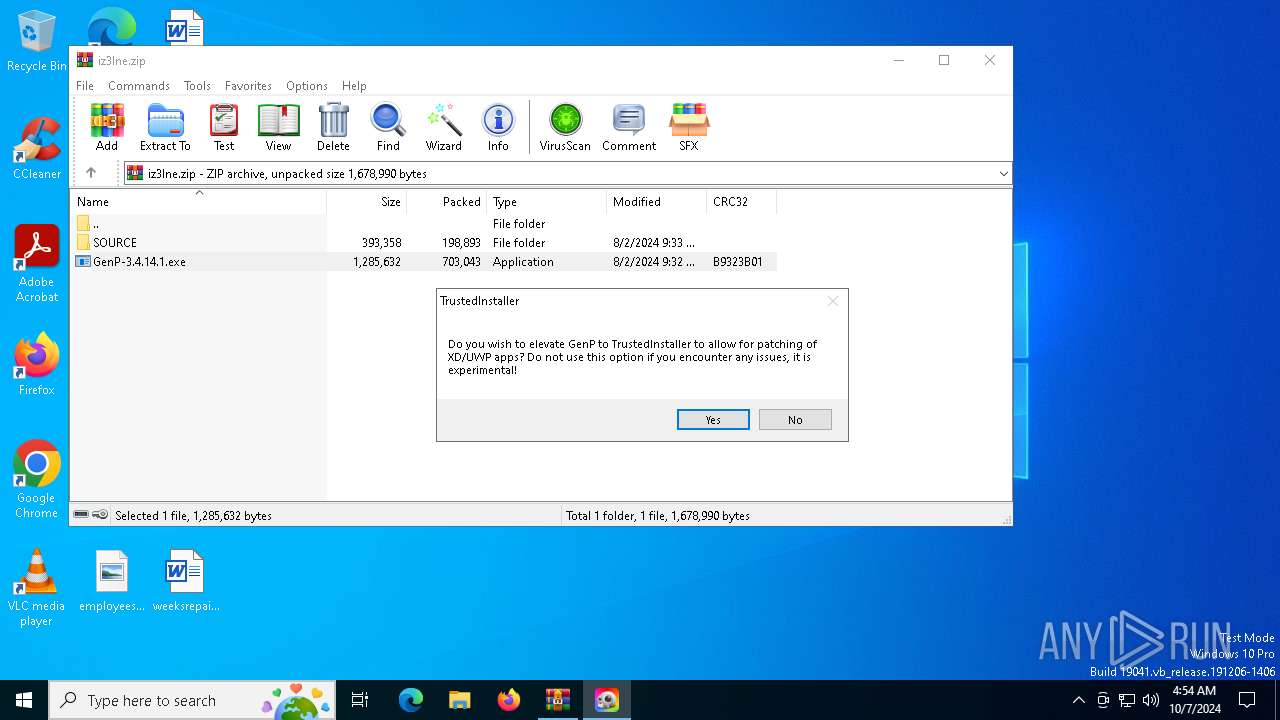
User: admin Company: GenP Integrity Level: MEDIUM Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 1108 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.22747\GenP-3.4.14.1.exe" ! | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.22747\GenP-3.4.14.1.exe | GenP-3.4.14.1.exe | ||||||||||||
User: admin Company: GenP Integrity Level: HIGH Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 1156 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20708\GenP-3.4.14.1.exe" ! | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20708\GenP-3.4.14.1.exe | GenP-3.4.14.1.exe | ||||||||||||
User: admin Company: GenP Integrity Level: HIGH Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 1488 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\iz3lne.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1492 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.22710\GenP-3.4.14.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.22710\GenP-3.4.14.1.exe | — | WinRAR.exe | |||||||||||
User: admin Company: GenP Integrity Level: MEDIUM Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 2132 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20528\GenP-3.4.14.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20528\GenP-3.4.14.1.exe | — | WinRAR.exe | |||||||||||
User: admin Company: GenP Integrity Level: MEDIUM Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 3288 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3924 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.21378\GenP-3.4.14.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.21378\GenP-3.4.14.1.exe | — | WinRAR.exe | |||||||||||
User: admin Company: GenP Integrity Level: MEDIUM Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 4004 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20492\GenP-3.4.14.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20492\GenP-3.4.14.1.exe | — | WinRAR.exe | |||||||||||
User: admin Company: GenP Integrity Level: MEDIUM Description: GenP v3.4.14.1 Exit code: 0 Version: 3.4.14.1 Modules
| |||||||||||||||
| 4196 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.21378\GenP-3.4.14.1.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.21378\GenP-3.4.14.1.exe | NSudoLG.exe | ||||||||||||
User: SYSTEM Company: GenP Integrity Level: SYSTEM Description: GenP v3.4.14.1 Version: 3.4.14.1 Modules
| |||||||||||||||
Total events
10 406
Read events
10 353
Write events
45
Delete events
8
Modification events
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\iz3lne.zip | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1488) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6948) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | delete value | Name: | MRUList |
Value: | |||
| (PID) Process: | (6948) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00520061007200240045005800610031003400380038002E00310037003500310039005C00470065006E0050002D0033002E0034002E00310034002E0031002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00520061007200240045005800610031003400380038002E00310037003500310039000000 | |||
| (PID) Process: | (6948) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (6948) GenP-3.4.14.1.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | delete value | Name: | MRUList |
Value: | |||
Executable files
21
Suspicious files
36
Text files
47
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.17519\GenP-3.4.14.1.exe | executable | |
MD5:5AA73CE6297B35AAC0067529A47B44C5 | SHA256:3BDDB83344219A07A43E53F68A0F6920FDD51B7412540D0DAAEAC353B6AB11A2 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.17519\SOURCE\config.ini | ini | |
MD5:ADD427035968BC6F8BCDF0C5D7580495 | SHA256:66232A4D8677CD50612EAEBC664B2F2F3556B497D5BF8657967C259EF4723B68 | |||
| 6948 | GenP-3.4.14.1.exe | C:\Windows\Temp\NSudoLG.exe | executable | |
MD5:7AACFD85B8DFF0AA6867BEDE82CFD147 | SHA256:871E4F28FE39BCAD8D295AE46E148BE458778C0195ED660B7DB18EB595D00BD8 | |||
| 4840 | GenP-3.4.14.1.exe | C:\Users\admin\AppData\Local\Temp\NSudoLG.exe | executable | |
MD5:7AACFD85B8DFF0AA6867BEDE82CFD147 | SHA256:871E4F28FE39BCAD8D295AE46E148BE458778C0195ED660B7DB18EB595D00BD8 | |||
| 6948 | GenP-3.4.14.1.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Explorer\iconcache_16.db | binary | |
MD5:14F4F76B352D3C1D2E3430B71B053926 | SHA256:980982E3051A6BF460C09AB9108D758375F25ED9AEA8D0212277A03383C5B2D2 | |||
| 6948 | GenP-3.4.14.1.exe | C:\Windows\Temp\aut7D4B.tmp | binary | |
MD5:6F040B192B47D1D0860045AA30C102A0 | SHA256:A85D89E380CBF4929EE5B6E7D91BE71AF1C3A727A91CF30AFFB414B98E912180 | |||
| 6948 | GenP-3.4.14.1.exe | C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Windows\Explorer\iconcache_32.db | binary | |
MD5:D85DE9CDBE4505A04A1A70D76CFCC9FC | SHA256:D1078FEC0AC1D09CE878EC574D99EBAFEE3C56DBB192745AB2A4F6E81A535A6F | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20492\GenP-3.4.14.1.exe | executable | |
MD5:5AA73CE6297B35AAC0067529A47B44C5 | SHA256:3BDDB83344219A07A43E53F68A0F6920FDD51B7412540D0DAAEAC353B6AB11A2 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.20492\SOURCE\COMPILE.txt | text | |
MD5:B089647B4BFE6964655CB784D4F1AE38 | SHA256:87B24B13BAA368A62E7F5E377BFA1551CCE0BB2224AA350309F571C24452AC30 | |||
| 1488 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1488.17519\SOURCE\GenP-3.4.14.1.au3 | text | |
MD5:42C434F0A040132E37EDDB5B1D886F8E | SHA256:3DD6CF96E38768110C8F0E64AE8C698E43931FF9FB57B4A1476B63F4E5D45554 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
45
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4076 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4076 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5400 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3528 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2808 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4324 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3528 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
Threats
Process | Message |
|---|---|
GenP-3.4.14.1.exe | Unable to get NTFS id
|
GenP-3.4.14.1.exe | Unable to get NTFS id
|
GenP-3.4.14.1.exe | Unable to get NTFS id
|
GenP-3.4.14.1.exe | Unable to get NTFS id
|
GenP-3.4.14.1.exe | Unable to get NTFS id
|
GenP-3.4.14.1.exe | Unable to get NTFS id
|
GenP-3.4.14.1.exe | Unable to get NTFS id
|
GenP-3.4.14.1.exe | Unable to get NTFS id
|