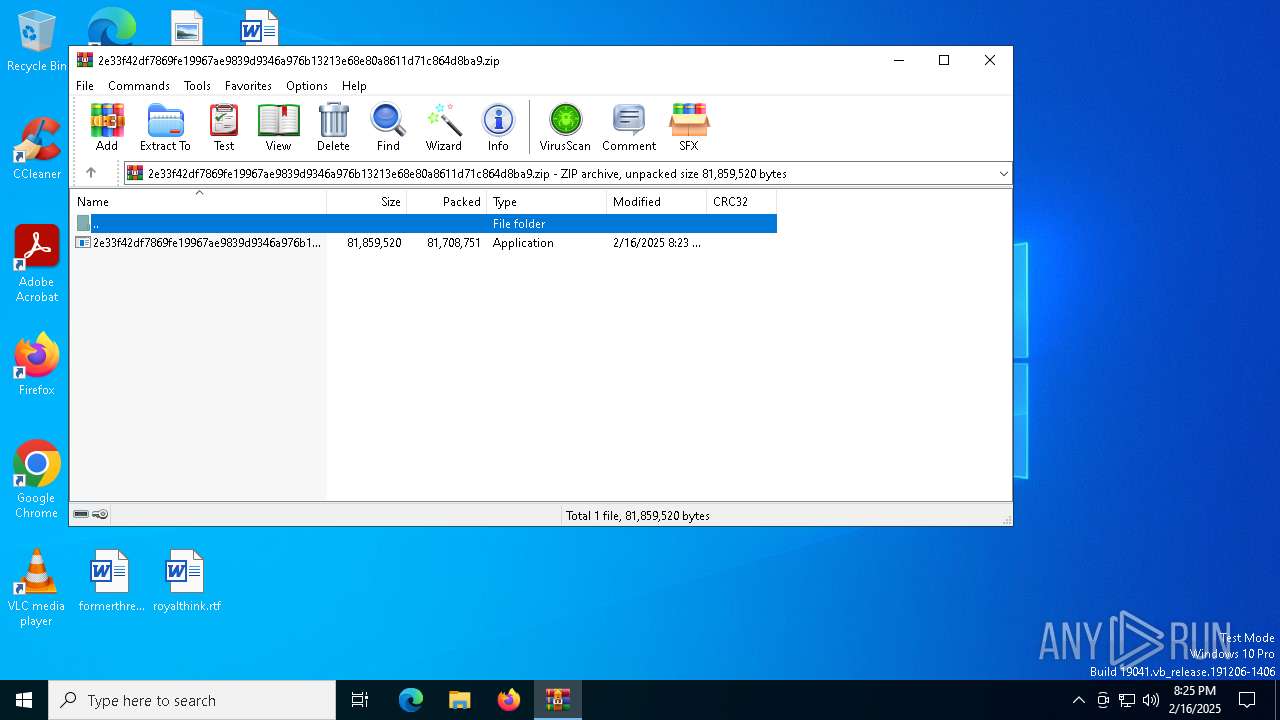
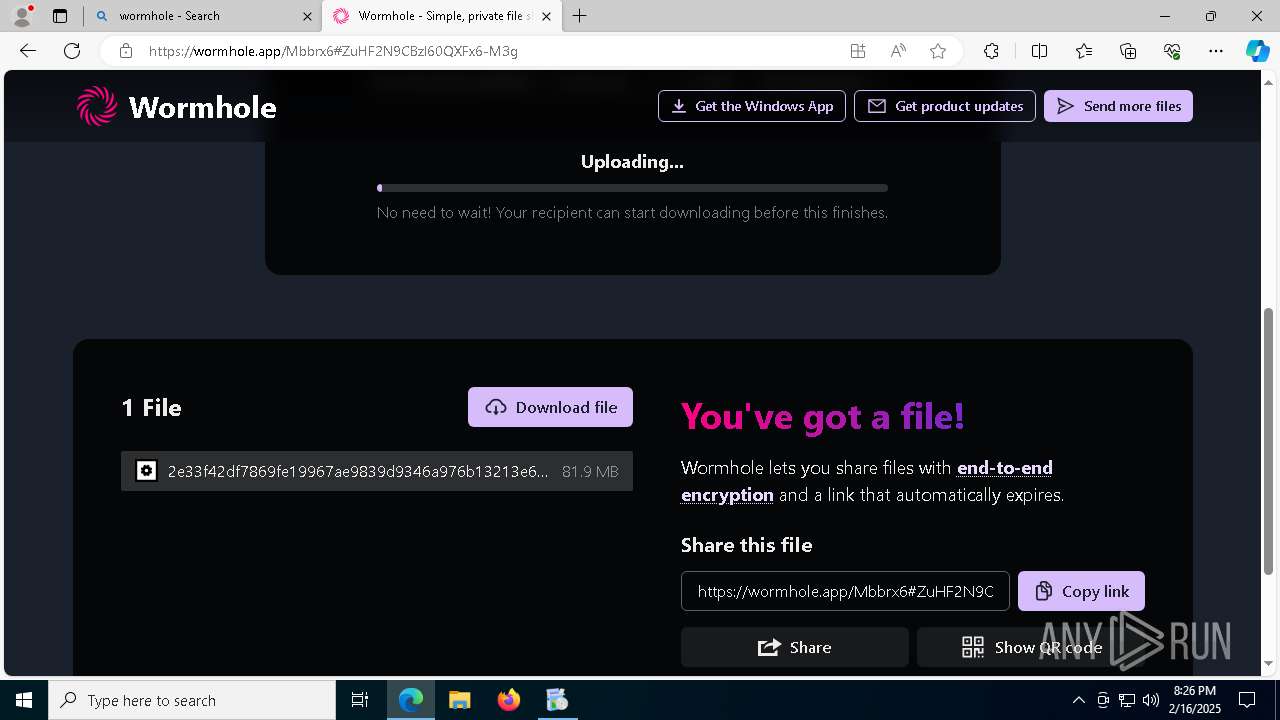
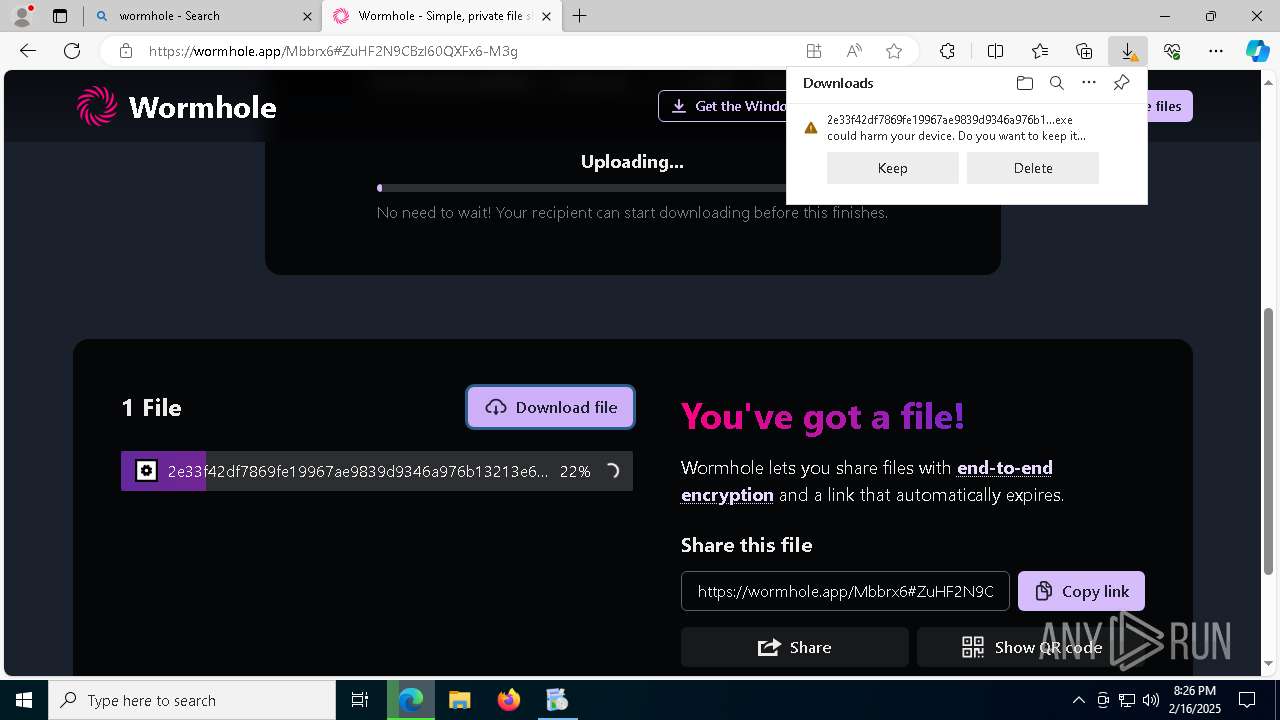
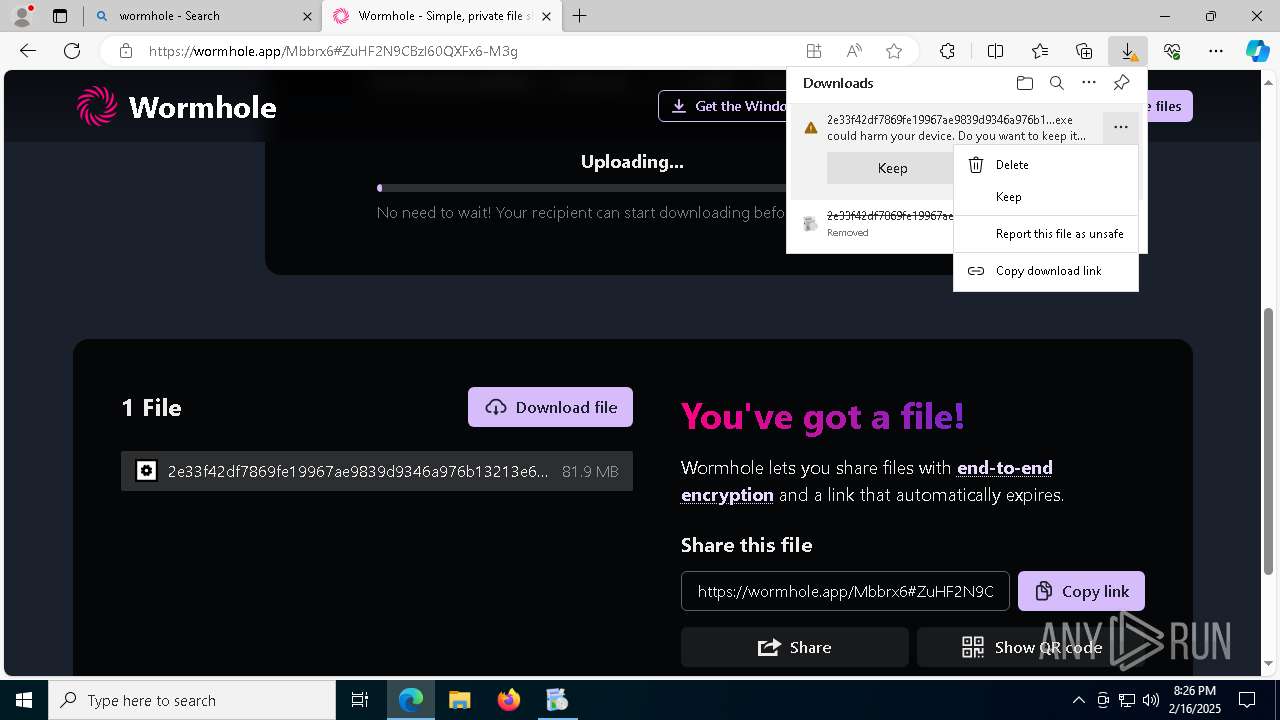
| File name: | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.zip |
| Full analysis: | https://app.any.run/tasks/ecabcb31-f497-446b-a988-875eeeba1dec |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2025, 20:24:37 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
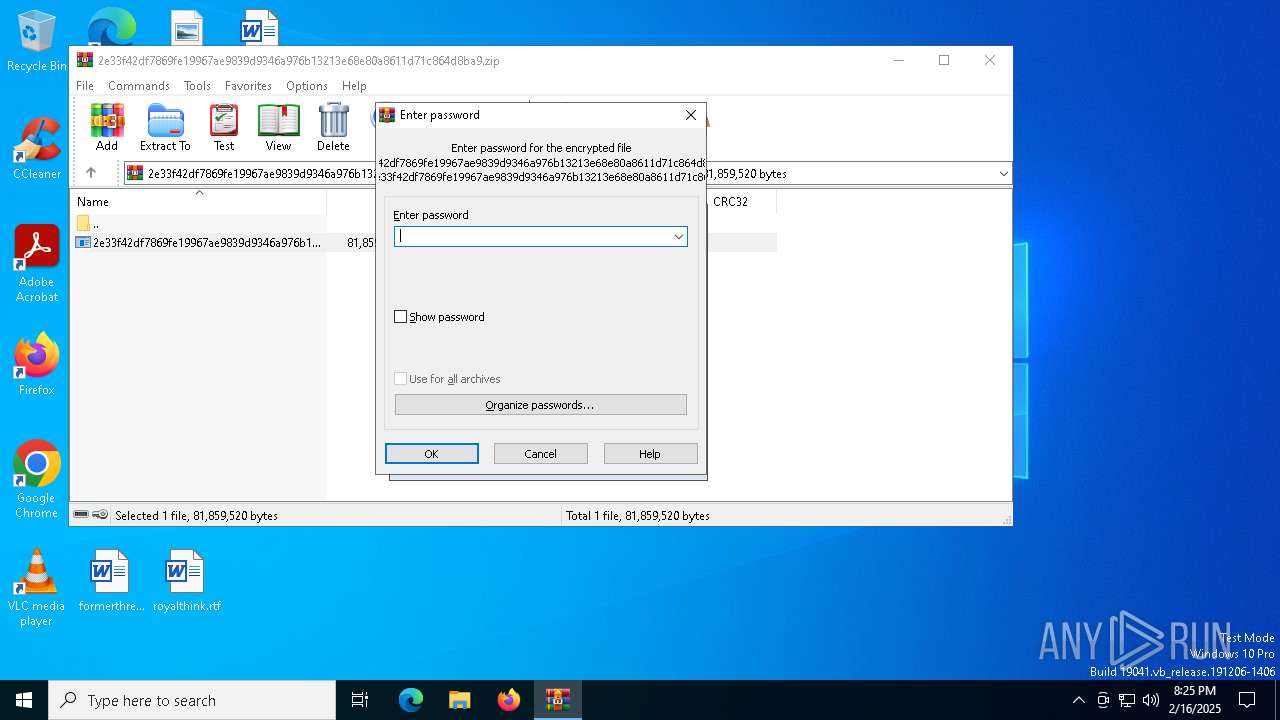
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 68A7B10704B51F65F1107A8799C7D670 |
| SHA1: | F14F41F5A836F404122B4692504FA834B014A90F |
| SHA256: | 14BD85C5613C71E49AAC825CF1EC0269F91784A9E395E8D94CC7D26CDA34FFA8 |
| SSDEEP: | 786432:MFd2I7vobNN2CFPjAr5NncfZfNQhtzeiZoYmDQ:MFsI7vobr28jAr5tcFNQhUiyYmDQ |
MALICIOUS
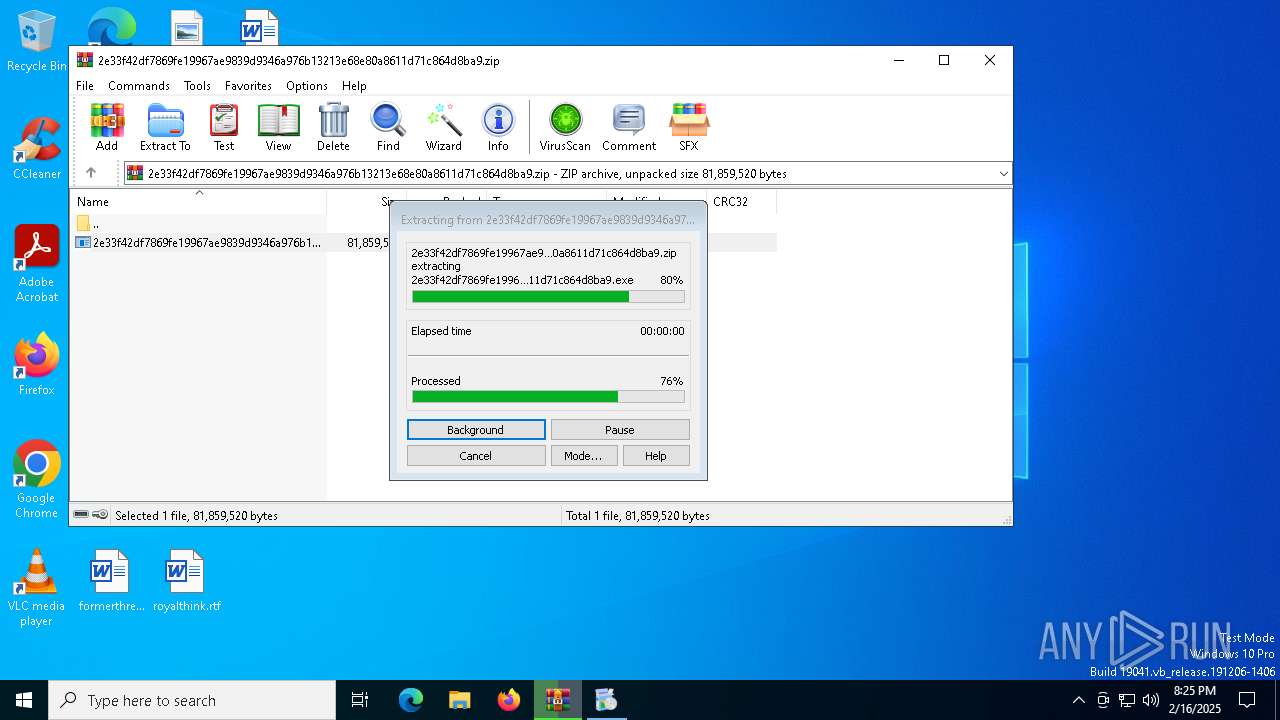
Generic archive extractor
- WinRAR.exe (PID: 1512)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1512)
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
The process creates files with name similar to system file names
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
Malware-specific behavior (creating "System.dll" in Temp)
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
Get information on the list of running processes
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
- cmd.exe (PID: 3696)
Starts CMD.EXE for commands execution
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
Drops 7-zip archiver for unpacking
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
Executable content was dropped or overwritten
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
Process drops legitimate windows executable
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
There is functionality for taking screenshot (YARA)
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
Creates a software uninstall entry
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
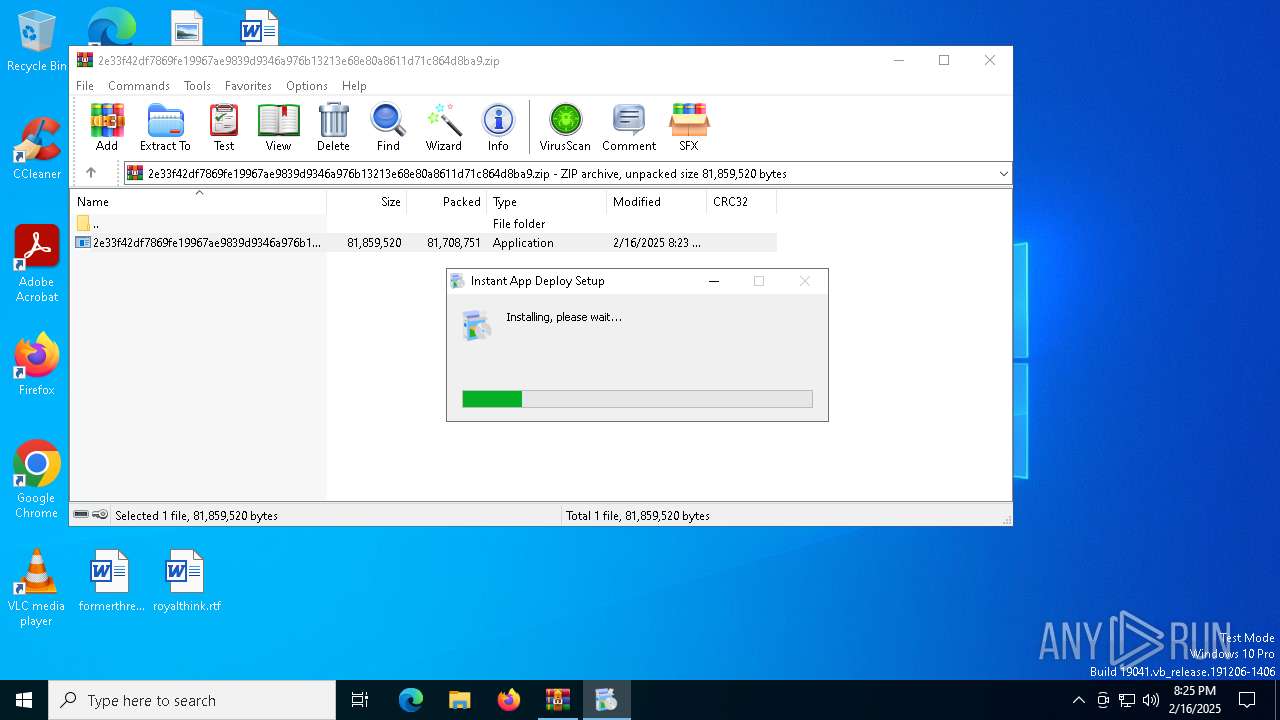
Application launched itself
- Instant App Deploy.exe (PID: 2428)
INFO
Checks supported languages
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
- Instant App Deploy.exe (PID: 2428)
- Instant App Deploy.exe (PID: 2200)
- Instant App Deploy.exe (PID: 3032)
- Instant App Deploy.exe (PID: 432)
- Instant App Deploy.exe (PID: 4468)
- identity_helper.exe (PID: 7496)
Reads the computer name
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
- Instant App Deploy.exe (PID: 2200)
- Instant App Deploy.exe (PID: 3032)
- Instant App Deploy.exe (PID: 2428)
- identity_helper.exe (PID: 7496)
Create files in a temporary directory
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
- Instant App Deploy.exe (PID: 2428)
The sample compiled with english language support
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
Creates files or folders in the user directory
- 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe (PID: 1228)
- Instant App Deploy.exe (PID: 2428)
- Instant App Deploy.exe (PID: 3032)
Manual execution by a user
- Instant App Deploy.exe (PID: 2428)
- msedge.exe (PID: 4908)
Reads Environment values
- Instant App Deploy.exe (PID: 2428)
- identity_helper.exe (PID: 7496)
Reads product name
- Instant App Deploy.exe (PID: 2428)
Checks proxy server information
- Instant App Deploy.exe (PID: 2428)
Process checks computer location settings
- Instant App Deploy.exe (PID: 2428)
- Instant App Deploy.exe (PID: 432)
- Instant App Deploy.exe (PID: 4468)
Reads the machine GUID from the registry
- Instant App Deploy.exe (PID: 2428)
Application launched itself
- msedge.exe (PID: 4908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:02:16 20:23:50 |
| ZipCRC: | 0x7bd63545 |
| ZipCompressedSize: | 81708751 |
| ZipUncompressedSize: | 81859520 |
| ZipFileName: | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe |
Total processes
182
Monitored processes
61
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=20 --mojo-platform-channel-handle=4872 --field-trial-handle=2452,i,11525307760223030094,12991848126235294980,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 432 | "C:\Users\admin\AppData\Local\Programs\InstantAppDeploy\Instant App Deploy.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\InstantAppDeploy" --app-path="C:\Users\admin\AppData\Local\Programs\InstantAppDeploy\resources\app.asar" --enable-sandbox --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --field-trial-handle=2584,i,3910922880775103414,3285254522777538866,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2580 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\InstantAppDeploy\Instant App Deploy.exe | — | Instant App Deploy.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: Instant App Deploy Exit code: 0 Version: 2.1.0 Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb1512.33138\2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb1512.33138\2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 2.1.0 Modules
| |||||||||||||||
| 1512 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1580 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5880 --field-trial-handle=2452,i,11525307760223030094,12991848126235294980,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1876 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5992 --field-trial-handle=2452,i,11525307760223030094,12991848126235294980,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2072 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6216 --field-trial-handle=2452,i,11525307760223030094,12991848126235294980,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2200 | "C:\Users\admin\AppData\Local\Programs\InstantAppDeploy\Instant App Deploy.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\InstantAppDeploy" --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=1836,i,3910922880775103414,3285254522777538866,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=1828 /prefetch:2 | C:\Users\admin\AppData\Local\Programs\InstantAppDeploy\Instant App Deploy.exe | — | Instant App Deploy.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: LOW Description: Instant App Deploy Version: 2.1.0 Modules
| |||||||||||||||
| 2424 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=41 --mojo-platform-channel-handle=7708 --field-trial-handle=2452,i,11525307760223030094,12991848126235294980,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2428 | "C:\Users\admin\AppData\Local\Programs\InstantAppDeploy\Instant App Deploy.exe" | C:\Users\admin\AppData\Local\Programs\InstantAppDeploy\Instant App Deploy.exe | — | explorer.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: Instant App Deploy Version: 2.1.0 Modules
| |||||||||||||||
Total events
10 251
Read events
10 162
Write events
71
Delete events
18
Modification events
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.zip | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1512) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1228) 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\c7062070-279b-58f2-9aed-9ae1f29f455c |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\InstantAppDeploy | |||
Executable files
63
Suspicious files
904
Text files
90
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1512 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb1512.33138\2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | — | |
MD5:— | SHA256:— | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\app-64.7z | — | |
MD5:— | SHA256:— | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\7z-out\icudtl.dat | — | |
MD5:— | SHA256:— | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\7z-out\LICENSES.chromium.html | — | |
MD5:— | SHA256:— | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\StdUtils.dll | executable | |
MD5:C6A6E03F77C313B267498515488C5740 | SHA256:B72E9013A6204E9F01076DC38DABBF30870D44DFC66962ADBF73619D4331601E | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\7z-out\locales\af.pak | binary | |
MD5:FC32A6B72FC91E1BE9C2C9D2EA586EC3 | SHA256:C56CB2841EE2E40FBDD6B7E293A1CE74BD10FD500465FCF99D1E07F8D69F8CE7 | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\nsis7z.dll | executable | |
MD5:80E44CE4895304C6A3A831310FBF8CD0 | SHA256:B393F05E8FF919EF071181050E1873C9A776E1A0AE8329AEFFF7007D0CADF592 | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\nsExec.dll | executable | |
MD5:EC0504E6B8A11D5AAD43B296BEEB84B2 | SHA256:5D9CEB1CE5F35AEA5F9E5A0C0EDEEEC04DFEFE0C77890C80C70E98209B58B962 | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\7z-out\chrome_100_percent.pak | binary | |
MD5:83EC43F2AF9FC52025F3F807B185D424 | SHA256:A659EE9EB38636F85F5336587C578FB29740D3EFFAFF9B92852C8A210E92978C | |||
| 1228 | 2e33f42df7869fe19967ae9839d9346a976b13213e68e80a8611d71c864d8ba9.exe | C:\Users\admin\AppData\Local\Temp\nsnF800.tmp\7z-out\locales\bg.pak | binary | |
MD5:D9D3B4D420BE9277D69584A3C0B5080A | SHA256:F08DE6909FAF88465C28388AA03FDF08E165866A5A23C738ED33382275C4EC83 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
206
DNS requests
157
Threats
125
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1016 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1016 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2624 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | HEAD | 200 | 23.50.131.81:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/68591036-2289-4858-9f7f-9149e89c8a08?P1=1739887802&P2=404&P3=2&P4=Ah252GxOB7A1QrdqsZBC%2blqHfogzYFAZfxaRy8SI0ch23DHLGXsPpxWF0RnGI%2b8S0Z%2fIvVG2aSx9uooIPyZmiA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5588 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.176:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1016 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1016 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6300 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wormhole .app) |
6300 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wormhole .app) |
6300 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wormhole .app) |
6300 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Related Domain in DNS Lookup (wormhole .app) |
6300 | msedge.exe | Misc activity | ET FILE_SHARING File Sharing Domain Observed in TLS SNI (wormhole .app) |
6300 | msedge.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard Low Port) |
6300 | msedge.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard Low Port) |
6300 | msedge.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard Low Port) |
6300 | msedge.exe | Misc activity | ET INFO Session Traversal Utilities for NAT (STUN Binding Request On Non-Standard Low Port) |
6300 | msedge.exe | Generic Protocol Command Decode | SURICATA QUIC error on data |