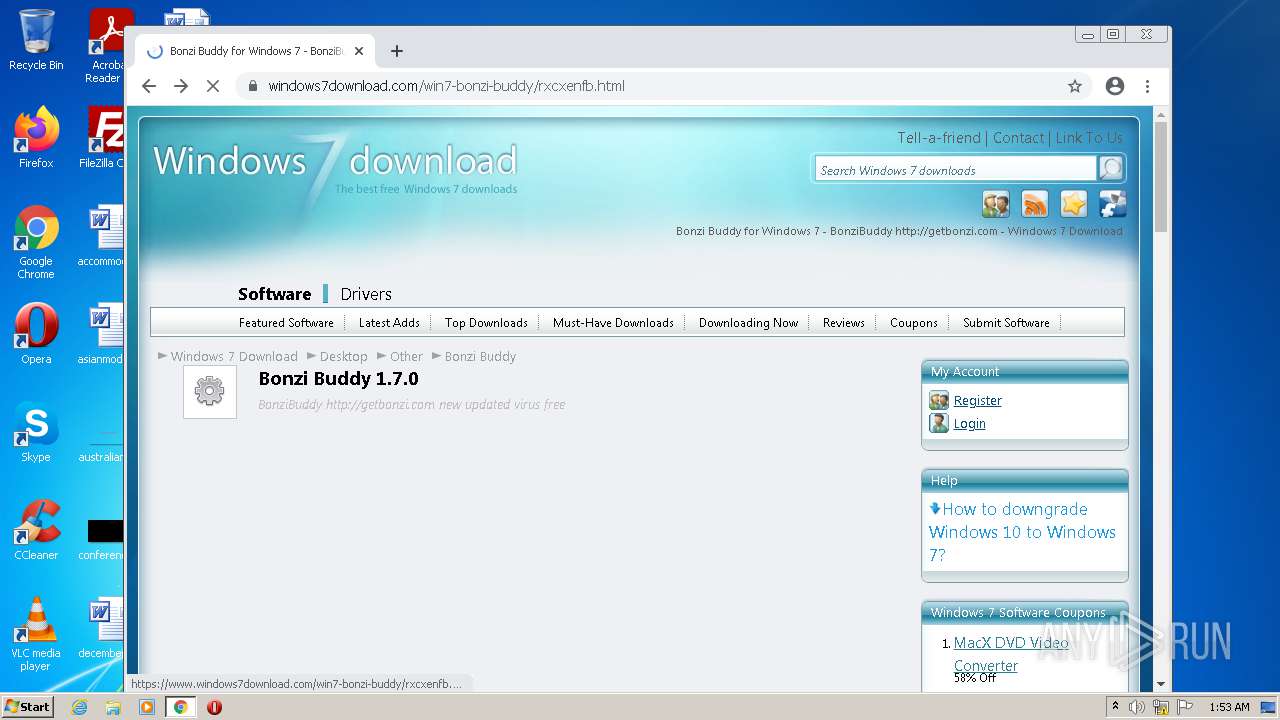
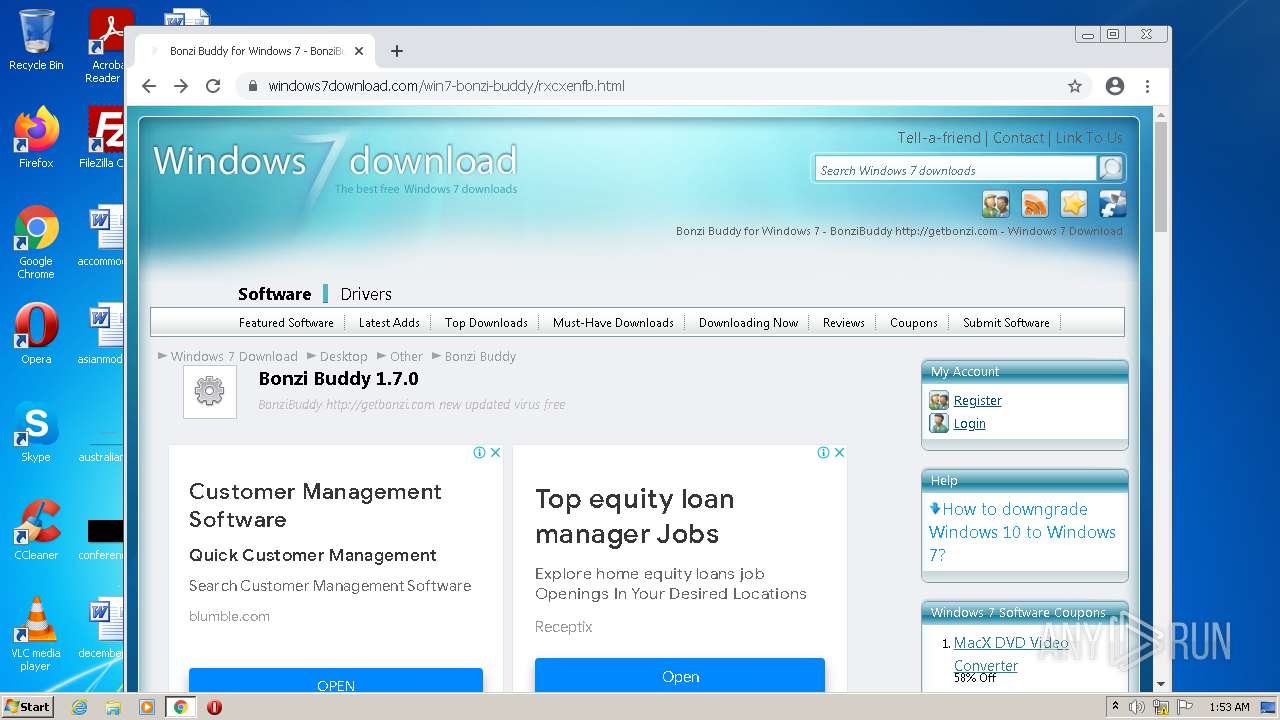
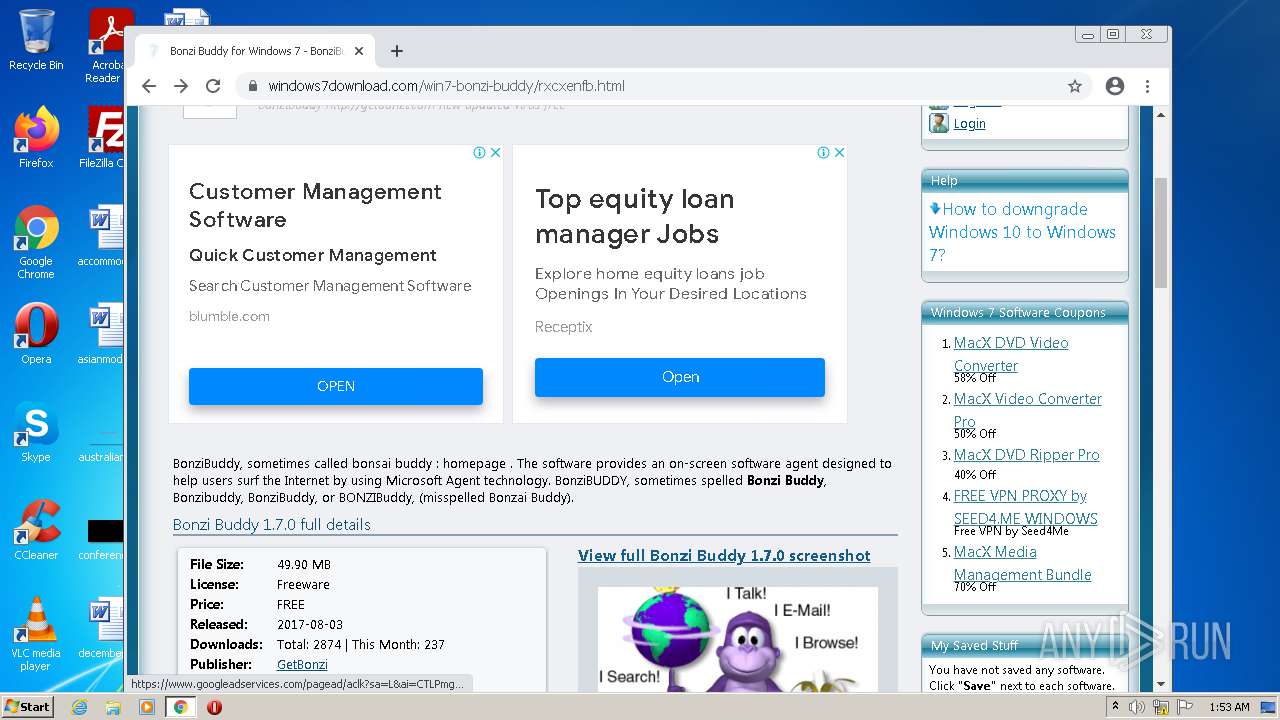
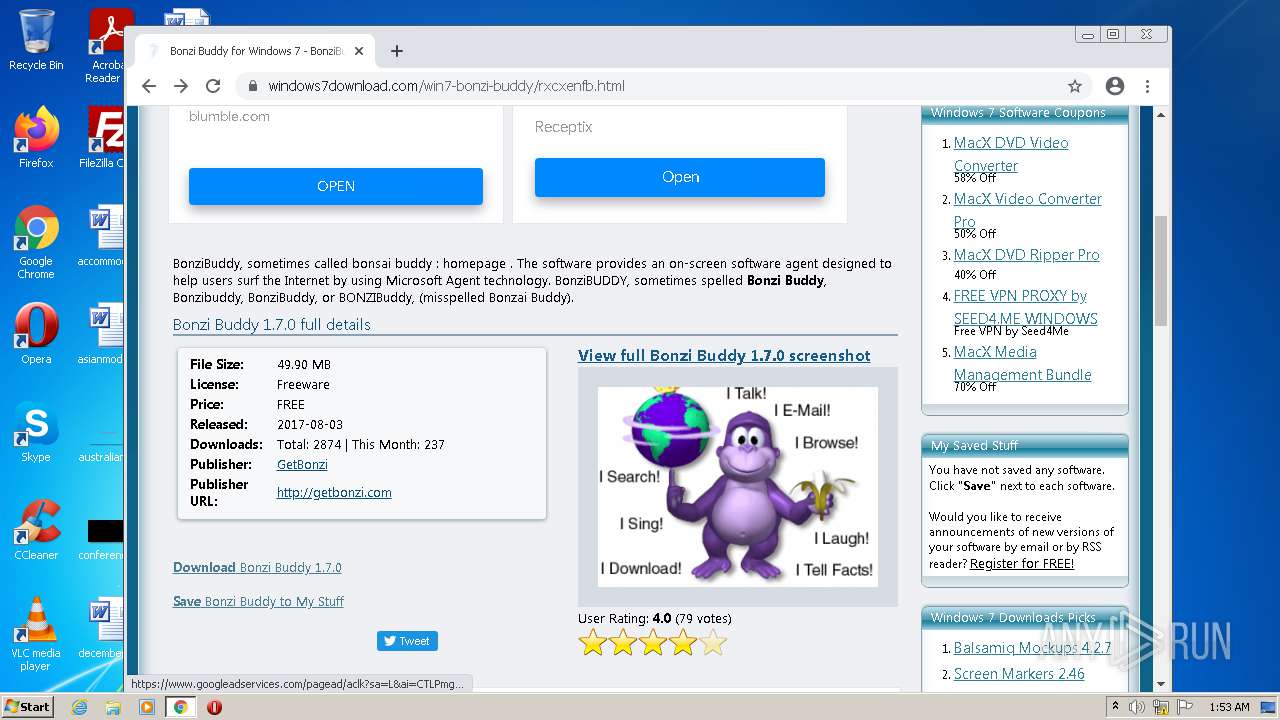
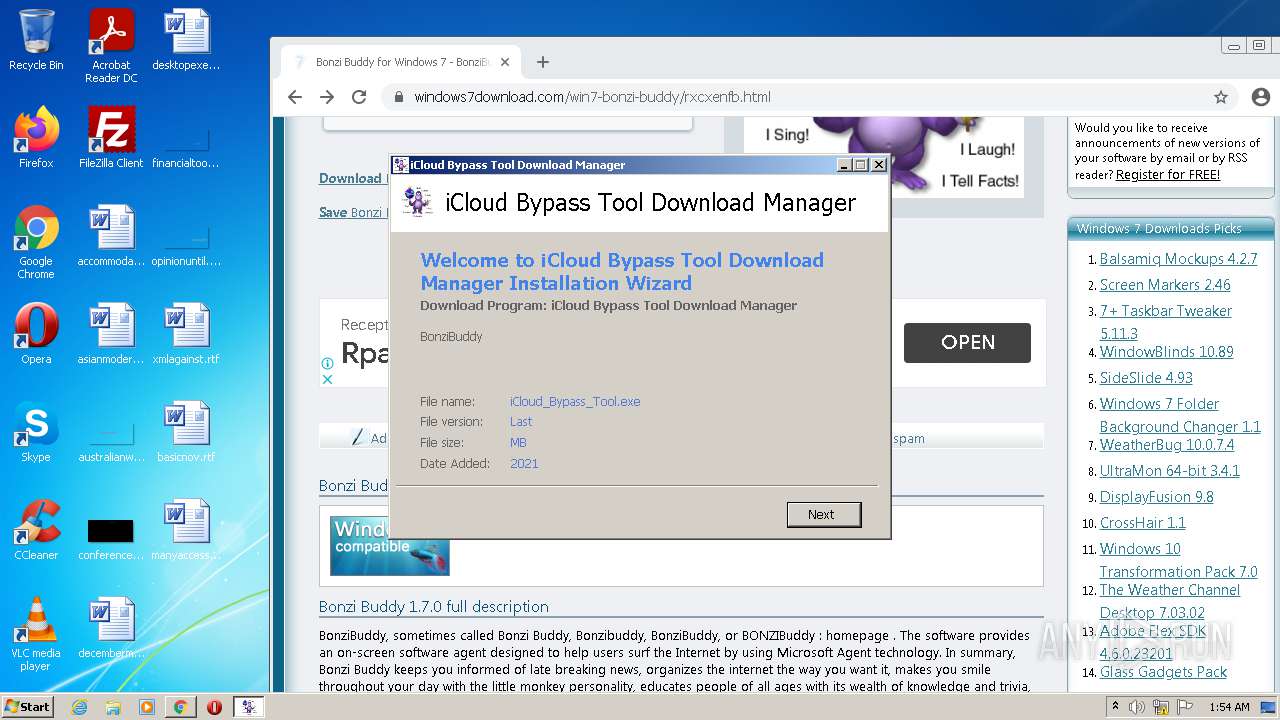
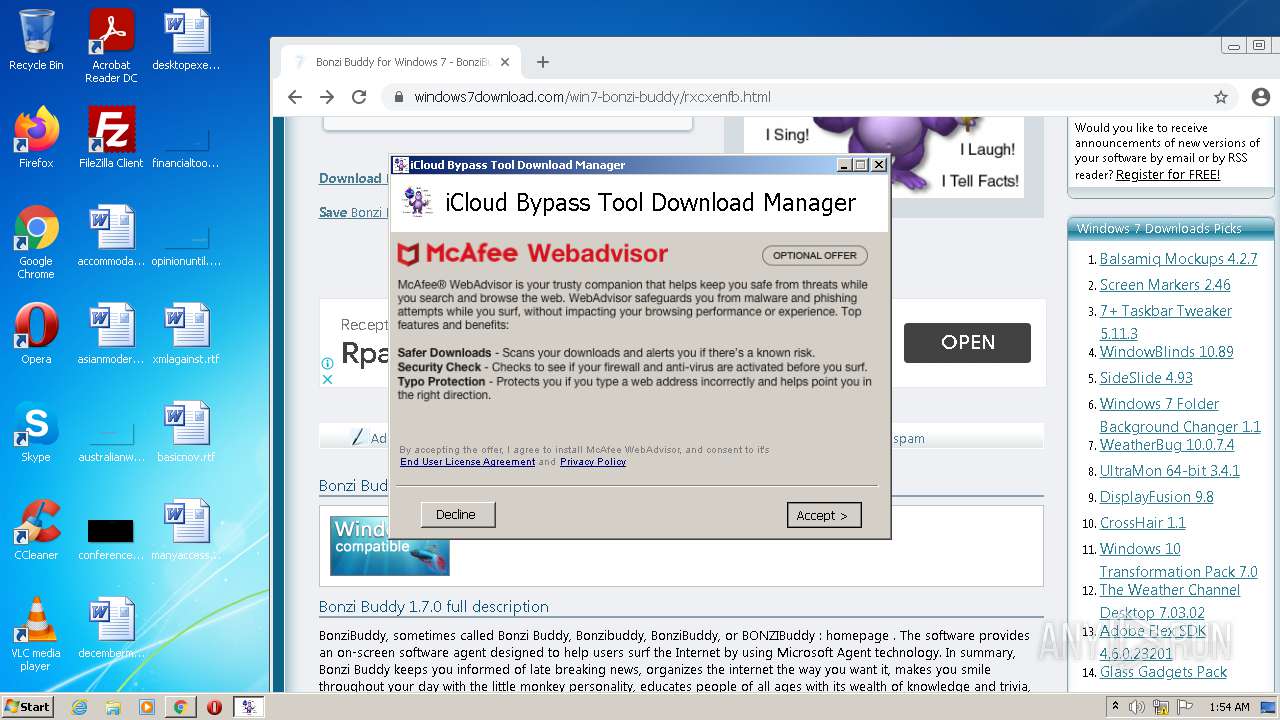
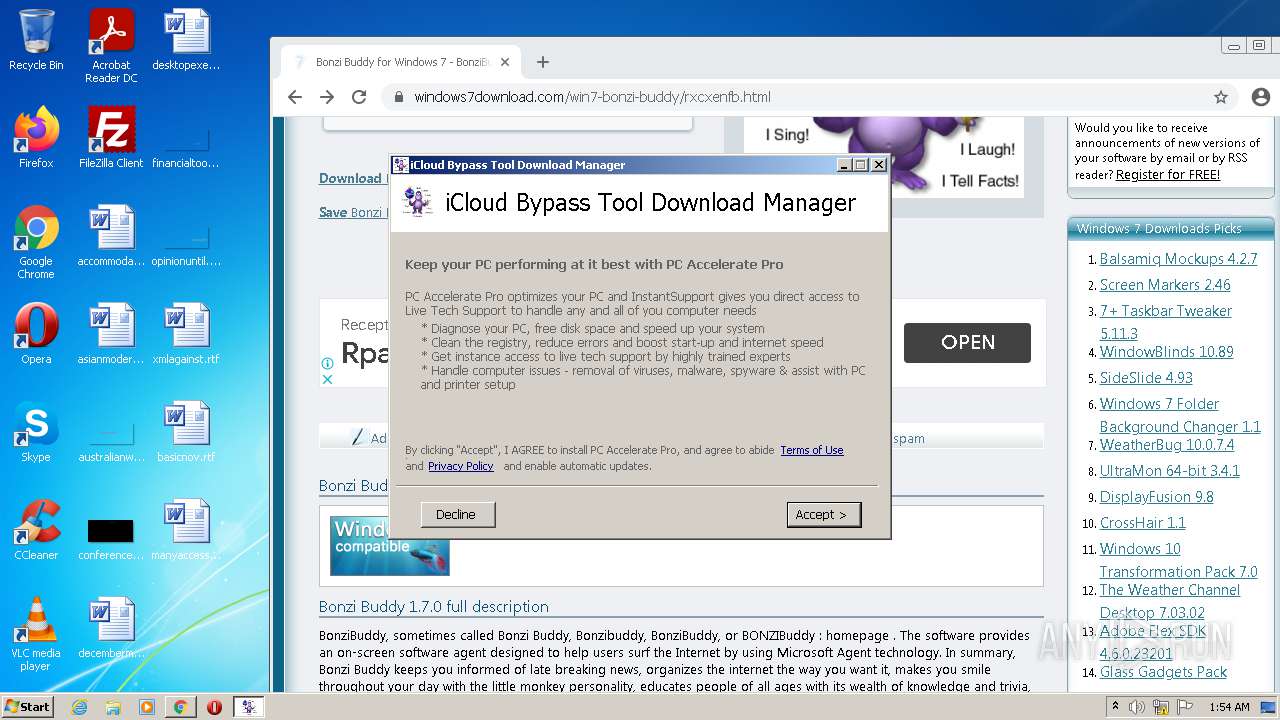
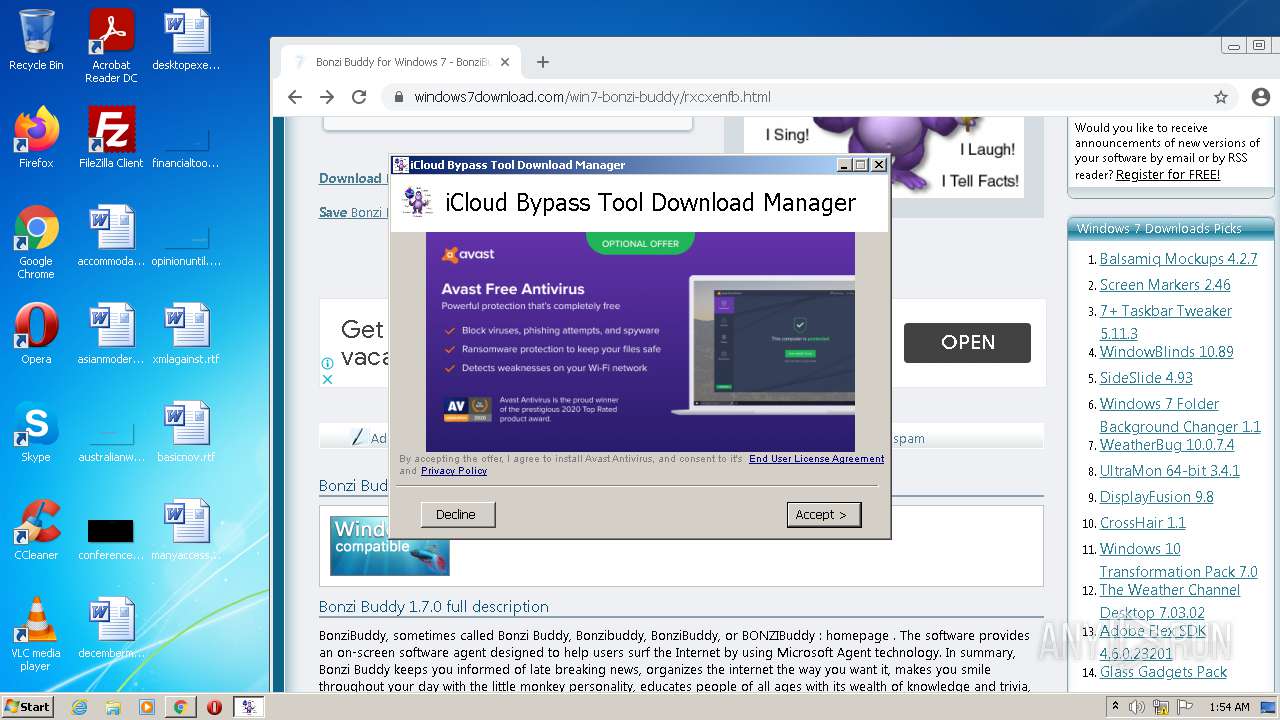
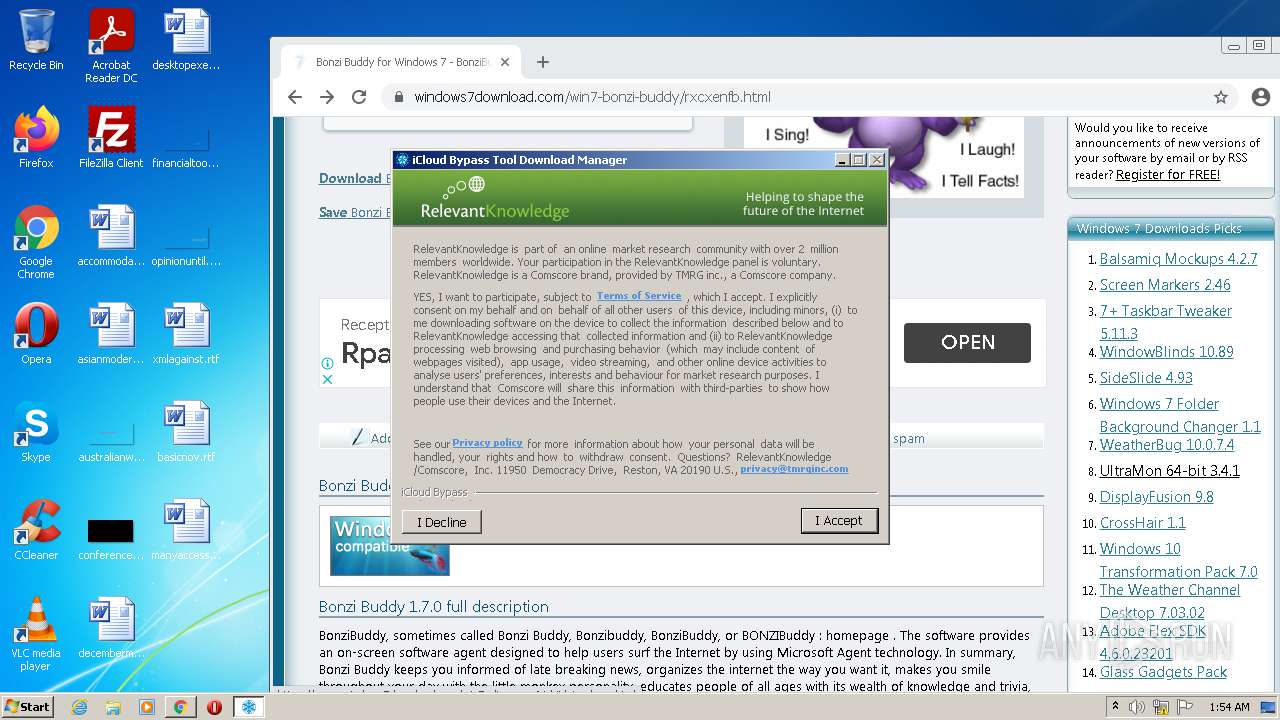
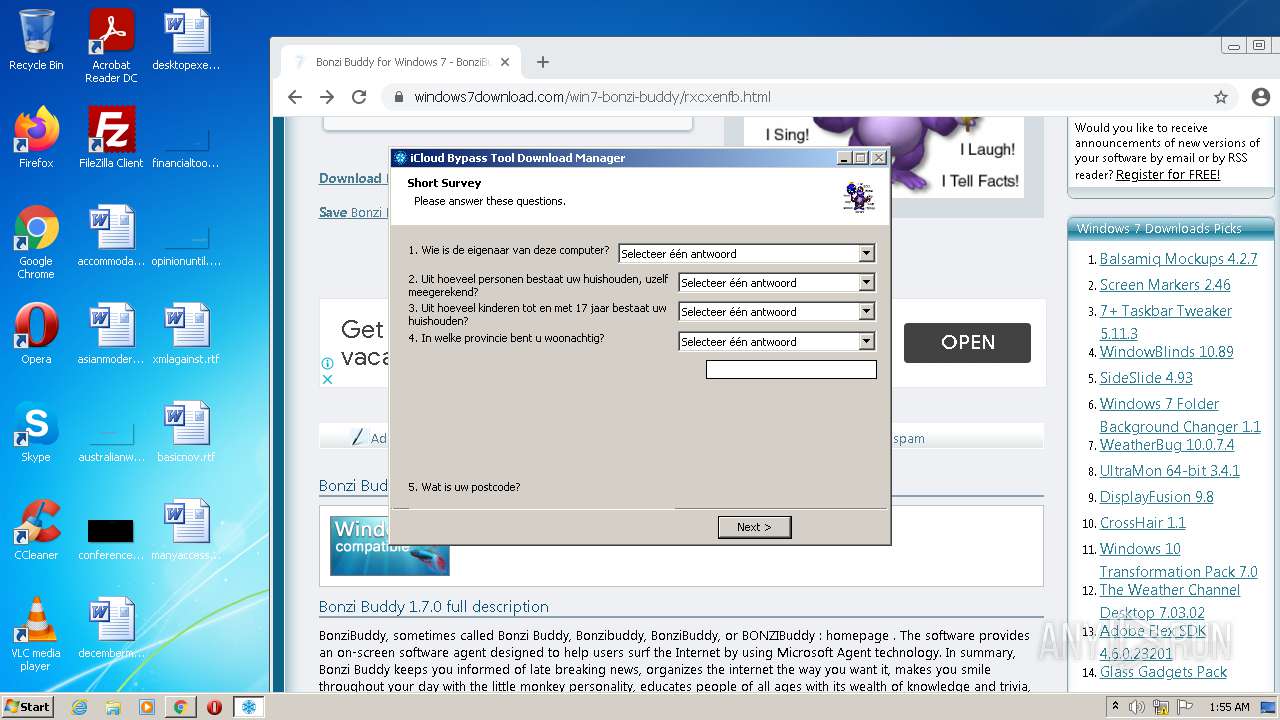
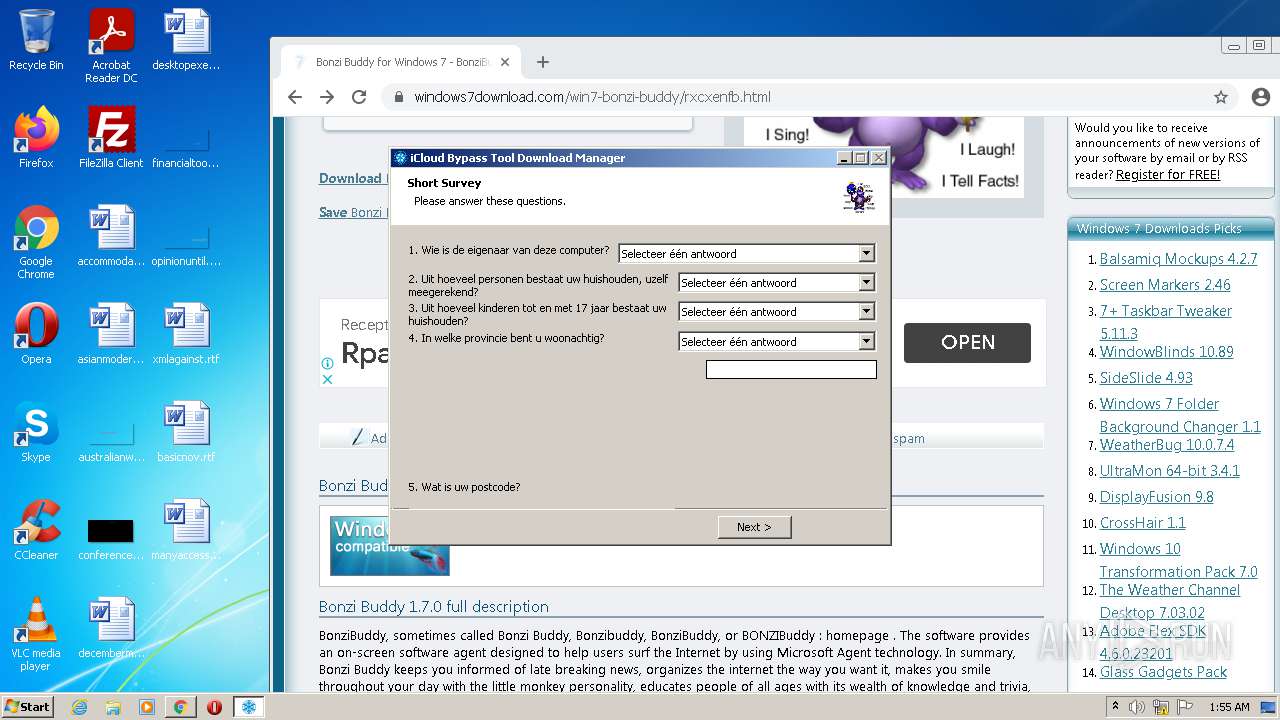
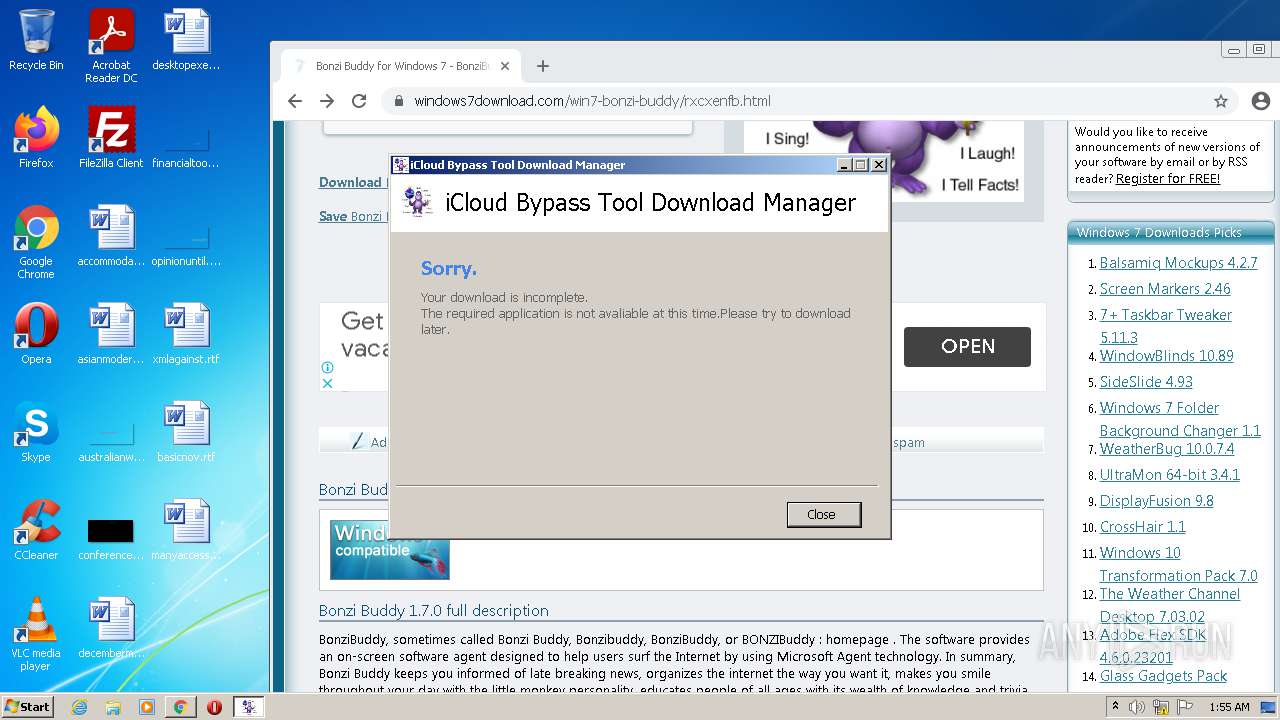
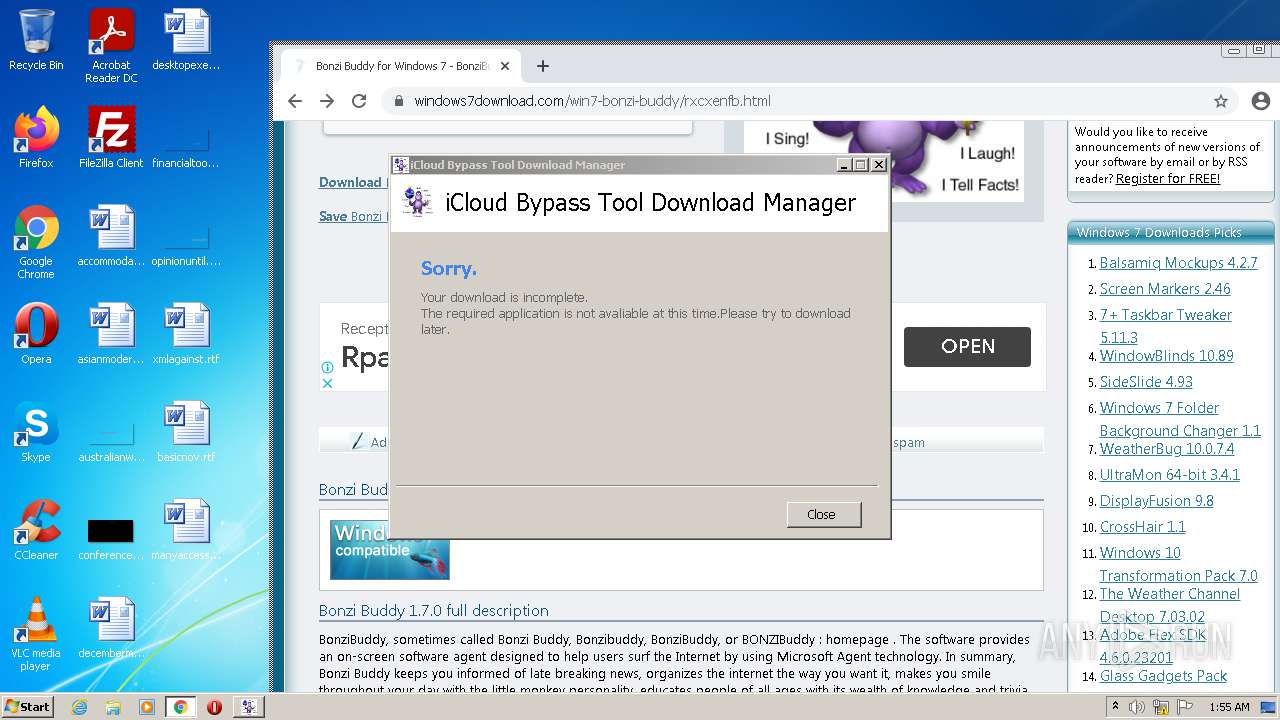
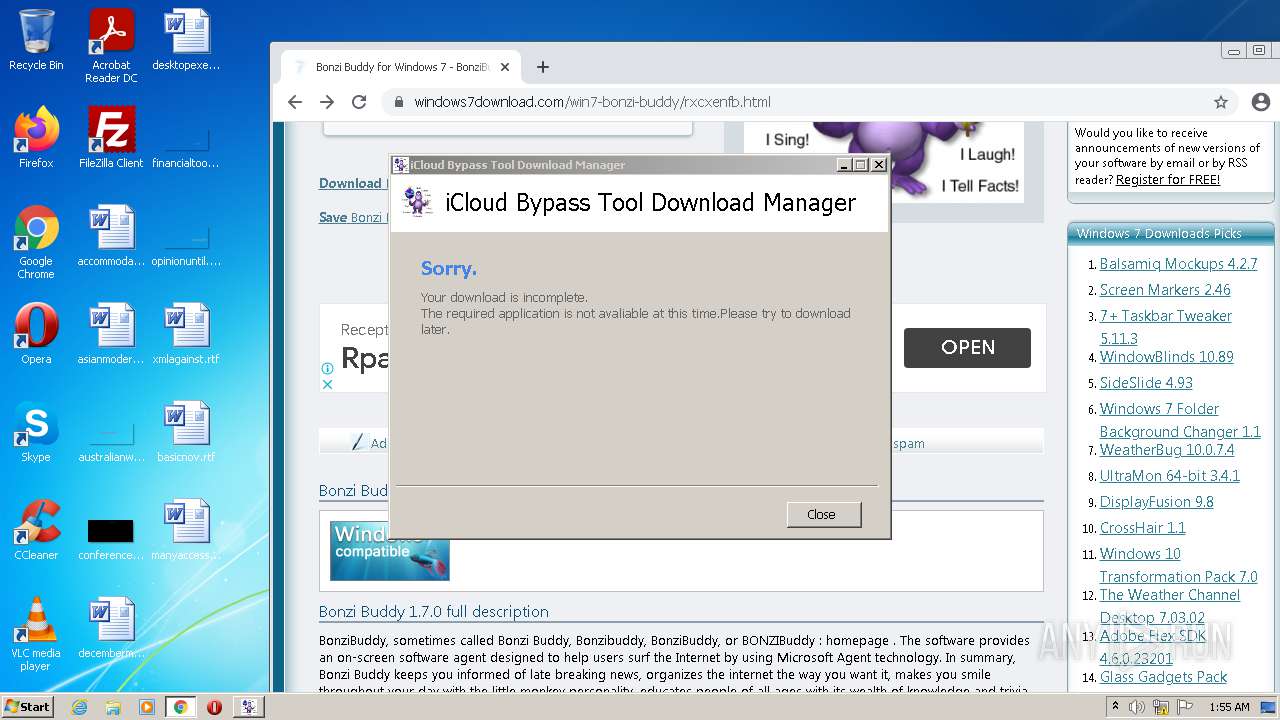
| File name: | jalkakuva_1 |
| Full analysis: | https://app.any.run/tasks/81cf5029-76c6-4bbc-be29-7d39444af341 |
| Verdict: | Malicious activity |
| Analysis date: | July 22, 2021, 00:51:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | image/jpeg |
| File info: | JPEG image data, Exif standard: [TIFF image data, big-endian, direntries=0], baseline, precision 8, 864x1738, frames 3 |
| MD5: | 7944CE539C151BF5B70817E3913C14C1 |
| SHA1: | 1E7E5394223225EC720E1F83053E25D8E46CC9BD |
| SHA256: | 14B38066552F5AD97F66337EFC300009DC0B3272C8E95BA305C57726B8A9D1CB |
| SSDEEP: | 6144:2Py97Nsp0QJrkLMfX+Owa6Qk0iP9ZcZ/D2+HFgSqZ1pa4yX+Et9K:2G7DQtfR1kxP9ZcAki1w4yOu0 |
MALICIOUS
Application was dropped or rewritten from another process
- SushiSetup.exe (PID: 572)
- SushiSetup.exe (PID: 1096)
- SushiePower.tmp (PID: 880)
- saBSI.exe (PID: 3996)
- installer.exe (PID: 4028)
- forget_bell.tmp (PID: 3832)
- response_obey.tmp (PID: 572)
- pcapd.exe (PID: 1428)
- installer.exe (PID: 2588)
- RFileStpOn.tmp (PID: 3736)
- assistant.tmp (PID: 3268)
- ServiceHost.exe (PID: 2752)
- UIHost.exe (PID: 1096)
- rlservice.exe (PID: 128)
- updater.exe (PID: 2768)
- rlvknlg.exe (PID: 4092)
Changes settings of System certificates
- saBSI.exe (PID: 3996)
Drops executable file immediately after starts
- installer.exe (PID: 4028)
- pcapd.exe (PID: 1428)
- forget_bell.tmp (PID: 3832)
- rlvknlg.exe (PID: 4092)
- chrome.exe (PID: 3504)
Registers / Runs the DLL via REGSVR32.EXE
- installer.exe (PID: 2588)
- ServiceHost.exe (PID: 2752)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 3748)
- regsvr32.exe (PID: 2384)
- ServiceHost.exe (PID: 2752)
- UIHost.exe (PID: 1096)
- regsvr32.exe (PID: 128)
- rlvknlg.exe (PID: 4092)
- response_obey.tmp (PID: 572)
Actions looks like stealing of personal data
- ServiceHost.exe (PID: 2752)
- UIHost.exe (PID: 1096)
Steals credentials from Web Browsers
- ServiceHost.exe (PID: 2752)
- UIHost.exe (PID: 1096)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1340)
Starts Microsoft Installer
- chrome.exe (PID: 1340)
Reads Windows owner or organization settings
- msiexec.exe (PID: 3840)
- msiexec.exe (PID: 2440)
Executable content was dropped or overwritten
- chrome.exe (PID: 1340)
- msiexec.exe (PID: 2440)
- SushiSetup.exe (PID: 572)
- SushiePower.tmp (PID: 880)
- saBSI.exe (PID: 3996)
- chrome.exe (PID: 2988)
- installer.exe (PID: 4028)
- installer.exe (PID: 2588)
- pcapd.exe (PID: 1428)
- RFileStpOn.tmp (PID: 3736)
- forget_bell.tmp (PID: 3832)
- response_obey.tmp (PID: 572)
- rlvknlg.exe (PID: 4092)
- chrome.exe (PID: 3504)
Reads the Windows organization settings
- msiexec.exe (PID: 3840)
- msiexec.exe (PID: 2440)
Executed as Windows Service
- msiexec.exe (PID: 2440)
- ServiceHost.exe (PID: 2752)
- rlservice.exe (PID: 128)
Drops a file with a compile date too recent
- msiexec.exe (PID: 2440)
- SushiSetup.exe (PID: 572)
- SushiePower.tmp (PID: 880)
- pcapd.exe (PID: 1428)
- response_obey.tmp (PID: 572)
- rlvknlg.exe (PID: 4092)
Checks supported languages
- SushiSetup.exe (PID: 1096)
- cmd.exe (PID: 3904)
- SushiSetup.exe (PID: 572)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 2592)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 696)
- cmd.exe (PID: 3784)
- SushiePower.tmp (PID: 880)
- cmd.exe (PID: 1060)
- cmd.exe (PID: 2000)
- cmd.exe (PID: 4068)
- cmd.exe (PID: 788)
- saBSI.exe (PID: 3996)
- installer.exe (PID: 4028)
- installer.exe (PID: 2588)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 2744)
- RFileStpOn.tmp (PID: 3736)
- cmd.exe (PID: 2376)
- cmd.exe (PID: 3400)
- cmd.exe (PID: 1780)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 852)
- forget_bell.tmp (PID: 3832)
- pcapd.exe (PID: 1428)
- unsecapp.exe (PID: 2592)
- response_obey.tmp (PID: 572)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 604)
- cmd.exe (PID: 3724)
- assistant.tmp (PID: 3268)
- UIHost.exe (PID: 1096)
- ServiceHost.exe (PID: 2752)
- rlvknlg.exe (PID: 4092)
- rlservice.exe (PID: 128)
- cmd.exe (PID: 1000)
- updater.exe (PID: 2768)
- cmd.exe (PID: 2500)
- cmd.exe (PID: 2480)
Reads the computer name
- SushiSetup.exe (PID: 1096)
- SushiSetup.exe (PID: 572)
- SushiePower.tmp (PID: 880)
- saBSI.exe (PID: 3996)
- installer.exe (PID: 2588)
- RFileStpOn.tmp (PID: 3736)
- pcapd.exe (PID: 1428)
- forget_bell.tmp (PID: 3832)
- unsecapp.exe (PID: 2592)
- response_obey.tmp (PID: 572)
- assistant.tmp (PID: 3268)
- UIHost.exe (PID: 1096)
- ServiceHost.exe (PID: 2752)
- rlservice.exe (PID: 128)
- rlvknlg.exe (PID: 4092)
- updater.exe (PID: 2768)
Starts CMD.EXE for commands execution
- SushiSetup.exe (PID: 1096)
- SushiSetup.exe (PID: 572)
- cmd.exe (PID: 2592)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 696)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 1060)
- SushiePower.tmp (PID: 880)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 852)
- cmd.exe (PID: 2376)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 604)
- updater.exe (PID: 2768)
- RFileStpOn.tmp (PID: 3736)
Starts SC.EXE for service management
- cmd.exe (PID: 3936)
- cmd.exe (PID: 3904)
- cmd.exe (PID: 2216)
- cmd.exe (PID: 3300)
- installer.exe (PID: 2588)
Application launched itself
- SushiSetup.exe (PID: 1096)
- cmd.exe (PID: 2592)
- cmd.exe (PID: 2244)
- cmd.exe (PID: 696)
- cmd.exe (PID: 3784)
- cmd.exe (PID: 2148)
- cmd.exe (PID: 1060)
- cmd.exe (PID: 1812)
- cmd.exe (PID: 852)
- cmd.exe (PID: 2376)
- cmd.exe (PID: 2744)
- cmd.exe (PID: 3936)
- cmd.exe (PID: 604)
Creates a directory in Program Files
- SushiSetup.exe (PID: 572)
- installer.exe (PID: 4028)
- installer.exe (PID: 2588)
- response_obey.tmp (PID: 572)
Creates files in the program directory
- SushiSetup.exe (PID: 572)
- saBSI.exe (PID: 3996)
- installer.exe (PID: 4028)
- ServiceHost.exe (PID: 2752)
- UIHost.exe (PID: 1096)
- response_obey.tmp (PID: 572)
- rlvknlg.exe (PID: 4092)
- installer.exe (PID: 2588)
Searches for installed software
- SushiePower.tmp (PID: 880)
- rlvknlg.exe (PID: 4092)
- rlservice.exe (PID: 128)
- updater.exe (PID: 2768)
Reads Environment values
- SushiePower.tmp (PID: 880)
- ServiceHost.exe (PID: 2752)
- netsh.exe (PID: 2608)
Reads the date of Windows installation
- SushiePower.tmp (PID: 880)
Starts CMD.EXE for self-deleting
- SushiSetup.exe (PID: 572)
- cmd.exe (PID: 1060)
Starts application with an unusual extension
- cmd.exe (PID: 4068)
- cmd.exe (PID: 1780)
- RFileStpOn.tmp (PID: 3736)
- cmd.exe (PID: 3724)
Drops a file that was compiled in debug mode
- SushiePower.tmp (PID: 880)
- saBSI.exe (PID: 3996)
- installer.exe (PID: 4028)
- installer.exe (PID: 2588)
- RFileStpOn.tmp (PID: 3736)
- forget_bell.tmp (PID: 3832)
- chrome.exe (PID: 3504)
Adds / modifies Windows certificates
- saBSI.exe (PID: 3996)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 3748)
- regsvr32.exe (PID: 2384)
- regsvr32.exe (PID: 128)
Drops a file with too old compile date
- SushiePower.tmp (PID: 880)
Reads Windows Product ID
- RFileStpOn.tmp (PID: 3736)
Executed via COM
- unsecapp.exe (PID: 2592)
Creates a software uninstall entry
- installer.exe (PID: 2588)
- ServiceHost.exe (PID: 2752)
- rlvknlg.exe (PID: 4092)
- response_obey.tmp (PID: 572)
Creates files in the Windows directory
- ServiceHost.exe (PID: 2752)
- rlvknlg.exe (PID: 4092)
Removes files from Windows directory
- ServiceHost.exe (PID: 2752)
Uses NETSH.EXE for network configuration
- rlvknlg.exe (PID: 4092)
INFO
Application launched itself
- chrome.exe (PID: 1340)
Manual execution by user
- chrome.exe (PID: 1340)
Reads the computer name
- chrome.exe (PID: 1340)
- chrome.exe (PID: 2956)
- chrome.exe (PID: 3240)
- chrome.exe (PID: 2988)
- chrome.exe (PID: 3932)
- chrome.exe (PID: 980)
- chrome.exe (PID: 392)
- chrome.exe (PID: 3820)
- chrome.exe (PID: 336)
- chrome.exe (PID: 2052)
- msiexec.exe (PID: 2440)
- msiexec.exe (PID: 3840)
- sc.exe (PID: 3872)
- sc.exe (PID: 588)
- sc.exe (PID: 2596)
- sc.exe (PID: 3032)
- chrome.exe (PID: 2912)
- sc.exe (PID: 2376)
- sc.exe (PID: 3832)
- sc.exe (PID: 1280)
- regsvr32.exe (PID: 2384)
- sc.exe (PID: 3516)
- regsvr32.exe (PID: 128)
- netsh.exe (PID: 2608)
Reads the hosts file
- chrome.exe (PID: 1340)
- chrome.exe (PID: 2988)
Checks supported languages
- chrome.exe (PID: 3020)
- chrome.exe (PID: 2988)
- chrome.exe (PID: 3884)
- chrome.exe (PID: 3240)
- rundll32.exe (PID: 3648)
- chrome.exe (PID: 1340)
- chrome.exe (PID: 3908)
- chrome.exe (PID: 2956)
- chrome.exe (PID: 1436)
- chrome.exe (PID: 2440)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 3376)
- chrome.exe (PID: 3780)
- chrome.exe (PID: 2176)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 3492)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 3660)
- chrome.exe (PID: 3676)
- chrome.exe (PID: 3828)
- chrome.exe (PID: 2324)
- chrome.exe (PID: 1192)
- chrome.exe (PID: 2316)
- chrome.exe (PID: 3472)
- chrome.exe (PID: 2088)
- chrome.exe (PID: 3932)
- chrome.exe (PID: 2280)
- chrome.exe (PID: 3924)
- chrome.exe (PID: 732)
- chrome.exe (PID: 2072)
- chrome.exe (PID: 1964)
- chrome.exe (PID: 2748)
- chrome.exe (PID: 1280)
- chrome.exe (PID: 3460)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 2408)
- chrome.exe (PID: 3132)
- chrome.exe (PID: 3380)
- chrome.exe (PID: 472)
- chrome.exe (PID: 3308)
- chrome.exe (PID: 3832)
- chrome.exe (PID: 2108)
- chrome.exe (PID: 3776)
- chrome.exe (PID: 392)
- chrome.exe (PID: 2828)
- chrome.exe (PID: 980)
- chrome.exe (PID: 3888)
- chrome.exe (PID: 648)
- chrome.exe (PID: 536)
- chrome.exe (PID: 3820)
- chrome.exe (PID: 1156)
- chrome.exe (PID: 2644)
- chrome.exe (PID: 4048)
- chrome.exe (PID: 3024)
- chrome.exe (PID: 3784)
- chrome.exe (PID: 3788)
- chrome.exe (PID: 4088)
- chrome.exe (PID: 1136)
- chrome.exe (PID: 1204)
- chrome.exe (PID: 2532)
- chrome.exe (PID: 1040)
- chrome.exe (PID: 288)
- chrome.exe (PID: 1020)
- chrome.exe (PID: 336)
- chrome.exe (PID: 2596)
- chrome.exe (PID: 3972)
- chrome.exe (PID: 1280)
- chrome.exe (PID: 2472)
- chrome.exe (PID: 2800)
- chrome.exe (PID: 440)
- chrome.exe (PID: 3832)
- chrome.exe (PID: 1900)
- chrome.exe (PID: 2544)
- chrome.exe (PID: 4036)
- chrome.exe (PID: 2140)
- chrome.exe (PID: 2340)
- chrome.exe (PID: 3660)
- chrome.exe (PID: 2320)
- chrome.exe (PID: 3260)
- chrome.exe (PID: 2932)
- chrome.exe (PID: 3596)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 2384)
- chrome.exe (PID: 720)
- chrome.exe (PID: 2912)
- msiexec.exe (PID: 3840)
- chrome.exe (PID: 2052)
- msiexec.exe (PID: 2440)
- find.exe (PID: 616)
- sc.exe (PID: 3872)
- sc.exe (PID: 588)
- find.exe (PID: 3560)
- sc.exe (PID: 2596)
- find.exe (PID: 3460)
- sc.exe (PID: 3032)
- find.exe (PID: 1244)
- chrome.exe (PID: 3364)
- timeout.exe (PID: 4076)
- chrome.exe (PID: 2404)
- sc.exe (PID: 3832)
- sc.exe (PID: 2376)
- sc.exe (PID: 1280)
- regsvr32.exe (PID: 3748)
- regsvr32.exe (PID: 2384)
- sc.exe (PID: 3516)
- regsvr32.exe (PID: 128)
- netsh.exe (PID: 2608)
- chrome.exe (PID: 3504)
- timeout.exe (PID: 3016)
Reads settings of System Certificates
- chrome.exe (PID: 2988)
- chrome.exe (PID: 1340)
- msiexec.exe (PID: 3840)
- msiexec.exe (PID: 2440)
- SushiePower.tmp (PID: 880)
- saBSI.exe (PID: 3996)
- installer.exe (PID: 2588)
- pcapd.exe (PID: 1428)
- assistant.tmp (PID: 3268)
- ServiceHost.exe (PID: 2752)
- UIHost.exe (PID: 1096)
- rlvknlg.exe (PID: 4092)
- updater.exe (PID: 2768)
Reads the date of Windows installation
- chrome.exe (PID: 3820)
Checks Windows Trust Settings
- msiexec.exe (PID: 3840)
- chrome.exe (PID: 1340)
- msiexec.exe (PID: 2440)
- SushiePower.tmp (PID: 880)
- saBSI.exe (PID: 3996)
- installer.exe (PID: 2588)
- pcapd.exe (PID: 1428)
- assistant.tmp (PID: 3268)
- ServiceHost.exe (PID: 2752)
- UIHost.exe (PID: 1096)
- rlvknlg.exe (PID: 4092)
- updater.exe (PID: 2768)
Dropped object may contain Bitcoin addresses
- installer.exe (PID: 4028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jpg | | | JFIF-EXIF JPEG Bitmap (55.5) |
|---|---|---|
| .jpg | | | JPEG bitmap (33.3) |
| .mp3 | | | MP3 audio (11.1) |
EXIF
Composite
| Megapixels: | 1.5 |
|---|---|
| ImageSize: | 864x1738 |
Total processes
215
Monitored processes
151
Malicious processes
14
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | "C:\Windows\system32\regsvr32.exe" /s "C:\Program Files\McAfee\WebAdvisor\win32\IEPlugin.dll" | C:\Windows\system32\regsvr32.exe | — | ServiceHost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 128 | "C:\Program Files\RelevantKnowledge\rlservice.exe" /service | C:\Program Files\RelevantKnowledge\rlservice.exe | — | services.exe | |||||||||||
User: SYSTEM Company: TMRG, Inc. Integrity Level: SYSTEM Description: Relevant-Knowledge Exit code: 0 Version: 1.1.24.126 (Build 24.126) Modules
| |||||||||||||||
| 288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,4928621000112584194,2859277031420024529,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=56 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4080 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1060,4928621000112584194,2859277031420024529,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1896 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1060,4928621000112584194,2859277031420024529,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4188 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 440 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,4928621000112584194,2859277031420024529,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=73 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3292 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 472 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,4928621000112584194,2859277031420024529,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=36 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2812 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1060,4928621000112584194,2859277031420024529,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=48 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3712 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
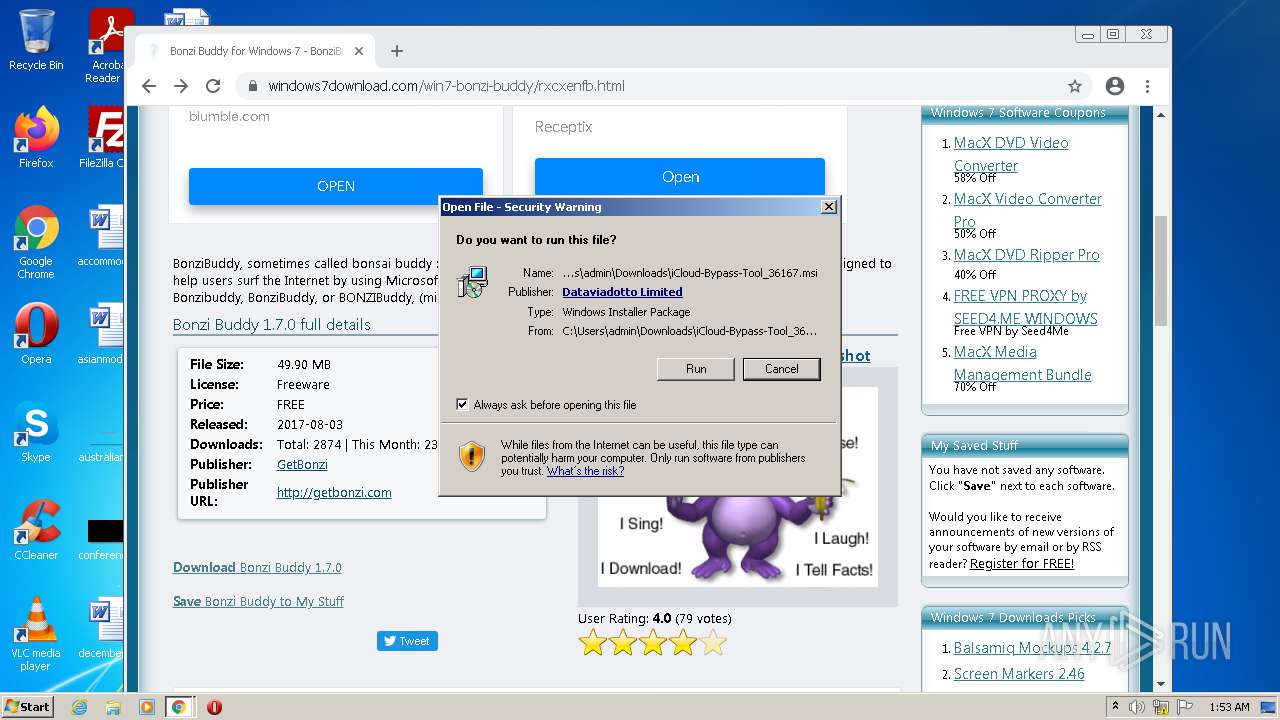
| 572 | "C:\Users\admin\AppData\Local\SushiSetupkf\SushiSetup.exe" /elv C:\Users\admin\Downloads\iCloud-Bypass-Tool_36167.msi | C:\Users\admin\AppData\Local\SushiSetupkf\SushiSetup.exe | SushiSetup.exe | ||||||||||||
User: admin Company: Sushi Power Setup Integrity Level: HIGH Description: Sushi Power Setup Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
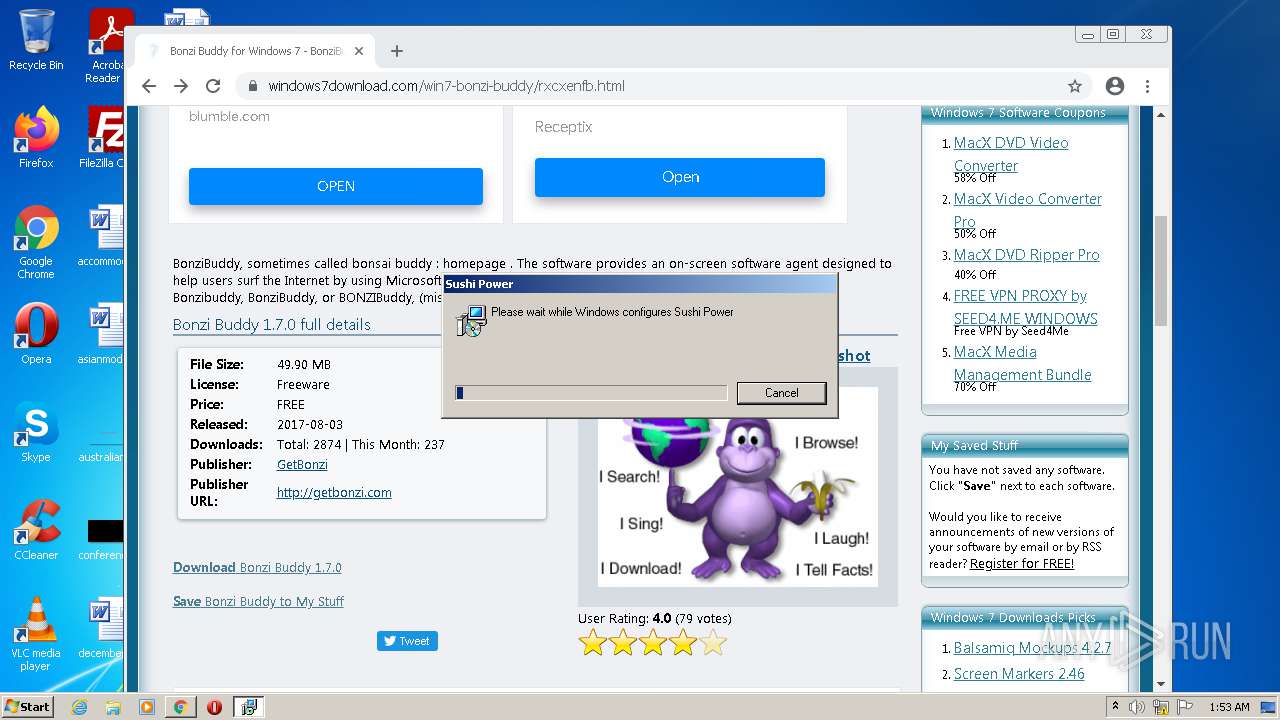
| 572 | "C:\Users\admin\AppData\Local\Temp\1WCS5Gqb\partners\response_obey.tmp" -c:860 -t:IT_InstaWorks_DDMP_PP | C:\Users\admin\AppData\Local\Temp\1WCS5Gqb\partners\response_obey.tmp | RFileStpOn.tmp | ||||||||||||
User: admin Company: TMRG, INC. Integrity Level: HIGH Description: Relevant-Knowledge Installer Exit code: 0 Version: 1.0.5.6 (Build 6) Modules
| |||||||||||||||
Total events
100 599
Read events
99 685
Write events
879
Delete events
35
Modification events
| (PID) Process: | (3648) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: rundll32.exe | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1340) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
50
Suspicious files
327
Text files
1 266
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-60F8C139-53C.pma | — | |
MD5:— | SHA256:— | |||
| 2988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\index | binary | |
MD5:— | SHA256:— | |||
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\c5e35cfa-a981-44e5-9a82-02cd3b65a2cf.tmp | text | |
MD5:— | SHA256:— | |||
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF3712f0.TMP | text | |
MD5:936EB7280DA791E6DD28EF3A9B46D39C | SHA256:CBAF2AFD831B32F6D1C12337EE5D2F090D6AE1F4DCB40B08BEF49BF52AD9721F | |||
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:5BD3C311F2136A7A88D3E197E55CF902 | SHA256:FA331915E1797E59979A3E4BCC2BD0D3DEAA039B94D4DB992BE251FD02A224B9 | |||
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:8FF312A95D60ED89857FEB720D80D4E1 | SHA256:946A57FAFDD28C3164D5AB8AB4971B21BD5EC5BFFF7554DBF832CB58CC37700B | |||
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old~RF3713bb.TMP | text | |
MD5:109A25C32EE1132ECD6D9F3ED9ADF01A | SHA256:DA6028DB9485C65E683643658326F02B1D0A1566DE14914EF28E5248EB94F0DD | |||
| 2988 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\data_2 | vxd | |
MD5:0962291D6D367570BEE5454721C17E11 | SHA256:EC1702806F4CC7C42A82FC2B38E89835FDE7C64BB32060E0823C9077CA92EFB7 | |||
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:00046F773EFDD3C8F8F6D0F87A2B93DC | SHA256:593EDE11D17AF7F016828068BCA2E93CF240417563FB06DC8A579110AEF81731 | |||
| 1340 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:7721CDA9F5B73CE8A135471EB53B4E0E | SHA256:DD730C576766A46FFC84E682123248ECE1FF1887EC0ACAB22A5CE93A450F4500 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
82
TCP/UDP connections
180
DNS requests
107
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
904 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTQ3QUFYQzF5VF9DcWNsa0ZkMGdTQmdvQQ/1.0.0.8_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
904 | svchost.exe | HEAD | 200 | 74.125.8.137:80 | http://r3---sn-5hnednlk.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTQ3QUFYQzF5VF9DcWNsa0ZkMGdTQmdvQQ/1.0.0.8_llkgjffcdpffmhiakmfcdcblohccpfmo.crx?cms_redirect=yes&mh=Yu&mip=85.203.44.65&mm=28&mn=sn-5hnednlk&ms=nvh&mt=1626914905&mv=m&mvi=3&pl=25&shardbypass=yes&smhost=r3---sn-5hnekn7z.gvt1.com | US | — | — | whitelisted |
904 | svchost.exe | HEAD | 403 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | — | — | whitelisted |
904 | svchost.exe | HEAD | 302 | 142.250.186.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTQ3QUFYQzF5VF9DcWNsa0ZkMGdTQmdvQQ/1.0.0.8_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
904 | svchost.exe | HEAD | 200 | 74.125.8.72:80 | http://r3---sn-5hneknee.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw?cms_redirect=yes&mh=LV&mip=85.203.44.65&mm=28&mn=sn-5hneknee&ms=nvh&mt=1626914905&mv=m&mvi=3&pl=25&rmhost=r1---sn-5hneknee.gvt1.com&shardbypass=yes | US | — | — | whitelisted |
2988 | chrome.exe | GET | 302 | 142.250.186.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 592 b | whitelisted |
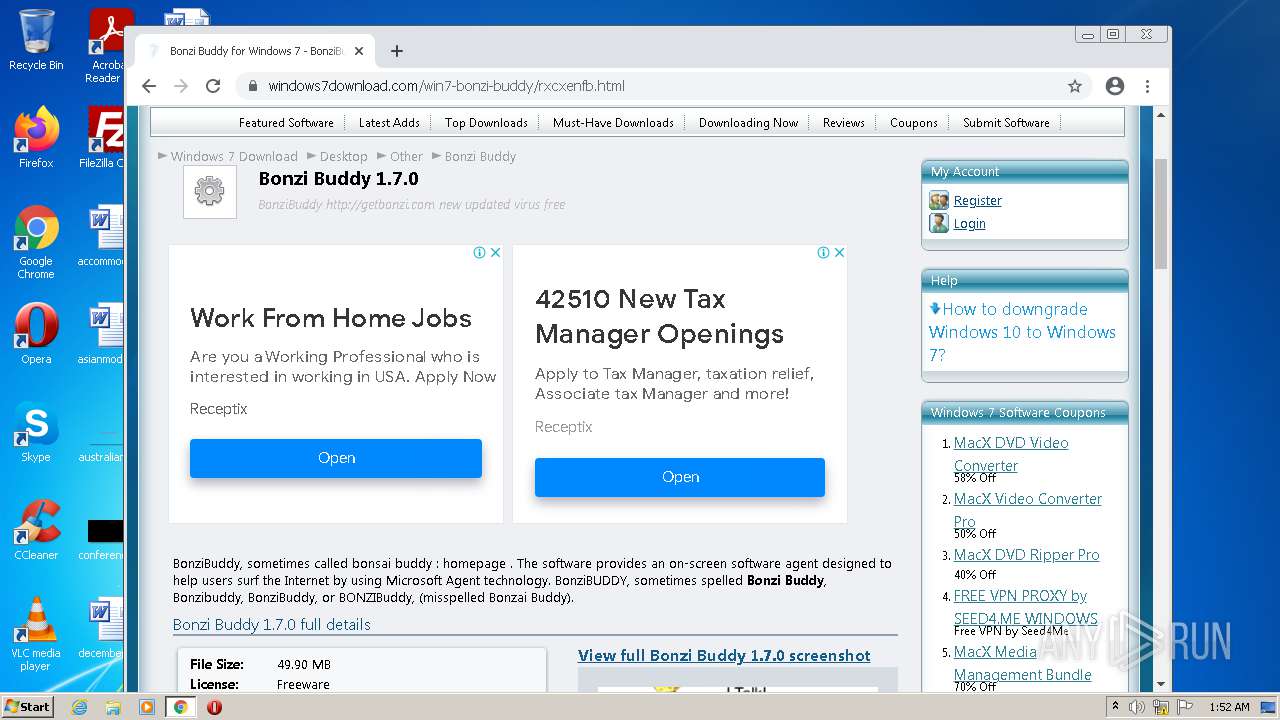
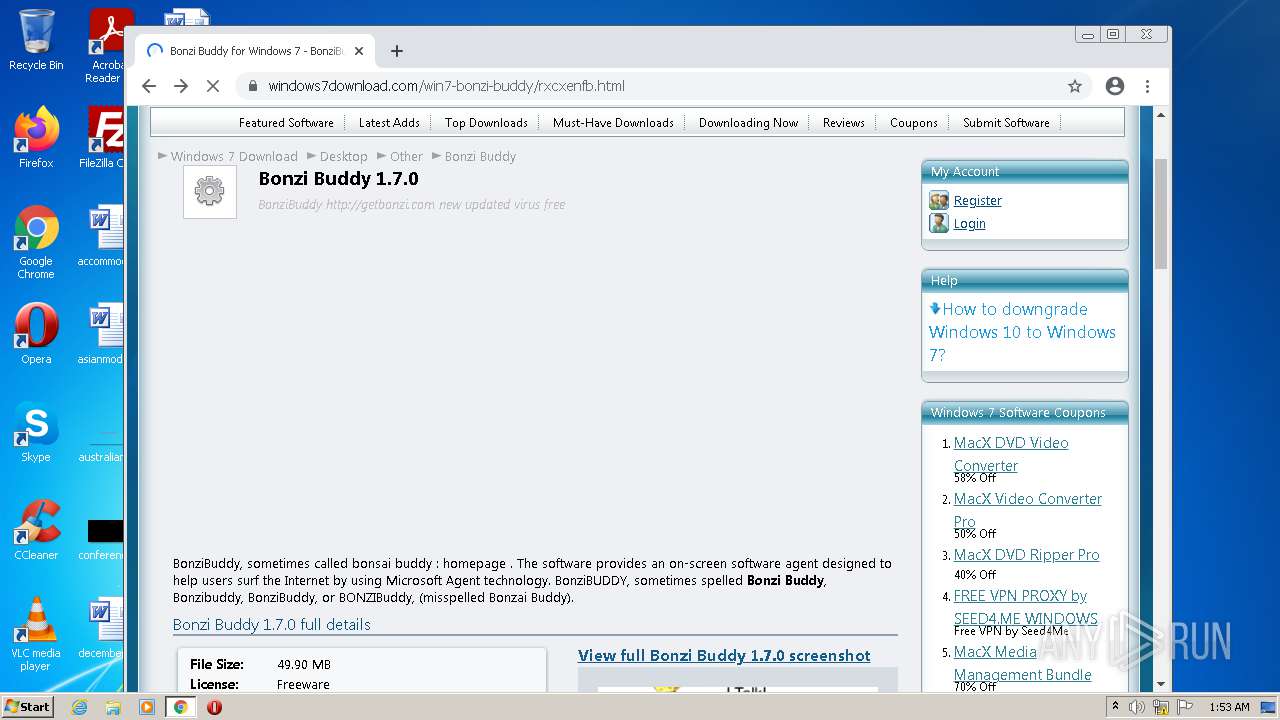
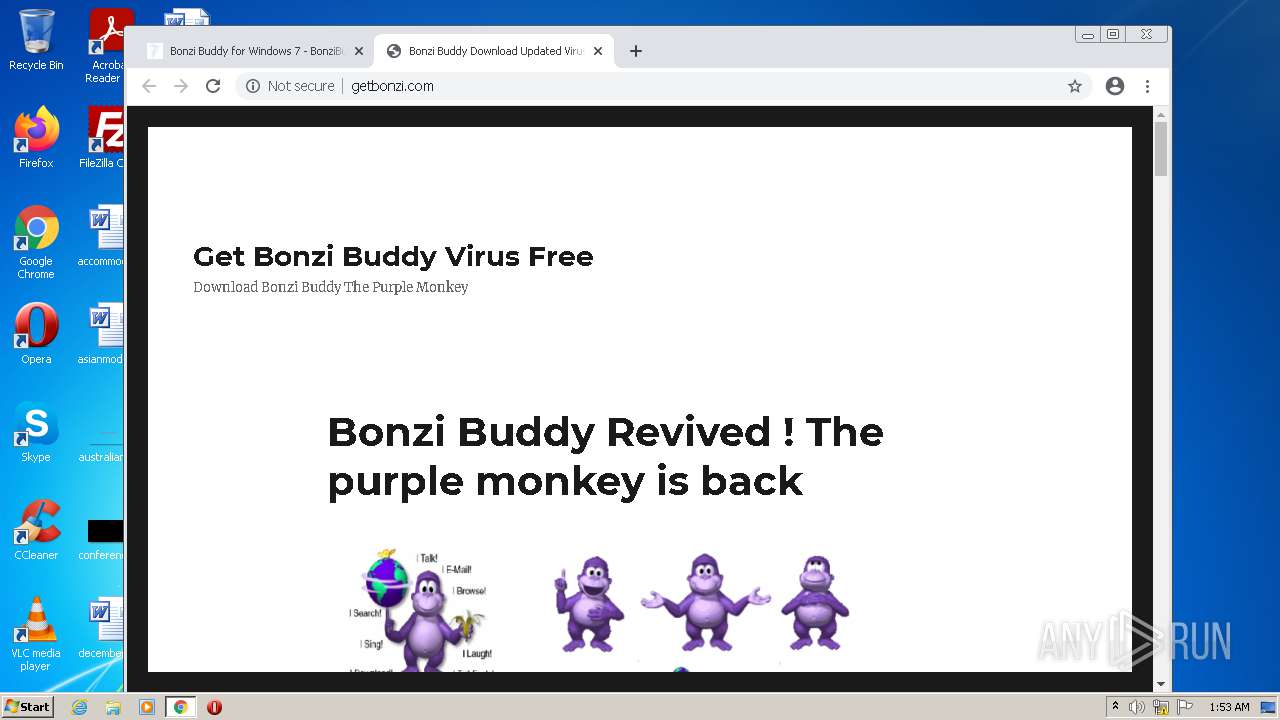
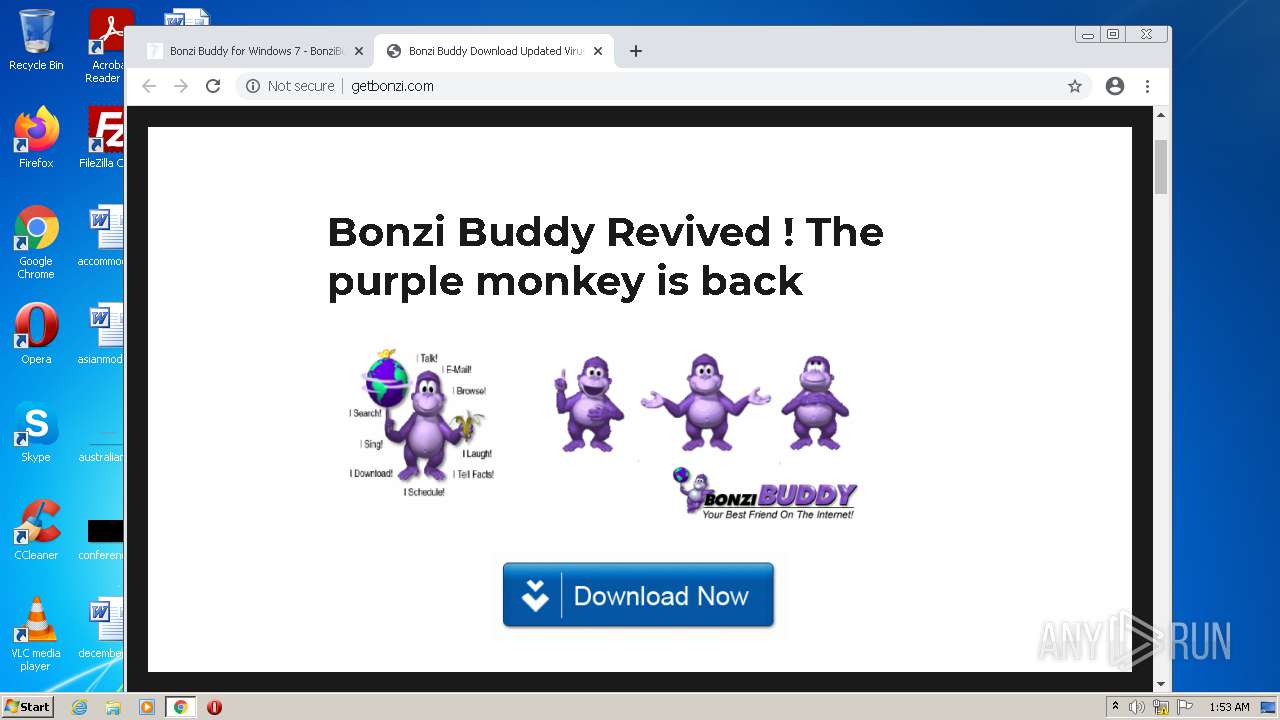
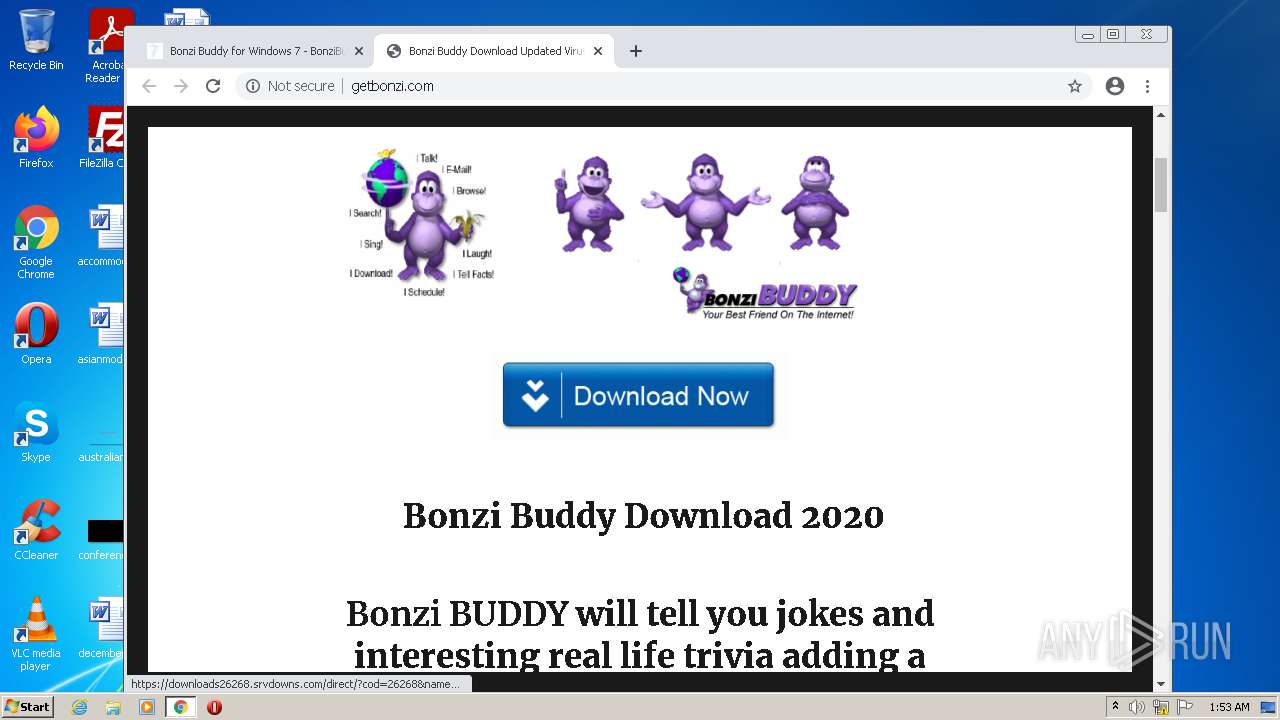
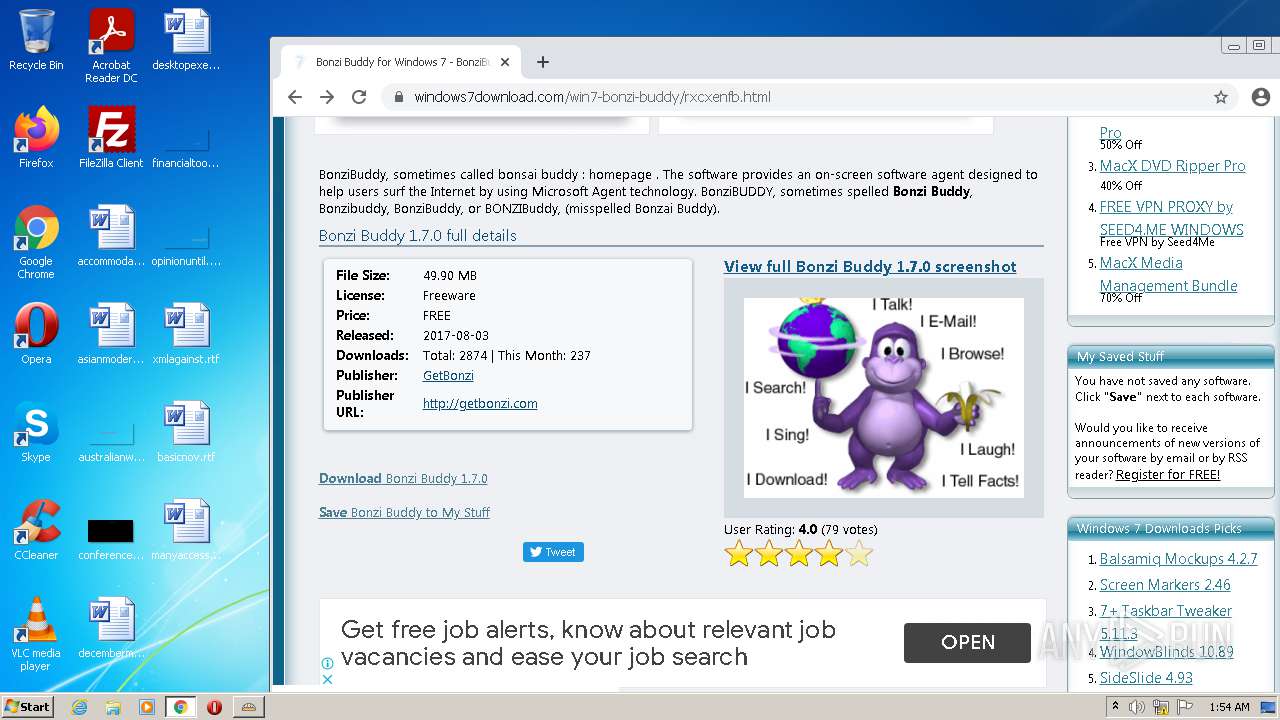
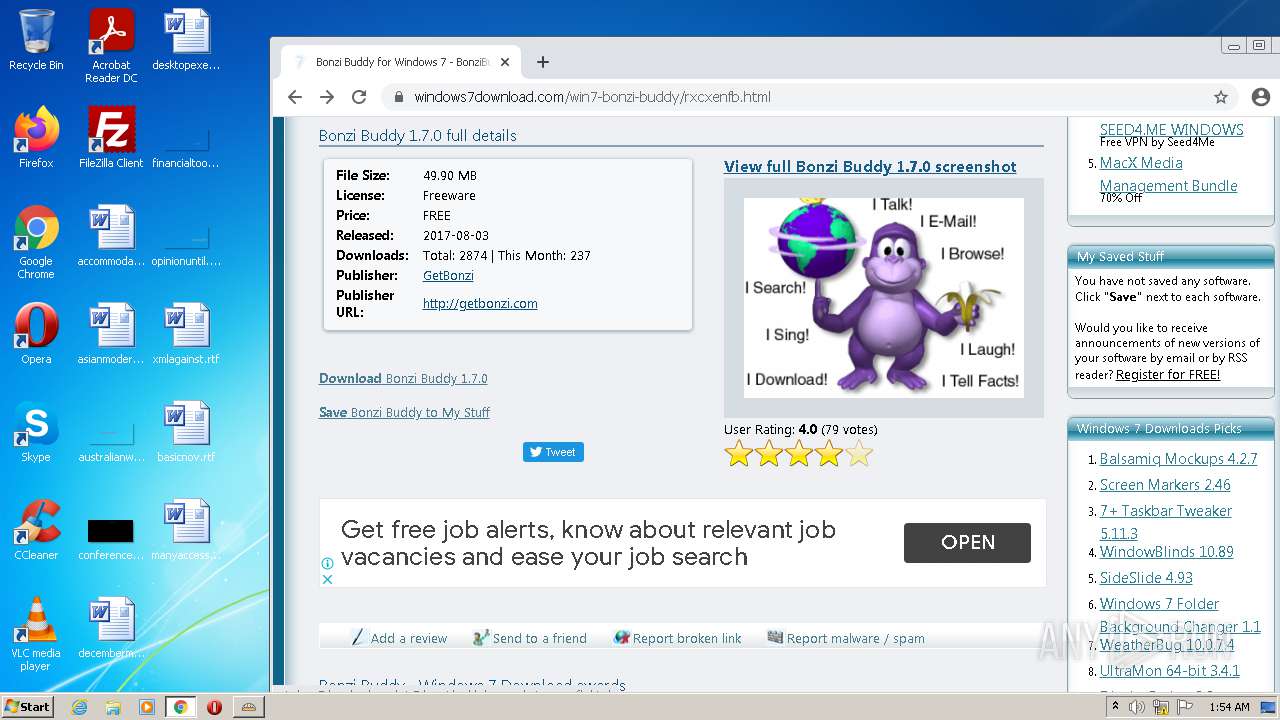
2988 | chrome.exe | GET | 200 | 142.11.237.167:80 | http://getbonzi.com/wp-content/uploads/2017/01/bonzi-buddy-1.png | US | image | 82.0 Kb | malicious |
2988 | chrome.exe | GET | 200 | 142.11.237.167:80 | http://getbonzi.com/ | US | html | 18.2 Kb | malicious |
904 | svchost.exe | GET | 302 | 142.250.186.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYTQ3QUFYQzF5VF9DcWNsa0ZkMGdTQmdvQQ/1.0.0.8_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | html | 555 b | whitelisted |
904 | svchost.exe | GET | 302 | 142.250.186.174:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | html | 503 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2988 | chrome.exe | 34.104.35.123:80 | edgedl.me.gvt1.com | — | US | whitelisted |
2988 | chrome.exe | 142.250.186.174:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
2988 | chrome.exe | 74.125.100.139:80 | r5---sn-5hnedn7e.gvt1.com | Google Inc. | US | whitelisted |
2988 | chrome.exe | 142.250.185.173:443 | accounts.google.com | Google Inc. | US | suspicious |
2988 | chrome.exe | 142.250.184.228:443 | www.google.com | Google Inc. | US | whitelisted |
2988 | chrome.exe | 142.250.184.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
— | — | 142.250.184.228:443 | www.google.com | Google Inc. | US | whitelisted |
2988 | chrome.exe | 142.250.74.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2988 | chrome.exe | 142.250.185.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2988 | chrome.exe | 142.250.185.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
880 | SushiePower.tmp | Potentially Bad Traffic | ET USER_AGENTS Observed Suspicious UA (NSIS_Inetc (Mozilla)) |
Process | Message |
|---|---|
saBSI.exe | NotComDllGetInterface: DLL not found in install location, looking in current directory |
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NotComDllGetInterface: DLL not found in install location, looking in current directory |
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
saBSI.exe | NotComDllGetInterface: DLL not found in install location, looking in current directory |
saBSI.exe | NotComDllGetInterface: C:\Users\admin\AppData\Local\Temp\saBSI.exe loading C:\Users\admin\AppData\Local\Temp\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
installer.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|
installer.exe | NCPrivateLoadAndValidateMPTDll: Looking in EXE directory
|
installer.exe | NotComDllGetInterface: C:\Program Files\McAfee\Temp2046851566\installer.exe loading C:\Program Files\McAfee\Temp2046851566\mfeaaca.dll, WinVerifyTrust failed with 80092003
|
installer.exe | NCPrivateLoadAndValidateMPTDll: Looking in current directory
|