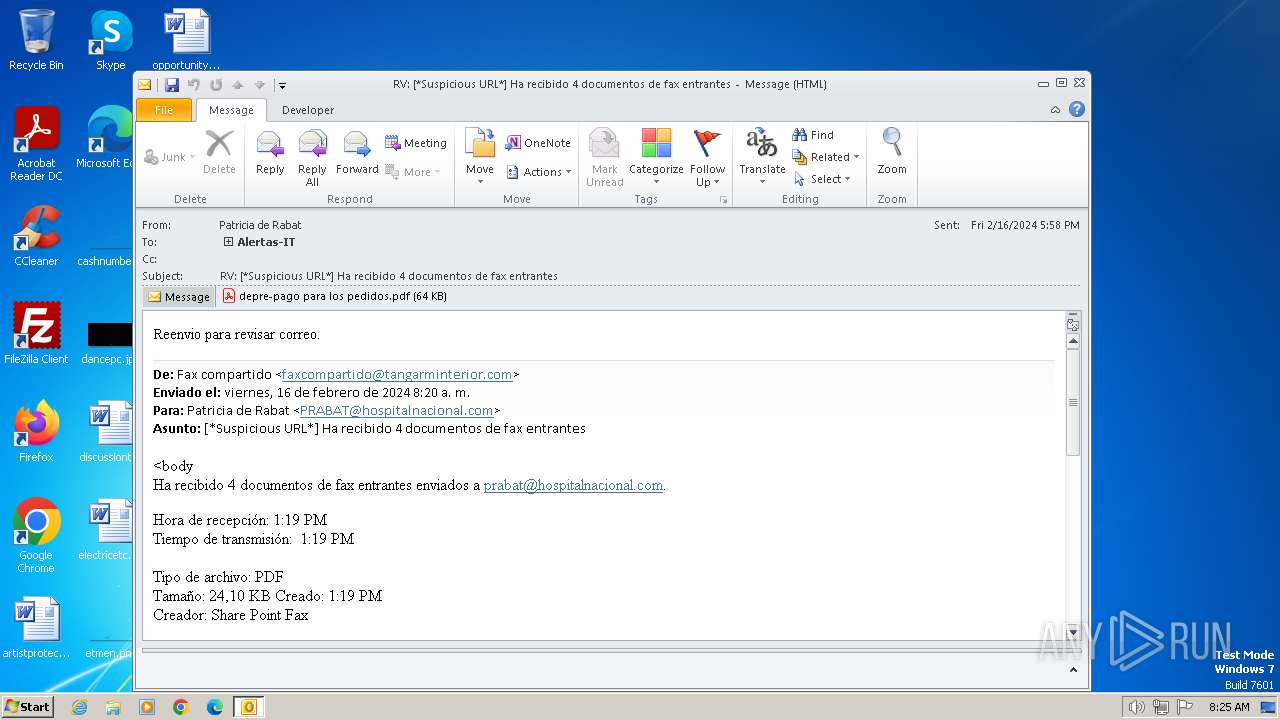
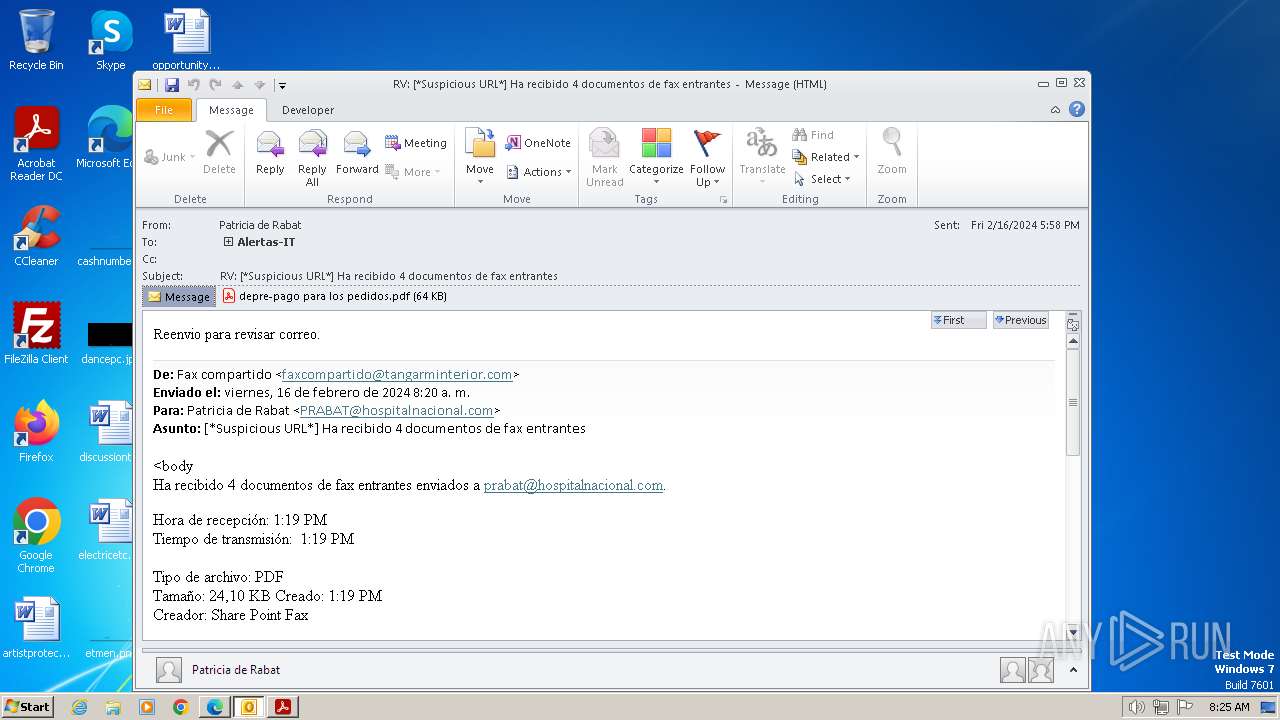
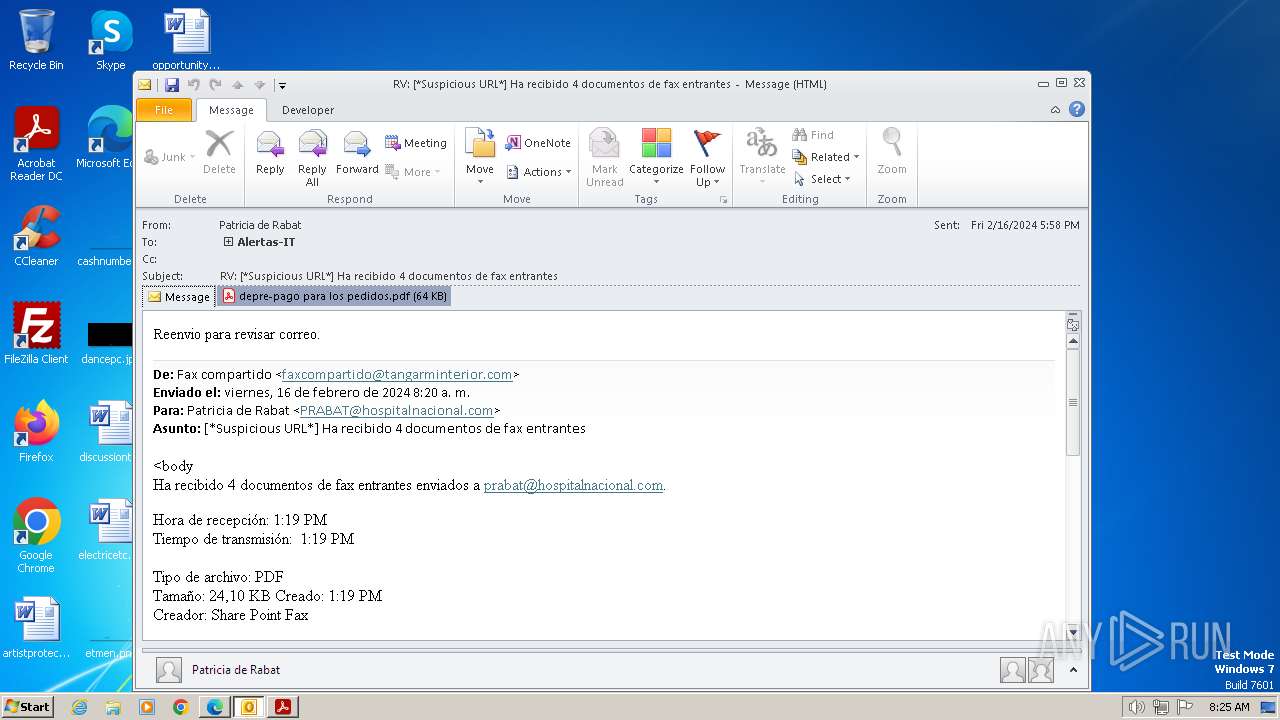
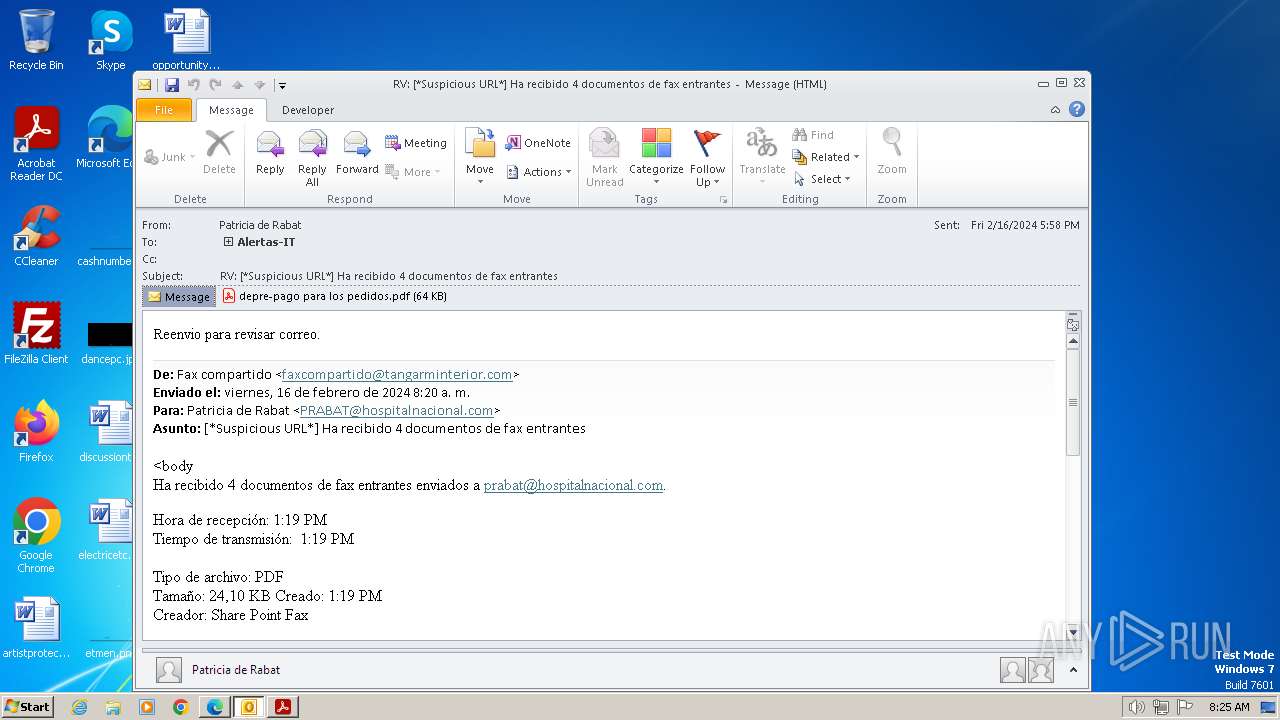
| File name: | RV_ __Suspicious URL__ Ha recibido 4 documentos de fax entrantes.msg |
| Full analysis: | https://app.any.run/tasks/55796d9e-c39b-44ef-80a5-564801eb4871 |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2024, 08:25:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | DE090880AAA9DA328500E1EEE948A67A |
| SHA1: | 3B9C81D414797339DF244A587338F60DC64DAF52 |
| SHA256: | 149E18234AC49E942A095DC1FFA70EEBA7D8196BB23B0FBFD15B3FB0A61A1E0B |
| SSDEEP: | 6144:cIm7w1wggF+4wYRvKIHU9GM/1gR7uMVf:c3DpXHMJuR7PZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3668)
Reads Microsoft Office registry keys
- AcroRd32.exe (PID: 4044)
Application launched itself
- AcroRd32.exe (PID: 3092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (50.8) |
|---|---|---|
| .oft | | | Outlook Form Template (29.7) |
| .doc | | | Microsoft Word document (old ver.) (13.6) |
Total processes
41
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
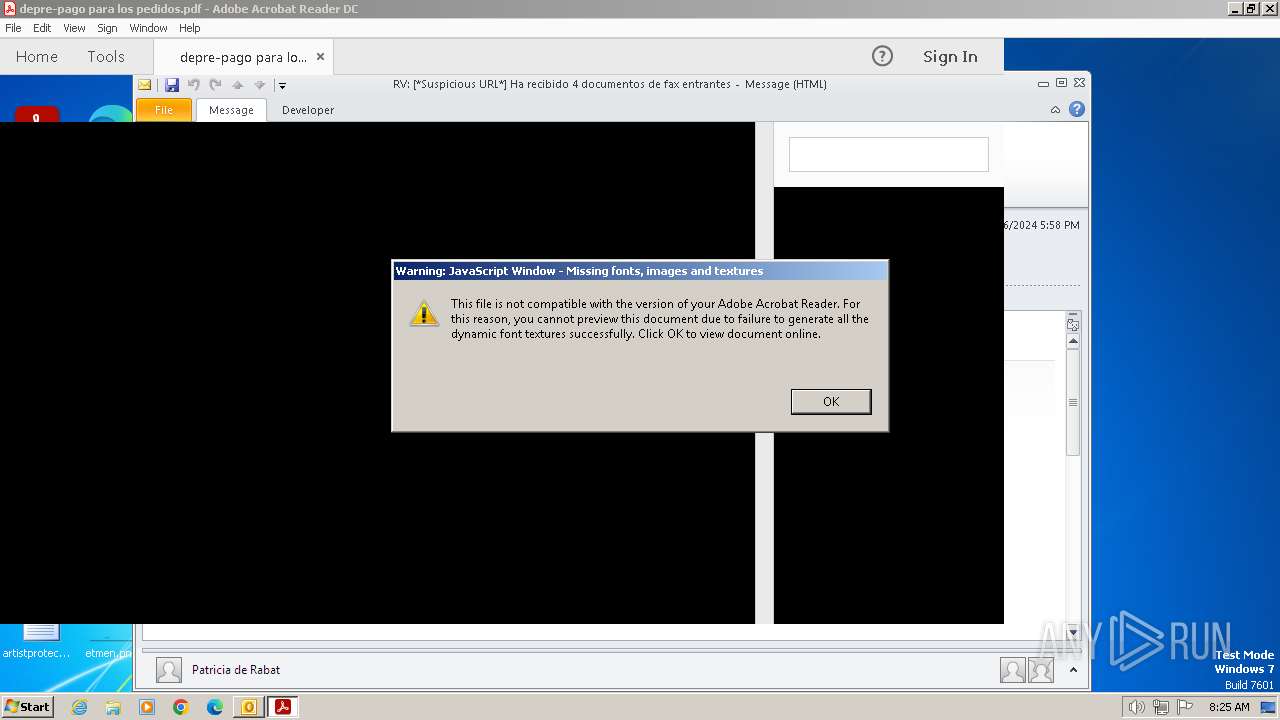
| 3092 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\9ZRCMDG4\depre-pago para los pedidos.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3668 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\RV_ __Suspicious URL__ Ha recibido 4 documentos de fax entrantes.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 4044 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\9ZRCMDG4\depre-pago para los pedidos.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
11 841
Read events
10 908
Write events
900
Delete events
33
Modification events
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3668) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
3
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRED5D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3668 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:D55C2E067BF87DC4498C25A4C391A9E1 | SHA256:C940284436F450D2EDC7A919010C4F916B4B780202E0C1897C0EB42424D7A9A3 | |||
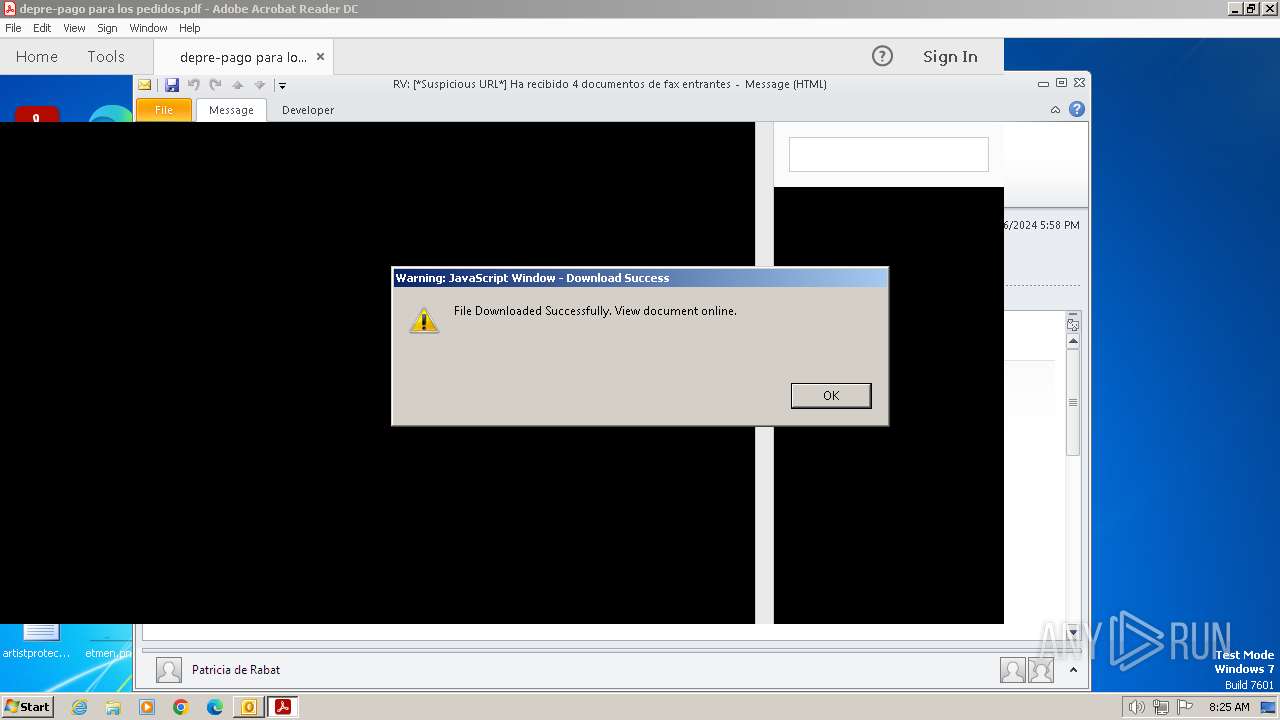
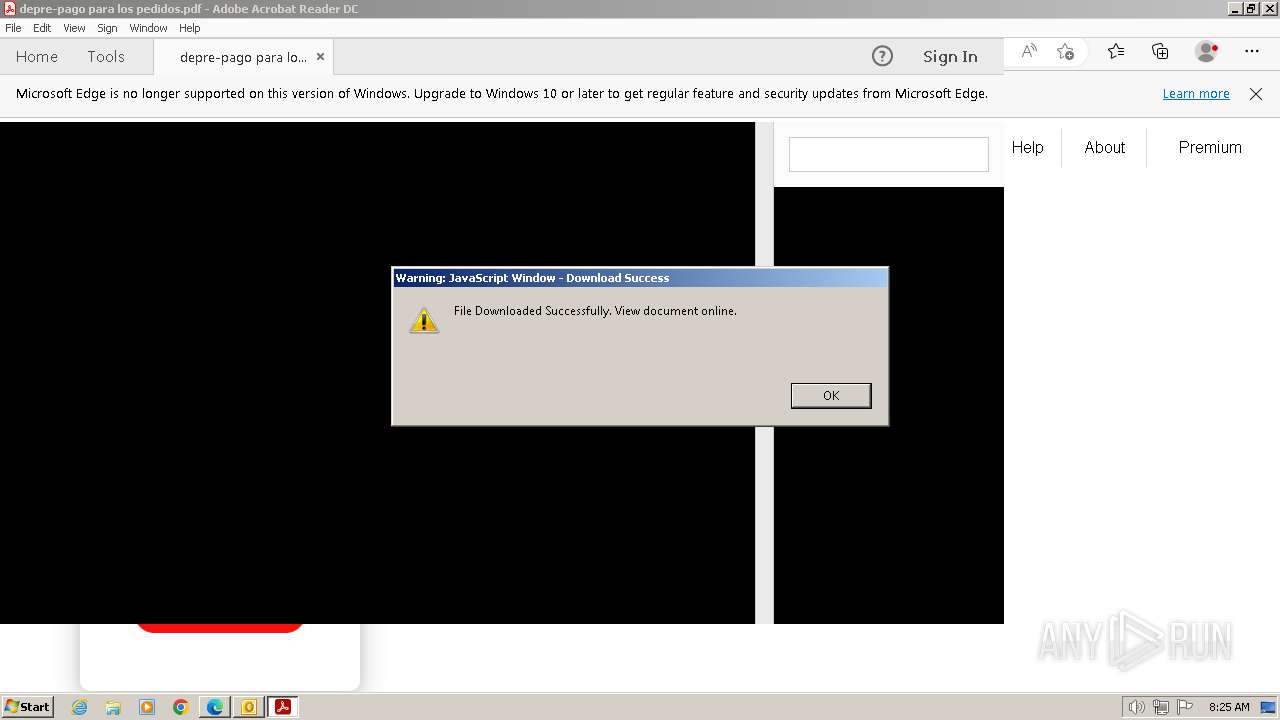
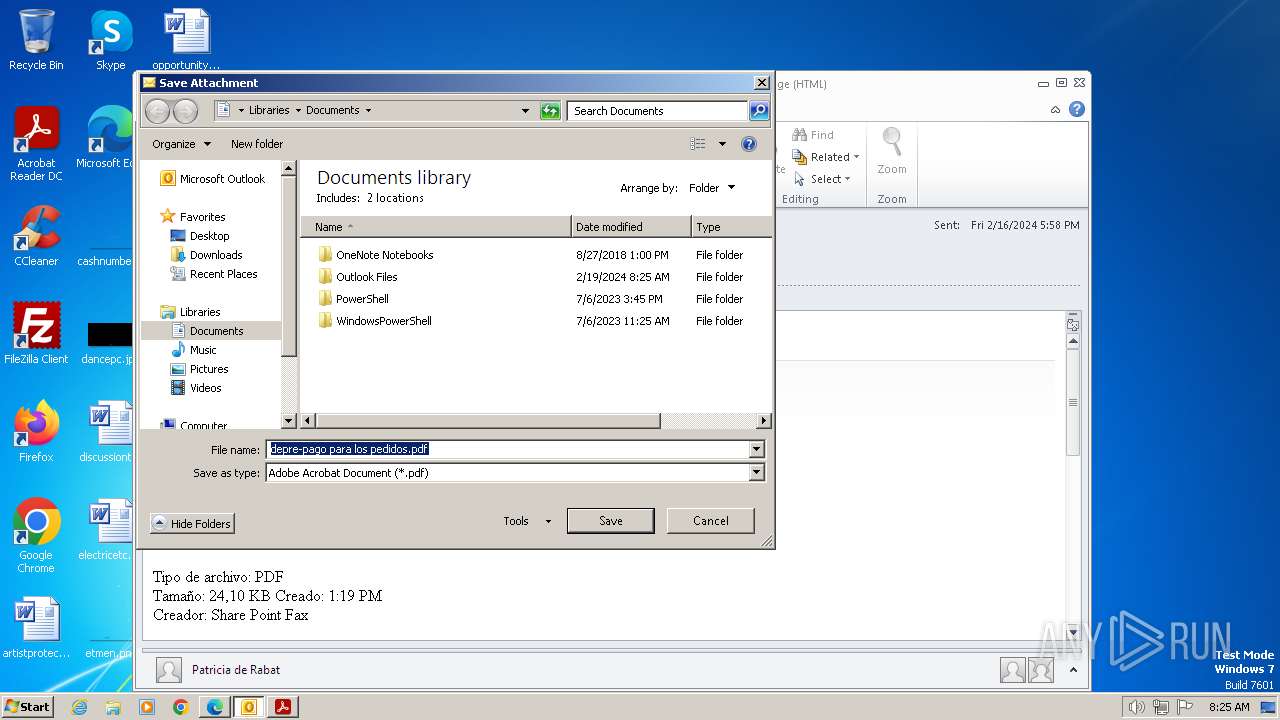
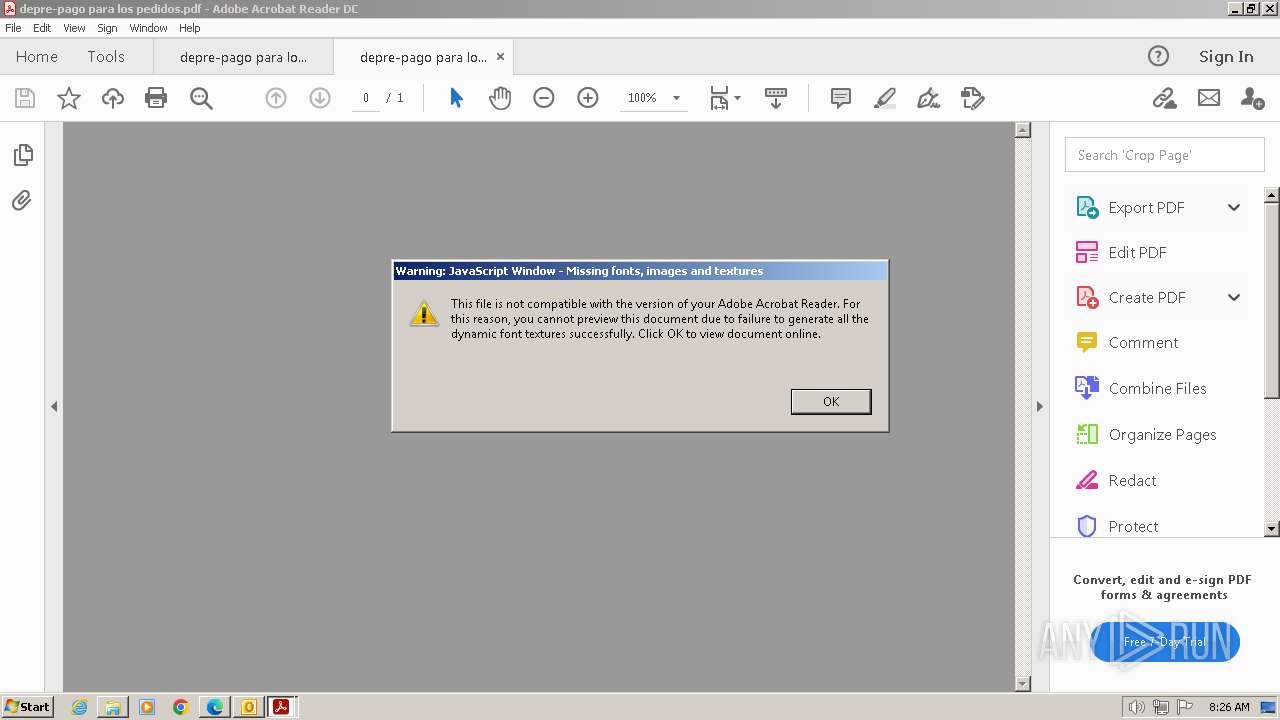
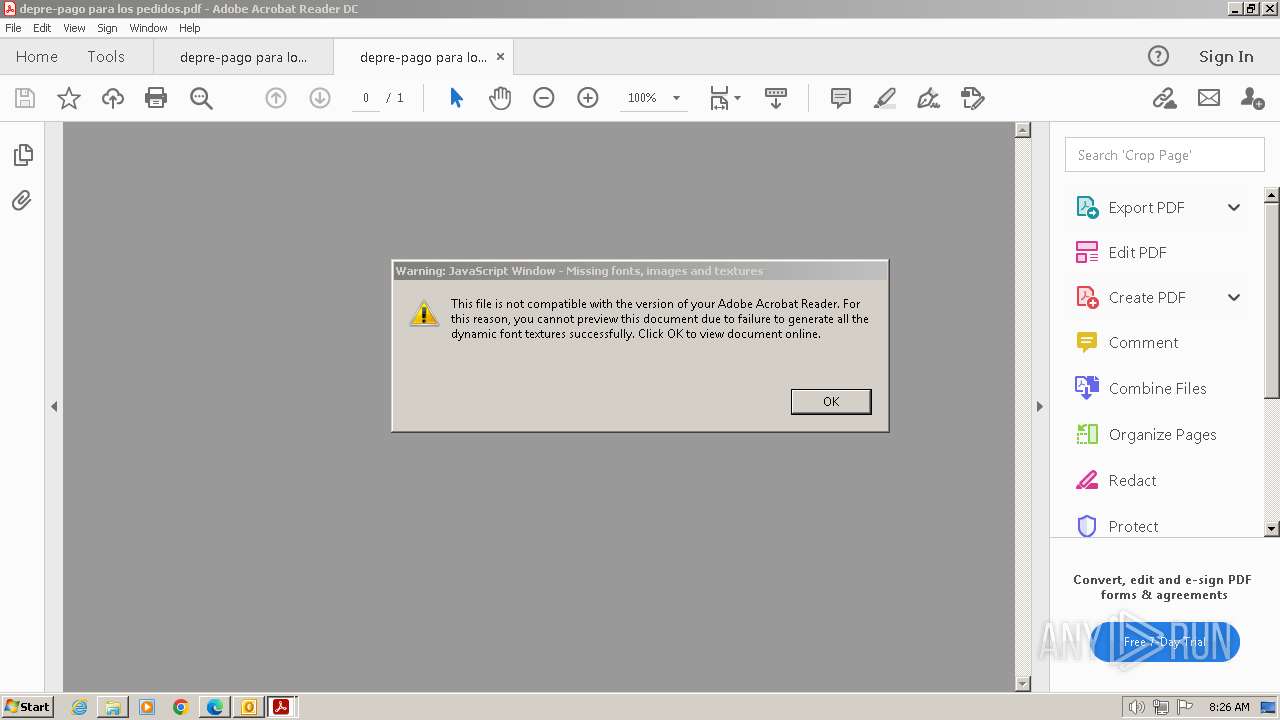
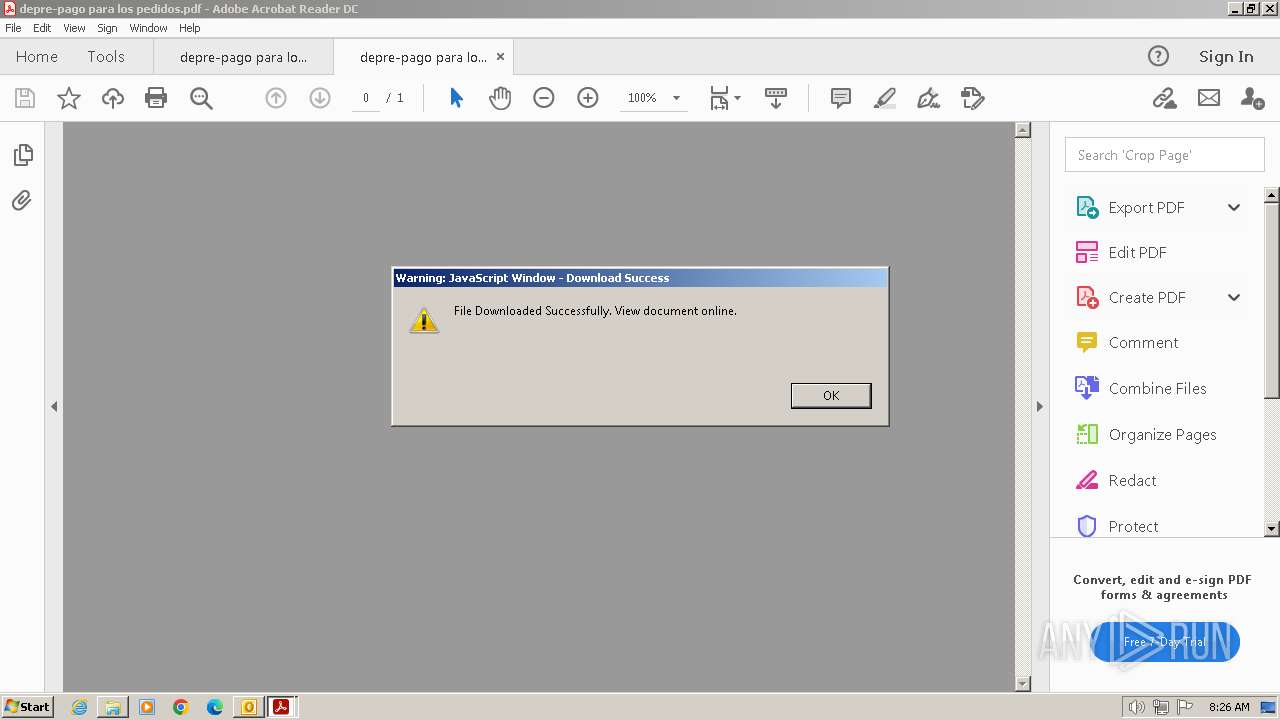
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\9ZRCMDG4\depre-pago para los pedidos.pdf | ||
MD5:E13F0364F602A20C1A71C51D730EA8EE | SHA256:9724CDA107D3F0A4CE222242198FFDD6CE72A202DF117B1CEB4CC9D5338F4D21 | |||
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\9ZRCMDG4\depre-pago para los pedidos.pdf:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{87FF8B23-4CF4-4A8E-A109-1347F089A577}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\9ZRCMDG4\depre-pago para los pedidos (2).pdf:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\43CBF357.dat | image | |
MD5:0BCD614EEBAF0A5561060FCD0CCF1249 | SHA256:4C487894BD8427BA6F11A29A5028E654F6CE4B5A9840A7697BB0DD7B77D39AAE | |||
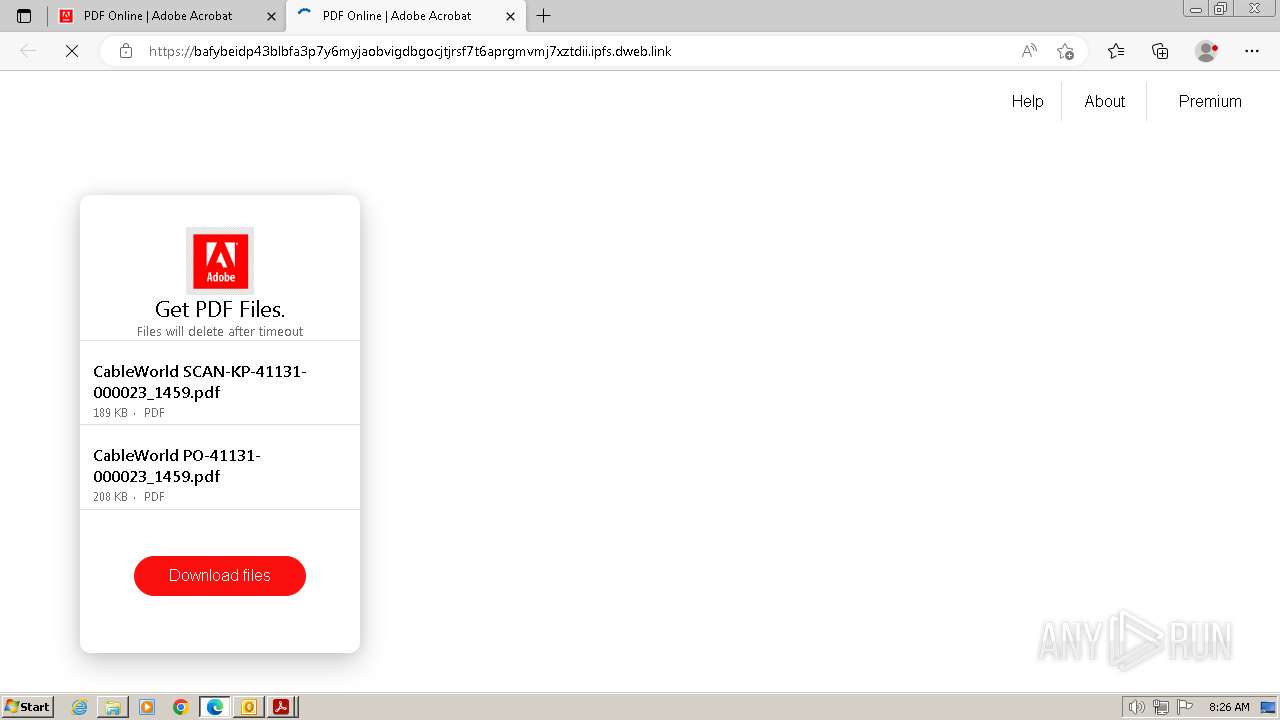
| 3668 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\9ZRCMDG4\depre-pago para los pedidos (2).pdf | ||
MD5:E13F0364F602A20C1A71C51D730EA8EE | SHA256:9724CDA107D3F0A4CE222242198FFDD6CE72A202DF117B1CEB4CC9D5338F4D21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
35
DNS requests
45
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?7a7be0dec4f1d978 | unknown | — | — | unknown |
— | — | GET | 304 | 2.16.100.168:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d9993a3118f4f6b2 | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
— | — | GET | 200 | 88.221.110.91:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e2ddf83a2417bb20 | unknown | compressed | 65.2 Kb | unknown |
— | — | GET | 304 | 88.221.110.91:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fc91d912a85a08d5 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3668 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
— | — | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 3.75.46.157:443 | linkprotect.cudasvc.com | AMAZON-02 | DE | unknown |
— | — | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
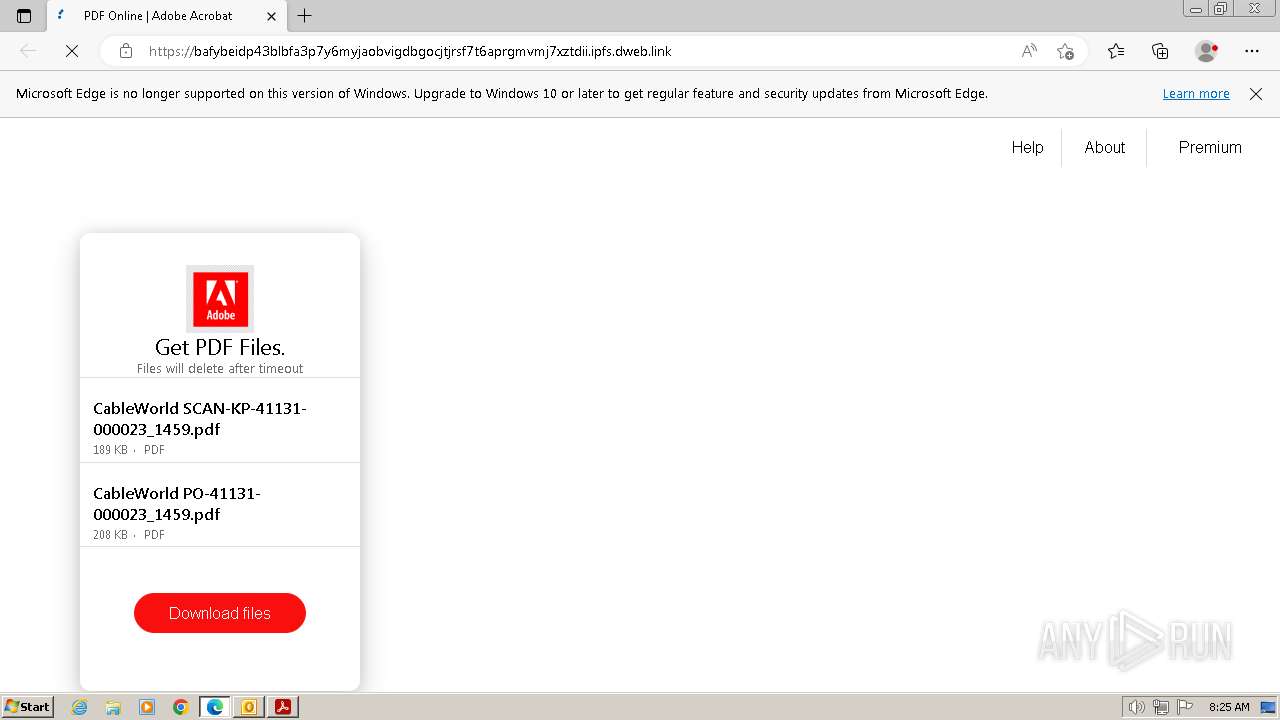
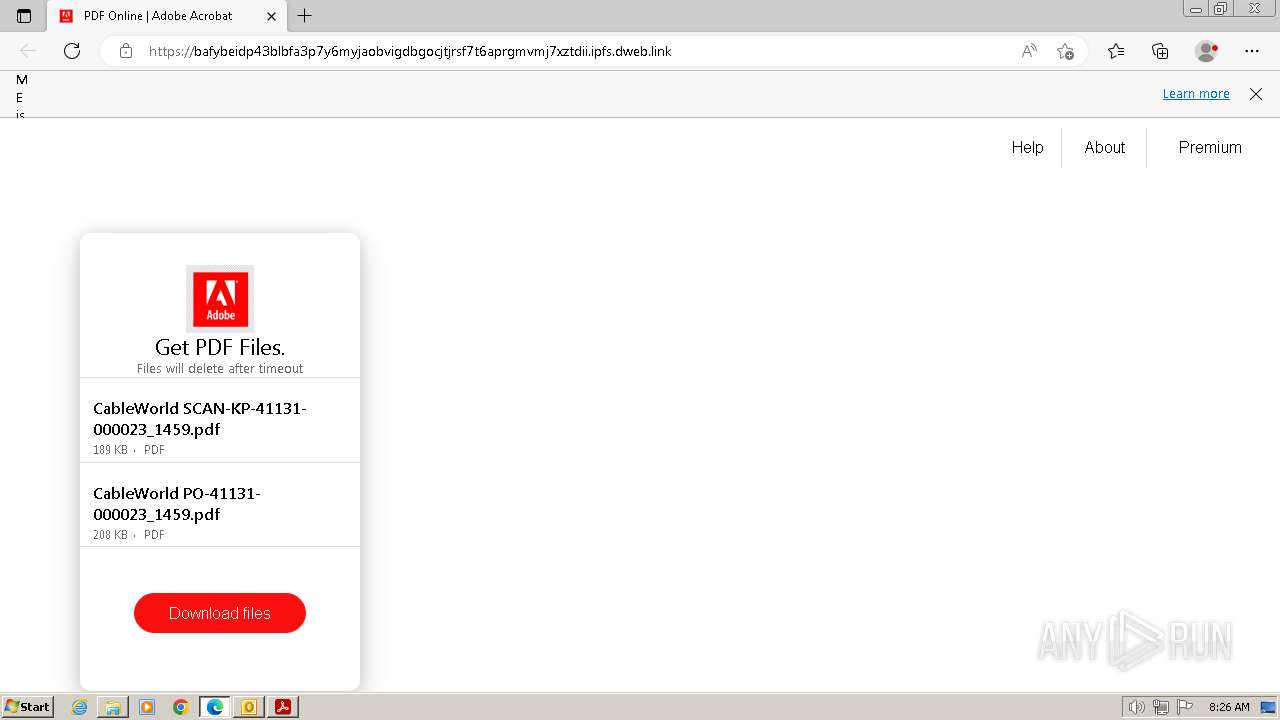
— | — | 209.94.90.1:443 | dweb.link | PROTOCOL | US | unknown |
— | — | 188.114.97.3:443 | c0.klipartz.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
linkprotect.cudasvc.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
dweb.link |
| malicious |
bafybeidp43blbfa3p7y6myjaobvigdbgocjtjrsf7t6aprgmvmj7xztdii.ipfs.dweb.link |
| unknown |
c0.klipartz.com |
| unknown |
code.jquery.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET HUNTING IPFS Gateway Domain in DNS Lookup (ipfs .dweb .link) |
— | — | Misc activity | ET HUNTING IPFS Gateway Domain in DNS Lookup (ipfs .dweb .link) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code.jquery .com) |
— | — | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain chain detected (ipfsquery) |