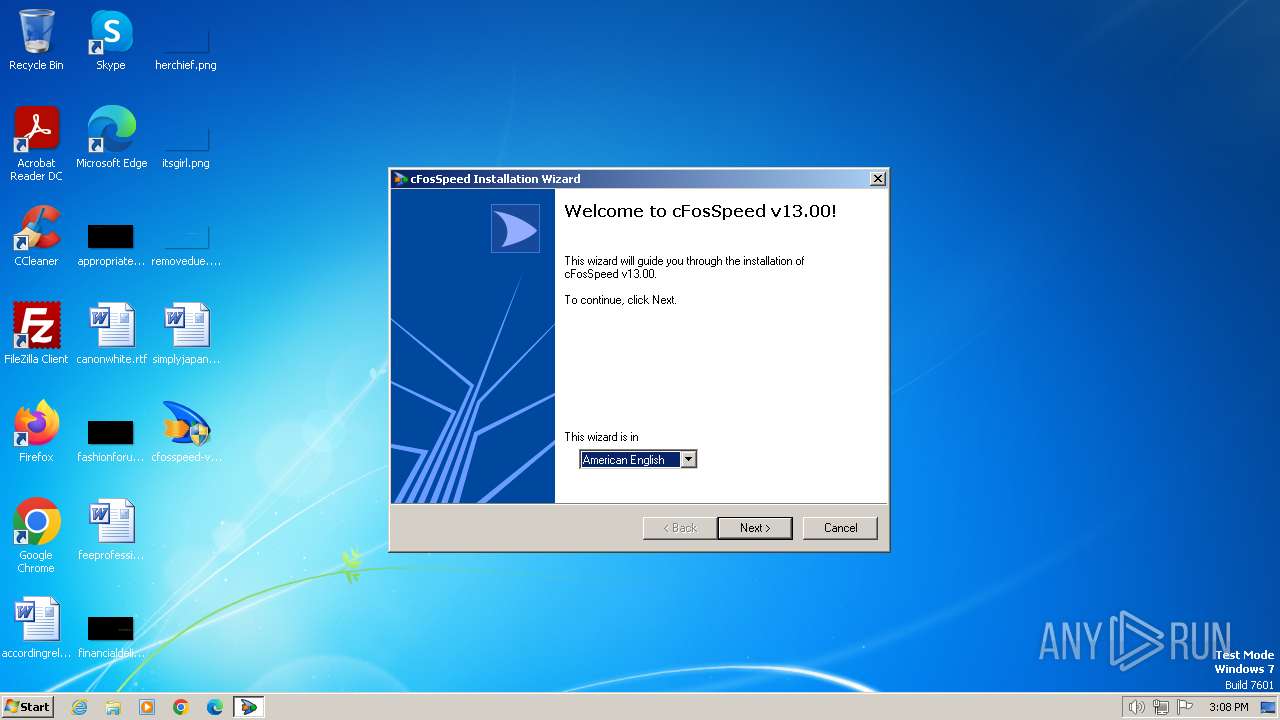
| File name: | cfosspeed-v1300-build3000.exe |
| Full analysis: | https://app.any.run/tasks/6e7d0a32-76a5-4657-9efd-27dfaa61fe8c |
| Verdict: | Malicious activity |
| Analysis date: | February 26, 2024, 15:08:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, InstallShield self-extracting archive |
| MD5: | 1C7C0C9E1B0D3EB69BFB916706E549CA |
| SHA1: | A05B55B4C73436CE1CEDC6C4384CE03A8BACC297 |
| SHA256: | 14907BE46280AEA0162AE96DC841F5321216B2EAD63A88AEE5E0F9C2F98E607F |
| SSDEEP: | 98304:lAfmctp5yQ0LacESM9WbdLiKOy8kbD9/wwqjGmZvwM1ZLJmP4ieOFTvcL/YfxPID:zh4Y8Z7 |
MALICIOUS
Drops the executable file immediately after the start
- cfosspeed-v1300-build3000.exe (PID: 1776)
- setup.exe (PID: 1492)
- drvinst.exe (PID: 2148)
Creates a writable file in the system directory
- drvinst.exe (PID: 2148)
SUSPICIOUS
Executable content was dropped or overwritten
- cfosspeed-v1300-build3000.exe (PID: 1776)
- setup.exe (PID: 1492)
- drvinst.exe (PID: 2148)
Drops a system driver (possible attempt to evade defenses)
- cfosspeed-v1300-build3000.exe (PID: 1776)
- setup.exe (PID: 1492)
- drvinst.exe (PID: 2148)
Reads the Windows owner or organization settings
- setup.exe (PID: 1492)
Suspicious use of NETSH.EXE
- setup.exe (PID: 1492)
Reads the Internet Settings
- setup.exe (PID: 1492)
Creates a software uninstall entry
- setup.exe (PID: 1492)
Adds/modifies Windows certificates
- setup.exe (PID: 1492)
Creates or modifies Windows services
- setup.exe (PID: 1492)
Creates files in the driver directory
- drvinst.exe (PID: 2148)
Checks Windows Trust Settings
- drvinst.exe (PID: 2148)
INFO
Checks supported languages
- cfosspeed-v1300-build3000.exe (PID: 1776)
- setup.exe (PID: 1492)
- drvinst.exe (PID: 2148)
Create files in a temporary directory
- cfosspeed-v1300-build3000.exe (PID: 1776)
- setup.exe (PID: 1492)
Reads the computer name
- setup.exe (PID: 1492)
- drvinst.exe (PID: 2148)
Reads product name
- setup.exe (PID: 1492)
Reads Windows Product ID
- setup.exe (PID: 1492)
Reads the machine GUID from the registry
- setup.exe (PID: 1492)
- drvinst.exe (PID: 2148)
Process checks computer location settings
- setup.exe (PID: 1492)
Reads Environment values
- setup.exe (PID: 1492)
Creates files in the program directory
- setup.exe (PID: 1492)
Reads the software policy settings
- drvinst.exe (PID: 2148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:07 09:43:21+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 56832 |
| InitializedDataSize: | 142336 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27d9 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
Total processes
49
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 10 Global\{549da1df-2a90-20af-83fd-d76b8254782f} Global\{144af8fc-2c7e-6ad0-7555-c92be4acff3c} C:\Windows\System32\DriverStore\Temp\{2a274c41-5cc5-68c6-d8de-5c7d044e3a67}\speed6.inf C:\Windows\System32\DriverStore\Temp\{2a274c41-5cc5-68c6-d8de-5c7d044e3a67}\speed.cat | C:\Windows\System32\rundll32.exe | — | drvinst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | "C:\Users\admin\AppData\Local\Temp\$cfsfx.0\setup.exe" -parentdir:"C:\Users\admin\Desktop\" | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\setup.exe | cfosspeed-v1300-build3000.exe | ||||||||||||
User: admin Company: Atlas Tech Solutions SM PC Integrity Level: HIGH Description: cFosSpeed Installer Exit code: 0 Version: 13.00.3000 Modules
| |||||||||||||||
| 1776 | "C:\Users\admin\Desktop\cfosspeed-v1300-build3000.exe" | C:\Users\admin\Desktop\cfosspeed-v1300-build3000.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2148 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{7e0c4b27-dc93-6564-26b5-6a73a4144862}\speed6.inf" "0" "67da035fb" "000005C8" "WinSta0\Default" "000004B0" "208" "C:\Program Files\cFosSpeed" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2304 | netsh int tcp show global | C:\Windows\System32\netsh.exe | — | setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3700 | "C:\Users\admin\Desktop\cfosspeed-v1300-build3000.exe" | C:\Users\admin\Desktop\cfosspeed-v1300-build3000.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
6 416
Read events
6 290
Write events
122
Delete events
4
Modification events
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-100 |
Value: DHCP Quarantine Enforcement Client | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-101 |
Value: Provides DHCP based enforcement for NAP | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-103 |
Value: 1.0 | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\dhcpqec.dll,-102 |
Value: Microsoft Corporation | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-1 |
Value: IPsec Relying Party | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-2 |
Value: Provides IPsec based enforcement for Network Access Protection | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-4 |
Value: 1.0 | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\napipsec.dll,-3 |
Value: Microsoft Corporation | |||
| (PID) Process: | (2304) netsh.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\tsgqec.dll,-100 |
Value: RD Gateway Quarantine Enforcement Client | |||
Executable files
88
Suspicious files
135
Text files
1 026
Unknown types
400
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\programdata\pub\pingstat_tpl.htm | html | |
MD5:868D01A6F5E2D7B418D547E5FF2F3555 | SHA256:E8DA00EEDB95A942F57D3BF171C301CD43358AED11462E64A4FF106649E627B1 | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\cfosspeedsh.cab | compressed | |
MD5:86E3D7B7240D336F2B32E8025D01F745 | SHA256:9FB380FAB5AD6A016A19E532BE655F74502CC51328D6DC584F5A871185B3289F | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\cfosspeed32.cab | compressed | |
MD5:337DC207C41B61A60E2C2FB78CBC2D78 | SHA256:59612D39BB32919A03303597696C8D154BC61A4B911BA1F863B49D2343A8CB67 | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\programdata\pub\slot_tpl.htm | html | |
MD5:EAFF81F3F5F6B2FF2E688A87E2B7180B | SHA256:FE99CC0A2ECF6A4B5043BF370E53D27B563027BF14F08B226E8AB43419118CBE | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\readme.txt | text | |
MD5:FA973156191A11EE8D83BC354E9B2054 | SHA256:16ADDAEAB3B215489D1B393C0DB80712917E4BB3E2DA71ECE435897AFA69A8CA | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\license_webview2.txt | text | |
MD5:89AC2D3232149F6C00251DE9162FA6E3 | SHA256:0AF8F1B807512AAE39C2AC1AA4D0CAE65CABECB6FD554B8439A5162A0D6ECA55 | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\speedml.txt | text | |
MD5:976DD976CC6BF5A1A7BF011F6AF29D1A | SHA256:75A45A13A9B89E918B8C57BCA162B5B9713FD79440013568301C08DFBD7AFCF8 | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\programdata\pub\priority_tpl.htm | html | |
MD5:A4A32219CD3E1B8ADDBFE6F08EFD41A9 | SHA256:1CC5A5D849D04A8FBE57578DA936D05E79BEBD8D6BEA48635409950CEB0E4264 | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\programdata\pub\spdbudget_tpl.htm | html | |
MD5:7EA6A649CC347A676FBE1922CEB2DB73 | SHA256:F50AE0193EF1631FA780F47468B5111A5A7880A6F24EEAFE602AFA9A2DC4D035 | |||
| 1776 | cfosspeed-v1300-build3000.exe | C:\Users\admin\AppData\Local\Temp\$cfsfx.0\speedml_1337.txt | text | |
MD5:F8FE92EA4662F3E8C89E929579EC8B27 | SHA256:B6665504DAAE9239C9EB4A15A63EA1A55D46E07FEE4F24DB0FE8C1774B7BC1A6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
5
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1492 | setup.exe | GET | — | 95.100.53.90:80 | http://go.microsoft.com/fwlink/p/?LinkId=2124703 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1492 | setup.exe | 95.100.53.90:443 | go.microsoft.com | AKAMAI-AS | CH | unknown |
1492 | setup.exe | 95.100.53.90:80 | go.microsoft.com | AKAMAI-AS | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
atlas-cfosspeed.com |
| unknown |
go.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
setup.exe | file 'C:\Program Files\cFosSpeed\cFosSpeed.ini' open error 3
|
setup.exe | file 'C:\Program Files\cFosSpeed\cFosSpeed.ini' open error 3
|
setup.exe | file 'C:\Program Files\cFosSpeed\cFosSpeed.ini' open error 3
|
setup.exe | file 'C:\Program Files\cFosSpeed\cFosSpeed.ini' open error 3
|
setup.exe | Unable to open device 'CFOSSPEED$D'.
|