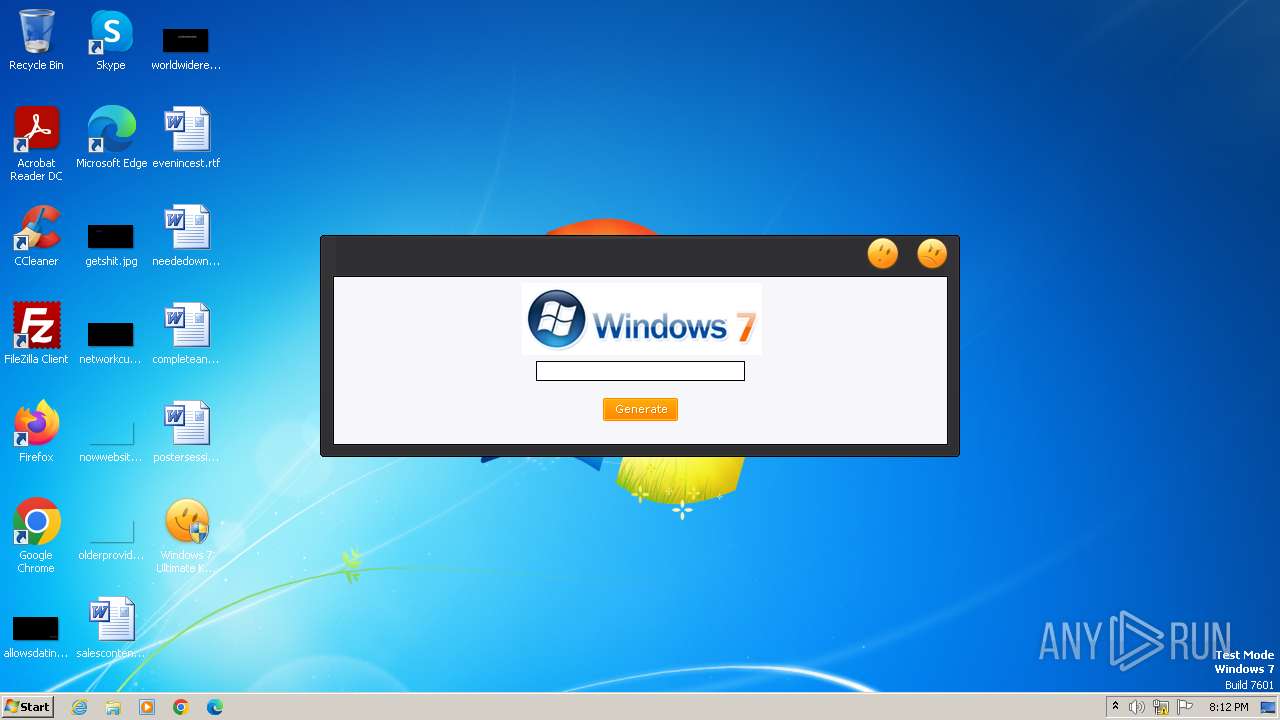
| File name: | Windows 7 Ultimate KEYGEN.exe |
| Full analysis: | https://app.any.run/tasks/2e616bcd-2621-4780-aec2-1c4e0ba3999c |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2023, 20:12:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 3746D013FA415A504B1BFD7ADFF4E123 |
| SHA1: | 6597005F238C22460DF8C3746600F223EA4C7CAD |
| SHA256: | 148F3A96A936F61E25E1A76818058C193B30D70AC38B03465FEAB2ABEDDB4D5D |
| SSDEEP: | 49152:UPQZKAFx4BwLHJDH5SqtcuoivBYx9JgcxtKYzMr5dHjijycOO3MkX79ZfpaB2/vz:UPaKAM0HJDZX3oSBYx9SotFYrbHjiBR7 |
MALICIOUS
UAC/LUA settings modification
- reg.exe (PID: 600)
Drops the executable file immediately after the start
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
Changes firewall settings
- reg.exe (PID: 3936)
SUSPICIOUS
Reads the Internet Settings
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
Starts CMD.EXE for commands execution
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
- winlogon.exe (PID: 1696)
Executing commands from a ".bat" file
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1036)
- cmd.exe (PID: 3112)
- cmd.exe (PID: 3108)
- cmd.exe (PID: 3084)
- cmd.exe (PID: 3200)
- cmd.exe (PID: 3428)
The process creates files with name similar to system file names
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
Process drops legitimate windows executable
- winlogon.exe (PID: 1696)
Starts itself from another location
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
INFO
Reads Environment values
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
- confhost.exe (PID: 240)
Create files in a temporary directory
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
- oVgkx.exe (PID: 1860)
Reads the computer name
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
- oVgkx.exe (PID: 1860)
- confhost.exe (PID: 240)
Checks supported languages
- Windows 7 Ultimate KEYGEN.exe (PID: 1840)
- oVgkx.exe (PID: 1860)
- confhost.exe (PID: 240)
Reads the machine GUID from the registry
- oVgkx.exe (PID: 1860)
Drops the executable file immediately after the start
- winlogon.exe (PID: 1696)
Creates files or folders in the user directory
- winlogon.exe (PID: 1696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2011:02:23 11:35:59+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 954368 |
| InitializedDataSize: | 102400 |
| UninitializedDataSize: | 7151616 |
| EntryPoint: | 0x7bb240 |
| OSVersion: | 4 |
| ImageVersion: | 19.29 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | TheOrb666 |
| FileDescription: | Windows 7 Ultimate Keygen |
| FileVersion: | 1.0.0.0 |
| InternalName: | Windows 7 Ultimate KEYGEN.exe |
| LegalCopyright: | Copyright © TheOrb666 |
| OriginalFileName: | Windows 7 Ultimate KEYGEN.exe |
| ProductName: | Windows 7 Ultimate Keygen |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.50.1.0 |
Total processes
63
Monitored processes
18
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Windows\NetMeeting\confhost.exe" | C:\Windows\NetMeeting\confhost.exe | — | Windows 7 Ultimate KEYGEN.exe | |||||||||||
User: admin Company: TheOrb666 Integrity Level: HIGH Description: Windows 7 Ultimate Keygen Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 280 | "C:\Users\admin\Desktop\Windows 7 Ultimate KEYGEN.exe" | C:\Users\admin\Desktop\Windows 7 Ultimate KEYGEN.exe | — | explorer.exe | |||||||||||
User: admin Company: TheOrb666 Integrity Level: MEDIUM Description: Windows 7 Ultimate Keygen Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 600 | REG ADD HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v EnableLUA /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\JTLSHI.bat" " | C:\Windows\System32\cmd.exe | — | Windows 7 Ultimate KEYGEN.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1696 | winlogon.exe | C:\Windows\System32\winlogon.exe | — | confhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Logon Application Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1840 | "C:\Users\admin\Desktop\Windows 7 Ultimate KEYGEN.exe" | C:\Users\admin\Desktop\Windows 7 Ultimate KEYGEN.exe | explorer.exe | ||||||||||||
User: admin Company: TheOrb666 Integrity Level: HIGH Description: Windows 7 Ultimate Keygen Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1844 | REG ADD "HKCU\Software\Microsoft\Windows\CurrentVersion\Run" /v "ConfHost" /t REG_SZ /d "C:\Windows\NetMeeting\confhost.exe" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\AppData\Local\Temp\oVgkx.exe" | C:\Users\admin\AppData\Local\Temp\oVgkx.exe | — | Windows 7 Ultimate KEYGEN.exe | |||||||||||
User: admin Company: TheOrb666 Integrity Level: HIGH Description: Windows 7 Ultimate Keygen Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2976 | REG ADD HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center /v UACDisableNotify /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3000 | REG ADD HKLM\System\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List /v "C:\Windows\system32\winlogon.exe" /t REG_SZ /d "C:\Windows\system32\winlogon.exe:*:Enabled:Windows Messanger" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 178
Read events
1 168
Write events
10
Delete events
0
Modification events
| (PID) Process: | (1840) Windows 7 Ultimate KEYGEN.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1840) Windows 7 Ultimate KEYGEN.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1840) Windows 7 Ultimate KEYGEN.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1840) Windows 7 Ultimate KEYGEN.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (600) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | EnableLUA |
Value: 1 | |||
| (PID) Process: | (3936) reg.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\SharedAccess\Parameters\FirewallPolicy\StandardProfile |
| Operation: | write | Name: | DoNotAllowExceptions |
Value: 0 | |||
Executable files
4
Suspicious files
1
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1840 | Windows 7 Ultimate KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\JTLSHI.txt | text | |
MD5:0E3B75534086EBF315C2C8412E9DE4F2 | SHA256:4BC2F340E93A9BF84A32ADFBDC50AE117144C5B8FD9E2C08B1519EDAD3A0D79B | |||
| 1860 | oVgkx.exe | C:\Users\admin\AppData\Local\Temp\myxmfile.xm | binary | |
MD5:66AA97D41D73CF8F40E1DD2002ADF687 | SHA256:FFBD19C6BCD18EDBA20410B5A8C5F2421D4A51D5BA5C64DBCCD0FC8FB074974D | |||
| 1840 | Windows 7 Ultimate KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\nQpdh.bat | text | |
MD5:7142981B929138E1EB4A1E9A277CE1BD | SHA256:15FCAE3DCC5EF240C0703743C9FA5B705613C1D7AFADE6ADAF5D9FF59826660D | |||
| 1840 | Windows 7 Ultimate KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\JTLSHI.bat | text | |
MD5:0E3B75534086EBF315C2C8412E9DE4F2 | SHA256:4BC2F340E93A9BF84A32ADFBDC50AE117144C5B8FD9E2C08B1519EDAD3A0D79B | |||
| 1696 | winlogon.exe | C:\Users\admin\AppData\Roaming\data.dat | text | |
MD5:99B4B65A4125EFCD02A3F0A510ADCEBB | SHA256:CF452BCF0BAFC80BDC4C8F608F5503F62EA0F9ADC635FC32DB1A1BCFE551FF64 | |||
| 1696 | winlogon.exe | C:\Users\admin\AppData\Roaming\Torrent.exe | executable | |
MD5:C5A164338B12BFBEBA2EB55757A27E8B | SHA256:E76E33BF19DAD281E8D8A8F86CEB161E676B5424684FB3D89984D1A40559CCBB | |||
| 1840 | Windows 7 Ultimate KEYGEN.exe | C:\Windows\NetMeeting\confhost.exe | executable | |
MD5:30D7510AEE190D8C9FFE923521B0DA33 | SHA256:6800847ACCD0D3381B5C52BD2929622E1883A8CC514CEE7D856DE3A26665175A | |||
| 1840 | Windows 7 Ultimate KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\nQpdh.txt | text | |
MD5:7142981B929138E1EB4A1E9A277CE1BD | SHA256:15FCAE3DCC5EF240C0703743C9FA5B705613C1D7AFADE6ADAF5D9FF59826660D | |||
| 1840 | Windows 7 Ultimate KEYGEN.exe | C:\Windows\NetMeeting\confhost.txt | executable | |
MD5:3746D013FA415A504B1BFD7ADFF4E123 | SHA256:148F3A96A936F61E25E1A76818058C193B30D70AC38B03465FEAB2ABEDDB4D5D | |||
| 1840 | Windows 7 Ultimate KEYGEN.exe | C:\Users\admin\AppData\Local\Temp\oVgkx.exe | executable | |
MD5:7C7276DB195E71CD40F8ABB611479916 | SHA256:FDEF1BD30DB0B69DB8A4293516099C3CDBE4EA75A951F08C839EAE7359223D4E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
santaclaus1.no-ip.biz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |