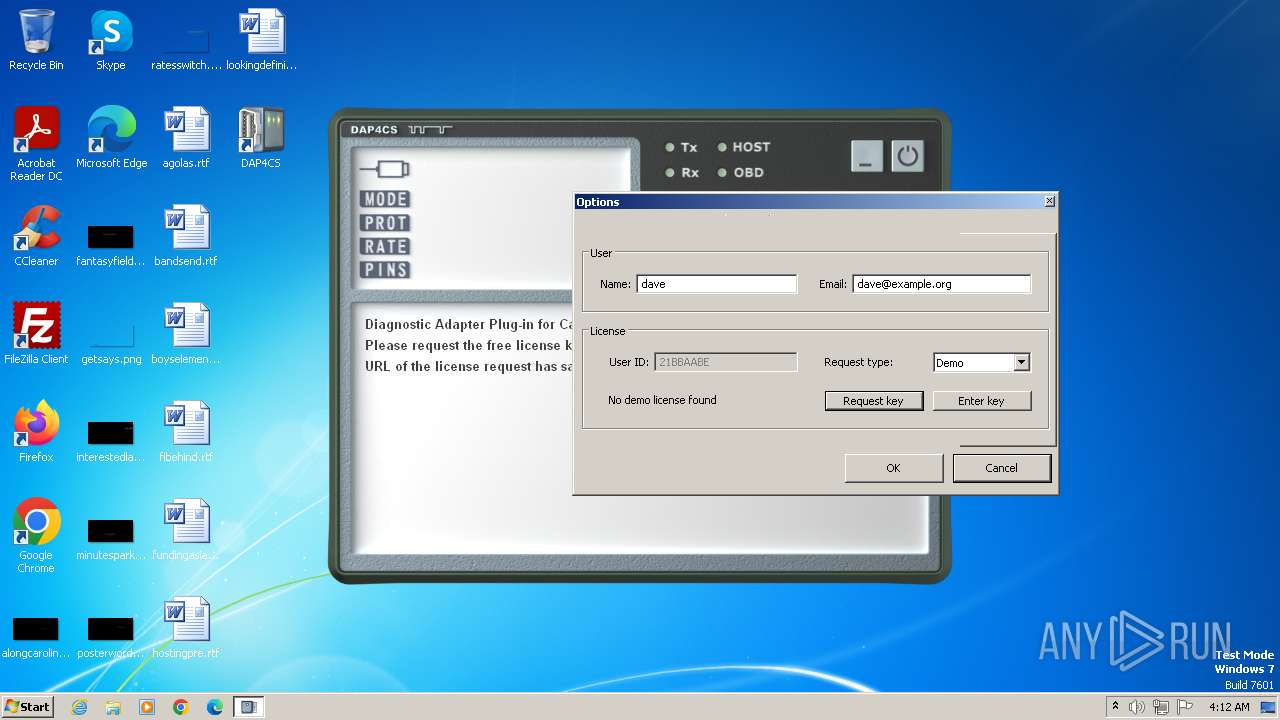
| File name: | Install_DAP4CS_1.0.4.1.exe |
| Full analysis: | https://app.any.run/tasks/803bcd90-f6ef-435a-883a-57e5a81b1ada |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2023, 04:10:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 39F98FD26C38387F62091048FCBE3B1A |
| SHA1: | 07493138CD6AE2FA364D9C84B24A2C017E293CBF |
| SHA256: | 148D53F25CB7F1B5B1CD24E8486EEF5EFAD81207E52D0C3AED0E08E2204ECF60 |
| SSDEEP: | 98304:zygyQSUdDsamnytExDWUX3L/77c1fezy2aFiI2ElyGMvcbO5VSZsbiqUrzb72a2z:2o9q+OhwiuL |
MALICIOUS
Adds path to the Windows Defender exclusion list
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
- cmd.exe (PID: 2300)
- cmd.exe (PID: 684)
Drops the executable file immediately after the start
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
SUSPICIOUS
Powershell version downgrade attack
- powershell.exe (PID: 3924)
- powershell.exe (PID: 3832)
Starts CMD.EXE for commands execution
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 684)
- cmd.exe (PID: 2300)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2300)
- cmd.exe (PID: 684)
Reads the Internet Settings
- DAP4CS.exe (PID: 2716)
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
- DAP4CS.exe (PID: 2520)
- ieframe.exe (PID: 2064)
- ieframe.exe (PID: 3220)
- DAP4CS.exe (PID: 2028)
Application launched itself
- DAP4CS.exe (PID: 2716)
- DAP4CS.exe (PID: 2028)
Reads settings of System Certificates
- ieframe.exe (PID: 2064)
Reads Internet Explorer settings
- ieframe.exe (PID: 2064)
- ieframe.exe (PID: 3220)
Adds/modifies Windows certificates
- ieframe.exe (PID: 2064)
Reads security settings of Internet Explorer
- ieframe.exe (PID: 2064)
Checks Windows Trust Settings
- ieframe.exe (PID: 2064)
Reads Microsoft Outlook installation path
- ieframe.exe (PID: 2064)
- ieframe.exe (PID: 3220)
Malware-specific behavior (creating "System.dll" in Temp)
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
The process creates files with name similar to system file names
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
INFO
Reads the computer name
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
- DAP4CS.exe (PID: 2716)
- DAP4CS.exe (PID: 2520)
- wmpnscfg.exe (PID: 3932)
- ieframe.exe (PID: 2064)
- ieframe.exe (PID: 3220)
- DAP4CS.exe (PID: 2028)
- DAP4CS.exe (PID: 188)
Checks supported languages
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
- DAP4CS.exe (PID: 2716)
- DAP4CS.exe (PID: 2520)
- wmpnscfg.exe (PID: 3932)
- pm0.exe (PID: 3204)
- ieframe.exe (PID: 2064)
- ieframe.exe (PID: 3728)
- pm1.exe (PID: 2456)
- ieframe.exe (PID: 3220)
- ieframe.exe (PID: 556)
- DAP4CS.exe (PID: 2028)
- DAP4CS.exe (PID: 188)
Creates files or folders in the user directory
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
- ieframe.exe (PID: 2064)
Reads the machine GUID from the registry
- DAP4CS.exe (PID: 2520)
- ieframe.exe (PID: 2064)
- ieframe.exe (PID: 3220)
- DAP4CS.exe (PID: 188)
Create files in a temporary directory
- DAP4CS.exe (PID: 2520)
- ieframe.exe (PID: 2064)
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
Manual execution by a user
- wmpnscfg.exe (PID: 3932)
- DAP4CS.exe (PID: 2028)
Creates files in the program directory
- pm0.exe (PID: 3204)
- DAP4CS.exe (PID: 2520)
- pm1.exe (PID: 2456)
- Install_DAP4CS_1.0.4.1.exe (PID: 2600)
Checks proxy server information
- ieframe.exe (PID: 2064)
- ieframe.exe (PID: 3220)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 04:57:41+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26112 |
| InitializedDataSize: | 141824 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x34a5 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
64
Monitored processes
17
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\DAP4CS\App\DAP4CS.exe" -token-7ae584d4-a5c2d7a5 | C:\Program Files\DAP4CS\App\DAP4CS.exe | DAP4CS.exe | ||||||||||||
User: admin Company: dap4cs.com Integrity Level: HIGH Description: Diagnostic Adapter Plug-in for CarmanScan Exit code: 0 Version: 1, 0, 4, 1 Modules
| |||||||||||||||
| 556 | "C:\Program Files\DAP4CS\App\ieframe.exe" -w 680 -h 620 -r -m | C:\Program Files\DAP4CS\App\ieframe.exe | — | DAP4CS.exe | |||||||||||
User: admin Company: AlMeRus Integrity Level: HIGH Description: IE Frame Exit code: 0 Version: 0, 8, 6, b Modules
| |||||||||||||||
| 684 | "C:\Windows\system32\cmd.exe" /C powershell -Command Add-MpPreference -ExclusionPath 'C:\Program Files\DAP4CS' | C:\Windows\System32\cmd.exe | — | Install_DAP4CS_1.0.4.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2028 | "C:\Program Files\DAP4CS\App\DAP4CS.exe" | C:\Program Files\DAP4CS\App\DAP4CS.exe | — | explorer.exe | |||||||||||
User: admin Company: dap4cs.com Integrity Level: MEDIUM Description: Diagnostic Adapter Plug-in for CarmanScan Exit code: 0 Version: 1, 0, 4, 1 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\DAP4CS\App\ieframe.exe" -w 680 -h 620 -r -m | C:\Program Files\DAP4CS\App\ieframe.exe | DAP4CS.exe | ||||||||||||
User: admin Company: AlMeRus Integrity Level: HIGH Description: IE Frame Exit code: 0 Version: 0, 8, 6, b Modules
| |||||||||||||||
| 2300 | "C:\Windows\system32\cmd.exe" /C powershell -Command Add-MpPreference -ExclusionPath 'C:\Program Files\CarmanInternational' | C:\Windows\System32\cmd.exe | — | Install_DAP4CS_1.0.4.1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2456 | -a 0 -r | C:\Program Files\DAP4CS\App\pm1.exe | — | DAP4CS.exe | |||||||||||
User: admin Company: dap4cs.com Integrity Level: HIGH Description: DAP4CS Module Exit code: 0 Version: 1, 0, 4, 1 Modules
| |||||||||||||||
| 2520 | "C:\Program Files\DAP4CS\App\DAP4CS.exe" -token-740c38ac-f4795d0f | C:\Program Files\DAP4CS\App\DAP4CS.exe | DAP4CS.exe | ||||||||||||
User: admin Company: dap4cs.com Integrity Level: HIGH Description: Diagnostic Adapter Plug-in for CarmanScan Exit code: 0 Version: 1, 0, 4, 1 Modules
| |||||||||||||||
| 2600 | "C:\Users\admin\AppData\Local\Temp\Install_DAP4CS_1.0.4.1.exe" | C:\Users\admin\AppData\Local\Temp\Install_DAP4CS_1.0.4.1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2716 | "C:\Program Files\DAP4CS\App\DAP4CS.exe" | C:\Program Files\DAP4CS\App\DAP4CS.exe | — | Install_DAP4CS_1.0.4.1.exe | |||||||||||
User: admin Company: dap4cs.com Integrity Level: HIGH Description: Diagnostic Adapter Plug-in for CarmanScan Exit code: 0 Version: 1, 0, 4, 1 Modules
| |||||||||||||||
Total events
11 171
Read events
10 924
Write events
247
Delete events
0
Modification events
| (PID) Process: | (2600) Install_DAP4CS_1.0.4.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2600) Install_DAP4CS_1.0.4.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2600) Install_DAP4CS_1.0.4.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2600) Install_DAP4CS_1.0.4.1.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3832) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3924) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2716) DAP4CS.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2716) DAP4CS.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2716) DAP4CS.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2716) DAP4CS.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
10
Suspicious files
40
Text files
30
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3924 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\J07IULL67YGAX4EUV31N.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2600 | Install_DAP4CS_1.0.4.1.exe | C:\Users\admin\AppData\Local\Temp\nsrA81.tmp\modern-header.bmp | image | |
MD5:36EF5F30B6568D433F219F72C1CC25CF | SHA256:F6AD467343B4D66F917EE65EA1B7837D771E4DBAE3BDD3F8E780D5DF8F7E4B89 | |||
| 2600 | Install_DAP4CS_1.0.4.1.exe | C:\Program Files\DAP4CS\App\DAP4CS.dat | binary | |
MD5:A4E0B0F151A3F8BD4B3070649701307F | SHA256:D5870B33A395CCA1B27991D6768C35F65BE3C34CB29CE401790C5F49501E9327 | |||
| 2600 | Install_DAP4CS_1.0.4.1.exe | C:\Users\admin\AppData\Local\Temp\nsrA81.tmp\nsDialogs.dll | executable | |
MD5:CA95C9DA8CEF7062813B989AB9486201 | SHA256:FEB6364375D0AB081E9CDF11271C40CB966AF295C600903383B0730F0821C0BE | |||
| 2600 | Install_DAP4CS_1.0.4.1.exe | C:\Users\admin\AppData\Local\Temp\nsrA81.tmp\modern-wizard.bmp | image | |
MD5:6324E4676ED4F789B4376E6501AE7B1D | SHA256:6AC3D0714503A34D438B030DB129DD1FC44A22C80A320D1842593FEB9BCDFE50 | |||
| 2600 | Install_DAP4CS_1.0.4.1.exe | C:\Users\admin\AppData\Local\Temp\nsrA81.tmp\LangDLL.dll | executable | |
MD5:3DD80DFF583544514EEB3A5ED851A519 | SHA256:86CFF5EACA76C49F924CB123D242FDCFD45AB99C4B638D3B8F4A8CFB1970AB5B | |||
| 3832 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2600 | Install_DAP4CS_1.0.4.1.exe | C:\Program Files\DAP4CS\App\Prototype.ttf | binary | |
MD5:0483B4EEAAEFC7B81986E43702C7900D | SHA256:CE7F544CFC3F02953F79D065BCD16C8CC0EB041F76FC987AE6ADCC3B21005774 | |||
| 3832 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\D3VYYSB4POZFI8K6FT9B.temp | binary | |
MD5:16F6D260068B85896C0EBB2E1B2A60D1 | SHA256:6E3B1EF1FB4736A9BF18FADF8E42935CC5053478B6F403A38EFBA8500E819984 | |||
| 2600 | Install_DAP4CS_1.0.4.1.exe | C:\Program Files\DAP4CS\App\DAP4CS.exe | executable | |
MD5:51D9E656F8909D3945A5E010D967DBBB | SHA256:D71D917FD67DB5382215957F97A2462192C684007037EAF01031EA044E31CD01 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
18
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
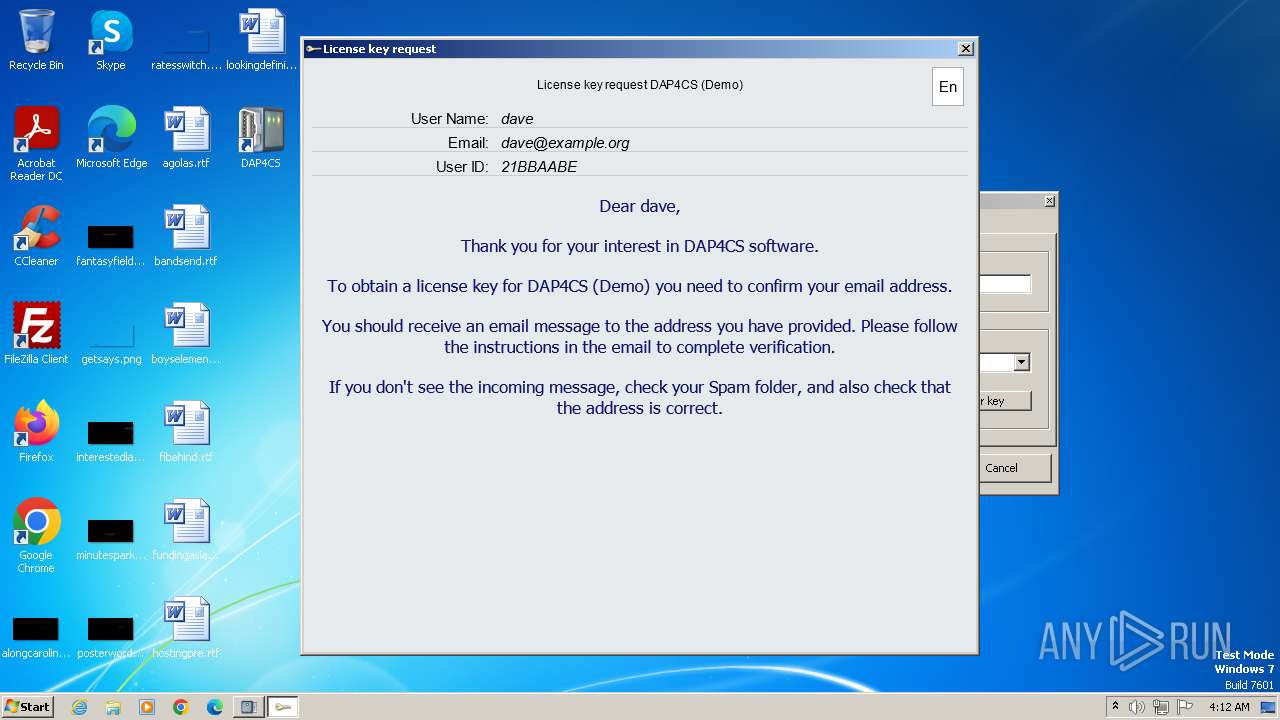
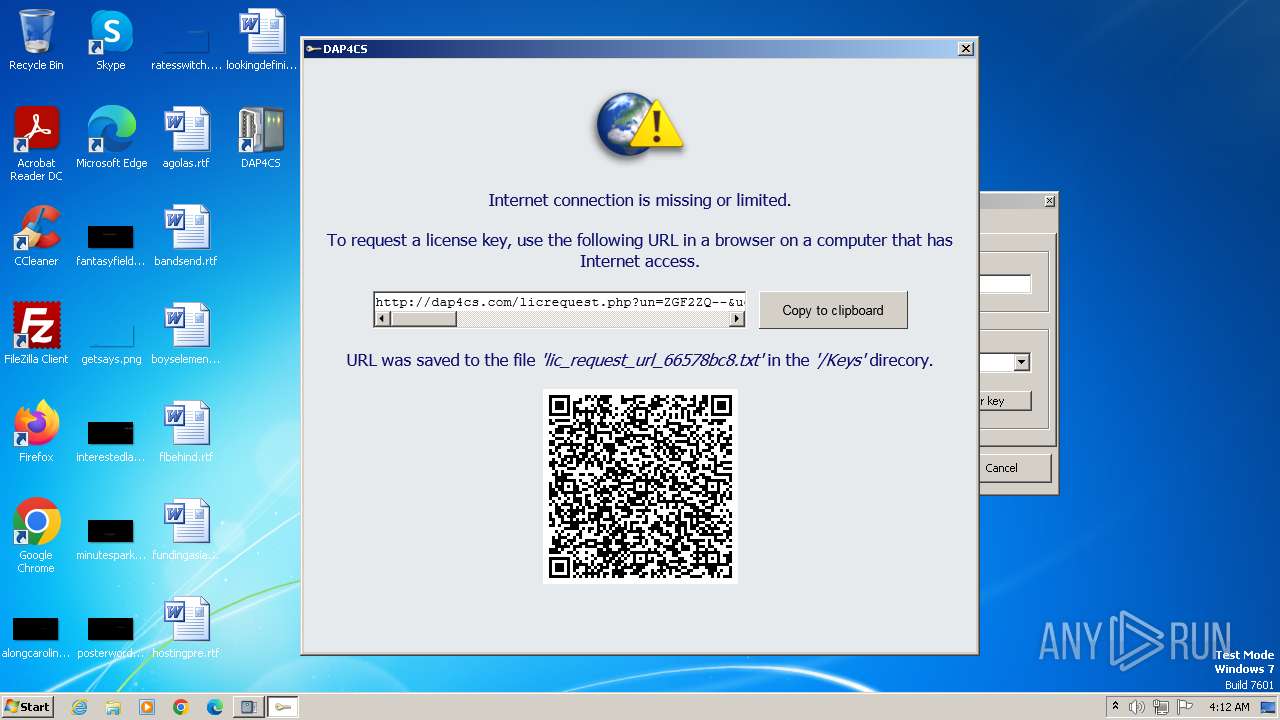
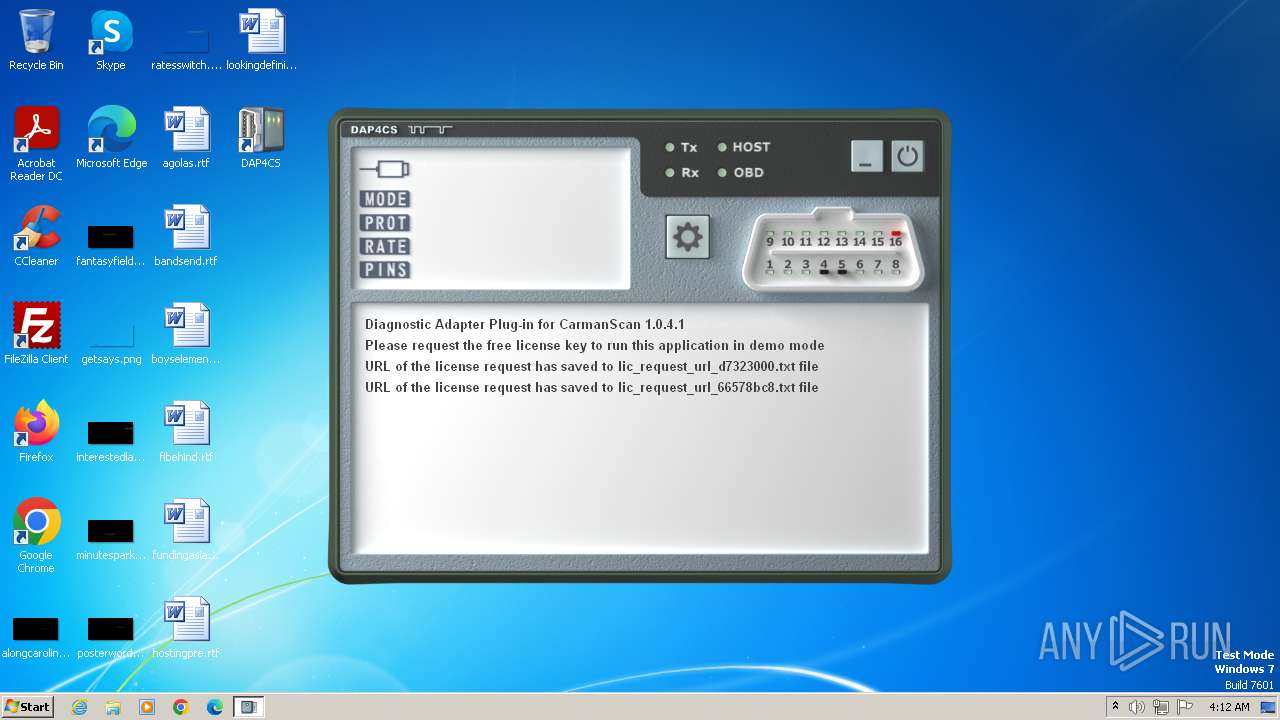
2064 | ieframe.exe | GET | 301 | 94.103.81.208:80 | http://dap4cs.com/licrequest.php?un=ZGF2ZQ--&ue=ZGF2ZUBleGFtcGxlLm9yZw--&ui=21bbaabe&rt=0&lh=d7323000&ld=Stww7RncfNtK1wLBS4YD3yjaluz7LSehHovV.JqN9EkQlW8VFsqvWbLCFFaXLrgwBtDC18ReZheO3Rhx6twoXR7DxmIAvxFq&ch=40563bb6&lang=0&v=1.0.4.1 | unknown | html | 162 b | unknown |
2064 | ieframe.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f889698b54d9e6b7 | unknown | compressed | 4.66 Kb | unknown |
2064 | ieframe.exe | GET | 200 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1d0e5584be0e8c8b | unknown | compressed | 65.2 Kb | unknown |
3220 | ieframe.exe | GET | — | 94.103.81.208:80 | http://dap4cs.com/licrequest.php?un=ZGF2ZQ--&ue=ZGF2ZUBleGFtcGxlLm9yZw--&ui=21bbaabe&rt=1&lh=66578bc8&ld=sq4vA5XwNYrKBQ5pjCtfHf7NlOx_KWrIztvflu8vrgdVsPamqW5Cw6m5nGsottEjImYk7l8x748af68qte_yc4.SehLjtpSs&ch=f0bdb8d5&lang=0&v=1.0.4.1 | unknown | — | — | unknown |
2064 | ieframe.exe | GET | 200 | 23.212.210.158:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
2064 | ieframe.exe | GET | 200 | 184.24.77.54:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgRFqeoRDPl314lPwaW%2FWTBrJg%3D%3D | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 23.35.228.137:80 | — | AKAMAI-AS | DE | unknown |
2520 | DAP4CS.exe | 51.137.137.111:123 | time.windows.com | — | — | unknown |
2520 | DAP4CS.exe | 132.163.96.6:123 | time.nist.gov | — | — | unknown |
868 | svchost.exe | 95.101.148.135:80 | armmf.adobe.com | Akamai International B.V. | NL | unknown |
2520 | DAP4CS.exe | 95.31.7.160:123 | 0.ru.pool.ntp.org | — | — | unknown |
2520 | DAP4CS.exe | 162.159.200.123:123 | 1.ru.pool.ntp.org | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
time.windows.com |
| whitelisted |
time.nist.gov |
| whitelisted |
armmf.adobe.com |
| whitelisted |
0.ru.pool.ntp.org |
| unknown |
1.ru.pool.ntp.org |
| unknown |
dap4cs.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |