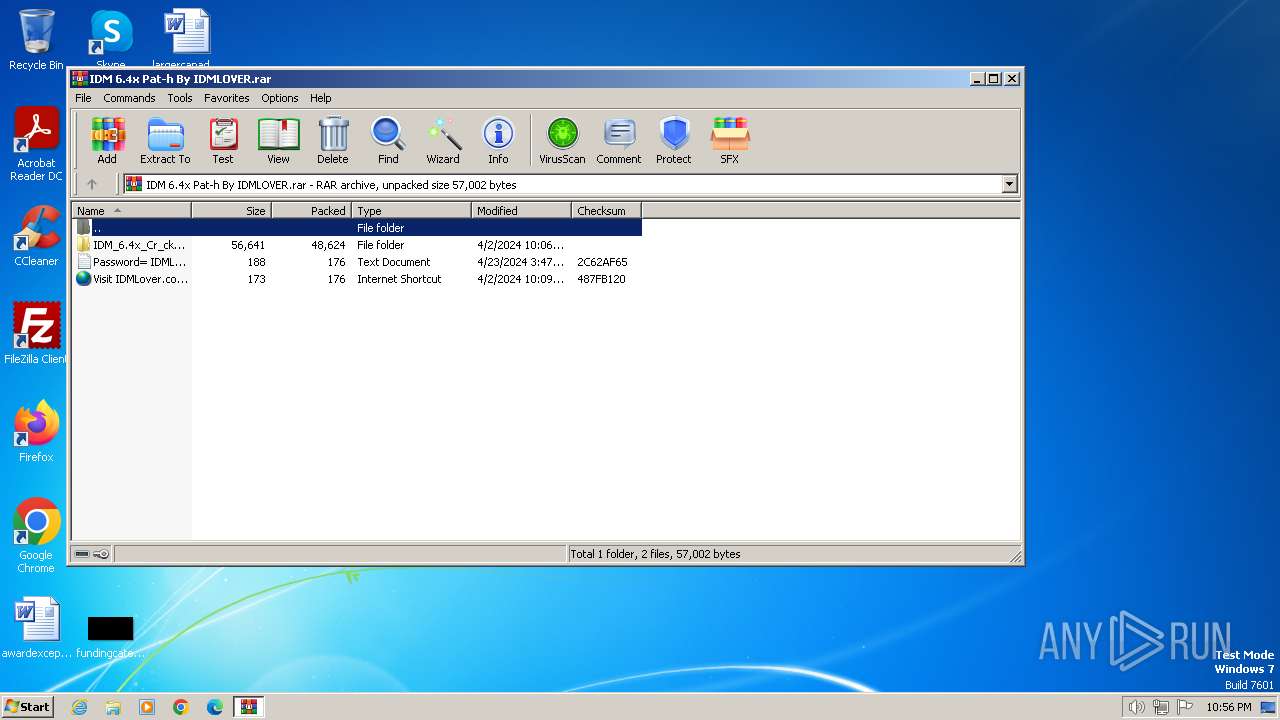
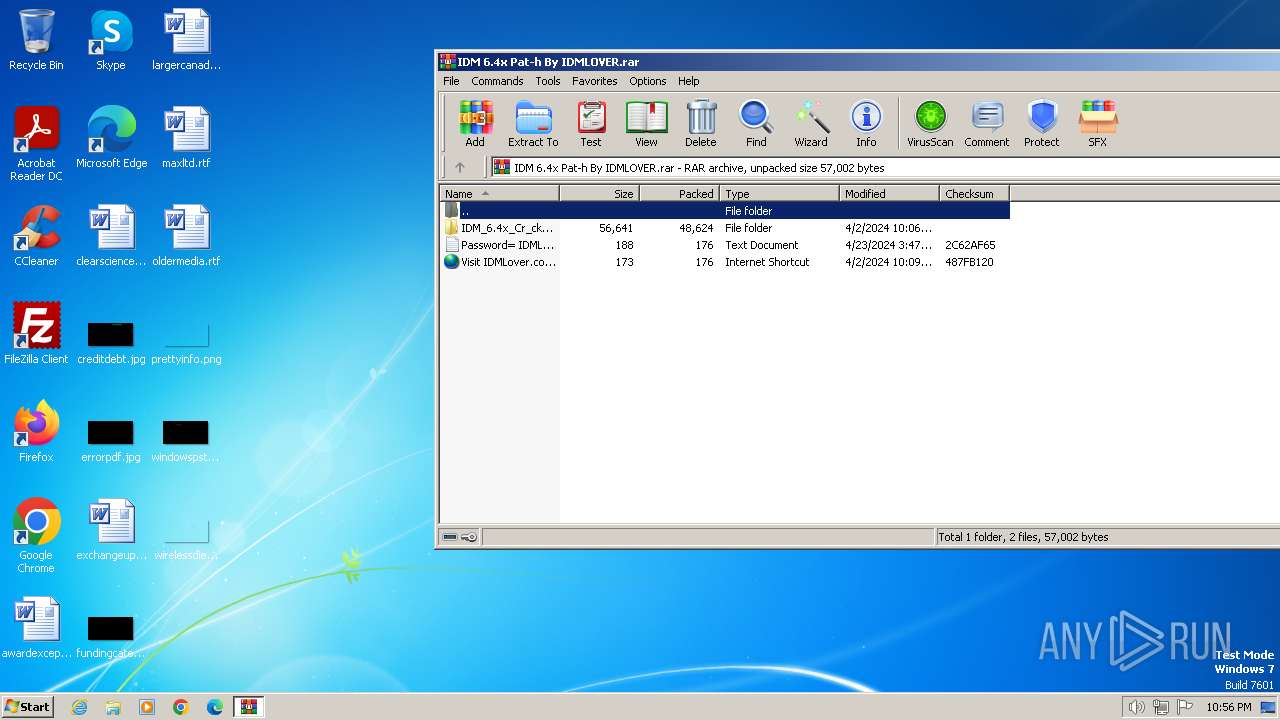
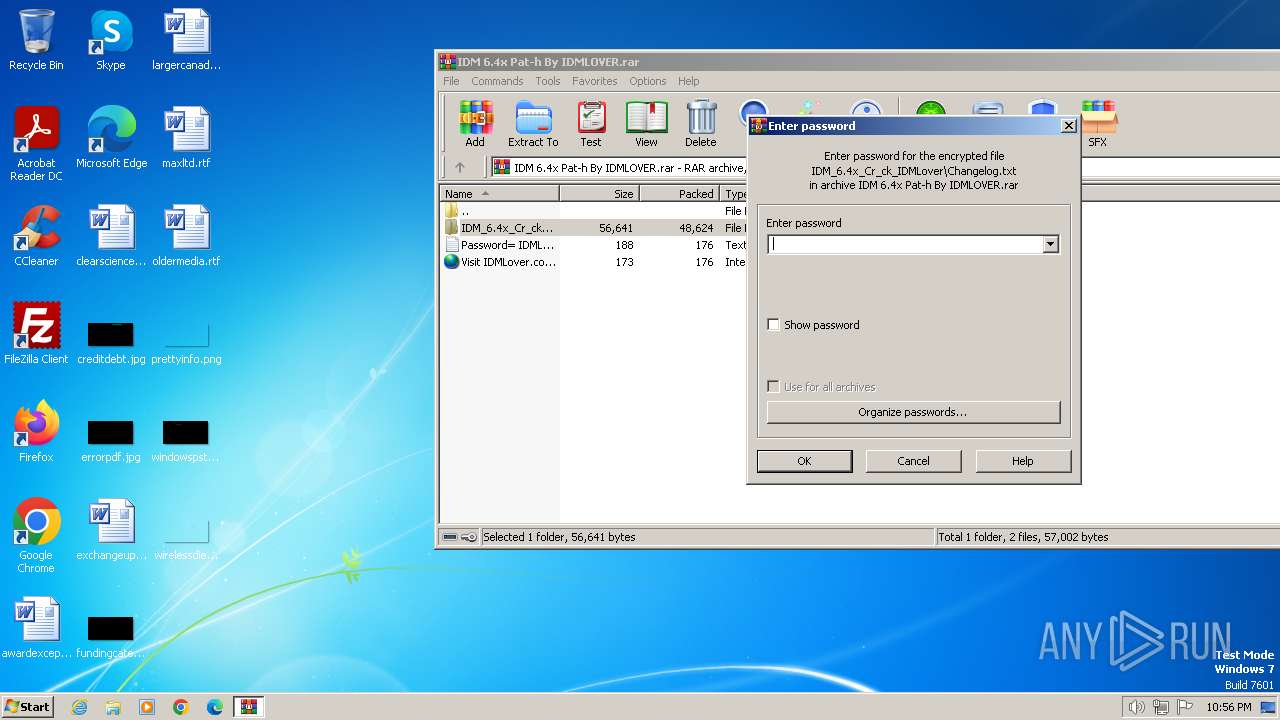
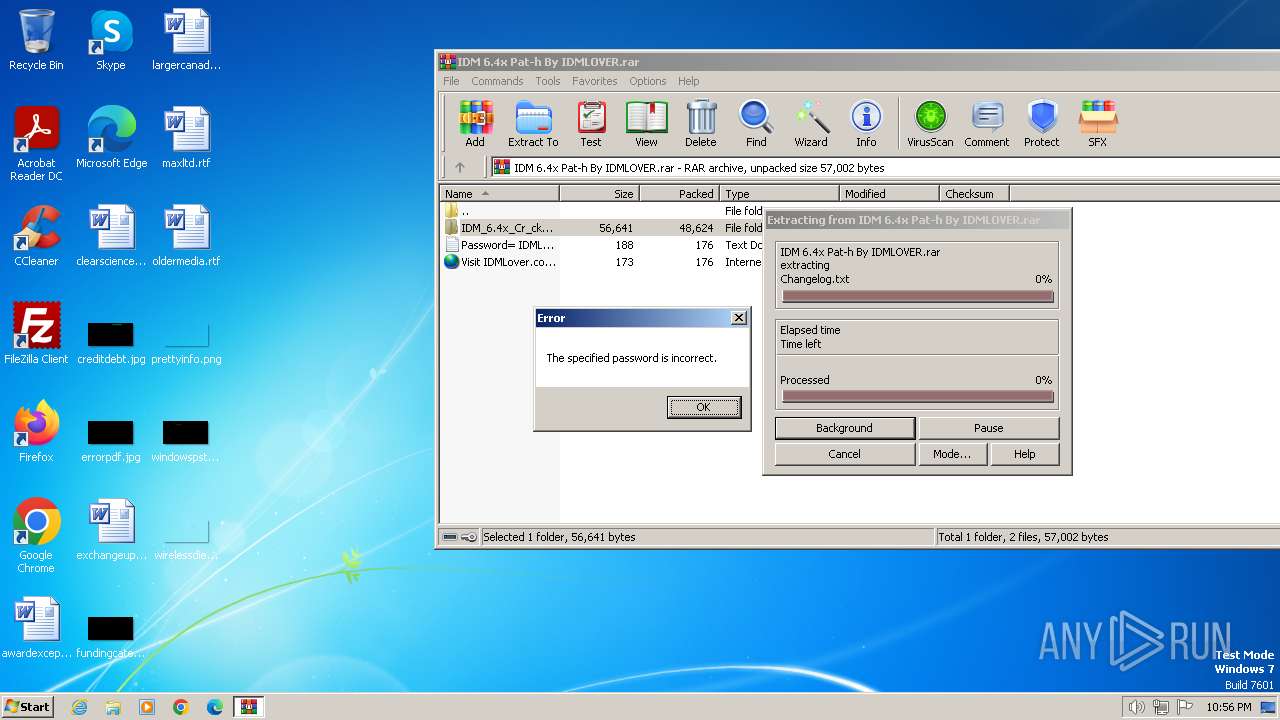
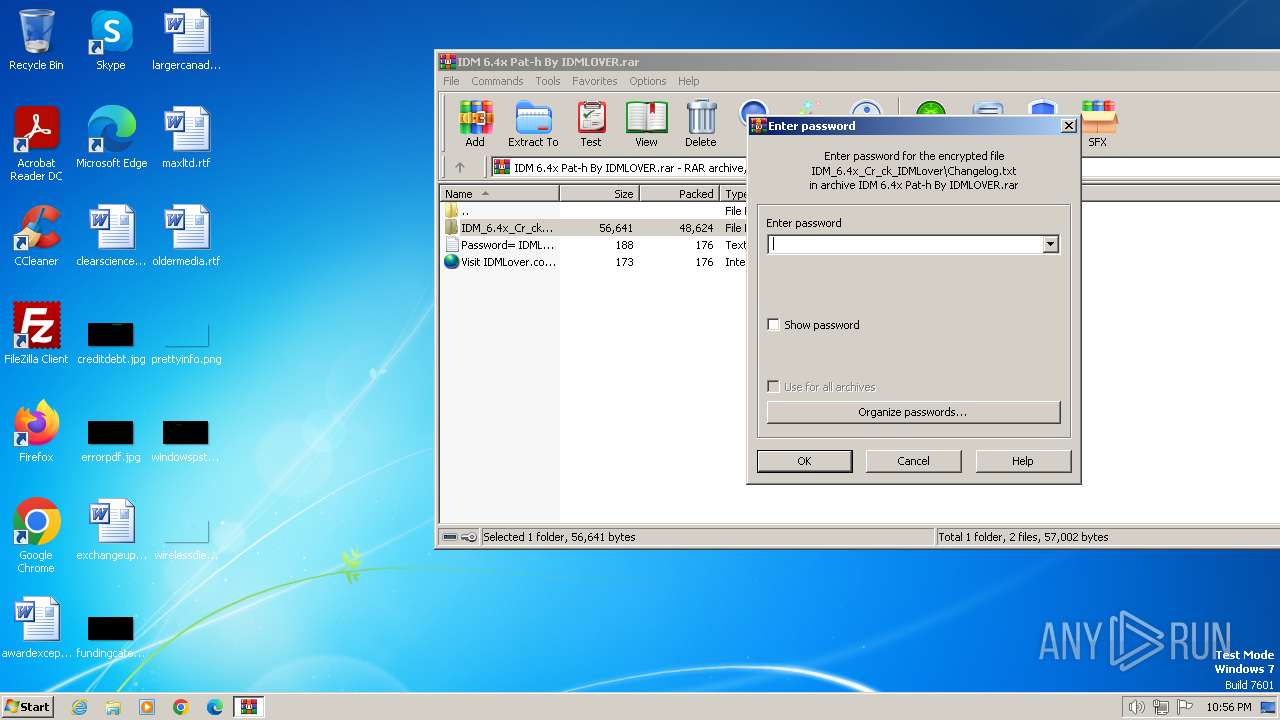
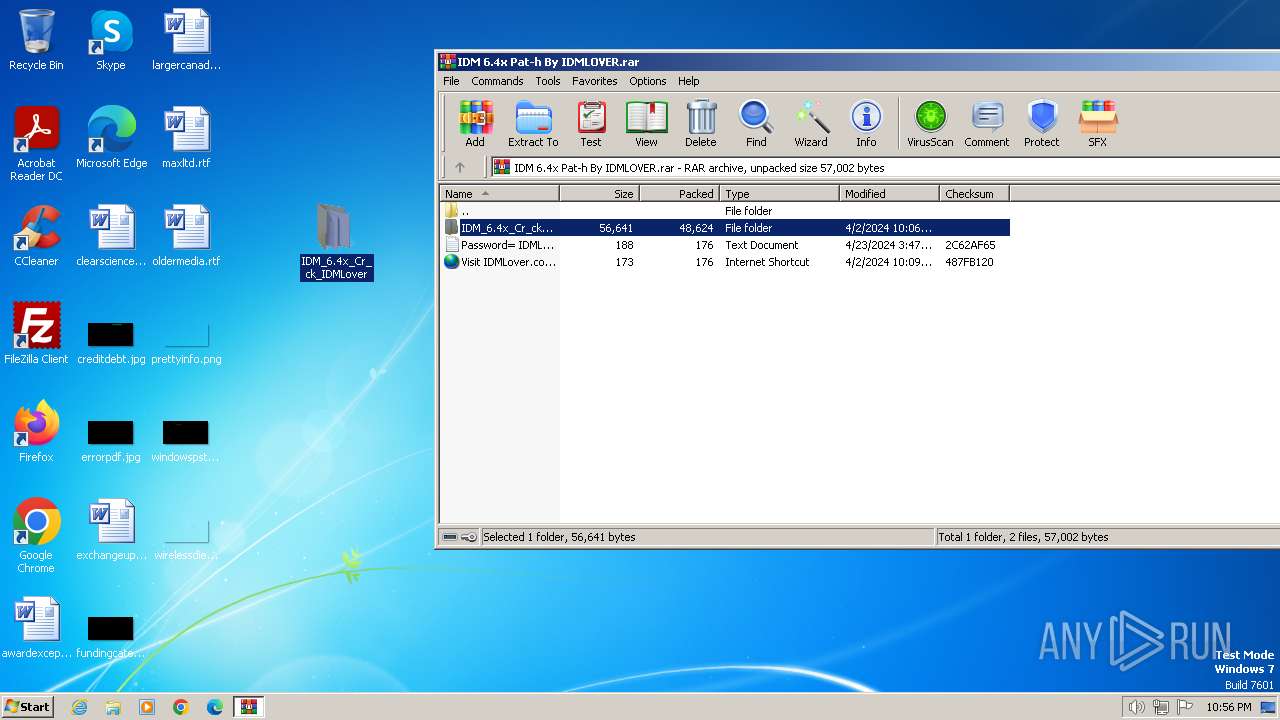
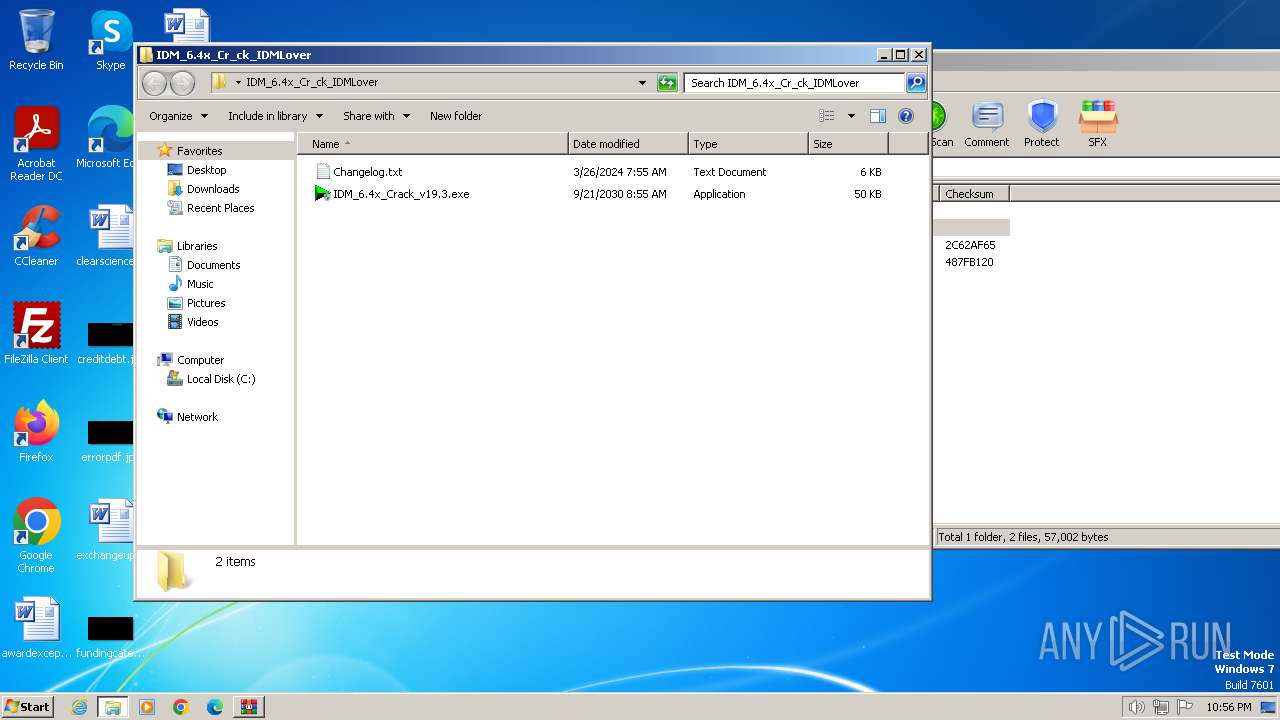
| File name: | IDM 6.4x Pat-h By IDMLOVER.rar |
| Full analysis: | https://app.any.run/tasks/3bebe02b-2f9c-444e-8d4a-f3d8e379ddec |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2024, 21:56:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7BAC86712070C1049008623407642506 |
| SHA1: | C8F09406C4B48BBBB28B5D087C96999BEC489746 |
| SHA256: | 146D62CDD7AF8F7AD498E571319716EC11DB2E6F2CE8D30DE6D016677F559A2F |
| SSDEEP: | 1536:S5sWJXrbeY2A2J3VtjpJs0dQW9PdB49Q/9u9+U/HFIBOVtai8:SmUuYwp31Js0WkBCVfFoT |
MALICIOUS
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 3604)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 3604)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 3604)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 3604)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
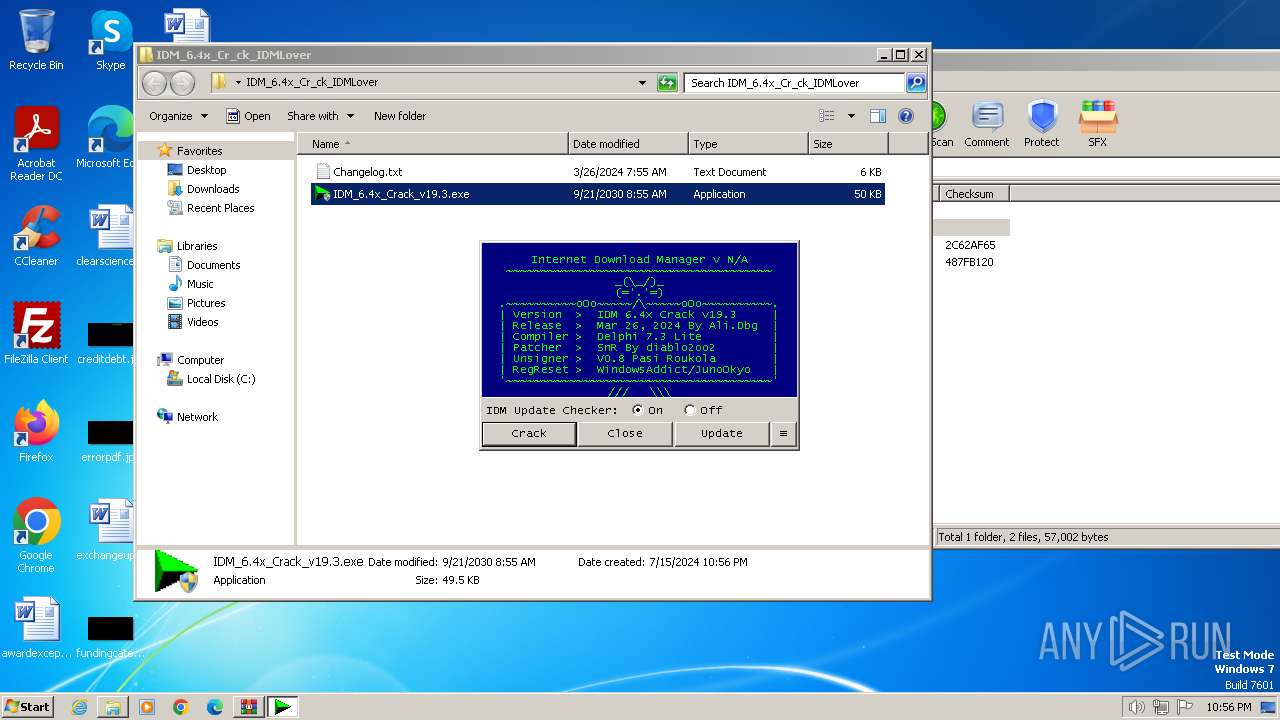
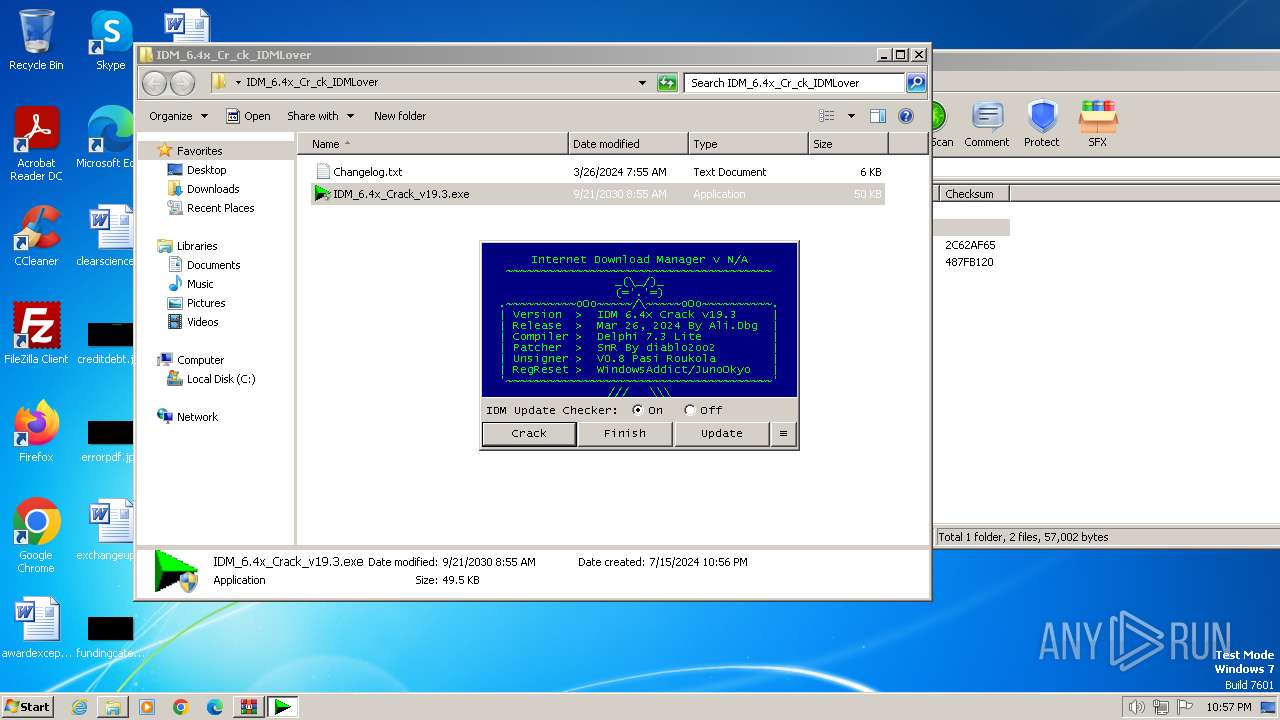
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
- cmd.exe (PID: 936)
- cmd.exe (PID: 952)
Executing commands from a ".bat" file
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
- cmd.exe (PID: 936)
Application launched itself
- cmd.exe (PID: 936)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 936)
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 936)
- cmd.exe (PID: 2720)
- cmd.exe (PID: 2912)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 936)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 936)
Hides command output
- cmd.exe (PID: 2720)
- cmd.exe (PID: 952)
Starts application with an unusual extension
- cmd.exe (PID: 936)
The process executes VB scripts
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3604)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3520)
- IDM_6.4x_Crack_v19.3.exe (PID: 2940)
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
Checks supported languages
- wmpnscfg.exe (PID: 3520)
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
- chcp.com (PID: 1200)
Reads the computer name
- wmpnscfg.exe (PID: 3520)
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3400)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3400)
Create files in a temporary directory
- IDM_6.4x_Crack_v19.3.exe (PID: 3528)
- reg.exe (PID: 3800)
Checks operating system version
- cmd.exe (PID: 936)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 2644)
- powershell.exe (PID: 1596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
96
Monitored processes
53
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | reg query "HKCU\Software\DownloadManager" "/v" "LastCheckQU" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 660 | reg delete HKU\S-1-5-21-1302019708-1500728564-335382590-1000\IAS_TEST /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 724 | REG ADD "HKCU\Software\DownloadManager" /v "nLst" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 744 | C:\Windows\system32\cmd.exe /c reg query "HKLM\SYSTEM\CurrentControlSet\Control\Session Manager\Environment" /v PROCESSOR_ARCHITECTURE | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 880 | reg add HKCU\IAS_TEST | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 936 | cmd.exe /c call "C:\Users\admin\AppData\Local\Temp\BATCLEN.bat" | C:\Windows\System32\cmd.exe | — | IDM_6.4x_Crack_v19.3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 952 | C:\Windows\system32\cmd.exe /c reg query "HKU\S-1-5-21-1302019708-1500728564-335382590-1000\Software\DownloadManager" /v ExePath 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1020 | reg query "HKCU\Software\DownloadManager" "/v" "LstCheck" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1200 | chcp 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1324 | reg query HKCU\Console /v QuickEdit | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
23 600
Read events
23 532
Write events
53
Delete events
15
Modification events
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\IDM 6.4x Pat-h By IDMLOVER.rar | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3400) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
13
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3400.39478\IDM_6.4x_Cr_ck_IDMLover\IDM_6.4x_Crack_v19.3.exe | executable | |
MD5:F149E4A106B1A6941F6FB1B3B8AB87AE | SHA256:AF26D2A5315BBE1D8F772CA82FFCB55131E84FADBC3869B6BD5C36729A610399 | |||
| 2860 | powershell.exe | C:\Users\admin\AppData\Local\Temp\rum3ej5j.itq.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 1596 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 2860 | powershell.exe | C:\Users\admin\AppData\Local\Temp\i1h3wu1i.oge.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3728 | powershell.exe | C:\Users\admin\AppData\Local\Temp\h4j04eoy.twz.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\k05aiwrq.ran.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2644 | powershell.exe | C:\Users\admin\AppData\Local\Temp\4xff1njs.ajp.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3800 | reg.exe | C:\Users\admin\AppData\Local\Temp\REGC3A5.tmp | text | |
MD5:F58D4E5F0B6A7E69AA96964ABCDEF744 | SHA256:253D606D5060BB62CFA2411477004C8ED2ECA7925A2B0770691D485678AABF73 | |||
| 3728 | powershell.exe | C:\Users\admin\AppData\Local\Temp\enrgzrop.dot.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3800 | reg.exe | C:\Windows\Temp\_Backup_HKCU_CLSID_20240715-225708775.reg | text | |
MD5:F58D4E5F0B6A7E69AA96964ABCDEF744 | SHA256:253D606D5060BB62CFA2411477004C8ED2ECA7925A2B0770691D485678AABF73 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
10
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
1060 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
idm.0dy.ir |
| unknown |