| File name: | eagleget-2-1-6-50.exe |
| Full analysis: | https://app.any.run/tasks/d7c8836e-b161-4190-9601-997826afaa16 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2024, 02:01:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 9 sections |
| MD5: | E96DD956BC2159FF1D073876EF5D4E58 |
| SHA1: | A0DA0D7C8394D646EB5A0F64BE14397235F22704 |
| SHA256: | 14636B7FC900E2BE3FEE5ABB409E3B7A3CDF5A99107BF6D7DCBCCE4B26EE0D34 |
| SSDEEP: | 98304:eLMru/vgZAm4EWVmz5c+aZ96/QTDgKkZ0s68xCT7JAAPGyJAgMv4io3GEMD/N8jn:Ki3EZYlsygUyxEqjdyNLja |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- eagleget-2-1-6-50.tmp (PID: 6584)
SUSPICIOUS
Reads security settings of Internet Explorer
- eagleget-2-1-6-50.tmp (PID: 6360)
- eagleget-2-1-6-50.tmp (PID: 6584)
Executable content was dropped or overwritten
- eagleget-2-1-6-50.exe (PID: 6340)
- eagleget-2-1-6-50.exe (PID: 6560)
- eagleget-2-1-6-50.tmp (PID: 6584)
- net_updater32.exe (PID: 7132)
Reads the Windows owner or organization settings
- eagleget-2-1-6-50.tmp (PID: 6584)
Uses TASKKILL.EXE to kill process
- eagleget-2-1-6-50.tmp (PID: 6584)
Drops a system driver (possible attempt to evade defenses)
- eagleget-2-1-6-50.tmp (PID: 6584)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7048)
- regsvr32.exe (PID: 7072)
- regsvr32.exe (PID: 7096)
Process drops legitimate windows executable
- eagleget-2-1-6-50.tmp (PID: 6584)
- net_updater32.exe (PID: 7132)
The process drops C-runtime libraries
- eagleget-2-1-6-50.tmp (PID: 6584)
- net_updater32.exe (PID: 7132)
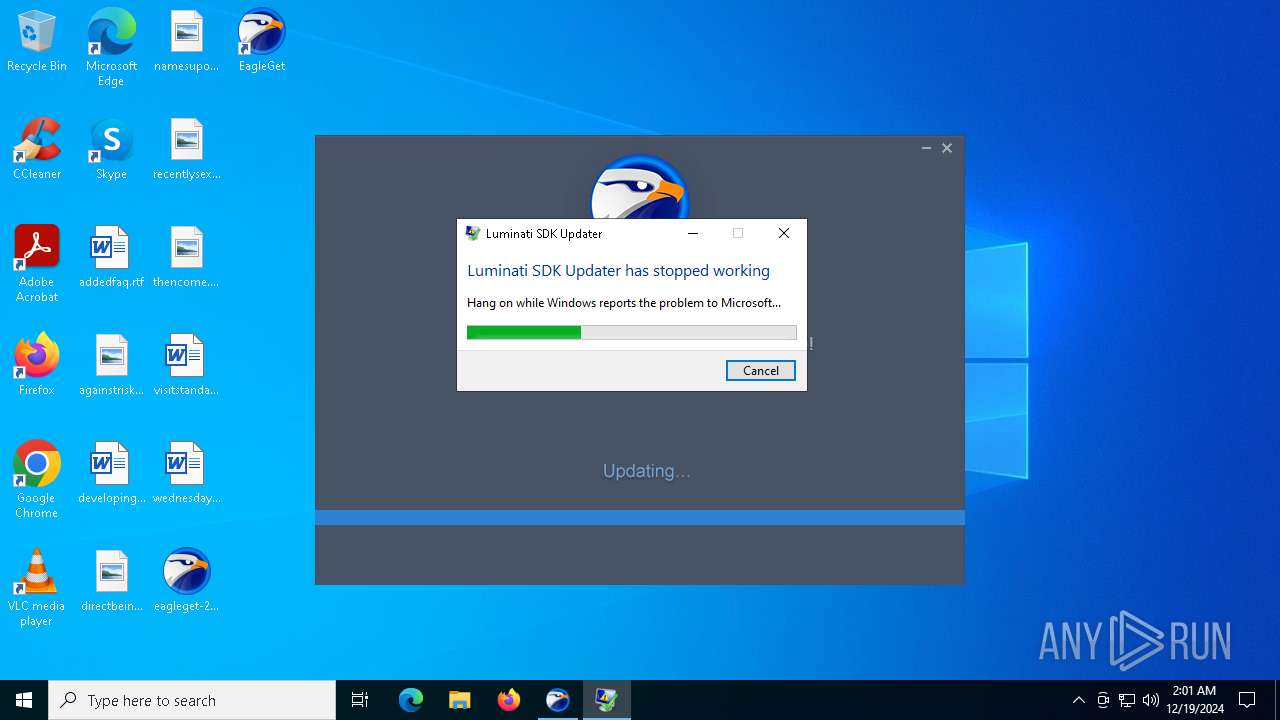
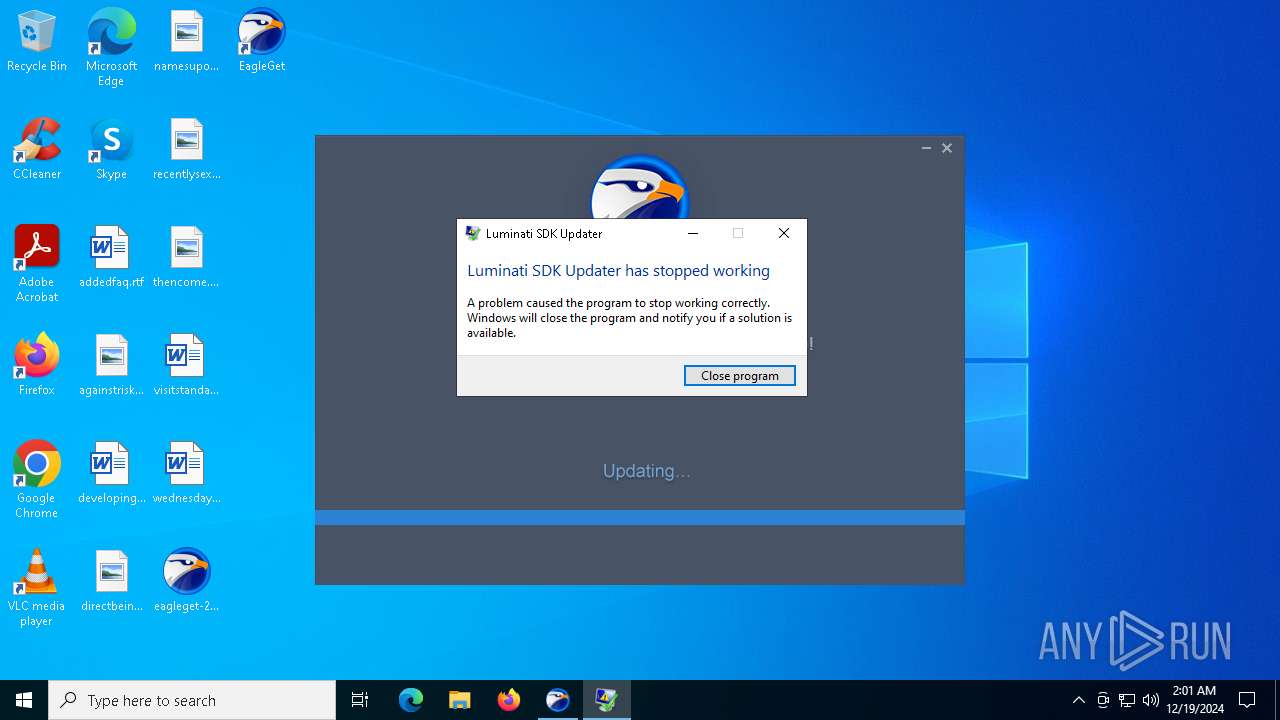
Executes application which crashes
- net_updater32.exe (PID: 7132)
Potential Corporate Privacy Violation
- net_updater32.exe (PID: 7132)
INFO
Checks supported languages
- eagleget-2-1-6-50.exe (PID: 6340)
- eagleget-2-1-6-50.tmp (PID: 6360)
- eagleget-2-1-6-50.tmp (PID: 6584)
- eagleget-2-1-6-50.exe (PID: 6560)
- net_updater32.exe (PID: 7132)
- test_wpf.exe (PID: 5848)
The sample compiled with chinese language support
- eagleget-2-1-6-50.exe (PID: 6340)
- eagleget-2-1-6-50.exe (PID: 6560)
- eagleget-2-1-6-50.tmp (PID: 6584)
Process checks computer location settings
- eagleget-2-1-6-50.tmp (PID: 6360)
- eagleget-2-1-6-50.tmp (PID: 6584)
Reads the computer name
- eagleget-2-1-6-50.tmp (PID: 6360)
- eagleget-2-1-6-50.tmp (PID: 6584)
- net_updater32.exe (PID: 7132)
- test_wpf.exe (PID: 5848)
Create files in a temporary directory
- eagleget-2-1-6-50.exe (PID: 6340)
- eagleget-2-1-6-50.exe (PID: 6560)
- eagleget-2-1-6-50.tmp (PID: 6584)
The sample compiled with russian language support
- eagleget-2-1-6-50.tmp (PID: 6584)
Creates files in the program directory
- eagleget-2-1-6-50.tmp (PID: 6584)
- net_updater32.exe (PID: 7132)
The sample compiled with english language support
- eagleget-2-1-6-50.tmp (PID: 6584)
- net_updater32.exe (PID: 7132)
Creates files or folders in the user directory
- eagleget-2-1-6-50.tmp (PID: 6584)
Creates a software uninstall entry
- eagleget-2-1-6-50.tmp (PID: 6584)
Reads security settings of Internet Explorer
- regsvr32.exe (PID: 7048)
The process uses the downloaded file
- eagleget-2-1-6-50.tmp (PID: 6584)
Reads the software policy settings
- net_updater32.exe (PID: 7132)
- WerFault.exe (PID: 2776)
Reads the machine GUID from the registry
- test_wpf.exe (PID: 5848)
Checks proxy server information
- WerFault.exe (PID: 2776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:08 12:51:37+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 69120 |
| InitializedDataSize: | 104960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x117e4 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.1.6.50 |
| ProductVersionNumber: | 2.1.6.50 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | ASCII |
| Comments: | 此安装程序由 Inno Setup 构建。 |
| CompanyName: | EagleGet |
| FileDescription: | EagleGet Setup |
| FileVersion: | 2.1.6.50 |
| LegalCopyright: | |
| ProductName: | EagleGet |
| ProductVersion: | 2.1.6.50 |
Total processes
142
Monitored processes
13
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2776 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7132 -s 1212 | C:\Windows\SysWOW64\WerFault.exe | net_updater32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5848 | C:\Program Files (x86)\EagleGet\test_wpf.exe | C:\Program Files (x86)\EagleGet\test_wpf.exe | — | net_updater32.exe | |||||||||||
User: admin Company: Luminati Networks Ltd. Integrity Level: HIGH Description: test_wpf Exit code: 0 Version: 1.172.289 Modules
| |||||||||||||||
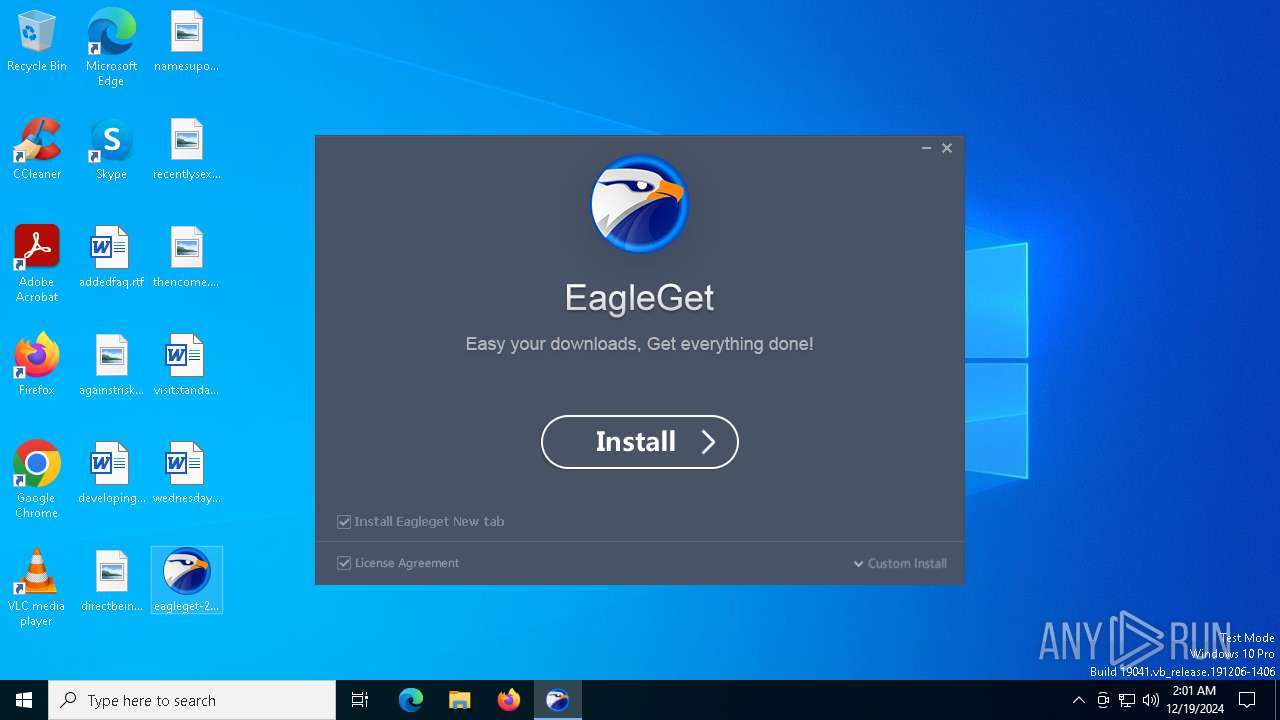
| 6340 | "C:\Users\admin\Desktop\eagleget-2-1-6-50.exe" | C:\Users\admin\Desktop\eagleget-2-1-6-50.exe | explorer.exe | ||||||||||||
User: admin Company: EagleGet Integrity Level: MEDIUM Description: EagleGet Setup Version: 2.1.6.50 Modules
| |||||||||||||||
| 6360 | "C:\Users\admin\AppData\Local\Temp\is-PTJ7M.tmp\eagleget-2-1-6-50.tmp" /SL5="$801F2,9993427,175104,C:\Users\admin\Desktop\eagleget-2-1-6-50.exe" | C:\Users\admin\AppData\Local\Temp\is-PTJ7M.tmp\eagleget-2-1-6-50.tmp | — | eagleget-2-1-6-50.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: 安装/卸载 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6560 | "C:\Users\admin\Desktop\eagleget-2-1-6-50.exe" /SPAWNWND=$50242 /NOTIFYWND=$801F2 | C:\Users\admin\Desktop\eagleget-2-1-6-50.exe | eagleget-2-1-6-50.tmp | ||||||||||||
User: admin Company: EagleGet Integrity Level: HIGH Description: EagleGet Setup Version: 2.1.6.50 Modules
| |||||||||||||||
| 6584 | "C:\Users\admin\AppData\Local\Temp\is-TVNQH.tmp\eagleget-2-1-6-50.tmp" /SL5="$1202D6,9993427,175104,C:\Users\admin\Desktop\eagleget-2-1-6-50.exe" /SPAWNWND=$50242 /NOTIFYWND=$801F2 | C:\Users\admin\AppData\Local\Temp\is-TVNQH.tmp\eagleget-2-1-6-50.tmp | eagleget-2-1-6-50.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 安装/卸载 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6624 | "taskkill.exe" /f /im "net_updater32.exe" | C:\Windows\SysWOW64\taskkill.exe | — | eagleget-2-1-6-50.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7048 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\EagleGet\eagleSniffer.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | eagleget-2-1-6-50.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7072 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\EagleGet\npEagleget.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | eagleget-2-1-6-50.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 346
Read events
5 280
Write events
62
Delete events
4
Modification events
| (PID) Process: | (6584) eagleget-2-1-6-50.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | delete value | Name: | Enable Browser Extensions |
Value: yes | |||
| (PID) Process: | (6584) eagleget-2-1-6-50.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | Enable Browser Extensions |
Value: y | |||
| (PID) Process: | (6584) eagleget-2-1-6-50.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\EagleGet |
| Operation: | write | Name: | path |
Value: C:\Program Files (x86)\EagleGet | |||
| (PID) Process: | (6584) eagleget-2-1-6-50.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\EagleGet |
| Operation: | write | Name: | Version |
Value: 2.1.6.50 | |||
| (PID) Process: | (6584) eagleget-2-1-6-50.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\EagleGet |
| Operation: | write | Name: | showlum |
Value: 1 | |||
| (PID) Process: | (7048) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{1E871FF8-029C-4732-8AA7-39E3D3872057}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (7048) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{13D6E221-D1CC-4cc1-8410-66CD89818A6F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (7048) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Internet Explorer |
| Operation: | write | Name: | DownloadUI |
Value: {13D6E221-D1CC-4cc1-8410-66CD89818A6F} | |||
| (PID) Process: | (7048) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Internet Explorer\Extension Validation\{13D6E221-D1CC-4cc1-8410-66CD89818A6F}\InprocServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
| (PID) Process: | (7048) regsvr32.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer |
| Operation: | write | Name: | DownloadUI |
Value: {13D6E221-D1CC-4cc1-8410-66CD89818A6F} | |||
Executable files
77
Suspicious files
20
Text files
135
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6340 | eagleget-2-1-6-50.exe | C:\Users\admin\AppData\Local\Temp\is-PTJ7M.tmp\eagleget-2-1-6-50.tmp | executable | |
MD5:EB42E5720E09CD014694A22C86929F5E | SHA256:4DC2D414277E497490D2009F370051298BCCAA649D0A335B064269A0BB9BBBF3 | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\util.dll | executable | |
MD5:192C98CB51F39BE053AD5C7E029E75F8 | SHA256:A2EF6B8FBF44BC77631D5635B8ABEDF90DB5903B94618753168F5A904EBC5F60 | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\EULA.txt | text | |
MD5:FB6AF880AC5C043FBA64AAC80C868CA2 | SHA256:743EEB3247A44B8544598EABE0FFAB10557FF4A5DA448B5889788C5C54C9A706 | |||
| 6560 | eagleget-2-1-6-50.exe | C:\Users\admin\AppData\Local\Temp\is-TVNQH.tmp\eagleget-2-1-6-50.tmp | executable | |
MD5:EB42E5720E09CD014694A22C86929F5E | SHA256:4DC2D414277E497490D2009F370051298BCCAA649D0A335B064269A0BB9BBBF3 | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\sqlite3.dll | executable | |
MD5:EE7E9A4CB1BC952E356145EB6306A6EE | SHA256:50F7C306C28A22CD277DAFFA5D3F28AC7CB4C561B260AA8C4626587F8E82F103 | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\CallbackCtrl.dll | executable | |
MD5:F07E819BA2E46A897CFABF816D7557B2 | SHA256:68F42A7823ED7EE88A5C59020AC52D4BBCADF1036611E96E470D986C8FAA172D | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\btn_complete.png | image | |
MD5:AF03B33CB3B3FCCE4B69E62CD1078DC6 | SHA256:A37B5AF0B4EC0C9598E0FD6570F4B4F60A4D9D9D10E589B93F509A60F04ACE55 | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\btn_n.png | image | |
MD5:66DEFF37283BCA24EA963AE3A3963B38 | SHA256:D9F0859F6A5648B0A9060200CC9A7534161E1B22844F631766E4E3540090790A | |||
| 6584 | eagleget-2-1-6-50.tmp | C:\Users\admin\AppData\Local\Temp\is-J7S13.tmp\bg_license.png | image | |
MD5:582FDA5363B76D1D022FFC35DC25D3E7 | SHA256:8D8698834690E763D378E7D4353B3B3353E01047C927AF4E66F829C61DC448B8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
35
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5208 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5208 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2776 | WerFault.exe | GET | 200 | 2.16.164.106:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2776 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6688 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5432 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6688 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5208 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5208 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.dropbox.com |
| shared |
watson.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7132 | net_updater32.exe | Potential Corporate Privacy Violation | ET POLICY Dropbox.com Offsite File Backup in Use |