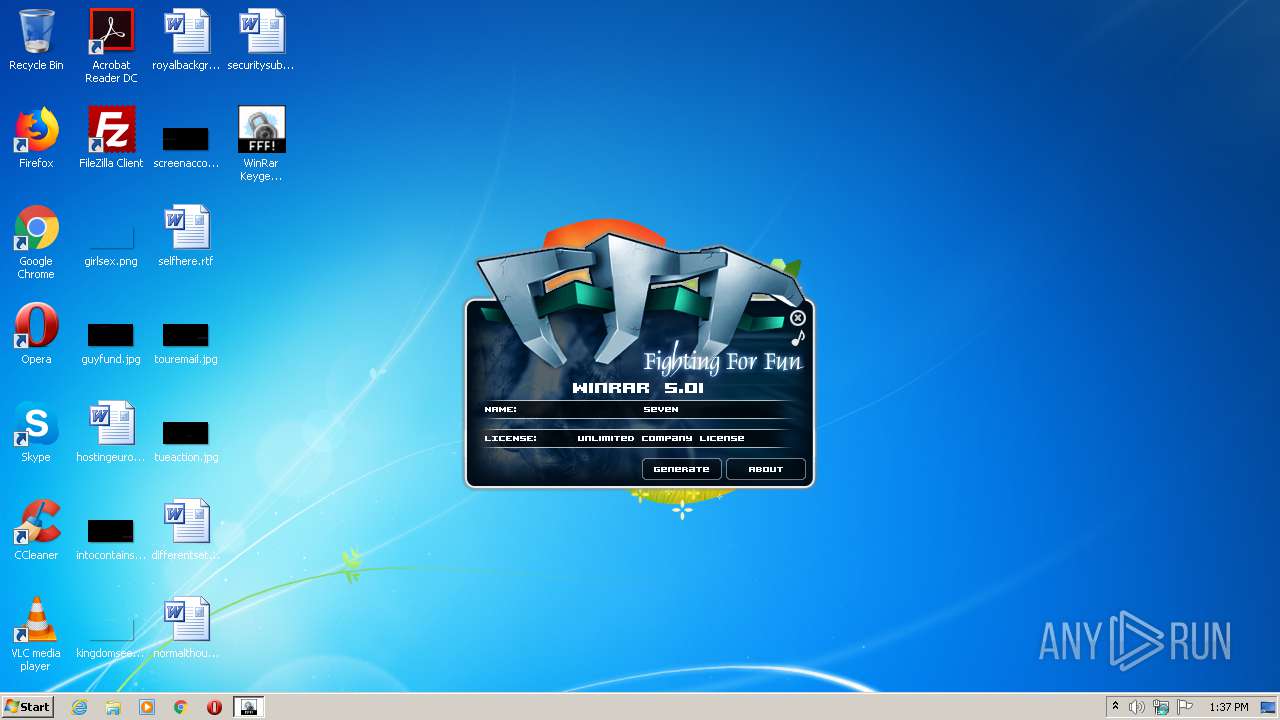
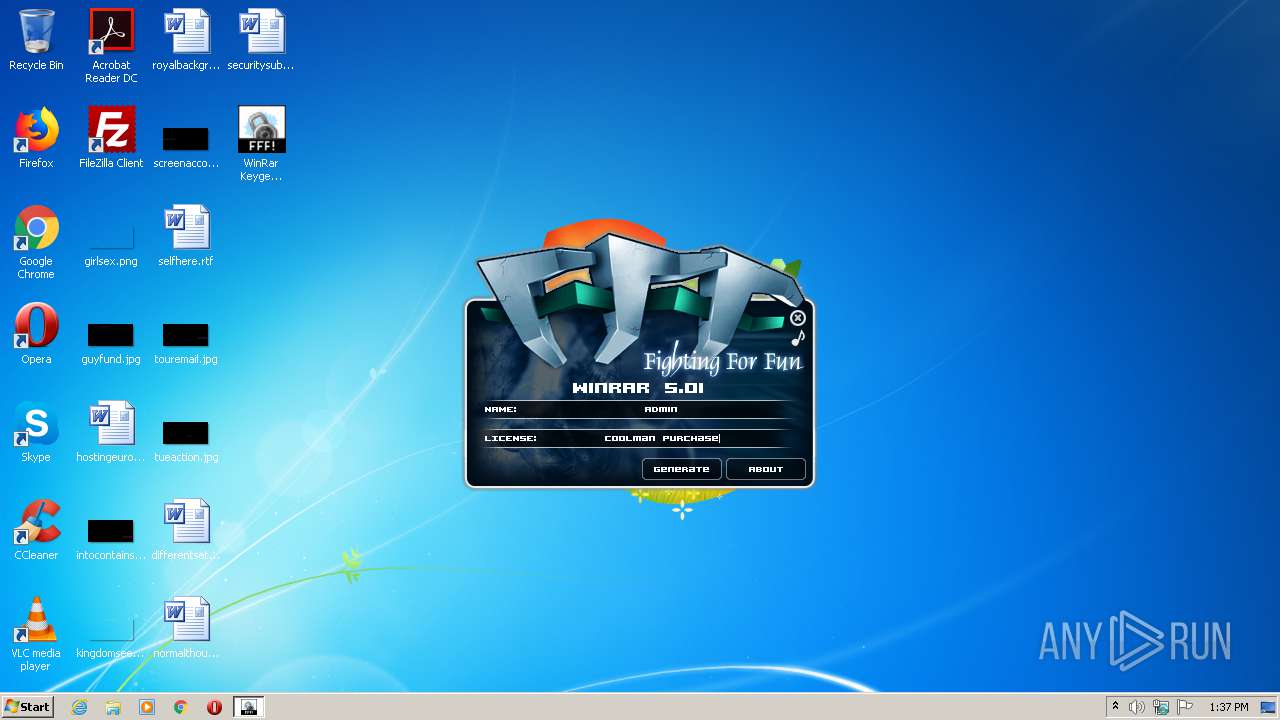
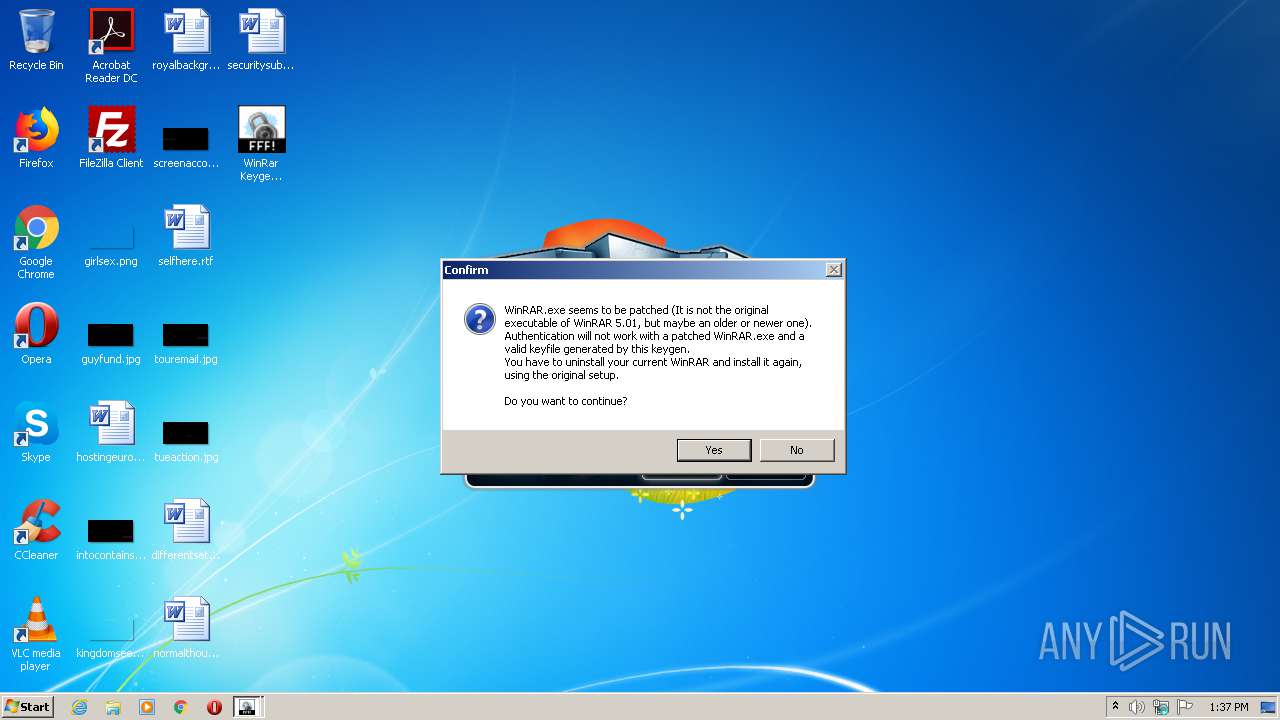
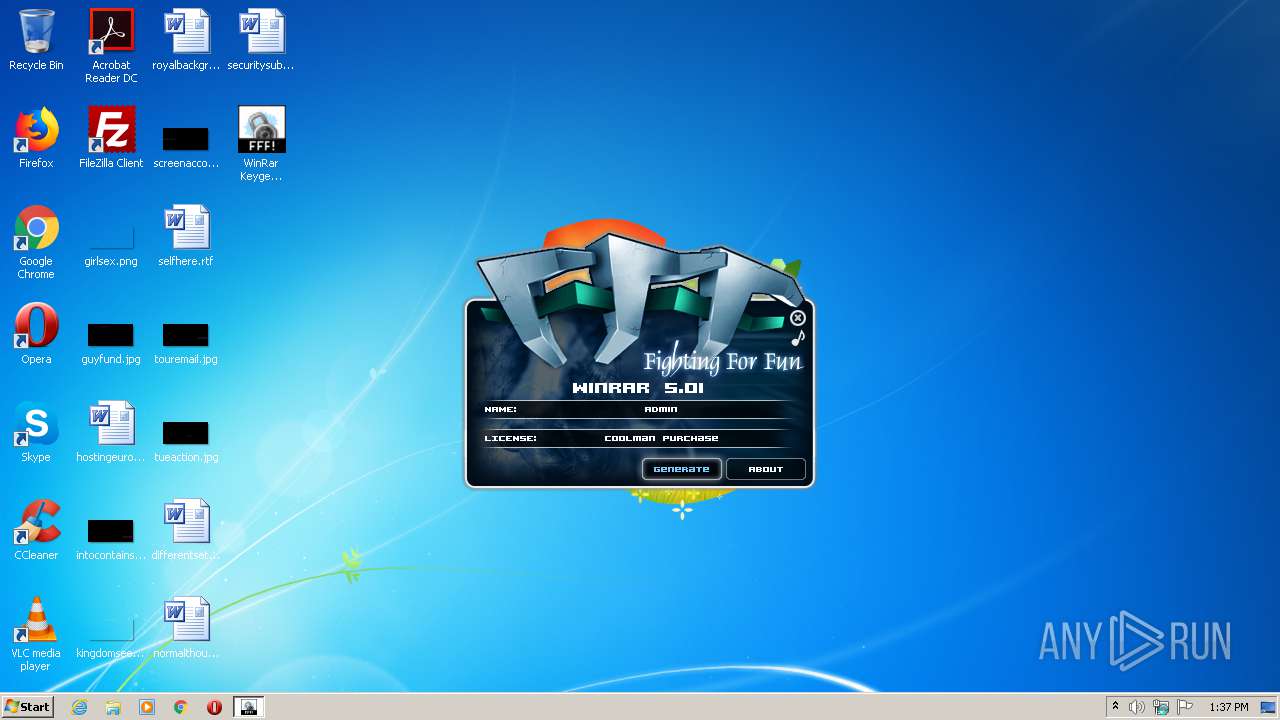
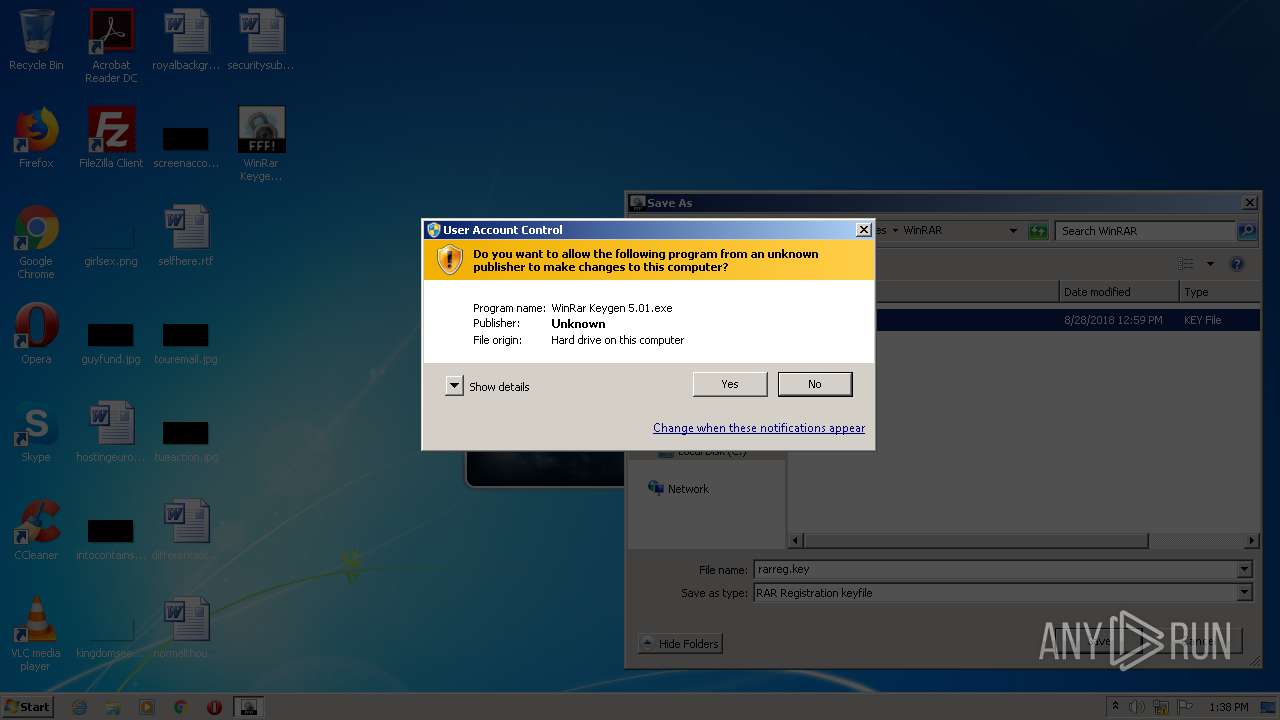
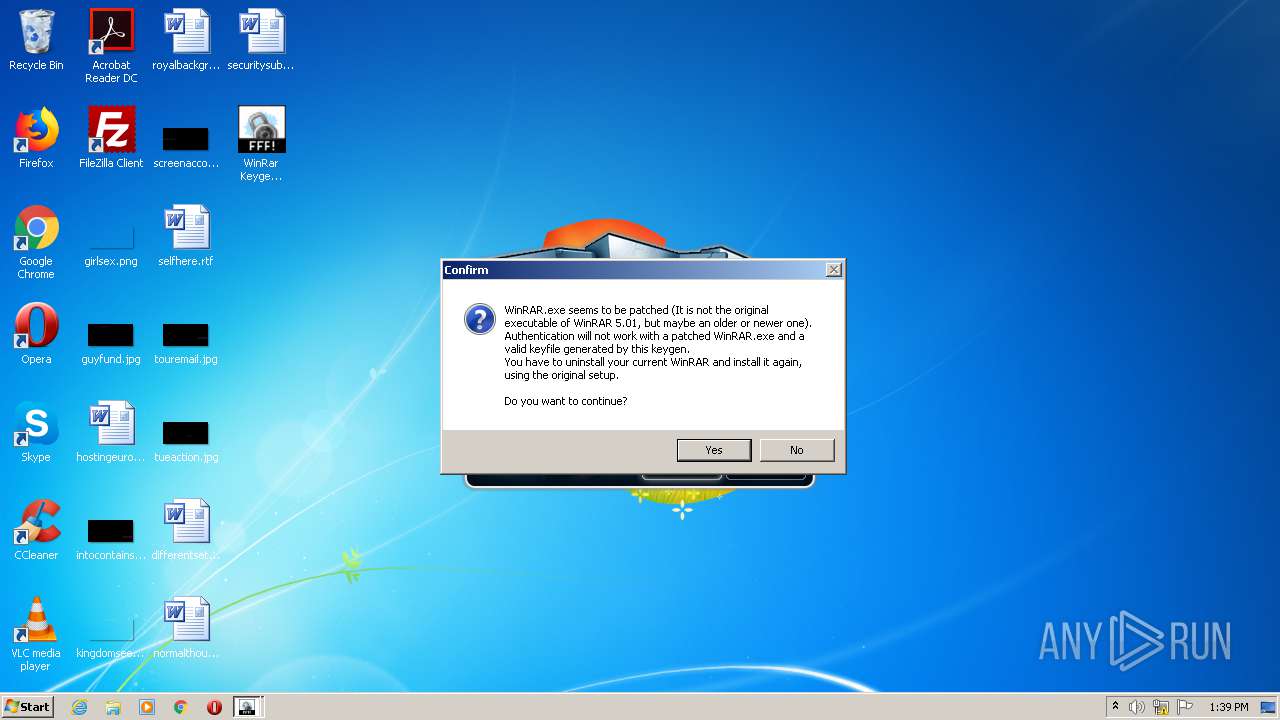
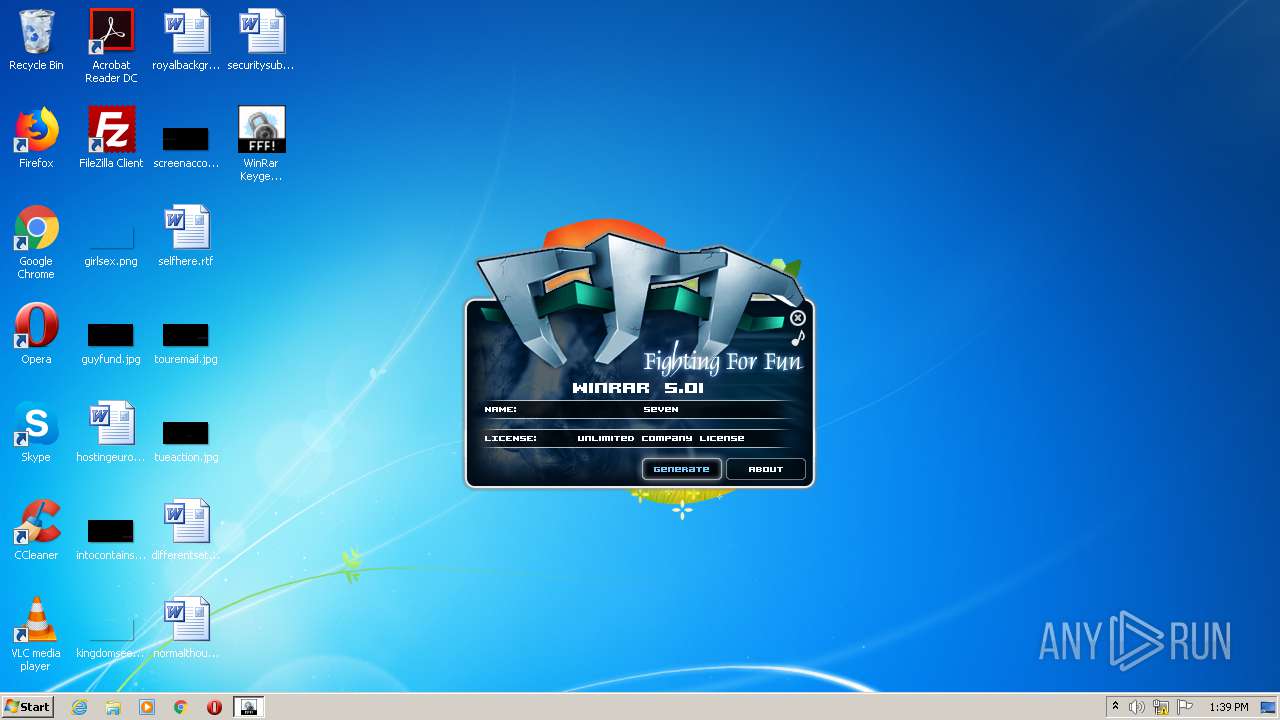
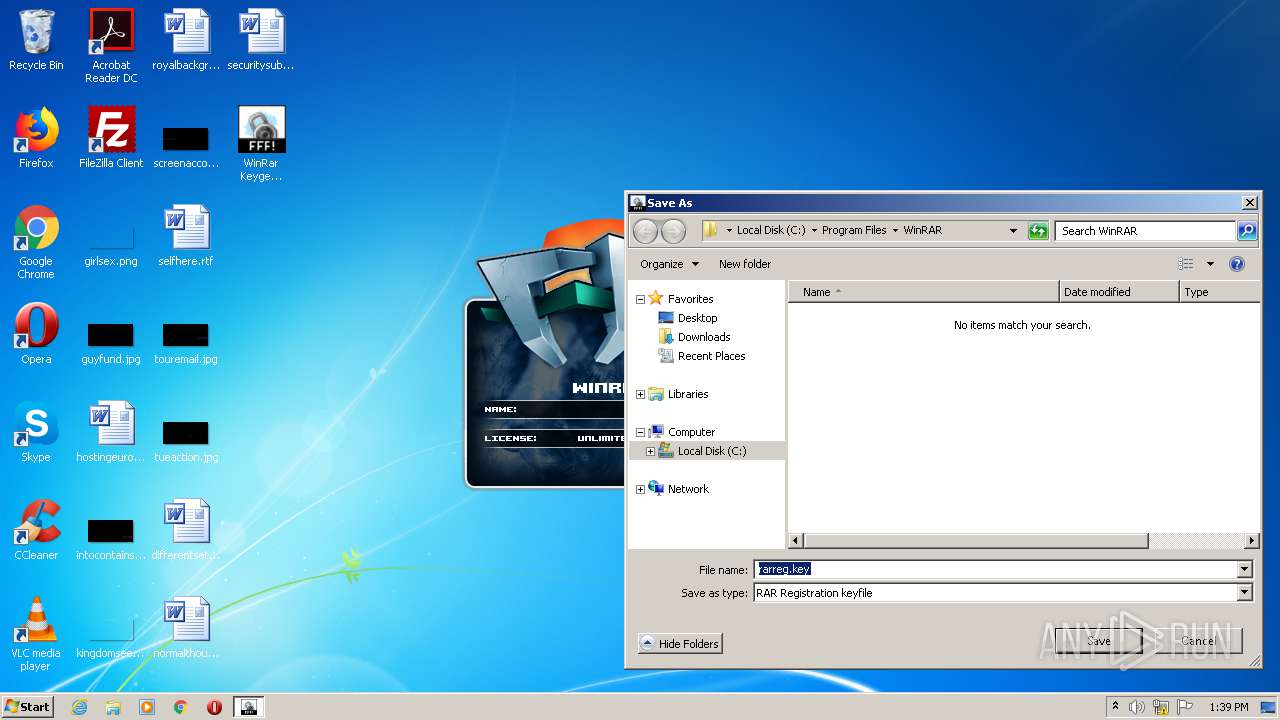
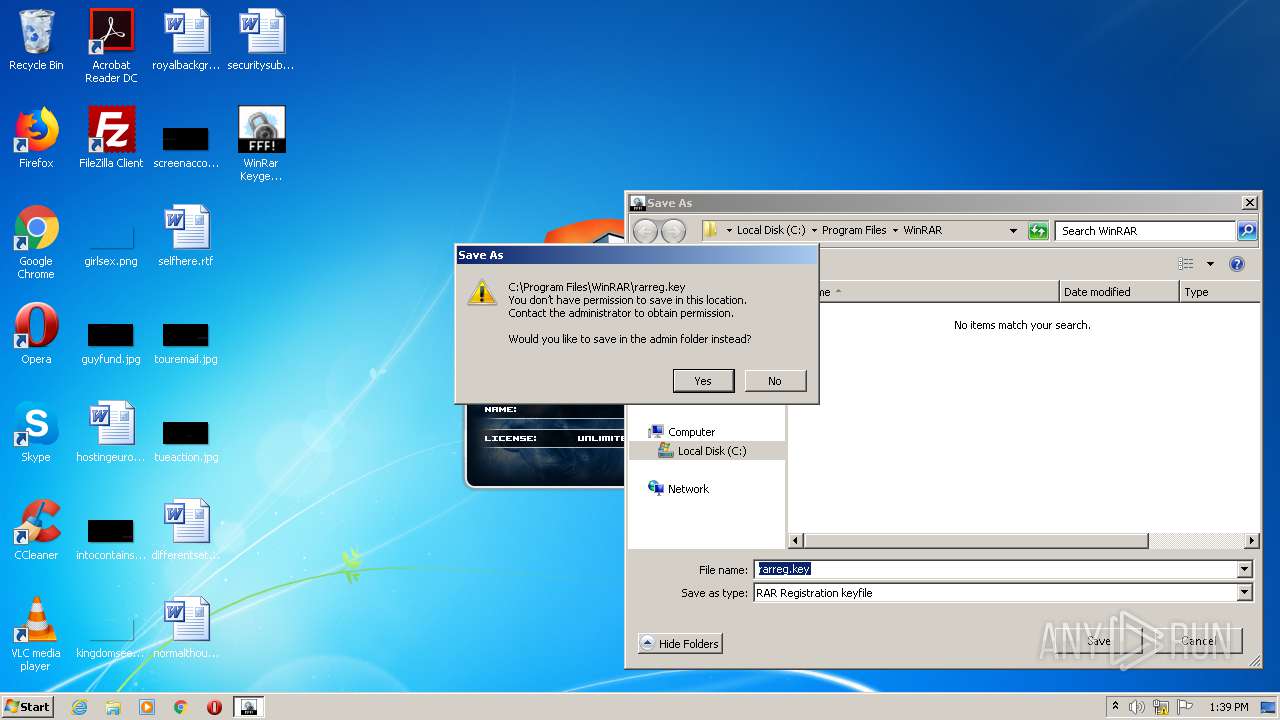
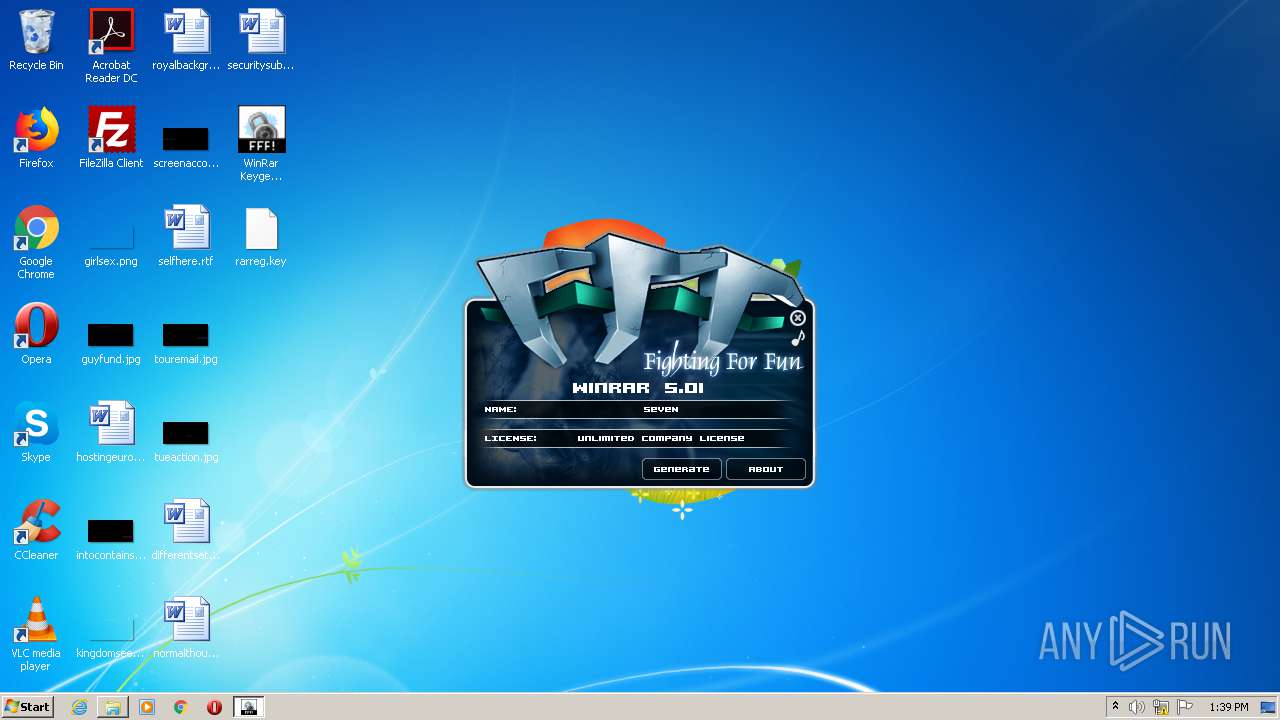
| File name: | WinRar Keygen 5.01.exe |
| Full analysis: | https://app.any.run/tasks/ae4f1da8-5900-4bb2-9cb1-79789b15d681 |
| Verdict: | Malicious activity |
| Analysis date: | October 05, 2020, 12:37:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, PECompact2 compressed |
| MD5: | 2257D9B1D98795C90AEEA996D98A8D9C |
| SHA1: | F2F388AB6B485B43BBBB5954F54F6B1585CA4EE8 |
| SHA256: | 144BD20A74A86304809B57A1E28595E0E172308A3D620874CAC5E160E7A7B488 |
| SSDEEP: | 6144:QNcD+22e7tJudIPFsb5zR0130g6hljhjrObGu:CcDL2e79PFY5101MtjqbG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- DllHost.exe (PID: 4020)
- DllHost.exe (PID: 664)
Reads Internet Cache Settings
- WinRAR.exe (PID: 2228)
Reads internet explorer settings
- WinRAR.exe (PID: 2228)
Creates files in the user directory
- WinRAR.exe (PID: 2228)
INFO
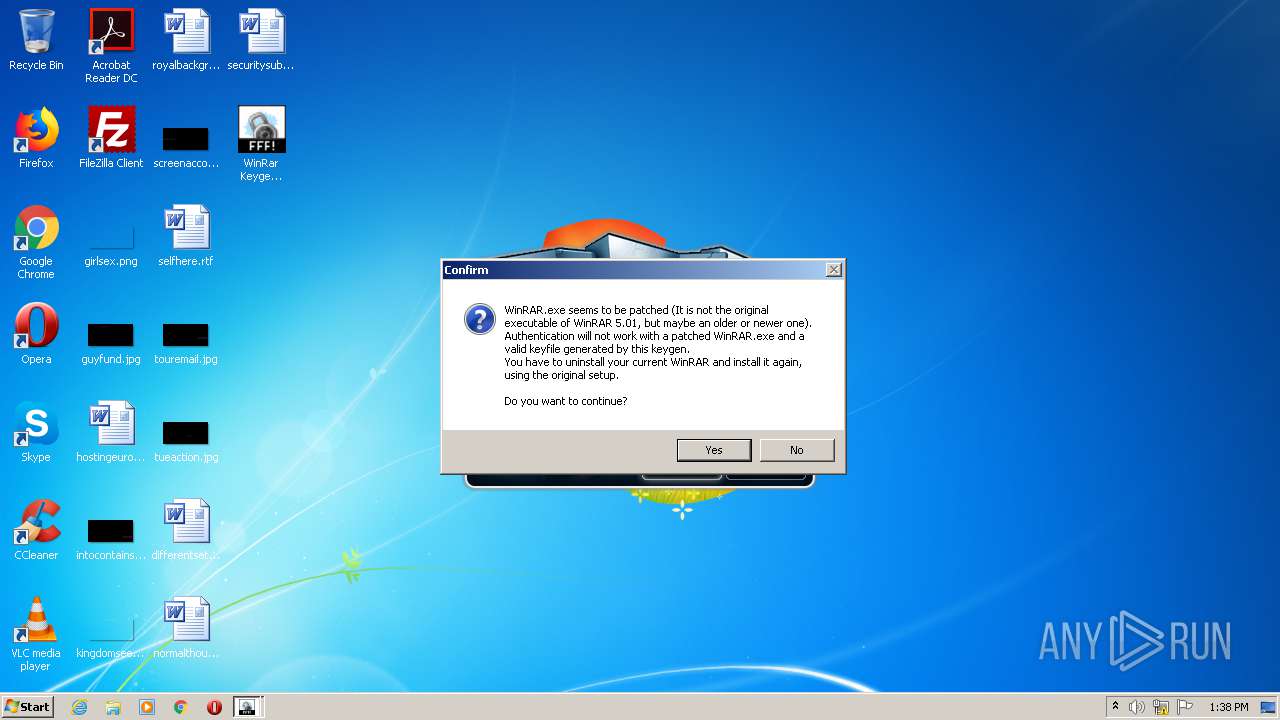
Manual execution by user
- WinRAR.exe (PID: 2228)
- WinRar Keygen 5.01.exe (PID: 2852)
- WinRAR.exe (PID: 3024)
- explorer.exe (PID: 2828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (v2.x) (51) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (35.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:04:06 16:44:53+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 86016 |
| InitializedDataSize: | 218624 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x959e |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 06-Apr-2014 14:44:53 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 2 |
| Time date stamp: | 06-Apr-2014 14:44:53 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00055000 | 0x00034000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99909 |
.rsrc | 0x00056000 | 0x00002000 | 0x00001A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 6.9655 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.79597 | 346 | Latin 1 / Western European | English - United States | RT_MANIFEST |
108 | 7.95329 | 105398 | Latin 1 / Western European | French - France | PNG |
109 | 1.81924 | 20 | Latin 1 / Western European | French - France | RT_GROUP_ICON |
111 | 0 | 3552 | Latin 1 / Western European | French - France | RT_RCDATA |
112 | 0 | 1443 | Latin 1 / Western European | French - France | PNG |
113 | 0 | 68526 | Latin 1 / Western European | French - France | RT_RCDATA |
Imports
kernel32.dll |
Total processes
49
Monitored processes
7
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2228 | "C:\Program Files\WinRAR\WinRAR.exe" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
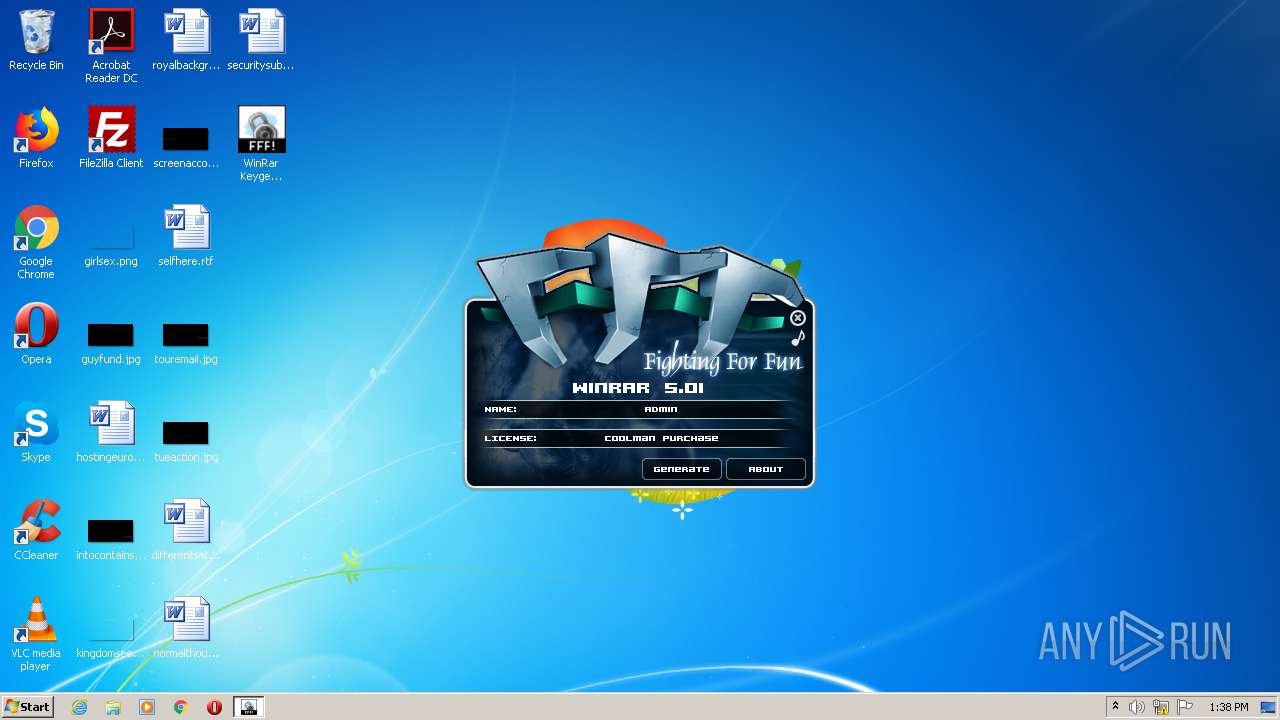
| 2680 | "C:\Users\admin\Desktop\WinRar Keygen 5.01.exe" | C:\Users\admin\Desktop\WinRar Keygen 5.01.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2828 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2852 | "C:\Users\admin\Desktop\WinRar Keygen 5.01.exe" | C:\Users\admin\Desktop\WinRar Keygen 5.01.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3024 | "C:\Program Files\WinRAR\WinRAR.exe" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 4020 | C:\Windows\system32\DllHost.exe /Processid:{3AD05575-8857-4850-9277-11B85BDB8E09} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 586
Read events
2 168
Write events
407
Delete events
11
Modification events
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | 0 |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C004400650073006B0074006F0070005C00570069006E0052006100720020004B0065007900670065006E00200035002E00300031002E00650078006500000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C00570069006E005200410052000000 | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\FirstFolder |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0700000001000000020000000B000000000000000A000000090000000800000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1 |
| Operation: | write | Name: | 1 |
Value: 52003100000000001E4D9C6E1020526F616D696E67003C0008000400EFBE454B814A1E4D9C6E2A0000007D01000000000200000000000000000000000000000052006F0061006D0069006E006700000016000000 | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1 |
| Operation: | write | Name: | MRUListEx |
Value: 0100000000000000FFFFFFFF | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\1 |
| Operation: | write | Name: | 0 |
Value: 50003100000000001C4DC35E102057696E52415200003A0008000400EFBE1C4DC35E1C4DC35E2A00000007C40000000002000000000000000000000000000000570069006E00520041005200000016000000 | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\1 |
| Operation: | write | Name: | MRUListEx |
Value: 00000000FFFFFFFF | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2680) WinRar Keygen 5.01.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\7\1\1\0 |
| Operation: | write | Name: | NodeSlot |
Value: 127 | |||
Executable files
0
Suspicious files
13
Text files
22
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CabC5A7.tmp | — | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\TarC5A8.tmp | — | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C14EF41B12D2E3FC98A6E6C6AAEDB98F | binary | |
MD5:— | SHA256:— | |||
| 4020 | DllHost.exe | C:\$RECYCLE.BIN\S-1-5-21-1302019708-1500728564-335382590-1000\$I36D6XY.key | binary | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\logo-winrar[1].gif | image | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\basic[1].css | text | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | der | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C14EF41B12D2E3FC98A6E6C6AAEDB98F | der | |
MD5:— | SHA256:— | |||
| 2228 | WinRAR.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\BJE1O2DT.htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
8
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2228 | WinRAR.exe | GET | 200 | 95.101.72.176:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
2228 | WinRAR.exe | GET | 200 | 95.101.72.175:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgQRczpDruT6kd%2FDEOV3hncMjA%3D%3D | unknown | der | 527 b | whitelisted |
2228 | WinRAR.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2228 | WinRAR.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAyDrs7o0RpNCAAAAABXoKo%3D | US | der | 471 b | whitelisted |
2228 | WinRAR.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2228 | WinRAR.exe | GET | 200 | 172.217.22.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAyDrs7o0RpNCAAAAABXoKo%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2228 | WinRAR.exe | 51.195.68.173:443 | notifier.win-rar.com | — | GB | suspicious |
2228 | WinRAR.exe | 95.101.72.176:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2228 | WinRAR.exe | 95.101.72.175:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | whitelisted |
2228 | WinRAR.exe | 216.58.212.174:443 | www.google-analytics.com | Google Inc. | US | whitelisted |
2228 | WinRAR.exe | 216.58.207.72:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
2228 | WinRAR.exe | 172.217.22.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notifier.win-rar.com |
| suspicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
www.google-analytics.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |