| File name: | utau0419cInstaller.exe |
| Full analysis: | https://app.any.run/tasks/177ffc19-90eb-4b01-9f62-2ebcd36b113f |
| Verdict: | Malicious activity |
| Analysis date: | July 31, 2024, 21:21:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, MS CAB-Installer self-extracting archive |
| MD5: | B3FBD653A84017E567D7CFC7C9D14456 |
| SHA1: | A39E627F0D243B21B7F14764F99F8898B2C13F5B |
| SHA256: | 144B853BD7066A736EF8347118CF82C18B7A5BE313F7EDF66571E5D9816828AD |
| SSDEEP: | 98304:NWJHHJ2g4xL/oU2GjYxXfD0Z8mV0C0FW4+VUjsIxHv6Z6XcQnJptnnwwjXaPpUdG:8N2CbSg02 |
MALICIOUS
Drops the executable file immediately after the start
- utau0419cInstaller.exe (PID: 6488)
- msiexec.exe (PID: 6676)
Changes the autorun value in the registry
- utau0419cInstaller.exe (PID: 6488)
SUSPICIOUS
Process drops legitimate windows executable
- utau0419cInstaller.exe (PID: 6488)
- msiexec.exe (PID: 6676)
Starts a Microsoft application from unusual location
- utau0419cInstaller.exe (PID: 6488)
- utau0419cInstaller.exe (PID: 6440)
Executable content was dropped or overwritten
- utau0419cInstaller.exe (PID: 6488)
Reads the Windows owner or organization settings
- setup.exe (PID: 6640)
- msiexec.exe (PID: 6676)
Executes as Windows Service
- VSSVC.exe (PID: 2628)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 5552)
- msiexec.exe (PID: 5944)
- msiexec.exe (PID: 300)
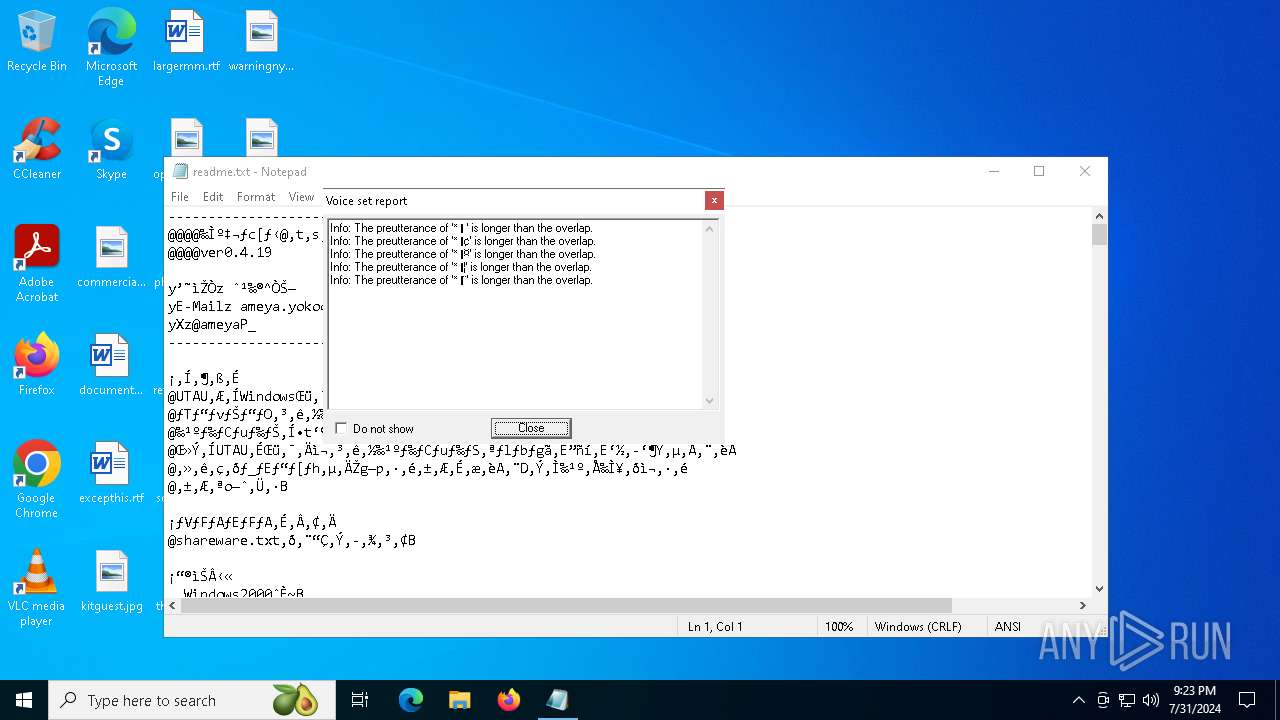
Start notepad (likely ransomware note)
- utau.exe (PID: 6712)
Reads security settings of Internet Explorer
- utau.exe (PID: 6712)
Reads the date of Windows installation
- utau.exe (PID: 6712)
Executing commands from a ".bat" file
- utau.exe (PID: 6712)
Starts CMD.EXE for commands execution
- utau.exe (PID: 6712)
INFO
Reads the computer name
- msiexec.exe (PID: 6676)
- setup.exe (PID: 6640)
- utau0419cInstaller.exe (PID: 6488)
- TextInputHost.exe (PID: 5632)
- utau.exe (PID: 6712)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6676)
Create files in a temporary directory
- setup.exe (PID: 6640)
- utau0419cInstaller.exe (PID: 6488)
- utau.exe (PID: 6712)
- wavtool.exe (PID: 3140)
- wavtool.exe (PID: 1120)
- wavtool.exe (PID: 1288)
- wavtool.exe (PID: 6616)
- wavtool.exe (PID: 2396)
- wavtool.exe (PID: 2228)
- wavtool.exe (PID: 5852)
- wavtool.exe (PID: 6668)
- wavtool.exe (PID: 1224)
- wavtool.exe (PID: 4024)
- wavtool.exe (PID: 3696)
- wavtool.exe (PID: 3660)
- wavtool.exe (PID: 3568)
- wavtool.exe (PID: 3552)
- wavtool.exe (PID: 4192)
- wavtool.exe (PID: 6268)
- wavtool.exe (PID: 6992)
- wavtool.exe (PID: 5244)
- wavtool.exe (PID: 6332)
- wavtool.exe (PID: 6460)
- wavtool.exe (PID: 6872)
- wavtool.exe (PID: 6476)
- wavtool.exe (PID: 4236)
- wavtool.exe (PID: 6920)
- wavtool.exe (PID: 7044)
- wavtool.exe (PID: 7132)
- wavtool.exe (PID: 6452)
Checks supported languages
- setup.exe (PID: 6640)
- utau0419cInstaller.exe (PID: 6488)
- msiexec.exe (PID: 6676)
- TextInputHost.exe (PID: 5632)
- utau.exe (PID: 6712)
- wavtool.exe (PID: 3140)
- wavtool.exe (PID: 4192)
- wavtool.exe (PID: 2228)
- wavtool.exe (PID: 1288)
- wavtool.exe (PID: 5852)
- wavtool.exe (PID: 1120)
- wavtool.exe (PID: 6616)
- wavtool.exe (PID: 6268)
- wavtool.exe (PID: 2396)
- wavtool.exe (PID: 3660)
- wavtool.exe (PID: 6668)
- wavtool.exe (PID: 3568)
- wavtool.exe (PID: 1224)
- wavtool.exe (PID: 4024)
- wavtool.exe (PID: 3696)
- wavtool.exe (PID: 3552)
- wavtool.exe (PID: 6920)
- wavtool.exe (PID: 7132)
- wavtool.exe (PID: 6460)
- wavtool.exe (PID: 5244)
- wavtool.exe (PID: 6992)
- wavtool.exe (PID: 6332)
- wavtool.exe (PID: 6476)
- wavtool.exe (PID: 6872)
- wavtool.exe (PID: 4236)
- wavtool.exe (PID: 7044)
- wavtool.exe (PID: 6452)
Creates a software uninstall entry
- msiexec.exe (PID: 6676)
Reads mouse settings
- msiexec.exe (PID: 5944)
- utau.exe (PID: 6712)
Manual execution by a user
- utau.exe (PID: 6712)
Reads Windows Product ID
- utau.exe (PID: 6712)
Creates files or folders in the user directory
- utau.exe (PID: 6712)
- msiexec.exe (PID: 6676)
Process checks computer location settings
- utau.exe (PID: 6712)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1999:09:25 11:18:31+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 5.12 |
| CodeSize: | 34304 |
| InitializedDataSize: | 6825472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x283d |
| OSVersion: | 5 |
| ImageVersion: | 5 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.0.2920.0 |
| ProductVersionNumber: | 5.0.2920.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Japanese |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 キャビネット自己展開ツール |
| FileVersion: | 5.00.2920.0000 |
| InternalName: | Wextract |
| LegalCopyright: | Copyright (C) Microsoft Corp. 1981-1999 |
| OriginalFileName: | WEXTRACT.EXE |
| ProductName: | Microsoft(R) Windows (R) 2000 Operating System |
| ProductVersion: | 5.00.2920.0000 |
Total processes
190
Monitored processes
42
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Windows\syswow64\MsiExec.exe" /Y "C:\WINDOWS\SysWOW64\COMDLG32.OCX" | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | "C:\Program Files (x86)\UTAU\wavtool.exe" "temp.wav" "C:\Program Files (x86)\UTAU\voice\uta\R.wav" 0 480@120+.0 0 0 | C:\Program Files (x86)\UTAU\wavtool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1140 | C:\WINDOWS\system32\cmd.exe /c C:\Users\admin\AppData\Local\Temp\utau1\temp.bat | C:\Windows\SysWOW64\cmd.exe | — | utau.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | "C:\Program Files (x86)\UTAU\wavtool.exe" "temp.wav" "C:\Program Files (x86)\UTAU\voice\uta\R.wav" 0 480@120+.0 0 0 | C:\Program Files (x86)\UTAU\wavtool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1288 | "C:\Program Files (x86)\UTAU\wavtool.exe" "temp.wav" "C:\Program Files (x86)\UTAU\voice\uta\R.wav" 0 480@120+.0 0 0 | C:\Program Files (x86)\UTAU\wavtool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2228 | "C:\Program Files (x86)\UTAU\wavtool.exe" "temp.wav" "C:\Program Files (x86)\UTAU\voice\uta\R.wav" 0 480@120+.0 0 0 | C:\Program Files (x86)\UTAU\wavtool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2396 | "C:\Program Files (x86)\UTAU\wavtool.exe" "temp.wav" "C:\Program Files (x86)\UTAU\voice\uta\R.wav" 0 480@120+.0 0 0 | C:\Program Files (x86)\UTAU\wavtool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2628 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | "C:\Program Files (x86)\UTAU\wavtool.exe" "temp.wav" "C:\Program Files (x86)\UTAU\voice\uta\R.wav" 0 480@120+.0 0 0 | C:\Program Files (x86)\UTAU\wavtool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3552 | "C:\Program Files (x86)\UTAU\wavtool.exe" "temp.wav" "C:\Program Files (x86)\UTAU\voice\uta\R.wav" 0 480@120+.0 0 0 | C:\Program Files (x86)\UTAU\wavtool.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
34 311
Read events
33 403
Write events
819
Delete events
89
Modification events
| (PID) Process: | (6488) utau0419cInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (6640) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6640) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6640) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6640) setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (6676) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000048F736BB8FE3DA01141A0000A4120000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6676) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000048F736BB8FE3DA01141A0000A4120000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6676) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000054AF79BB8FE3DA01141A0000A4120000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6676) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000054AF79BB8FE3DA01141A0000A4120000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6676) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000096327CBB8FE3DA01141A0000A4120000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
22
Suspicious files
228
Text files
68
Unknown types
80
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
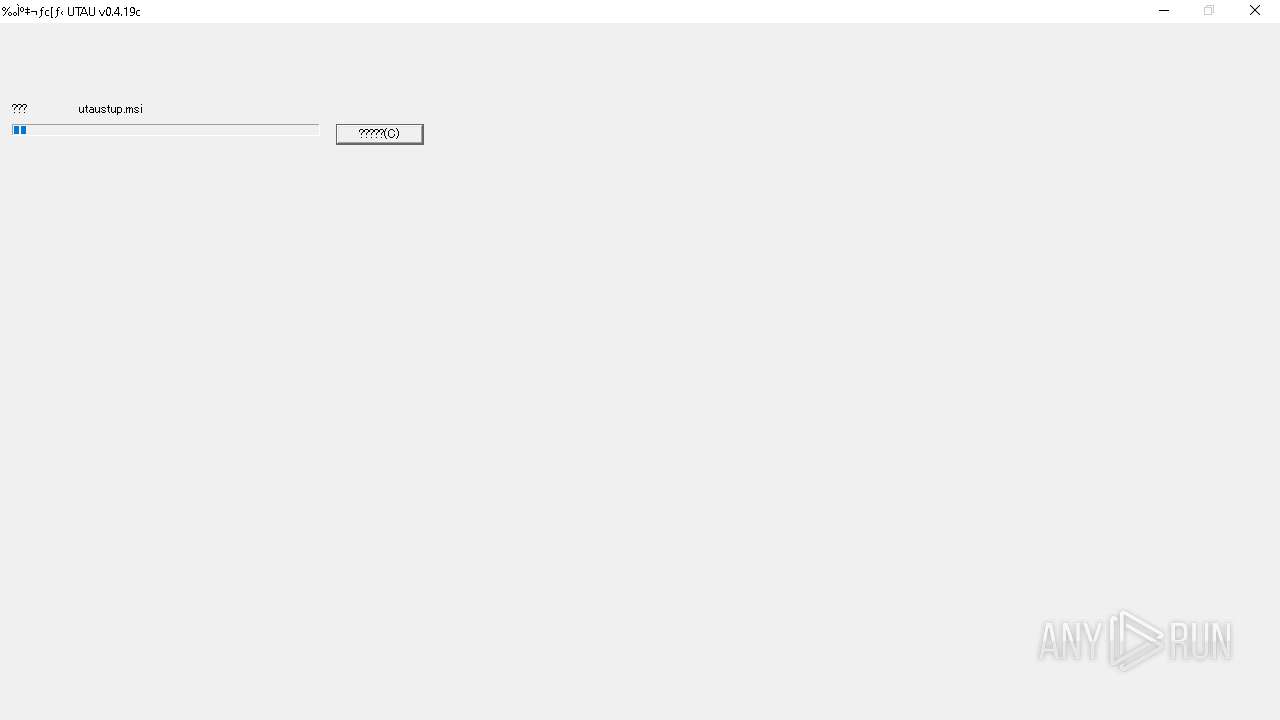
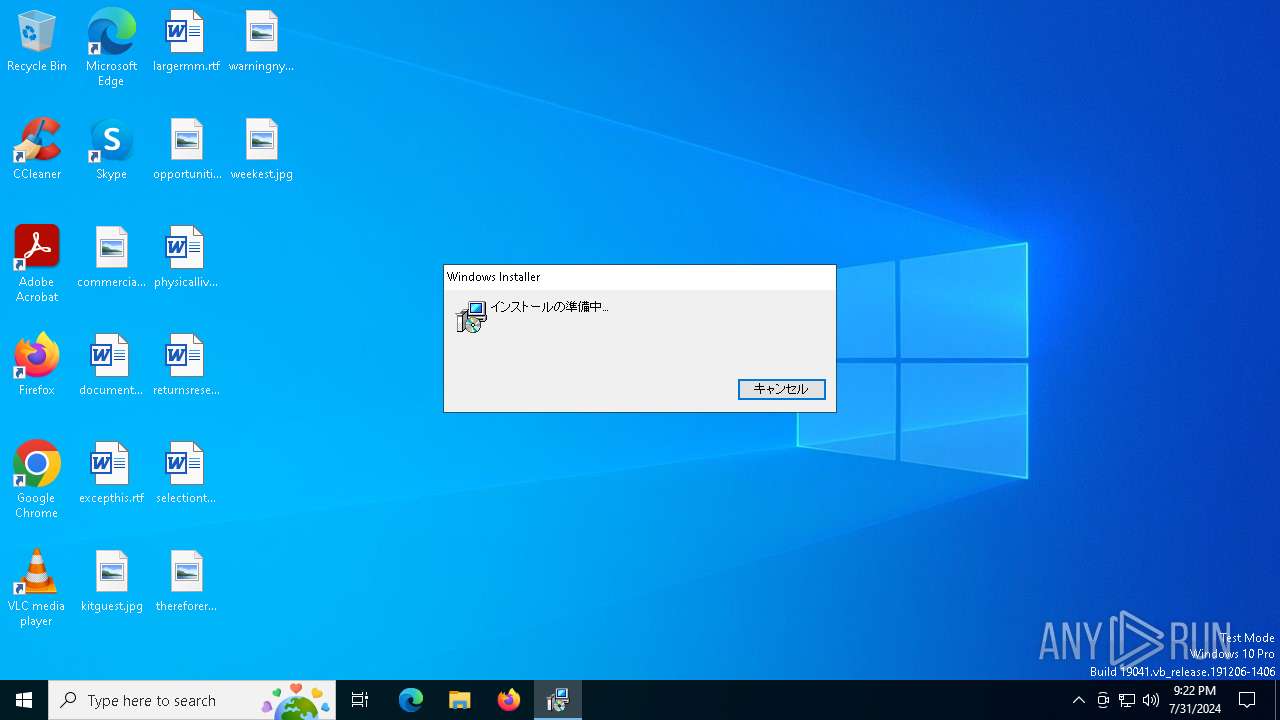
| 6488 | utau0419cInstaller.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\utaustup.msi | — | |
MD5:— | SHA256:— | |||
| 6676 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6676 | msiexec.exe | C:\Windows\Installer\ecfaf.msi | — | |
MD5:— | SHA256:— | |||
| 6676 | msiexec.exe | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\ngen.log | text | |
MD5:7B176DC14BDF74A995FE10A894D1CE31 | SHA256:2EDE3B4DEDFF90A9524B38B2740A3023E42A9CED398833B57B136F8C5181056A | |||
| 6676 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:B361C92B23023826A161255521488888 | SHA256:CCEDAB8DE53E813C81F13BE50DD041BB5DE1352D8597256A7739EB6C9D9204CA | |||
| 6676 | msiexec.exe | C:\Windows\Temp\~DF9A8405D5BC786212.TMP | binary | |
MD5:4324925E4EDDF3DCC3EE26FA9EC4F1F4 | SHA256:FB4F1DDCEBFE8FD0B47E9753B456EF044D5EDAA6CB37248AC04DE7AE94645FA8 | |||
| 6676 | msiexec.exe | C:\Windows\Temp\~DFCE5C5DCC54DCA569.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 6488 | utau0419cInstaller.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\setup.exe | executable | |
MD5:D60900A7B0FFF3BD9F109B3CC00F7804 | SHA256:8F1B93D05B2CD046F87F10ED5C11430BDE70439CAF34DC6BB81B12AE2D25EB9F | |||
| 6676 | msiexec.exe | C:\Program Files (x86)\UTAU\voice\uta\ろ_wav.frq | binary | |
MD5:1CF4597D1E670F1E94E1C8E92CC6BAC8 | SHA256:C472826EAA4FC069A596CDCC4B68845DE4E6CA9CAC582090BF31D12DFD3BBC96 | |||
| 6676 | msiexec.exe | C:\Program Files (x86)\UTAU\voice\uta\すぃ.wav | binary | |
MD5:5A23D8468A54F45949678020A6A10578 | SHA256:9E214B7D8662AE7A7DC5D5F4A2D00437359E59189E1FF8810D9C7F95680AE51A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
61
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
640 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
640 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6904 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6952 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5484 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4936 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
640 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
640 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |