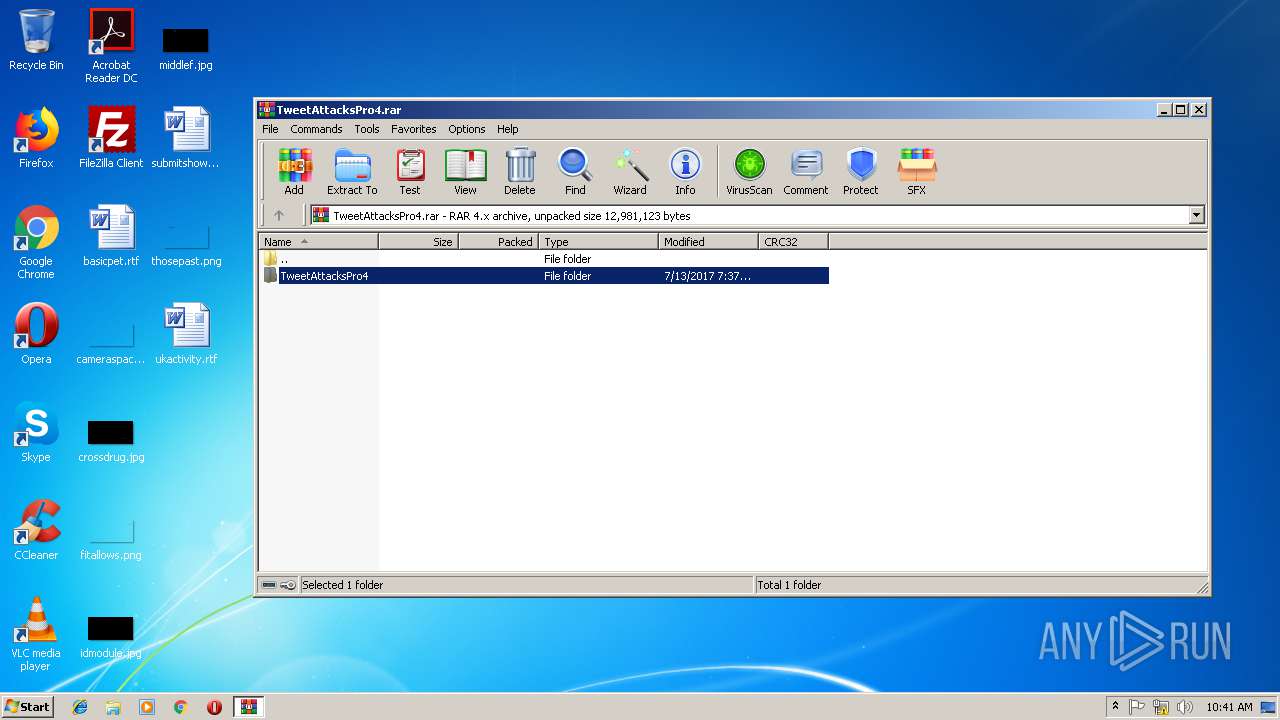
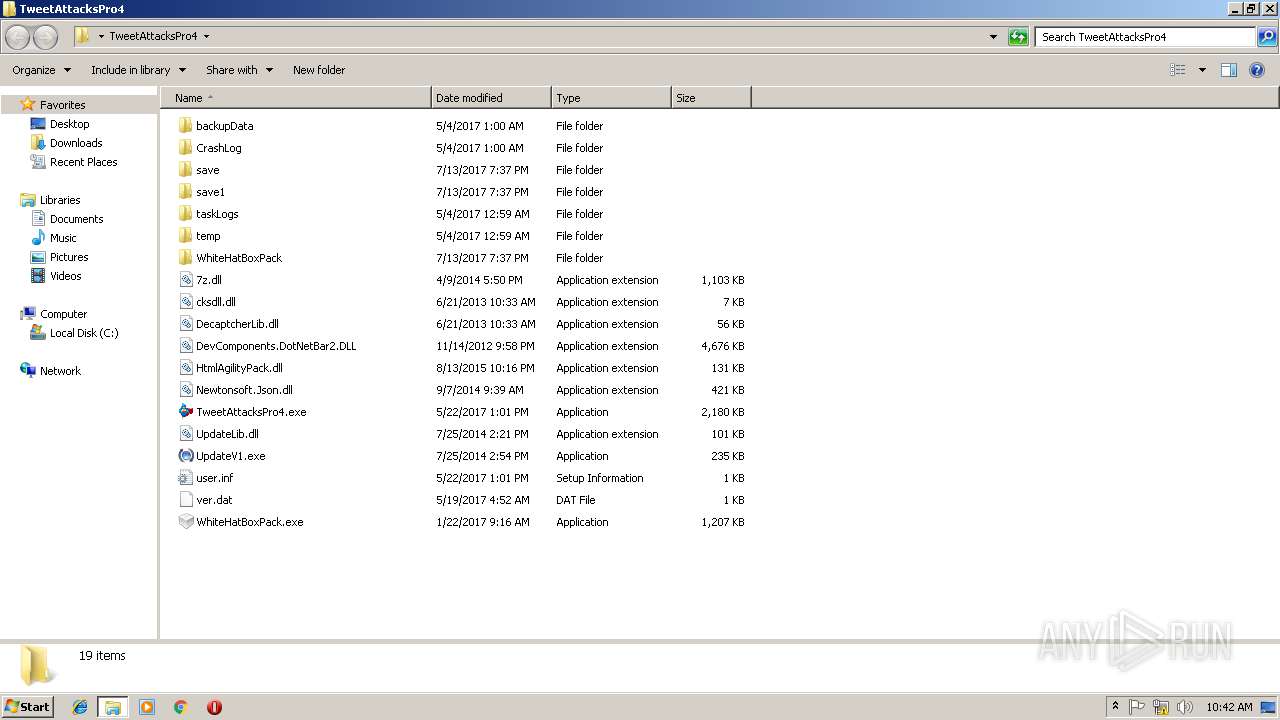
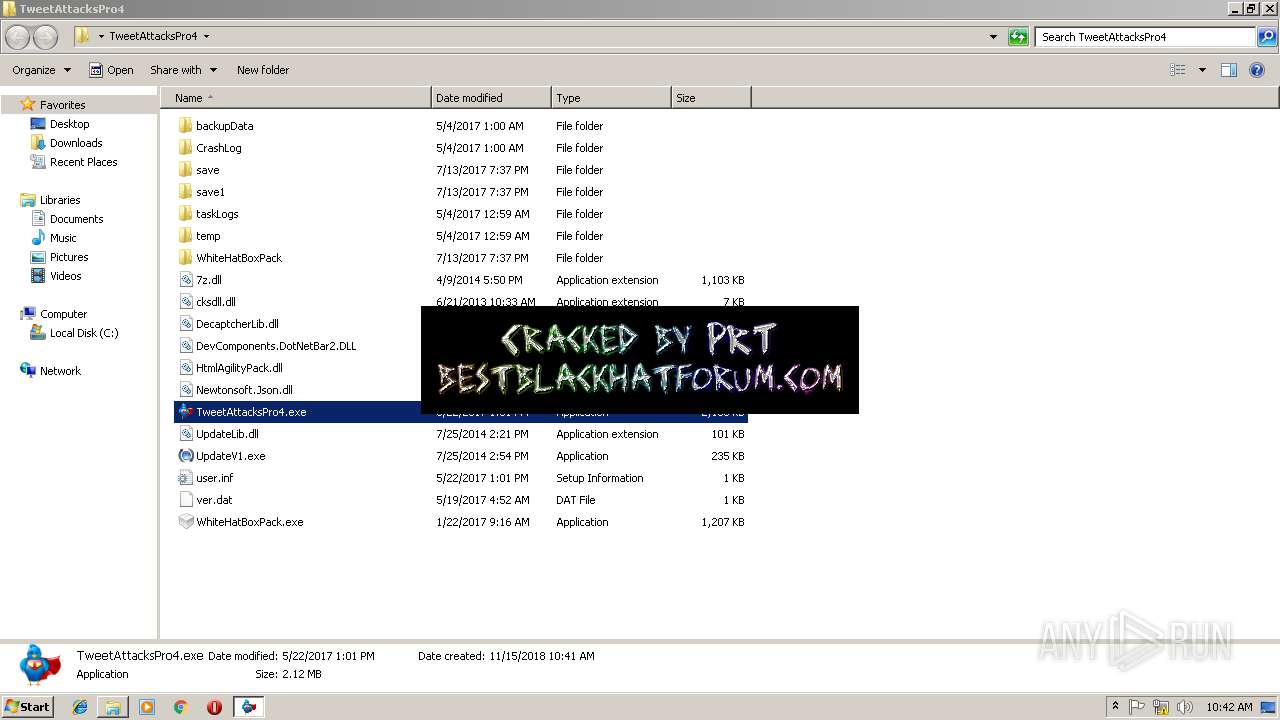
| File name: | TweetAttacksPro4.rar |
| Full analysis: | https://app.any.run/tasks/50325e36-0eac-4e2f-be8d-0c2c91f5784d |
| Verdict: | Malicious activity |
| Analysis date: | November 15, 2018, 10:41:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 961CDBB52D757B120809B1766E57C958 |
| SHA1: | 420545D05A9A09988EAE262D913D1E1653A3DC8D |
| SHA256: | 1446815D1229D1F88DAC3935E975EFA1727111E597A14593EF2287FE01F64AF5 |
| SSDEEP: | 98304:NhinMlLoPFXvfAu3WVzBUyuAlilAjDLibzLTe8G96beBXMhiqTW4haLFTjb1cVL8:NjlLoPFXvfxGJF5ilAjs3QUU8DW4Ybq+ |
MALICIOUS
Loads dropped or rewritten executable
- TweetAttacksPro4.exe (PID: 3968)
- SearchProtocolHost.exe (PID: 2124)
- TweetAttacksPro4.exe (PID: 3952)
Application was dropped or rewritten from another process
- TweetAttacksPro4.exe (PID: 3952)
- TweetAttacksPro4.exe (PID: 3968)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3360)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 428915 |
|---|---|
| UncompressedSize: | 1129472 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2014:04:09 17:50:29 |
| PackingMethod: | Normal |
| ArchivedFileName: | TweetAttacksPro4\7z.dll |
Total processes
36
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2124 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3360 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\TweetAttacksPro4.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3952 | "C:\Users\admin\Desktop\TweetAttacksPro4\TweetAttacksPro4.exe" | C:\Users\admin\Desktop\TweetAttacksPro4\TweetAttacksPro4.exe | explorer.exe | ||||||||||||
User: admin Company: WhiteHatBox Integrity Level: MEDIUM Description: Tweet Attacks Pro 4 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3968 | "C:\Users\admin\Desktop\TweetAttacksPro4\TweetAttacksPro4.exe" | C:\Users\admin\Desktop\TweetAttacksPro4\TweetAttacksPro4.exe | explorer.exe | ||||||||||||
User: admin Company: WhiteHatBox Integrity Level: MEDIUM Description: Tweet Attacks Pro 4 Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
865
Read events
830
Write events
35
Delete events
0
Modification events
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TweetAttacksPro4.rar | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3360) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2124) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2124) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
11
Suspicious files
14
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\save\tasks\T1437030201831\T1437030201831.dat | binary | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\cksdll.dll | executable | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\save\GFollowingFollowersPageInfo.dat | text | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\save\GTAPTaskIdDic.dat | pgc | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\save\GAccountCategoryInfoDic.dat | text | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\save\tasks\T1436739310089\T1436739310089.dat | binary | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\save\tasks\T1436777008401\T1436777008401.dat | binary | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\save\tasks\T1437030932356\T1437030932356.dat | binary | |
MD5:— | SHA256:— | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\7z.dll | executable | |
MD5:42EDF51C86E726F00379CCBDAD2BC796 | SHA256:F7E6FB7F23AC191CCAE310DEAEA112D03A17D507755D3E041D4213C02AD7BE9D | |||
| 3360 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3360.989\TweetAttacksPro4\Newtonsoft.Json.dll | executable | |
MD5:FBD7CC5869DFB0E2F34EF27F6C459D9F | SHA256:BA03235CAE5CF39386BE73D8520AC33A6E2709F878EA58218AB6F7B82AB458B1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3968 | TweetAttacksPro4.exe | GET | — | 120.25.67.116:80 | http://www.imtopsoft.com/TwitterAttacksProII/msg.html | CN | — | — | unknown |
3952 | TweetAttacksPro4.exe | GET | — | 120.25.67.116:80 | http://www.imtopsoft.com/TwitterAttacksProII/msg.html | CN | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3968 | TweetAttacksPro4.exe | 120.25.67.116:80 | www.imtopsoft.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3952 | TweetAttacksPro4.exe | 120.25.67.116:80 | www.imtopsoft.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.imtopsoft.com |
| unknown |
seoc.ga |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ga Domain |
Process | Message |
|---|---|
TweetAttacksPro4.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|
TweetAttacksPro4.exe |
%s------------------------------------------------
--- Themida Professional ---
--- (c)2012 Oreans Technologies ---
------------------------------------------------
|