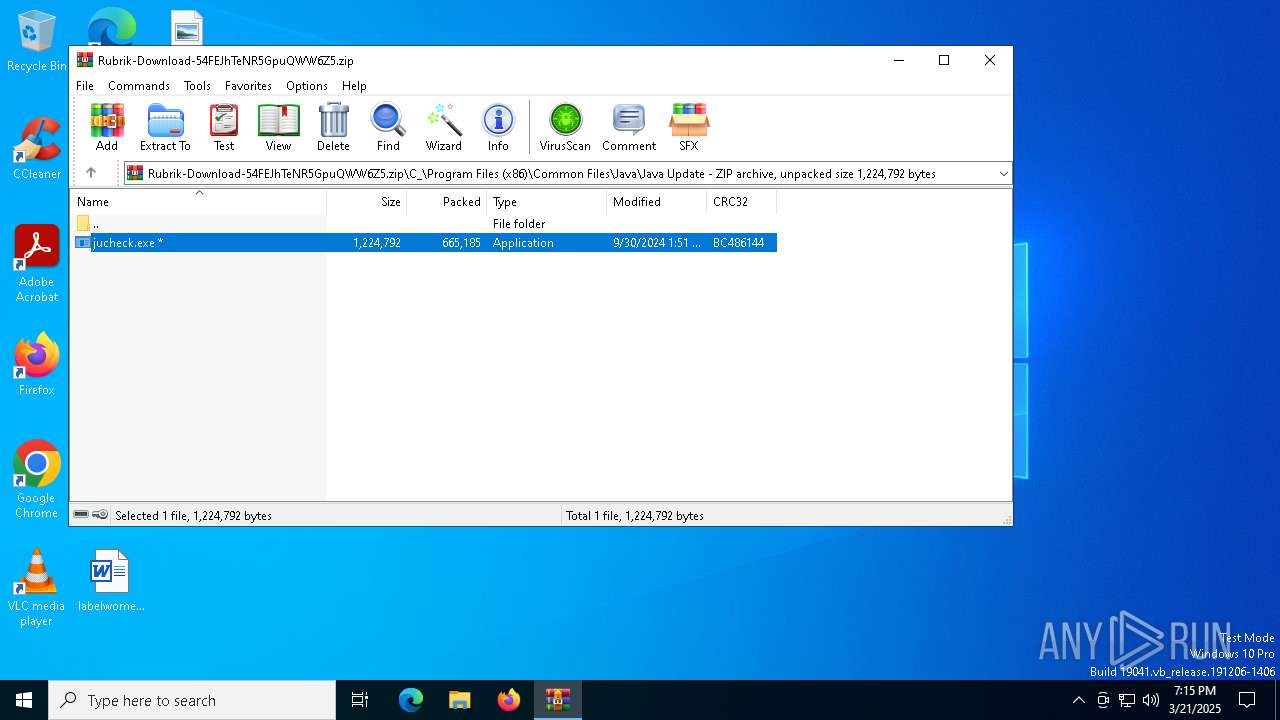
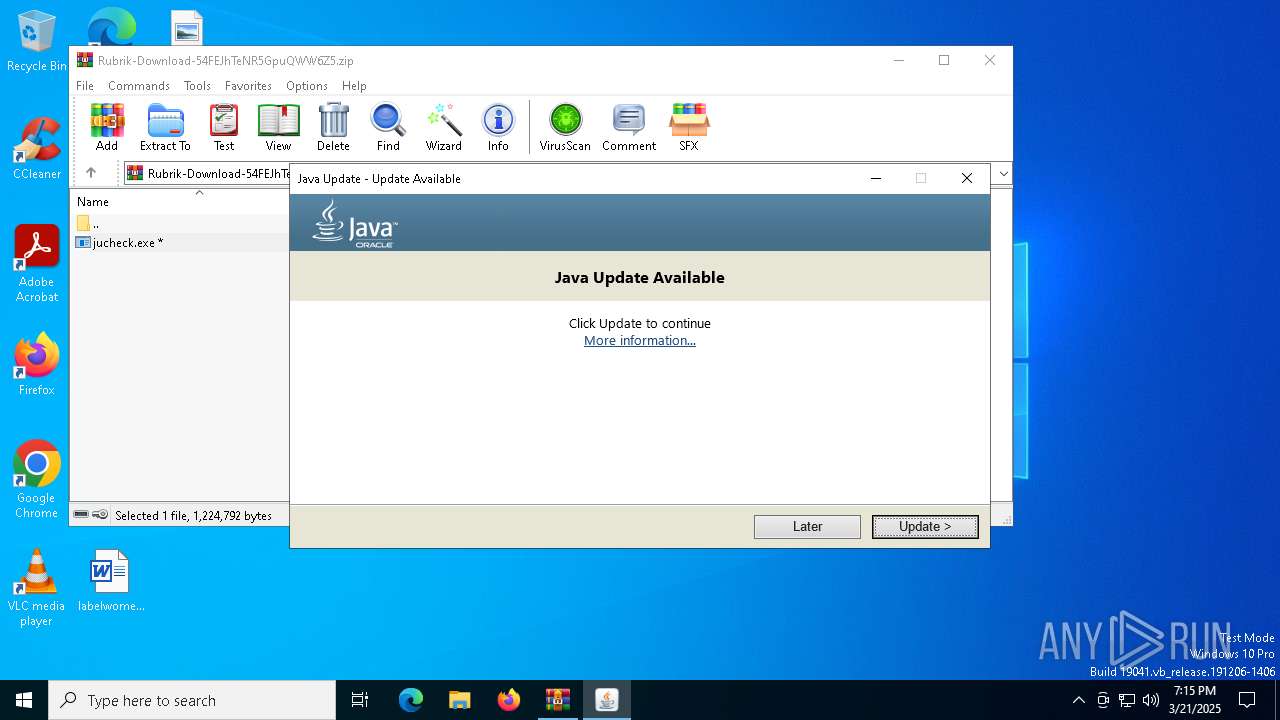
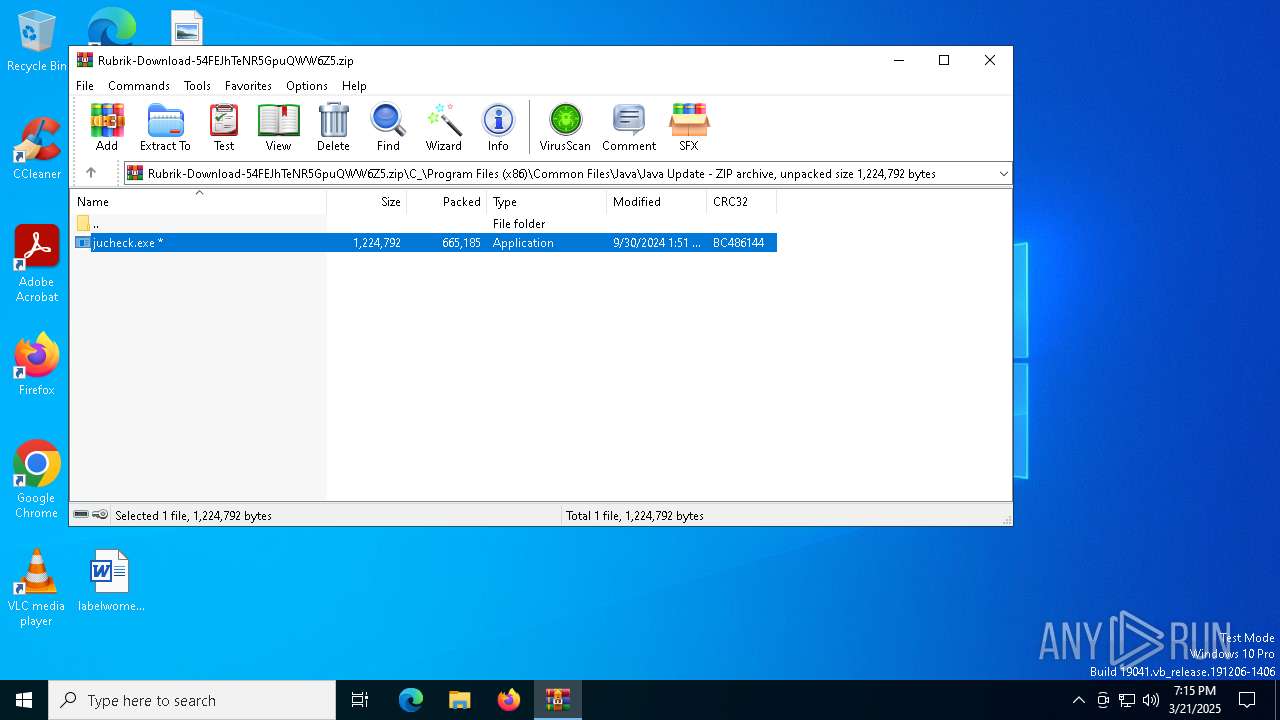
| File name: | Rubrik-Download-54FEJhTeNR5GpuQWW6Z5.zip |
| Full analysis: | https://app.any.run/tasks/895b64d7-ee13-4ee0-99b4-a878c04e2ac4 |
| Verdict: | Malicious activity |
| Analysis date: | March 21, 2025, 19:14:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | ECEB5DA2050E52CCE6C6DDA71FBEBF81 |
| SHA1: | 619E83D452B4789B4F4F766B3E43C793EABC116B |
| SHA256: | 142FA0F7837572549F204B97A983502E9ABD90F3AA88623293993C465098E907 |
| SSDEEP: | 24576:P1MdozeT71wvzMbxkEfJm0Nqzq6Q4DAHLbxAkoARK0WuVPFY7/pLybJ9:P1MdozeT71wvzMbWEfJm0NqzqJ4DAHLL |
MALICIOUS
No malicious indicators.SUSPICIOUS
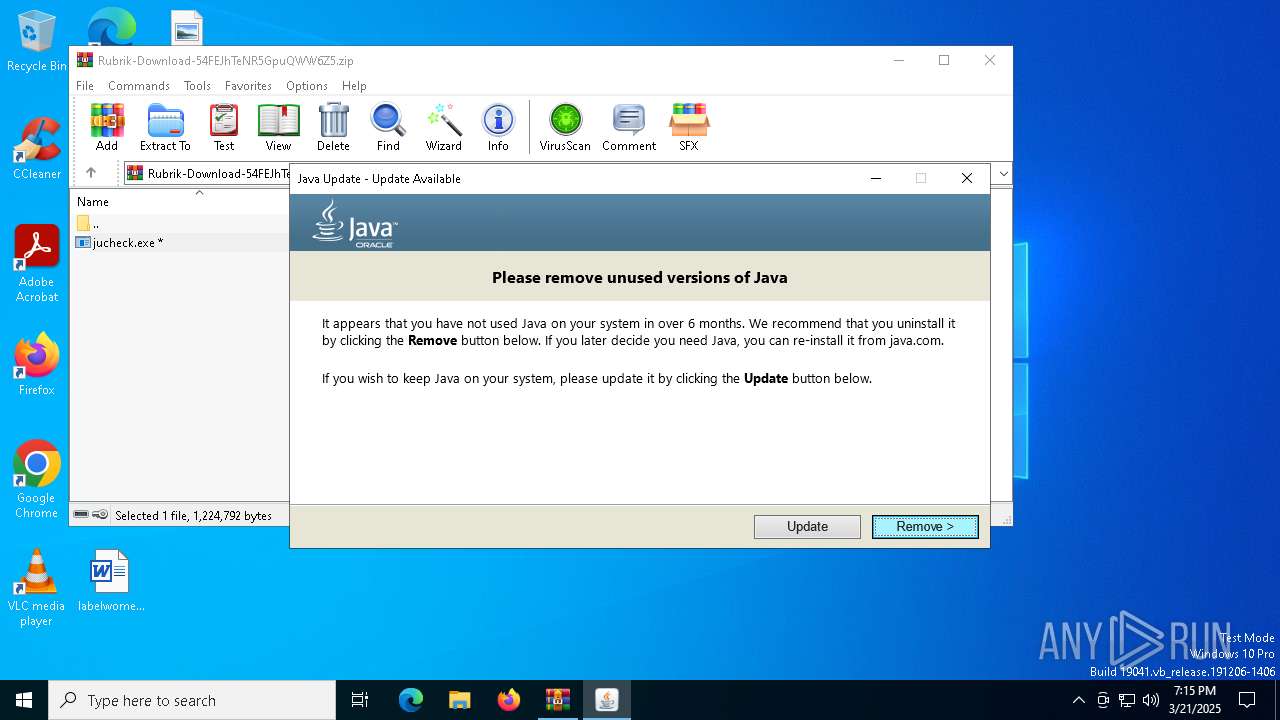
Checks for Java to be installed
- jucheck.exe (PID: 4008)
- jp2launcher.exe (PID: 1052)
- jre-8u441-windows-au.exe (PID: 1272)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4200)
- jucheck.exe (PID: 4008)
- jp2launcher.exe (PID: 1052)
- jre-8u441-windows-au.exe (PID: 1272)
Reads Microsoft Outlook installation path
- jucheck.exe (PID: 4008)
- jre-8u441-windows-au.exe (PID: 1272)
Executable content was dropped or overwritten
- jucheck.exe (PID: 4008)
- jre-8u441-windows-au.exe (PID: 5008)
Reads Internet Explorer settings
- jucheck.exe (PID: 4008)
- jre-8u441-windows-au.exe (PID: 1272)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4200)
- jucheck.exe (PID: 4008)
- jre-8u441-windows-au.exe (PID: 5008)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4200)
Checks supported languages
- jucheck.exe (PID: 4008)
- jp2launcher.exe (PID: 1052)
- javaws.exe (PID: 3100)
- jre-8u441-windows-au.exe (PID: 5008)
- jre-8u441-windows-au.exe (PID: 1272)
JAVA mutex has been found
- javaws.exe (PID: 3100)
- jp2launcher.exe (PID: 1052)
- jucheck.exe (PID: 4008)
Create files in a temporary directory
- jp2launcher.exe (PID: 1052)
- jucheck.exe (PID: 4008)
- jre-8u441-windows-au.exe (PID: 5008)
Reads the machine GUID from the registry
- jucheck.exe (PID: 4008)
- jp2launcher.exe (PID: 1052)
- jre-8u441-windows-au.exe (PID: 1272)
Reads the computer name
- jucheck.exe (PID: 4008)
- jp2launcher.exe (PID: 1052)
- javaws.exe (PID: 3100)
- jre-8u441-windows-au.exe (PID: 5008)
- jre-8u441-windows-au.exe (PID: 1272)
Creates files or folders in the user directory
- jucheck.exe (PID: 4008)
- jp2launcher.exe (PID: 1052)
- jre-8u441-windows-au.exe (PID: 1272)
Checks proxy server information
- jp2launcher.exe (PID: 1052)
- jucheck.exe (PID: 4008)
- slui.exe (PID: 5756)
- jre-8u441-windows-au.exe (PID: 1272)
Java executable
- jre-8u441-windows-au.exe (PID: 5008)
- jre-8u441-windows-au.exe (PID: 1272)
Reads the software policy settings
- jucheck.exe (PID: 4008)
- slui.exe (PID: 6184)
- jre-8u441-windows-au.exe (PID: 1272)
- slui.exe (PID: 5756)
Process checks computer location settings
- jucheck.exe (PID: 4008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x000d |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:30 13:51:30 |
| ZipCRC: | 0xbc486144 |
| ZipCompressedSize: | 665185 |
| ZipUncompressedSize: | 1224792 |
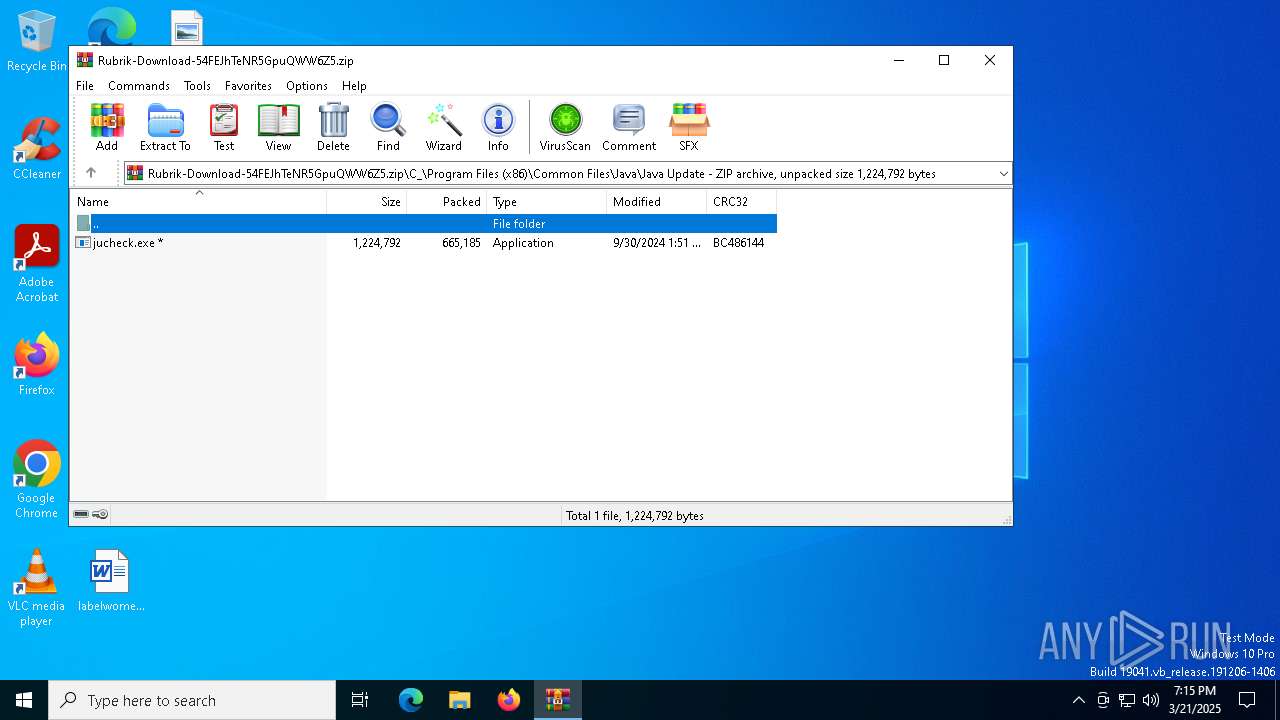
| ZipFileName: | C_/Program Files (x86)/Common Files/Java/Java Update/jucheck.exe |
Total processes
144
Monitored processes
9
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 1272 | "C:\Users\admin\AppData\Local\Temp\jds1129140.tmp\jre-8u441-windows-au.exe" "/installmethod=jau-m" "FAMILYUPGRADE=1" | C:\Users\admin\AppData\Local\Temp\jds1129140.tmp\jre-8u441-windows-au.exe | jre-8u441-windows-au.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Version: 8.0.4410.7 Modules
| |||||||||||||||
| 3100 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jucheck.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 4008 | "C:\Users\admin\AppData\Local\Temp\Rar$EXb4200.31673\C_\Program Files (x86)\Common Files\Java\Java Update\jucheck.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXb4200.31673\C_\Program Files (x86)\Common Files\Java\Java Update\jucheck.exe | WinRAR.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Checker Exit code: 0 Version: 2.8.431.10 Modules
| |||||||||||||||
| 4200 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rubrik-Download-54FEJhTeNR5GpuQWW6Z5.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5008 | "C:\Users\admin\AppData\Local\Temp\jre-8u441-windows-au.exe" /installmethod=jau-m FAMILYUPGRADE=1 | C:\Users\admin\AppData\Local\Temp\jre-8u441-windows-au.exe | jucheck.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java Platform SE binary Version: 8.0.4410.7 Modules
| |||||||||||||||
| 5756 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6184 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 364
Read events
14 127
Write events
202
Delete events
35
Modification events
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Rubrik-Download-54FEJhTeNR5GpuQWW6Z5.zip | |||
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4008) jucheck.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\JavaSoft\Java Update\Policy\jucheck |
| Operation: | write | Name: | Method |
Value: jau-m | |||
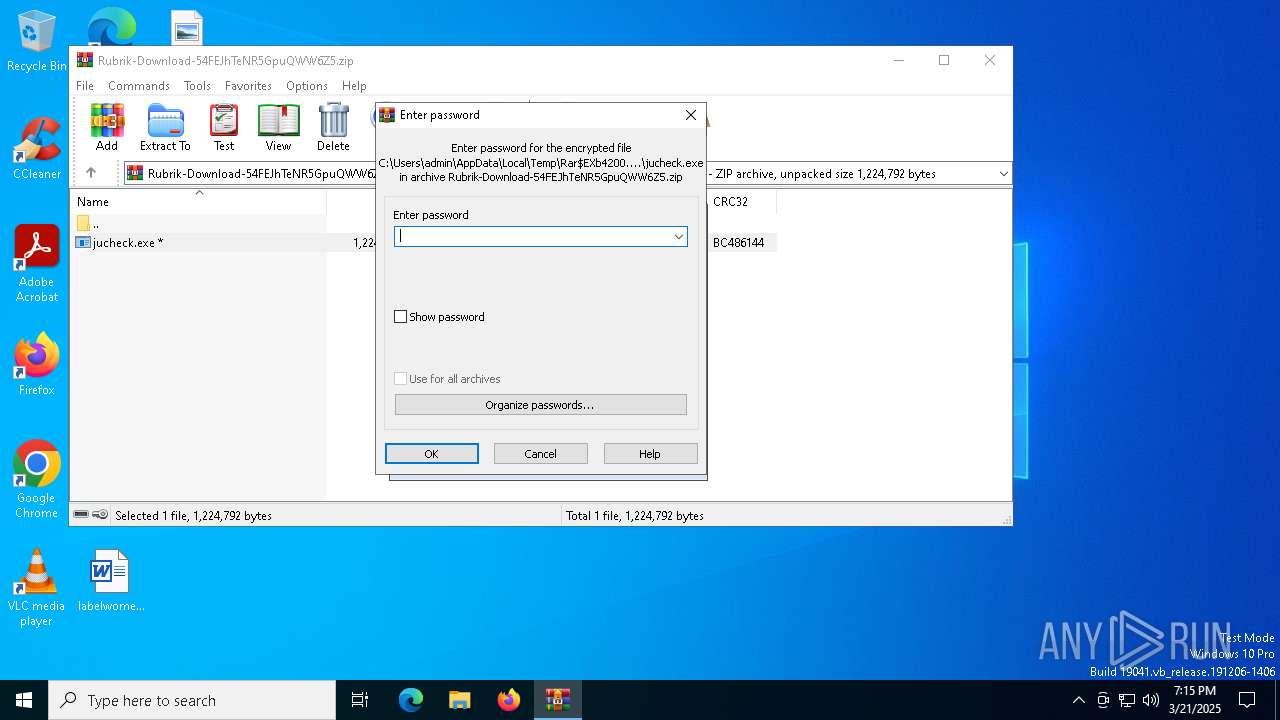
| (PID) Process: | (4200) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 1 | |||
Executable files
6
Suspicious files
10
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4200 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4200.31673\C_\Program Files (x86)\Common Files\Java\Java Update\jucheck.exe | executable | |
MD5:11B7ED0DE6B7FF2AD2773A3945D6D052 | SHA256:8A285816ADA4F318AD2FC595ECAB08A2CEB8A5418DCAD3FADFAA84582AE8B47F | |||
| 4008 | jucheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:E950EC3D3B3C125A21A2A18E32092E77 | SHA256:9A3C28F7F3140AA1D42C2DFE59AC0D46ED7DF39C9AE70196F00F0C1858B223A4 | |||
| 4008 | jucheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:E62F4FB3D77C8E85BDB7135043839445 | SHA256:F1C62AFEC1061FFDE782E823AC492E13E37340C79E5CDDE8B0D4F89A8A77D96A | |||
| 1052 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\update.securitypack.timestamp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 1052 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\blacklist.dynamic | text | |
MD5:B2C6EAE6382150192EA3912393747180 | SHA256:6C73C877B36D4ABD086CB691959B180513AC5ABC0C87FE9070D2D5426D3DBF71 | |||
| 4008 | jucheck.exe | C:\Users\admin\AppData\Local\Temp\jusched.log | text | |
MD5:E91A0B6B5873DDA3B96C11A67B8B4CF0 | SHA256:A25763EC71D681FC750E11E3498EFEB99173A502C3EED308826C2F122CBC61C0 | |||
| 1052 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\blacklisted.certs | text | |
MD5:8273F70416F494F7FA5B6C70A101E00E | SHA256:583500B76965EB54B03493372989AB4D3426F85462D1DB232C5AE6706A4D6C58 | |||
| 1052 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:DCFDAD9BAE357AB357A16F2EB8F028FE | SHA256:394544C68D01D8C9BACD70BF98777BFE569149F4B5FF14ABB239F1A53FEB97ED | |||
| 4008 | jucheck.exe | C:\Users\admin\AppData\Local\Temp\au-descriptor-1.8.0_441-b07.xml | xml | |
MD5:AA7101E77C83866CBC61A06A83BD7AA3 | SHA256:FE43C0B927A1948EDAB455B09EBF32CBF4777570C14EFBFCAB60FA250E5ABB22 | |||
| 1052 | jp2launcher.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\security\baseline.versions | text | |
MD5:CCC4D962D728250E93FC0A506BB60627 | SHA256:037D819F2C09987E0864AB8E33DC757571670910E80EDABC702D34FED3C0DB04 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
32
DNS requests
19
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4980 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4008 | jucheck.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | whitelisted |
1052 | jp2launcher.exe | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
1052 | jp2launcher.exe | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
5756 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1052 | jp2launcher.exe | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
1052 | jp2launcher.exe | POST | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/ | unknown | — | — | whitelisted |
5756 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4980 | backgroundTaskHost.exe | 20.199.58.43:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
javadl-esd-secure.oracle.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | jp2launcher.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |
1052 | jp2launcher.exe | Potentially Bad Traffic | ET INFO Vulnerable Java Version 1.8.x Detected |