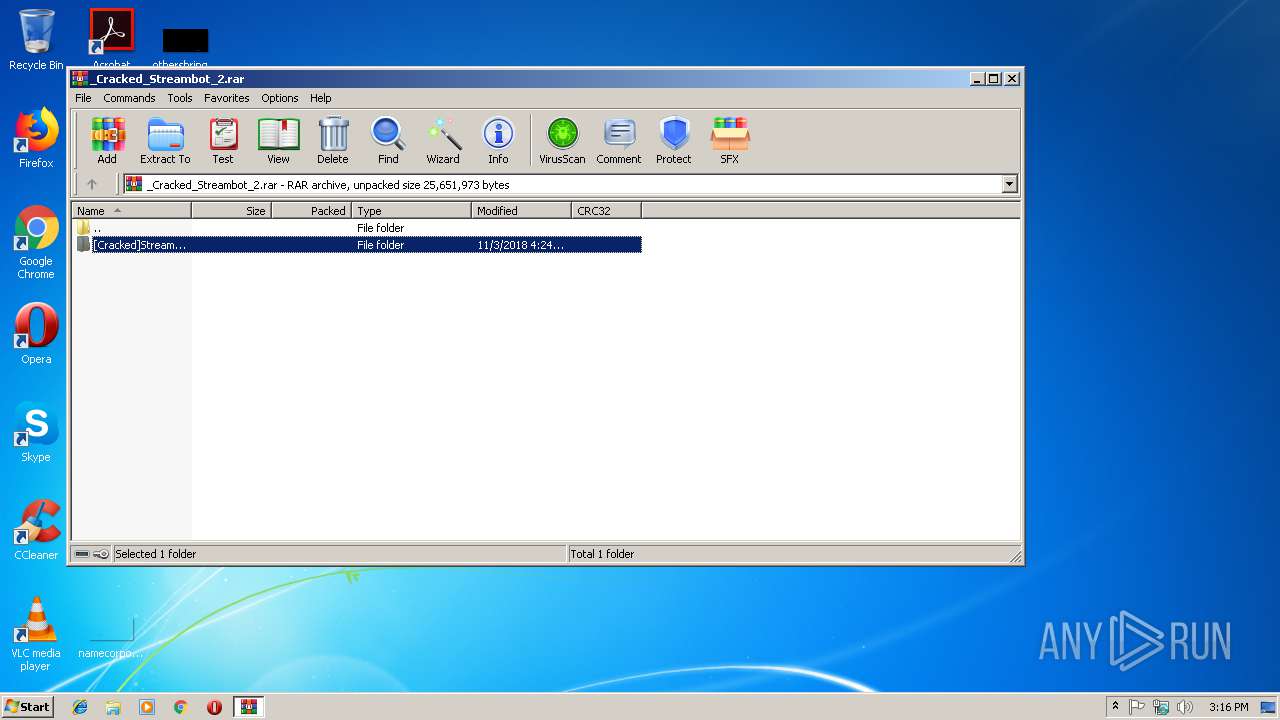
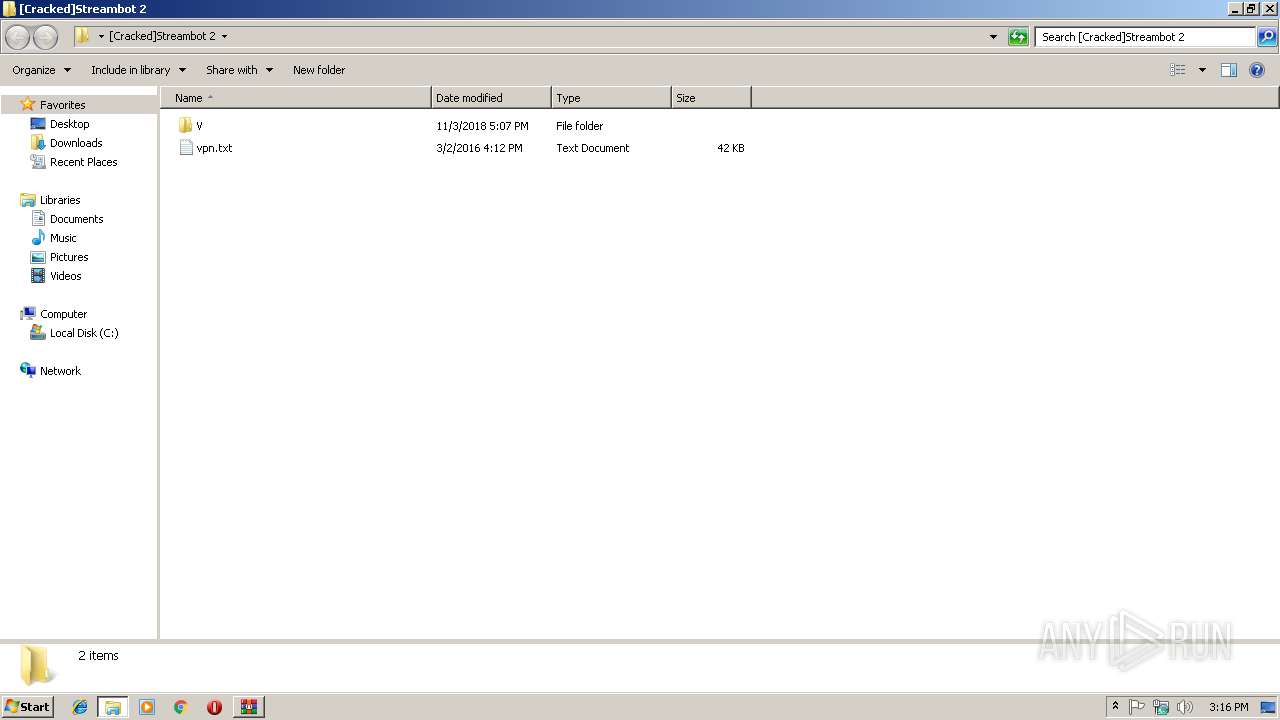
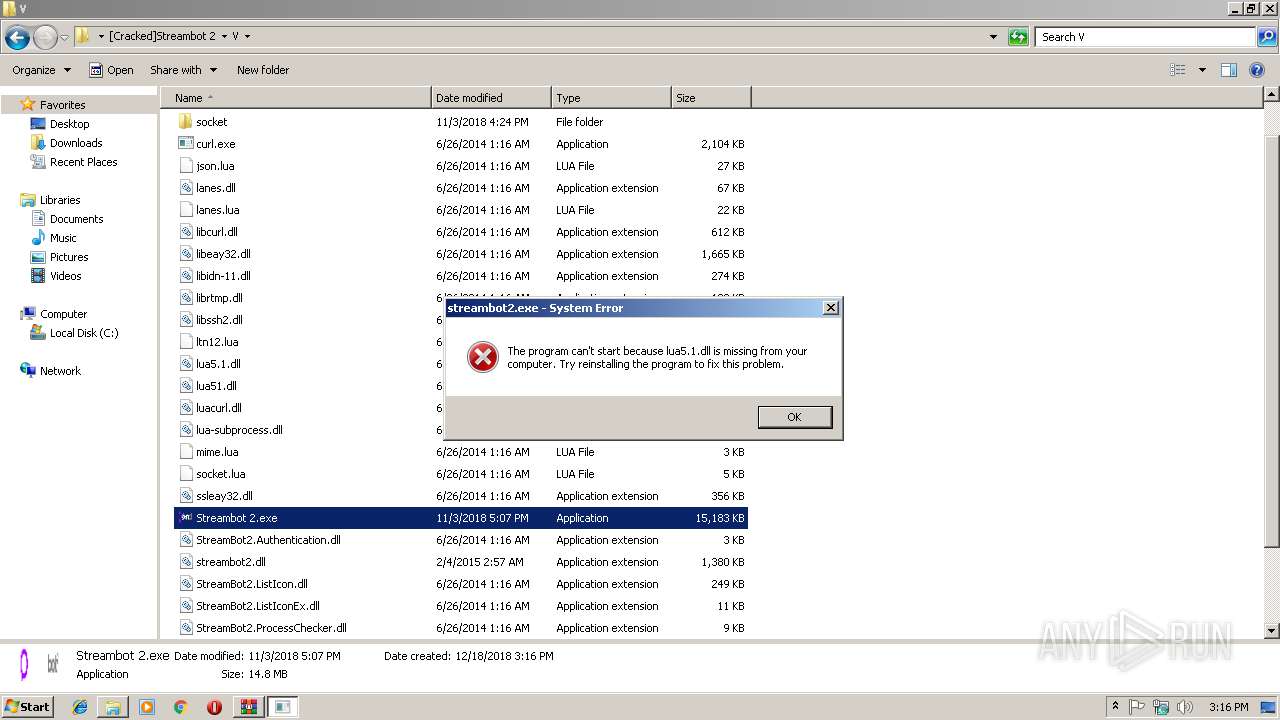
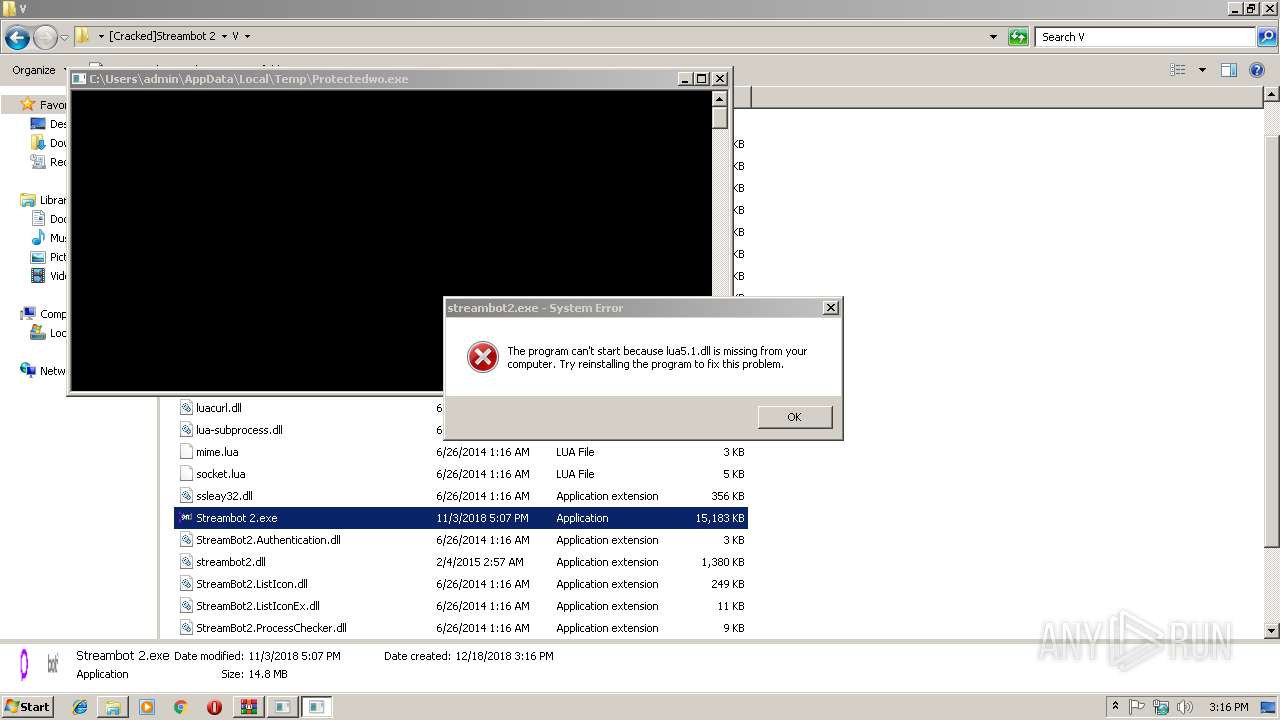
| File name: | _Cracked_Streambot_2.rar |
| Full analysis: | https://app.any.run/tasks/547416d6-3361-4a73-818d-e3c339f8a221 |
| Verdict: | Malicious activity |
| Threats: | Crypto mining malware is a resource-intensive threat that infiltrates computers with the purpose of mining cryptocurrencies. This type of threat can be deployed either on an infected machine or a compromised website. In both cases the miner will utilize the computing power of the device and its network bandwidth. |
| Analysis date: | December 18, 2018, 15:15:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C98AAE43EC84FADC9EAC5EBC0CD7A1B2 |
| SHA1: | FCD63318B9146484A521D9AFC0AFC0AE17F13D18 |
| SHA256: | 141FB3AB10523E8624E5736218F9A6B7A8CD1FFB3862444F491D5792FA6D3142 |
| SSDEEP: | 196608:R9itwJNPwD7qM2KFJUycFd+o+zOwAd+jDoWRJO4Zvj57UIG+uMNZkyzf29F0Hl:uiJNYy4C/Fd+ond47nOc9UIG+DZ/29Fg |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1040)
Known privilege escalation attack
- Streambot 2.exe (PID: 3836)
Uses Task Scheduler to run other applications
- Protectedwo.exe (PID: 2520)
- 22.exe (PID: 3644)
- 2222.exe (PID: 3724)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 2584)
- schtasks.exe (PID: 3916)
- schtasks.exe (PID: 3900)
- schtasks.exe (PID: 3956)
- schtasks.exe (PID: 3944)
Application was dropped or rewritten from another process
- streambot2.exe (PID: 2912)
- 2222.exe (PID: 3724)
- 22.exe (PID: 3644)
- Protectednj.exe (PID: 3436)
- Protectedwo.exe (PID: 2520)
- Protectedin.exe (PID: 2192)
- Protectedwo.exe (PID: 908)
- Protectedcy.exe (PID: 3652)
- 2222.sfx.exe (PID: 3052)
- SDVGJHKHC.exe (PID: 2864)
- ZVKQHTPNL.exe (PID: 3008)
Changes the autorun value in the registry
- 22.exe (PID: 3644)
- cscript.exe (PID: 3396)
- 2222.exe (PID: 3724)
- wscript.exe (PID: 2848)
Writes to a start menu file
- cscript.exe (PID: 3396)
- wscript.exe (PID: 2848)
MINER was detected
- SDVGJHKHC.exe (PID: 2864)
- ZVKQHTPNL.exe (PID: 3008)
Connects to CnC server
- SDVGJHKHC.exe (PID: 2864)
- ZVKQHTPNL.exe (PID: 3008)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3308)
- Streambot 2.exe (PID: 3272)
- Protectedwo.exe (PID: 2520)
- 2222.sfx.exe (PID: 3052)
- 22.exe (PID: 3644)
- 2222.exe (PID: 3724)
Modifies the open verb of a shell class
- Streambot 2.exe (PID: 3836)
Executes scripts
- Protectedwo.exe (PID: 908)
- cscript.exe (PID: 3396)
Creates files in the user directory
- cscript.exe (PID: 3396)
Connects to unusual port
- SDVGJHKHC.exe (PID: 2864)
- ZVKQHTPNL.exe (PID: 3008)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
66
Monitored processes
25
Malicious processes
13
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 908 | "C:\Users\admin\AppData\Local\Temp\Protectedwo.exe" | C:\Users\admin\AppData\Local\Temp\Protectedwo.exe | — | Protectedwo.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1040 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1328 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2192 | "C:\Users\admin\AppData\Local\Temp\Protectedin.exe" | C:\Users\admin\AppData\Local\Temp\Protectedin.exe | — | Streambot 2.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2520 | "C:\Users\admin\AppData\Local\Temp\Protectedwo.exe" | C:\Users\admin\AppData\Local\Temp\Protectedwo.exe | Streambot 2.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2584 | "C:\Windows\System32\schtasks.exe" /create /tn 66717363737462656F6C797A /tr "C:\Users\admin\AppData\Local\Temp\awafvqrobbjo\skecatbucrom.exe" /sc minute /mo 1 /F | C:\Windows\System32\schtasks.exe | — | Protectedwo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Windows\System32\wscript.exe" //B "C:\Users\admin\AppData\Local\Temp\6C9.vbs" | C:\Windows\System32\wscript.exe | cscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2864 | C:\Users\admin\AppData\Local\Temp\BVPWSLUSIHIG\SDVGJHKHC.exe -o pooleu.xmrminingpool.net:2222 -u 4BrL51JCc9NGQ71kWhnYoDRffsDZy7m1HUU7MRU4nUMXAHNFBEJhkTZV9HdaL4gfuNBxLPc3BeMkLGaPbF5vWtANQtz7XNvpsygAzF9g1Y -p 2222 -a cryptonight --max-cpu-usage 58 | C:\Users\admin\AppData\Local\Temp\BVPWSLUSIHIG\SDVGJHKHC.exe | 22.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: UpdaterWindows Exit code: 0 Modules
| |||||||||||||||
| 2912 | "C:\Users\admin\AppData\Local\Temp\streambot2.exe" | C:\Users\admin\AppData\Local\Temp\streambot2.exe | — | Streambot 2.exe | |||||||||||
User: admin Company: Shadiku Izayoi, Emma Skye <neosyndicate.net> Integrity Level: HIGH Description: streambot² Exit code: 3221225781 Version: 2.5.0.0 Modules
| |||||||||||||||
| 3008 | C:\Users\admin\AppData\Local\Temp\VNBZOAYJFDRA\ZVKQHTPNL.exe -o pooleu.xmrminingpool.net:2222 -u 4BrL51JCc9NGQ71kWhnYoDRffsDZy7m1HUU7MRU4nUMXAHNFBEJhkTZV9HdaL4gfuNBxLPc3BeMkLGaPbF5vWtANQtz7XNvpsygAzF9g1Y -p 2222 -a cryptonight --max-cpu-usage 58 | C:\Users\admin\AppData\Local\Temp\VNBZOAYJFDRA\ZVKQHTPNL.exe | 2222.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: UpdaterWindows Exit code: 0 Modules
| |||||||||||||||
Total events
1 960
Read events
1 916
Write events
44
Delete events
0
Modification events
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\_Cracked_Streambot_2.rar | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3308) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1040) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1040) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
30
Suspicious files
8
Text files
45
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap10.dat | image | |
MD5:15FEC6C33A20A6ECB295FA55514781E7 | SHA256:E238521A1915A0C488D87FA0068D03135BA2D806268F58E973B858195975B20D | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap11.dat | compressed | |
MD5:EEB4B272A3C00AB96E0D854BDF67BB9A | SHA256:BC42AC736F96D0CD124FDA4933B83B64C7DA3E8DC4C764D87215D2F332B8B280 | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap1.dat | text | |
MD5:38DE427224A5082A04FE82E2BD4EA9EC | SHA256:12F99F53144294750FE8713D580EDA286F4BD95CD9C840DB8AB957DEF8040028 | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap13.dat | image | |
MD5:636121997F8139FA039DA7EAA207C23F | SHA256:7F7E0C0BAA8EDB2035D7108ED7760C7F26D80205CB6CA2609904E5B8F69BE6F1 | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap14.dat | image | |
MD5:58724CE63DFB037C86EE19358FC20157 | SHA256:D4D9BE6BFBAAF7B4215D149907182B8D92137628E0369986D07E8E27006817E8 | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap15.dat | image | |
MD5:9739753453EC79E41C49500DDA06D0C9 | SHA256:56407243DFEA14F0A42D5CD7E0D7CE3D3D828C83AB3C1A70FC3E09056E99D110 | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap18.dat | image | |
MD5:9073D4D6CB37AB39CAA44CFF241182EE | SHA256:19105802E9202F5070919D1326732BE8E8B0D0EF0B9E7DD11AA6BF7DD43042D3 | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap17.dat | image | |
MD5:60B09CEE404FCC00B7CB15EC1FDA26DB | SHA256:6A17EAA4FE1B8574588367254EA27B9686C5B8DFB13928028D13415DCF44FDBB | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap21.dat | image | |
MD5:83E5EEF02E173AC3EFD8CA49609EC5E3 | SHA256:87249BFB103A8FDE22FE5C6C77CB990E36AE31FBFF8A5FF8361F99199B0F79F4 | |||
| 3308 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3308.16372\[Cracked]Streambot 2\V\includes\dat01\ap22.dat | compressed | |
MD5:45DDEF3B2DFA5D79DDE211620FCF538C | SHA256:1159A44808FAA6C897BDA6D66AE0620B898593A13EAF56318CDDBE66A8298583 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
8
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3008 | ZVKQHTPNL.exe | 192.154.110.50:2222 | pooleu.xmrminingpool.net | GorillaServers, Inc. | US | suspicious |
2864 | SDVGJHKHC.exe | 192.154.110.50:2222 | pooleu.xmrminingpool.net | GorillaServers, Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pooleu.xmrminingpool.net |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3008 | ZVKQHTPNL.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
3008 | ZVKQHTPNL.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
2864 | SDVGJHKHC.exe | Potential Corporate Privacy Violation | ET POLICY Cryptocurrency Miner Checkin |
2864 | SDVGJHKHC.exe | Misc activity | MINER [PTsecurity] CoinMiner CryptoNight XMRig JSON_RPC Client Login |
3008 | ZVKQHTPNL.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
3008 | ZVKQHTPNL.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |
2864 | SDVGJHKHC.exe | Misc activity | MINER [PTsecurity] Riskware/CoinMiner JSON_RPC Response |
2864 | SDVGJHKHC.exe | Misc activity | MINER [PTsecurity] Risktool.W32.coinminer!c |