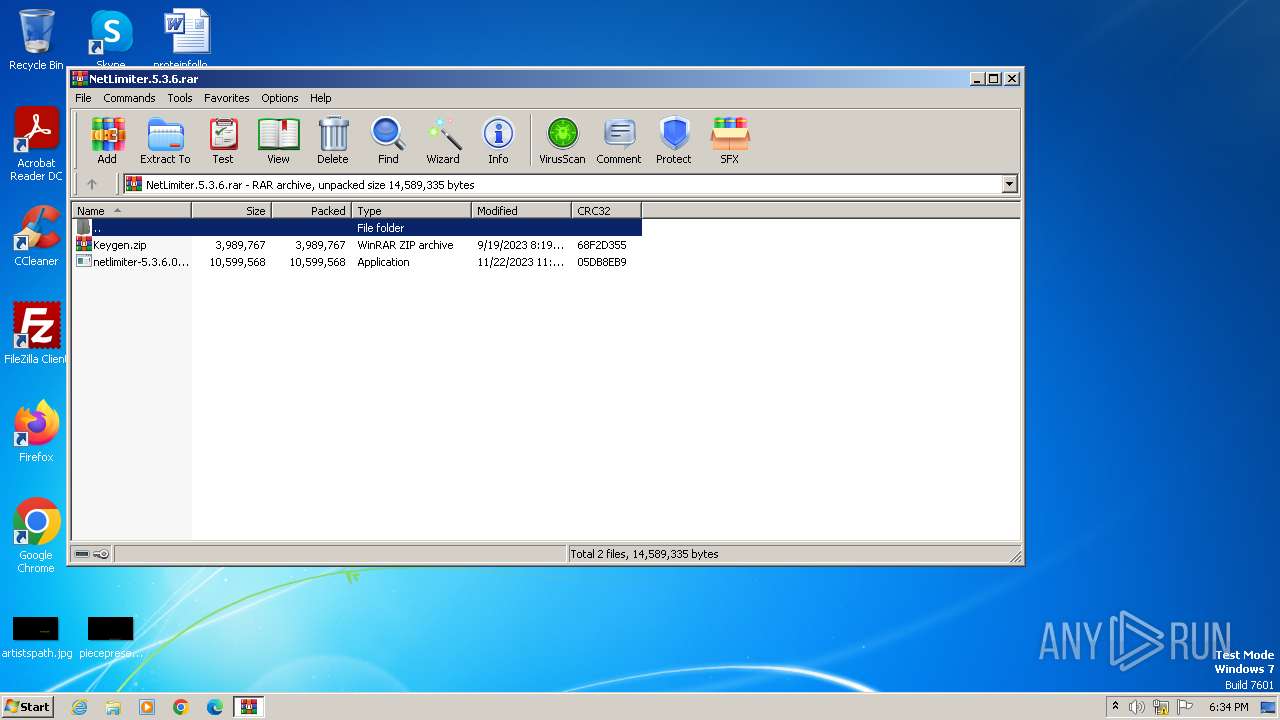
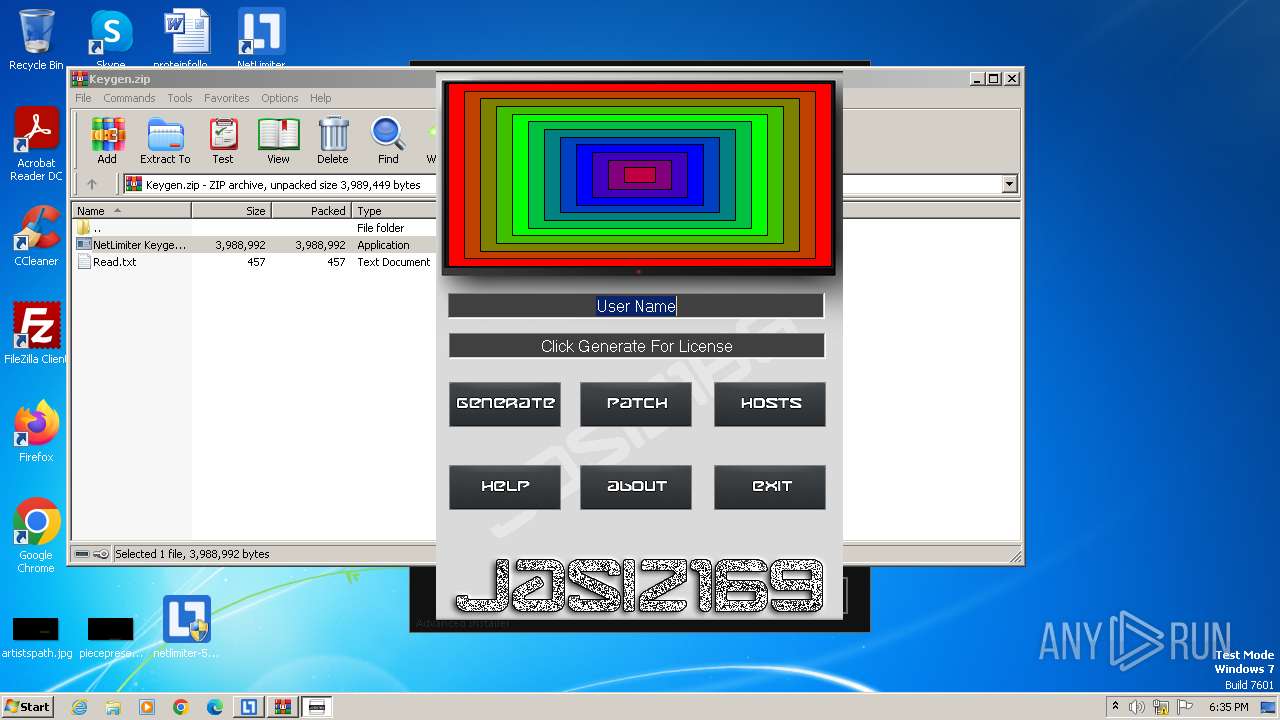
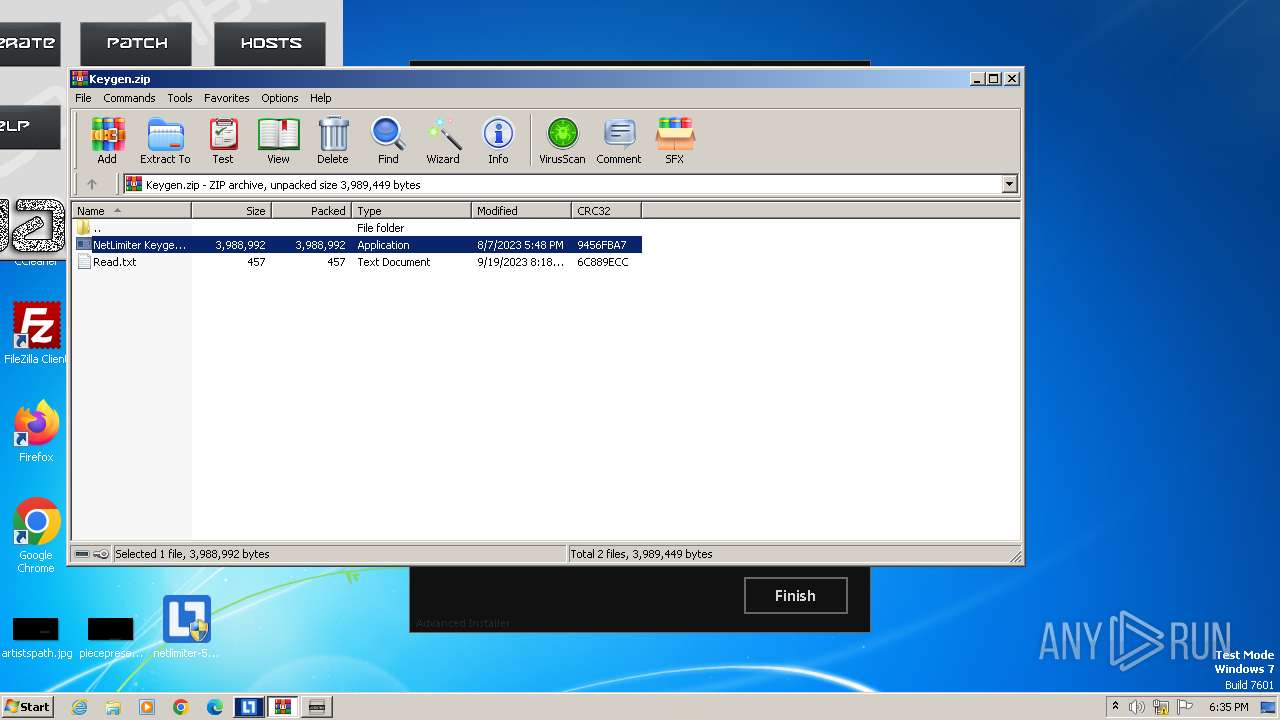
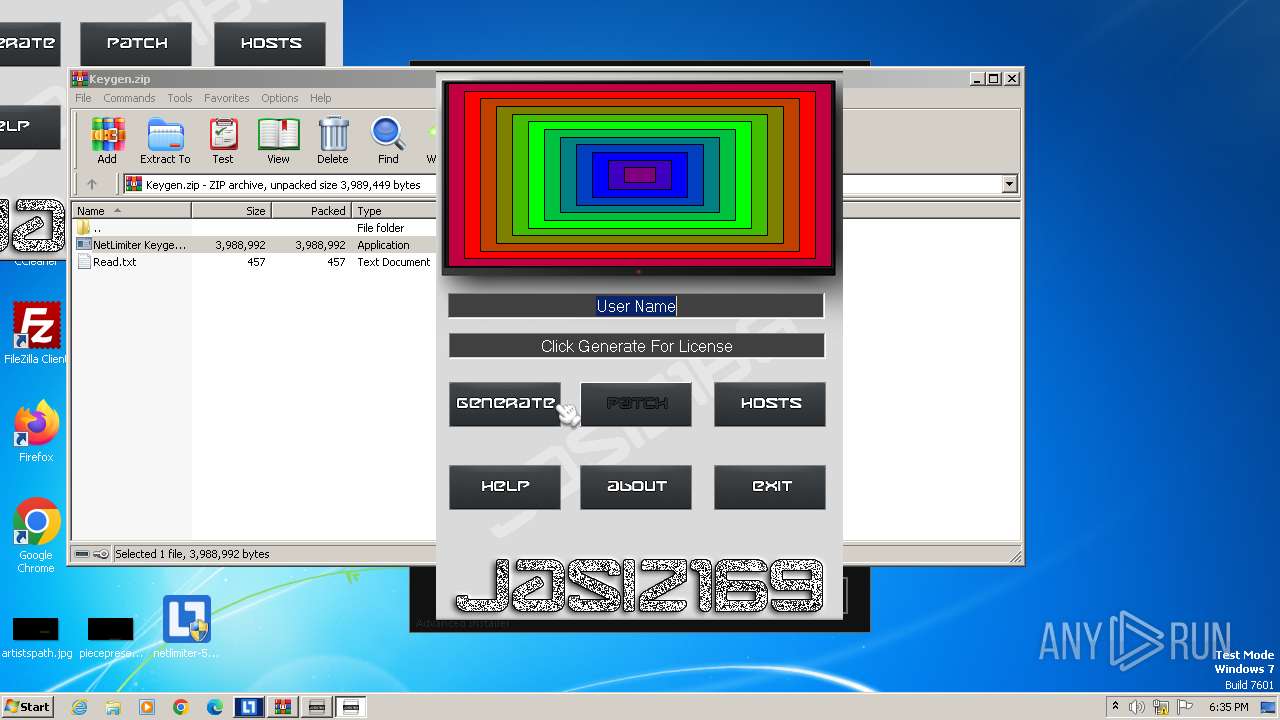
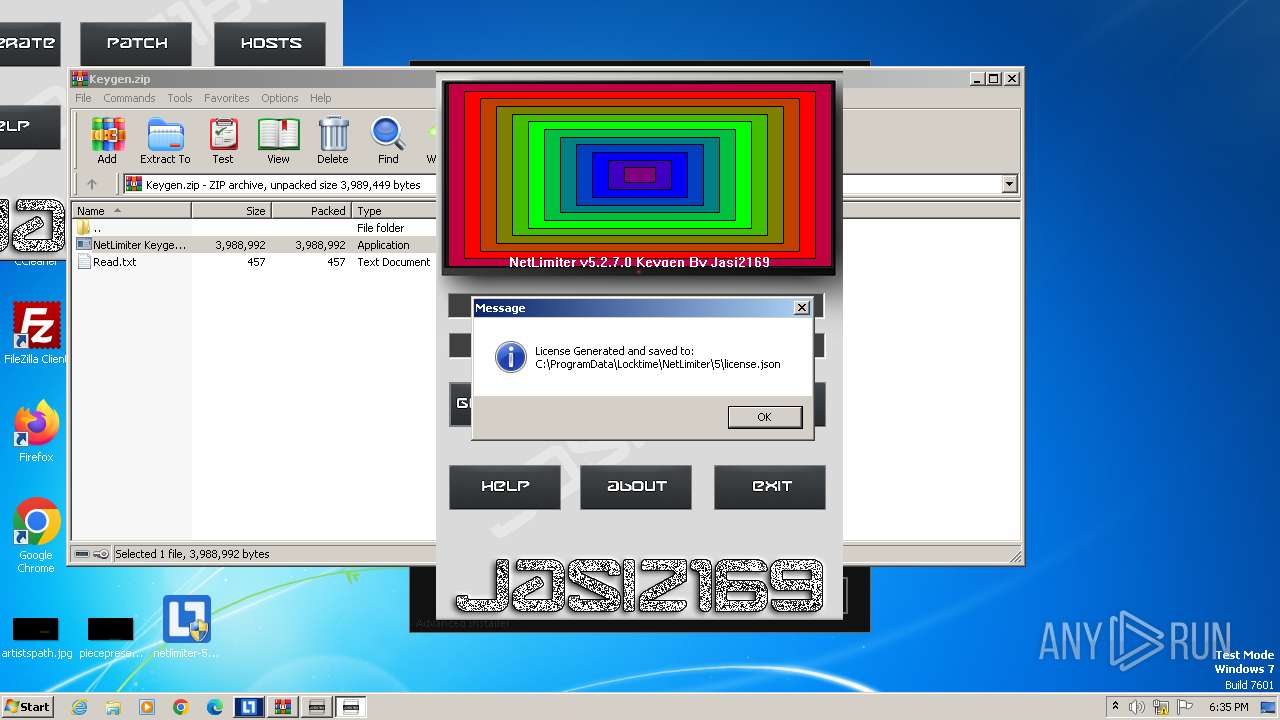
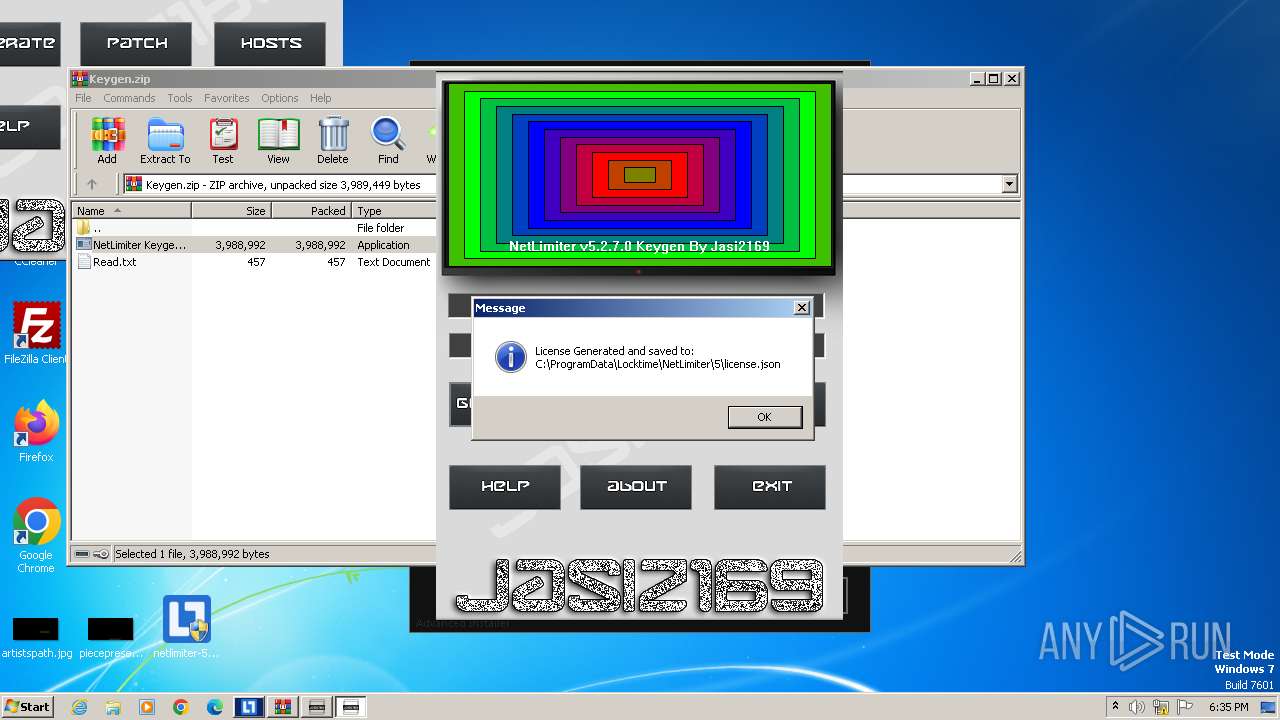
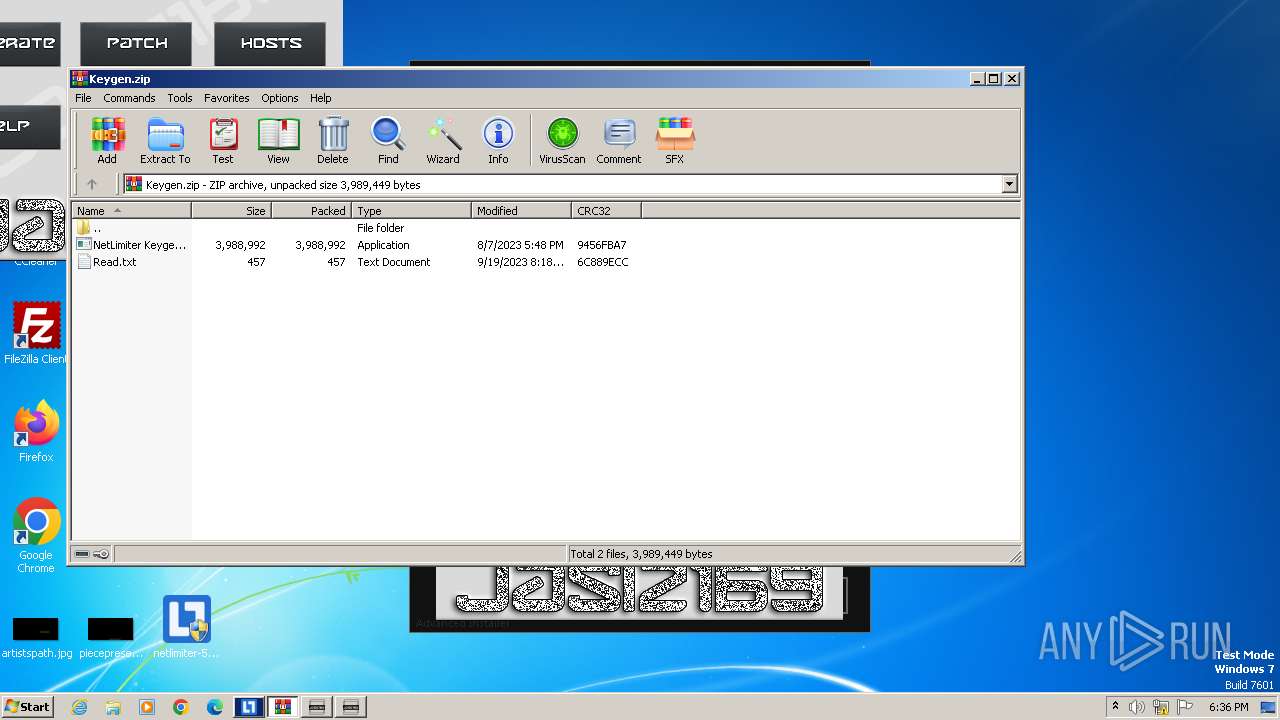
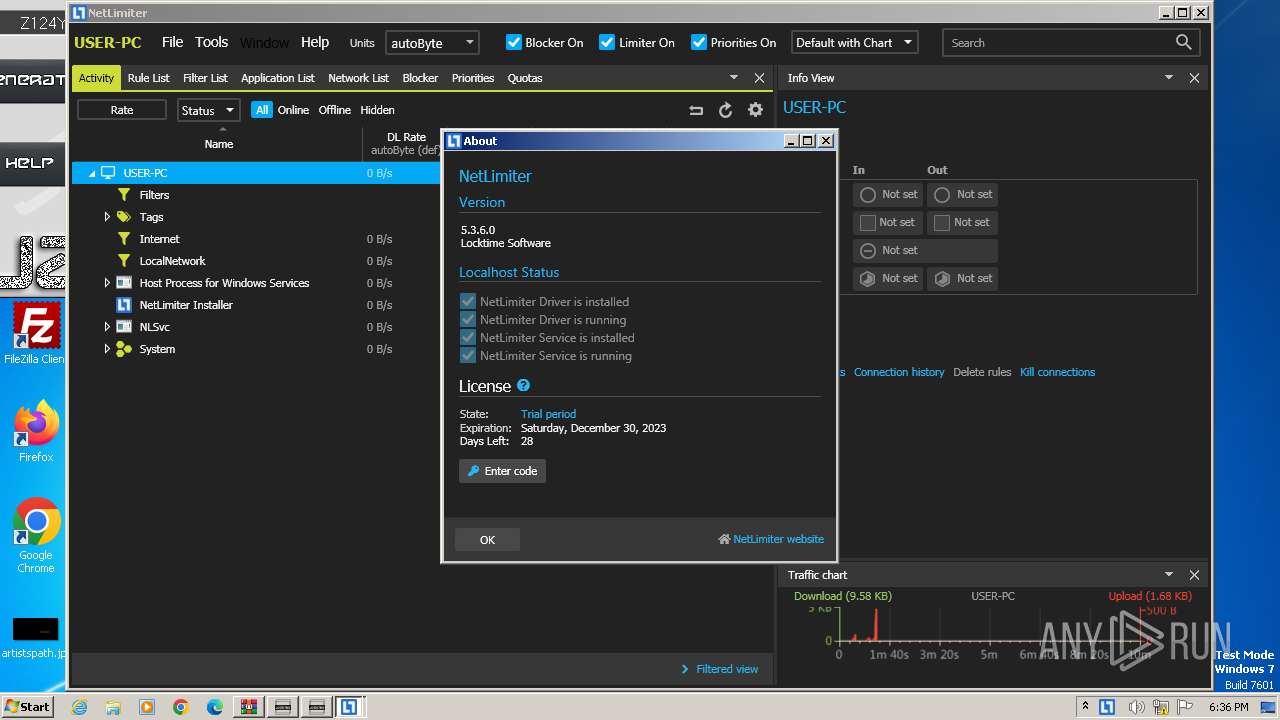
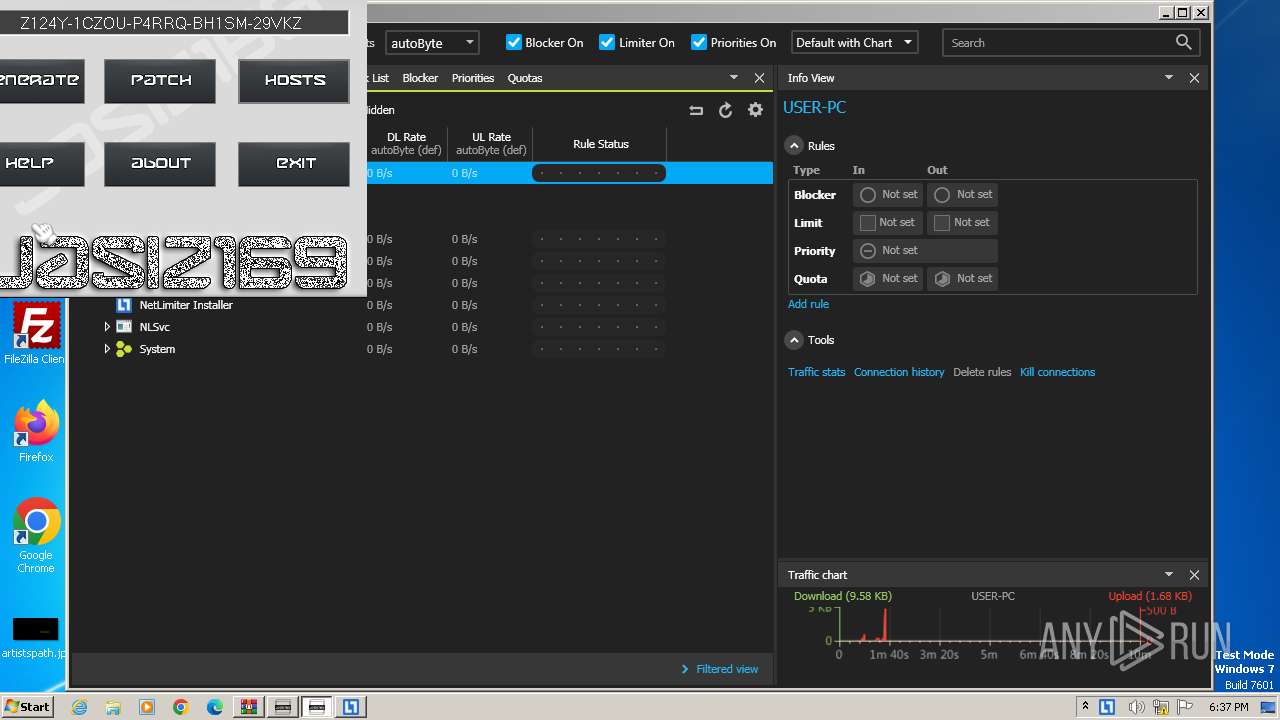
| File name: | NetLimiter.5.3.6.rar |
| Full analysis: | https://app.any.run/tasks/736c870d-fe6f-4ea0-bf66-fffe77b329b1 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 18:34:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | F29D9C83D7BC5CBC4B956D23F77330FD |
| SHA1: | 56DC1A647DEBE024FD9494DDCB630A5A1C7498E9 |
| SHA256: | 1416E0B95FB79B5BAB4E3E07AAB2C5969FF23A7D90DCC46773B66C3810CDBFF6 |
| SSDEEP: | 98304:6djZ9lWXWbnMGhEaW+0Am9sZBd2s1oPkvo5wdQ6RvtLDVKk4sfIgtjNQOAxf1gSI:6mpZydn2rb8fJ2idkewQ |
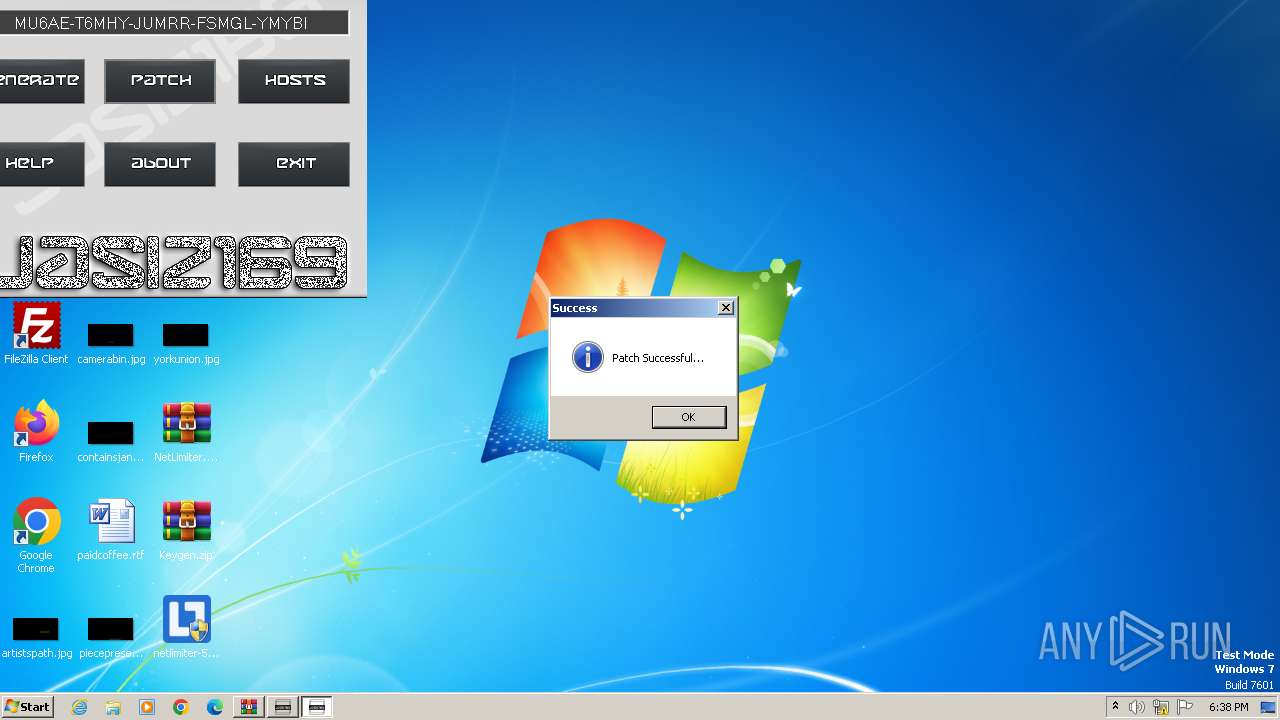
MALICIOUS
Creates a writable file in the system directory
- msiexec.exe (PID: 4060)
- NLSvc.exe (PID: 3336)
- NetLimiter Keygen v1.3.exe (PID: 1840)
Drops the executable file immediately after the start
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 4060)
- mscorsvw.exe (PID: 1364)
- mscorsvw.exe (PID: 2612)
- mscorsvw.exe (PID: 188)
- mscorsvw.exe (PID: 2088)
- mscorsvw.exe (PID: 3072)
- mscorsvw.exe (PID: 3444)
- mscorsvw.exe (PID: 1968)
- mscorsvw.exe (PID: 3352)
- mscorsvw.exe (PID: 2144)
- mscorsvw.exe (PID: 2552)
- mscorsvw.exe (PID: 2528)
- mscorsvw.exe (PID: 280)
- mscorsvw.exe (PID: 4036)
- mscorsvw.exe (PID: 2520)
- mscorsvw.exe (PID: 2548)
- mscorsvw.exe (PID: 2908)
- mscorsvw.exe (PID: 3500)
- mscorsvw.exe (PID: 1212)
- mscorsvw.exe (PID: 3936)
- mscorsvw.exe (PID: 3776)
- mscorsvw.exe (PID: 3380)
- mscorsvw.exe (PID: 756)
- mscorsvw.exe (PID: 4056)
- mscorsvw.exe (PID: 3944)
- mscorsvw.exe (PID: 836)
- mscorsvw.exe (PID: 2460)
- mscorsvw.exe (PID: 3988)
- mscorsvw.exe (PID: 1820)
- mscorsvw.exe (PID: 3700)
- mscorsvw.exe (PID: 2392)
- mscorsvw.exe (PID: 1588)
- mscorsvw.exe (PID: 2324)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 1072)
- mscorsvw.exe (PID: 1988)
- mscorsvw.exe (PID: 2408)
- mscorsvw.exe (PID: 3980)
- mscorsvw.exe (PID: 644)
- mscorsvw.exe (PID: 788)
- mscorsvw.exe (PID: 2076)
- mscorsvw.exe (PID: 2984)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 1756)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 1404)
- mscorsvw.exe (PID: 1380)
- mscorsvw.exe (PID: 3256)
- mscorsvw.exe (PID: 1816)
- mscorsvw.exe (PID: 3160)
- mscorsvw.exe (PID: 3740)
- mscorsvw.exe (PID: 3780)
- mscorsvw.exe (PID: 3796)
- mscorsvw.exe (PID: 1828)
- NetLimiter Keygen v1.3.exe (PID: 1840)
- NetLimiter Keygen v1.3.exe (PID: 2076)
- mscorsvw.exe (PID: 3084)
Starts NET.EXE for service management
- cmd.exe (PID: 2648)
- net.exe (PID: 3876)
- cmd.exe (PID: 1248)
- net.exe (PID: 2268)
SUSPICIOUS
Checks Windows Trust Settings
- netlimiter-5.3.6.0.exe (PID: 2544)
- netlimiter-5.3.6.0.exe (PID: 3044)
- msiexec.exe (PID: 4060)
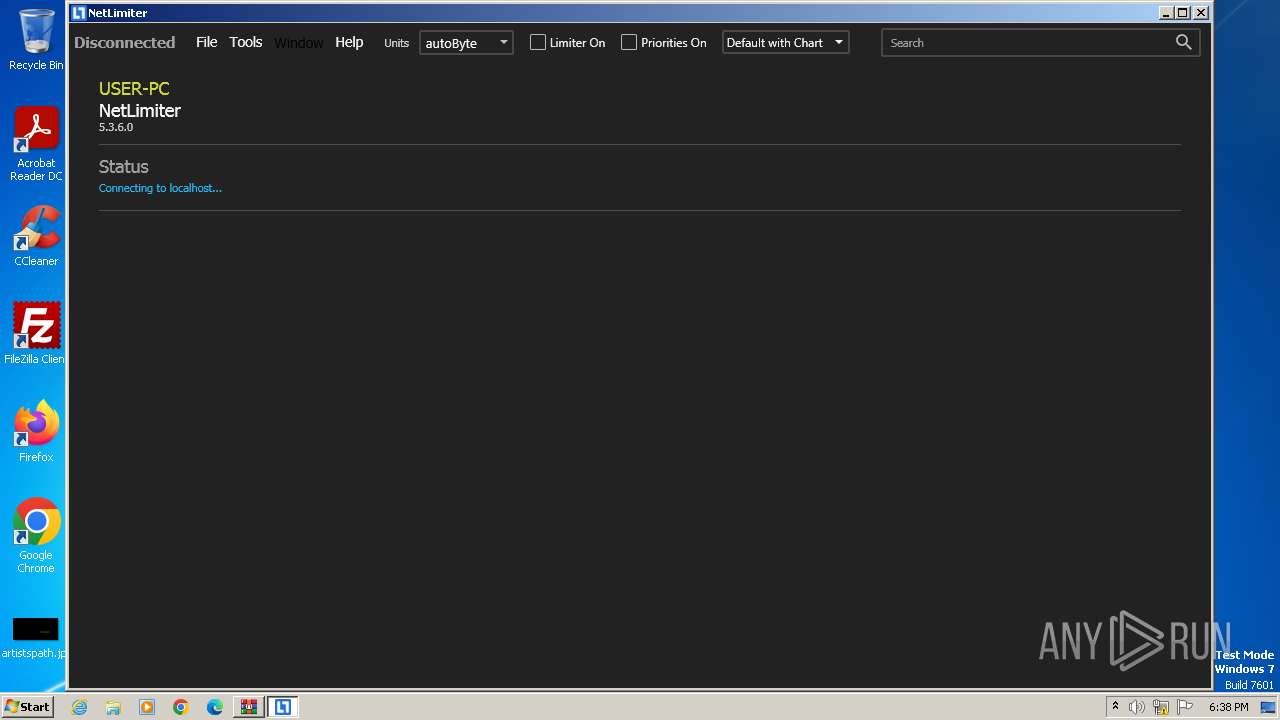
- NLSvc.exe (PID: 2448)
- NLSvc.exe (PID: 3336)
- NLClientApp.exe (PID: 2724)
- NLClientApp.exe (PID: 2448)
- NLSvc.exe (PID: 2840)
- NLClientApp.exe (PID: 3472)
Reads settings of System Certificates
- netlimiter-5.3.6.0.exe (PID: 2544)
- netlimiter-5.3.6.0.exe (PID: 3044)
- NLSvc.exe (PID: 2448)
- NLClientApp.exe (PID: 2724)
- NLClientApp.exe (PID: 2448)
- NLClientApp.exe (PID: 3472)
Reads security settings of Internet Explorer
- netlimiter-5.3.6.0.exe (PID: 2544)
- netlimiter-5.3.6.0.exe (PID: 3044)
- NLSvc.exe (PID: 2448)
- NLClientApp.exe (PID: 2724)
- NLClientApp.exe (PID: 2448)
- NLClientApp.exe (PID: 3472)
Adds/modifies Windows certificates
- netlimiter-5.3.6.0.exe (PID: 2544)
- netlimiter-5.3.6.0.exe (PID: 3044)
Reads the Internet Settings
- netlimiter-5.3.6.0.exe (PID: 2544)
- NLSvc.exe (PID: 2448)
- NLClientApp.exe (PID: 2724)
- NLClientApp.exe (PID: 2448)
- NetLimiter Keygen v1.3.exe (PID: 2076)
- NLClientApp.exe (PID: 3472)
Reads the Windows owner or organization settings
- netlimiter-5.3.6.0.exe (PID: 2544)
- netlimiter-5.3.6.0.exe (PID: 3044)
Application launched itself
- netlimiter-5.3.6.0.exe (PID: 2544)
Reads Internet Explorer settings
- netlimiter-5.3.6.0.exe (PID: 2544)
Executes as Windows Service
- VSSVC.exe (PID: 2696)
- NLSvc.exe (PID: 3336)
- NLSvc.exe (PID: 2840)
The process creates files with name similar to system file names
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 4060)
- mscorsvw.exe (PID: 2324)
Process drops legitimate windows executable
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 4060)
- mscorsvw.exe (PID: 1364)
- mscorsvw.exe (PID: 188)
- mscorsvw.exe (PID: 2088)
- mscorsvw.exe (PID: 3072)
- mscorsvw.exe (PID: 3444)
- mscorsvw.exe (PID: 1212)
- mscorsvw.exe (PID: 3352)
- mscorsvw.exe (PID: 2528)
- mscorsvw.exe (PID: 2552)
- mscorsvw.exe (PID: 2144)
- mscorsvw.exe (PID: 280)
- mscorsvw.exe (PID: 4036)
- mscorsvw.exe (PID: 2548)
- mscorsvw.exe (PID: 2520)
- mscorsvw.exe (PID: 3500)
- mscorsvw.exe (PID: 3936)
- mscorsvw.exe (PID: 2908)
- mscorsvw.exe (PID: 3776)
- mscorsvw.exe (PID: 3380)
- mscorsvw.exe (PID: 756)
- mscorsvw.exe (PID: 4056)
- mscorsvw.exe (PID: 3944)
- mscorsvw.exe (PID: 3988)
- mscorsvw.exe (PID: 3700)
- mscorsvw.exe (PID: 2460)
- mscorsvw.exe (PID: 1588)
- mscorsvw.exe (PID: 2324)
- mscorsvw.exe (PID: 1072)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 2408)
- mscorsvw.exe (PID: 1988)
- mscorsvw.exe (PID: 3980)
- mscorsvw.exe (PID: 644)
- mscorsvw.exe (PID: 788)
- mscorsvw.exe (PID: 2076)
- mscorsvw.exe (PID: 3084)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 1756)
- mscorsvw.exe (PID: 3796)
Drops a system driver (possible attempt to evade defenses)
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 4060)
Creates files in the driver directory
- msiexec.exe (PID: 4060)
Reads the BIOS version
- NetLimiter Keygen v1.3.exe (PID: 1840)
- NetLimiter Keygen v1.3.exe (PID: 2076)
Starts CMD.EXE for commands execution
- NetLimiter Keygen v1.3.exe (PID: 2076)
INFO
Manual execution by a user
- WinRAR.exe (PID: 124)
- netlimiter-5.3.6.0.exe (PID: 1088)
- netlimiter-5.3.6.0.exe (PID: 2544)
- WinRAR.exe (PID: 916)
- NLClientApp.exe (PID: 2448)
- NLClientApp.exe (PID: 3472)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 124)
- WinRAR.exe (PID: 916)
Checks supported languages
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 4060)
- msiexec.exe (PID: 1844)
- netlimiter-5.3.6.0.exe (PID: 3044)
- msiexec.exe (PID: 3228)
- msiexec.exe (PID: 2640)
- NLSvc.exe (PID: 2448)
- NLSvc.exe (PID: 3336)
- ngen.exe (PID: 1248)
- mscorsvw.exe (PID: 4052)
- mscorsvw.exe (PID: 188)
- mscorsvw.exe (PID: 1364)
- mscorsvw.exe (PID: 2612)
- mscorsvw.exe (PID: 2088)
- mscorsvw.exe (PID: 3352)
- mscorsvw.exe (PID: 3072)
- mscorsvw.exe (PID: 3444)
- mscorsvw.exe (PID: 3796)
- mscorsvw.exe (PID: 2144)
- mscorsvw.exe (PID: 1968)
- mscorsvw.exe (PID: 2552)
- mscorsvw.exe (PID: 2528)
- mscorsvw.exe (PID: 280)
- mscorsvw.exe (PID: 4036)
- mscorsvw.exe (PID: 2520)
- mscorsvw.exe (PID: 2908)
- mscorsvw.exe (PID: 2548)
- mscorsvw.exe (PID: 3936)
- mscorsvw.exe (PID: 3944)
- mscorsvw.exe (PID: 3500)
- mscorsvw.exe (PID: 3380)
- mscorsvw.exe (PID: 1212)
- mscorsvw.exe (PID: 3776)
- mscorsvw.exe (PID: 756)
- mscorsvw.exe (PID: 4056)
- mscorsvw.exe (PID: 836)
- mscorsvw.exe (PID: 2392)
- mscorsvw.exe (PID: 2460)
- mscorsvw.exe (PID: 1820)
- mscorsvw.exe (PID: 1072)
- mscorsvw.exe (PID: 3700)
- mscorsvw.exe (PID: 1588)
- mscorsvw.exe (PID: 2324)
- mscorsvw.exe (PID: 3988)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 2076)
- mscorsvw.exe (PID: 2408)
- mscorsvw.exe (PID: 3980)
- mscorsvw.exe (PID: 1988)
- mscorsvw.exe (PID: 644)
- mscorsvw.exe (PID: 3084)
- mscorsvw.exe (PID: 1380)
- mscorsvw.exe (PID: 1756)
- mscorsvw.exe (PID: 788)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 1404)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 3740)
- mscorsvw.exe (PID: 3256)
- mscorsvw.exe (PID: 1828)
- mscorsvw.exe (PID: 1816)
- mscorsvw.exe (PID: 3780)
- NLClientApp.exe (PID: 2724)
- NetLimiter Keygen v1.3.exe (PID: 1840)
- NetLimiter Keygen v1.3.exe (PID: 2076)
- NLClientApp.exe (PID: 2448)
- mscorsvw.exe (PID: 2984)
- NLSvcCliCnnCheck.exe (PID: 2836)
- NLClientApp.exe (PID: 3472)
- NLSvcCliCnnCheck.exe (PID: 3668)
- mscorsvw.exe (PID: 3160)
- NLSvc.exe (PID: 2840)
Reads Environment values
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 1844)
- netlimiter-5.3.6.0.exe (PID: 3044)
- msiexec.exe (PID: 3228)
Create files in a temporary directory
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 2640)
- msiexec.exe (PID: 3228)
- msiexec.exe (PID: 4060)
- NetLimiter Keygen v1.3.exe (PID: 2076)
- NetLimiter Keygen v1.3.exe (PID: 1840)
- NLClientApp.exe (PID: 2448)
- NLClientApp.exe (PID: 3472)
Reads the computer name
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 4060)
- msiexec.exe (PID: 1844)
- msiexec.exe (PID: 3228)
- msiexec.exe (PID: 2640)
- NLSvc.exe (PID: 2448)
- ngen.exe (PID: 1248)
- mscorsvw.exe (PID: 4052)
- netlimiter-5.3.6.0.exe (PID: 3044)
- mscorsvw.exe (PID: 2088)
- mscorsvw.exe (PID: 2612)
- mscorsvw.exe (PID: 188)
- mscorsvw.exe (PID: 1364)
- mscorsvw.exe (PID: 3352)
- mscorsvw.exe (PID: 3072)
- NLSvc.exe (PID: 3336)
- mscorsvw.exe (PID: 3444)
- mscorsvw.exe (PID: 3796)
- mscorsvw.exe (PID: 2144)
- mscorsvw.exe (PID: 2552)
- mscorsvw.exe (PID: 2528)
- mscorsvw.exe (PID: 280)
- mscorsvw.exe (PID: 4036)
- mscorsvw.exe (PID: 2520)
- mscorsvw.exe (PID: 2908)
- mscorsvw.exe (PID: 2548)
- mscorsvw.exe (PID: 3936)
- mscorsvw.exe (PID: 3944)
- mscorsvw.exe (PID: 3500)
- mscorsvw.exe (PID: 3380)
- mscorsvw.exe (PID: 1968)
- mscorsvw.exe (PID: 3776)
- mscorsvw.exe (PID: 756)
- mscorsvw.exe (PID: 4056)
- mscorsvw.exe (PID: 836)
- mscorsvw.exe (PID: 1212)
- mscorsvw.exe (PID: 1820)
- mscorsvw.exe (PID: 2392)
- mscorsvw.exe (PID: 2460)
- mscorsvw.exe (PID: 3988)
- mscorsvw.exe (PID: 1072)
- mscorsvw.exe (PID: 3700)
- mscorsvw.exe (PID: 1588)
- mscorsvw.exe (PID: 2324)
- mscorsvw.exe (PID: 2076)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 2408)
- mscorsvw.exe (PID: 1988)
- mscorsvw.exe (PID: 644)
- mscorsvw.exe (PID: 1756)
- mscorsvw.exe (PID: 3980)
- mscorsvw.exe (PID: 1380)
- mscorsvw.exe (PID: 788)
- mscorsvw.exe (PID: 3084)
- mscorsvw.exe (PID: 2984)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 1404)
- mscorsvw.exe (PID: 2760)
- mscorsvw.exe (PID: 3740)
- mscorsvw.exe (PID: 3256)
- mscorsvw.exe (PID: 1828)
- mscorsvw.exe (PID: 3160)
- mscorsvw.exe (PID: 1816)
- mscorsvw.exe (PID: 3780)
- NetLimiter Keygen v1.3.exe (PID: 1840)
- NLClientApp.exe (PID: 2724)
- NetLimiter Keygen v1.3.exe (PID: 2076)
- NLClientApp.exe (PID: 2448)
- NLSvc.exe (PID: 2840)
- NLClientApp.exe (PID: 3472)
Reads the machine GUID from the registry
- netlimiter-5.3.6.0.exe (PID: 2544)
- msiexec.exe (PID: 4060)
- msiexec.exe (PID: 1844)
- netlimiter-5.3.6.0.exe (PID: 3044)
- msiexec.exe (PID: 3228)
- msiexec.exe (PID: 2640)
- NLSvc.exe (PID: 2448)
- NLSvc.exe (PID: 3336)
- ngen.exe (PID: 1248)
- mscorsvw.exe (PID: 4052)
- mscorsvw.exe (PID: 1364)
- mscorsvw.exe (PID: 2612)
- mscorsvw.exe (PID: 188)
- mscorsvw.exe (PID: 2088)
- mscorsvw.exe (PID: 3352)
- mscorsvw.exe (PID: 3072)
- mscorsvw.exe (PID: 3444)
- mscorsvw.exe (PID: 1968)
- mscorsvw.exe (PID: 3796)
- mscorsvw.exe (PID: 2144)
- mscorsvw.exe (PID: 2552)
- mscorsvw.exe (PID: 2528)
- mscorsvw.exe (PID: 280)
- mscorsvw.exe (PID: 4036)
- mscorsvw.exe (PID: 2520)
- mscorsvw.exe (PID: 2908)
- mscorsvw.exe (PID: 2548)
- mscorsvw.exe (PID: 3936)
- mscorsvw.exe (PID: 3944)
- mscorsvw.exe (PID: 3500)
- mscorsvw.exe (PID: 3380)
- mscorsvw.exe (PID: 1212)
- mscorsvw.exe (PID: 3776)
- mscorsvw.exe (PID: 756)
- mscorsvw.exe (PID: 4056)
- mscorsvw.exe (PID: 1820)
- mscorsvw.exe (PID: 2392)
- mscorsvw.exe (PID: 2460)
- mscorsvw.exe (PID: 1072)
- mscorsvw.exe (PID: 3700)
- mscorsvw.exe (PID: 1588)
- mscorsvw.exe (PID: 3988)
- mscorsvw.exe (PID: 2324)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 2076)
- mscorsvw.exe (PID: 3980)
- mscorsvw.exe (PID: 1988)
- mscorsvw.exe (PID: 644)
- mscorsvw.exe (PID: 2408)
- mscorsvw.exe (PID: 788)
- mscorsvw.exe (PID: 1380)
- mscorsvw.exe (PID: 3084)
- mscorsvw.exe (PID: 1756)
- mscorsvw.exe (PID: 2984)
- mscorsvw.exe (PID: 2468)
- mscorsvw.exe (PID: 1404)
- mscorsvw.exe (PID: 836)
- mscorsvw.exe (PID: 3160)
- mscorsvw.exe (PID: 3740)
- mscorsvw.exe (PID: 3256)
- mscorsvw.exe (PID: 1816)
- mscorsvw.exe (PID: 3780)
- mscorsvw.exe (PID: 1828)
- NLClientApp.exe (PID: 2724)
- NetLimiter Keygen v1.3.exe (PID: 1840)
- NetLimiter Keygen v1.3.exe (PID: 2076)
- NLClientApp.exe (PID: 2448)
- mscorsvw.exe (PID: 2760)
- NLSvc.exe (PID: 2840)
- NLClientApp.exe (PID: 3472)
Creates files or folders in the user directory
- netlimiter-5.3.6.0.exe (PID: 2544)
- NLClientApp.exe (PID: 2448)
- NLClientApp.exe (PID: 3472)
Application launched itself
- msiexec.exe (PID: 4060)
Creates files in the program directory
- NLSvc.exe (PID: 2448)
- NLSvc.exe (PID: 3336)
- mscorsvw.exe (PID: 4052)
- NLClientApp.exe (PID: 2724)
- NetLimiter Keygen v1.3.exe (PID: 2076)
Process checks are UAC notifies on
- NetLimiter Keygen v1.3.exe (PID: 1840)
- NetLimiter Keygen v1.3.exe (PID: 2076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
143
Monitored processes
85
Malicious processes
14
Suspicious processes
51
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\NetLimiter.5.3.6.rar" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 188 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 1b0 -InterruptEvent 0 -NGENProcess 1ac -Pipe 1b8 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 280 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 1e4 -InterruptEvent 0 -NGENProcess 228 -Pipe 230 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 644 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 244 -InterruptEvent 0 -NGENProcess 23c -Pipe 284 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 756 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 1e4 -InterruptEvent 0 -NGENProcess 1f8 -Pipe 254 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 788 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 29c -InterruptEvent 0 -NGENProcess 2b0 -Pipe 280 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 836 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 1e4 -InterruptEvent 0 -NGENProcess 21c -Pipe 25c -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 916 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Keygen.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1008 | C:\Windows\system32\net1 start NLSvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1072 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 1b4 -InterruptEvent 0 -NGENProcess 228 -Pipe 1e4 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
68 451
Read events
68 070
Write events
365
Delete events
16
Modification events
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2644) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
591
Suspicious files
154
Text files
103
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\{0A88B24E-778A-4D6C-AEEE-0406A8209E91}\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\CabD073.tmp | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\{0A88B24E-778A-4D6C-AEEE-0406A8209E91}\8209E91\netlimiter-5.3.6.0.msi | executable | |
MD5:BA4A8B7F5666FE355104238BFD2A8515 | SHA256:6577EEC2D310AB68C4DD83B083AF50E4AC561344992A4BAD5A46AA0CA621A09C | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\{0A88B24E-778A-4D6C-AEEE-0406A8209E91}\8209E91\netlimiter-5.3.6.0.x64.msi | executable | |
MD5:52DC7CBAEBE73619A036DF2A28939996 | SHA256:0C9EFB57D3CB8D6E8B22C0888824924BA89238096178D75ED5C915A6CB963B72 | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:DE73F83C05478F16D30B24BF30D04D44 | SHA256:8F785A4F583F19F7A9B2D55356DC14527A60C0D1D97909134025273A9AD17B08 | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C5C8CC0A7FE31816B4641D0465402560 | binary | |
MD5:75F9887714FC28AF544148A1F0DA00A8 | SHA256:54C07A3B83F7F74B9F6F632636A4FAB5C763F38CCDEE04A9A2EAFB3A937C182E | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\MSID2A8.tmp | executable | |
MD5:DB7612F0FD6408D664185CFC81BEF0CB | SHA256:E9E426B679B3EFB233F03C696E997E2DA3402F16A321E954B54454317FCEB240 | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_2544\whitebackground | image | |
MD5:EB93C0ABAE8A7DE7AE6DC3755B12C802 | SHA256:EDA260871BBA09273B71A165DC8B4F254B186046AB383722DC2D8803FA698725 | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_2544\frame_bottom_right.bmp | image | |
MD5:1FB3755FE9676FCA35B8D3C6A8E80B45 | SHA256:384EBD5800BECADF3BD9014686E6CC09344F75CE426E966D788EB5473B28AA21 | |||
| 2544 | netlimiter-5.3.6.0.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_2544\repair.png | image | |
MD5:CE23E801FACF4DC9980692913ECC5FB3 | SHA256:A8856BD3783A5FC30504FD8AFCFABAA8295ECEFC0D91E5CDD00453F2137495D3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
9
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2544 | netlimiter-5.3.6.0.exe | GET | 200 | 151.101.2.133:80 | http://secure.globalsign.com/cacert/codesigningrootr45.crt | unknown | binary | 1.37 Kb | unknown |
2544 | netlimiter-5.3.6.0.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3bd832ed75e71a47 | unknown | compressed | 65.2 Kb | unknown |
3336 | NLSvc.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1a571236a36d6761 | unknown | compressed | 4.66 Kb | unknown |
3336 | NLSvc.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | binary | 1.67 Kb | unknown |
3336 | NLSvc.exe | GET | 200 | 151.101.2.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDEX685ZejurnNJyDZQ%3D%3D | unknown | binary | 1.65 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2544 | netlimiter-5.3.6.0.exe | 151.101.2.133:80 | secure.globalsign.com | FASTLY | US | unknown |
2544 | netlimiter-5.3.6.0.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3336 | NLSvc.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3336 | NLSvc.exe | 151.101.2.133:80 | secure.globalsign.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
secure.globalsign.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |