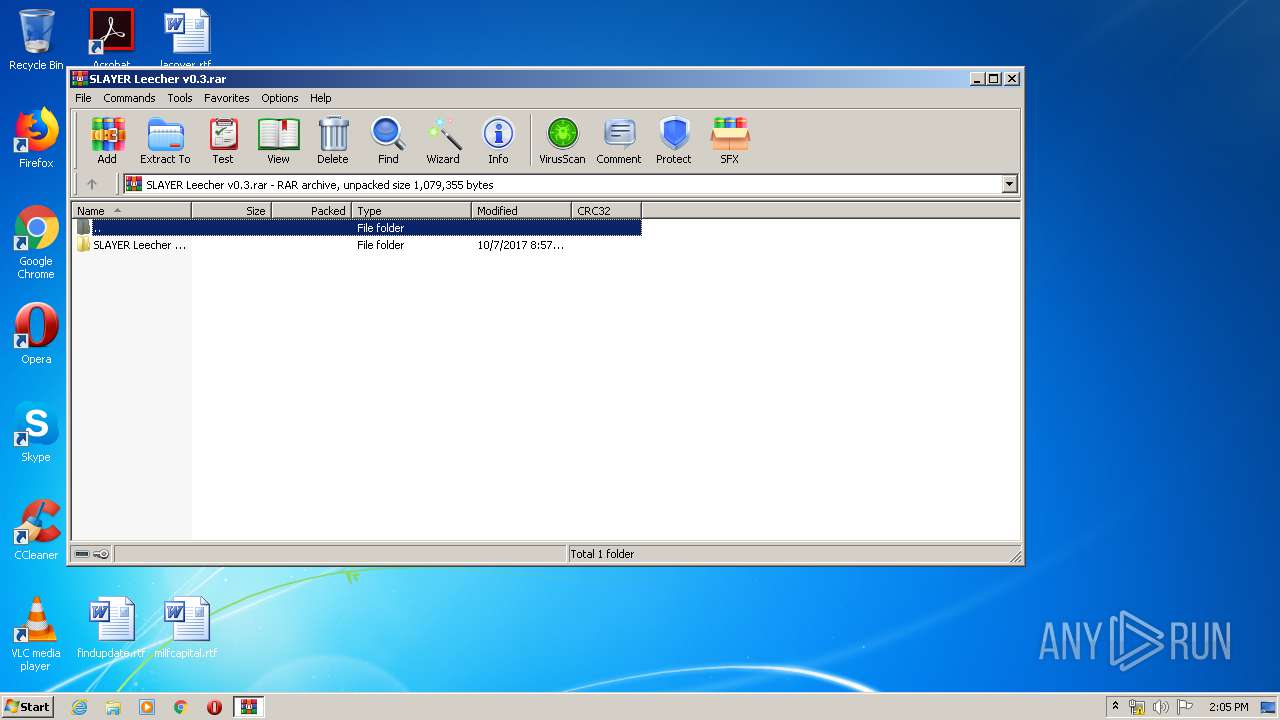
| File name: | SLAYER Leecher v0.3.rar |
| Full analysis: | https://app.any.run/tasks/3b44a1fe-32f1-4a02-877e-5812d7d883d9 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 13:04:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 05E446BED0DD438C6C4A0281B6E2BA5F |
| SHA1: | 48328ACB900A01D0F014BF7472369C3C3C1A97AD |
| SHA256: | 13FC15C1184FF37E87D345A2744D9CA1D75ECAAFB27336012849EC7D609521F7 |
| SSDEEP: | 12288:ARx63hpSy7Q7EZE1wNOs7ql6/H2pGKmGthNBd75Nyko5J8l4oew8Zr2uBY1QMa0O:ARx6RpSy07EZGwQs79P6GTGVvlm8G7wQ |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3372)
Application was dropped or rewritten from another process
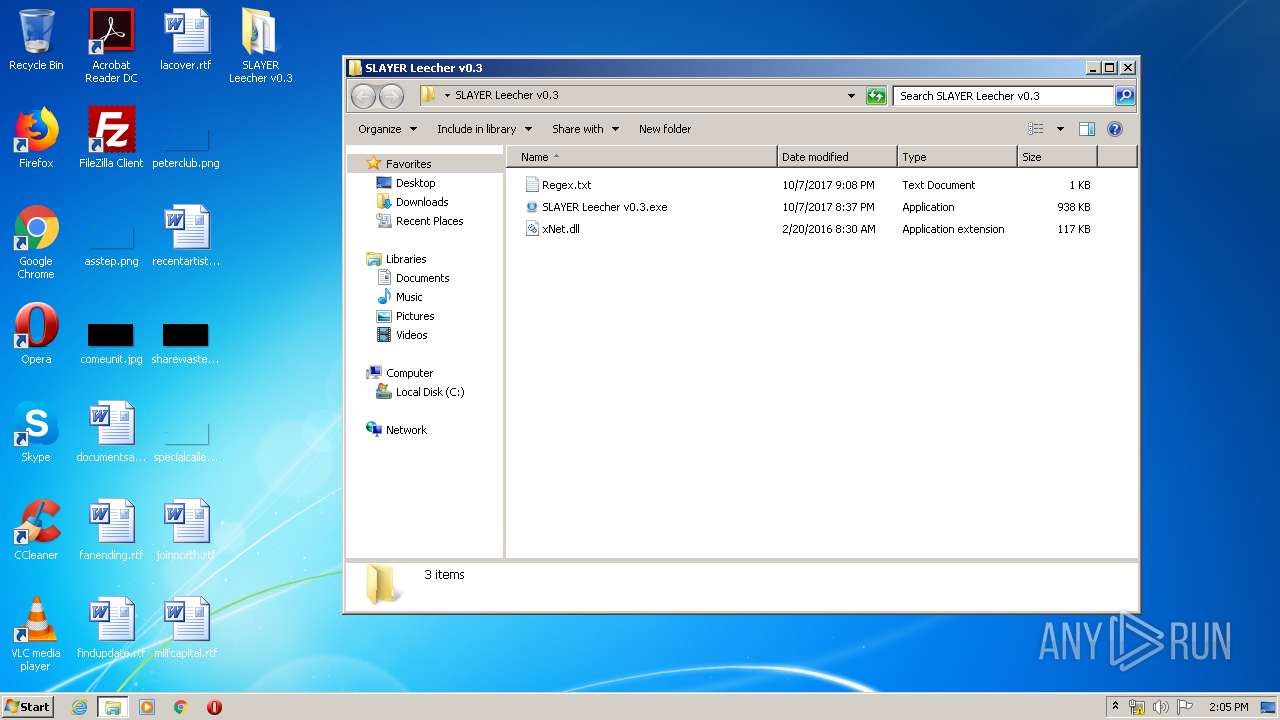
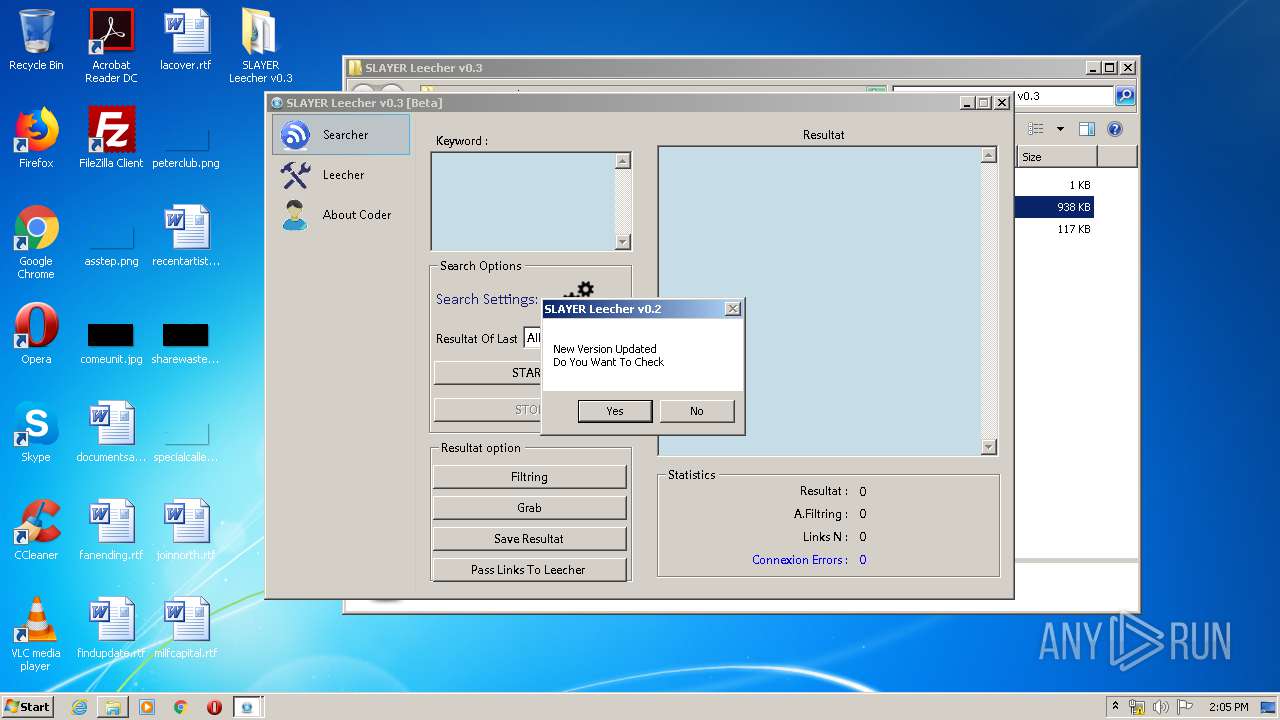
- SLAYER Leecher v0.3.exe (PID: 2556)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2384)
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3548)
Starts Internet Explorer
- SLAYER Leecher v0.3.exe (PID: 2556)
INFO
Reads settings of System Certificates
- SLAYER Leecher v0.3.exe (PID: 2556)
- iexplore.exe (PID: 3032)
Application launched itself
- iexplore.exe (PID: 3032)
Reads Internet Cache Settings
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 3032)
Reads internet explorer settings
- iexplore.exe (PID: 3476)
Changes internet zones settings
- iexplore.exe (PID: 3032)
Manual execution by user
- SLAYER Leecher v0.3.exe (PID: 2556)
Creates files in the user directory
- iexplore.exe (PID: 3476)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3548)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3032)
Changes settings of System certificates
- iexplore.exe (PID: 3032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
42
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2384 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\SLAYER Leecher v0.3.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2556 | "C:\Users\admin\Desktop\SLAYER Leecher v0.3\SLAYER Leecher v0.3.exe" | C:\Users\admin\Desktop\SLAYER Leecher v0.3\SLAYER Leecher v0.3.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: SLAYER Combo Searcher v 0.4 Exit code: 0 Version: 0.4 Modules
| |||||||||||||||
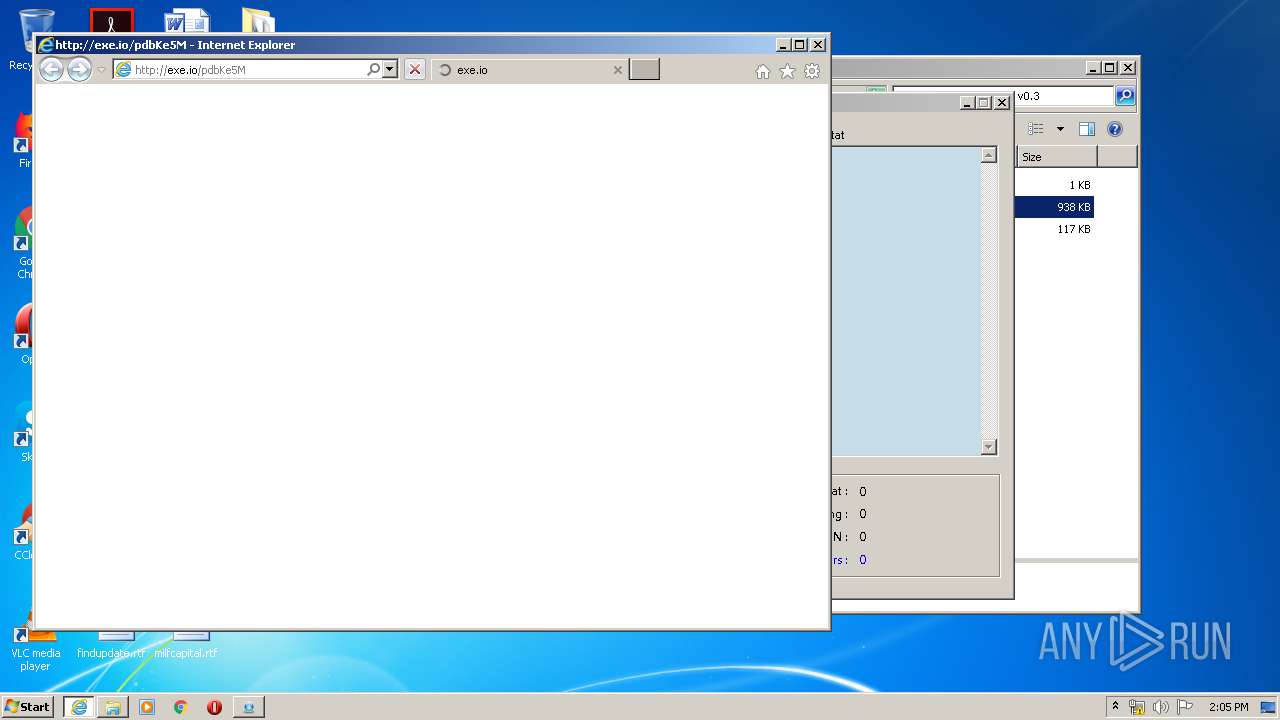
| 3032 | "C:\Program Files\Internet Explorer\iexplore.exe" http://exe.io/pdbKe5M | C:\Program Files\Internet Explorer\iexplore.exe | SLAYER Leecher v0.3.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3372 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3476 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3032 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3548 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
Total events
8 293
Read events
1 853
Write events
4 360
Delete events
2 080
Modification events
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SLAYER Leecher v0.3.rar | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
70
Text files
47
Unknown types
39
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3476 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabF28F.tmp | — | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarF290.tmp | — | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\pdbKe5M[1].htm | html | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3U85BWFV.txt | text | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\59G5GTIY.txt | text | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\pdbKe5M[2].htm | html | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | der | |
MD5:— | SHA256:— | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_74167E25E5476CCA2A5946AAA61BF9E1 | binary | |
MD5:— | SHA256:— | |||
| 2384 | WinRAR.exe | C:\Users\admin\Desktop\SLAYER Leecher v0.3\xNet.dll | executable | |
MD5:3DF8D87A482EFAD957D83819ADB3020F | SHA256:2AC175B4D44245EE8E7AEE9CC36DF86925EF903D8516F20A2C51D84E35F23DA4 | |||
| 3476 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ad-m[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
68
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3476 | iexplore.exe | GET | 301 | 104.26.2.103:80 | http://exe.io/pdbKe5M | US | — | — | malicious |
— | — | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
— | — | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
— | — | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
3476 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCDt7vp1xkTBAgAAAAAPr2u | US | der | 472 b | whitelisted |
— | — | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
3476 | iexplore.exe | GET | 200 | 52.222.168.181:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
— | — | GET | 304 | 52.222.168.58:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
— | — | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
3476 | iexplore.exe | GET | 200 | 216.58.212.131:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEAQoXs0GkwDRCAAAAAA%2Bvho%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2556 | SLAYER Leecher v0.3.exe | 104.23.99.190:443 | pastebin.com | Cloudflare Inc | US | malicious |
3476 | iexplore.exe | 104.26.2.103:80 | exe.io | Cloudflare Inc | US | shared |
3476 | iexplore.exe | 104.26.2.103:443 | exe.io | Cloudflare Inc | US | shared |
3476 | iexplore.exe | 72.21.91.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3032 | iexplore.exe | 104.26.2.103:443 | exe.io | Cloudflare Inc | US | shared |
3476 | iexplore.exe | 172.64.163.34:443 | exee.io | Cloudflare Inc | US | shared |
— | — | 52.222.168.58:80 | o.ss2.us | Amazon.com, Inc. | US | unknown |
— | — | 23.37.43.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
3476 | iexplore.exe | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
— | — | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
exe.io |
| malicious |
ocsp.digicert.com |
| whitelisted |
exee.io |
| malicious |
fonts.googleapis.com |
| whitelisted |
cdn.linearicons.com |
| shared |
dc5k8fg5ioc8s.cloudfront.net |
| shared |
sayfibhat.club |
| suspicious |
d3c3uihon9kmp.cloudfront.net |
| whitelisted |
www.googletagmanager.com |
| whitelisted |