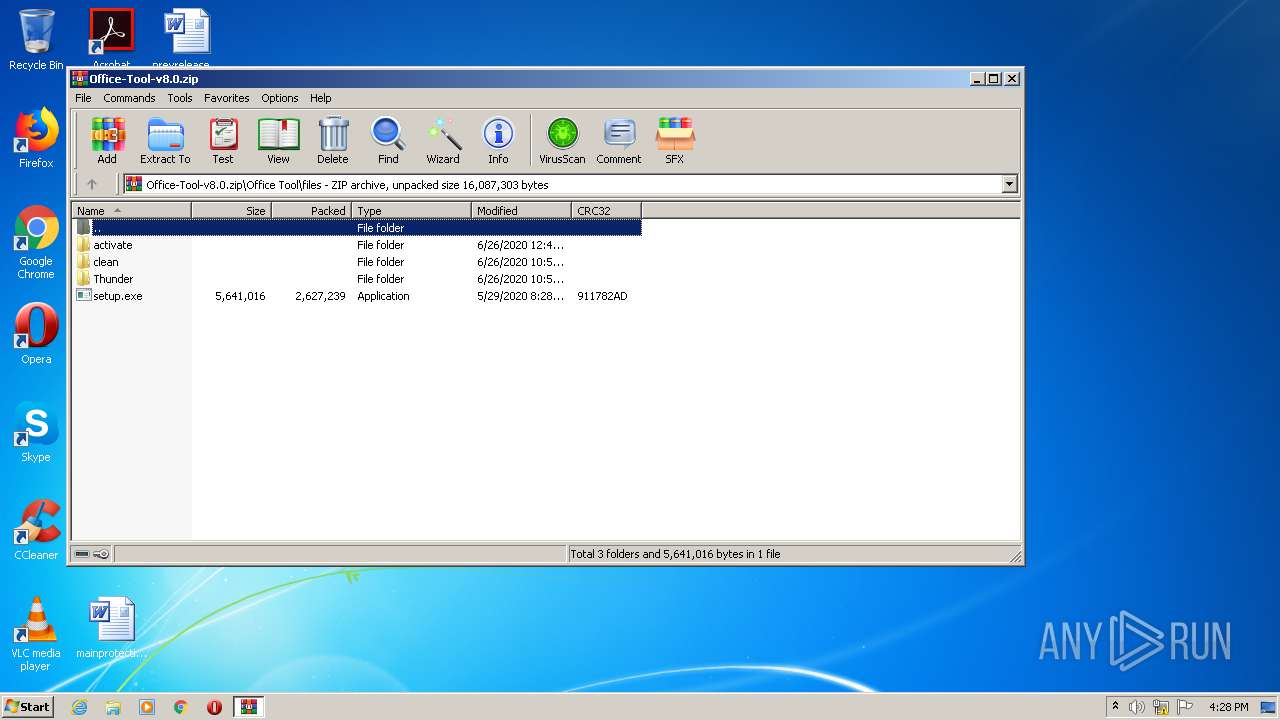
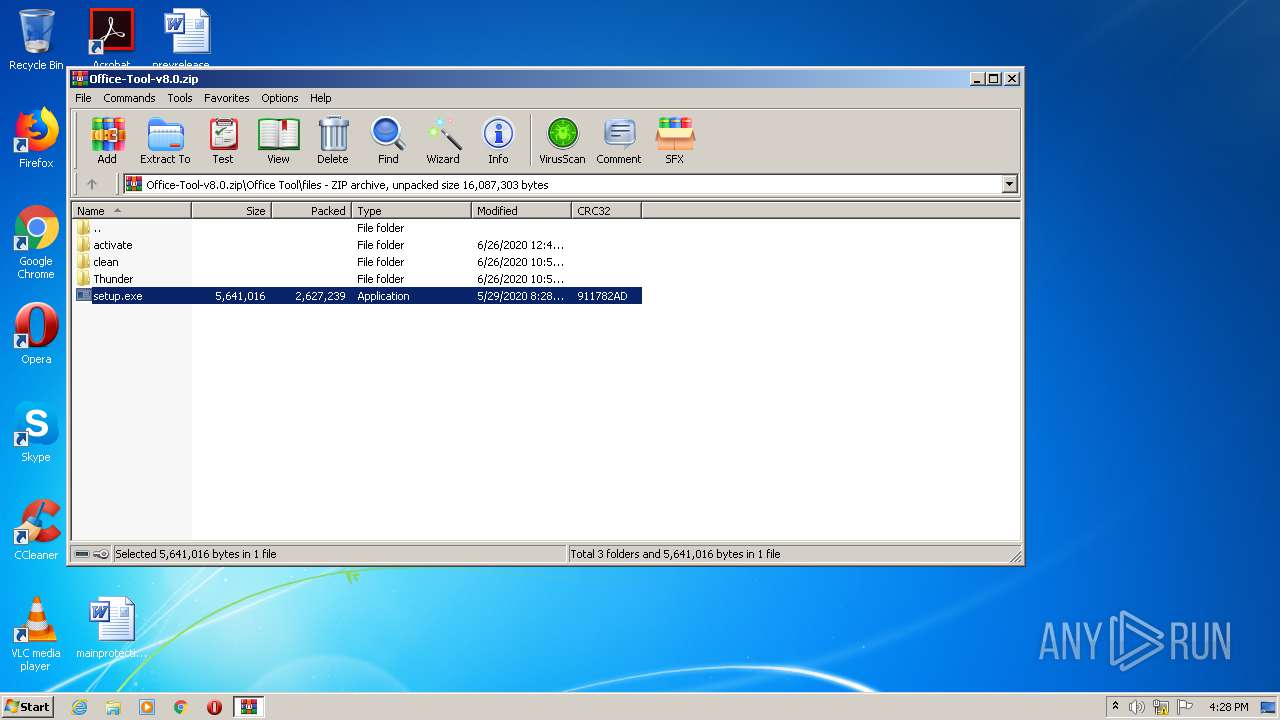
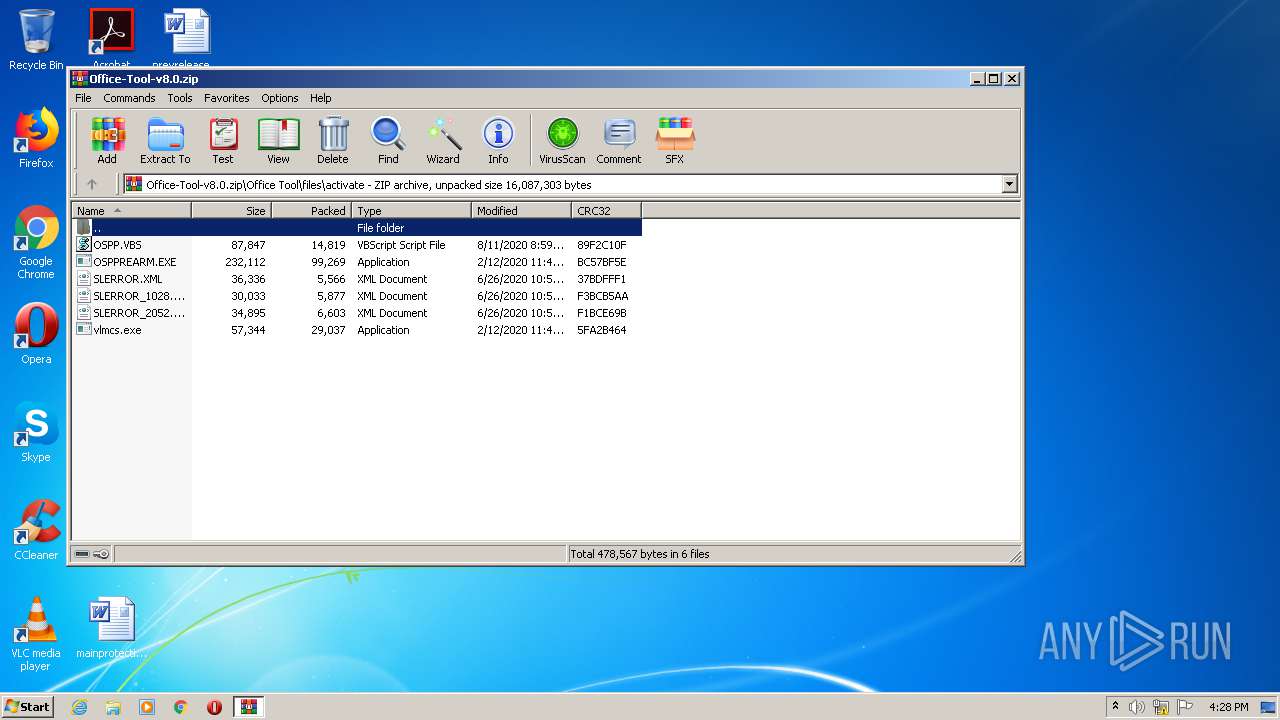
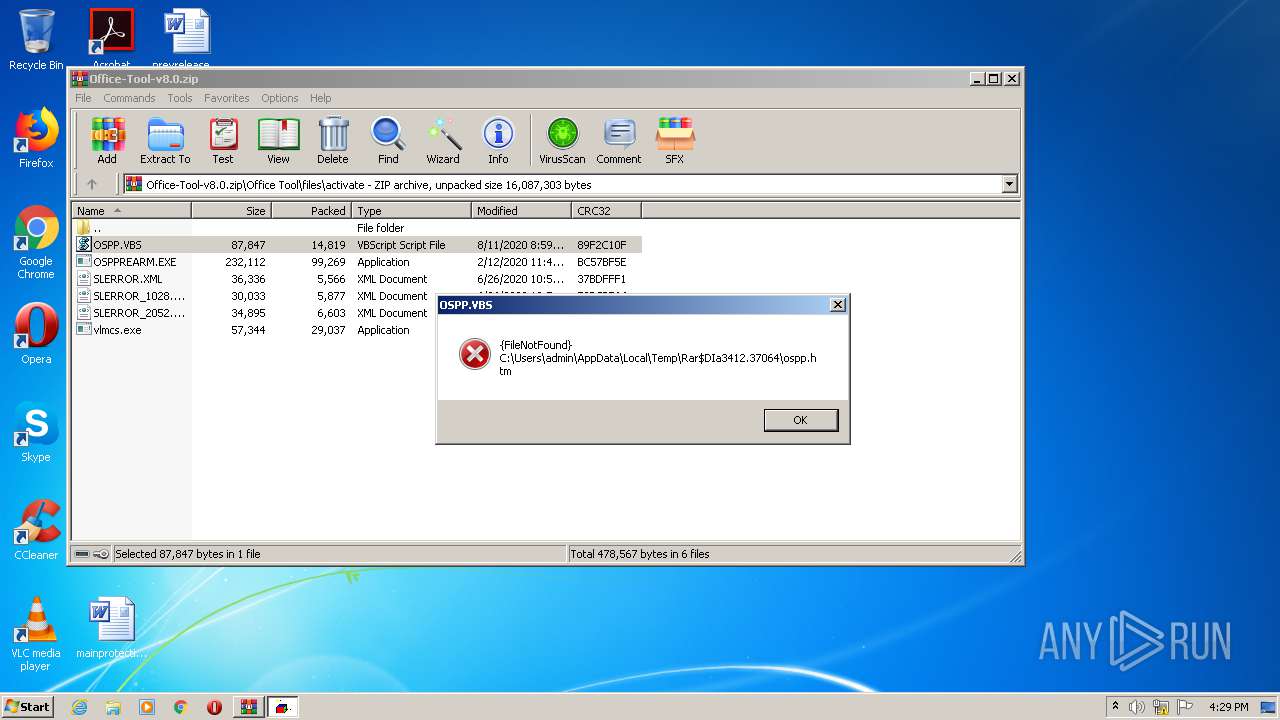
| File name: | Office-Tool-v8.0.zip |
| Full analysis: | https://app.any.run/tasks/846c553e-2a1a-4966-9795-efa3d07af096 |
| Verdict: | Malicious activity |
| Analysis date: | September 17, 2020, 15:28:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 6A5777FEBA7A09489332495385AE7583 |
| SHA1: | B11738F051D97CB4D407955B85E751329B3E03FF |
| SHA256: | 13F290FBB5DD72BCEB938D0C871DD1BA9DF52171F4561456E0D25140D2536151 |
| SSDEEP: | 196608:TqikhON1OVlhZrPvFRQ7R6w73/H8BXLoiX2CewkUX:TqGKVPZrPjExj/WGCewka |
MALICIOUS
Actions looks like stealing of personal data
- WinRAR.exe (PID: 3412)
Application was dropped or rewritten from another process
- setup.exe (PID: 1440)
- Office Tool Plus.exe (PID: 3832)
- Office Tool Plus.exe (PID: 3504)
- Office Tool Plus.exe (PID: 2796)
- Office Tool Plus.exe (PID: 3488)
- cleanospp.exe (PID: 2124)
- vlmcs.exe (PID: 2060)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2168)
- cleanospp.exe (PID: 2124)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3412)
- Office Tool Plus.exe (PID: 3488)
Starts Internet Explorer
- Office Tool Plus.exe (PID: 3504)
- cmd.exe (PID: 3256)
Reads Internet Cache Settings
- setup.exe (PID: 1440)
Executes scripts
- WinRAR.exe (PID: 3412)
Creates files in the program directory
- firefox.exe (PID: 3568)
INFO
Dropped object may contain Bitcoin addresses
- Office Tool Plus.exe (PID: 3488)
Manual execution by user
- Office Tool Plus.exe (PID: 3832)
- Office Tool Plus.exe (PID: 3488)
- Office Tool Plus.exe (PID: 2796)
- Office Tool Plus.exe (PID: 3504)
- firefox.exe (PID: 1144)
- cmd.exe (PID: 3256)
- cleanospp.exe (PID: 2124)
- WScript.exe (PID: 3272)
- WINWORD.EXE (PID: 1332)
- vlmcs.exe (PID: 2060)
Reads Internet Cache Settings
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 3640)
- firefox.exe (PID: 3568)
- pingsender.exe (PID: 3784)
- pingsender.exe (PID: 3484)
- iexplore.exe (PID: 2648)
- pingsender.exe (PID: 652)
- iexplore.exe (PID: 2452)
Changes internet zones settings
- iexplore.exe (PID: 3276)
- iexplore.exe (PID: 2648)
Application launched itself
- iexplore.exe (PID: 3276)
- firefox.exe (PID: 3568)
- firefox.exe (PID: 1144)
- iexplore.exe (PID: 2648)
Reads settings of System Certificates
- iexplore.exe (PID: 3640)
Reads internet explorer settings
- iexplore.exe (PID: 3640)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3640)
Reads CPU info
- firefox.exe (PID: 3568)
Creates files in the user directory
- firefox.exe (PID: 3568)
- WINWORD.EXE (PID: 1332)
Changes settings of System certificates
- iexplore.exe (PID: 3640)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1332)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:08:09 09:26:27 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Office Tool/ |
Total processes
82
Monitored processes
26
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 652 | "C:\Program Files\Mozilla Firefox\pingsender.exe" https://incoming.telemetry.mozilla.org/submit/telemetry/2d9fb232-5a70-490c-b84e-455ff3172f5d/event/Firefox/68.0.1/release/20190717172542?v=4 C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\saved-telemetry-pings\2d9fb232-5a70-490c-b84e-455ff3172f5d | C:\Program Files\Mozilla Firefox\pingsender.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Foundation Integrity Level: MEDIUM Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 1144 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 1332 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1420 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3568.13.1686628164\1673356913" -childID 2 -isForBrowser -prefsHandle 2940 -prefMapHandle 2944 -prefsLen 5996 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3568 "\\.\pipe\gecko-crash-server-pipe.3568" 2956 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 1440 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office Exit code: 0 Version: 16.0.12827.20258 Modules
| |||||||||||||||
| 1952 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3568.3.1211928071\1130710152" -childID 1 -isForBrowser -prefsHandle 1712 -prefMapHandle 1708 -prefsLen 1 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 3568 "\\.\pipe\gecko-crash-server-pipe.3568" 1732 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
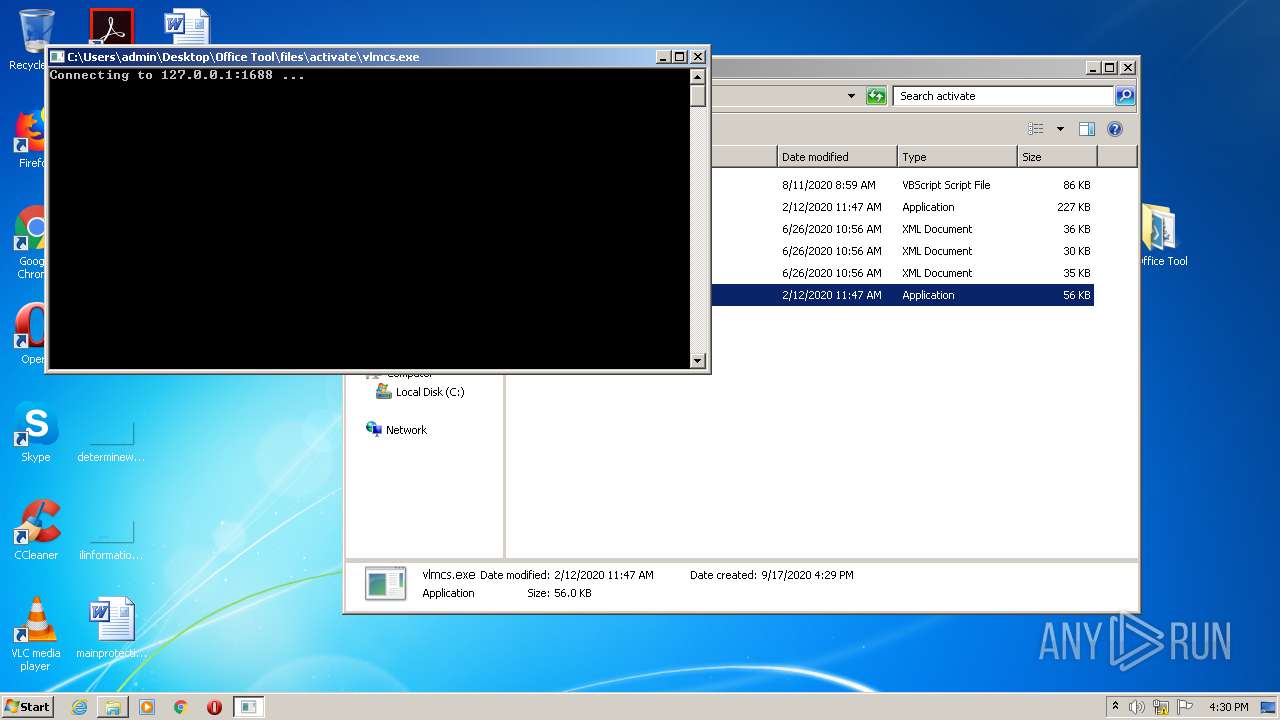
| 2060 | "C:\Users\admin\Desktop\Office Tool\files\activate\vlmcs.exe" | C:\Users\admin\Desktop\Office Tool\files\activate\vlmcs.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2124 | "C:\Users\admin\Desktop\Office Tool\files\clean\x86\cleanospp.exe" | C:\Users\admin\Desktop\Office Tool\files\clean\x86\cleanospp.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2168 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2648 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
2 974
Read events
2 418
Write events
384
Delete events
172
Modification events
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\139\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Office-Tool-v8.0.zip | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\139\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (3412) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
46
Suspicious files
63
Text files
57
Unknown types
42
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
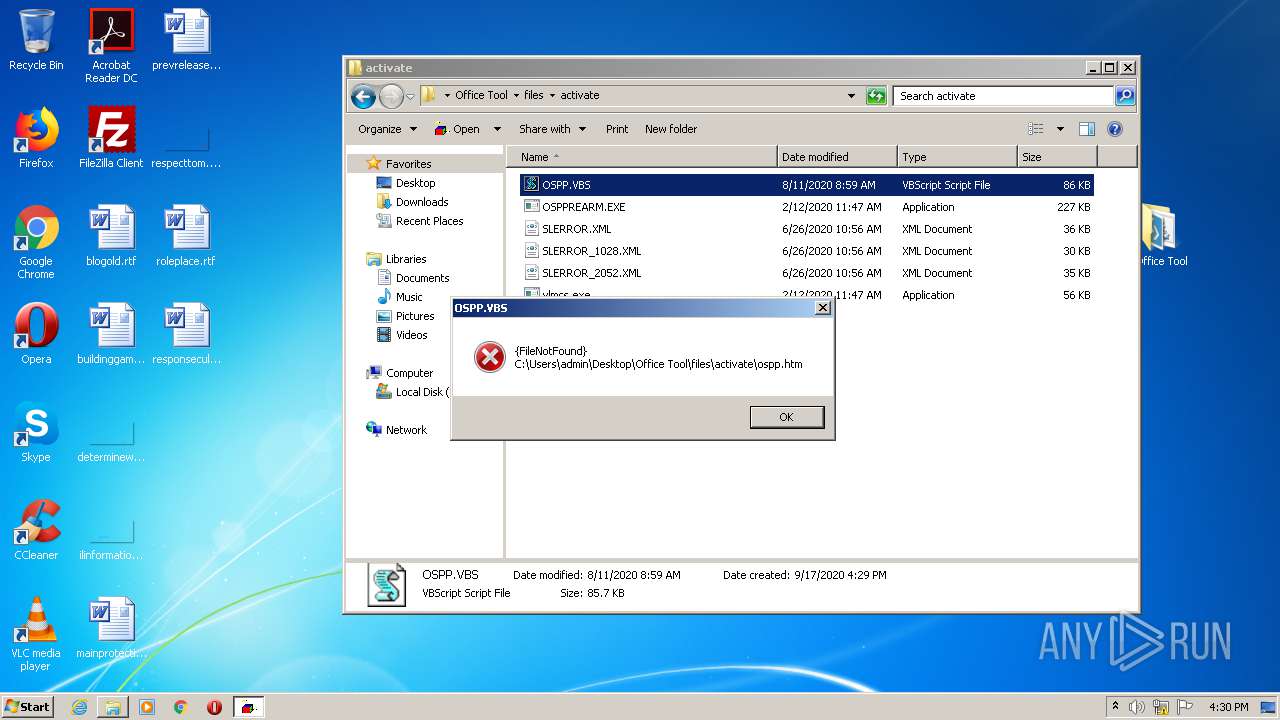
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\activate\OSPP.VBS | text | |
MD5:— | SHA256:— | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\activate\SLERROR_2052.XML | text | |
MD5:— | SHA256:— | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\clean\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\clean\x64\cleanospp.exe | executable | |
MD5:162AB955CB2F002A73C1530AA796477F | SHA256:5CE462E5F34065FC878362BA58617FAB28C22D631B9D836DDDCF43FB1AD4DE6E | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\Thunder\atl71.dll | executable | |
MD5:79CB6457C81ADA9EB7F2087CE799AAA7 | SHA256:A68E1297FAE2BCF854B47FFA444F490353028DE1FA2CA713B6CF6CC5AA22B88A | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\Thunder\dl_peer_id.dll | executable | |
MD5:DBA9A19752B52943A0850A7E19AC600A | SHA256:69A5E2A51094DC8F30788D63243B12A0EB2759A3F3C3A159B85FD422FC00AC26 | |||
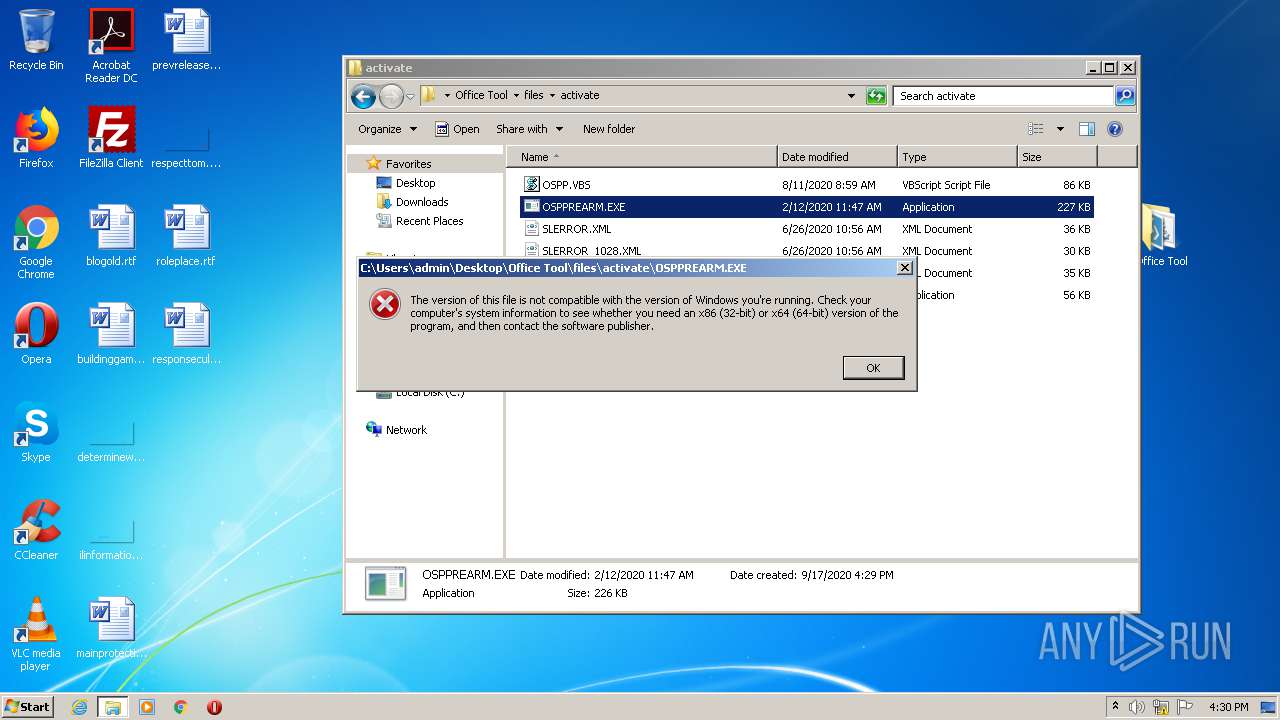
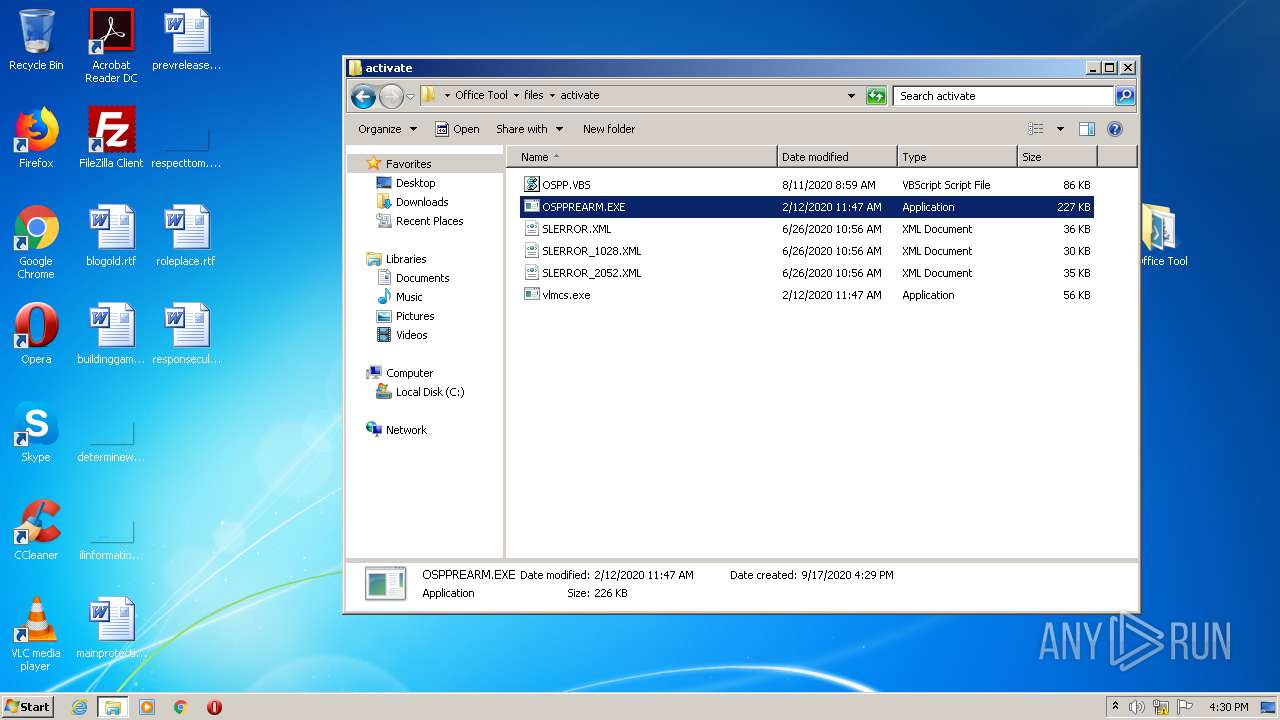
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\activate\OSPPREARM.EXE | executable | |
MD5:0425533B09F71EE34B65F60219A26F8F | SHA256:877811F5FEB1E7B1A6A0EA692B3B13C8351C08E01883C9A64E0A67E1F571CC55 | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\activate\SLERROR_1028.XML | text | |
MD5:— | SHA256:— | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\Thunder\MiniThunderPlatform.exe | executable | |
MD5:9F1D3DFAC55080C712C0281FB2EEEB47 | SHA256:A5622E2BF46CC2EC90C4DCA70372F051BFB5BF55DA3788B5DFCA9429529D285B | |||
| 3412 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3412.36112\Office Tool\files\Thunder\xldl.dll | executable | |
MD5:B700BD2DAF84E4DBBCAD96221A772D6B | SHA256:63AE9DD4A504261591F06BD9457D07629155241DF615BD46A0FB48E76C5E9D56 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
51
DNS requests
70
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3640 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 1.47 Kb | whitelisted |
3640 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
3640 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAtqs7A%2Bsan2xGCSaqjN%2FrM%3D | US | der | 1.47 Kb | whitelisted |
1048 | svchost.exe | GET | 200 | 2.16.186.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | der | 1.11 Kb | whitelisted |
3568 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3640 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 1.47 Kb | whitelisted |
3568 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://ocsp.pki.goog/gts1o1core | US | der | 472 b | whitelisted |
3276 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3640 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAtqs7A%2Bsan2xGCSaqjN%2FrM%3D | US | der | 1.47 Kb | whitelisted |
3568 | firefox.exe | GET | 200 | 2.16.177.88:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1440 | setup.exe | 52.113.194.132:443 | ecs.office.com | Microsoft Corporation | US | suspicious |
3640 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3276 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3640 | iexplore.exe | 104.125.79.182:443 | aka.ms | Akamai Technologies, Inc. | NL | unknown |
3640 | iexplore.exe | 13.107.246.10:443 | dotnet.microsoft.com | Microsoft Corporation | US | whitelisted |
3640 | iexplore.exe | 23.210.249.93:443 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3640 | iexplore.exe | 172.217.23.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3568 | firefox.exe | 2.16.177.88:80 | detectportal.firefox.com | Akamai International B.V. | — | suspicious |
3640 | iexplore.exe | 152.199.21.175:443 | az416426.vo.msecnd.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3640 | iexplore.exe | 23.210.248.233:443 | uhf.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ecs.office.com |
| whitelisted |
aka.ms |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
c.s-microsoft.com |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1048 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
Process | Message |
|---|---|
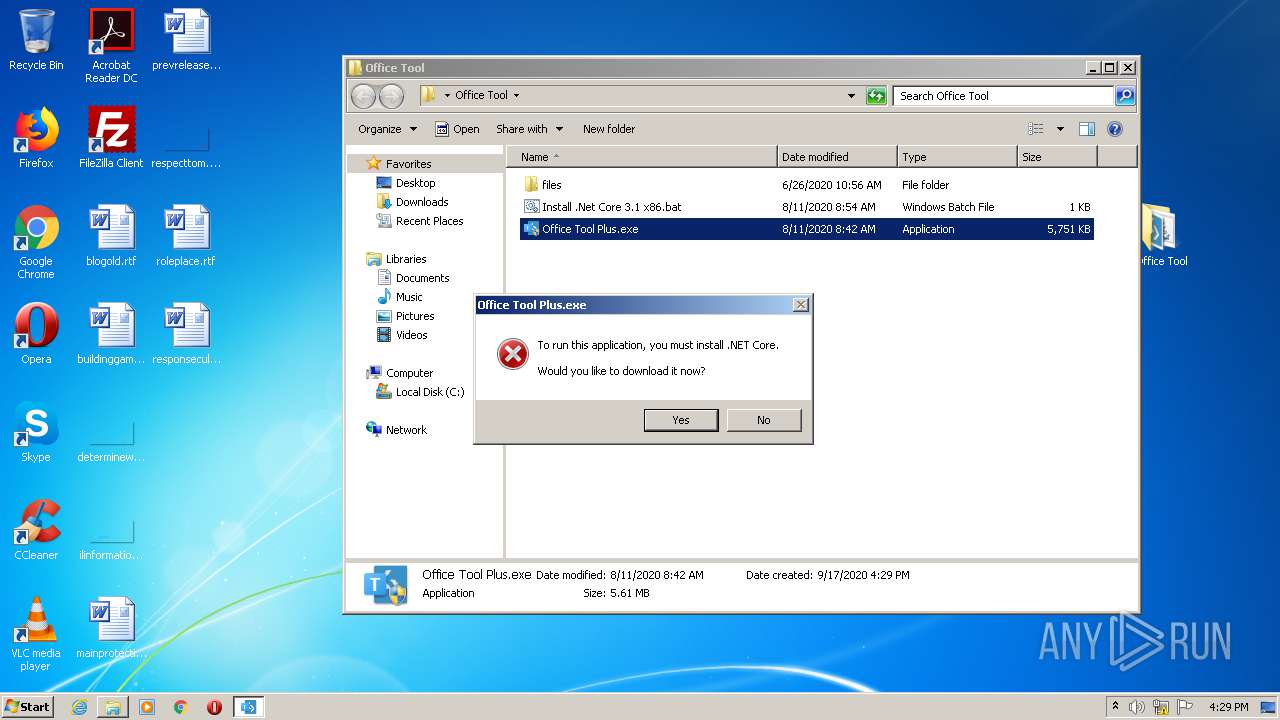
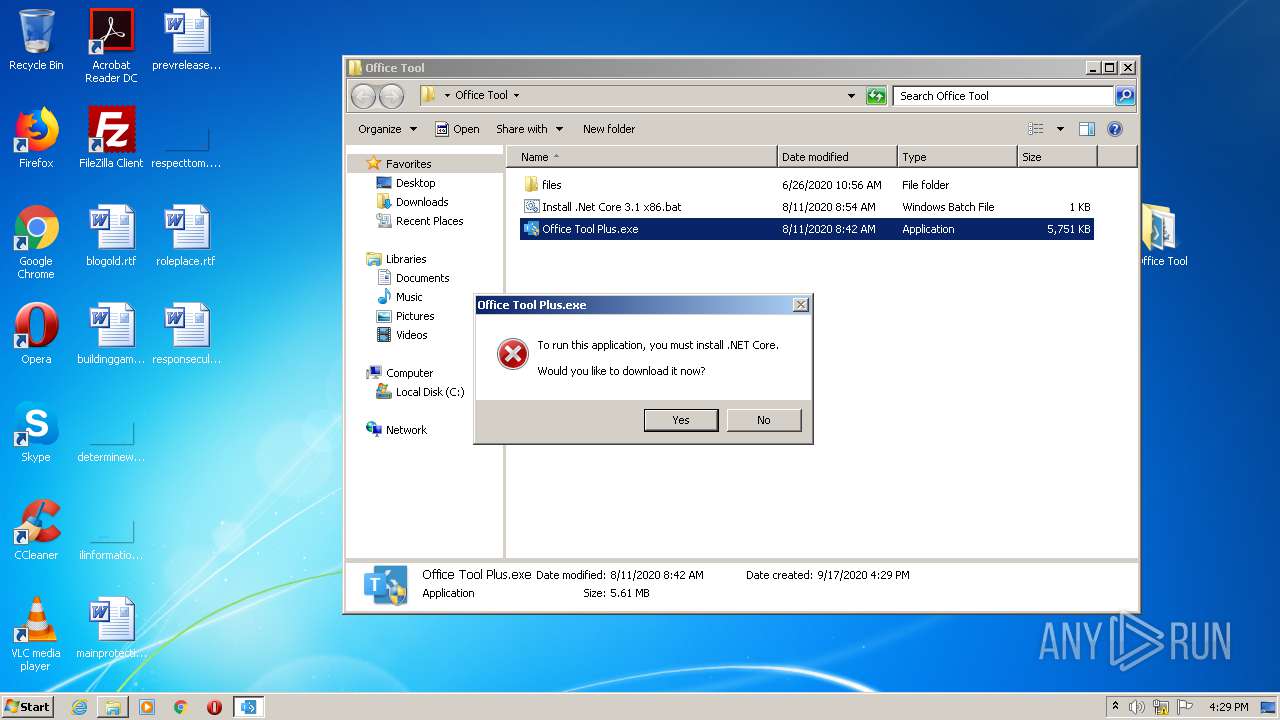
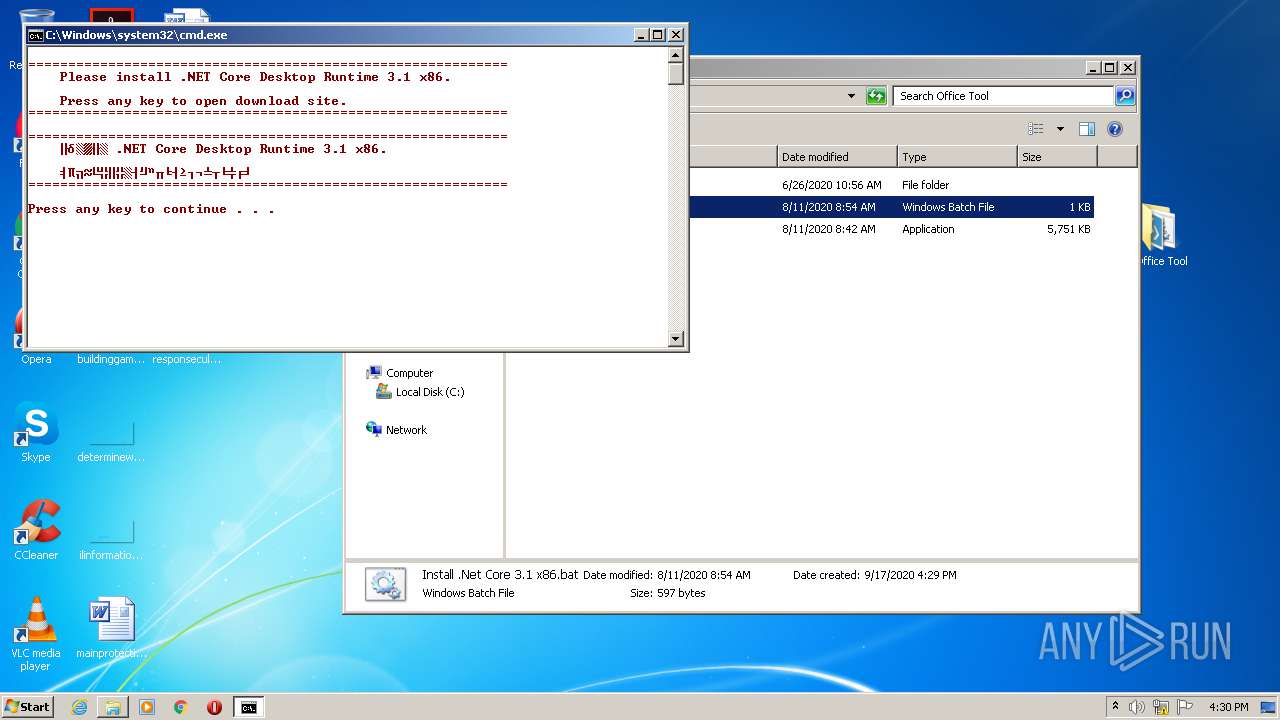
Office Tool Plus.exe | A fatal error occurred. The required library hostfxr.dll could not be found.
If this is a self-contained application, that library should exist in [C:\Users\admin\AppData\Local\Temp\.net\Office Tool Plus\idfffs5q.bq2\].
If this is a framework-dependent application, install the runtime in the global location [C:\Program Files\dotnet] or use the DOTNET_ROOT environment variable to specify the runtime location or register the runtime location in [HKLM\SOFTWARE\dotnet\Setup\InstalledVersions\x86\InstallLocation]. |
Office Tool Plus.exe | - https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x86&rid=win7-x86 |
Office Tool Plus.exe | The .NET Core runtime can be found at: |
Office Tool Plus.exe | - https://aka.ms/dotnet-core-applaunch?missing_runtime=true&arch=x86&rid=win7-x86 |
Office Tool Plus.exe | The .NET Core runtime can be found at: |
Office Tool Plus.exe | The .NET Core runtime can be found at: |