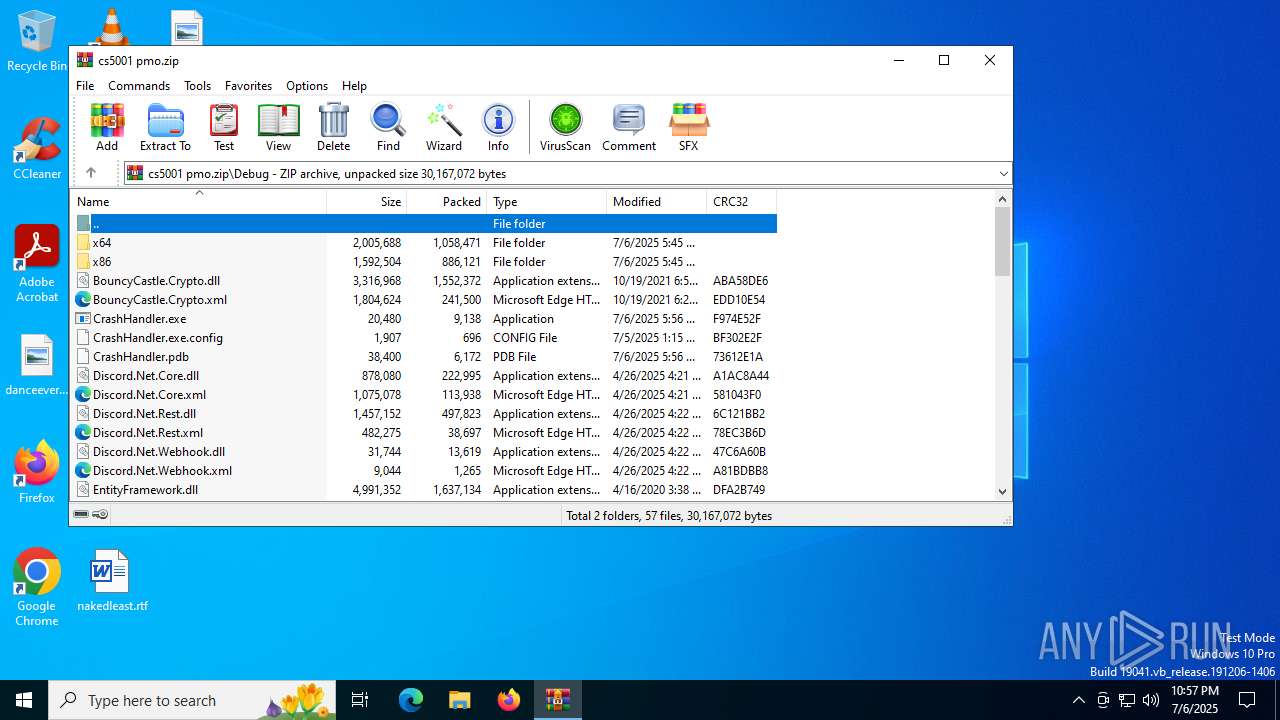
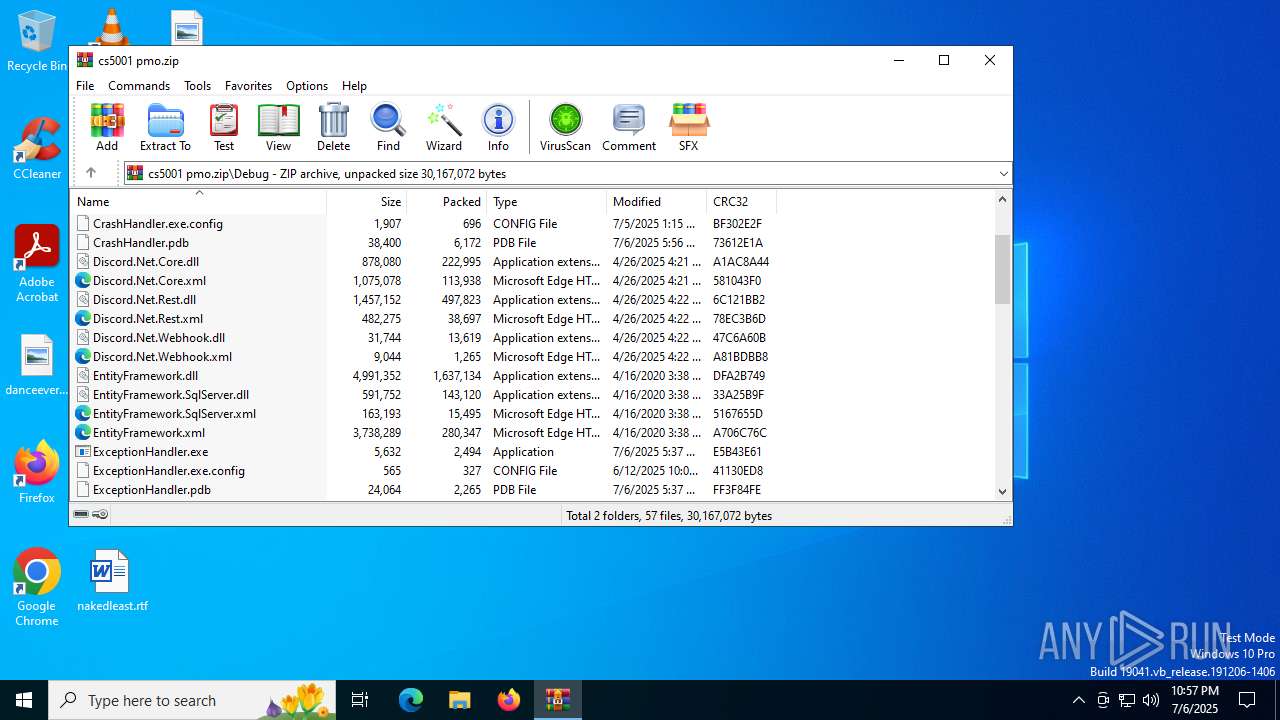
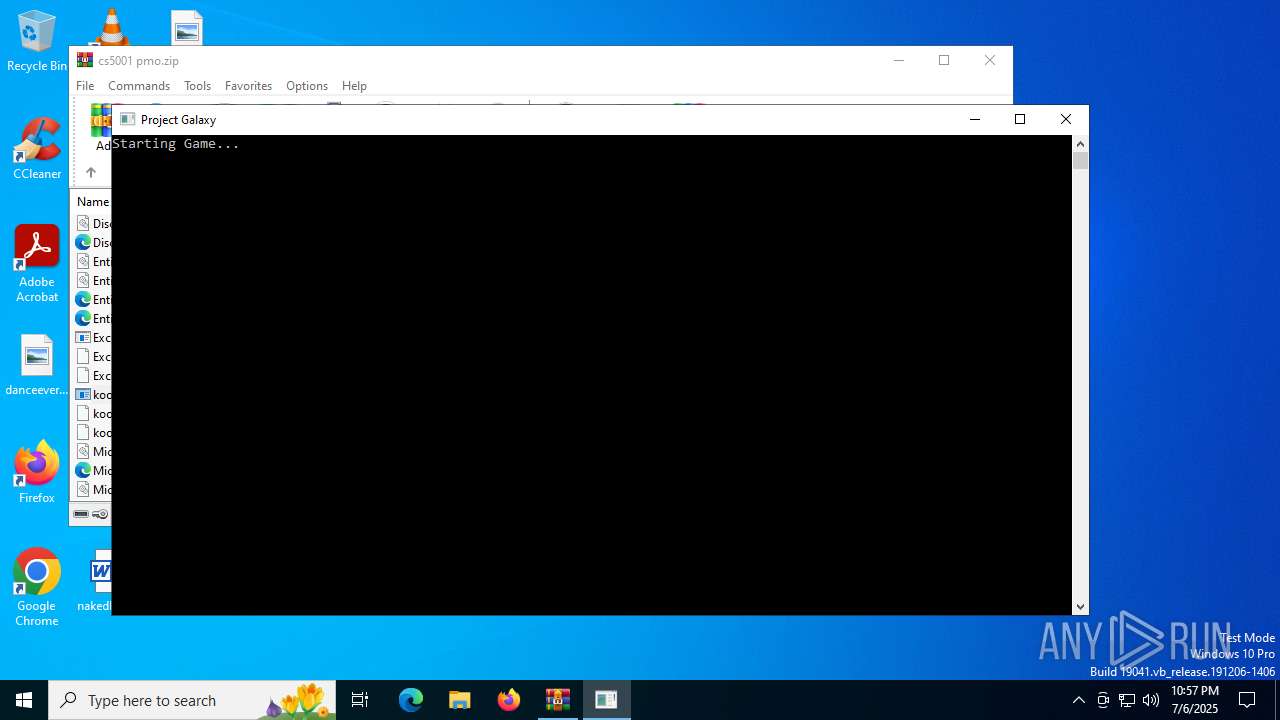
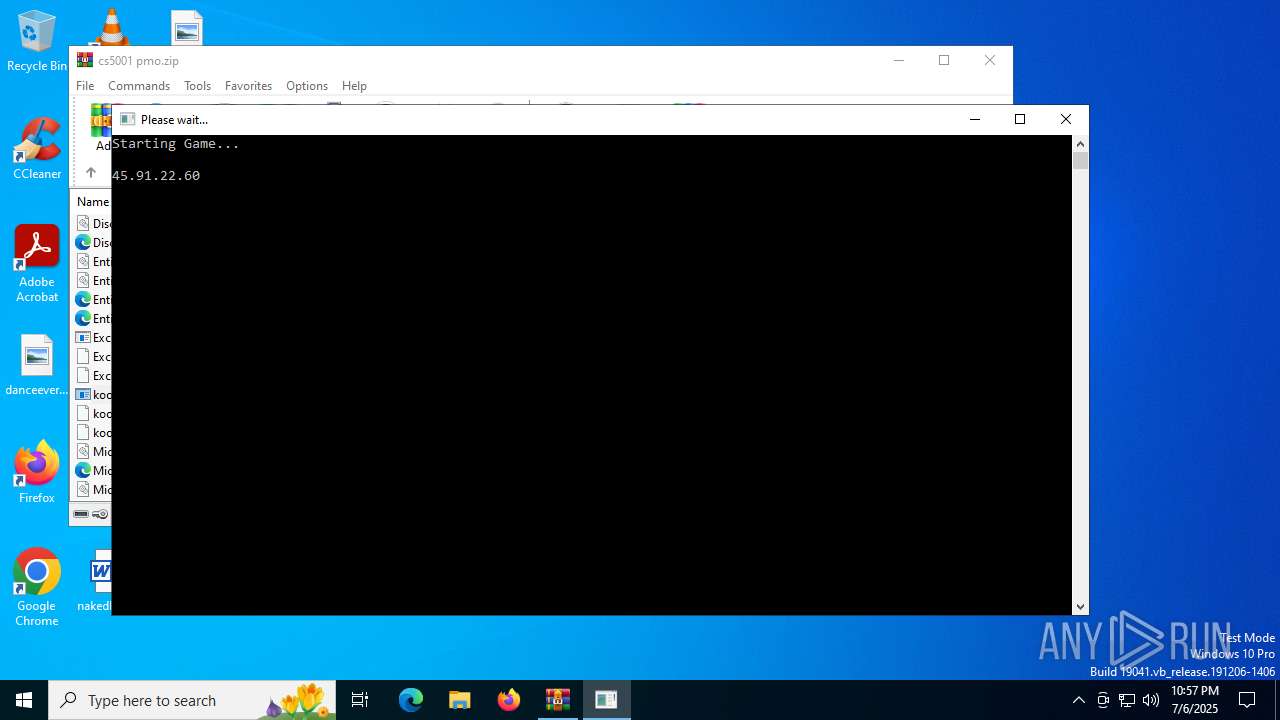
| File name: | cs5001 pmo.zip |
| Full analysis: | https://app.any.run/tasks/14bd2a2c-ae93-4636-b1cc-3bc72a89d0da |
| Verdict: | Malicious activity |
| Threats: | Stealers are a group of malicious software that are intended for gaining unauthorized access to users’ information and transferring it to the attacker. The stealer malware category includes various types of programs that focus on their particular kind of data, including files, passwords, and cryptocurrency. Stealers are capable of spying on their targets by recording their keystrokes and taking screenshots. This type of malware is primarily distributed as part of phishing campaigns. |
| Analysis date: | July 06, 2025, 22:57:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | BC6E84143228D178901731BB7EB38CB7 |
| SHA1: | 8E284C636D9BA1BE893C3281EEC6003FCF5EE69F |
| SHA256: | 13F0AB4008A4B06965A4D8430F091393DF29297C8F4C054F5CE59E2D89BF9AB2 |
| SSDEEP: | 98304:5vaxRVI5zRwpRB6/oKp8IvAUOQNz1A0RKTCatWuuHOA7v0Lxfv3+uV3MXlL+JZ4P:7Abvt5kC5yxYer |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 3100)
Changes Windows Defender settings
- kool.exe (PID: 2468)
TEAPOT has been detected
- kool.exe (PID: 2468)
Actions looks like stealing of personal data
- kool.exe (PID: 2468)
Steals credentials from Web Browsers
- kool.exe (PID: 2468)
Changes settings for real-time protection
- powershell.exe (PID: 1156)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3100)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3100)
- kool.exe (PID: 2468)
Starts POWERSHELL.EXE for commands execution
- kool.exe (PID: 2468)
Checks for external IP
- kool.exe (PID: 2468)
- svchost.exe (PID: 2200)
Script disables Windows Defender's real-time protection
- kool.exe (PID: 2468)
Uses NETSH.EXE to change the status of the firewall
- kool.exe (PID: 2468)
Uses NETSH.EXE to add a firewall rule or allowed programs
- kool.exe (PID: 2468)
Possible usage of Discord/Telegram API has been detected (YARA)
- kool.exe (PID: 2468)
Uses powercfg.exe to modify the power settings
- kool.exe (PID: 2468)
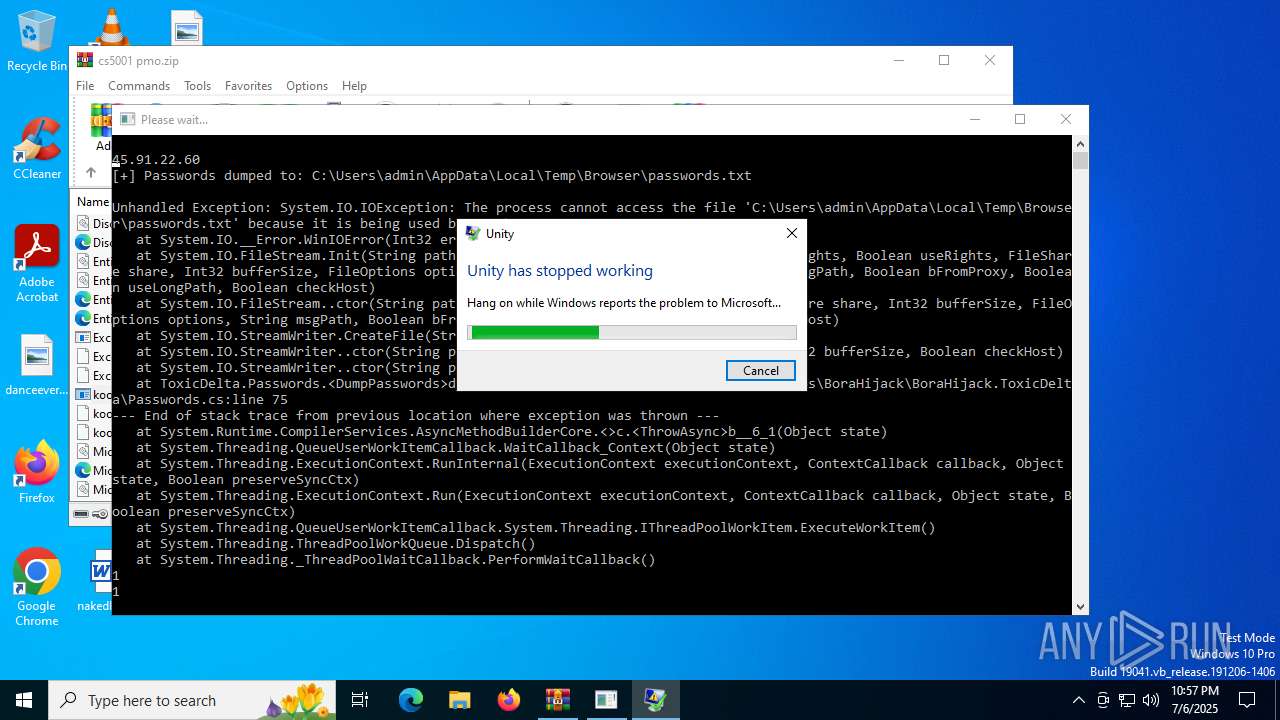
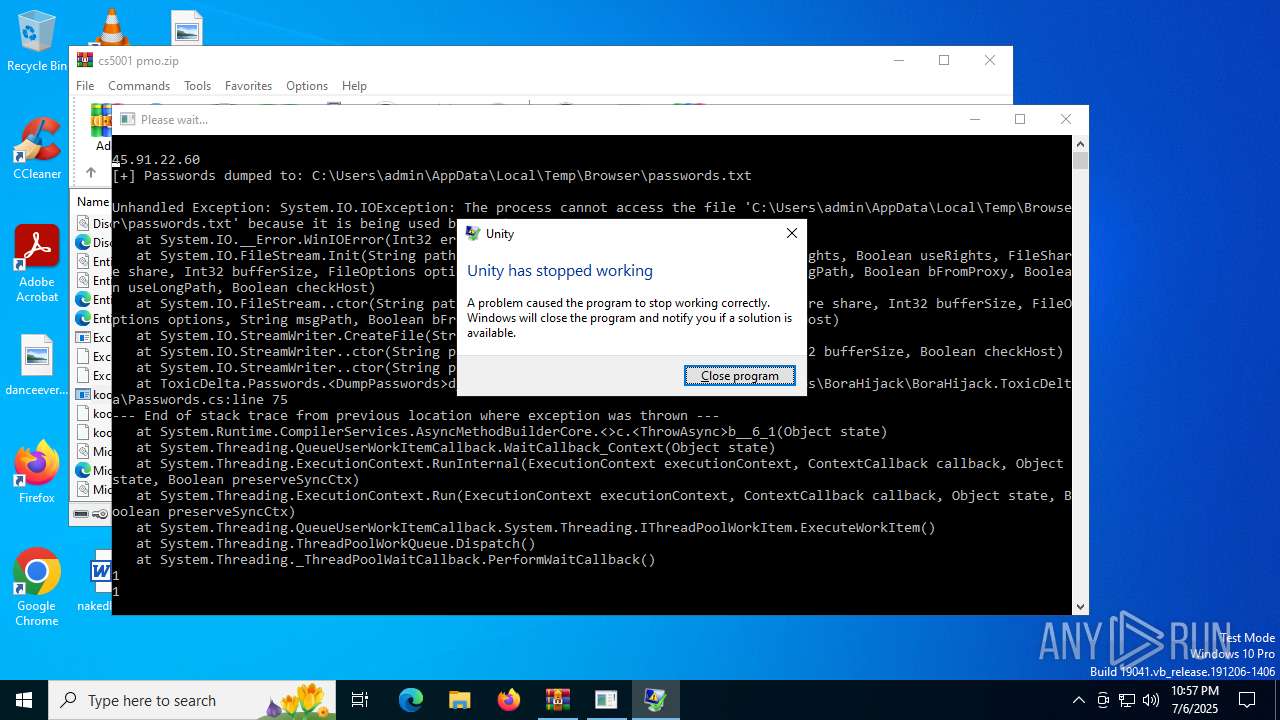
Executes application which crashes
- kool.exe (PID: 2468)
The process connected to a server suspected of theft
- kool.exe (PID: 2468)
INFO
Reads the computer name
- kool.exe (PID: 2468)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3100)
The sample compiled with english language support
- WinRAR.exe (PID: 3100)
Checks supported languages
- kool.exe (PID: 2468)
Creates files in the program directory
- kool.exe (PID: 2468)
Process checks computer location settings
- kool.exe (PID: 2468)
Create files in a temporary directory
- kool.exe (PID: 2468)
Checks proxy server information
- WerFault.exe (PID: 1688)
- slui.exe (PID: 2536)
- kool.exe (PID: 2468)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1156)
Reads the software policy settings
- WerFault.exe (PID: 1688)
- slui.exe (PID: 2536)
- kool.exe (PID: 2468)
Creates files or folders in the user directory
- WerFault.exe (PID: 1688)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1156)
Reads the machine GUID from the registry
- kool.exe (PID: 2468)
Disables trace logs
- kool.exe (PID: 2468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(2468) kool.exe
Discord-Webhook-Tokens (1)1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F
Discord-Info-Links
1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F
Get Webhook Infohttps://discord.com/api/webhooks/1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F
Discord-Webhook-Tokens (1)1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F
Discord-Info-Links
1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F
Get Webhook Infohttps://discord.com/api/webhooks/1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F
Discord-Responses
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleDefender Disabled!
descriptionBoraHijack has disabled Defender
footer
textMade by vanity (v1s0or)
content_scan_version0
timestamp2025-07-06T22:57:53.267000+00:00
edited_timestampnull
flags0
components (0)
id1391553772852871330
channel_id1381560051772297302
author
id1390391079706300456
usernameBoraHijack
avatarc09c54925ccca9a7d9309d30e11d8a3c
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
primary_guildnull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1390391079706300456
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleFirewall
descriptionDisabled Firewall!
color16770560
footer
textInjection/Firewall Service for BoraHijack • By v1s0or
content_scan_version0
timestamp2025-07-06T22:57:54.688000+00:00
edited_timestampnull
flags0
components (0)
id1391553778813112453
channel_id1381560051772297302
author
id1390391079706300456
usernameLambda
avatarnull
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
primary_guildnull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1390391079706300456
type0
content
mentions (0)
mention_roles (0)
attachments (0)
embeds
typerich
titleScreenshot Captured
timestamp2025-07-06T22:57:51.926869+00:00
image
urlhttps://cdn.discordapp.com/attachments/1381560051772297302/1391553769405153441/screenshot.png?ex=686c50f0&is=686aff70&hm=dd756563a206fa437f737ead6662bf32fe48572f6f8e6f36af6acd8052b8c353&
proxy_urlhttps://media.discordapp.net/attachments/1381560051772297302/1391553769405153441/screenshot.png?ex=686c50f0&is=686aff70&hm=dd756563a206fa437f737ead6662bf32fe48572f6f8e6f36af6acd8052b8c353&
width1280
height720
content_typeimage/png
placeholderUrYRLIi5qImMhoefdXkMiGGSCA==
placeholder_version1
footer
textmade by vanity (v1s0or)
content_scan_version2
timestamp2025-07-06T22:57:52.423000+00:00
edited_timestampnull
flags0
components (0)
id1391553769312882708
channel_id1381560051772297302
author
id1390391079706300456
usernameBoraHijack
avatarc09c54925ccca9a7d9309d30e11d8a3c
discriminator0000
public_flags0
flags0
bottrue
global_namenull
clannull
primary_guildnull
pinnedfalse
mention_everyonefalse
ttsfalse
webhook_id1390391079706300456
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:10:19 06:53:32 |
| ZipCRC: | 0xaba58de6 |
| ZipCompressedSize: | 1552372 |
| ZipUncompressedSize: | 3316968 |
| ZipFileName: | Debug/BouncyCastle.Crypto.dll |
Total processes
154
Monitored processes
17
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 592 | "C:\Windows\System32\netsh.exe" advfirewall set allprofiles state off | C:\Windows\SysWOW64\netsh.exe | — | kool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1156 | "powershell" Set-MpPreference -DisableRealtimeMonitoring $true | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | kool.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1688 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 2468 -s 2752 | C:\Windows\SysWOW64\WerFault.exe | kool.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\kool.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\kool.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Unity Version: 1.0.0.0 Modules
ims-api(PID) Process(2468) kool.exe Discord-Webhook-Tokens (1)1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F Discord-Info-Links 1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F Get Webhook Infohttps://discord.com/api/webhooks/1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F (PID) Process(2468) kool.exe Discord-Webhook-Tokens (1)1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F Discord-Info-Links 1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F Get Webhook Infohttps://discord.com/api/webhooks/1390391079706300456/dt5JuIBVLoTFDRFhKBlu3JJ0GHRr875vX6Xz9KCc6_PrUM8tb4AhdKBhd0tbmdvCQM1F Discord-Responses type0 content mentions (0) mention_roles (0) attachments (0) embeds typerich titleDefender Disabled! descriptionBoraHijack has disabled Defender footer textMade by vanity (v1s0or) content_scan_version0 timestamp2025-07-06T22:57:53.267000+00:00 edited_timestampnull flags0 components (0) id1391553772852871330 channel_id1381560051772297302 author id1390391079706300456 usernameBoraHijack avatarc09c54925ccca9a7d9309d30e11d8a3c discriminator0000 public_flags0 flags0 bottrue global_namenull clannull primary_guildnull pinnedfalse mention_everyonefalse ttsfalse webhook_id1390391079706300456 type0 content mentions (0) mention_roles (0) attachments (0) embeds typerich titleFirewall descriptionDisabled Firewall! color16770560 footer textInjection/Firewall Service for BoraHijack • By v1s0or content_scan_version0 timestamp2025-07-06T22:57:54.688000+00:00 edited_timestampnull flags0 components (0) id1391553778813112453 channel_id1381560051772297302 author id1390391079706300456 usernameLambda avatarnull discriminator0000 public_flags0 flags0 bottrue global_namenull clannull primary_guildnull pinnedfalse mention_everyonefalse ttsfalse webhook_id1390391079706300456 type0 content mentions (0) mention_roles (0) attachments (0) embeds typerich titleScreenshot Captured timestamp2025-07-06T22:57:51.926869+00:00 image urlhttps://cdn.discordapp.com/attachments/1381560051772297302/1391553769405153441/screenshot.png?ex=686c50f0&is=686aff70&hm=dd756563a206fa437f737ead6662bf32fe48572f6f8e6f36af6acd8052b8c353& proxy_urlhttps://media.discordapp.net/attachments/1381560051772297302/1391553769405153441/screenshot.png?ex=686c50f0&is=686aff70&hm=dd756563a206fa437f737ead6662bf32fe48572f6f8e6f36af6acd8052b8c353& width1280 height720 content_typeimage/png placeholderUrYRLIi5qImMhoefdXkMiGGSCA== placeholder_version1 footer textmade by vanity (v1s0or) content_scan_version2 timestamp2025-07-06T22:57:52.423000+00:00 edited_timestampnull flags0 components (0) id1391553769312882708 channel_id1381560051772297302 author id1390391079706300456 usernameBoraHijack avatarc09c54925ccca9a7d9309d30e11d8a3c discriminator0000 public_flags0 flags0 bottrue global_namenull clannull primary_guildnull pinnedfalse mention_everyonefalse ttsfalse webhook_id1390391079706300456 | |||||||||||||||
| 2536 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\cs5001 pmo.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4820 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 624
Read events
13 593
Write events
28
Delete events
3
Modification events
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\cs5001 pmo.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2468) kool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\kool_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2468) kool.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\kool_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
30
Suspicious files
12
Text files
33
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\BouncyCastle.Crypto.dll | executable | |
MD5:0CF454B6ED4D9E46BC40306421E4B800 | SHA256:E51721DC0647F4838B1ABC592BD95FD8CB924716E8A64F83D4B947821FA1FA42 | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\Discord.Net.Core.dll | executable | |
MD5:FD74B80FD1A3869F5D9739B0B73DD37A | SHA256:CD3A429CE4B0B26F6238031182509F51B7EA3F4F8D013662325BAA493C22E957 | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\CrashHandler.exe.config | xml | |
MD5:566C416A285BC4AE78242CE08557079A | SHA256:52FCD428084804ED302ACF25E09A6498D6264403A2561E18B67CF63F2C7C81BB | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\CrashHandler.pdb | binary | |
MD5:EA5502994C55BE2B8AA4D5D5702C7CE4 | SHA256:44B35D11283D0A48067CB049BE2AE802C874A70801D0980C4CF5708700979825 | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\Discord.Net.Core.xml | xml | |
MD5:6FBDA8D8FF9A6A0C2452B740C87EC86F | SHA256:CDD16543E2074894F706AA5DCE205C9541ED2F3DE4B144BA0A7717FA05A9546F | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\Discord.Net.Rest.dll | executable | |
MD5:50626F3681286452F989A94BA43B7CBD | SHA256:E1B9DD7B63CD2F5412A5A0B69FCE37148A7CBABA1985BE1967713CBEAE3D7BD8 | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\BouncyCastle.Crypto.xml | xml | |
MD5:253AEC9D04057E346233763B2AE93A11 | SHA256:DE94C224474FAD71CD45A2FCD802976F16B8EDF7DC290F1E353752D495703E10 | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\CrashHandler.exe | executable | |
MD5:F9B828D864FC751916C50C5FEA3DA2B0 | SHA256:0D139CA7F75EF0B890FD8EEC3A3CA455526FA5EA5088AF42FB953B0F67B766B4 | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\EntityFramework.dll | executable | |
MD5:FFDCF232D0BB2FFF78721FB347641A76 | SHA256:FF42BCA704605E187ABB45523868B15128D6AF1C28AD40A4579D507D34A953B2 | |||
| 3100 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\Discord.Net.Webhook.xml | xml | |
MD5:77F3EC7D7D6E721BC58EB9C999F9DA9A | SHA256:A1A1F4236944013D119813A03AB1F643F8A417273EE1692DF93CE5B3CF107777 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
35
DNS requests
20
Threats
18
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.20:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5444 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3672 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3672 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1688 | WerFault.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1688 | WerFault.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4816 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.216.77.20:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5444 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5444 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
discord.com |
| whitelisted |
ipinfo.io |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2200 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
2468 | kool.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2200 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
2468 | kool.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2468 | kool.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2468 | kool.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2468 | kool.exe | Successful Credential Theft Detected | STEALER [ANY.RUN] Attempt to exfiltrate via Discord |
2468 | kool.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2468 | kool.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |
2468 | kool.exe | Device Retrieving External IP Address Detected | ET INFO Possible External IP Lookup Domain Observed in SNI (ipinfo. io) |
Process | Message |
|---|---|
kool.exe | [2025-07-06 22:57:54.8958099] System.Data.SQLite (Preload): Native library pre-loader is trying to load native SQLite library "C:\Users\admin\AppData\Local\Temp\Rar$EXa3100.47721\Debug\x86\SQLite.Interop.dll"...
|
kool.exe | System.Transactions Critical: 0 : |
kool.exe | rveSyncCtx)
at System.Threading.ExecutionContext.Run(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean preserveSyncCtx)
at System.Threading.QueueUserWorkItemCallback.System.Threading.IThreadPoolWorkItem.ExecuteWorkItem()
at System.Threading.ThreadPoolWorkQueue.Dispatch()
at System.Threading._ThreadPoolWaitCallback.PerformWaitCallback()</ExceptionString></Exception></TraceRecord>
|
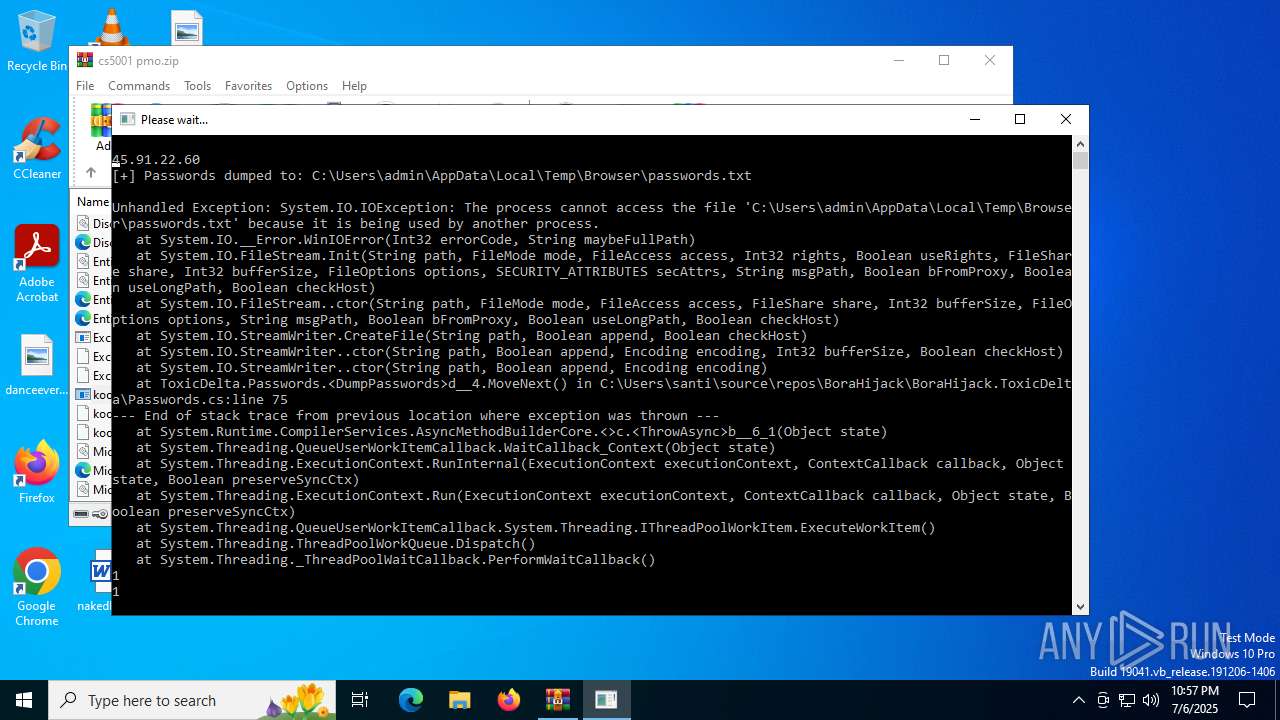
kool.exe | <TraceRecord xmlns="http://schemas.microsoft.com/2004/10/E2ETraceEvent/TraceRecord" Severity="Critical"><TraceIdentifier>http://msdn.microsoft.com/TraceCodes/System/ActivityTracing/2004/07/Reliability/Exception/Unhandled</TraceIdentifier><Description>Unhandled exception</Description><AppDomain>kool.exe</AppDomain><Exception><ExceptionType>System.IO.IOException, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089</ExceptionType><Message>The process cannot access the file 'C:\Users\admin\AppData\Local\Temp\Browser\passwords.txt' because it is being used by another process.</Message><StackTrace> at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath)
at System.IO.FileStream.Init(String path, FileMode mode, FileAccess access, Int32 rights, Boolean useRights, FileShare share, Int32 bufferSize, FileOptions options, SECURITY_ATTRIBUTES secAttrs, String msgPath, Boolean bFromProxy, Boolean useLongPath, Boolean checkHost)
at System.IO.FileStream..ctor(String path, FileMode mode, FileAccess access, FileShare share, Int32 bufferSize, FileOptions options, String msgPath, Boolean bFromProxy, Boolean useLongPath, Boolean checkHost)
at System.IO.StreamWriter.CreateFile(String path, Boolean append, Boolean checkHost)
at System.IO.StreamWriter..ctor(String path, Boolean append, Encoding encoding, Int32 bufferSize, Boolean checkHost)
at System.IO.StreamWriter..ctor(String path, Boolean append, Encoding encoding)
at ToxicDelta.Passwords.&lt;DumpPasswords&gt;d__4.MoveNext() in C:\Users\santi\source\repos\BoraHijack\BoraHijack.ToxicDelta\Passwords.cs:line 75
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.CompilerServices.AsyncMethodBuilderCore.&lt;&gt;c.&lt;ThrowAsync&gt;b__6_1(Object state)
at System.Threading.QueueUserWorkItemCallback.WaitCallback_Context(Object state)
at System.Threading.ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean preserveSyncCtx)
at System.Threading.ExecutionContext.Run(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean preserveSyncCtx)
at System.Threading.QueueUserWorkItemCallback.System.Threading.IThreadPoolWorkItem.ExecuteWorkItem()
at System.Threading.ThreadPoolWorkQueue.Dispatch()
at System.Threading._ThreadPoolWaitCallback.PerformWaitCallback()</StackTrace><ExceptionString>System.IO.IOException: The process cannot access the file 'C:\Users\admin\AppData\Local\Temp\Browser\passwords.txt' because it is being used by another process.
at System.IO.__Error.WinIOError(Int32 errorCode, String maybeFullPath)
at System.IO.FileStream.Init(String path, FileMode mode, FileAccess access, Int32 rights, Boolean useRights, FileShare share, Int32 bufferSize, FileOptions options, SECURITY_ATTRIBUTES secAttrs, String msgPath, Boolean bFromProxy, Boolean useLongPath, Boolean checkHost)
at System.IO.FileStream..ctor(String path, FileMode mode, FileAccess access, FileShare share, Int32 bufferSize, FileOptions options, String msgPath, Boolean bFromProxy, Boolean useLongPath, Boolean checkHost)
at System.IO.StreamWriter.CreateFile(String path, Boolean append, Boolean checkHost)
at System.IO.StreamWriter..ctor(String path, Boolean append, Encoding encoding, Int32 bufferSize, Boolean checkHost)
at System.IO.StreamWriter..ctor(String path, Boolean append, Encoding encoding)
at ToxicDelta.Passwords.&lt;DumpPasswords&gt;d__4.MoveNext() in C:\Users\santi\source\repos\BoraHijack\BoraHijack.ToxicDelta\Passwords.cs:line 75
--- End of stack trace from previous location where exception was thrown ---
at System.Runtime.CompilerServices.AsyncMethodBuilderCore.&lt;&gt;c.&lt;ThrowAsync&gt;b__6_1(Object state)
at System.Threading.QueueUserWorkItemCallback.WaitCallback_Context(Object state)
at System.Threading.ExecutionContext.RunInternal(ExecutionContext executionContext, ContextCallback callback, Object state, Boolean prese |