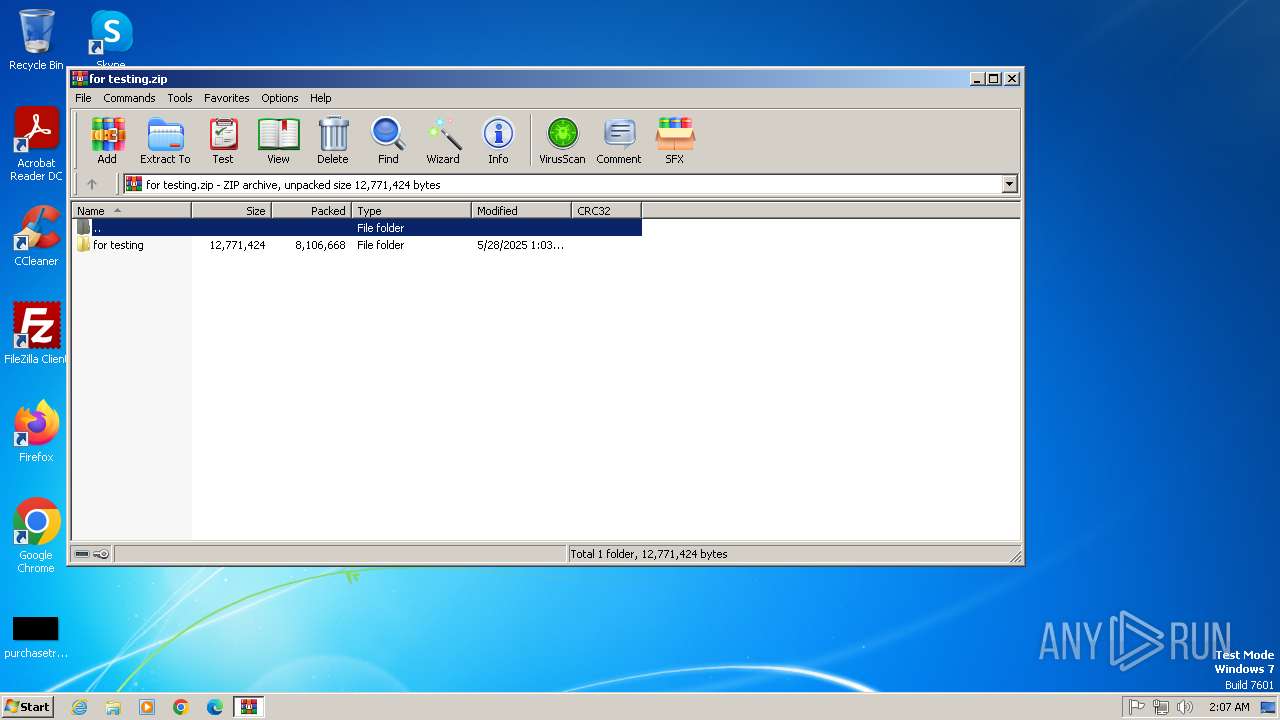
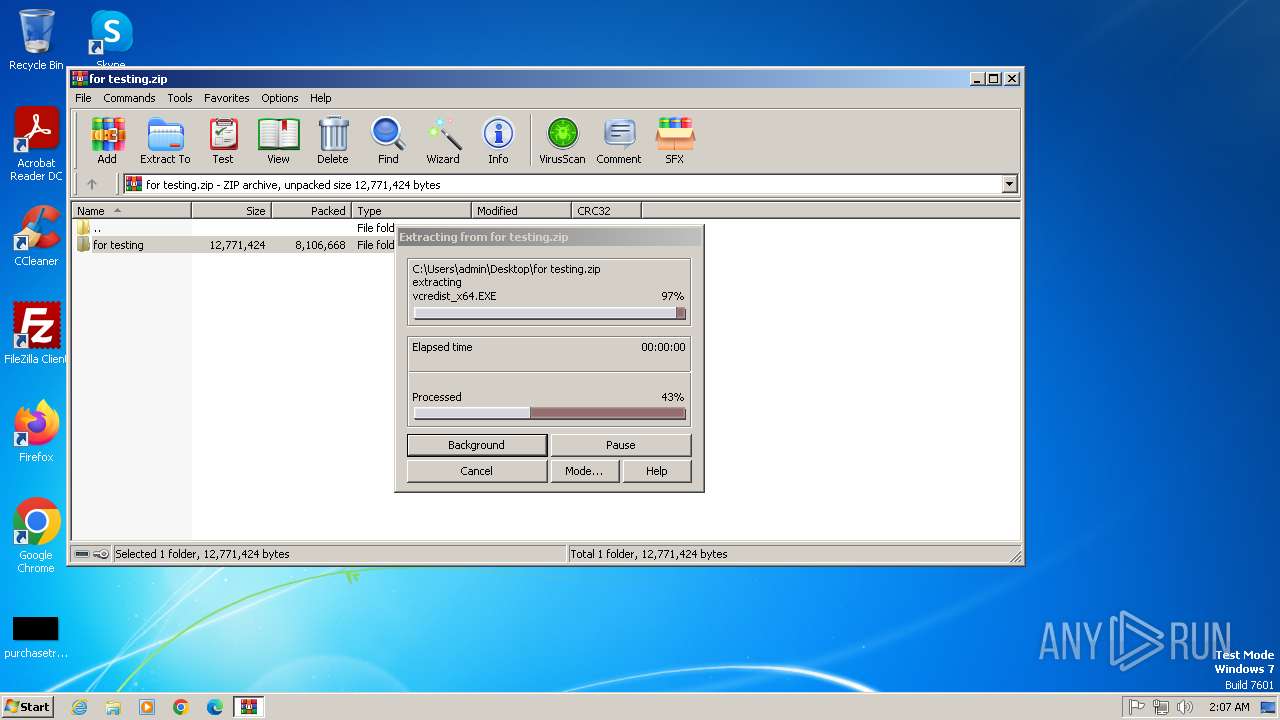
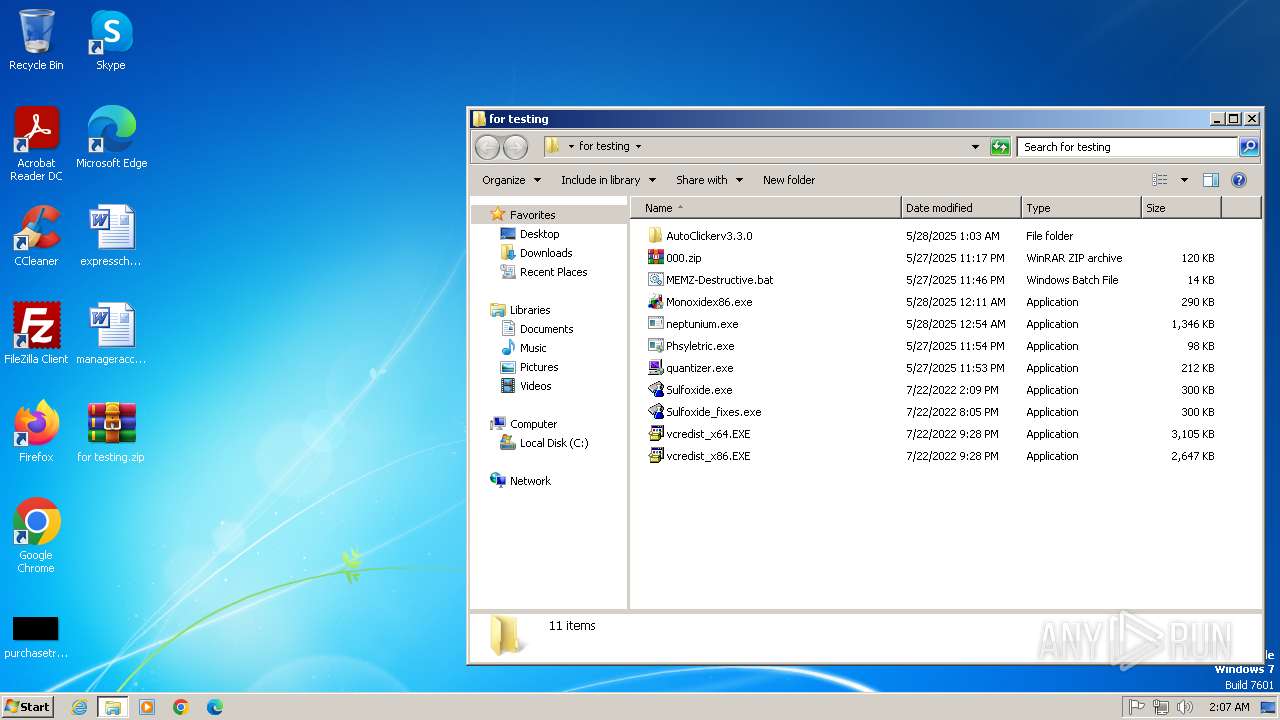
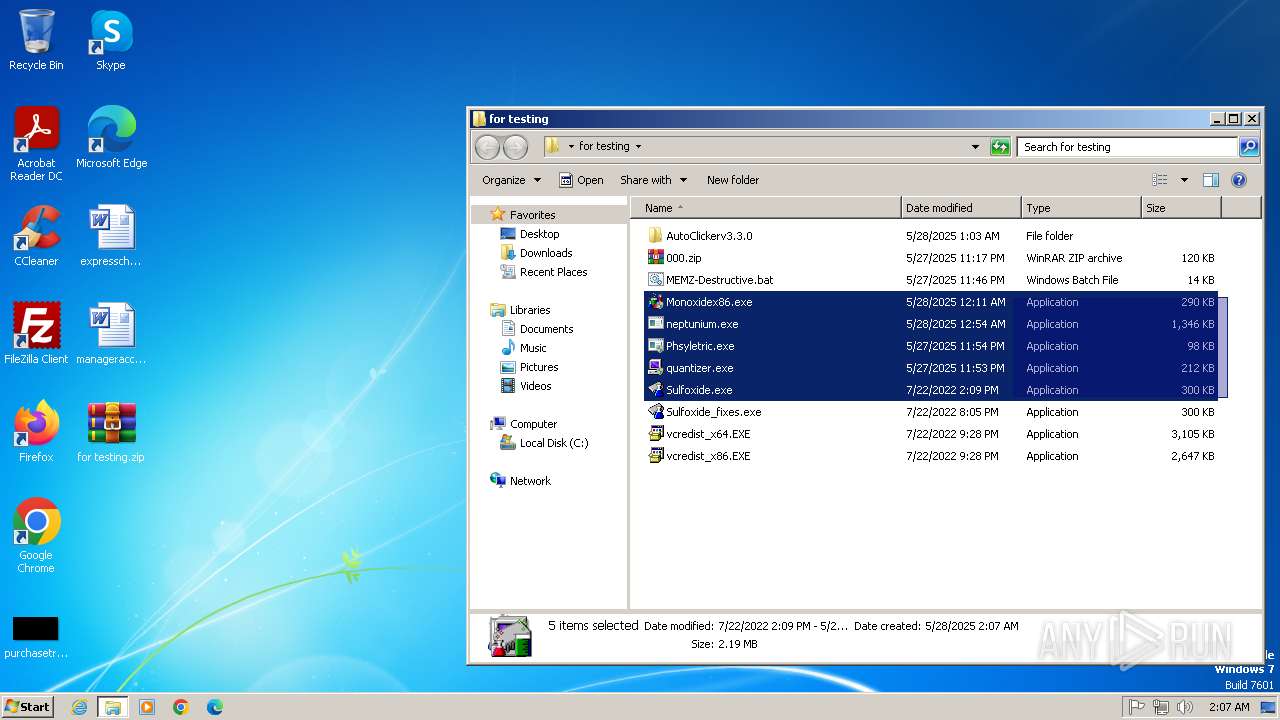
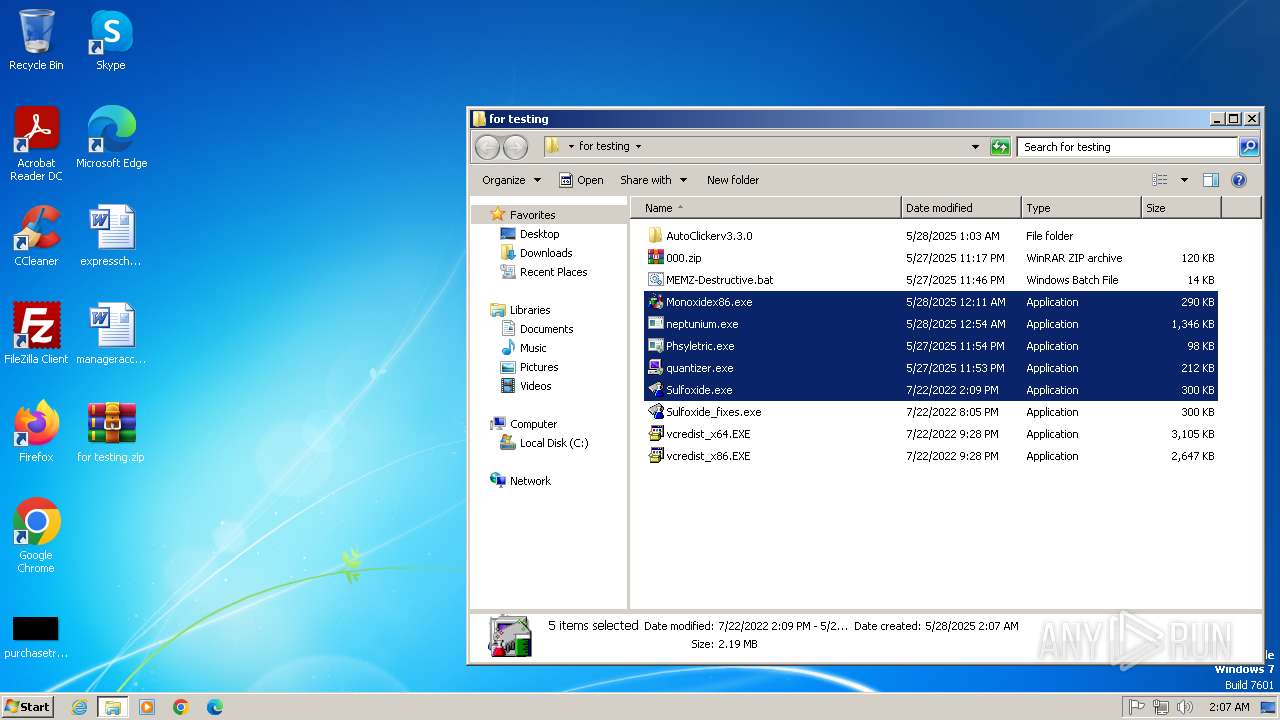
| File name: | for testing.zip |
| Full analysis: | https://app.any.run/tasks/742cd0b5-4948-4dcd-becb-0ff412a6cc9c |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2025, 01:07:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v4.5 to extract, compression method=deflate |
| MD5: | 69D8A7E28E7308AF7D06DDE0108E2ADA |
| SHA1: | 2F5D7C685C691E343F1778595936E23329E5810F |
| SHA256: | 13EF4942B63EAF5D333AB89DF95BEE2C826B648E4F0765E1A0BB16045935CB82 |
| SSDEEP: | 98304:oM/xLURvNr5K9Tpy3gp/j0qAYuqTVrhjXUcR6JsVoP3cDbtcUvCXv1ASMNGQzUcw:rzrTLizTlF2fWV |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2168)
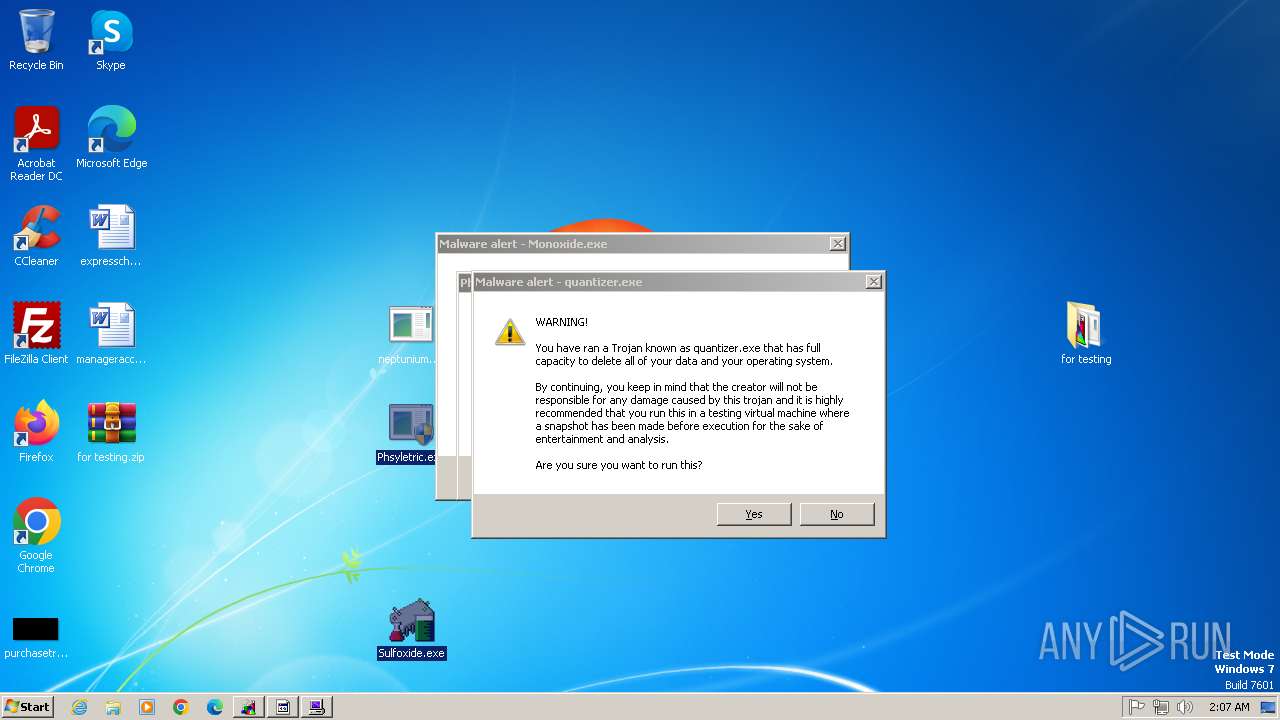
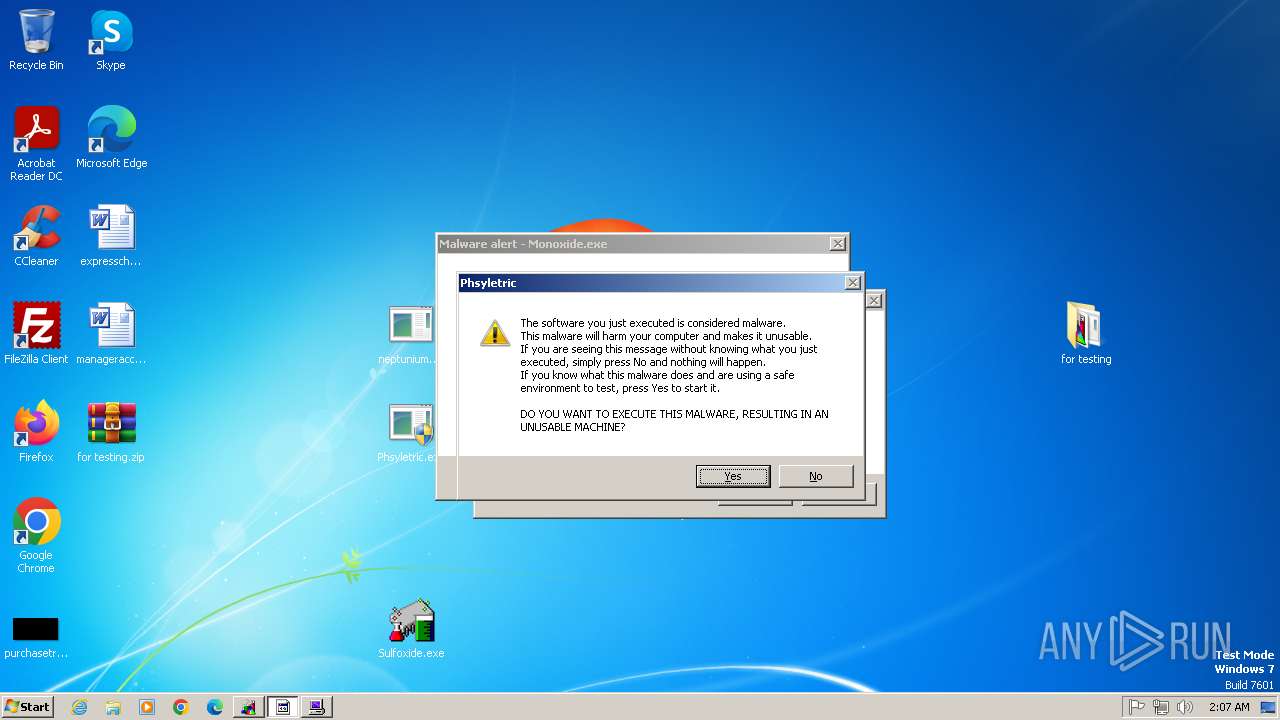
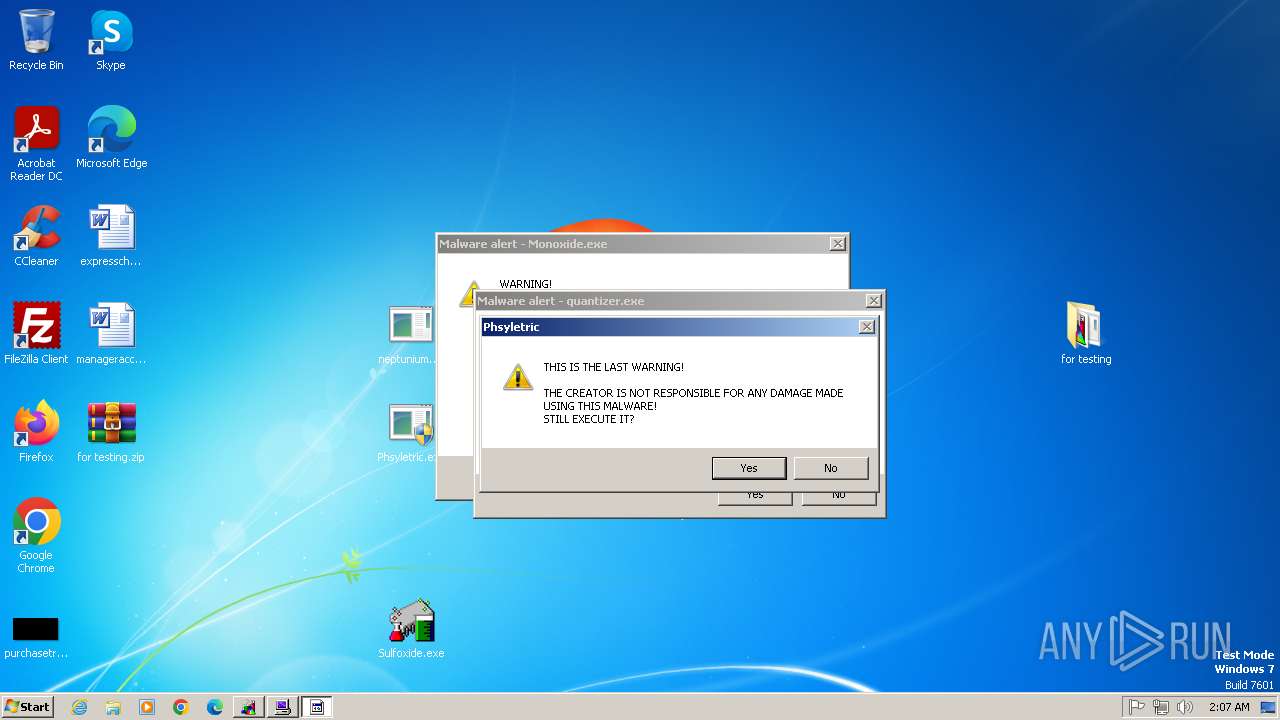
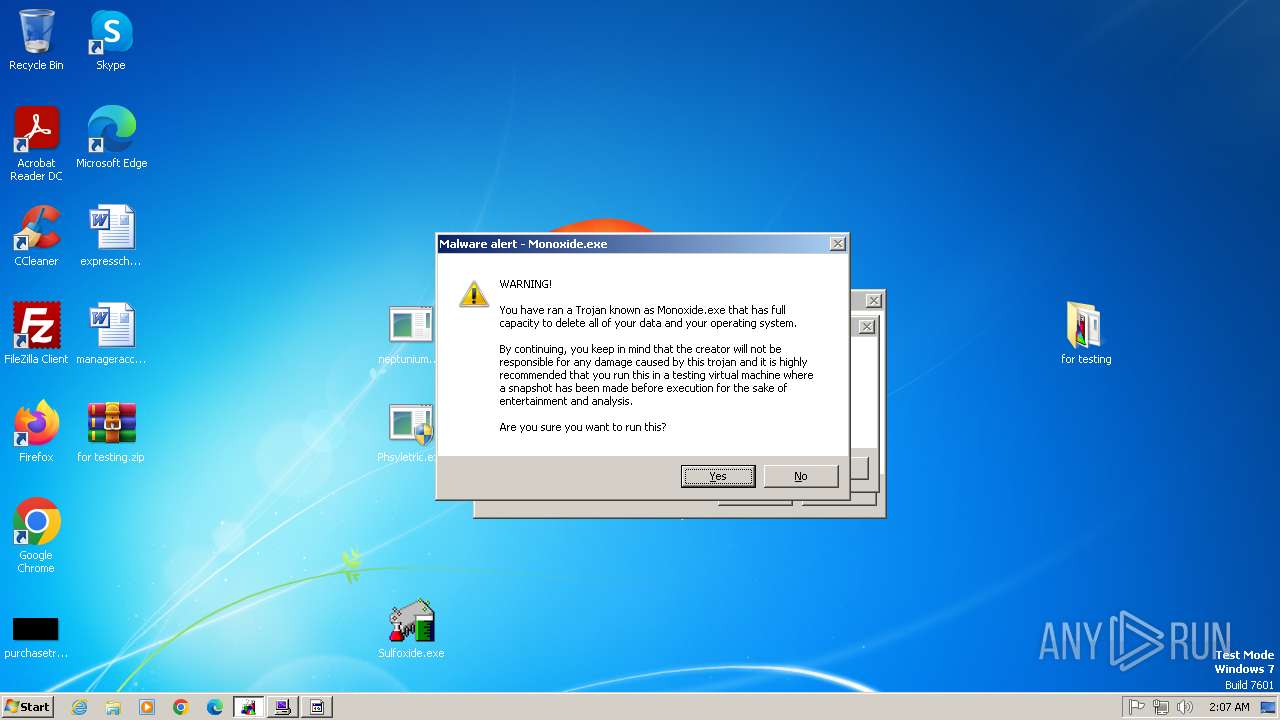
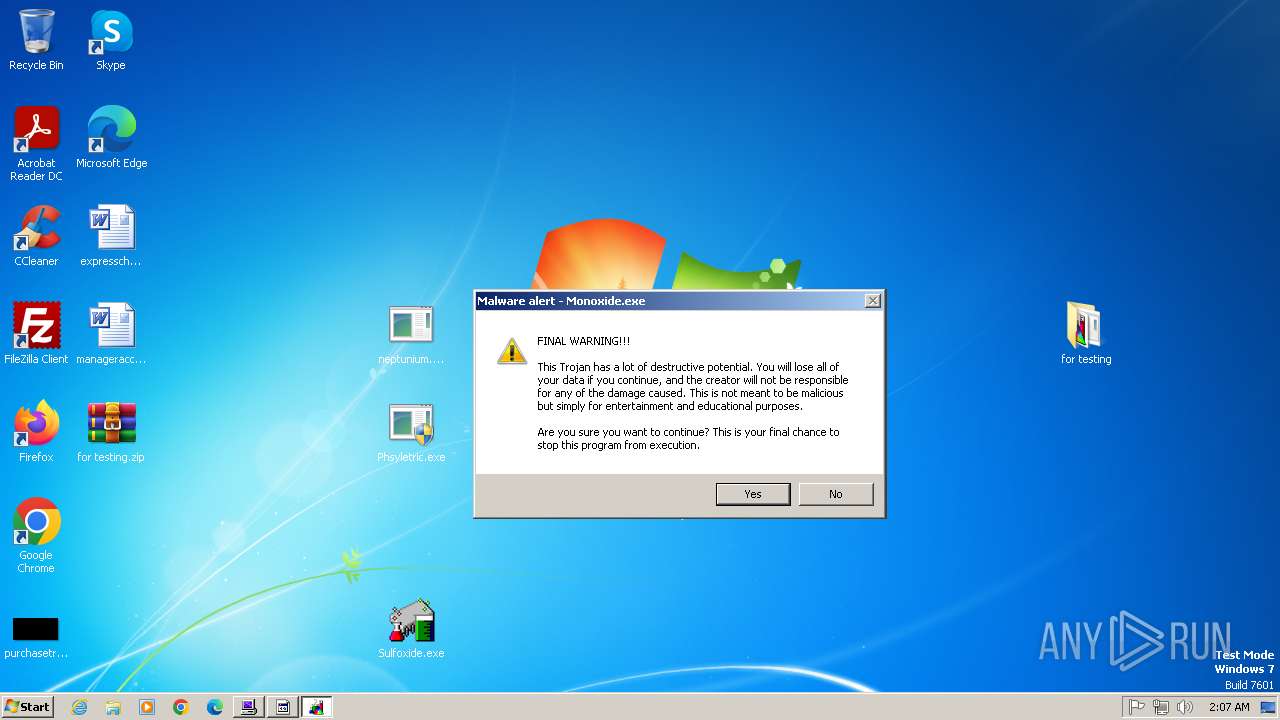
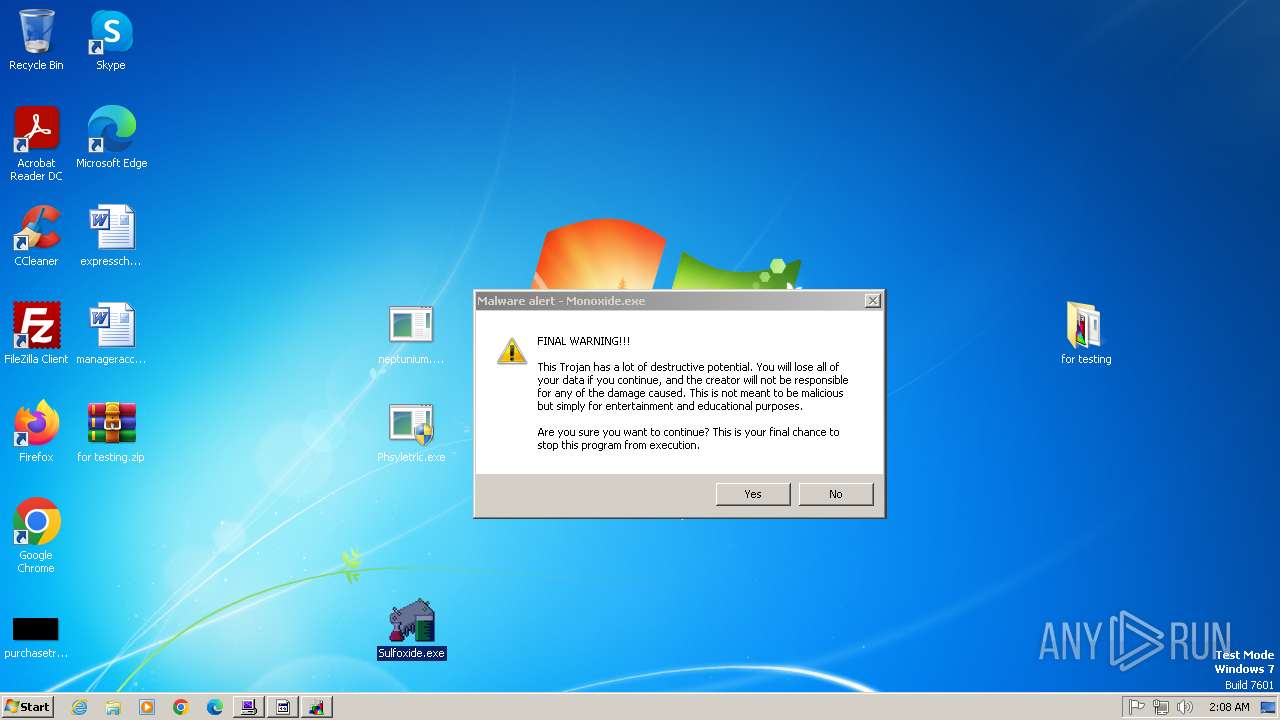
Monoxide mutex has been found
- 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe (PID: 2384)
Disables task manager
- 一一一一一一一一一一一一一一一一.exe (PID: 988)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 2168)
Starts itself from another location
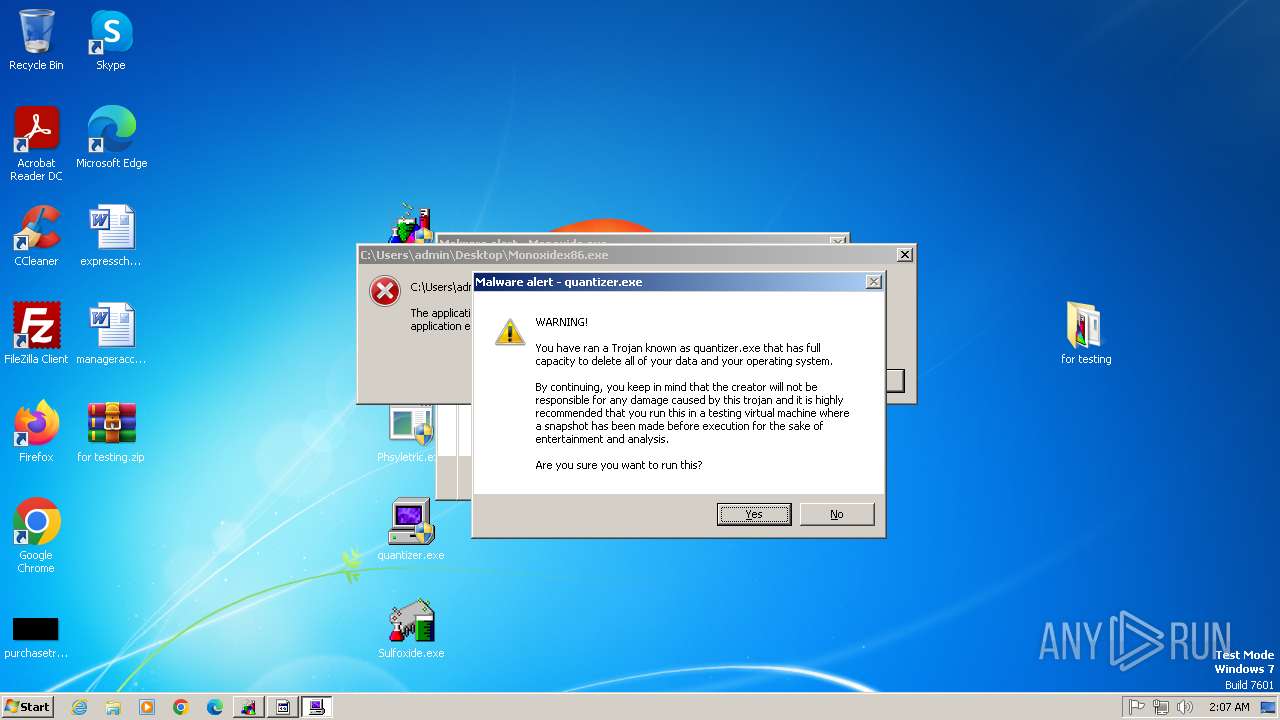
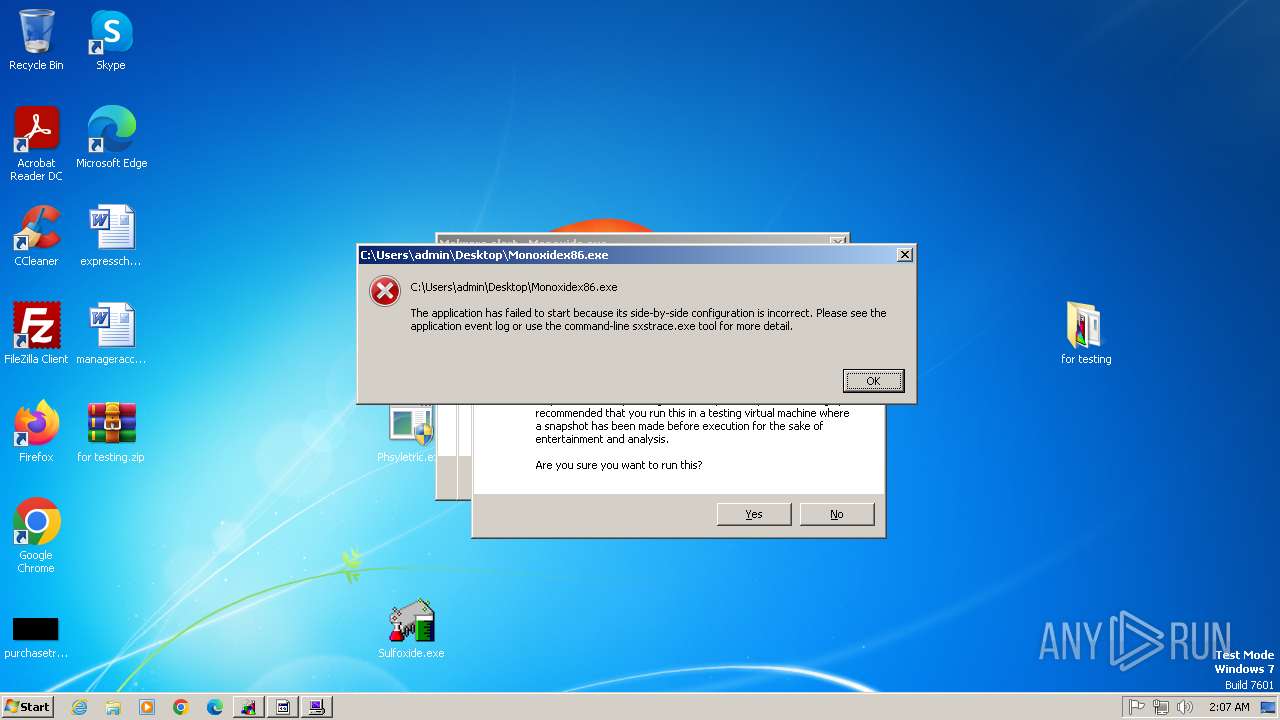
- Monoxidex86.exe (PID: 3876)
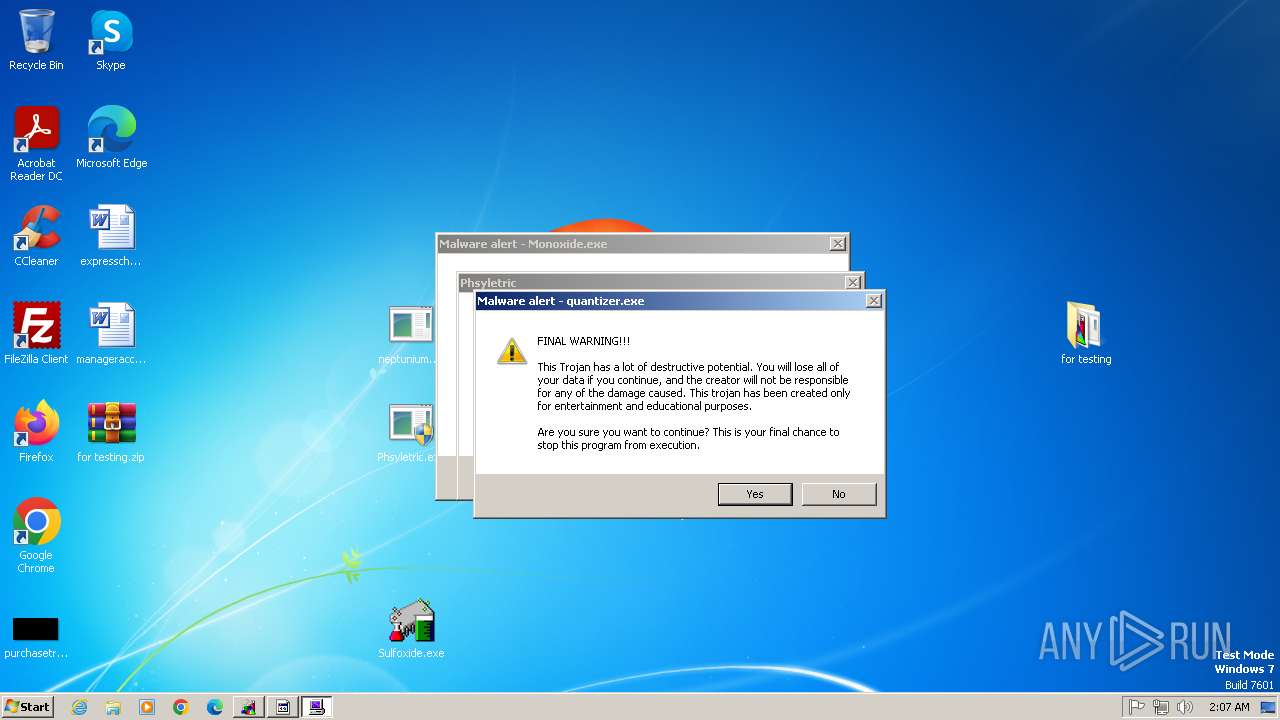
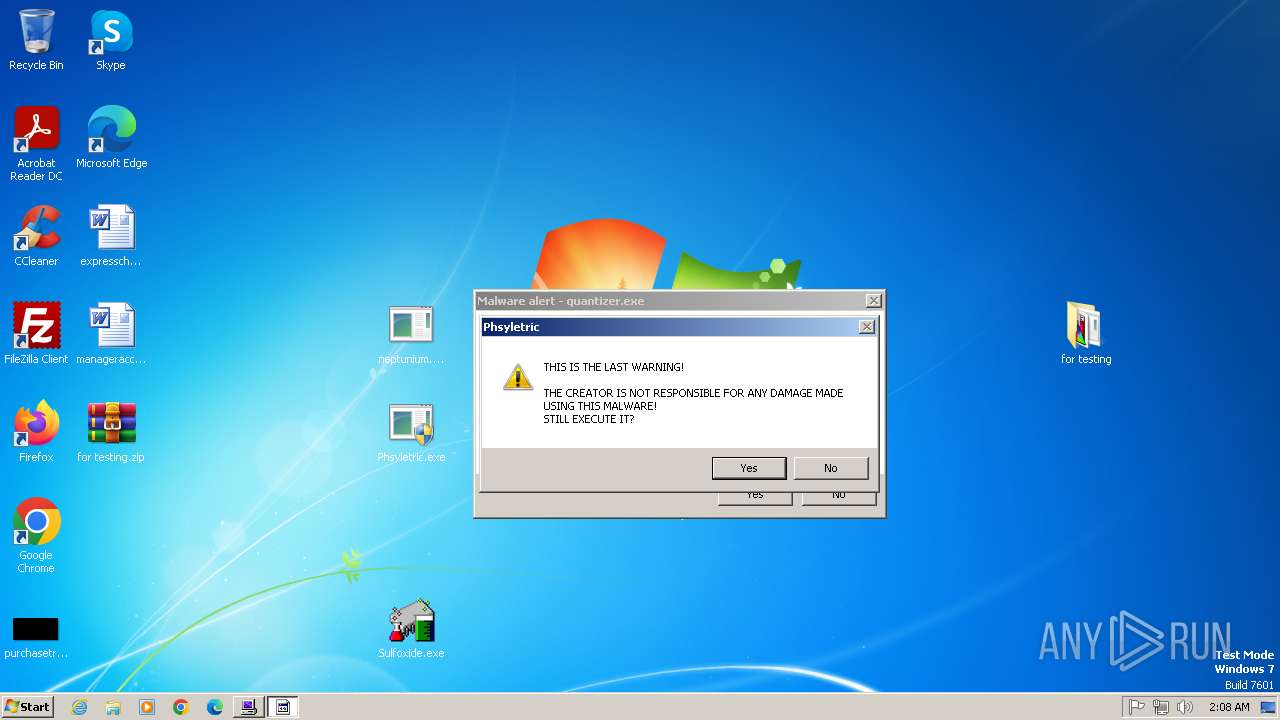
- quantizer.exe (PID: 2432)
Executable content was dropped or overwritten
- Monoxidex86.exe (PID: 3876)
- quantizer.exe (PID: 2432)
There is functionality for taking screenshot (YARA)
- 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe (PID: 2384)
- Phsyletric.exe (PID: 2740)
- 一一一一一一一一一一一一一一一一.exe (PID: 988)
- neptunium.exe (PID: 1560)
Creates file in the systems drive root
- 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe (PID: 2384)
Reads the Internet Settings
- 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe (PID: 2384)
Reads security settings of Internet Explorer
- 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe (PID: 2384)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 2168)
Manual execution by a user
- Monoxidex86.exe (PID: 3876)
- Monoxidex86.exe (PID: 2948)
- Phsyletric.exe (PID: 2532)
- Phsyletric.exe (PID: 2740)
- quantizer.exe (PID: 3160)
- quantizer.exe (PID: 2432)
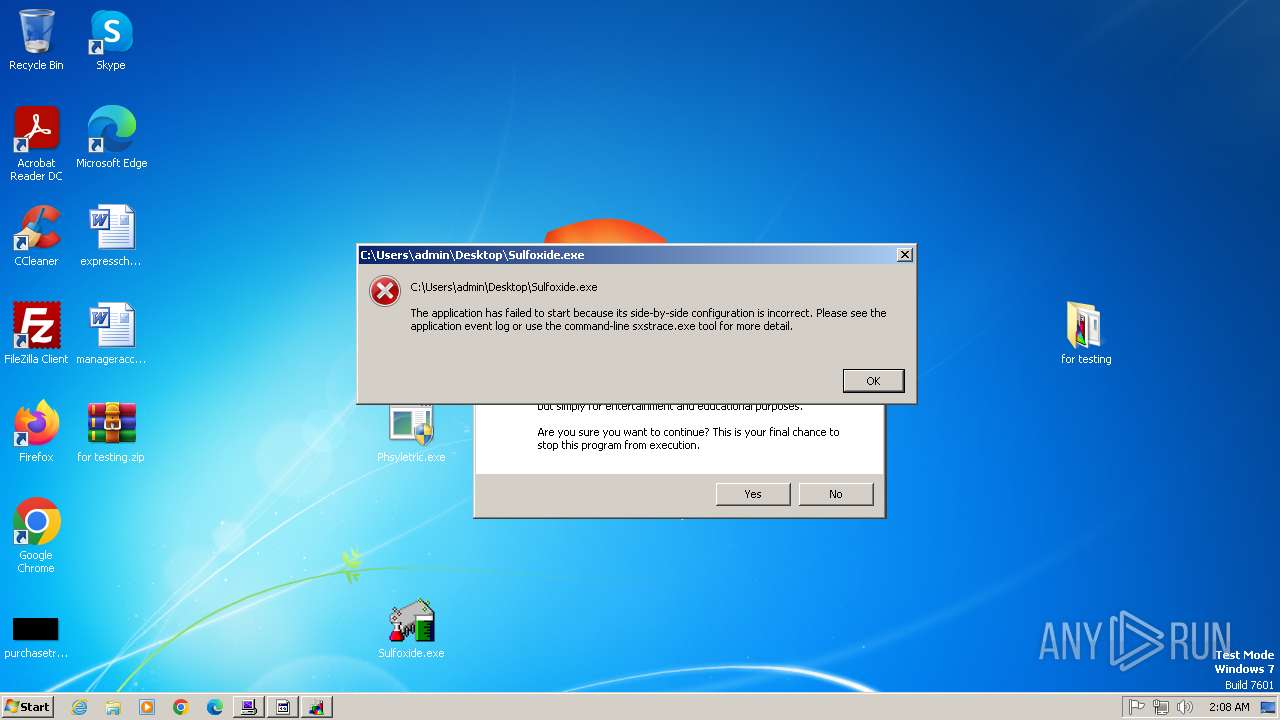
- Sulfoxide.exe (PID: 1028)
- Sulfoxide.exe (PID: 1268)
- neptunium.exe (PID: 1560)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2168)
Checks supported languages
- Monoxidex86.exe (PID: 3876)
- 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe (PID: 2384)
- Phsyletric.exe (PID: 2740)
- quantizer.exe (PID: 2432)
- 一一一一一一一一一一一一一一一一.exe (PID: 988)
- neptunium.exe (PID: 1560)
Create files in a temporary directory
- Monoxidex86.exe (PID: 3876)
- quantizer.exe (PID: 2432)
Reads the computer name
- Phsyletric.exe (PID: 2740)
- 一一一一一一一一一一一一一一一一.exe (PID: 988)
- neptunium.exe (PID: 1560)
- 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe (PID: 2384)
Application launched itself
- msedge.exe (PID: 3036)
- msedge.exe (PID: 1168)
- msedge.exe (PID: 3956)
- msedge.exe (PID: 2996)
- msedge.exe (PID: 2900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 45 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:28 01:03:30 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | for testing/ |
Total processes
70
Monitored processes
29
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 988 | "C:\Users\admin\AppData\Local\Temp\一一一一一一一一一一一一一一一一.exe" | C:\Users\admin\AppData\Local\Temp\一一一一一一一一一一一一一一一一.exe | — | quantizer.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 1020 | "C:\Windows\System32\msiexec.exe" /i "C:\MSOCache\All Users\{90140000-0018-0419-0000-0000000FF1CE}-C\PowerPointMUI.msi" | C:\Windows\System32\msiexec.exe | — | 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\Desktop\Sulfoxide.exe" | C:\Users\admin\Desktop\Sulfoxide.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
| 1168 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument C:\MSOCache\All Users\{90140000-0018-0410-0000-0000000FF1CE}-C\PowerPointMUI.xml | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | 仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1268 | "C:\Users\admin\Desktop\Sulfoxide.exe" | C:\Users\admin\Desktop\Sulfoxide.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3222601730 Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\Desktop\neptunium.exe" | C:\Users\admin\Desktop\neptunium.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2168 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\for testing.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2384 | "C:\Users\admin\AppData\Local\Temp\仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe" | C:\Users\admin\AppData\Local\Temp\仁侲壬輢嘱櫻瞝焲彳賠歏逨垿窀跘仆.exe | — | Monoxidex86.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2432 | "C:\Users\admin\Desktop\quantizer.exe" | C:\Users\admin\Desktop\quantizer.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2532 | "C:\Users\admin\Desktop\Phsyletric.exe" | C:\Users\admin\Desktop\Phsyletric.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
5 555
Read events
5 486
Write events
69
Delete events
0
Modification events
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\for testing.zip | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2168) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
29
Suspicious files
8
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\Phsyletric.exe | executable | |
MD5:4DB23CF50F64A83759DB9DF6AD222D65 | SHA256:465F8BF12FE8FC53C9EF45E498B5F9D95B783C61096147BBC09182F6D19DD129 | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\vcredist_x86.EXE | executable | |
MD5:4F1611F2D0AE799507F60C10FF8654C5 | SHA256:8648C5FC29C44B9112FE52F9A33F80E7FC42D10F3B5B42B2121542A13E44ADFD | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\000.zip | compressed | |
MD5:D113BD83E59586DD8F1843BDB9B98EE0 | SHA256:9D3FE04D88C401178165F7FBDF307AC0FB690CC5FEF8B70EE7F380307D4748F8 | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\quantizer.exe | executable | |
MD5:1458480CF8803569195F934D47AC7481 | SHA256:68D528F9AC891E920449188198A233B71B2860838AF4FB970B9966F941CE82CA | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\MEMZ-Destructive.bat | text | |
MD5:508CCEBEBAEFB2FB833BF8E7FEBFA209 | SHA256:17B1F1E3F6235008152F64BA8B8B4AF4ABBBEB0150DB3EF32EABF04EE3BDC5F4 | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\Sulfoxide.exe | executable | |
MD5:EBB8E4550DA773A639557E3BF7D1B29E | SHA256:84C052915829E69E49D0482F1C0EDDE678B3ECE6AC74CA8D1FE3F0DBE1C05EB0 | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\AutoClickerv3.3.0\System.Text.Encodings.Web.xml | xml | |
MD5:85BE27287D715B2AAC6D2671B66334F0 | SHA256:8E96160DD96E742F859587A710BBCFA2F11813BFE560CA823DA00D3557520D3D | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\AutoClickerv3.3.0\System.ValueTuple.xml | xml | |
MD5:B6E60687AE5DB6D011E21E6993620745 | SHA256:C37E163FA76629C196460C7B4D54E95B1A46A4C66AB7B6F3311959C8137DC5F1 | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\AutoClickerv3.3.0\Serilog.xml | xml | |
MD5:075BF81B4B754A66A1ADCA7C03B38233 | SHA256:FC0B6F200E09C013B143AC2F5DE0D98AF834E09227FB00C684286A4F708C289A | |||
| 2168 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2168.25826\for testing\AutoClickerv3.3.0\System.Numerics.Vectors.xml | xml | |
MD5:95DD29CA17B63843AD787D3BC9C8C933 | SHA256:AE2C3DE9AD57D7091D9F44DCDEE3F88ECCF2BA7CB43ADC9BB24769154A532DC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |