| File name: | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d |
| Full analysis: | https://app.any.run/tasks/e0166d5e-dc05-4ba0-8726-fd0d14946063 |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2019, 07:55:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 002021C8494300F8C5200C4380BA4681 |
| SHA1: | BE44DD7AB3F679258D0C54C7310B55530199BA23 |
| SHA256: | 13E87D264BF8CC399354F95710F1C2541886C6661982AC8D1B243153A176B63D |
| SSDEEP: | 6144:3gtJZ0DY5YELjw5obiE6MOnFxJj1kQ2iNu/C4k283LY9mAtj2TS6msDD7ZApM7RJ:3gWDY5rjBbiNMONj1kO8q4kL389pauZI |
MALICIOUS
Application was dropped or rewritten from another process
- pev.rkexe (PID: 3604)
- pev.rkexe (PID: 3508)
- pev.rkexe (PID: 3972)
- pev.rkexe (PID: 2480)
- pev.rkexe (PID: 2916)
- pev.rkexe (PID: 3392)
- nircmdc.rkexe (PID: 4076)
- nircmdc.rkexe (PID: 2516)
- nircmdc.rkexe (PID: 2904)
- nircmdc.rkexe (PID: 3368)
- nircmdc.rkexe (PID: 3820)
- nircmdc.rkexe (PID: 2264)
- nircmdc.rkexe (PID: 2076)
- nircmdc.rkexe (PID: 3064)
- pev.rkexe (PID: 3900)
- pev.rkexe (PID: 2380)
- pev.rkexe (PID: 2480)
- pev.rkexe (PID: 3372)
- pev.rkexe (PID: 2332)
- pev.rkexe (PID: 3876)
- sed.rkexe (PID: 2724)
- pev.rkexe (PID: 3760)
- pev.rkexe (PID: 3276)
- pev.rkexe (PID: 2816)
- pev.rkexe (PID: 2248)
- pev.rkexe (PID: 2716)
- pev.rkexe (PID: 3176)
- pev.rkexe (PID: 3696)
- pev.rkexe (PID: 3764)
- pev.rkexe (PID: 2240)
- sed.rkexe (PID: 3328)
- pev.rkexe (PID: 3904)
SUSPICIOUS
Executable content was dropped or overwritten
- 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe (PID: 2300)
Starts application with an unusual extension
- cmd.exe (PID: 3188)
Starts CMD.EXE for commands execution
- 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe (PID: 2300)
Modifies the open verb of a shell class
- pev.rkexe (PID: 2240)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2009:02:07 07:33:02+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 364544 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 98304 |
| EntryPoint: | 0x70760 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 07-Feb-2009 06:33:02 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 07-Feb-2009 06:33:02 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00018000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00019000 | 0x00059000 | 0x00058400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99882 |
.rsrc | 0x00072000 | 0x00001000 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.93418 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.09999 | 668 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
B | 7.92904 | 3109 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
F | 0 | 398216 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
I | 6.48289 | 119 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
N | 3.16993 | 9 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
O | 2.58496 | 6 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
COMCTL32.dll |
GDI32.dll |
KERNEL32.DLL |
MSVCRT.dll |
OLE32.dll |
SHELL32.dll |
USER32.dll |
Total processes
75
Monitored processes
37
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2076 | nircmdc.rkexe win close stitle "Security Central" | C:\Users\admin\AppData\Local\Temp\9F90.tmp\nircmdc.rkexe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: NirCmd Exit code: 4206720 Version: 2.37 Modules
| |||||||||||||||
| 2240 | PEV.rkexe RIMPORT rkill.reg | C:\Users\admin\AppData\Local\Temp\9F90.tmp\pev.rkexe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2248 | PEV.rkexe -k "C:\Users\admin\AppData\Local\Temp\*.exe" | C:\Users\admin\AppData\Local\Temp\9F90.tmp\pev.rkexe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 2264 | nircmdc.rkexe win close stitle "Enterprise Suite" | C:\Users\admin\AppData\Local\Temp\9F90.tmp\nircmdc.rkexe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: NirCmd Exit code: 4206720 Version: 2.37 Modules
| |||||||||||||||
| 2300 | "C:\Users\admin\AppData\Local\Temp\13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe" | C:\Users\admin\AppData\Local\Temp\13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2332 | PEV.rkexe -k *sftav.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\pev.rkexe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 2380 | PEV.rkexe -k "C:\Users\admin\*" | C:\Users\admin\AppData\Local\Temp\9F90.tmp\pev.rkexe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2480 | PEV.rkexe -k winlogon32.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\pev.rkexe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 2480 | PEV.rkexe -k antispyshield.exe f | C:\Users\admin\AppData\Local\Temp\9F90.tmp\pev.rkexe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 4 Modules
| |||||||||||||||
| 2516 | nircmdc.rkexe win close stitle "Smart Security" | C:\Users\admin\AppData\Local\Temp\9F90.tmp\nircmdc.rkexe | — | cmd.exe | |||||||||||
User: admin Company: NirSoft Integrity Level: HIGH Description: NirCmd Exit code: 4206720 Version: 2.37 Modules
| |||||||||||||||
Total events
53
Read events
46
Write events
6
Delete events
1
Modification events
| (PID) Process: | (2240) pev.rkexe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\.exe |
| Operation: | write | Name: | |
Value: exefile | |||
| (PID) Process: | (2240) pev.rkexe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\exefile\shell\open\command |
| Operation: | write | Name: | |
Value: "%1" %* | |||
| (PID) Process: | (2240) pev.rkexe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced |
| Operation: | delete value | Name: | HideIcons |
Value: 0 | |||
| (PID) Process: | (4020) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosX |
Value: 132 | |||
| (PID) Process: | (4020) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosY |
Value: 132 | |||
| (PID) Process: | (4020) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDX |
Value: 960 | |||
| (PID) Process: | (4020) NOTEPAD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Notepad |
| Operation: | write | Name: | iWindowPosDY |
Value: 501 | |||
Executable files
4
Suspicious files
0
Text files
23
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2300 | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\nircmd.rkexe | executable | |
MD5:AC6094297CD882B8626466CDEB64F19F | SHA256:27C7FFD8367AAA73155FBB287A7DF1F157F2D0C3323DBB176D02B36FF616FCA5 | |||
| 2300 | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\nircmdc.rkexe | executable | |
MD5:9CB3A38088807F54E7F89AC30E09C030 | SHA256:71579B7BB651004F9C2E3F8D62511F610443C7E8225001865415A4620BD04219 | |||
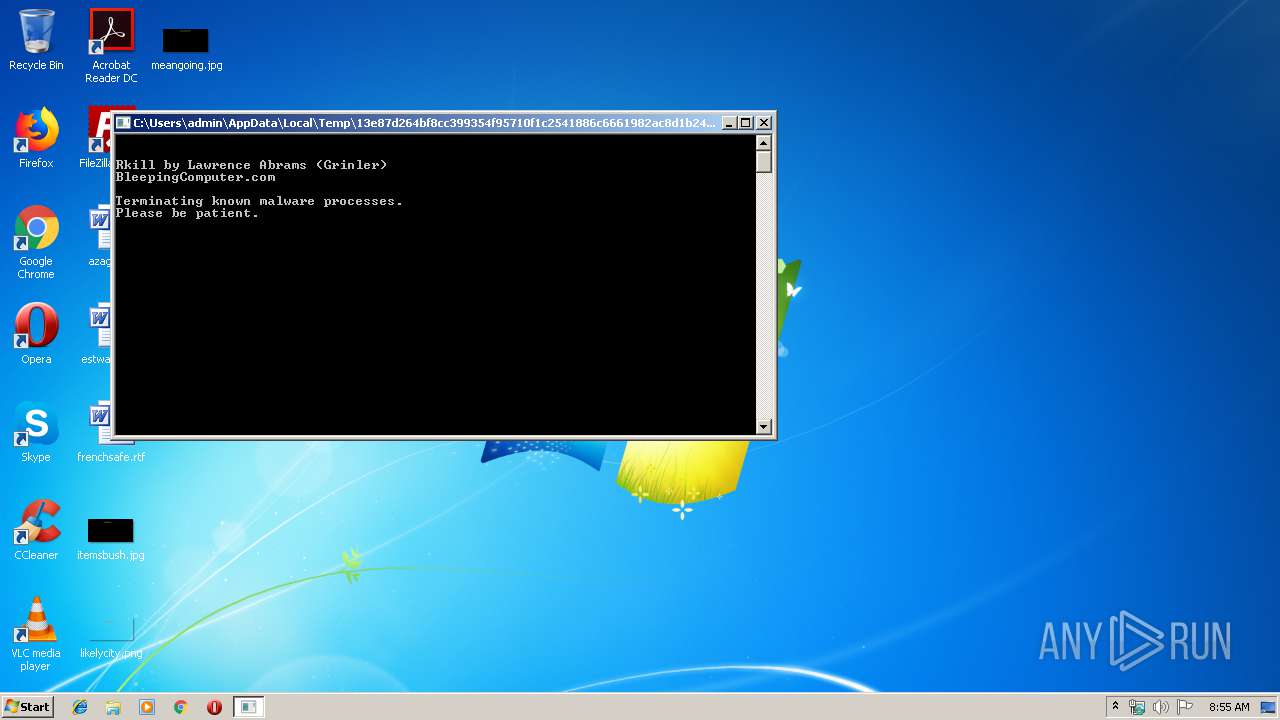
| 2300 | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\rkill.bat | text | |
MD5:BFA7B70D250AD5820D22F9A98525F06D | SHA256:7F3F17F0DDE827F339555D8558C8EF5848DF127290421DC0846CC0EC15311488 | |||
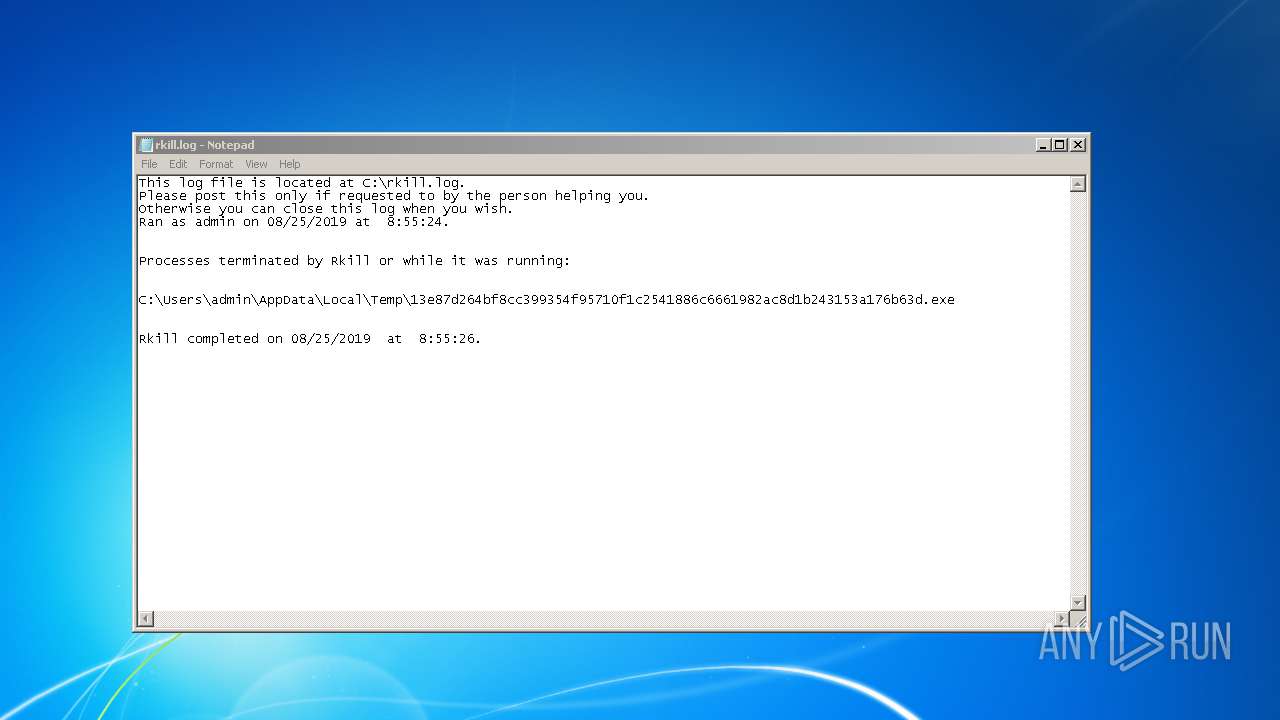
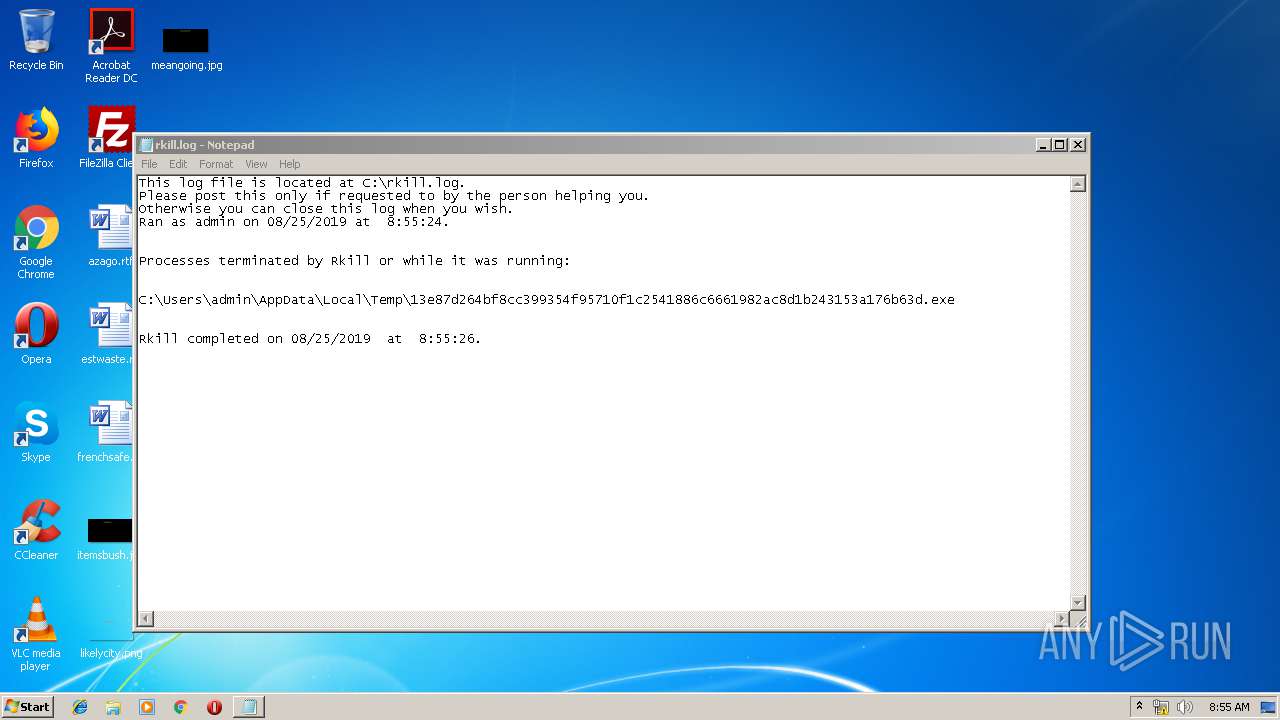
| 3188 | cmd.exe | C:\rkill.log | text | |
MD5:— | SHA256:— | |||
| 2300 | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\pev.rkexe | executable | |
MD5:3B44E6B3653FABDF876BC2B13C434E62 | SHA256:21793F8B54906EBD1DADA5BC350BAE8399E49409C889BF6DC6294ACB13BAF797 | |||
| 2300 | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\rkill.reg | text | |
MD5:9E0A0CE4ED43E9331D89174EC3D47FBD | SHA256:F75AC8FE4EFB702E945B39DE69CA137D01D6C8E4CFF8F5B038973D529402912E | |||
| 3188 | cmd.exe | C:\Users\admin\AppData\Local\Temp\rkill.log | text | |
MD5:BC949EA893A9384070C31F083CCEFD26 | SHA256:6BDF66B5BF2A44E658BEA2EE86695AB150A06E600BF67CD5CCE245AD54962C61 | |||
| 2300 | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\nircmd.chm | chi | |
MD5:BE5BF3E4122629A7F880C225F4EDEBFF | SHA256:75180851550EF13F7204CA182CC87EBE3AF50E73D3C08E66D2569ABB119F28AA | |||
| 2300 | 13e87d264bf8cc399354f95710f1c2541886c6661982ac8d1b243153a176b63d.exe | C:\Users\admin\AppData\Local\Temp\9F90.tmp\sed.rkexe | executable | |
MD5:3A34D017AA4E5C11F2A329AB04DA17F4 | SHA256:21A9D5EEE6CA1B6D3AA1FC64B3B53D0846EDF8A698AD7924D1321857F708001F | |||
| 3188 | cmd.exe | C:\Users\admin\AppData\Local\Temp\rks1.log | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report