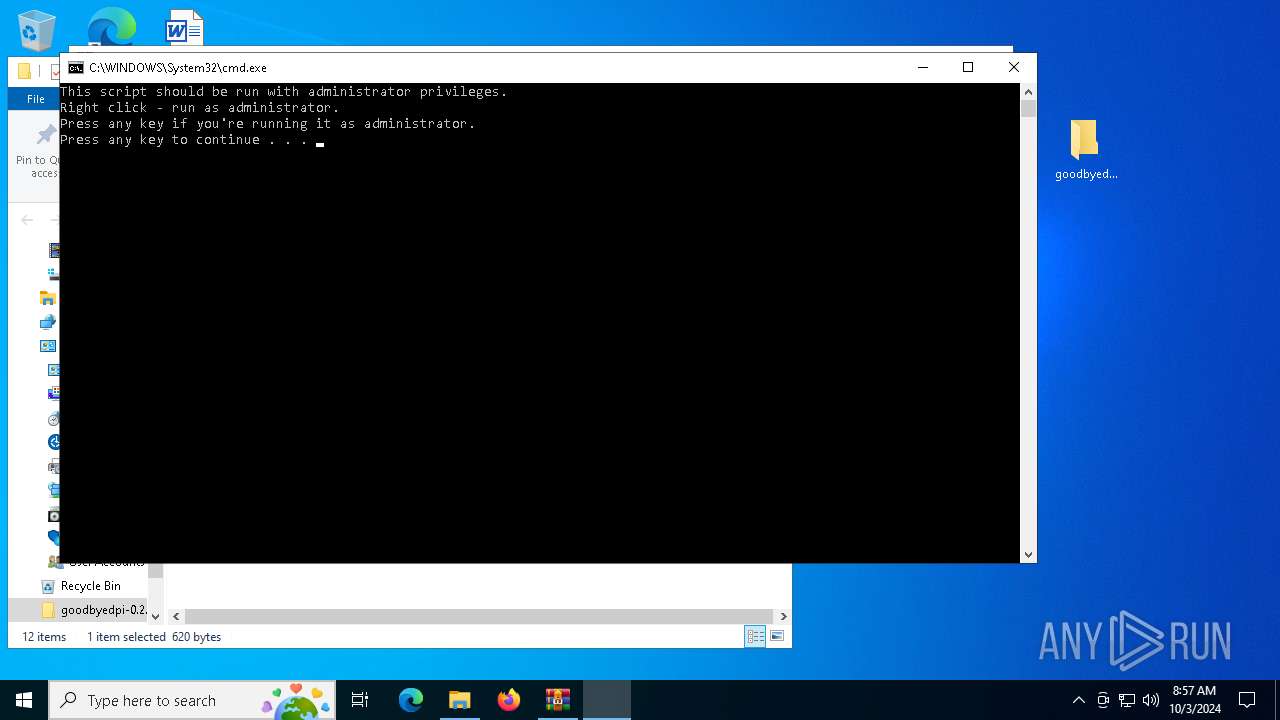
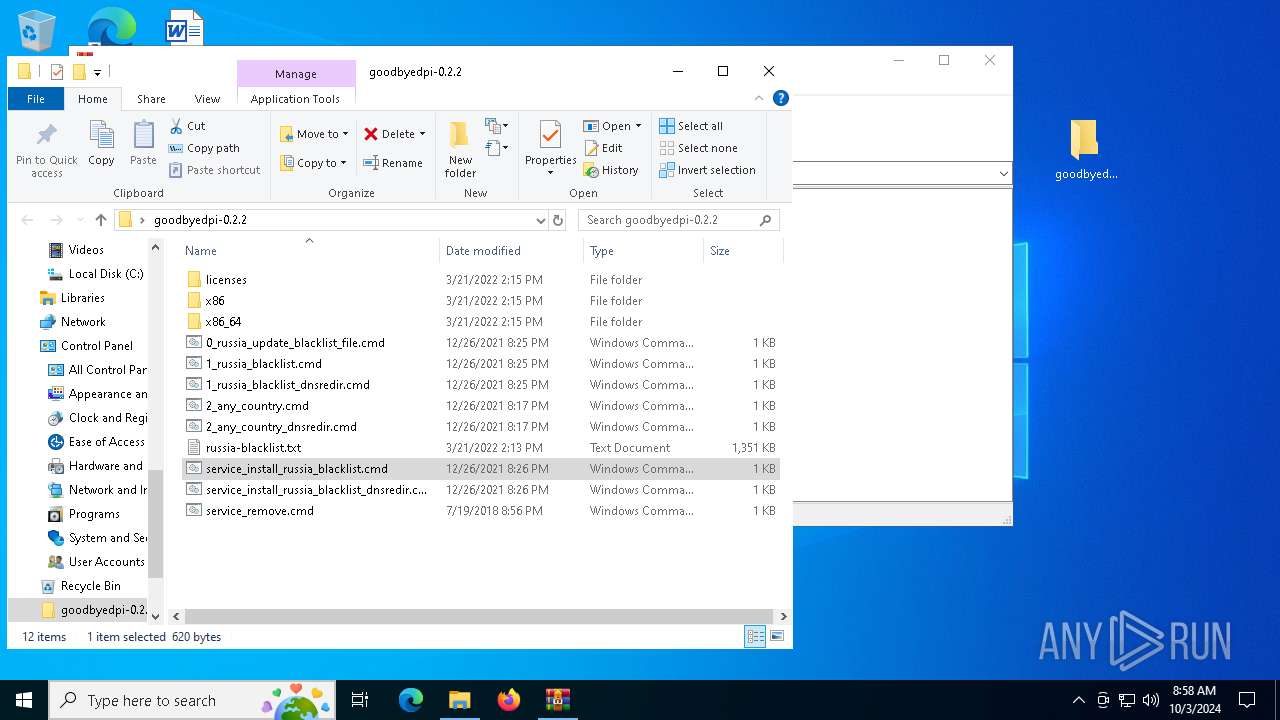
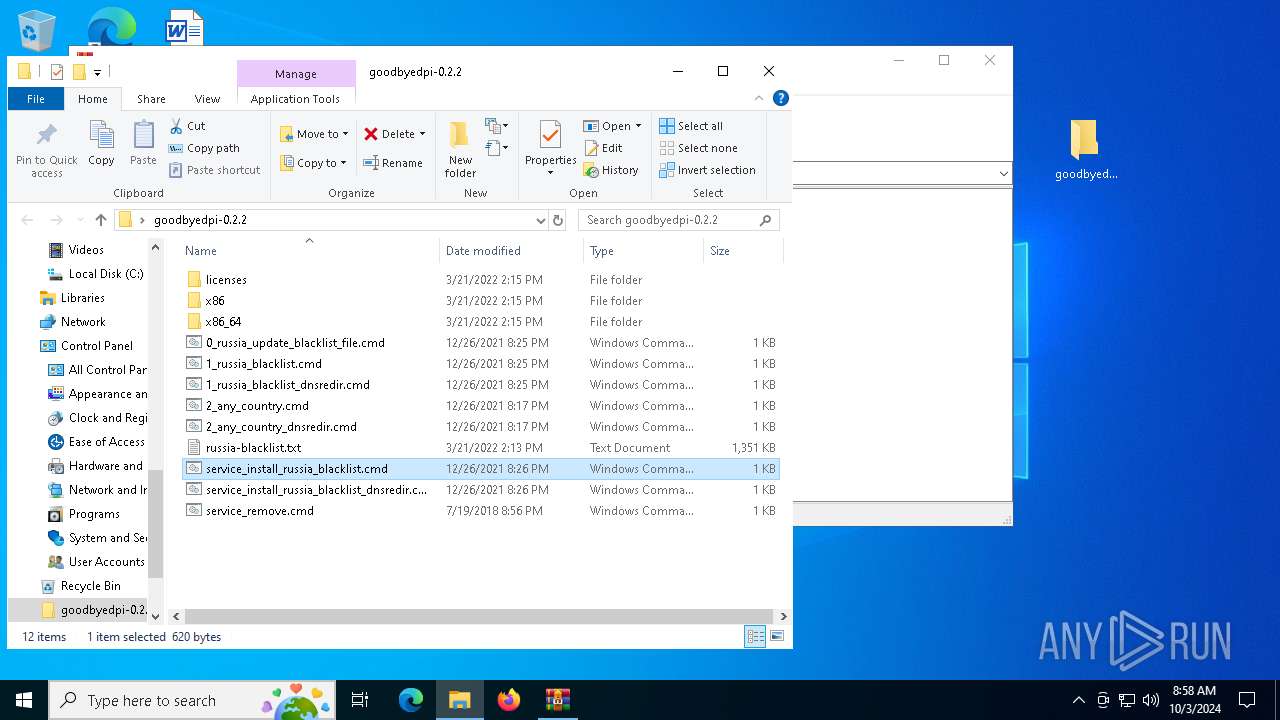
| download: | /ValdikSS-Win/GoodbyeDPI/releases/download/0.2.2/goodbyedpi-0.2.2.zip |
| Full analysis: | https://app.any.run/tasks/fdf18559-a93c-4908-8484-f164d759f4a6 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | October 03, 2024, 08:57:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 4FCB1C69B8B3FCCB2BA5A319DB5D8BFB |
| SHA1: | 7697B6682CE08C53D646CABD1D189DF1AA7C579E |
| SHA256: | 13CFF4CFD7A8723B40BD63CC05064472233EE32B29C9ACBB002C63DDAB65CF45 |
| SSDEEP: | 98304:eEgOjVGmpe/j4IWngWbiIqpN9/a/jZEJ+97XvLbYT9fNaCaM2vIbmCpyIjx2RPXx:O0SUkSUW |
MALICIOUS
DCRAT has been detected (YARA)
- WmiPrvSE.exe (PID: 3588)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 2536)
Starts SC.EXE for service management
- cmd.exe (PID: 2424)
- cmd.exe (PID: 2540)
Executes as Windows Service
- goodbyedpi.exe (PID: 5476)
Executable content was dropped or overwritten
- goodbyedpi.exe (PID: 5476)
- RegAsm.exe (PID: 5408)
- cq8CFbO6mf.exe (PID: 2648)
- WmiPrvSE.exe (PID: 3588)
Process drops legitimate windows executable
- RegAsm.exe (PID: 5408)
Executing commands from a ".bat" file
- cq8CFbO6mf.exe (PID: 2648)
Starts CMD.EXE for commands execution
- cq8CFbO6mf.exe (PID: 2648)
Starts application with an unusual extension
- cmd.exe (PID: 696)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 696)
INFO
Manual execution by a user
- cmd.exe (PID: 2424)
- cmd.exe (PID: 2540)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2536)
Changes the display of characters in the console
- cmd.exe (PID: 696)
Found Base64 encoded reference to WMI classes (YARA)
- WmiPrvSE.exe (PID: 3588)
Found Base64 encoded reference to AntiVirus WMI classes (YARA)
- WmiPrvSE.exe (PID: 3588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:12:26 20:25:00 |
| ZipCRC: | 0xbdb5c2e8 |
| ZipCompressedSize: | 125 |
| ZipUncompressedSize: | 139 |
| ZipFileName: | goodbyedpi-0.2.2/0_russia_update_blacklist_file.cmd |
Total processes
164
Monitored processes
31
Malicious processes
4
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | sc description "GoodbyeDPI" "Passive Deep Packet Inspection blocker and Active DPI circumvention utility" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Windows\Temp\JT5on9nNlg.bat" | C:\Windows\System32\cmd.exe | — | cq8CFbO6mf.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 4WAQaXlnG1.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2028 | sc description "GoodbyeDPI" "Passive Deep Packet Inspection blocker and Active DPI circumvention utility" | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | YAyQccMdIx.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
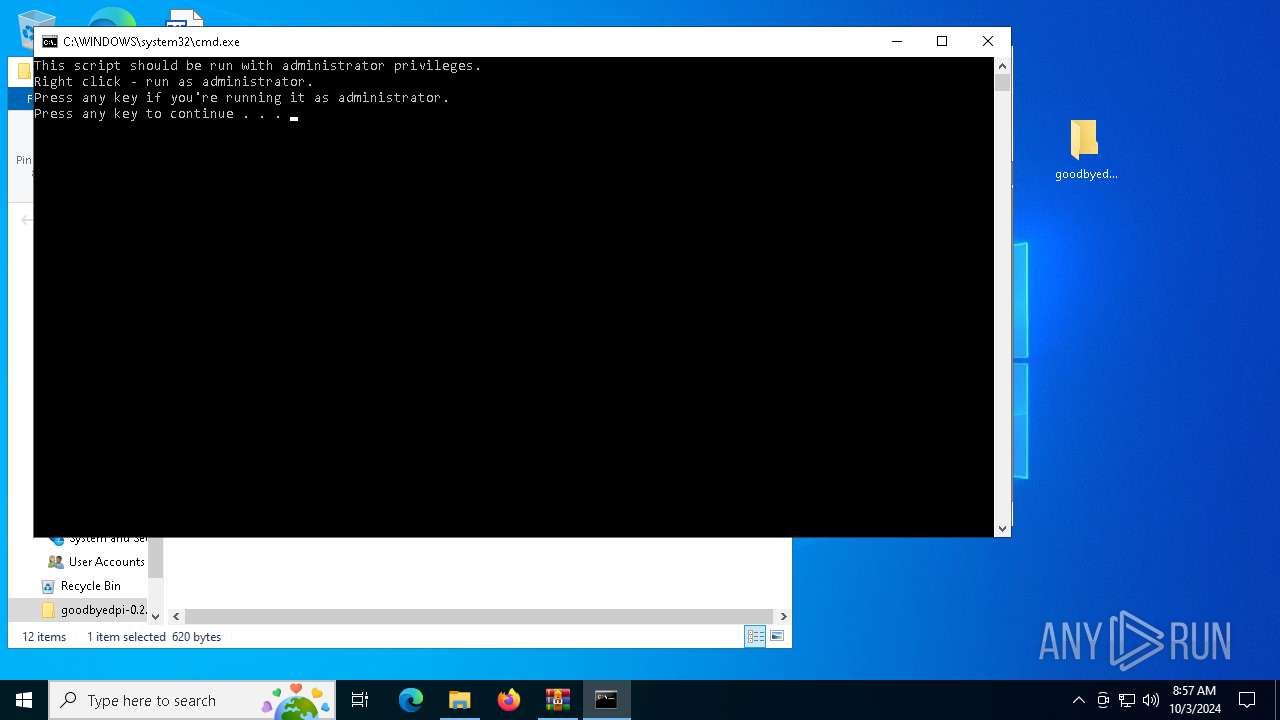
| 2424 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\goodbyedpi-0.2.2\service_install_russia_blacklist.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2536 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\goodbyedpi-0.2.2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2540 | "C:\WINDOWS\System32\cmd.exe" /C "C:\Users\admin\Desktop\goodbyedpi-0.2.2\service_install_russia_blacklist.cmd" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2648 | "C:\WINDOWS\system32\config\systemprofile\AppData\Roaming\cq8CFbO6mf.exe" | C:\Windows\SysWOW64\config\systemprofile\AppData\Roaming\cq8CFbO6mf.exe | RegAsm.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 16.10.31418.88 Modules
| |||||||||||||||
Total events
2 966
Read events
2 957
Write events
9
Delete events
0
Modification events
| (PID) Process: | (2536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (2536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\goodbyedpi-0.2.2.zip | |||
| (PID) Process: | (2536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2648) cq8CFbO6mf.exe | Key: | HKEY_USERS\.DEFAULT\Software\30876fffde222541d9482b3d38680f15cc8ea6b5 |
| Operation: | write | Name: | 063df4e422b5ac503adba3bd582354711fc63619 |
Value: H4sIAAAAAAAEAHWQT0sDQQzFv0rpSUGWRWQp3nRrYUHd0j3MwXiY7mS6Q2cma2b679sbFaEoPYU88t4vydu0vgdYMm1Yh8nCeUzS0gG5G9B7gK5nN2YRm5iy9h7Nj9JES6JaitnwfqCUCzzi9OZ/3uTqOKuuAWoKgeIv48HQGqWsXgD6xCmd2ZWLhg4yVHc1wP62KIsKIOqAadS9uFRwS953T5eQ4qw96ogM8KzjBmC1i9kFfGTaIp/ZLO2iKcqyBDCOpZZFP2yl8f7PTap5nbeqk4+ckmpVdSd7U7ROwtMpZQwjkxW43DSOc521QEkH90XvP2b1Yt1WwX4Hvn8CIXoFKnYBAAA= | |||
| (PID) Process: | (2648) cq8CFbO6mf.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {289AF617-1CC3-42A6-926C-E6A863F0E3BA} {ADD8BA80-002B-11D0-8F0F-00C04FD7D062} 0xFFFF |
Value: 01000000000000008ECB835D7215DB01 | |||
| (PID) Process: | (2648) cq8CFbO6mf.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {35786D3C-B075-49B9-88DD-029876E11C01} {ADD8BA80-002B-11D0-8F0F-00C04FD7D062} 0xFFFF |
Value: 01000000000000008ECB835D7215DB01 | |||
Executable files
22
Suspicious files
0
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
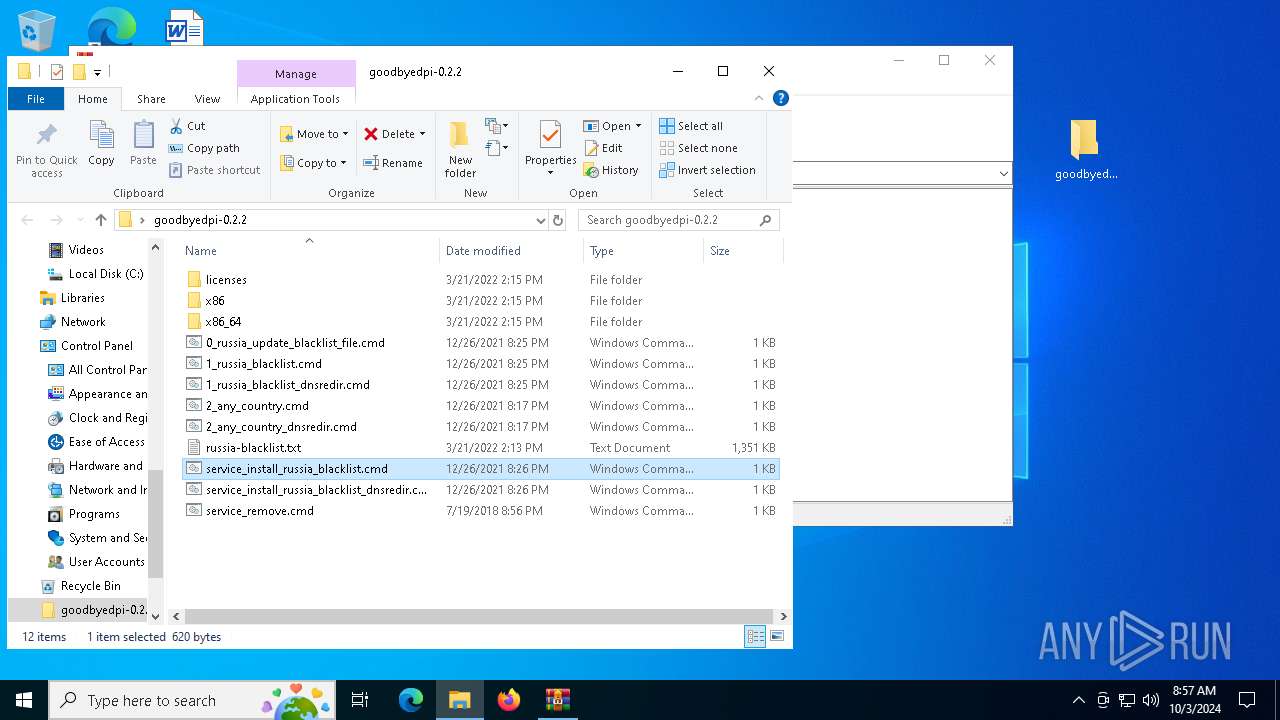
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\2_any_country_dnsredir.cmd | text | |
MD5:48DE91946FD423515B182A622842ADC5 | SHA256:A7762F252E434134245ADEE7398EABC7B96E4E83EE408CE63CC3F92B942C4B6B | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\russia-blacklist.txt | text | |
MD5:8F2D338776B38F15D72CFFFC9CC680E0 | SHA256:9A495E9CB16A4EB9585D3B8BDF22885E6156E9FD9094D0DBD05ADE3390C6A2EE | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\0_russia_update_blacklist_file.cmd | text | |
MD5:0D689231A9C73BDD03F25E8EC57A3DAB | SHA256:B9C8D691B2C1140455BE35B15873944896B46C29F12ED0332274432A1C45A021 | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\licenses\LICENSE-windivert.txt | text | |
MD5:B864FBB188A7C3A11CEF80F3EE902D77 | SHA256:E5453B2E71E4C4DCDB89A2539655ADD3A63202521CF3012B768E8BFEDA199312 | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\1_russia_blacklist_dnsredir.cmd | text | |
MD5:F73C24AA2A64A897D88FEE8787A48847 | SHA256:CEBFFBB31125A1AC8ABD68012BB413BAC6DA56258F0D4FA95DCB2F23E94B4779 | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\licenses\LICENSE-getline.txt | text | |
MD5:3A7EDEBC3612BCEA2306F73B92342A44 | SHA256:EC5F8E03FCCB3842CC62AD79EA5F6F6058988E2721A3E6566E8FB72786D485C4 | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\licenses\LICENSE-uthash.txt | text | |
MD5:5CC1F1E4C71F19F580458586756C02B4 | SHA256:D3C6556E48104C31E3E0C62238C749C2A09CA79EE87DA50B9CD29C6C9027D57D | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\1_russia_blacklist.cmd | text | |
MD5:10812F31EF70EDC954EAF63650336212 | SHA256:E155B6EADD37942F9BFC8D6D00ACA4F518A056FC81AC8666A6532BA90F77FD93 | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\2_any_country.cmd | text | |
MD5:2E479250A2D20C6D2D5FC5171528694B | SHA256:8F432FB6710D0D2D36D89AB4125157766722928AFE2E70077CD921F27579AD5A | |||
| 2536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2536.16493\goodbyedpi-0.2.2\x86_64\goodbyedpi.exe | executable | |
MD5:7A36F8EB2623A99F26ED3DA5ECBC2821 | SHA256:8EA02A5ABD596F2E2851881A0C92BA3440B6E5E9788A04B965742E87AFC65365 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
44
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6220 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6056 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3256 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3256 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5196 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5196 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6056 | svchost.exe | 20.190.159.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |