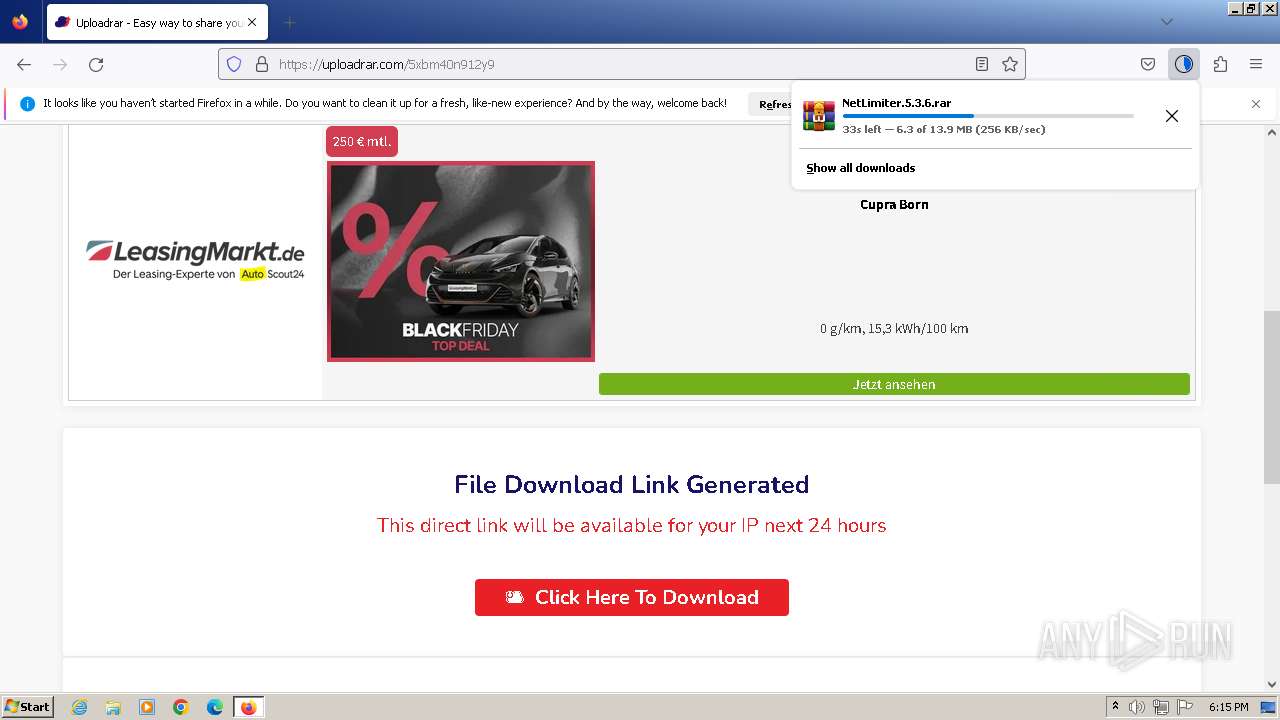
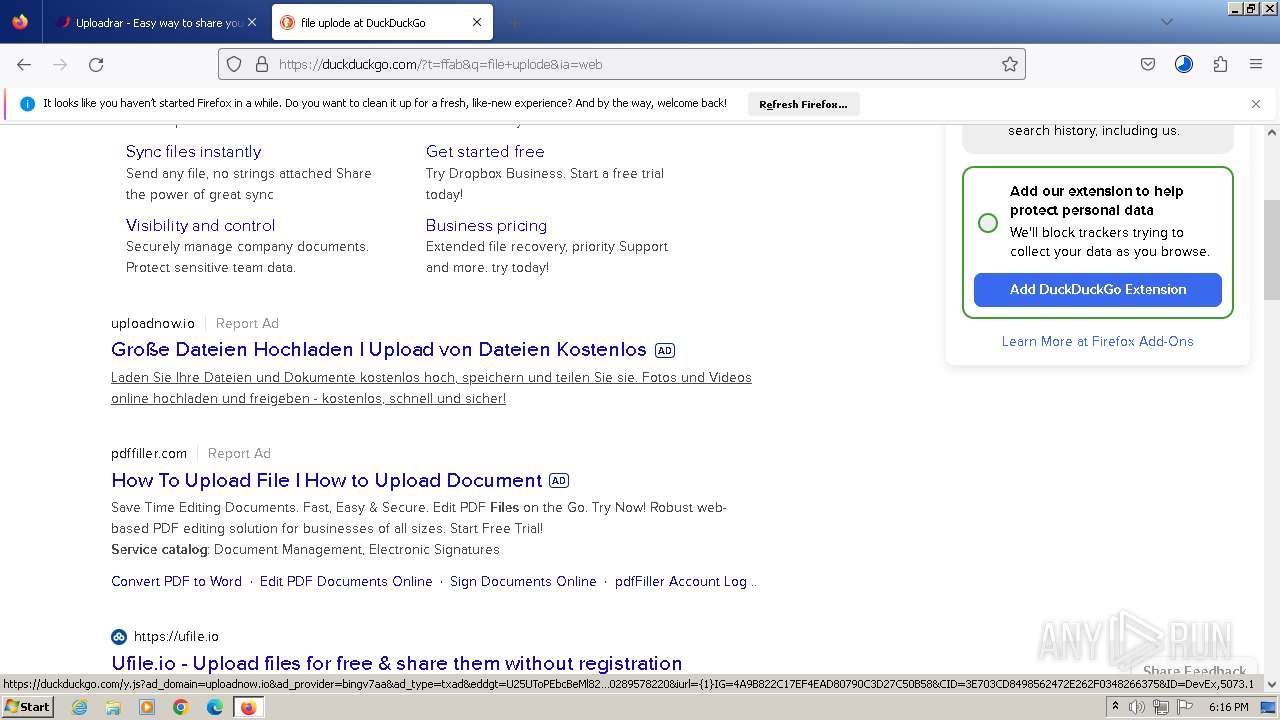
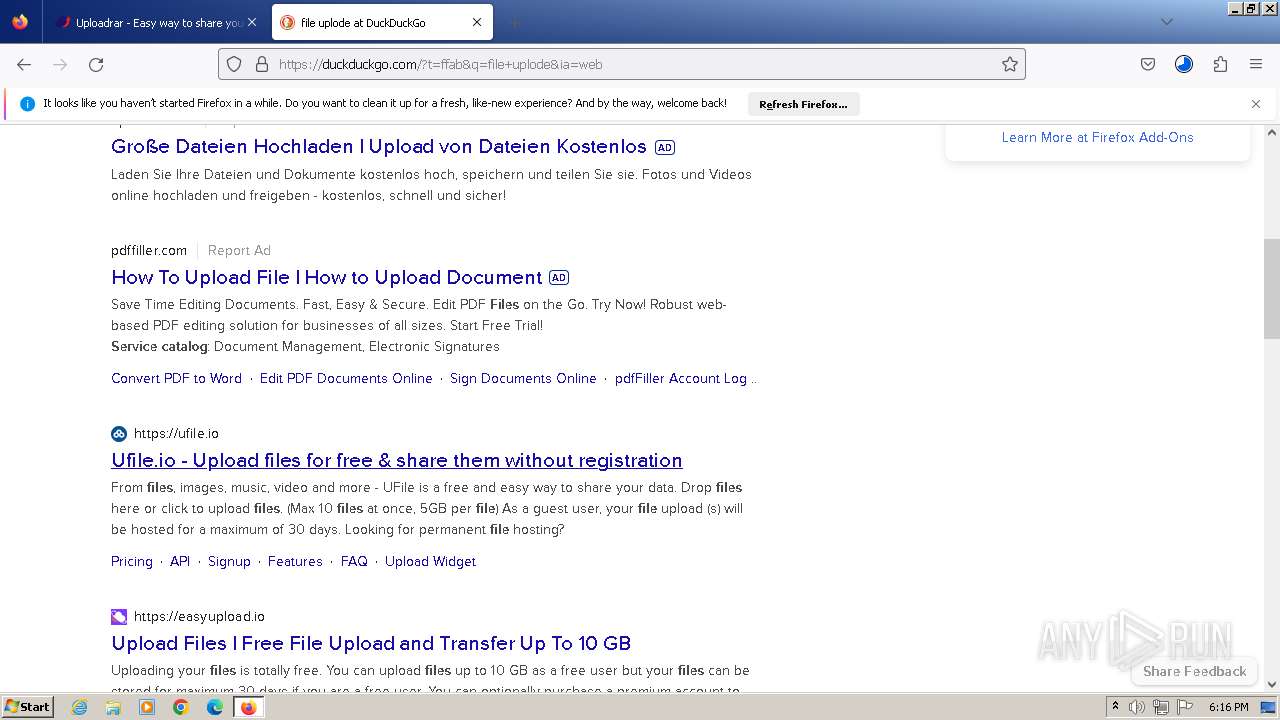
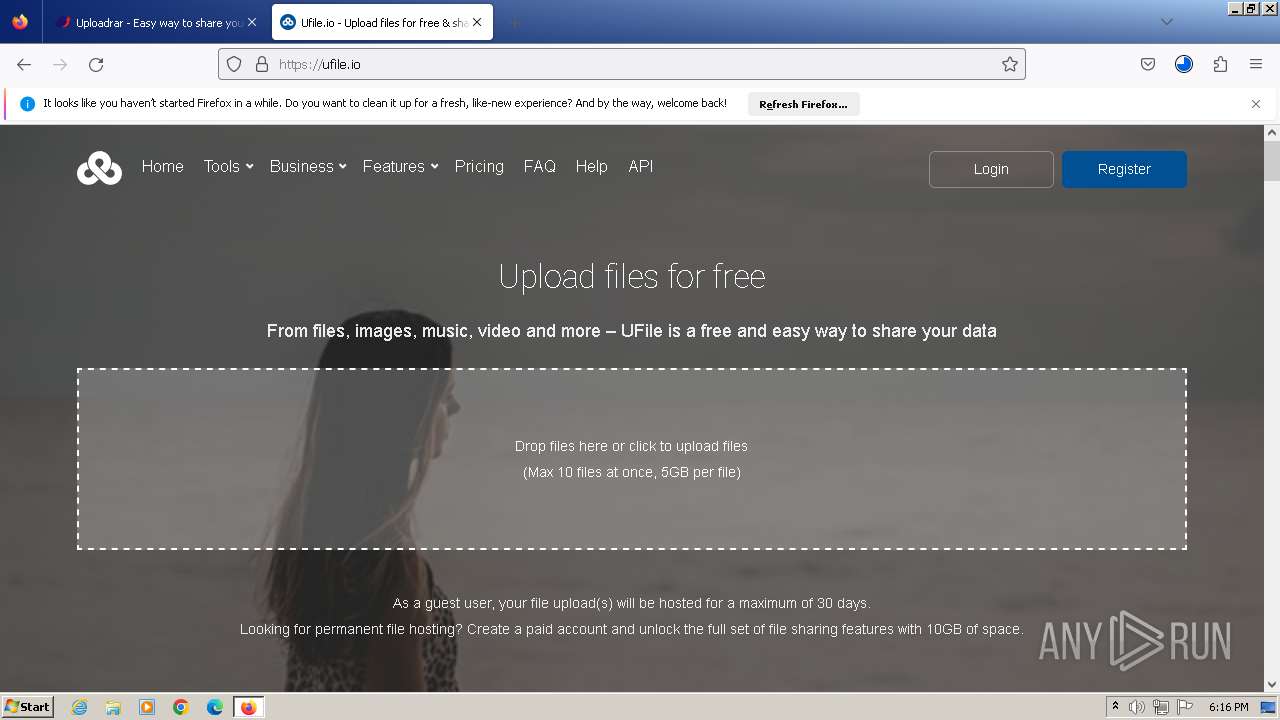
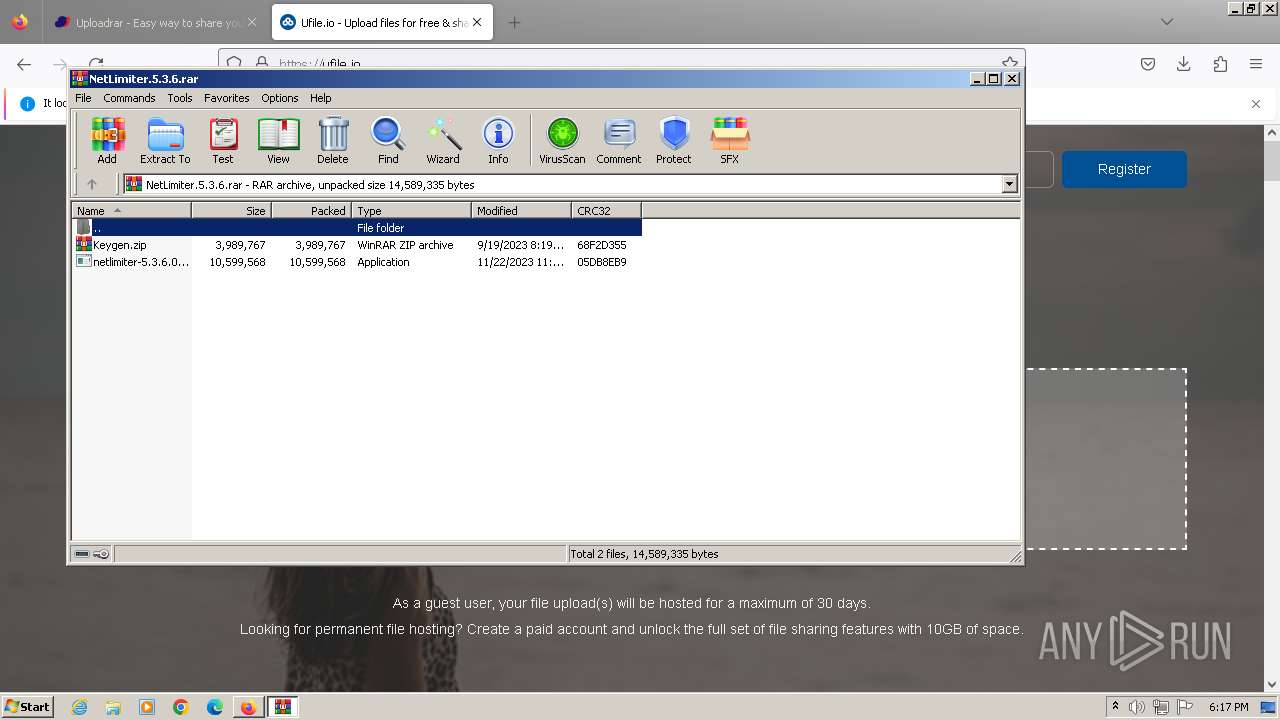
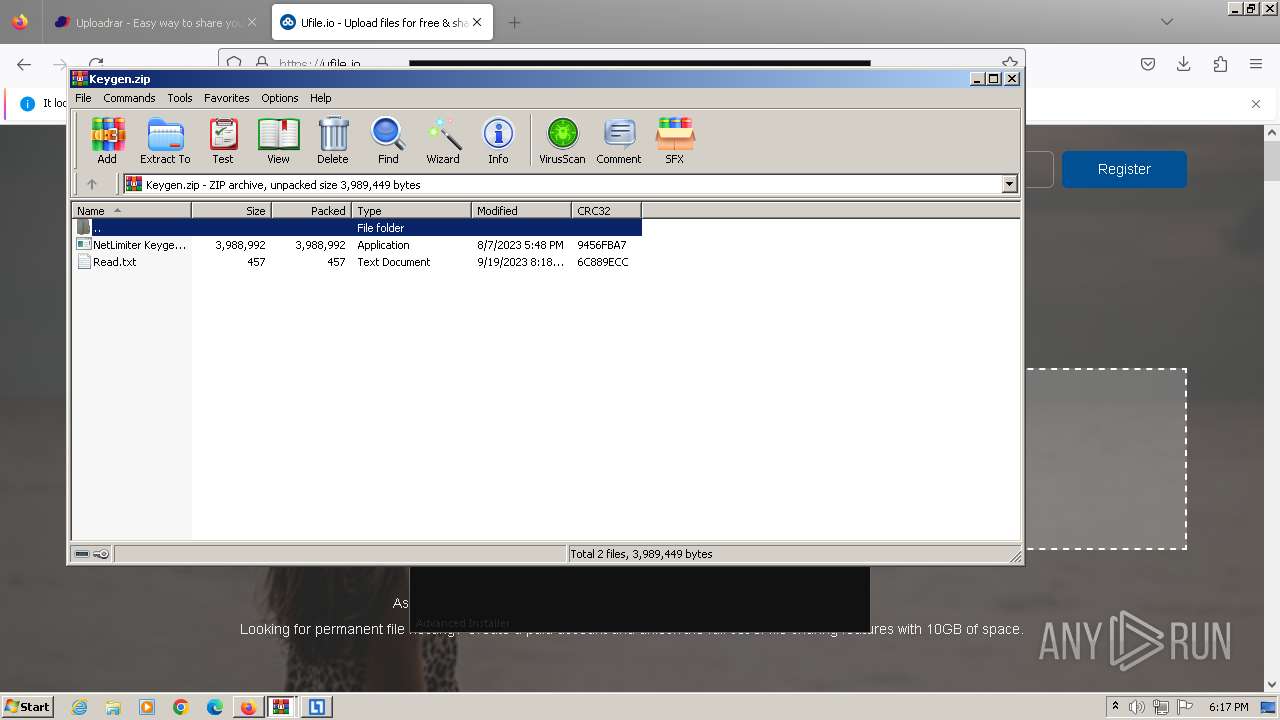
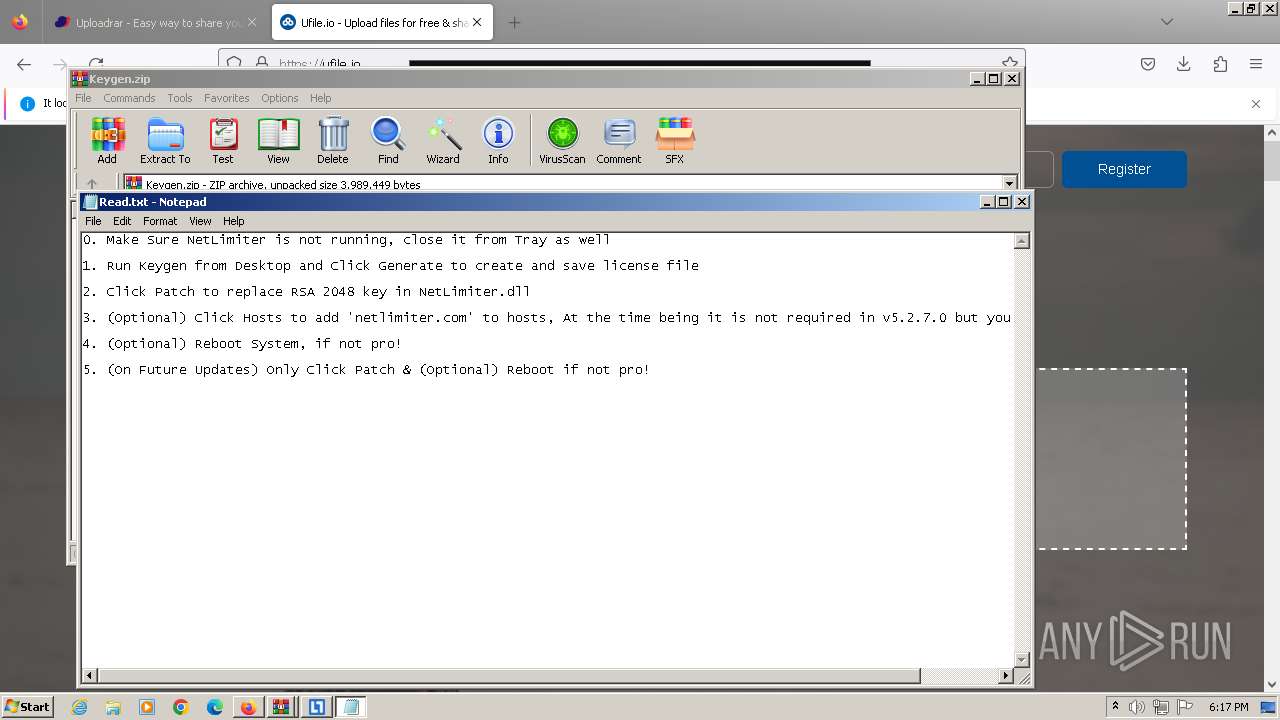
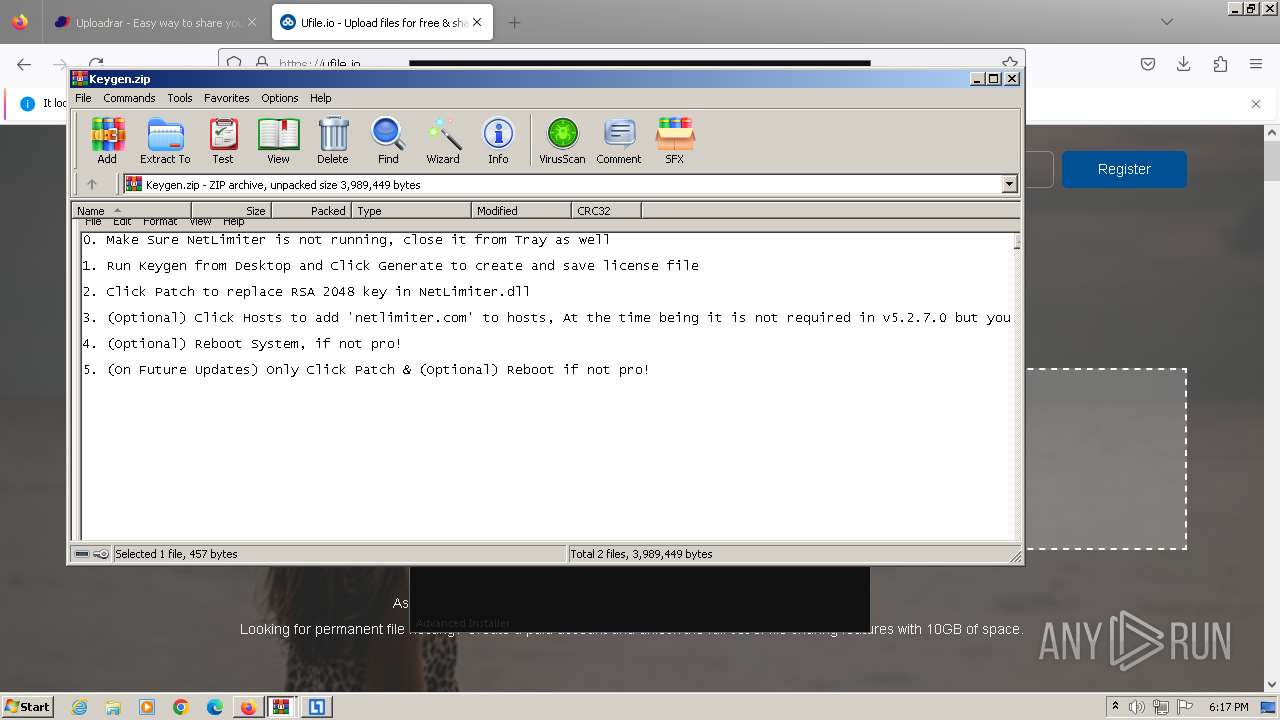
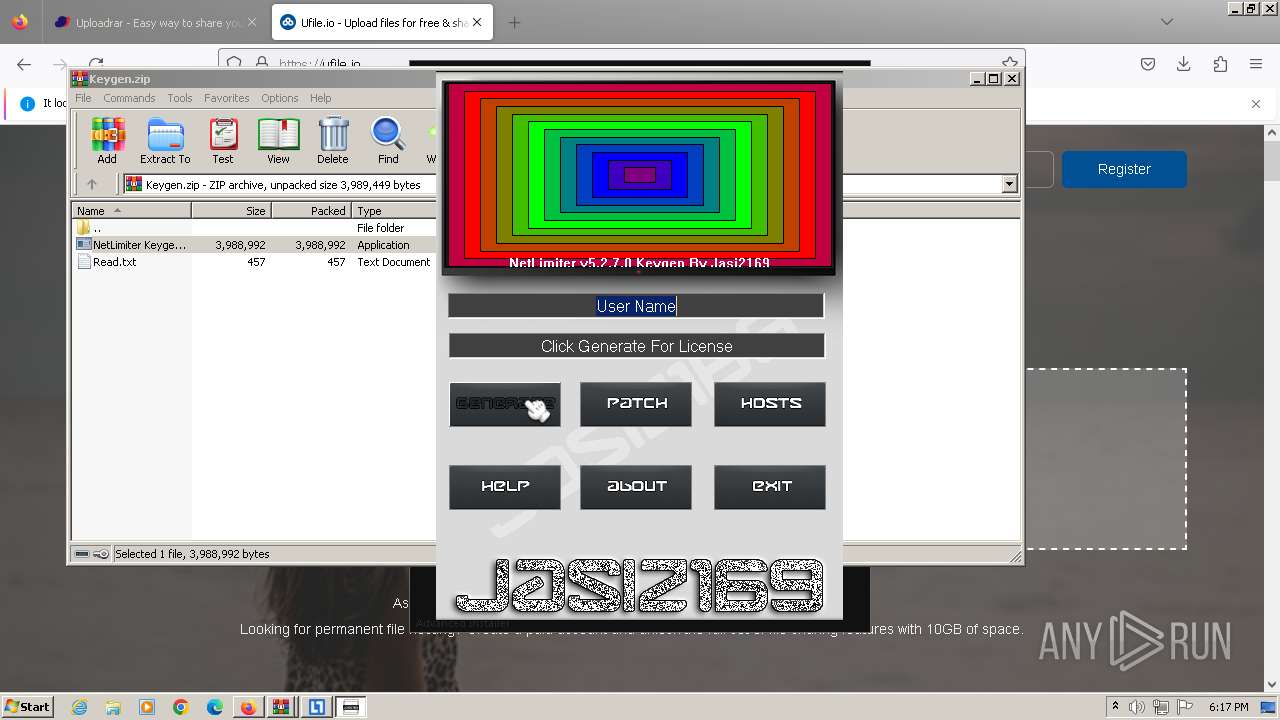
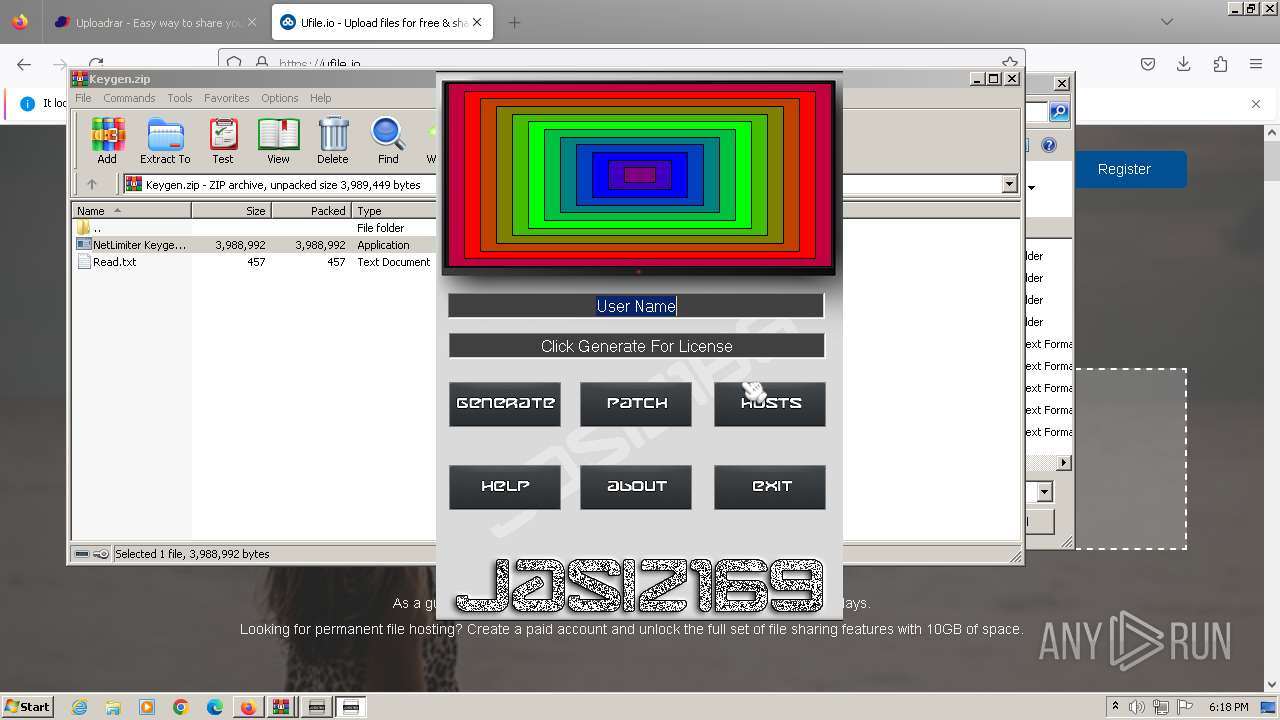
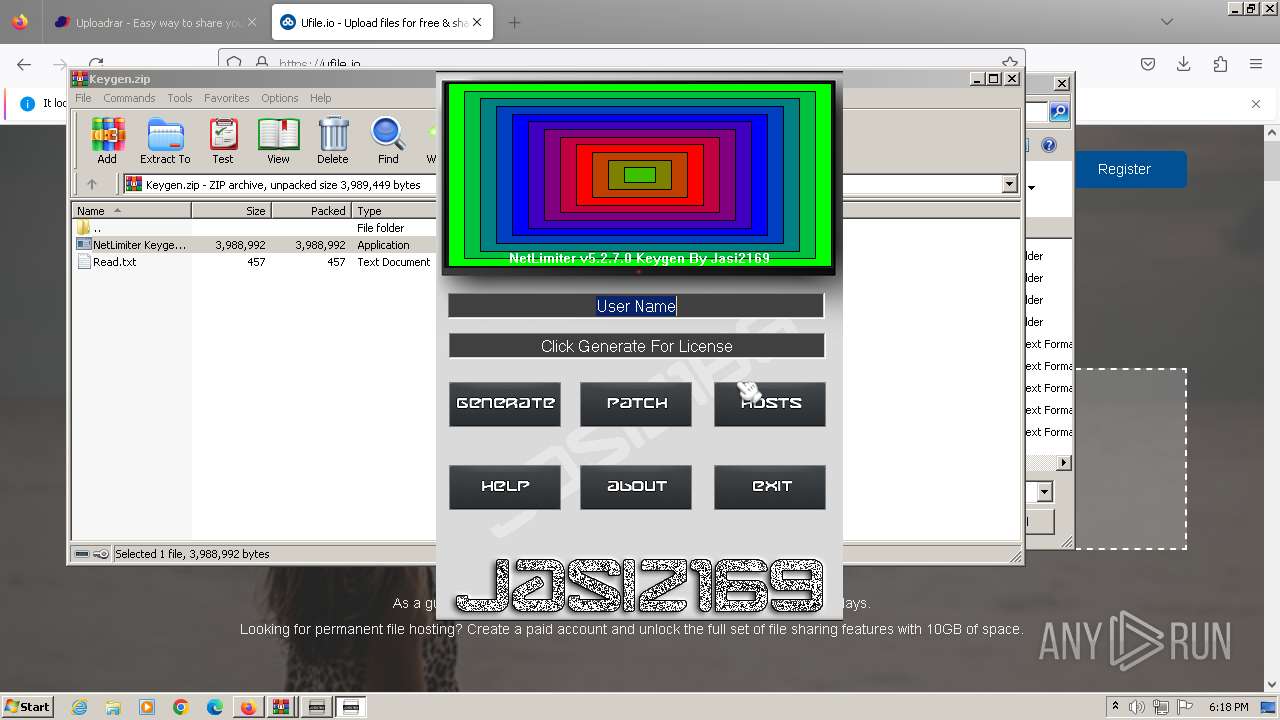
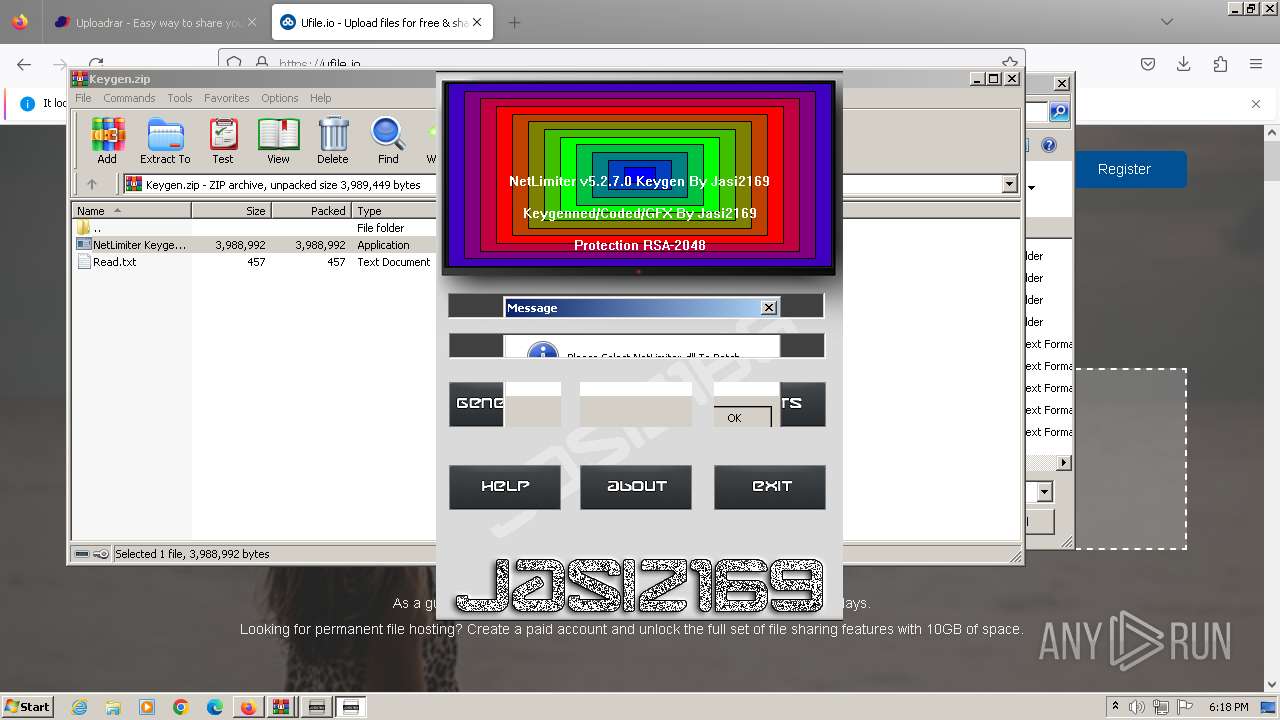
| URL: | https://file.io/TatzLqlBDtgx |
| Full analysis: | https://app.any.run/tasks/b7cf76c0-02e4-4d5d-8af7-26f49332c4f7 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 18:14:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | CB23C4848714A27B3A256958CD862EA7 |
| SHA1: | C0321264302D43325653BCDB0B2B1A2CE67FA527 |
| SHA256: | 13C91150A793279E2C5B8DEF0983489EEFB03039CF188016E4BB796D13923672 |
| SSDEEP: | 3:N8K4qHCd:2K4J |
MALICIOUS
Creates a writable file in the system directory
- msiexec.exe (PID: 5712)
- NLSvc.exe (PID: 1844)
- NetLimiter Keygen v1.3.exe (PID: 3324)
Drops the executable file immediately after the start
- msiexec.exe (PID: 5712)
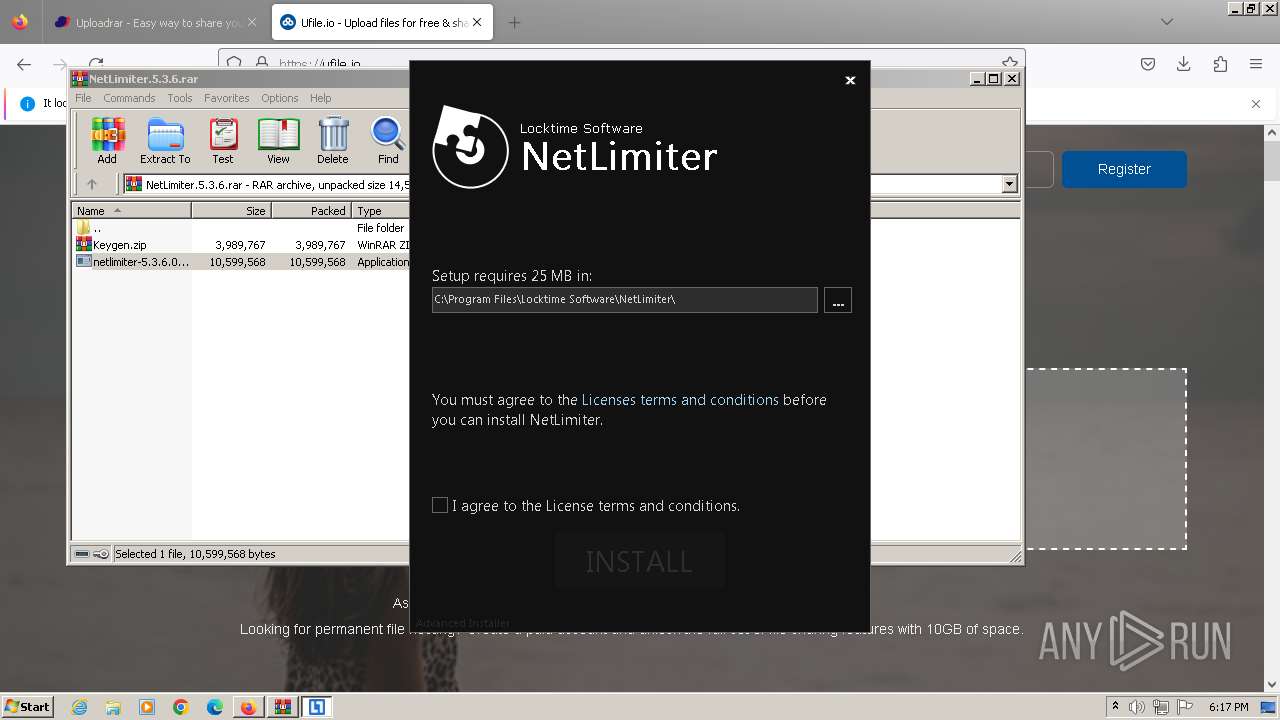
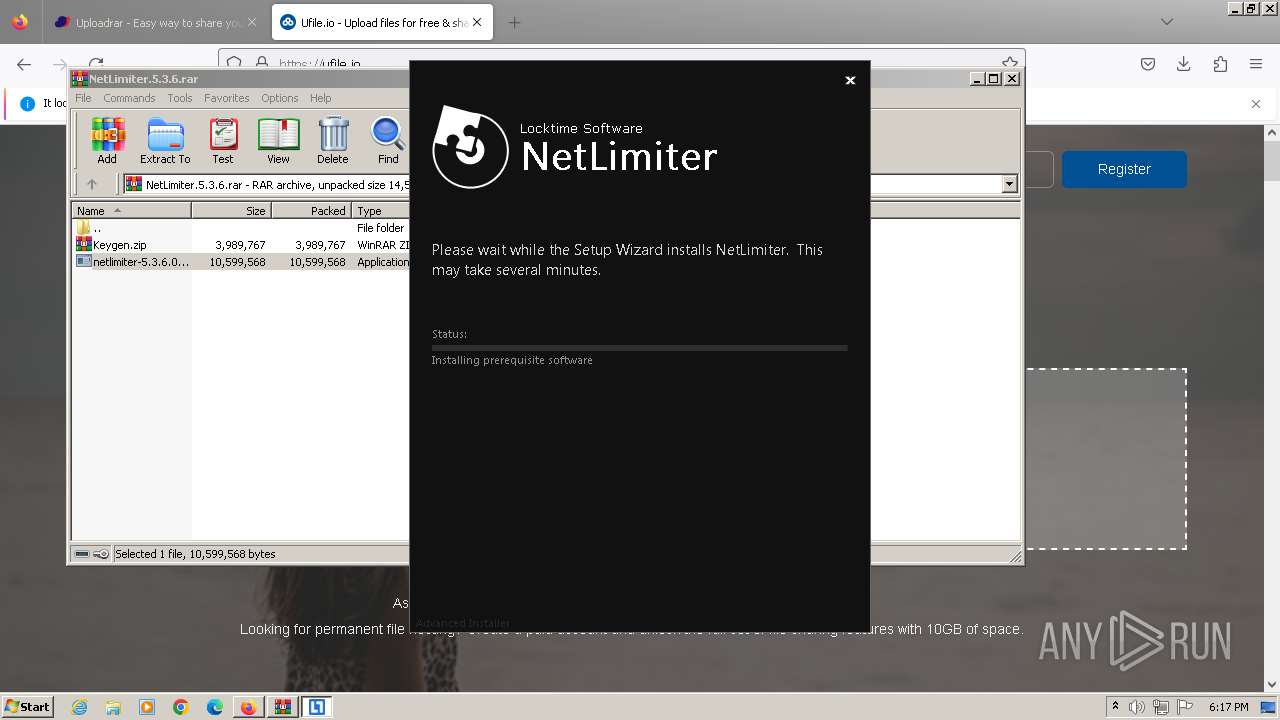
- netlimiter-5.3.6.0.exe (PID: 5608)
- mscorsvw.exe (PID: 4164)
- mscorsvw.exe (PID: 4192)
- mscorsvw.exe (PID: 4176)
- mscorsvw.exe (PID: 4160)
- mscorsvw.exe (PID: 1416)
- NetLimiter Keygen v1.3.exe (PID: 3324)
- mscorsvw.exe (PID: 1824)
- mscorsvw.exe (PID: 3520)
- mscorsvw.exe (PID: 1344)
- mscorsvw.exe (PID: 4880)
- mscorsvw.exe (PID: 5060)
- mscorsvw.exe (PID: 5320)
- mscorsvw.exe (PID: 2576)
- mscorsvw.exe (PID: 5076)
- mscorsvw.exe (PID: 4116)
- mscorsvw.exe (PID: 5420)
- mscorsvw.exe (PID: 3376)
- mscorsvw.exe (PID: 3568)
- mscorsvw.exe (PID: 5508)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 5792)
- mscorsvw.exe (PID: 5548)
- mscorsvw.exe (PID: 5588)
- mscorsvw.exe (PID: 5820)
- mscorsvw.exe (PID: 4020)
- mscorsvw.exe (PID: 2436)
- mscorsvw.exe (PID: 2480)
- mscorsvw.exe (PID: 6028)
- mscorsvw.exe (PID: 2724)
- mscorsvw.exe (PID: 1592)
- mscorsvw.exe (PID: 3620)
- mscorsvw.exe (PID: 3336)
- mscorsvw.exe (PID: 3928)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 3860)
- mscorsvw.exe (PID: 4208)
- mscorsvw.exe (PID: 4780)
- mscorsvw.exe (PID: 2828)
- mscorsvw.exe (PID: 3280)
- mscorsvw.exe (PID: 5064)
- mscorsvw.exe (PID: 4776)
- mscorsvw.exe (PID: 924)
- mscorsvw.exe (PID: 4200)
- mscorsvw.exe (PID: 1628)
- mscorsvw.exe (PID: 3168)
- mscorsvw.exe (PID: 4212)
- mscorsvw.exe (PID: 5476)
- mscorsvw.exe (PID: 3924)
- mscorsvw.exe (PID: 2412)
- mscorsvw.exe (PID: 5384)
- mscorsvw.exe (PID: 5496)
- mscorsvw.exe (PID: 5664)
- mscorsvw.exe (PID: 476)
- mscorsvw.exe (PID: 4520)
- mscorsvw.exe (PID: 588)
SUSPICIOUS
Adds/modifies Windows certificates
- netlimiter-5.3.6.0.exe (PID: 5608)
- netlimiter-5.3.6.0.exe (PID: 5868)
Reads security settings of Internet Explorer
- netlimiter-5.3.6.0.exe (PID: 5608)
- netlimiter-5.3.6.0.exe (PID: 5868)
- NLSvc.exe (PID: 4300)
- NLClientApp.exe (PID: 5864)
Checks Windows Trust Settings
- netlimiter-5.3.6.0.exe (PID: 5608)
- netlimiter-5.3.6.0.exe (PID: 5868)
- msiexec.exe (PID: 5712)
- NLSvc.exe (PID: 4300)
- NLSvc.exe (PID: 1844)
- NLClientApp.exe (PID: 5864)
Reads settings of System Certificates
- netlimiter-5.3.6.0.exe (PID: 5608)
- netlimiter-5.3.6.0.exe (PID: 5868)
- NLSvc.exe (PID: 4300)
- NLClientApp.exe (PID: 5864)
Reads the Internet Settings
- netlimiter-5.3.6.0.exe (PID: 5608)
- NLSvc.exe (PID: 4300)
- NLClientApp.exe (PID: 5864)
Application launched itself
- netlimiter-5.3.6.0.exe (PID: 5608)
- WinRAR.exe (PID: 5448)
Reads Internet Explorer settings
- netlimiter-5.3.6.0.exe (PID: 5608)
Reads the Windows owner or organization settings
- netlimiter-5.3.6.0.exe (PID: 5868)
- netlimiter-5.3.6.0.exe (PID: 5608)
Process drops legitimate windows executable
- netlimiter-5.3.6.0.exe (PID: 5608)
- msiexec.exe (PID: 5712)
- mscorsvw.exe (PID: 4164)
- mscorsvw.exe (PID: 4192)
- mscorsvw.exe (PID: 4176)
- mscorsvw.exe (PID: 1416)
- mscorsvw.exe (PID: 1824)
- mscorsvw.exe (PID: 3520)
- mscorsvw.exe (PID: 1344)
- mscorsvw.exe (PID: 5320)
- mscorsvw.exe (PID: 5060)
- mscorsvw.exe (PID: 2576)
- mscorsvw.exe (PID: 5076)
- mscorsvw.exe (PID: 5420)
- mscorsvw.exe (PID: 4116)
- mscorsvw.exe (PID: 3376)
- mscorsvw.exe (PID: 3568)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 5508)
- mscorsvw.exe (PID: 5820)
- mscorsvw.exe (PID: 5792)
- mscorsvw.exe (PID: 5548)
- mscorsvw.exe (PID: 5588)
- mscorsvw.exe (PID: 2480)
- mscorsvw.exe (PID: 3336)
- mscorsvw.exe (PID: 2724)
- mscorsvw.exe (PID: 1592)
- mscorsvw.exe (PID: 3620)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 3860)
- mscorsvw.exe (PID: 3928)
- mscorsvw.exe (PID: 4208)
- mscorsvw.exe (PID: 4780)
- mscorsvw.exe (PID: 2828)
- mscorsvw.exe (PID: 3280)
- mscorsvw.exe (PID: 5064)
- mscorsvw.exe (PID: 4776)
- mscorsvw.exe (PID: 924)
- mscorsvw.exe (PID: 4212)
- mscorsvw.exe (PID: 1628)
- mscorsvw.exe (PID: 4520)
The process creates files with name similar to system file names
- netlimiter-5.3.6.0.exe (PID: 5608)
- msiexec.exe (PID: 5712)
- mscorsvw.exe (PID: 2060)
Drops a system driver (possible attempt to evade defenses)
- netlimiter-5.3.6.0.exe (PID: 5608)
- msiexec.exe (PID: 5712)
Creates files in the driver directory
- msiexec.exe (PID: 5712)
Executes as Windows Service
- VSSVC.exe (PID: 5944)
- NLSvc.exe (PID: 1844)
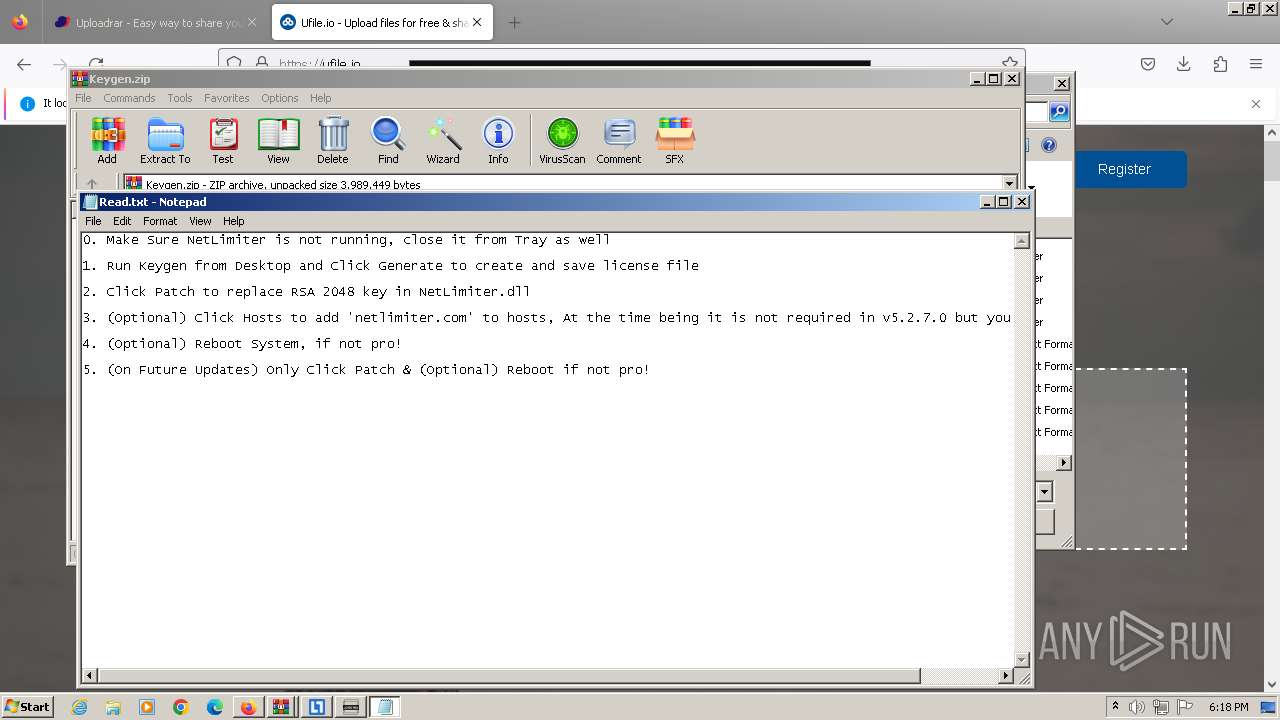
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 6104)
Reads the BIOS version
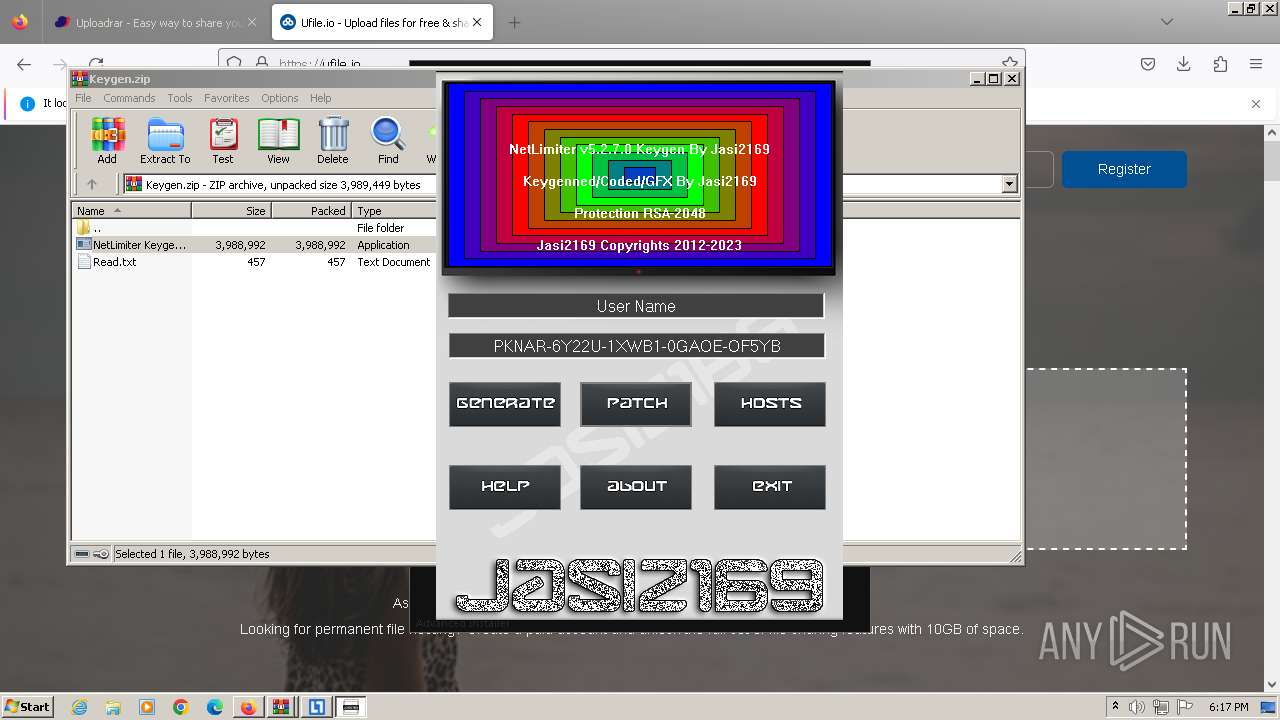
- NetLimiter Keygen v1.3.exe (PID: 3324)
- NetLimiter Keygen v1.3.exe (PID: 3272)
INFO
Application launched itself
- firefox.exe (PID: 2144)
- firefox.exe (PID: 1236)
- msiexec.exe (PID: 5712)
Checks supported languages
- wmpnscfg.exe (PID: 2436)
- netlimiter-5.3.6.0.exe (PID: 5608)
- msiexec.exe (PID: 5712)
- msiexec.exe (PID: 5760)
- netlimiter-5.3.6.0.exe (PID: 5868)
- msiexec.exe (PID: 1008)
- msiexec.exe (PID: 2100)
- NLSvc.exe (PID: 4300)
- NLSvc.exe (PID: 1844)
- mscorsvw.exe (PID: 3292)
- NetLimiter Keygen v1.3.exe (PID: 3324)
- mscorsvw.exe (PID: 4160)
- mscorsvw.exe (PID: 4164)
- mscorsvw.exe (PID: 4176)
- ngen.exe (PID: 4328)
- mscorsvw.exe (PID: 4192)
- mscorsvw.exe (PID: 1344)
- mscorsvw.exe (PID: 1416)
- mscorsvw.exe (PID: 3520)
- mscorsvw.exe (PID: 1824)
- mscorsvw.exe (PID: 4880)
- mscorsvw.exe (PID: 4520)
- mscorsvw.exe (PID: 5320)
- mscorsvw.exe (PID: 5076)
- mscorsvw.exe (PID: 5060)
- mscorsvw.exe (PID: 3376)
- mscorsvw.exe (PID: 4116)
- mscorsvw.exe (PID: 2576)
- mscorsvw.exe (PID: 3568)
- mscorsvw.exe (PID: 5508)
- mscorsvw.exe (PID: 5420)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 5792)
- mscorsvw.exe (PID: 5820)
- mscorsvw.exe (PID: 2480)
- mscorsvw.exe (PID: 5588)
- mscorsvw.exe (PID: 6028)
- mscorsvw.exe (PID: 4020)
- mscorsvw.exe (PID: 5548)
- mscorsvw.exe (PID: 2436)
- mscorsvw.exe (PID: 3336)
- mscorsvw.exe (PID: 1592)
- mscorsvw.exe (PID: 2724)
- mscorsvw.exe (PID: 3620)
- mscorsvw.exe (PID: 3928)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 4212)
- mscorsvw.exe (PID: 4208)
- mscorsvw.exe (PID: 2828)
- mscorsvw.exe (PID: 3860)
- mscorsvw.exe (PID: 4780)
- mscorsvw.exe (PID: 924)
- mscorsvw.exe (PID: 3280)
- mscorsvw.exe (PID: 5064)
- mscorsvw.exe (PID: 4776)
- mscorsvw.exe (PID: 4200)
- mscorsvw.exe (PID: 3924)
- mscorsvw.exe (PID: 1628)
- mscorsvw.exe (PID: 3168)
- mscorsvw.exe (PID: 2412)
- mscorsvw.exe (PID: 5384)
- mscorsvw.exe (PID: 5476)
- mscorsvw.exe (PID: 476)
- mscorsvw.exe (PID: 588)
- mscorsvw.exe (PID: 5496)
- mscorsvw.exe (PID: 5664)
- NetLimiter Keygen v1.3.exe (PID: 3272)
- NLClientApp.exe (PID: 5864)
Connects to unusual port
- firefox.exe (PID: 1236)
Manual execution by a user
- wmpnscfg.exe (PID: 2436)
- WinRAR.exe (PID: 5448)
Drops the executable file immediately after the start
- firefox.exe (PID: 1236)
- WinRAR.exe (PID: 5448)
- WinRAR.exe (PID: 6104)
Reads the computer name
- wmpnscfg.exe (PID: 2436)
- msiexec.exe (PID: 5712)
- netlimiter-5.3.6.0.exe (PID: 5608)
- netlimiter-5.3.6.0.exe (PID: 5868)
- msiexec.exe (PID: 5760)
- msiexec.exe (PID: 1008)
- msiexec.exe (PID: 2100)
- NLSvc.exe (PID: 4300)
- NLSvc.exe (PID: 1844)
- mscorsvw.exe (PID: 3292)
- ngen.exe (PID: 4328)
- mscorsvw.exe (PID: 4160)
- mscorsvw.exe (PID: 4164)
- mscorsvw.exe (PID: 4192)
- mscorsvw.exe (PID: 4176)
- mscorsvw.exe (PID: 1344)
- mscorsvw.exe (PID: 1416)
- mscorsvw.exe (PID: 1824)
- mscorsvw.exe (PID: 4880)
- mscorsvw.exe (PID: 3520)
- NetLimiter Keygen v1.3.exe (PID: 3324)
- mscorsvw.exe (PID: 5320)
- mscorsvw.exe (PID: 5076)
- mscorsvw.exe (PID: 4520)
- mscorsvw.exe (PID: 5060)
- mscorsvw.exe (PID: 3376)
- mscorsvw.exe (PID: 4116)
- mscorsvw.exe (PID: 2576)
- mscorsvw.exe (PID: 3568)
- mscorsvw.exe (PID: 5508)
- mscorsvw.exe (PID: 5420)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 5792)
- mscorsvw.exe (PID: 5820)
- mscorsvw.exe (PID: 2480)
- mscorsvw.exe (PID: 5548)
- mscorsvw.exe (PID: 5588)
- mscorsvw.exe (PID: 6028)
- mscorsvw.exe (PID: 4020)
- mscorsvw.exe (PID: 2436)
- mscorsvw.exe (PID: 3336)
- mscorsvw.exe (PID: 1592)
- mscorsvw.exe (PID: 3620)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 2724)
- mscorsvw.exe (PID: 3928)
- mscorsvw.exe (PID: 3860)
- mscorsvw.exe (PID: 4212)
- mscorsvw.exe (PID: 4208)
- mscorsvw.exe (PID: 2828)
- mscorsvw.exe (PID: 924)
- mscorsvw.exe (PID: 4780)
- mscorsvw.exe (PID: 3280)
- mscorsvw.exe (PID: 5064)
- mscorsvw.exe (PID: 4776)
- mscorsvw.exe (PID: 4200)
- mscorsvw.exe (PID: 1628)
- mscorsvw.exe (PID: 3168)
- mscorsvw.exe (PID: 2412)
- mscorsvw.exe (PID: 3924)
- mscorsvw.exe (PID: 476)
- mscorsvw.exe (PID: 5476)
- mscorsvw.exe (PID: 5384)
- mscorsvw.exe (PID: 5496)
- mscorsvw.exe (PID: 5664)
- mscorsvw.exe (PID: 588)
- NetLimiter Keygen v1.3.exe (PID: 3272)
- NLClientApp.exe (PID: 5864)
The process uses the downloaded file
- firefox.exe (PID: 1236)
- WinRAR.exe (PID: 5448)
Reads Environment values
- netlimiter-5.3.6.0.exe (PID: 5608)
- msiexec.exe (PID: 5760)
- netlimiter-5.3.6.0.exe (PID: 5868)
- msiexec.exe (PID: 1008)
Reads the machine GUID from the registry
- netlimiter-5.3.6.0.exe (PID: 5608)
- msiexec.exe (PID: 5760)
- netlimiter-5.3.6.0.exe (PID: 5868)
- msiexec.exe (PID: 5712)
- msiexec.exe (PID: 1008)
- msiexec.exe (PID: 2100)
- NLSvc.exe (PID: 4300)
- NLSvc.exe (PID: 1844)
- mscorsvw.exe (PID: 3292)
- ngen.exe (PID: 4328)
- mscorsvw.exe (PID: 4176)
- mscorsvw.exe (PID: 4164)
- mscorsvw.exe (PID: 4160)
- mscorsvw.exe (PID: 4192)
- mscorsvw.exe (PID: 1344)
- mscorsvw.exe (PID: 1416)
- mscorsvw.exe (PID: 1824)
- mscorsvw.exe (PID: 3520)
- NetLimiter Keygen v1.3.exe (PID: 3324)
- mscorsvw.exe (PID: 5076)
- mscorsvw.exe (PID: 5320)
- mscorsvw.exe (PID: 4520)
- mscorsvw.exe (PID: 4880)
- mscorsvw.exe (PID: 5060)
- mscorsvw.exe (PID: 3376)
- mscorsvw.exe (PID: 2576)
- mscorsvw.exe (PID: 3568)
- mscorsvw.exe (PID: 5508)
- mscorsvw.exe (PID: 4116)
- mscorsvw.exe (PID: 5420)
- mscorsvw.exe (PID: 2480)
- mscorsvw.exe (PID: 2344)
- mscorsvw.exe (PID: 5792)
- mscorsvw.exe (PID: 5820)
- mscorsvw.exe (PID: 5588)
- mscorsvw.exe (PID: 6028)
- mscorsvw.exe (PID: 5548)
- mscorsvw.exe (PID: 2436)
- mscorsvw.exe (PID: 3336)
- mscorsvw.exe (PID: 1592)
- mscorsvw.exe (PID: 4020)
- mscorsvw.exe (PID: 3620)
- mscorsvw.exe (PID: 3928)
- mscorsvw.exe (PID: 2724)
- mscorsvw.exe (PID: 3860)
- mscorsvw.exe (PID: 2060)
- mscorsvw.exe (PID: 4780)
- mscorsvw.exe (PID: 924)
- mscorsvw.exe (PID: 3280)
- mscorsvw.exe (PID: 4212)
- mscorsvw.exe (PID: 2828)
- mscorsvw.exe (PID: 4208)
- mscorsvw.exe (PID: 5064)
- mscorsvw.exe (PID: 4776)
- mscorsvw.exe (PID: 1628)
- mscorsvw.exe (PID: 3168)
- mscorsvw.exe (PID: 2412)
- mscorsvw.exe (PID: 3924)
- mscorsvw.exe (PID: 4200)
- mscorsvw.exe (PID: 5384)
- mscorsvw.exe (PID: 476)
- mscorsvw.exe (PID: 5476)
- mscorsvw.exe (PID: 588)
- mscorsvw.exe (PID: 5496)
- mscorsvw.exe (PID: 5664)
- NetLimiter Keygen v1.3.exe (PID: 3272)
- NLClientApp.exe (PID: 5864)
Create files in a temporary directory
- netlimiter-5.3.6.0.exe (PID: 5608)
- msiexec.exe (PID: 5712)
- msiexec.exe (PID: 2100)
- msiexec.exe (PID: 1008)
- NetLimiter Keygen v1.3.exe (PID: 3324)
- NetLimiter Keygen v1.3.exe (PID: 3272)
Creates files or folders in the user directory
- netlimiter-5.3.6.0.exe (PID: 5608)
Creates files in the program directory
- NLSvc.exe (PID: 4300)
- NLSvc.exe (PID: 1844)
- mscorsvw.exe (PID: 3292)
- NetLimiter Keygen v1.3.exe (PID: 3324)
- NLClientApp.exe (PID: 5864)
Process checks are UAC notifies on
- NetLimiter Keygen v1.3.exe (PID: 3324)
- NetLimiter Keygen v1.3.exe (PID: 3272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
158
Monitored processes
107
Malicious processes
10
Suspicious processes
55
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 276 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1236.14.640334652\569804156" -childID 11 -isForBrowser -prefsHandle 7388 -prefMapHandle 7384 -prefsLen 31122 -prefMapSize 244195 -jsInitHandle 884 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {74867251-1450-4528-b1c2-f299600f33c3} 1236 "\\.\pipe\gecko-crash-server-pipe.1236" 7400 25efee00 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 280 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1236.0.1792931140\929799879" -parentBuildID 20230710165010 -prefsHandle 1112 -prefMapHandle 1104 -prefsLen 28523 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b690c5c3-5566-4749-aaad-231de97e300a} 1236 "\\.\pipe\gecko-crash-server-pipe.1236" 1212 d8a8e50 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 476 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 298 -InterruptEvent 0 -NGENProcess 288 -Pipe 1dc -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 588 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 26c -InterruptEvent 0 -NGENProcess 2c8 -Pipe 2a8 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 924 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 238 -InterruptEvent 0 -NGENProcess 26c -Pipe 290 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1008 | C:\Windows\system32\MsiExec.exe -Embedding E14931DC5124CC3327BAB751E91B46DC | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1088 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="1236.1.435147002\255942857" -parentBuildID 20230710165010 -prefsHandle 1412 -prefMapHandle 1408 -prefsLen 28600 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {f346252b-d0b3-4e63-9951-8e0d0351e1e0} 1236 "\\.\pipe\gecko-crash-server-pipe.1236" 1424 d8215e0 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://file.io/TatzLqlBDtgx | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 1344 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 1c8 -InterruptEvent 0 -NGENProcess 1d4 -Pipe 1d0 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1416 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 218 -InterruptEvent 0 -NGENProcess 1c8 -Pipe 1b0 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
Total events
94 349
Read events
94 087
Write events
243
Delete events
19
Modification events
| (PID) Process: | (2144) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 2166C0A101000000 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 044CC1A101000000 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
| (PID) Process: | (1236) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|AppLastRunTime |
Value: D14E5F3C23B0D901 | |||
Executable files
592
Suspicious files
382
Text files
158
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | text | |
MD5:60E0DE9E05EC76C749D80F0D15A81B21 | SHA256:08252FA62CCCCD316474E20CC7317A6B5C932B2C972234318E8CCDA39EC2EF48 | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:B7A3C61D0C144CC5E166B1E769CA8F8C | SHA256:7FADCB77FFACA6B9E9F15C6F1CD3AAD4C20DCD90FA92429A627A3A7110CA2644 | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.tmp | binary | |
MD5:63B1BB87284EFE954E1C3AE390E7EE44 | SHA256:B017EE25A7F5C09EB4BF359CA721D67E6E9D9F95F8CE6F741D47F33BDE6EF73A | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\datareporting\glean\db\data.safe.bin | binary | |
MD5:63B1BB87284EFE954E1C3AE390E7EE44 | SHA256:B017EE25A7F5C09EB4BF359CA721D67E6E9D9F95F8CE6F741D47F33BDE6EF73A | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 1236 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
78
TCP/UDP connections
259
DNS requests
455
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1236 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
1236 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
1236 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
1236 | firefox.exe | POST | 200 | 184.24.77.46:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
1236 | firefox.exe | POST | 200 | 184.24.77.46:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
1236 | firefox.exe | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | binary | 472 b | unknown |
1236 | firefox.exe | POST | 200 | 184.24.77.46:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
1236 | firefox.exe | POST | 200 | 142.250.185.131:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
1236 | firefox.exe | POST | 200 | 184.24.77.53:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
1236 | firefox.exe | POST | 200 | 184.24.77.46:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1236 | firefox.exe | 45.55.107.24:443 | file.io | DIGITALOCEAN-ASN | US | unknown |
1236 | firefox.exe | 216.58.206.42:443 | safebrowsing.googleapis.com | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1236 | firefox.exe | 142.250.185.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1236 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | unknown |
1236 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
1236 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
file.io |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
spocs.getpocket.com |
| shared |
proxyserverecs-1736642167.us-east-1.elb.amazonaws.com |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (ufile .io) |
1080 | svchost.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (ufile .io) |
1080 | svchost.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (ufile .io) |
1236 | firefox.exe | Misc activity | ET INFO Observed External IP Lookup Domain (ufile .io in TLS SNI) |
1080 | svchost.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (ufile .io) |
1080 | svchost.exe | Misc activity | ET INFO File Sharing Service Domain in DNS Lookup (ufile .io) |
Process | Message |
|---|---|
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |
msiexec.exe | Logger::SetLogFile( C:\Users\admin\AppData\Roaming\Caphyon\Advanced Installer\AI_ResourceCleaner.log ) while OLD path is: |