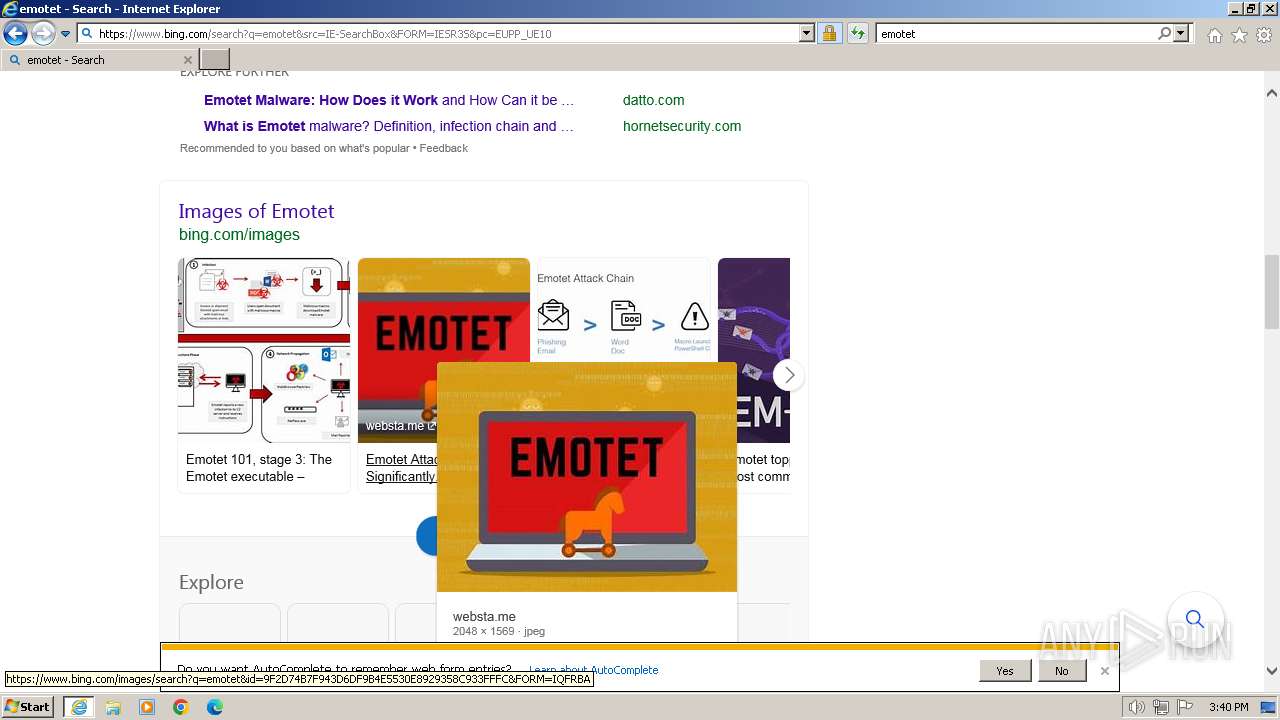
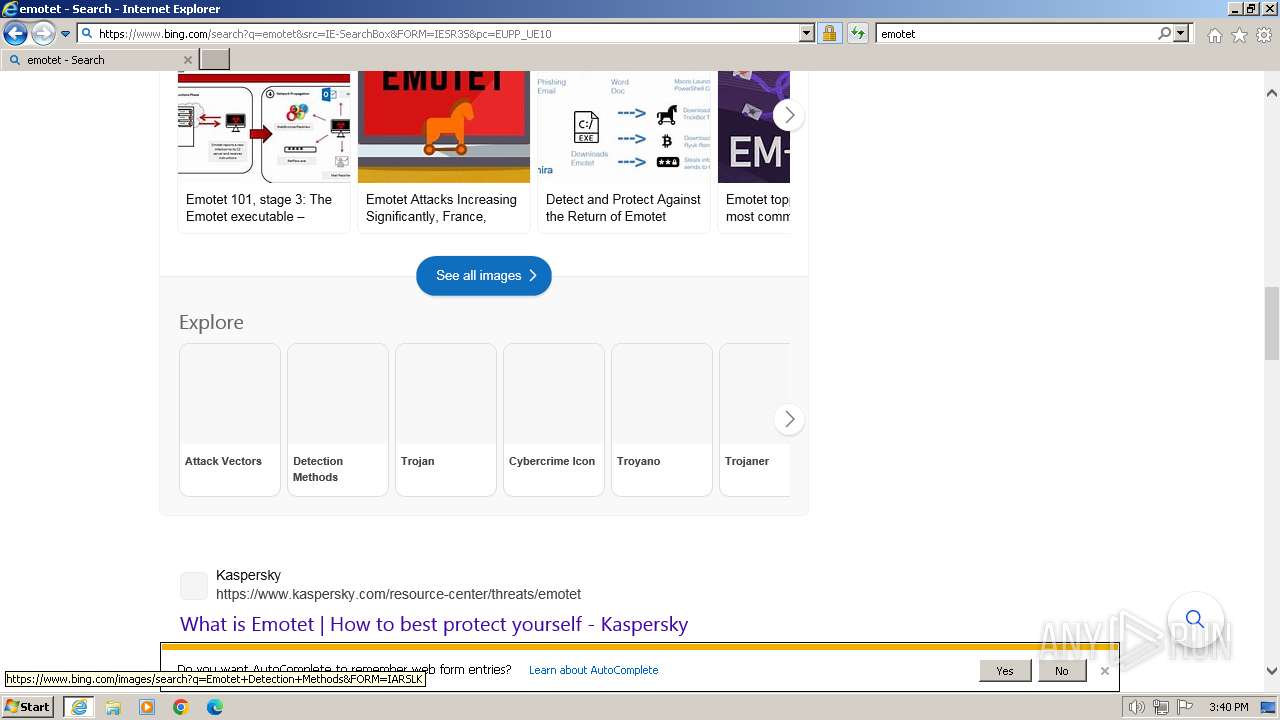
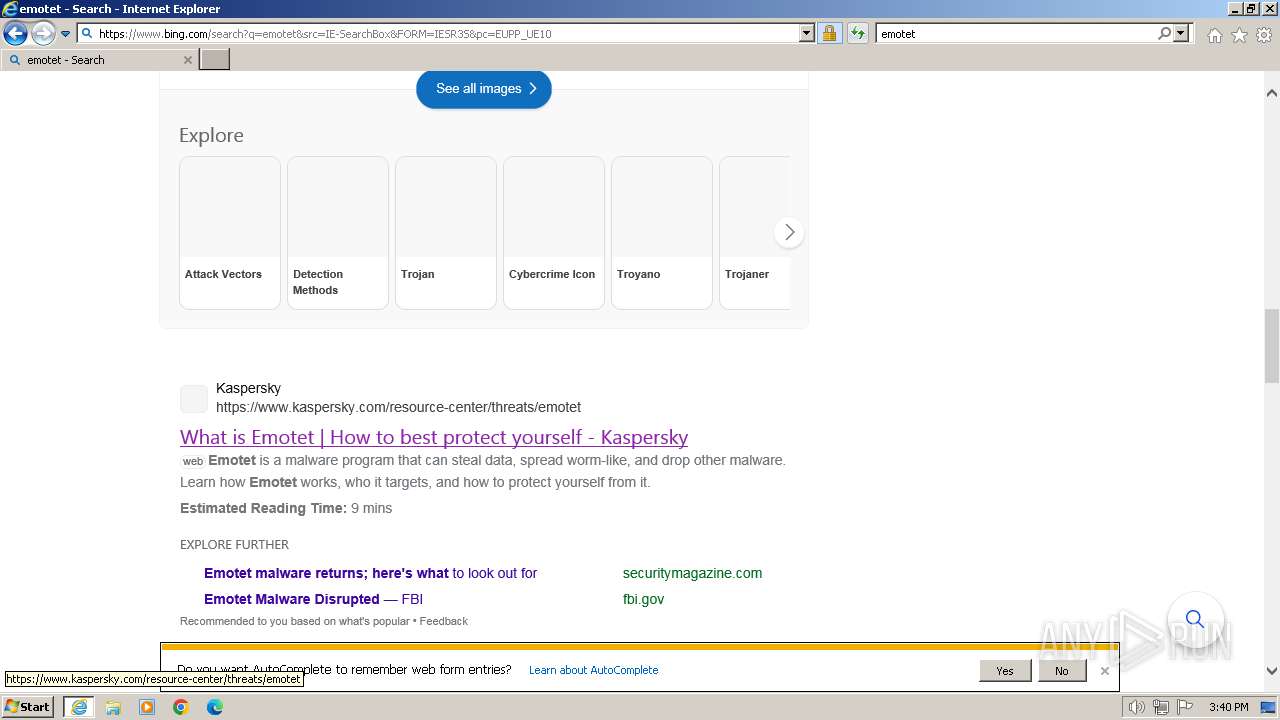
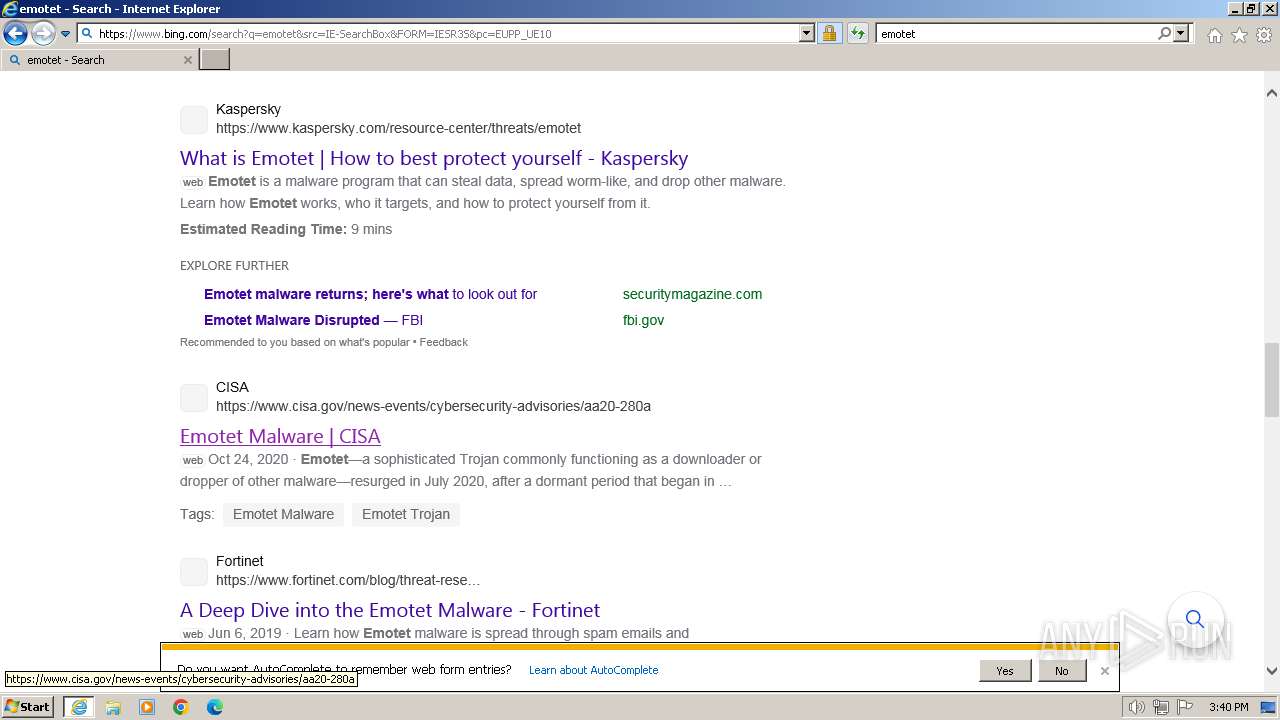
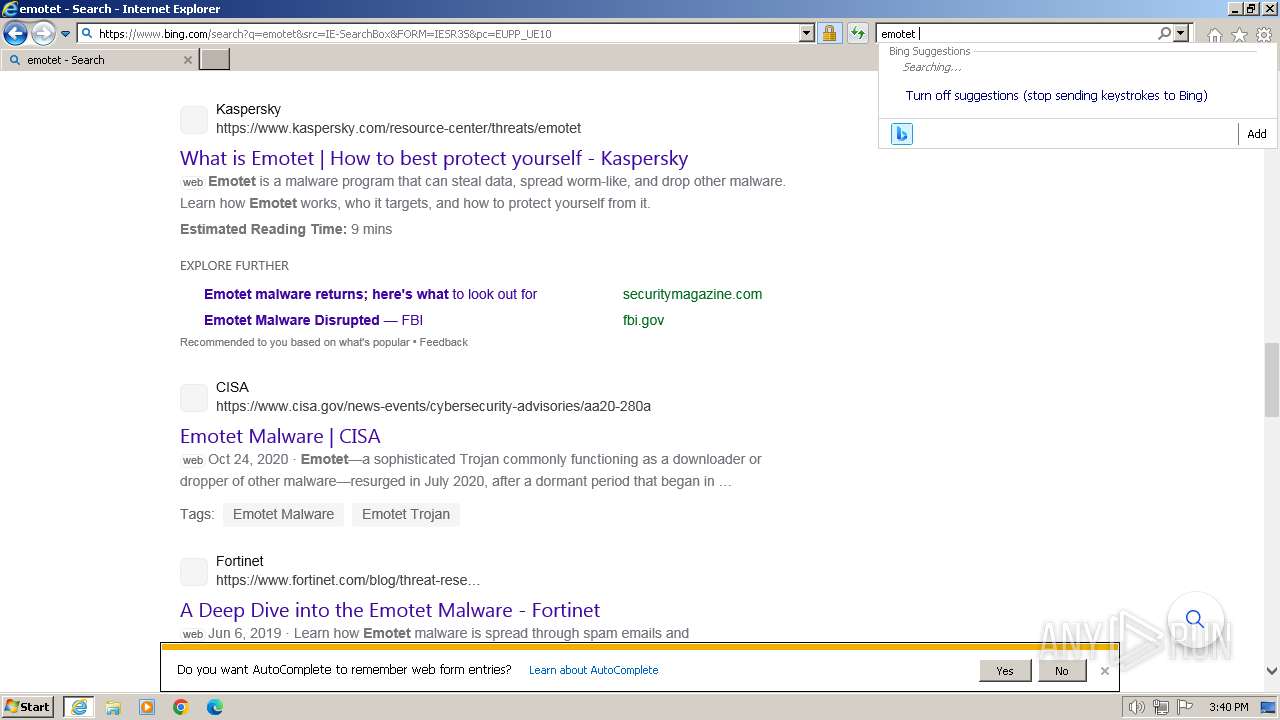
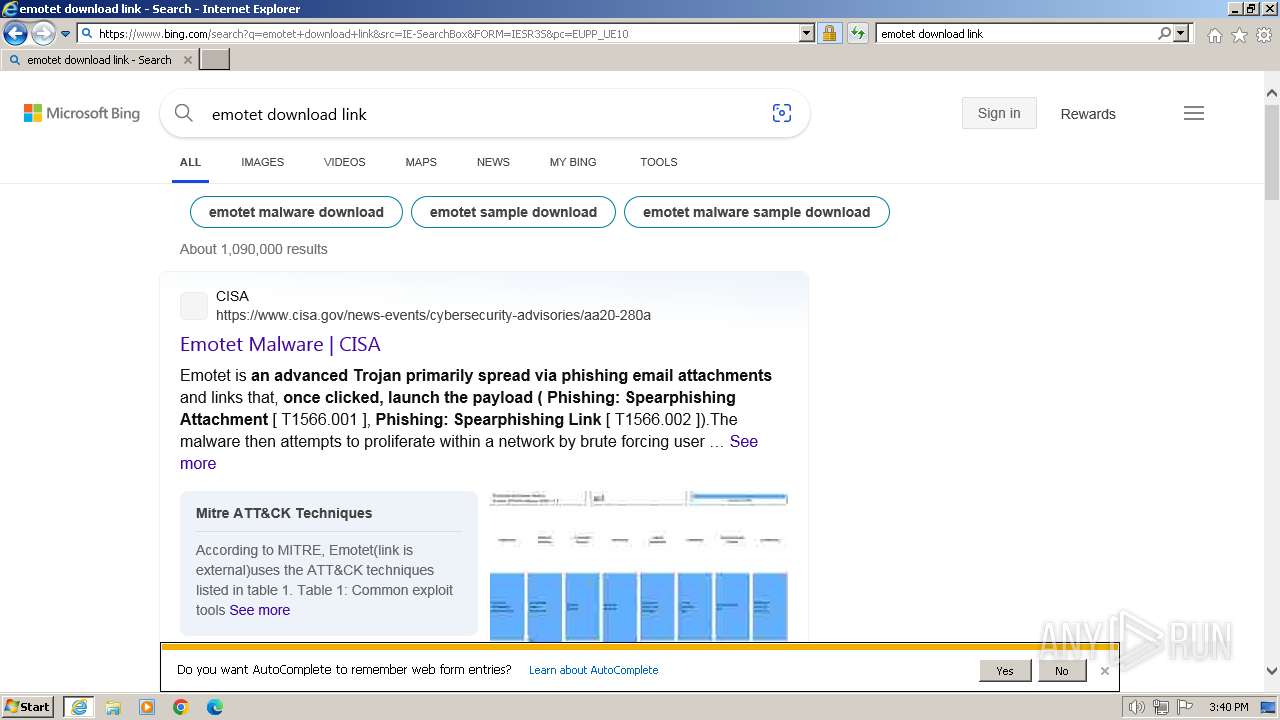
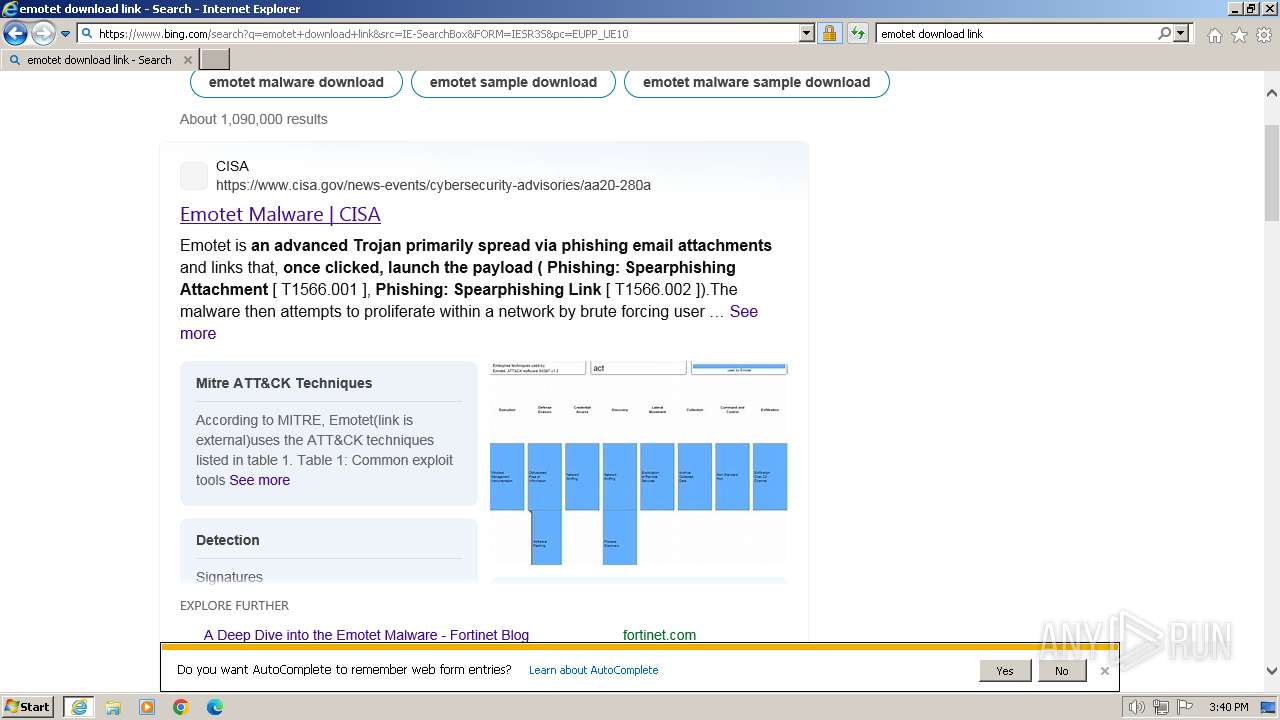
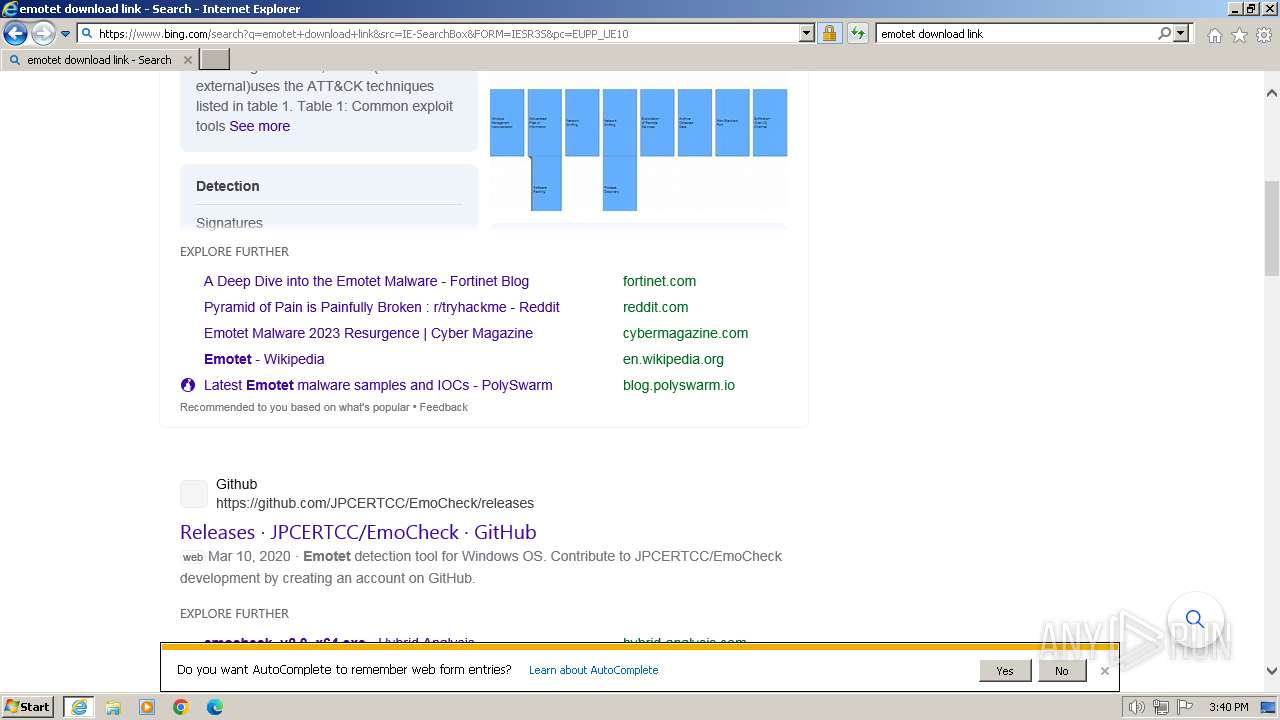
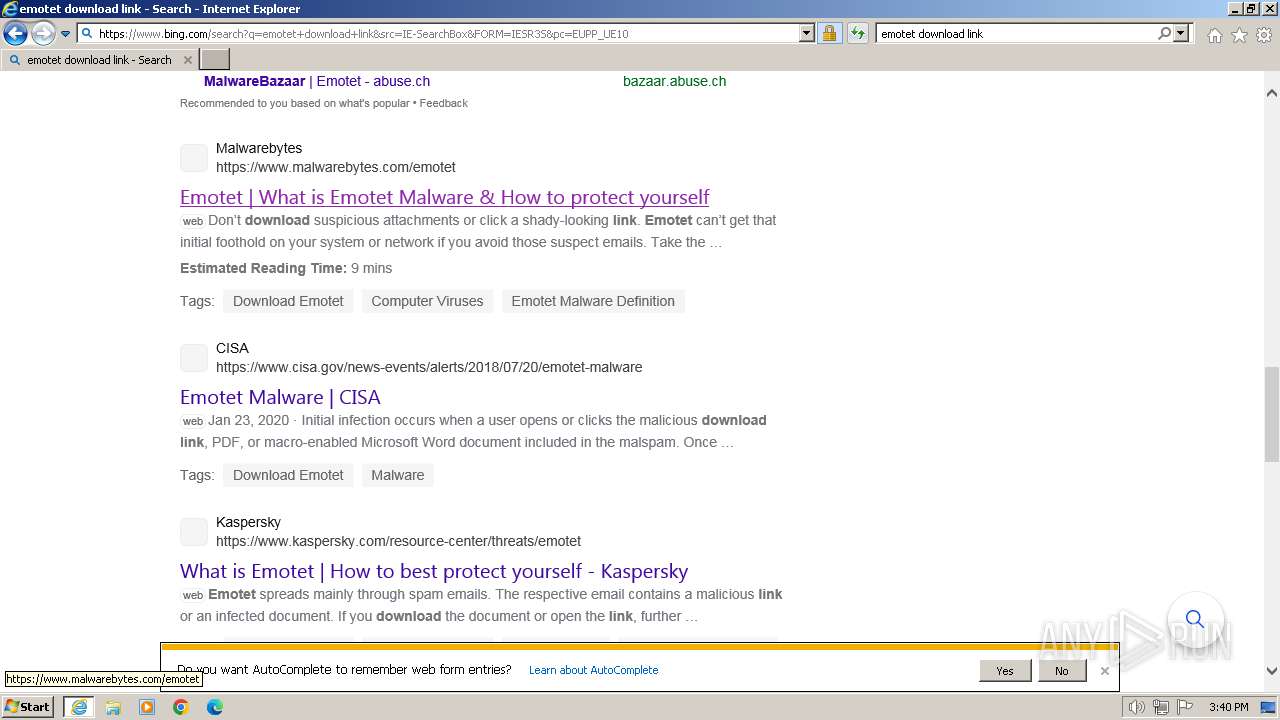
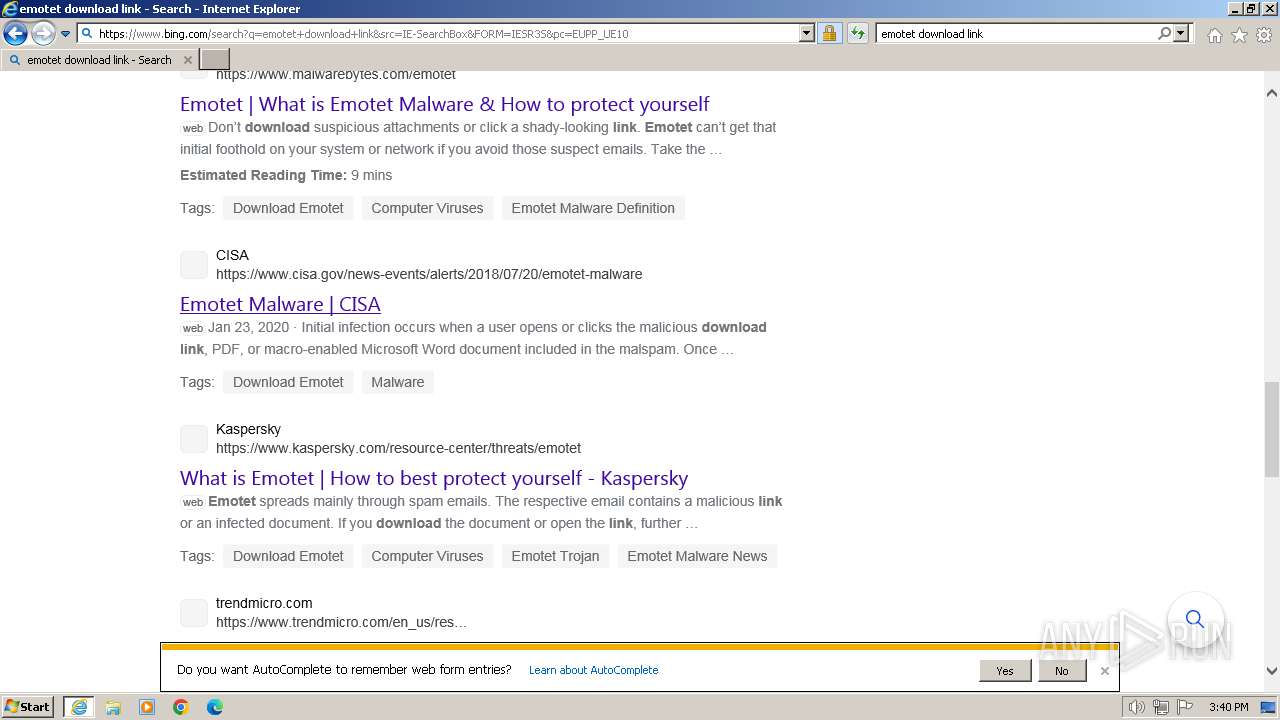
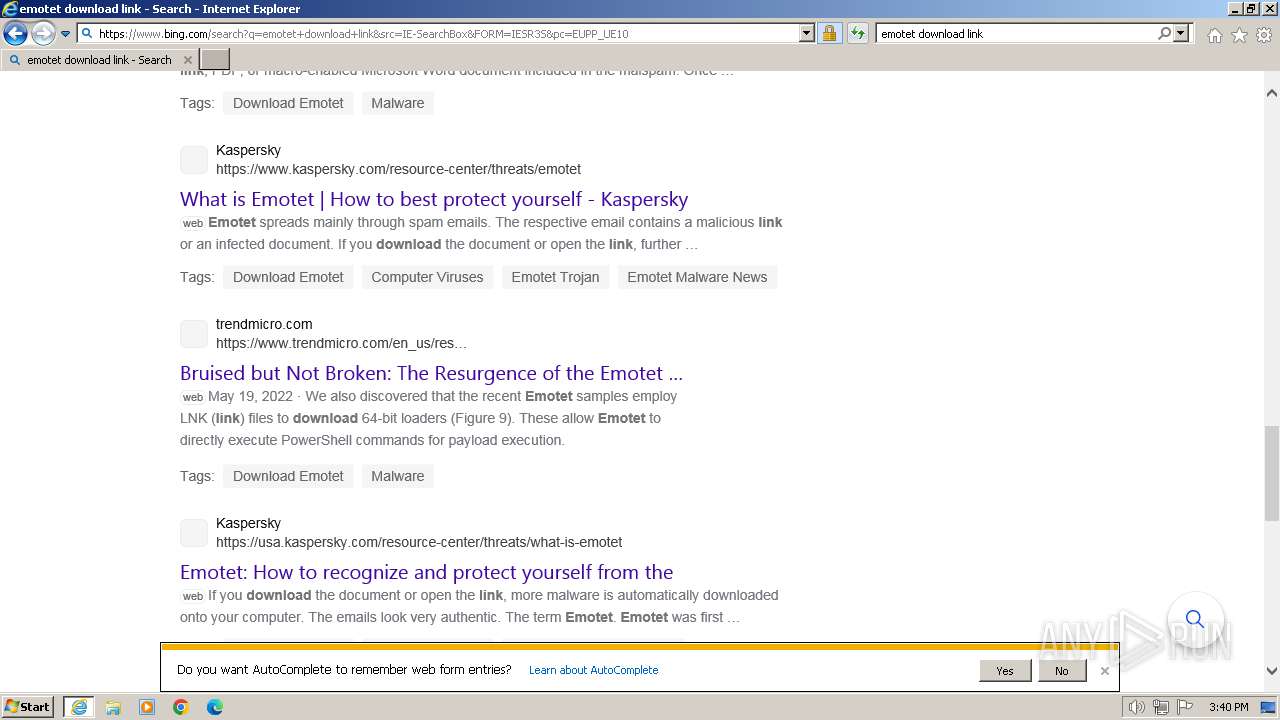
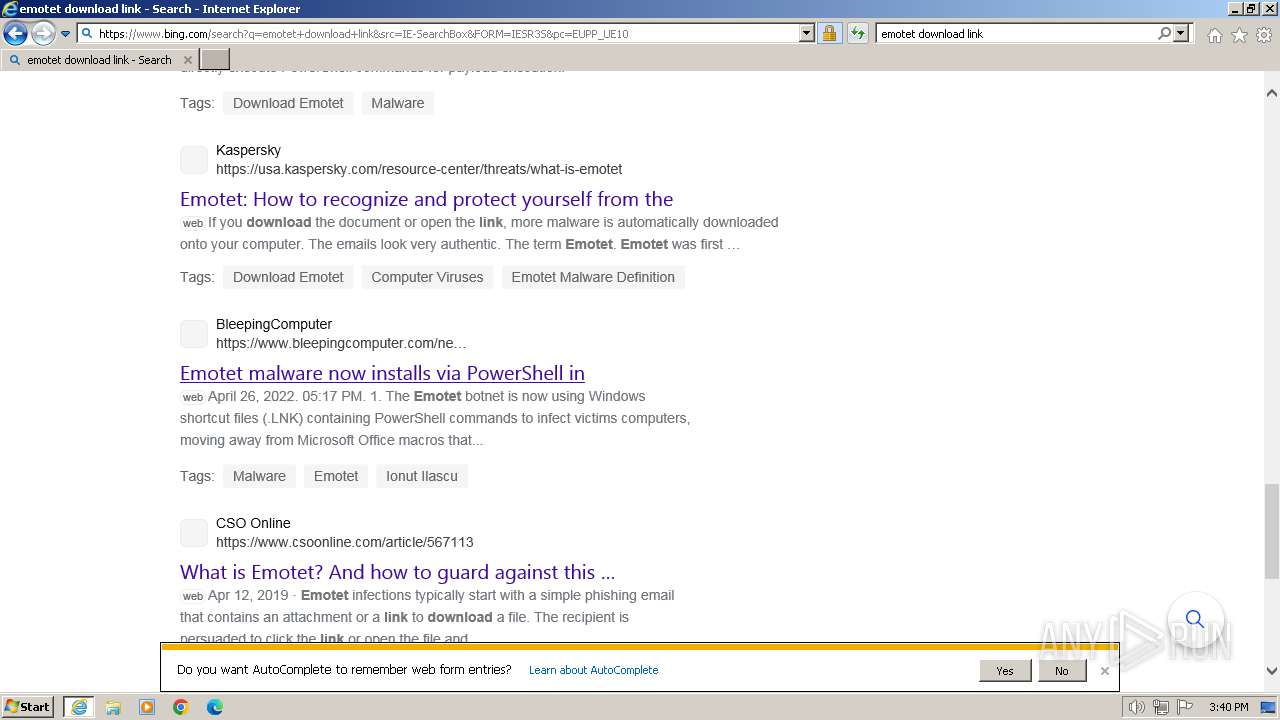
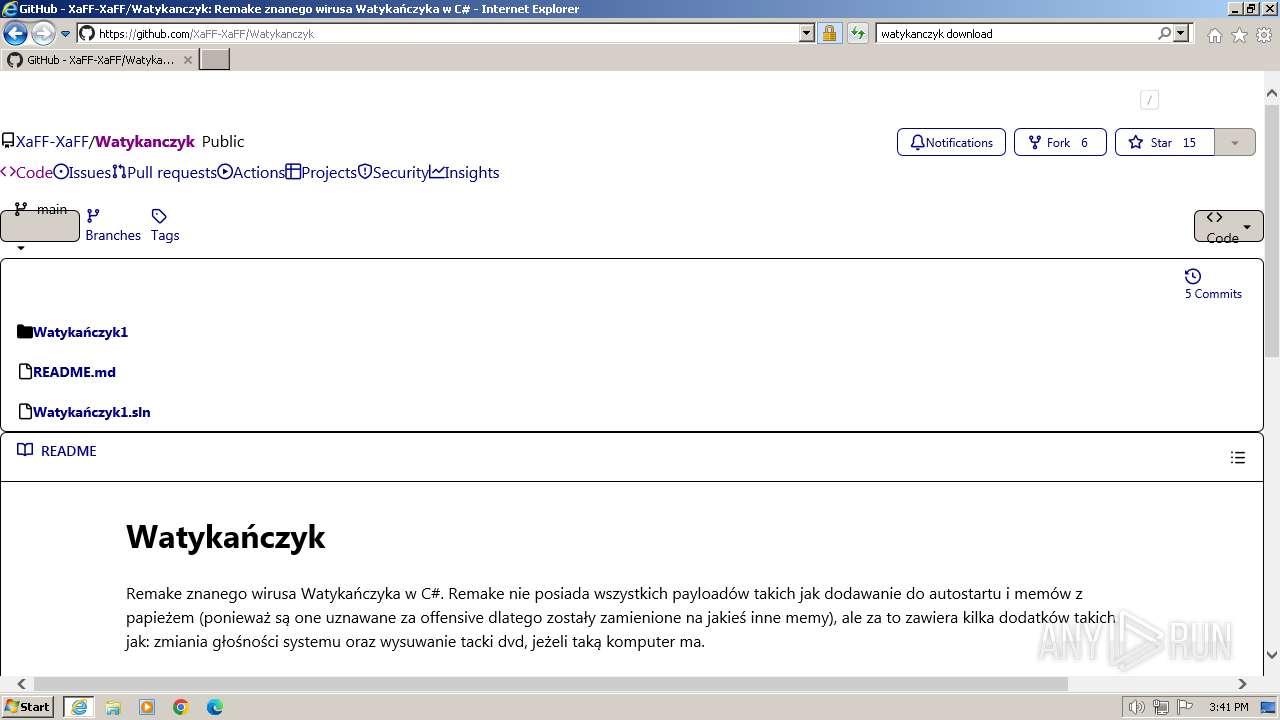
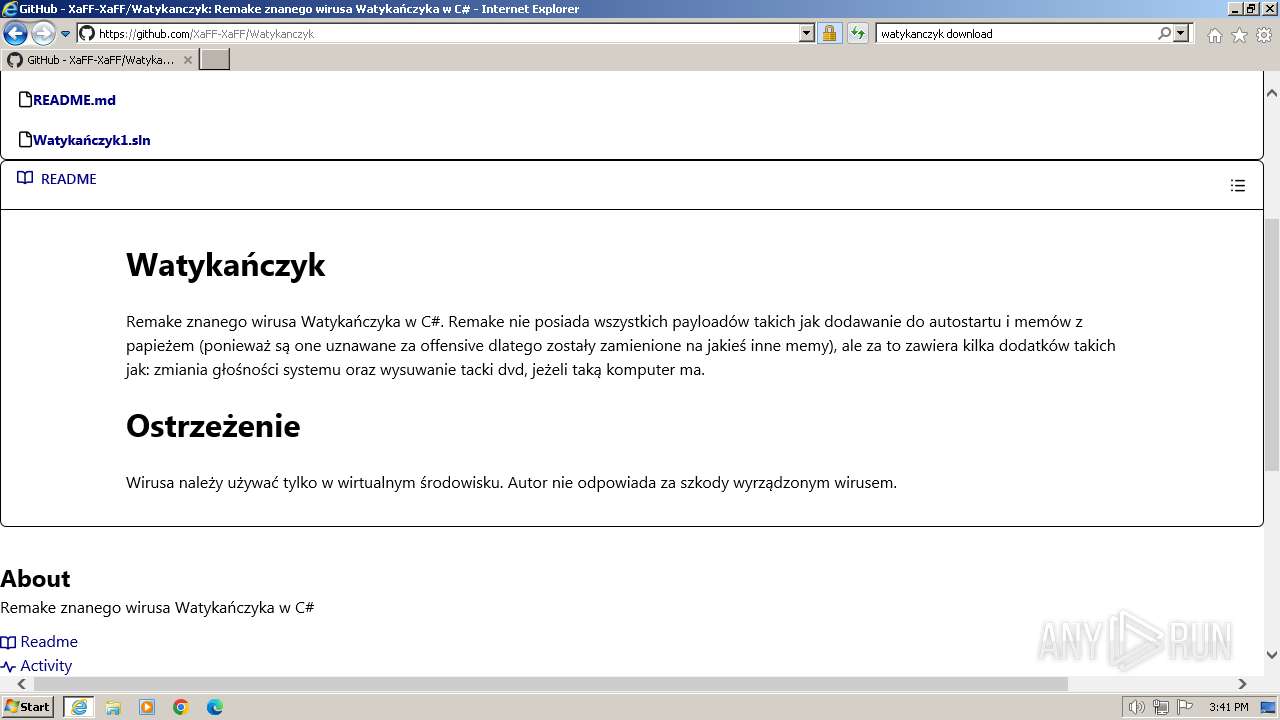
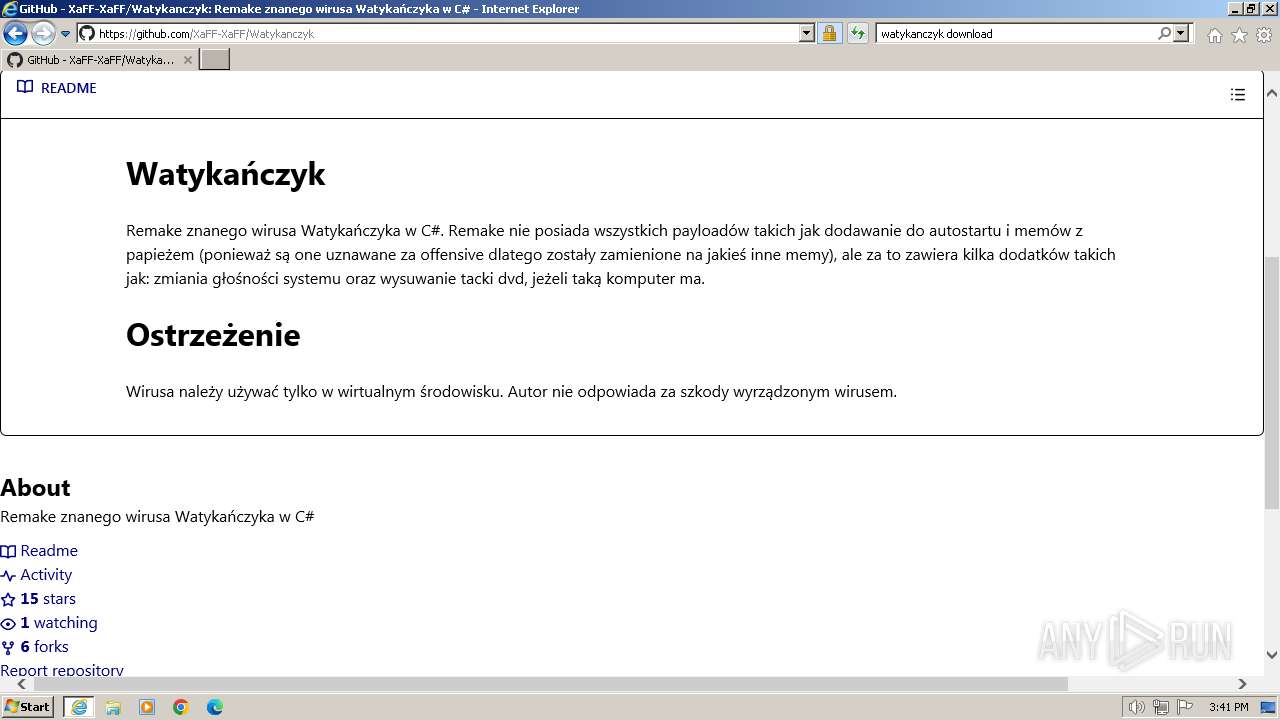
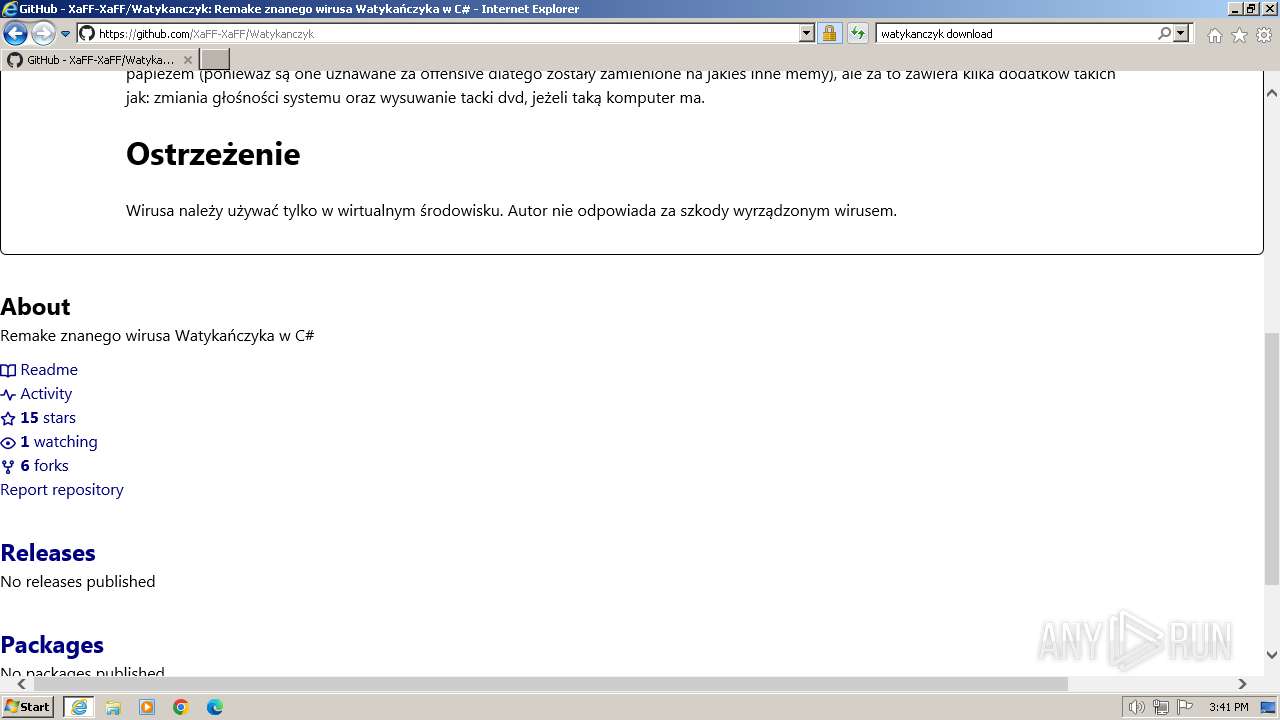
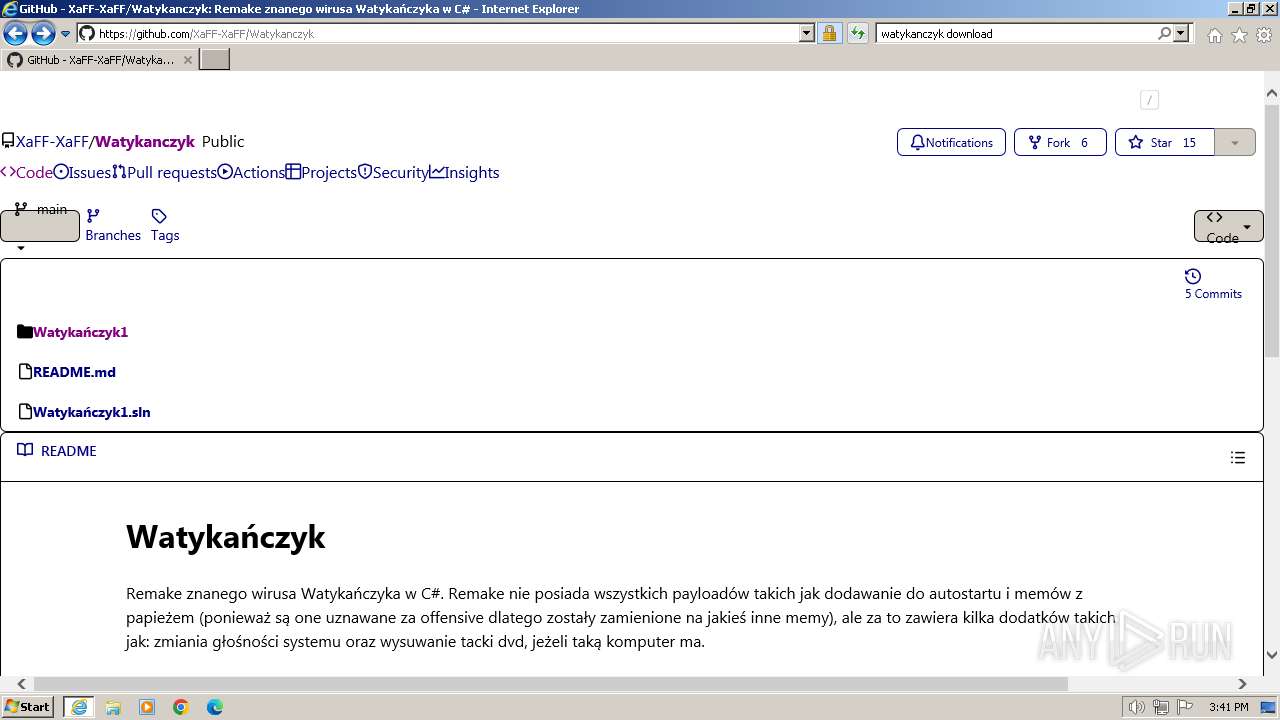
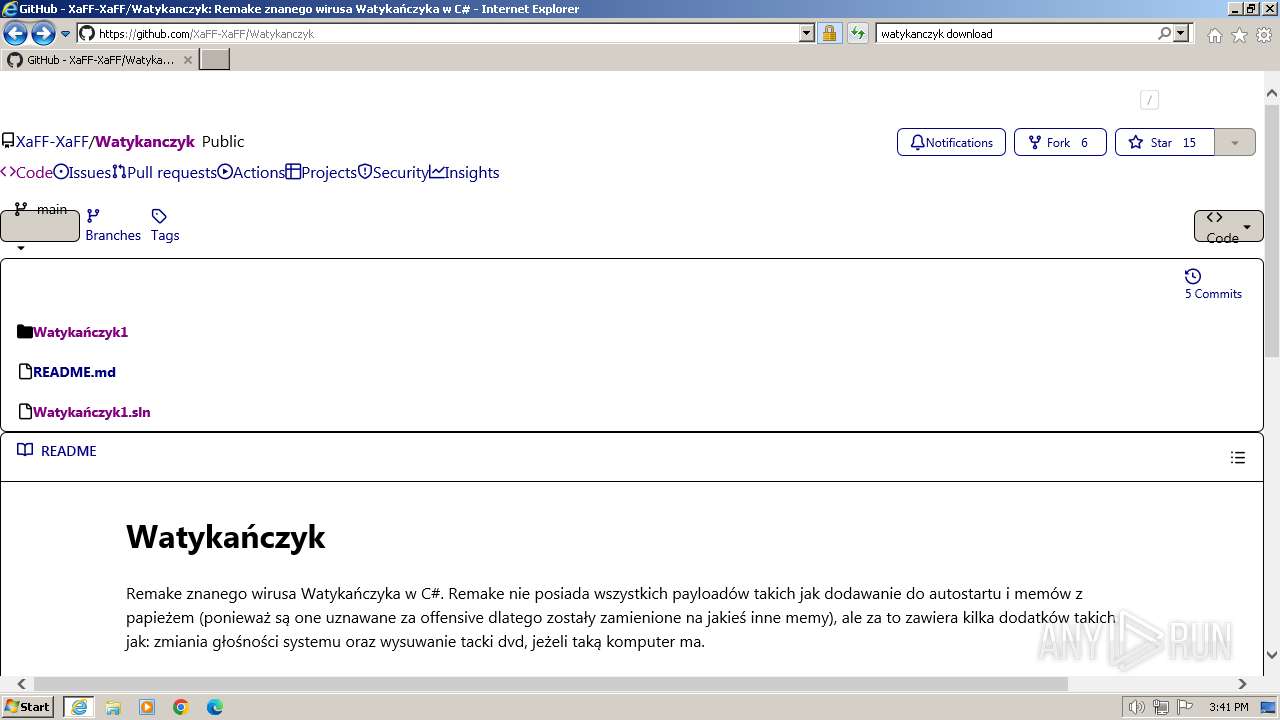
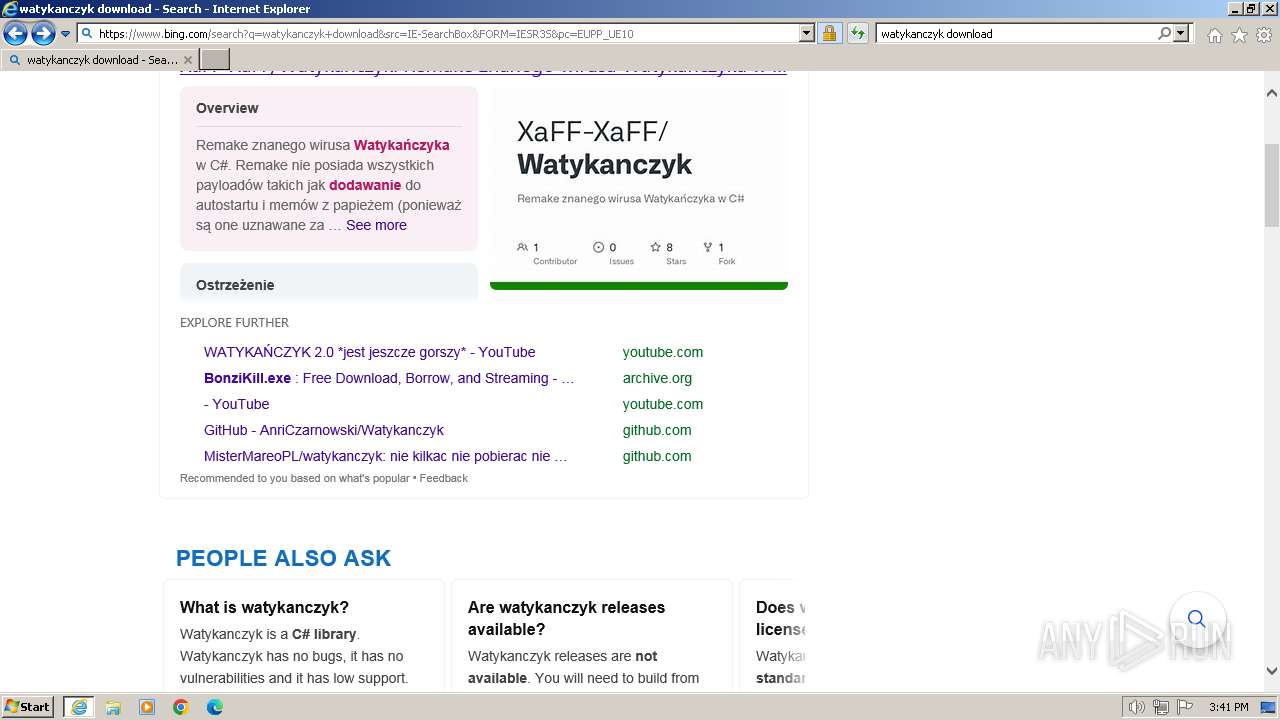
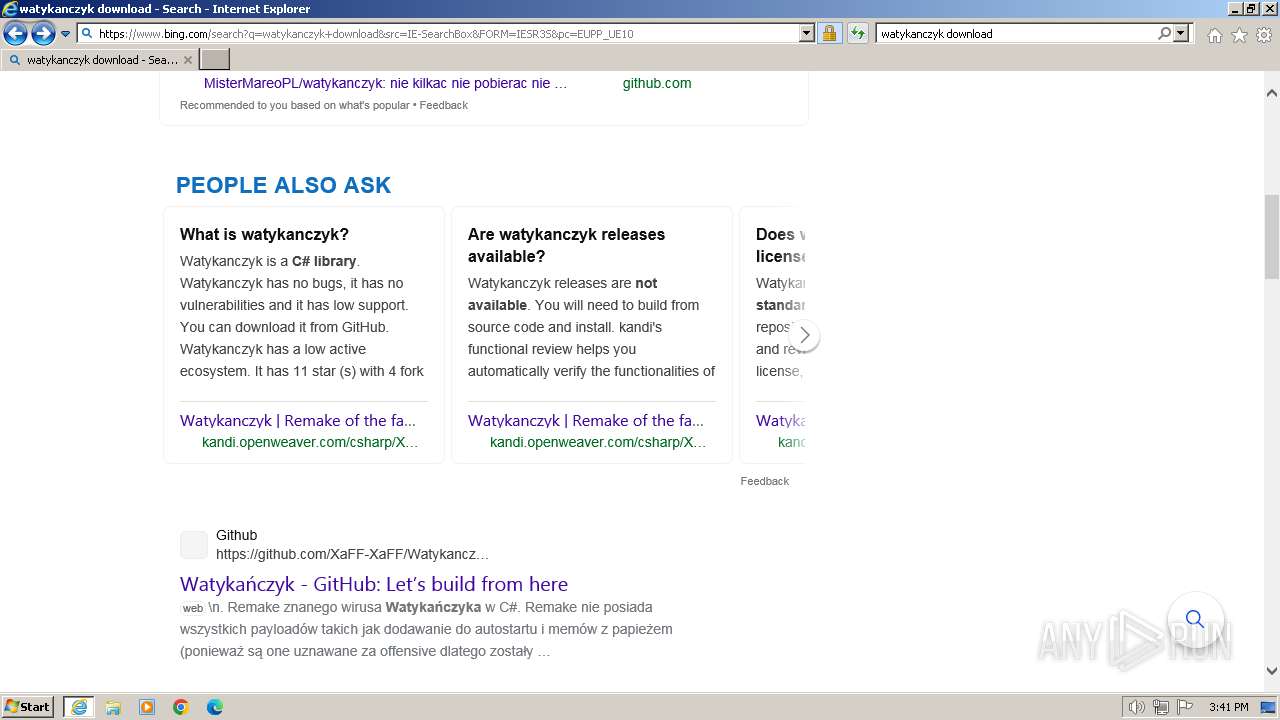
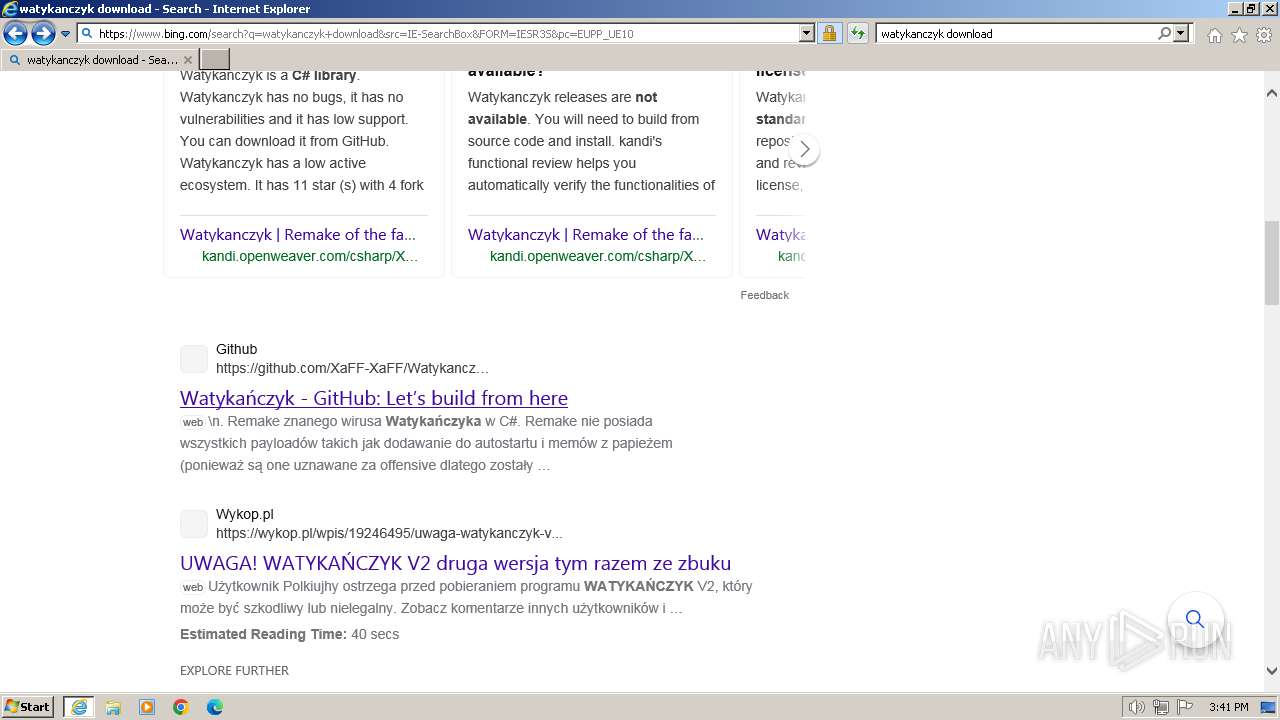
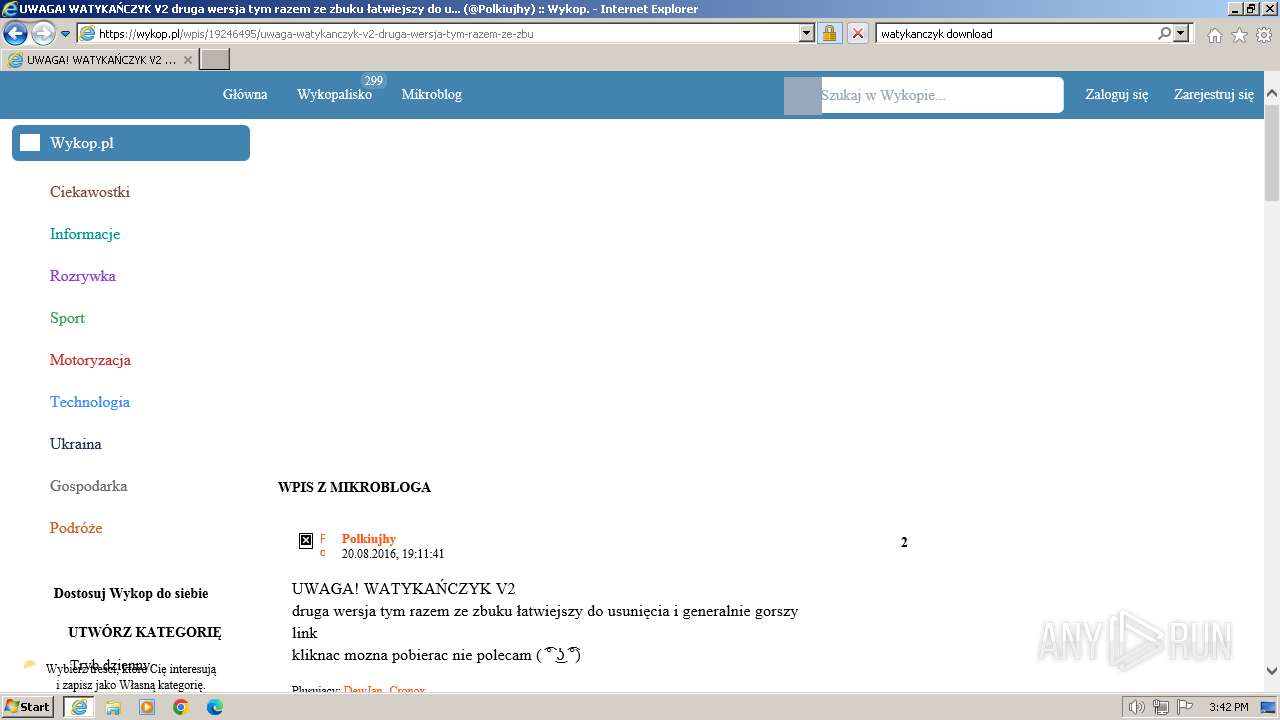
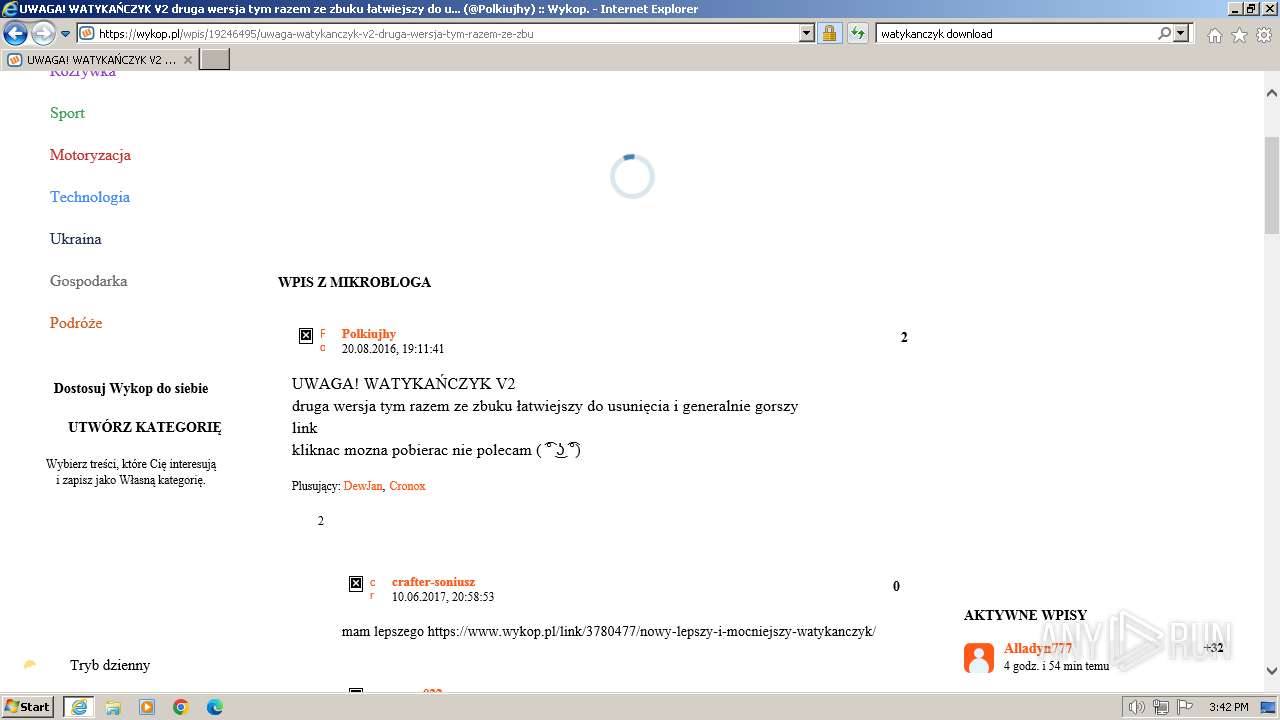
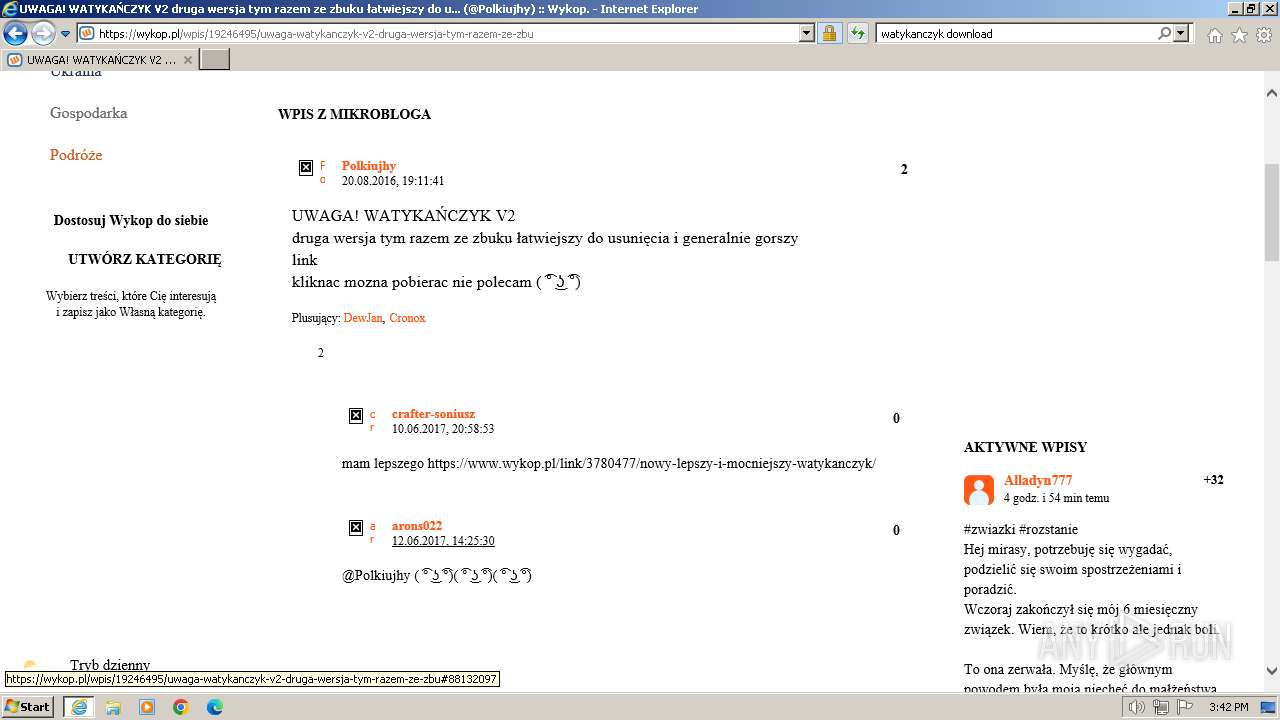
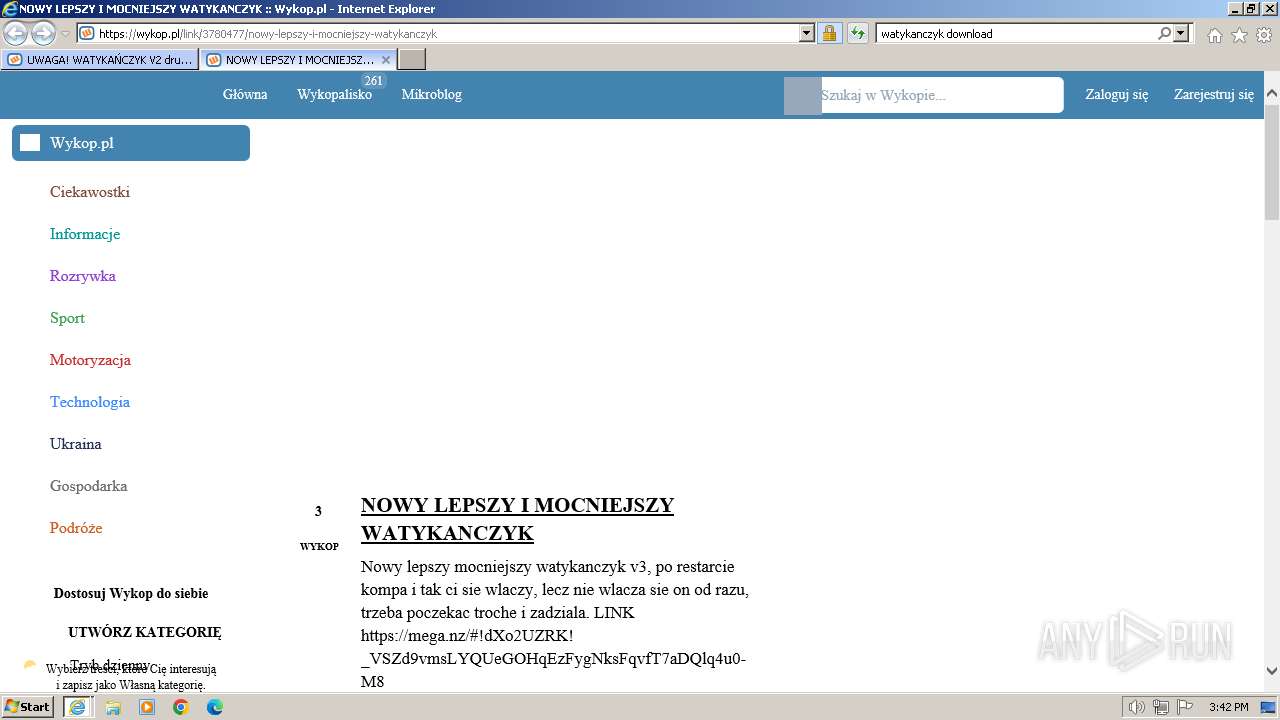
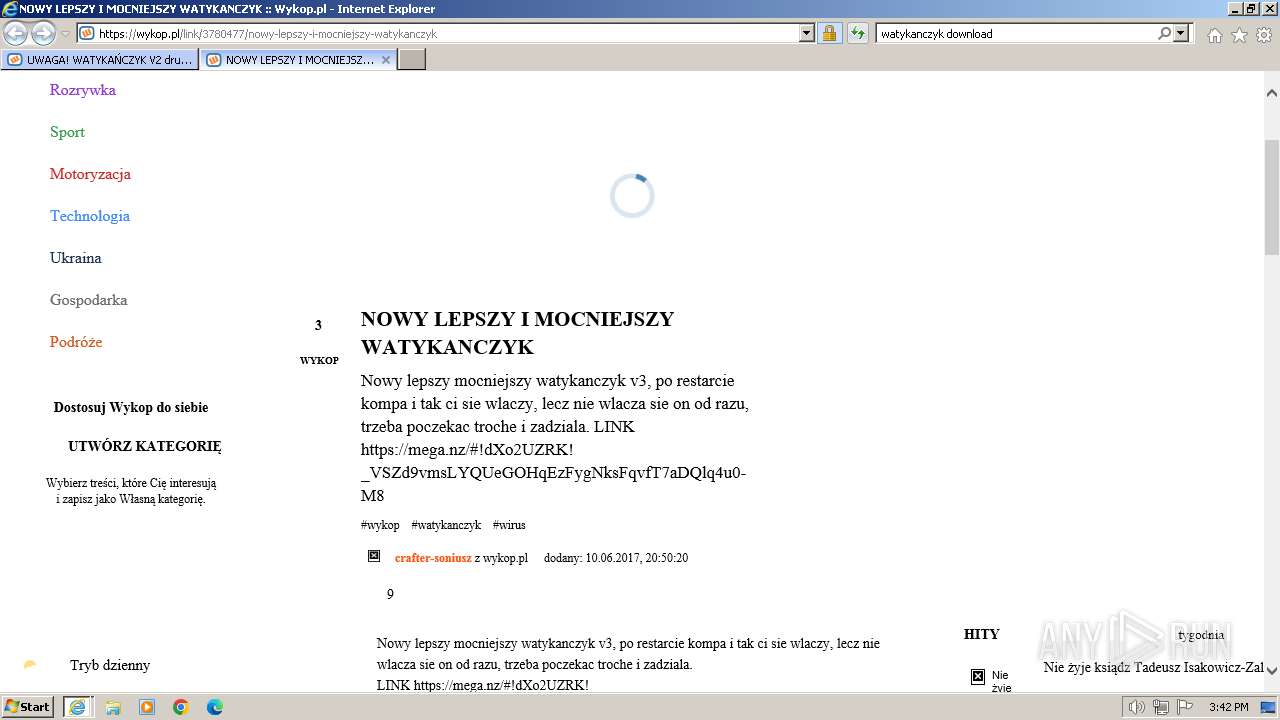
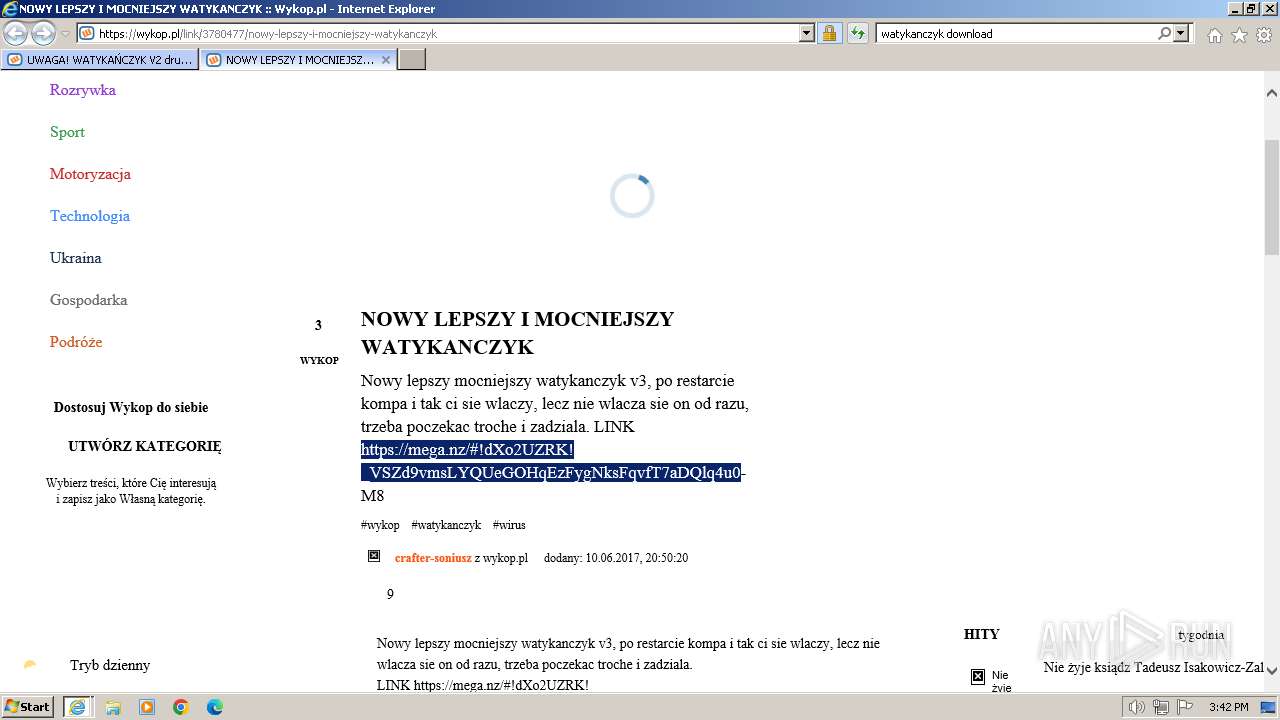
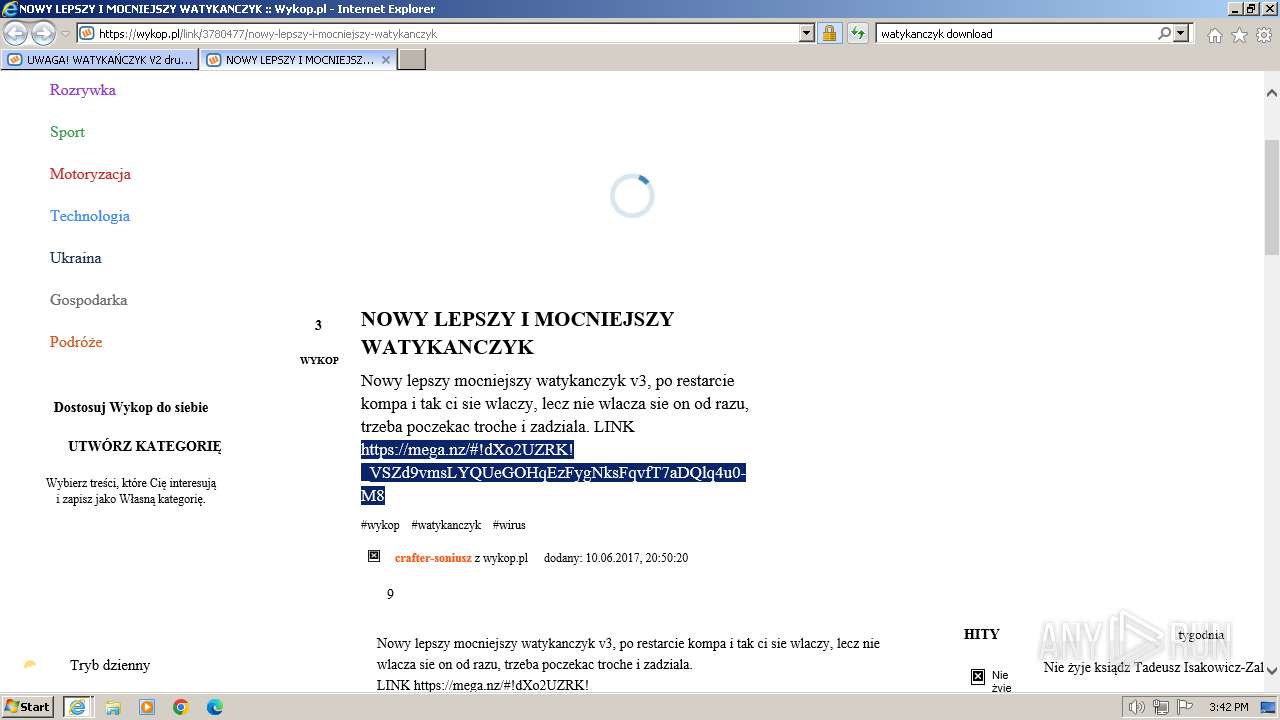
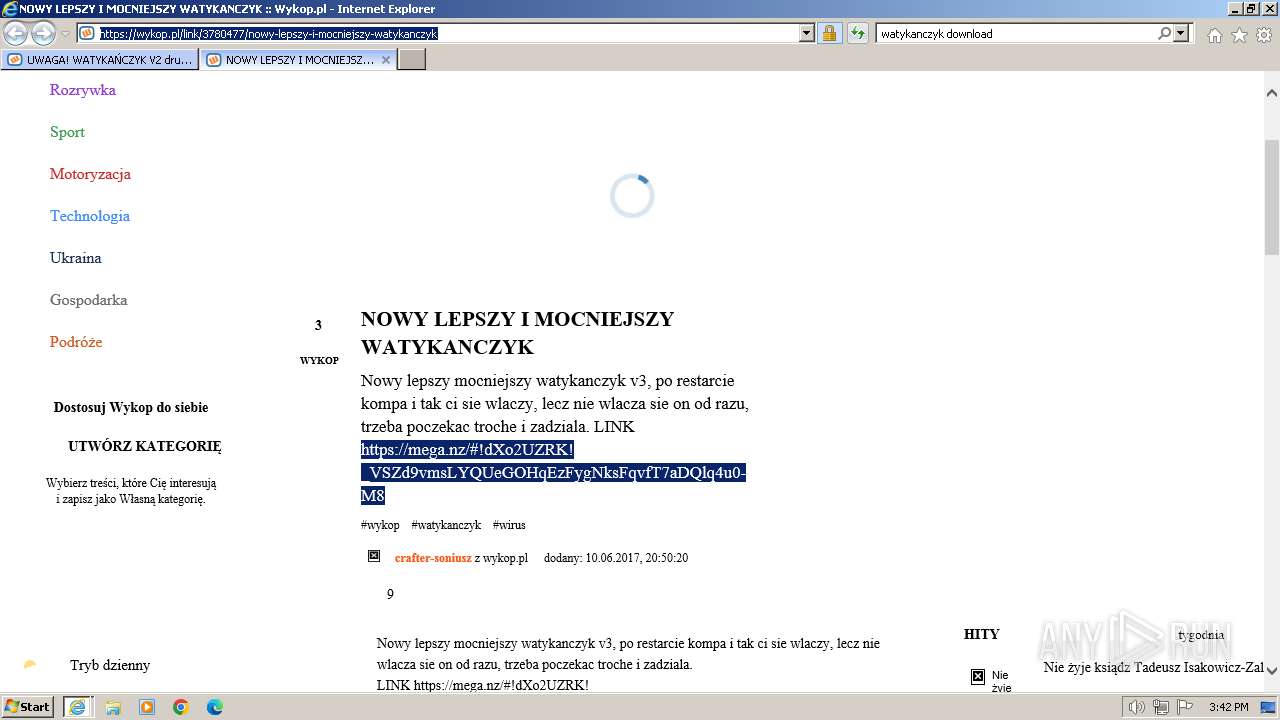
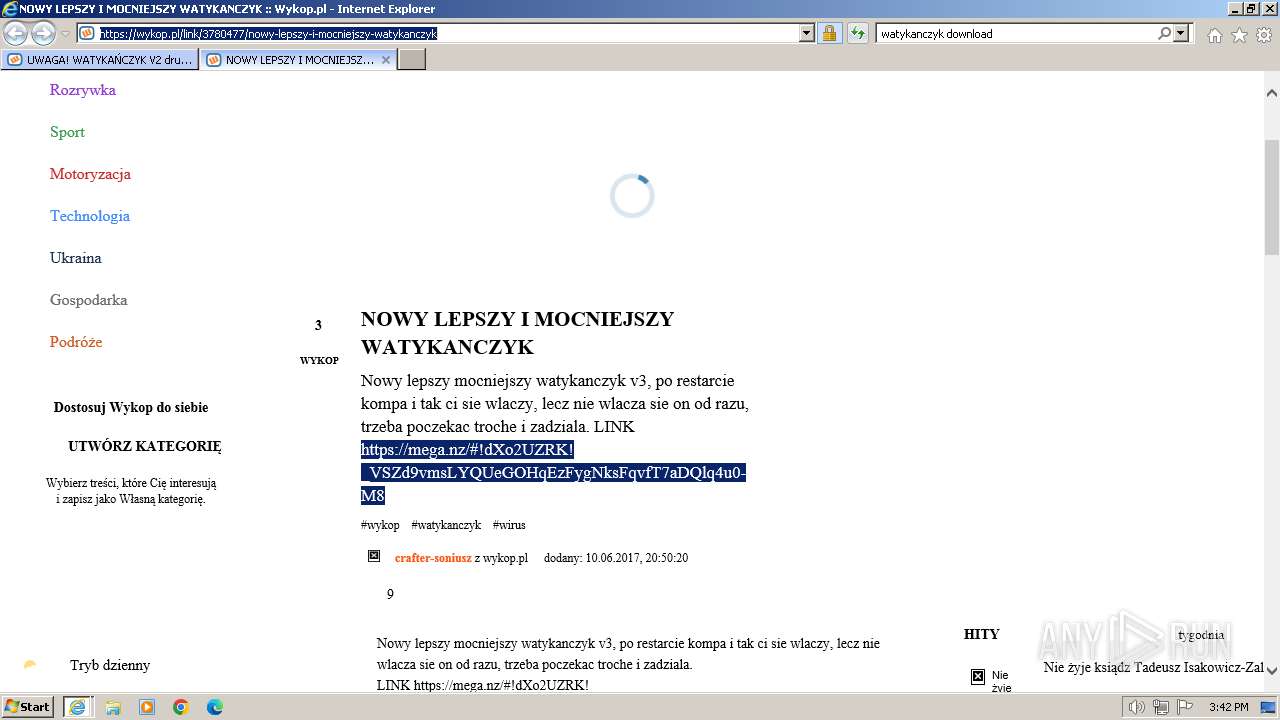
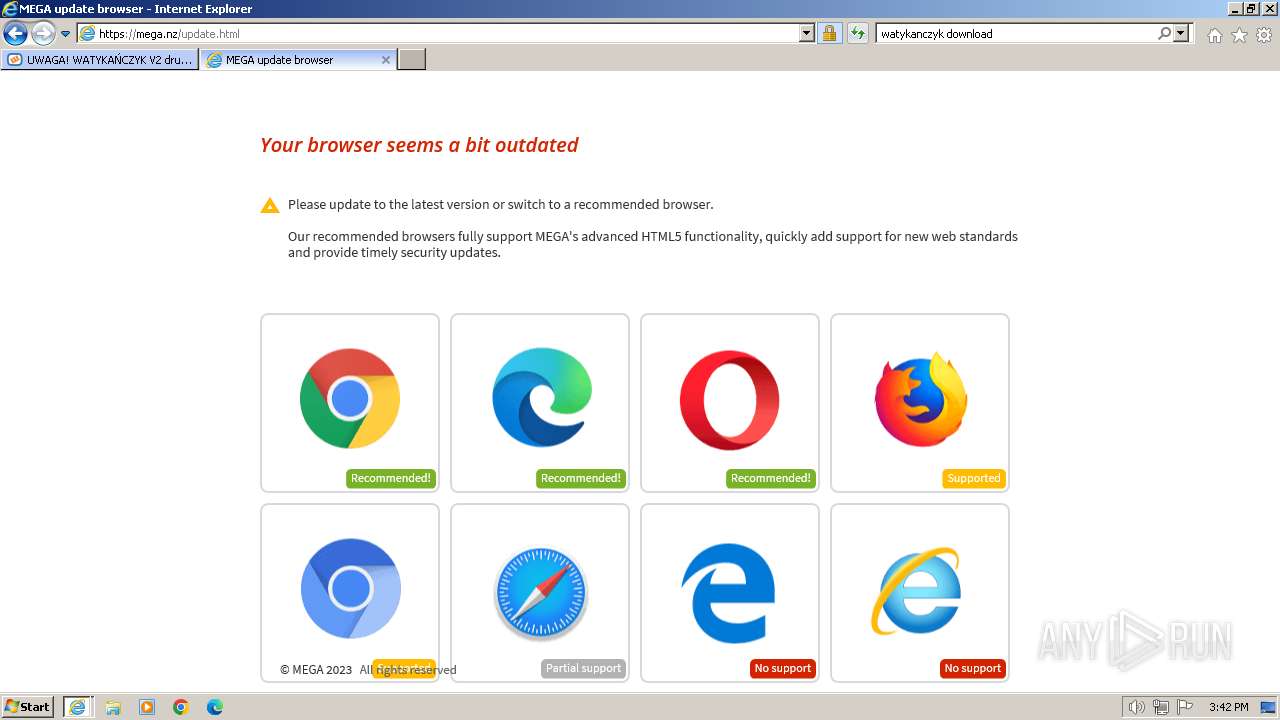
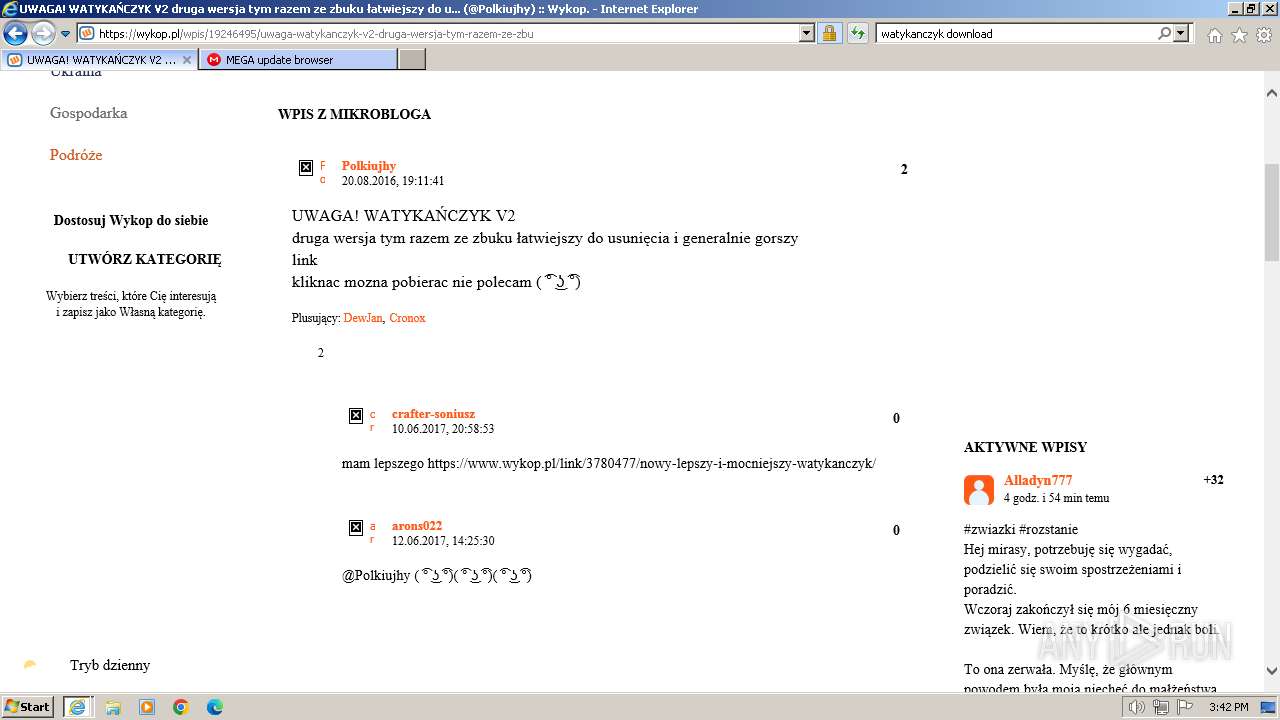
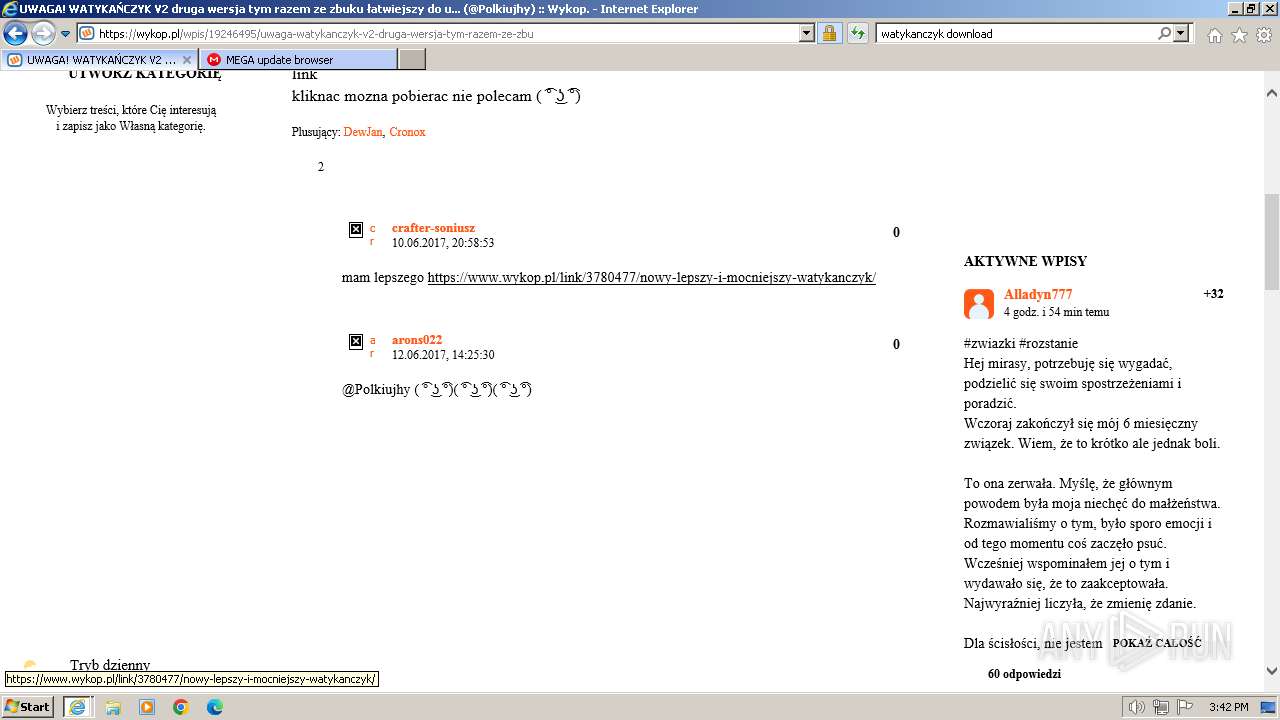
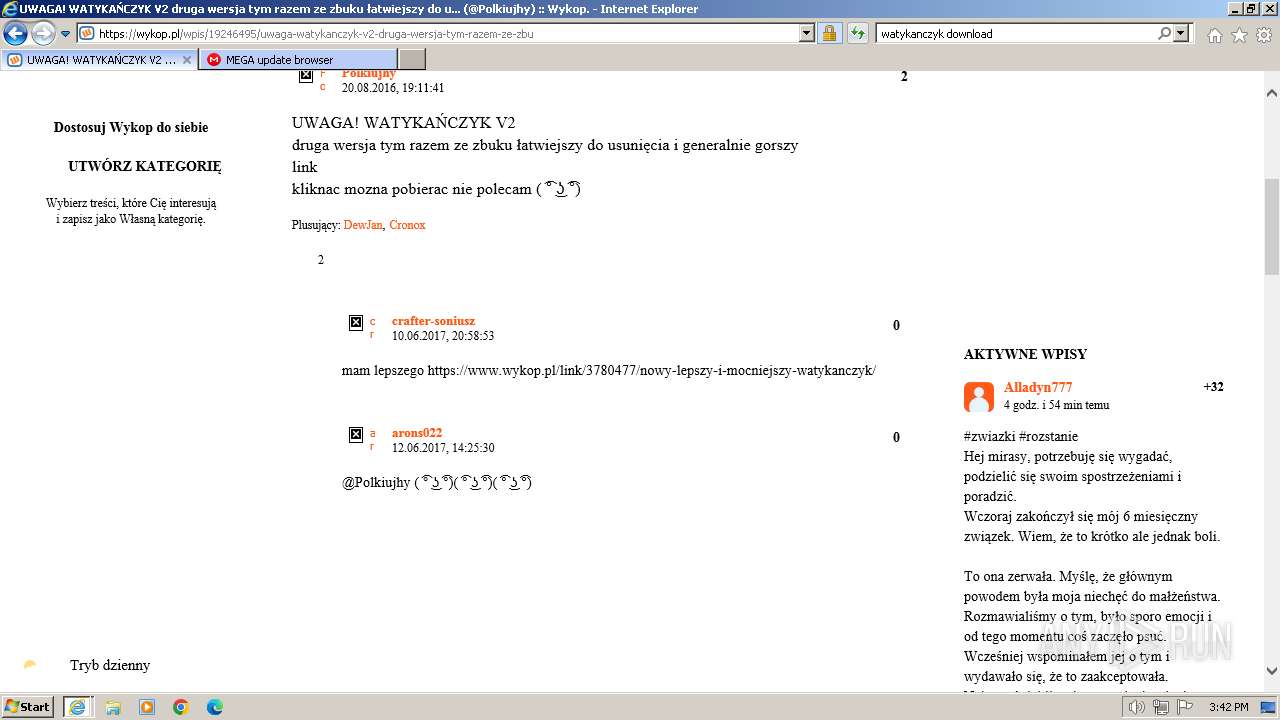
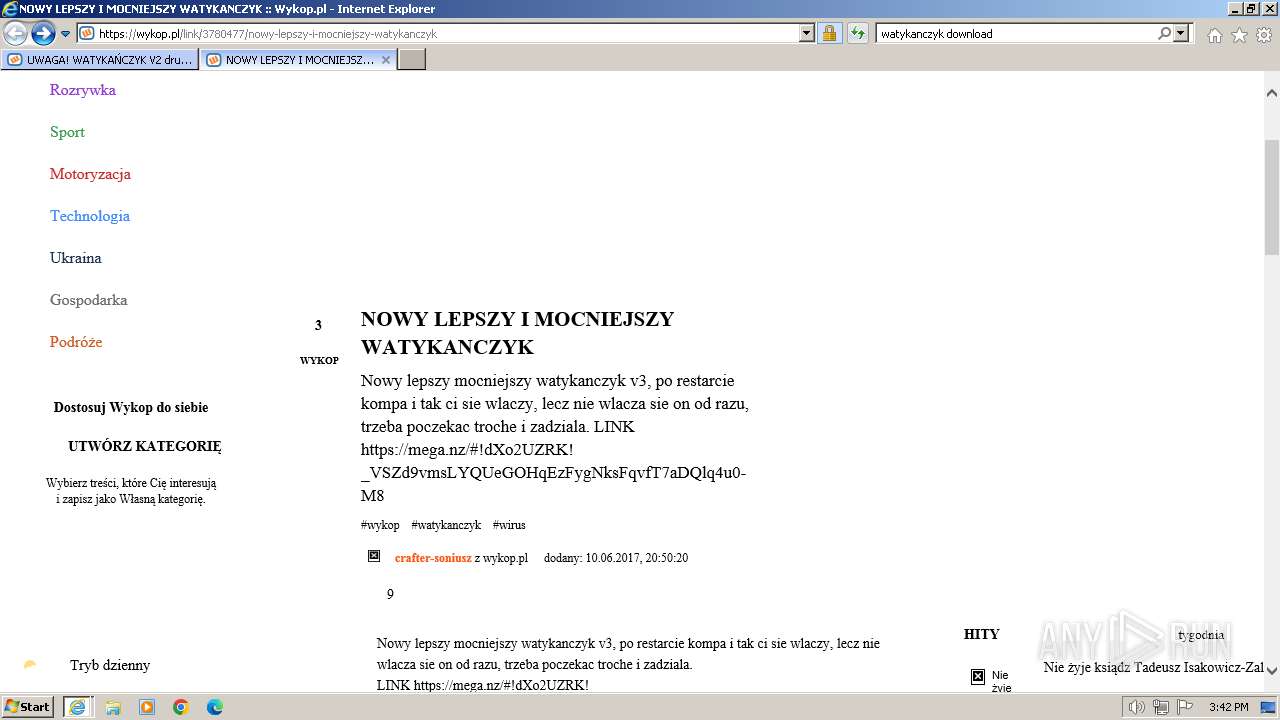
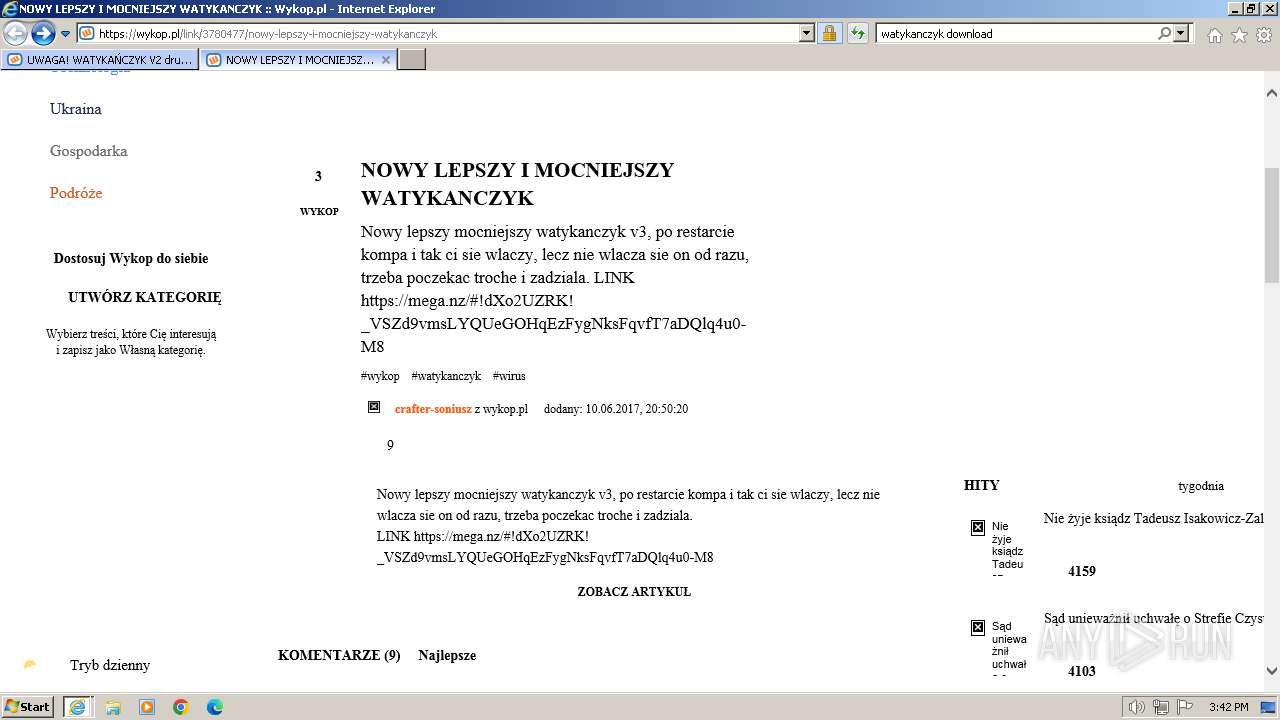
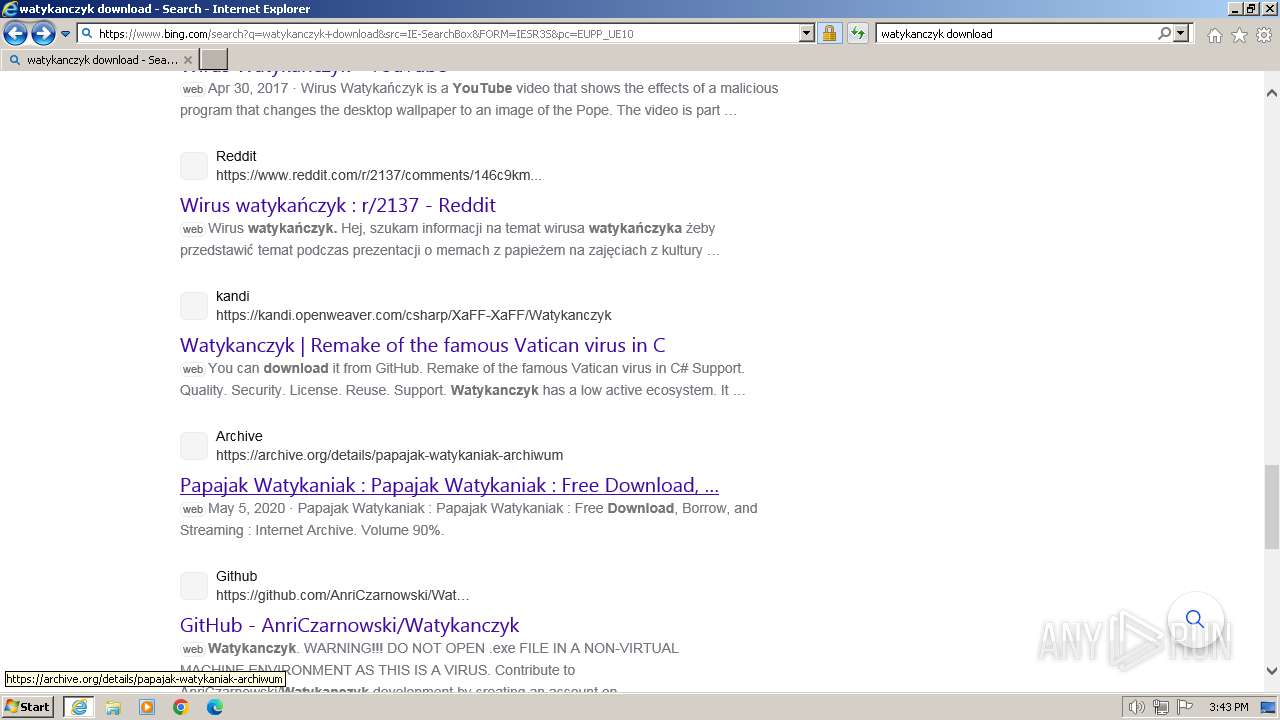
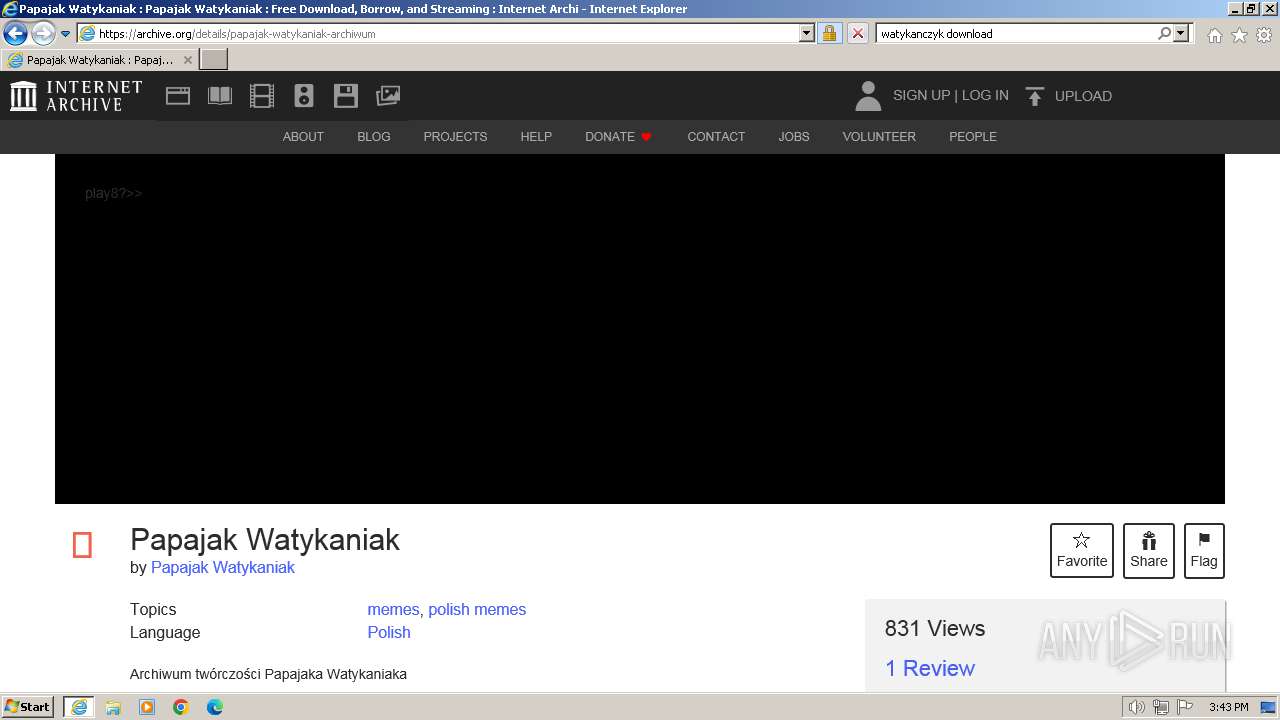
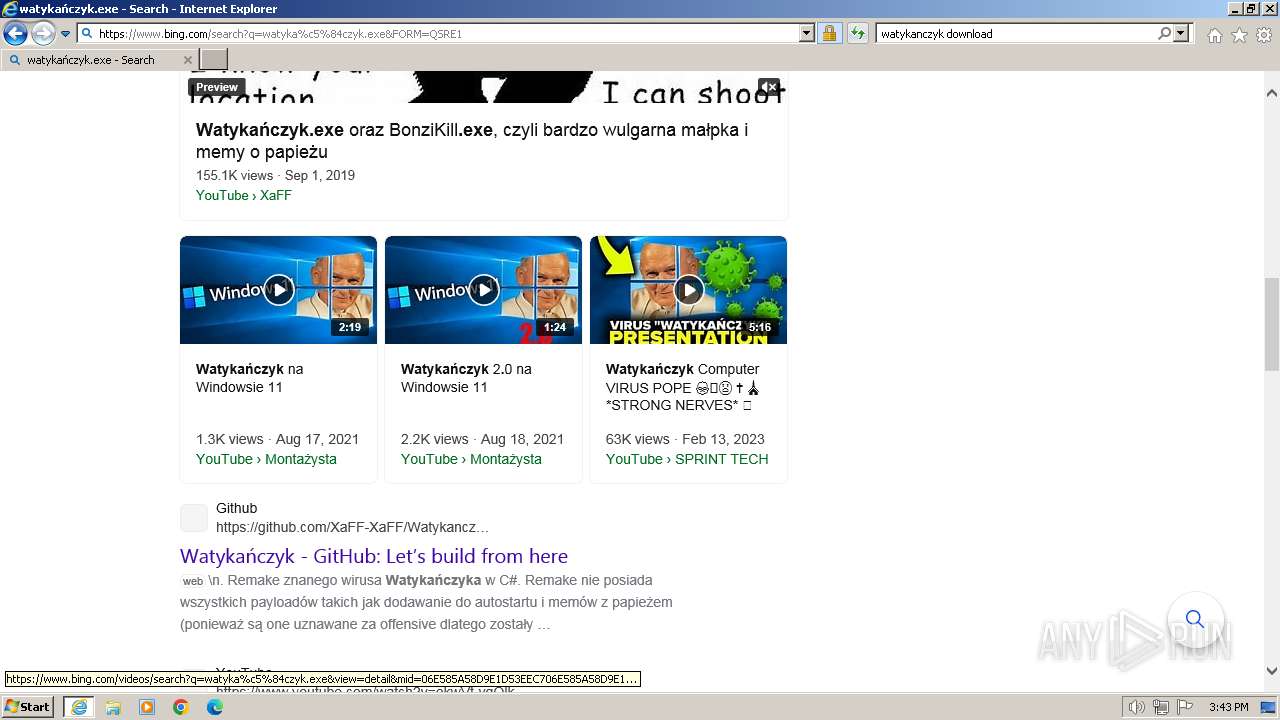
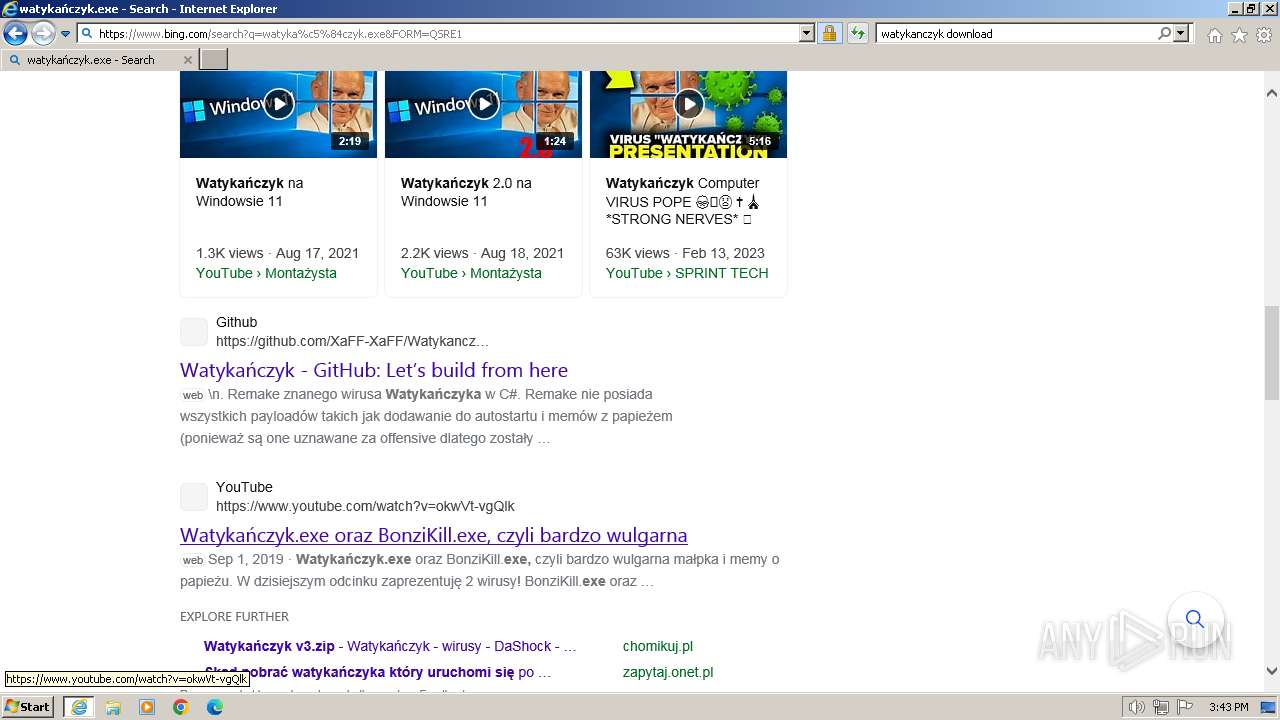
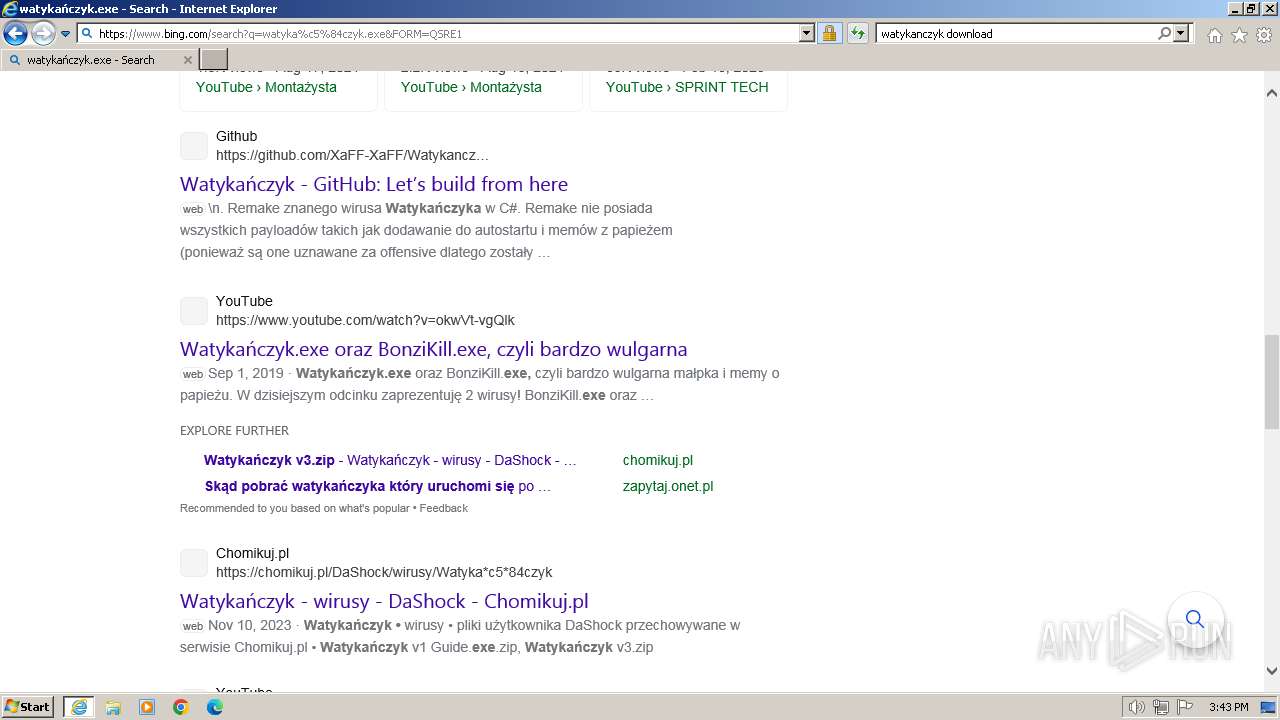
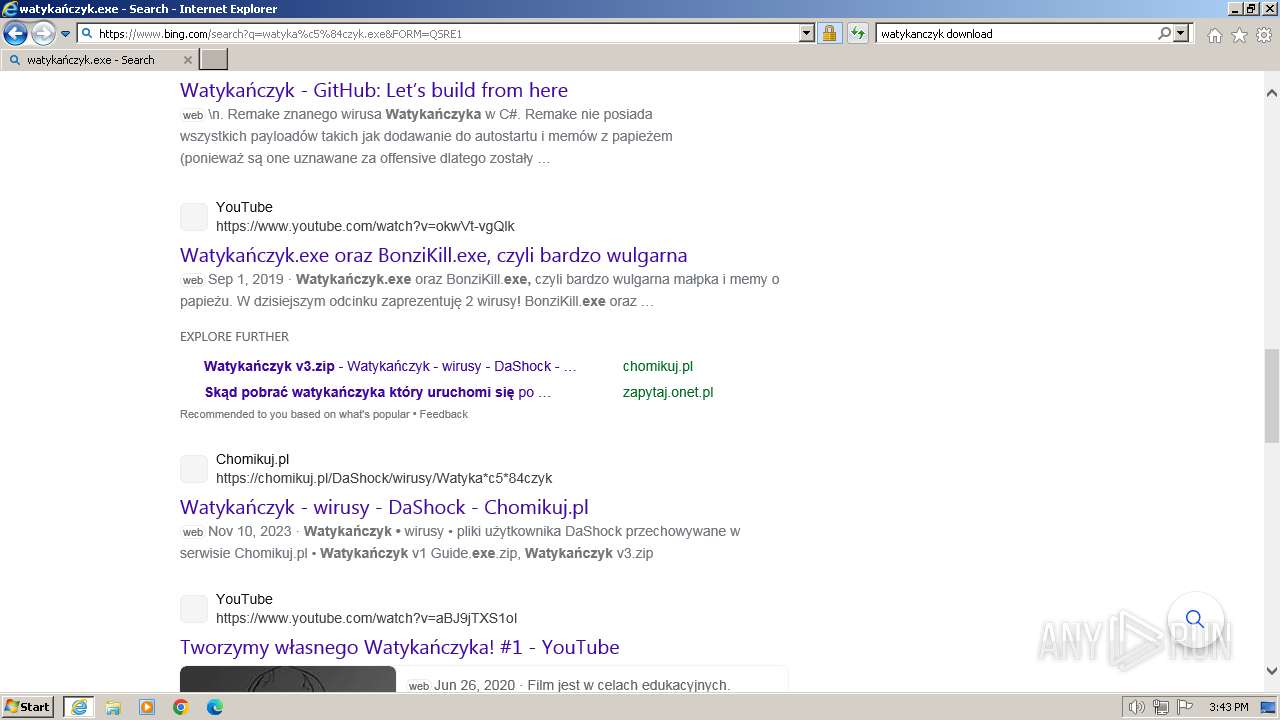
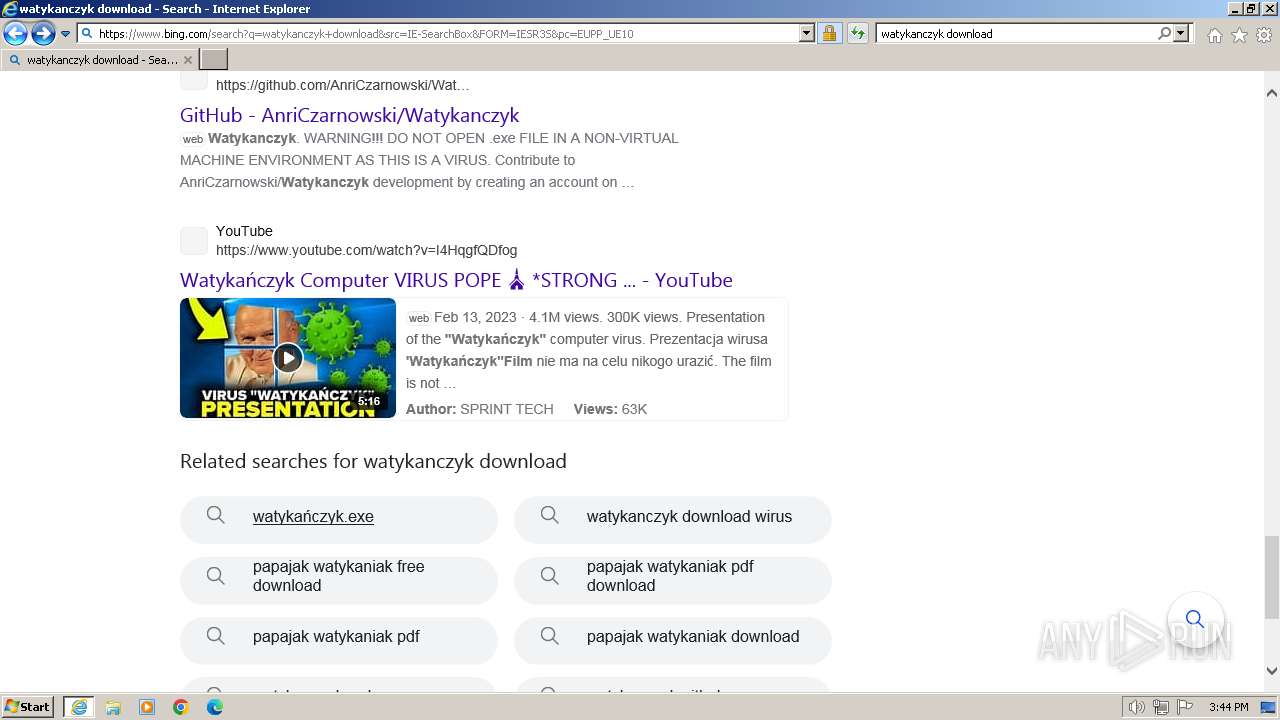
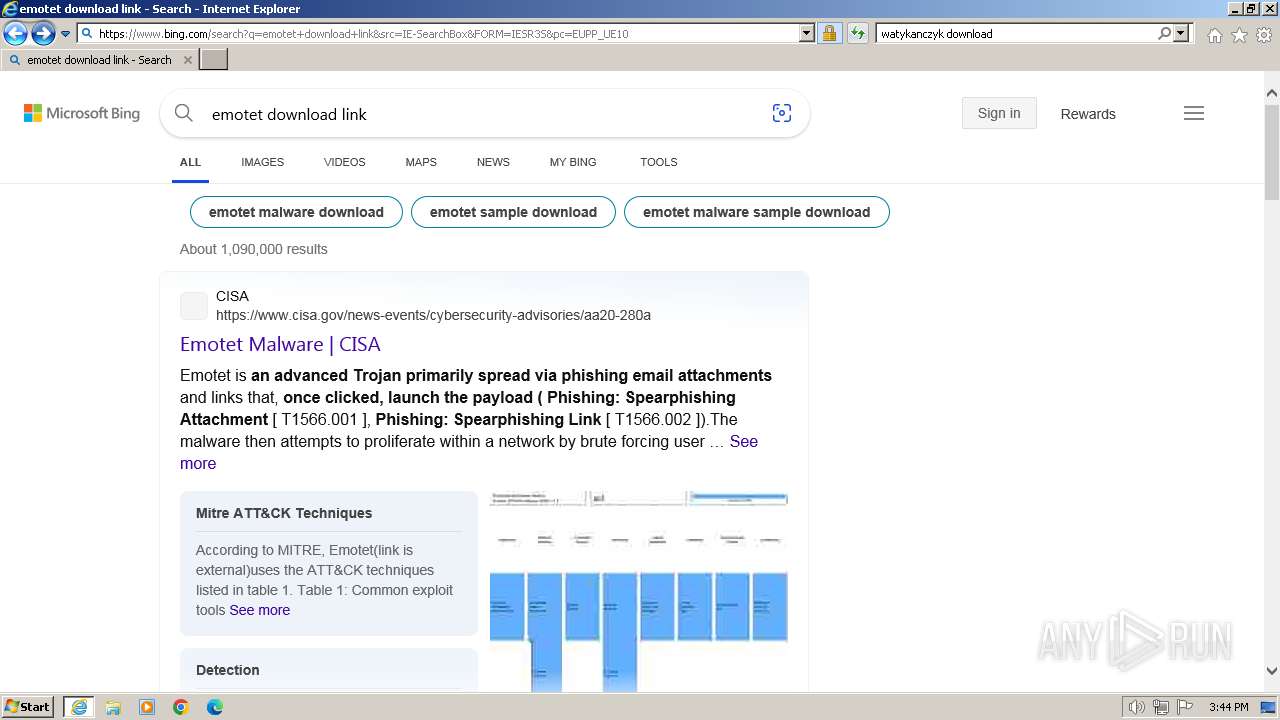
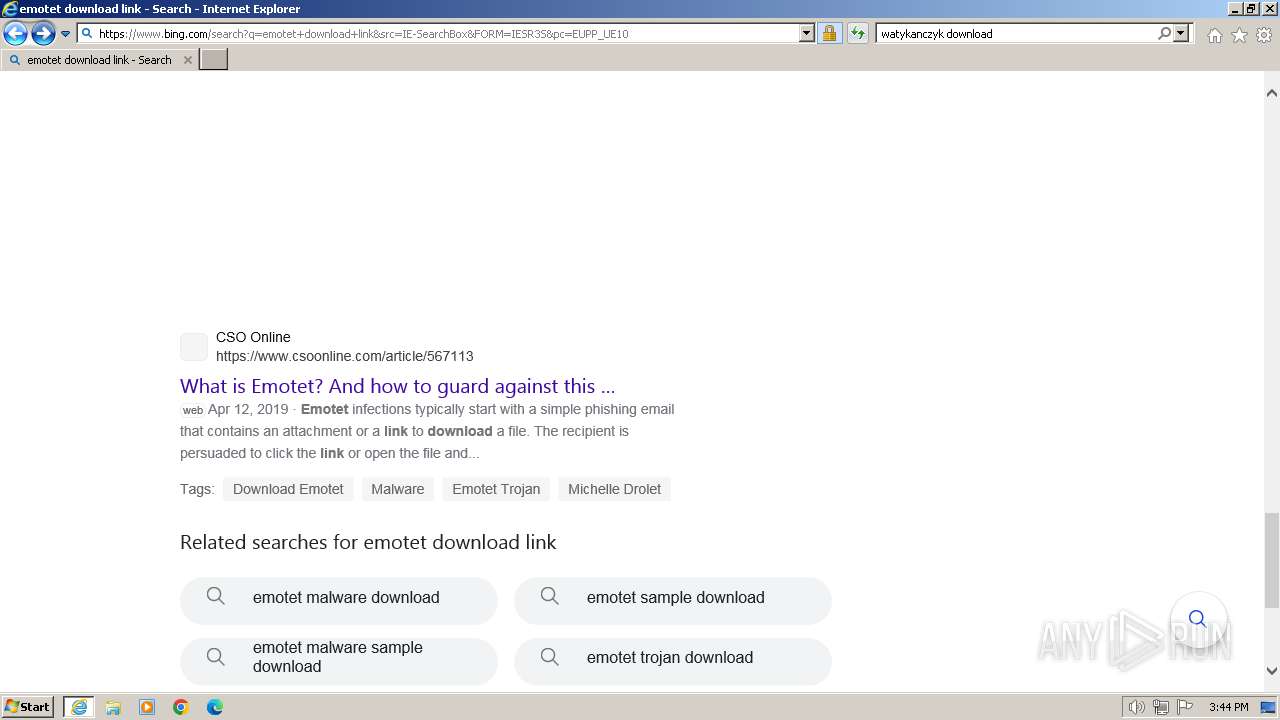
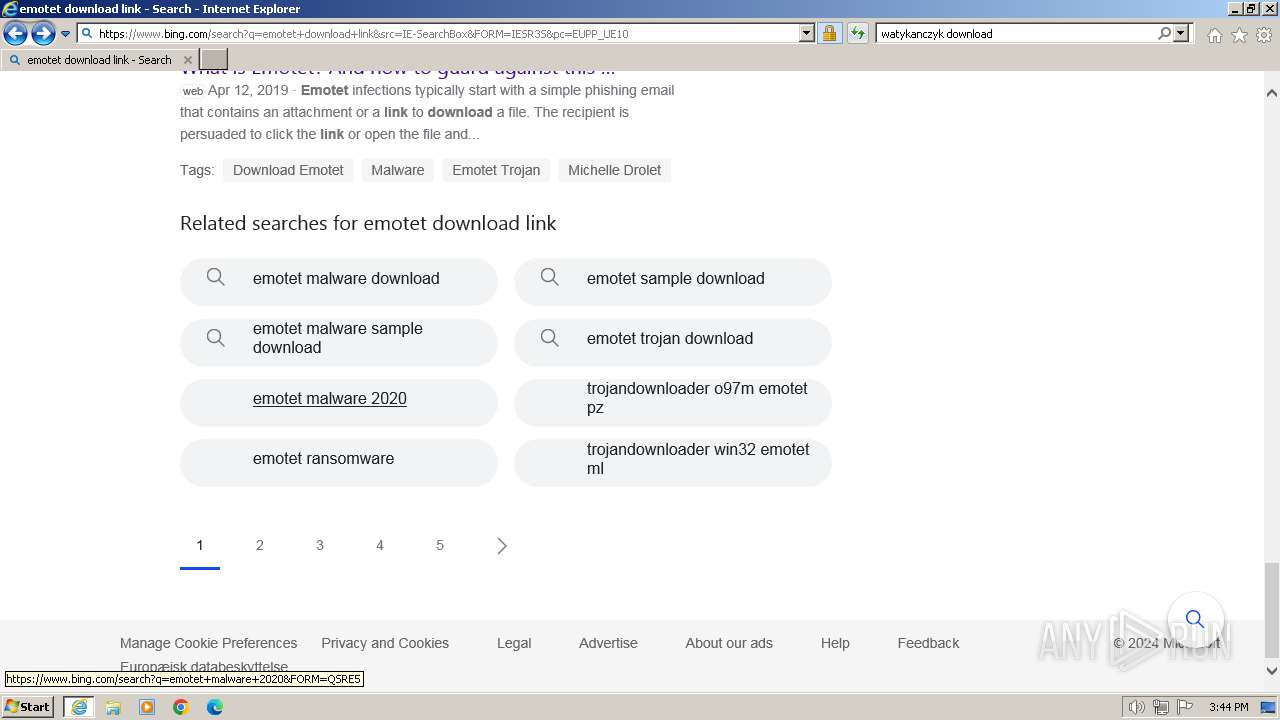
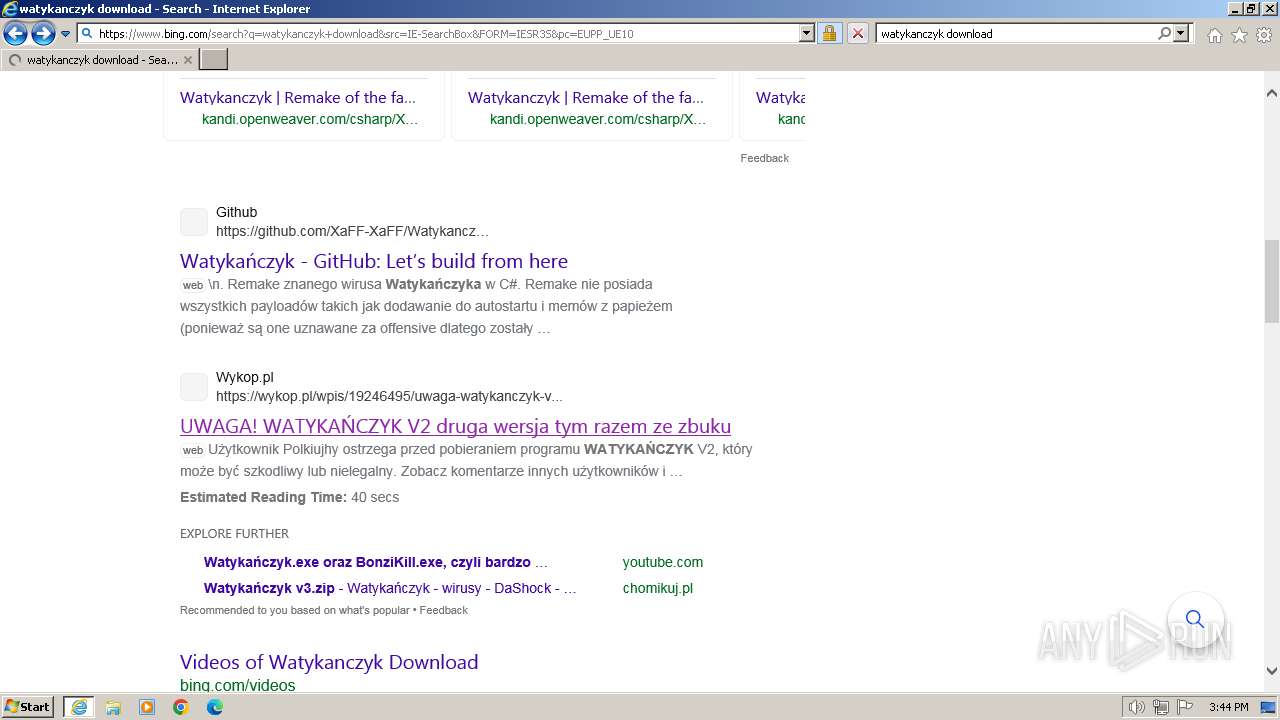
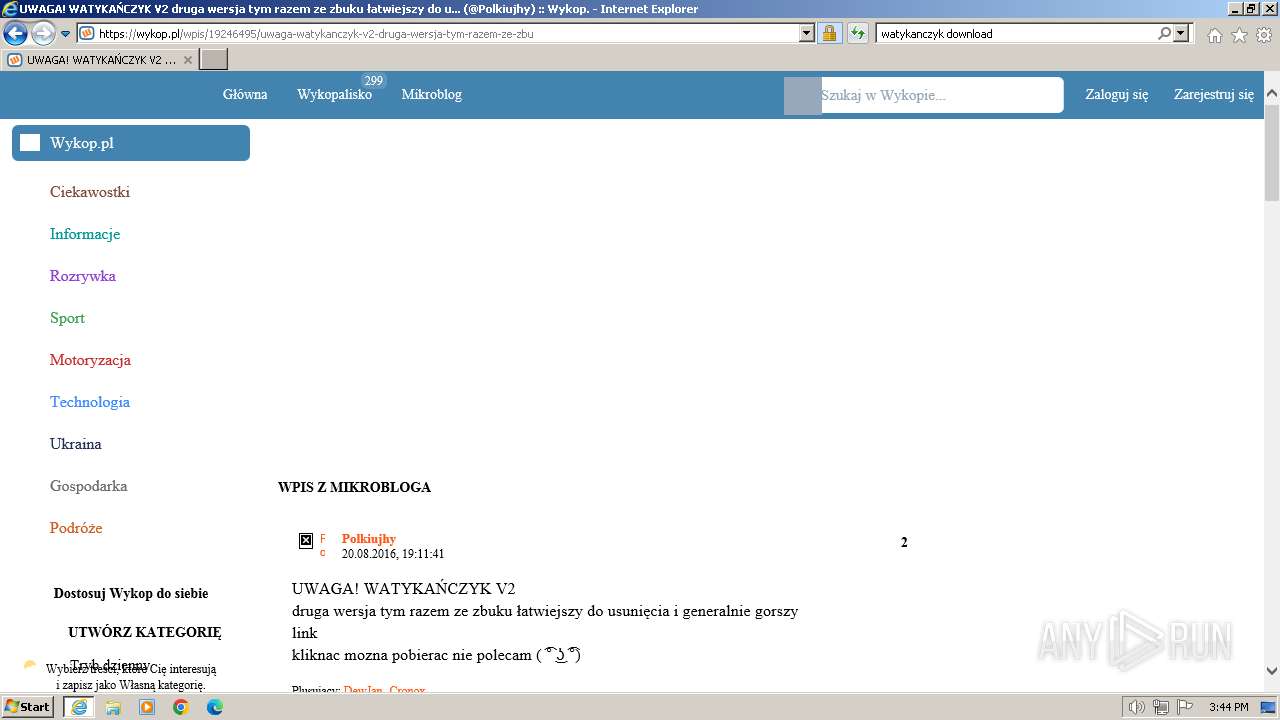
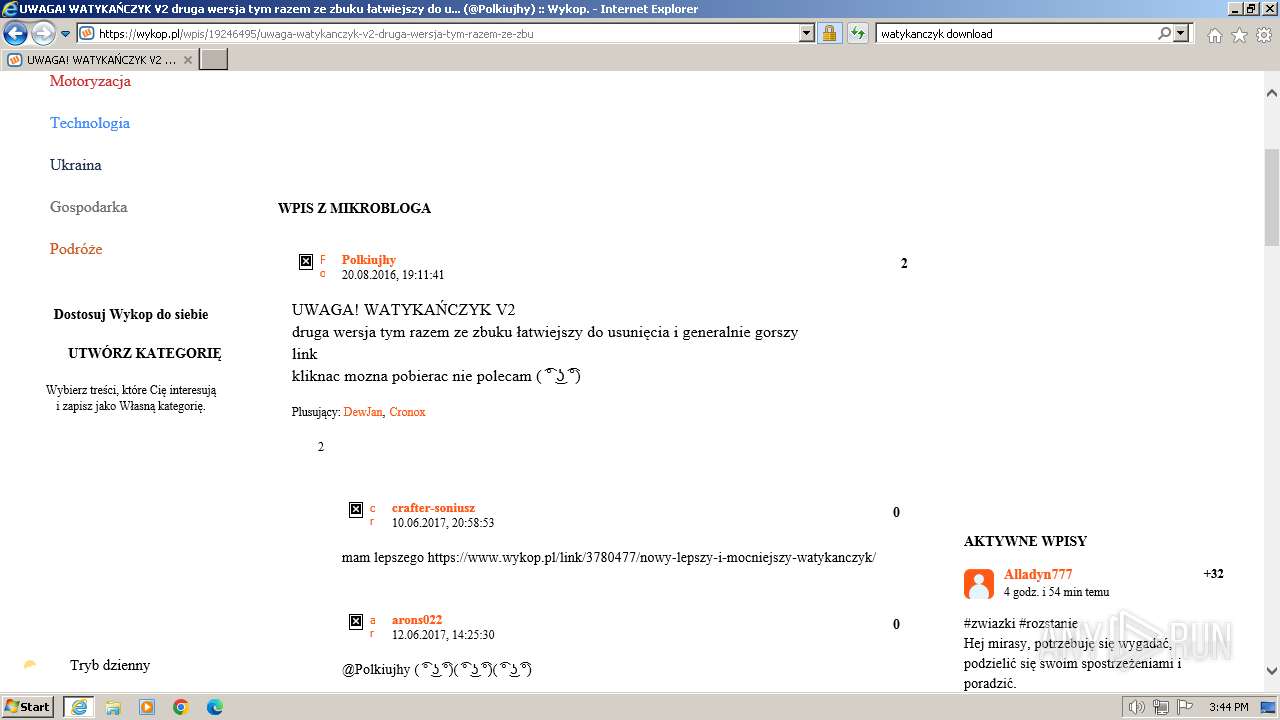
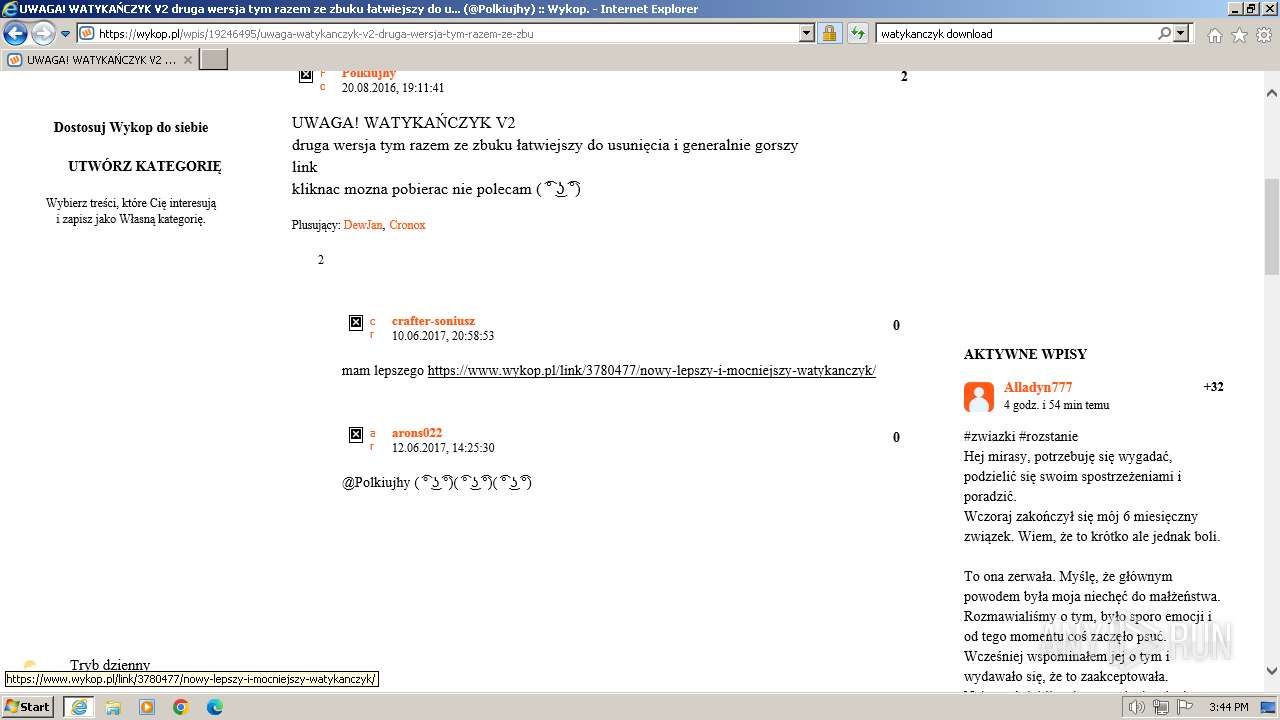
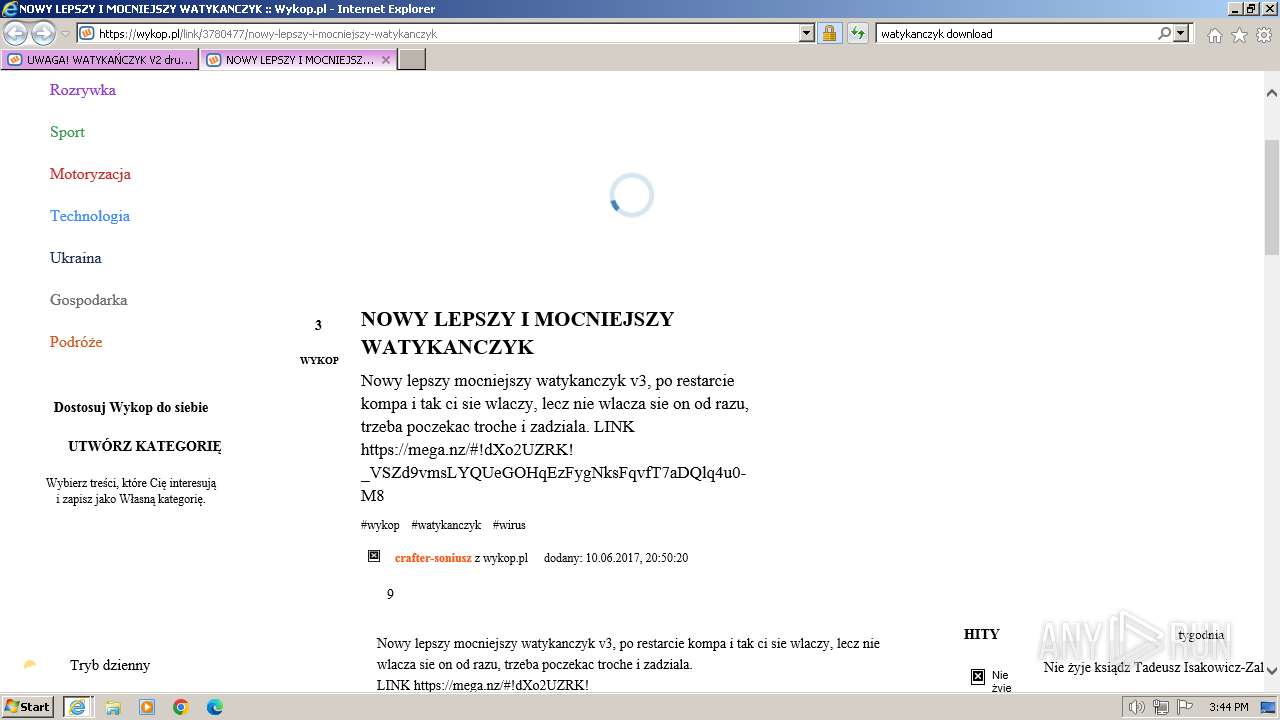
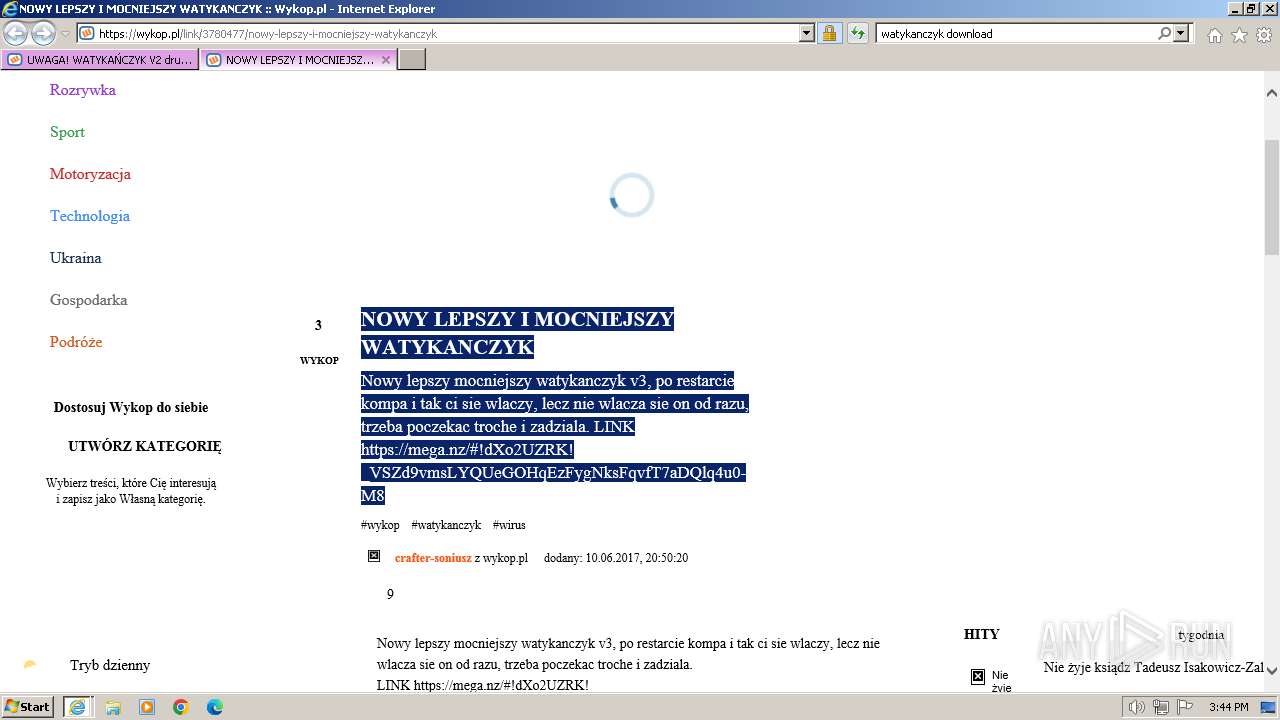
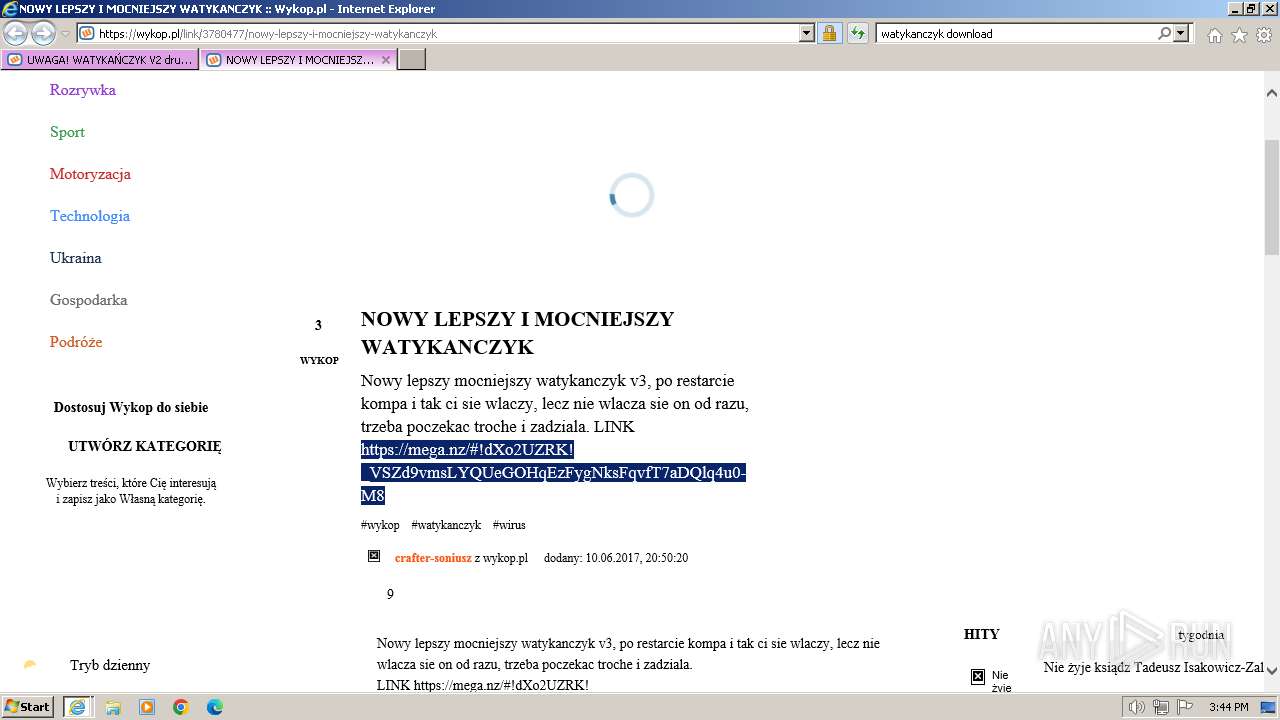
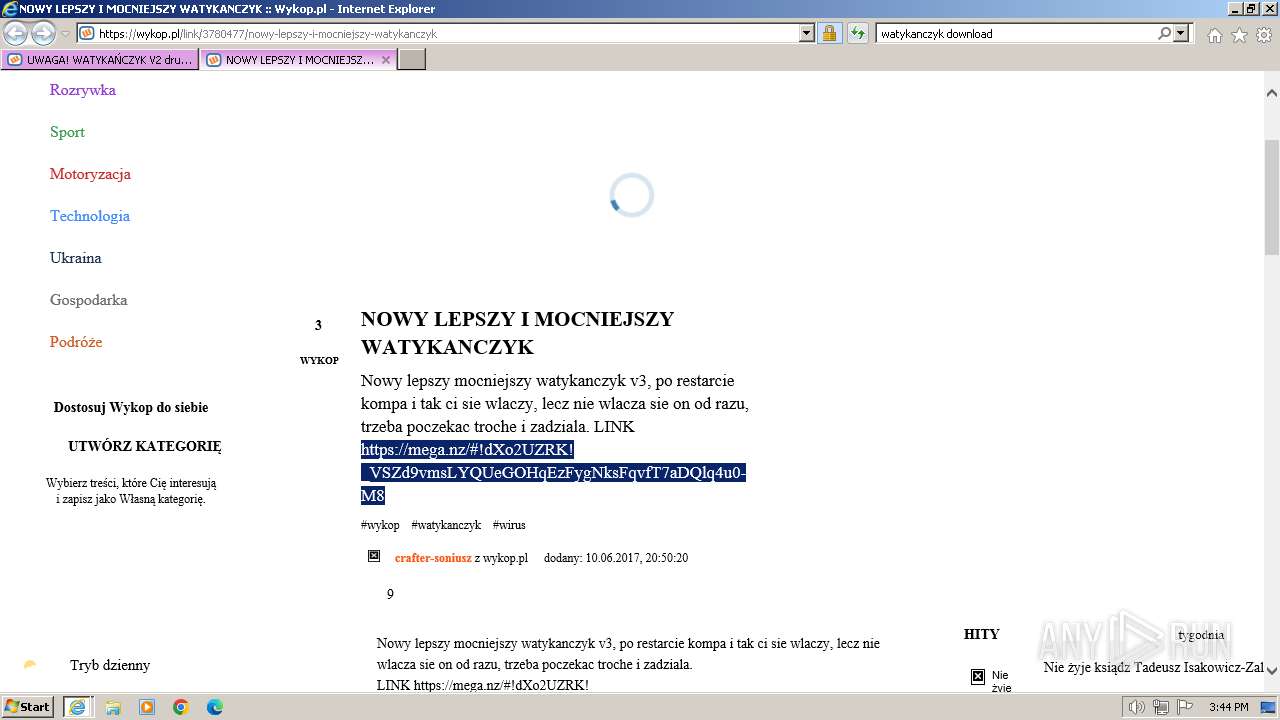
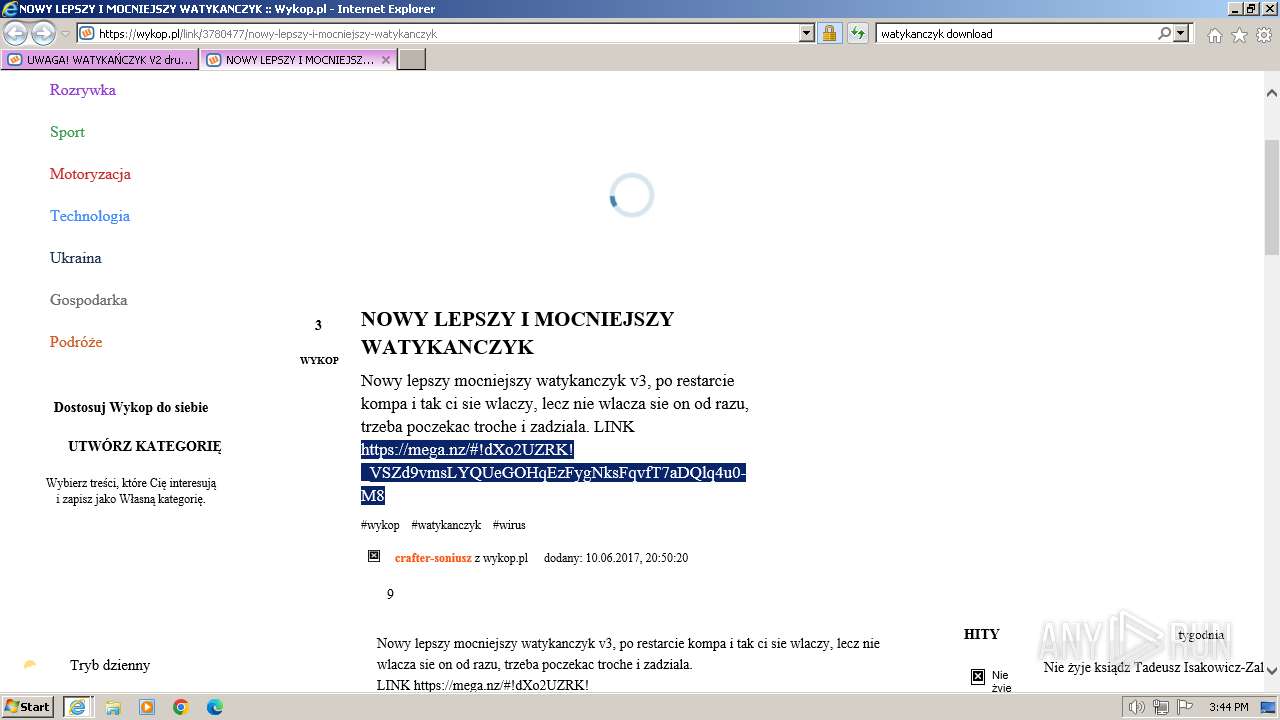
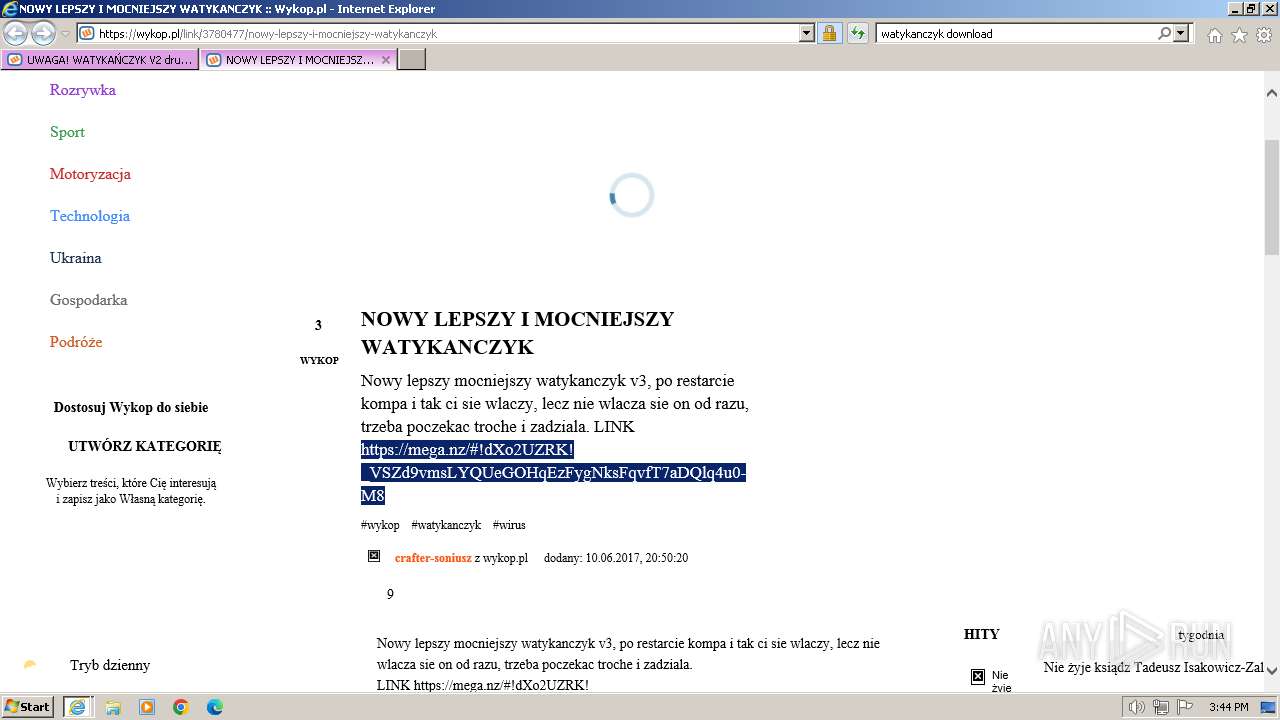
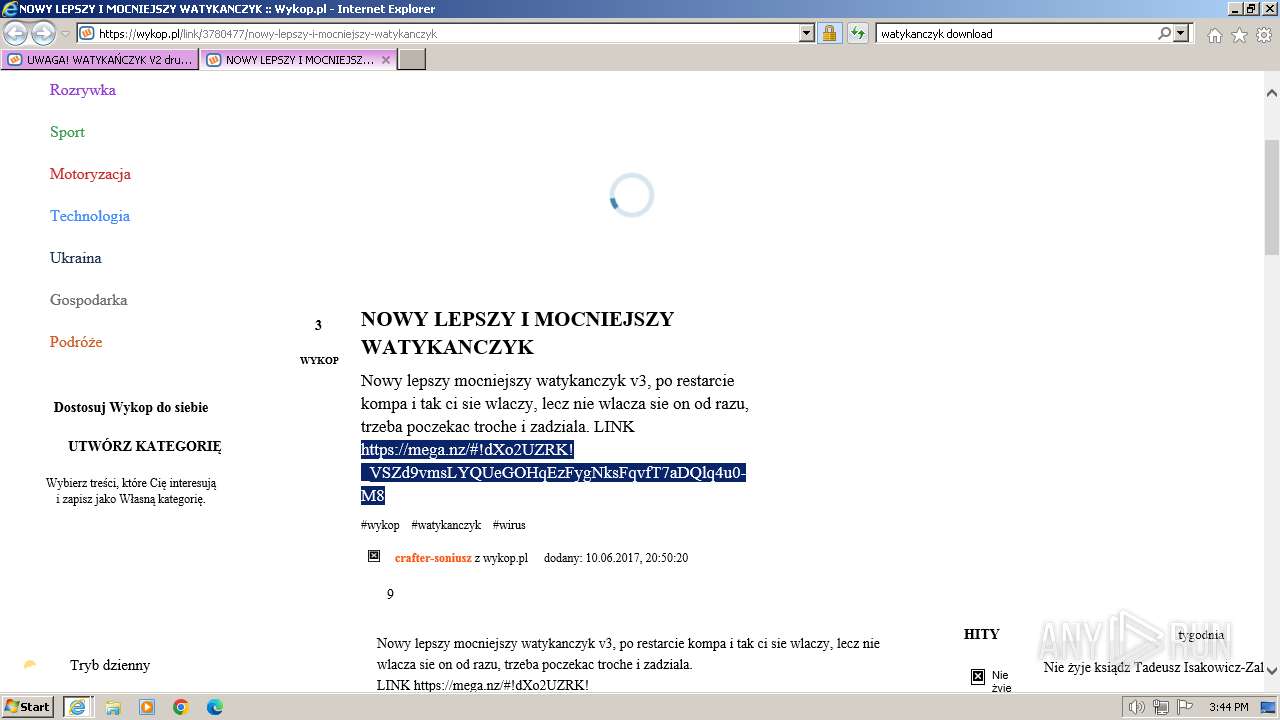
| URL: | https://managerplus.pl/top-5-malwareu-w-polsce-69920 |
| Full analysis: | https://app.any.run/tasks/cc67a2e9-e871-4a2a-be9f-1548ea04cd3b |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2024, 15:39:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 1721BFB89FB8A2CAFEABD391DE011B9D |
| SHA1: | A88076A55D0C09D8A8D65571C87022EF3C7DA338 |
| SHA256: | 13C773E49C4A747104CBEDB87B70373286094F799E4712E780E6A64F72689618 |
| SSDEEP: | 3:N8ELVJFERnQlEBXUIJFn:2ELVvCEi5 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Disables Form Suggestion in Internet Explorer
- iexplore.exe (PID: 1696)
INFO
Application launched itself
- iexplore.exe (PID: 1696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
43
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1696 CREDAT:3020047 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
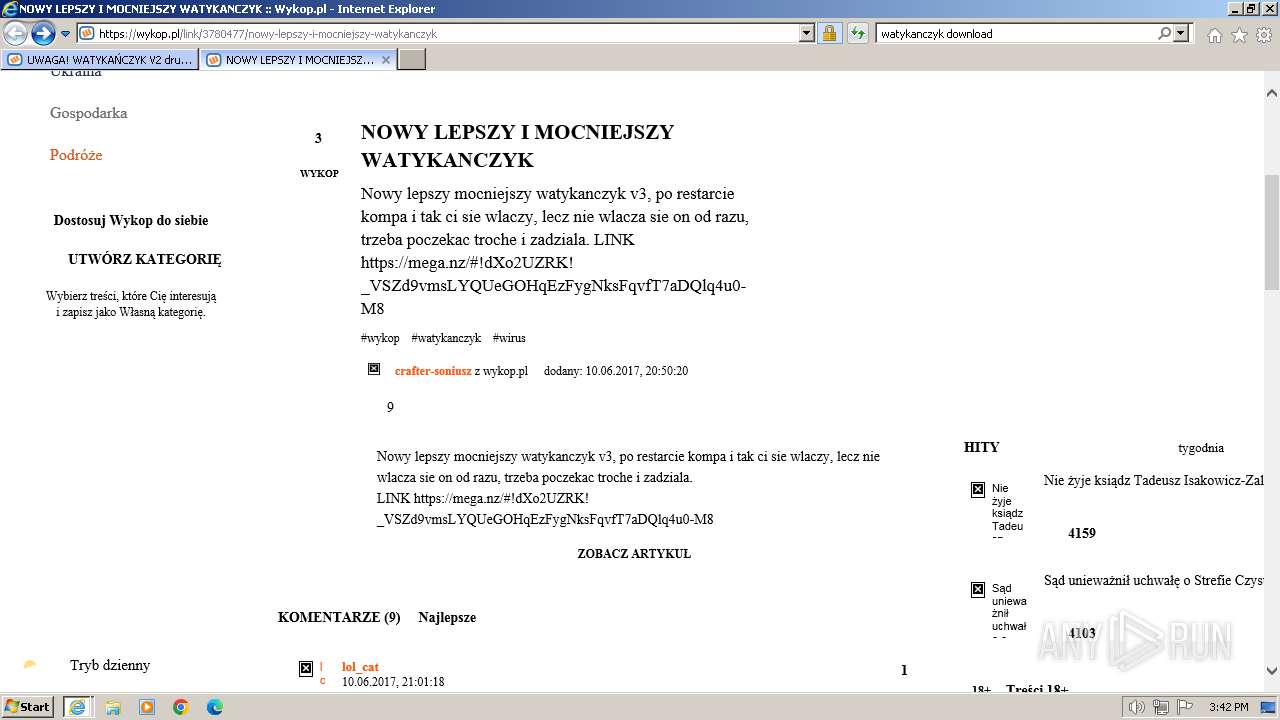
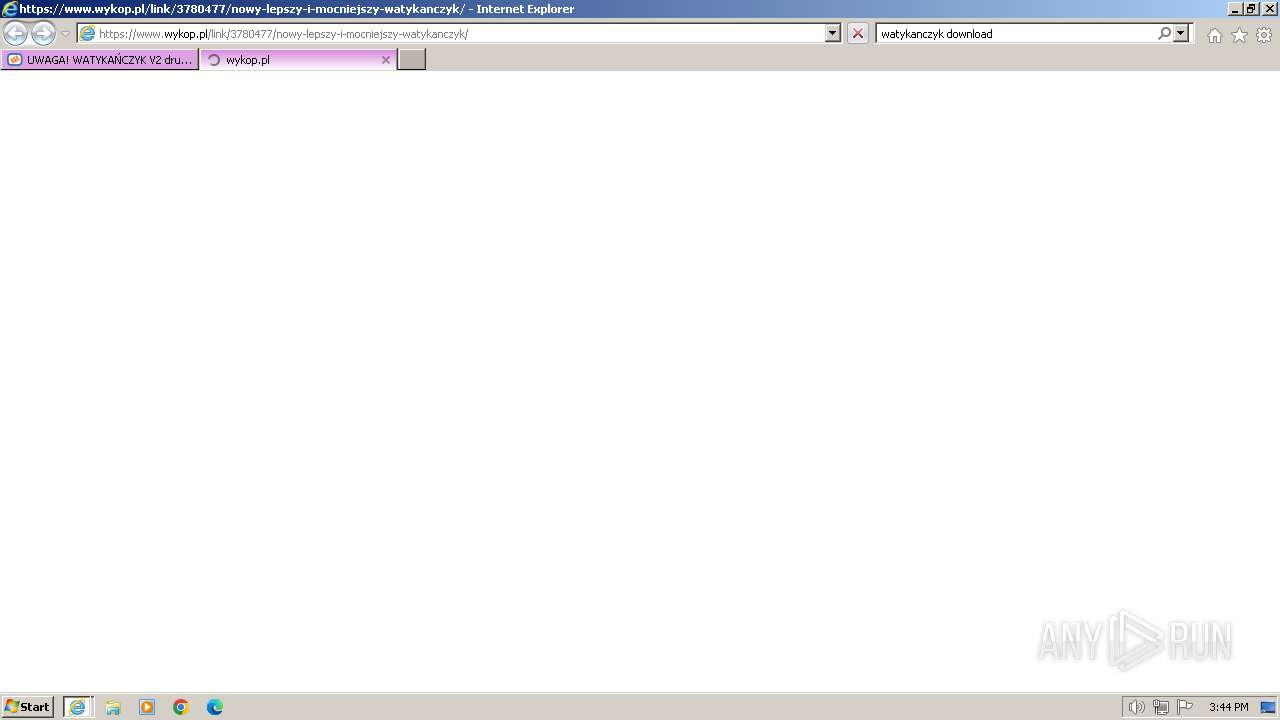
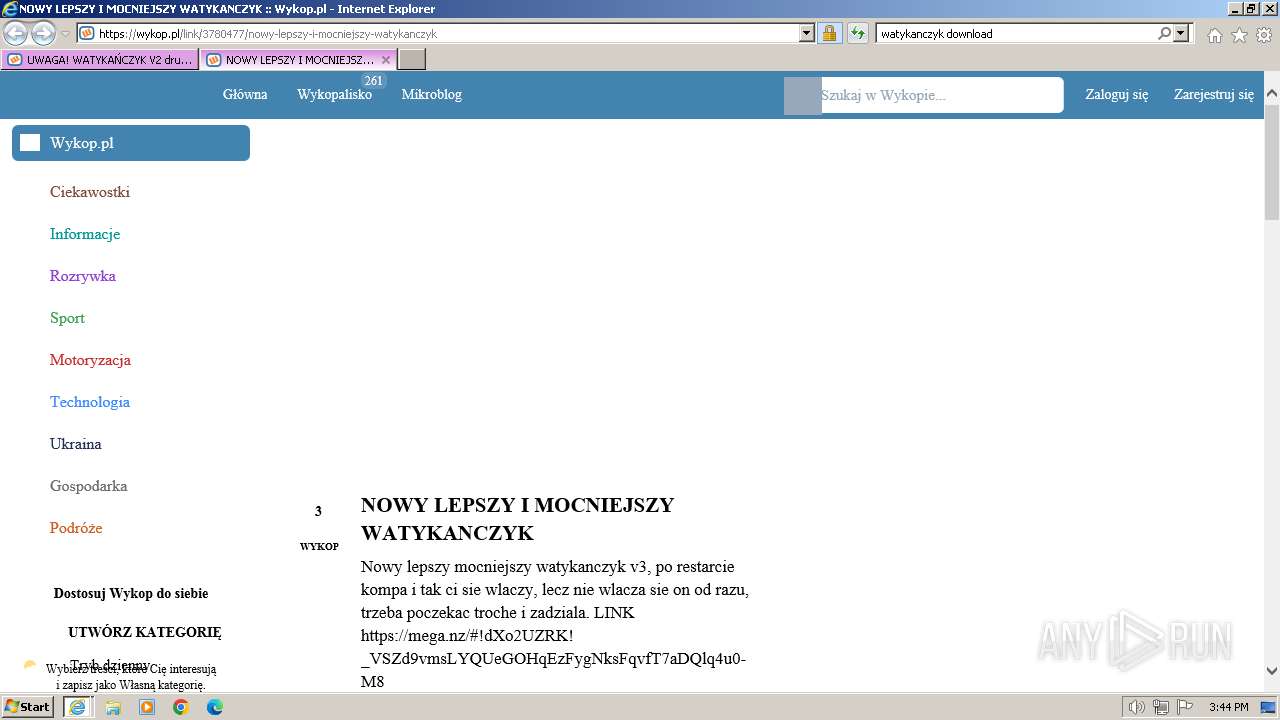
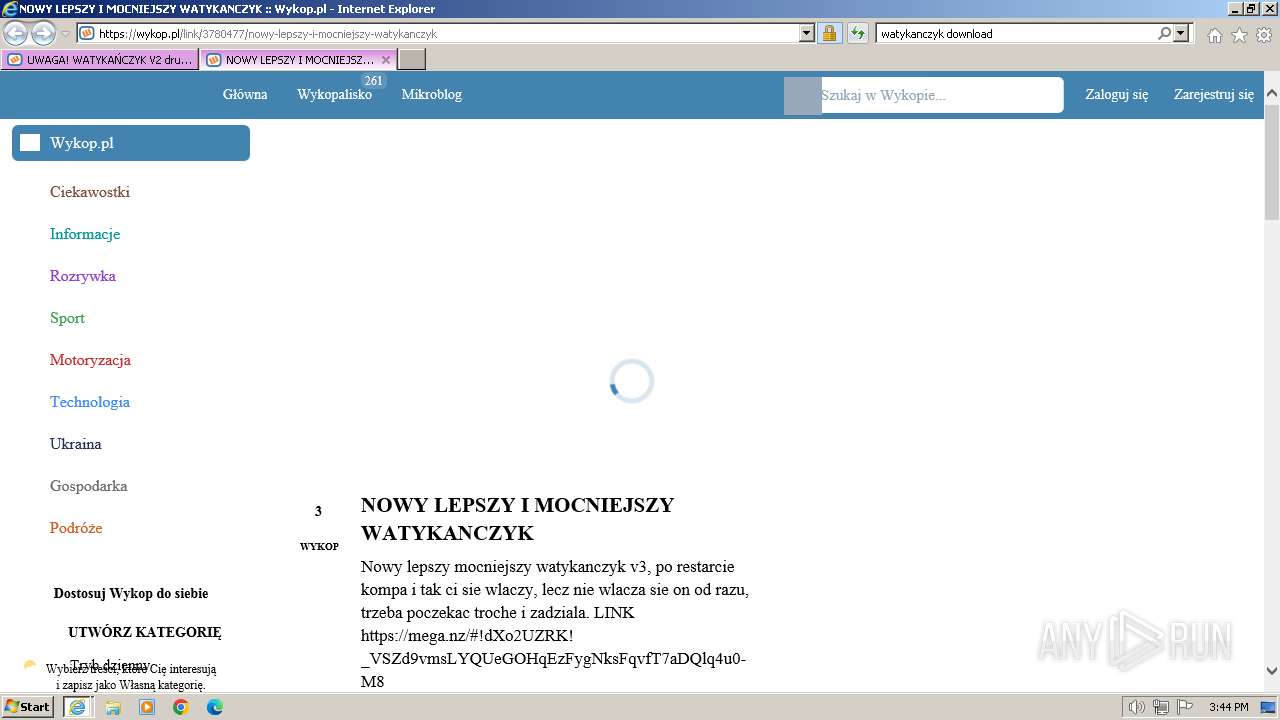
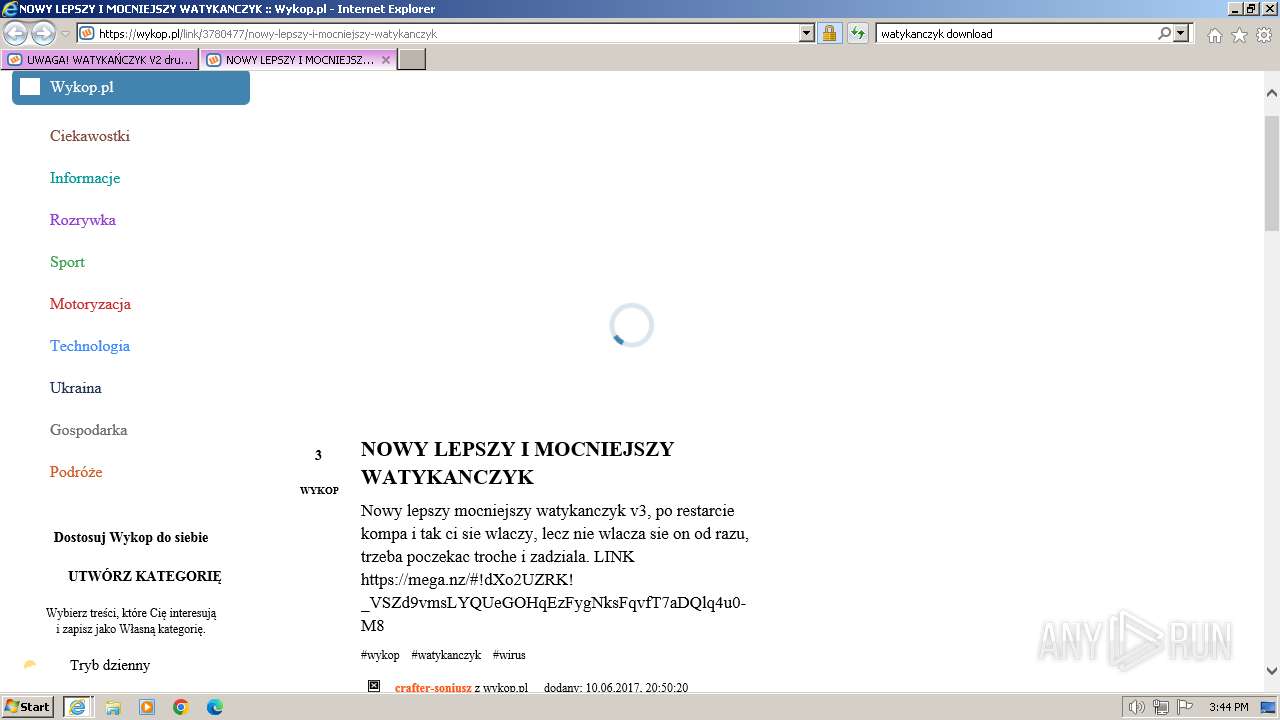
| 1696 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://managerplus.pl/top-5-malwareu-w-polsce-69920" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2836 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1696 CREDAT:1316144 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4000 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1696 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
79 656
Read events
79 338
Write events
187
Delete events
131
Modification events
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 818001248 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31094712 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31094712 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1696) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
75
Text files
516
Unknown types
43
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\tdb_main[1].css | text | |
MD5:B71962BA842EC8FE80423633C446A102 | SHA256:AFCC663536DE33D814D9D34E095D967C24CE211D814F8957FF9FF313BEA37693 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\style[2].css | text | |
MD5:33B98B30678FC90859AA7AE9EE0DA110 | SHA256:ACE42FE78BD5FD688FEE40965D85ACD39E37C5674CD203BFA901D4BDB1CC897A | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\td_legacy_main[1].css | text | |
MD5:98B50B8C03A68154AE234C95A0B0C045 | SHA256:6953E22FF9E5F712B5C0F5BD8F93D4185C9BC76A8084493316474F6810701065 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:F97A8BC2F2F2DE013C159B792DE5B024 | SHA256:61D8238BD4B4EC91DE40116B4FA6BE8038DA256D04594E0C4EFB8805E5836871 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\screen.min[1].css | text | |
MD5:14E1BA7BC29BFAE4538D5D720BEE50DC | SHA256:E37BA86536F9A12D450390901292AF30F4393D4FE3E06B907D351EF876264301 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F07644E38ED7C9F37D11EEC6D4335E02_08872284D8414653D8A6B617C1164F2D | binary | |
MD5:D10086CAA51E82B68A4372F69D4B3C1F | SHA256:9FDADA4984338B08A83465E3F0CE751CF2F0CD394D5DAADCBDD0AB0CA8CBC9F1 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F07644E38ED7C9F37D11EEC6D4335E02_08872284D8414653D8A6B617C1164F2D | der | |
MD5:AA5745C16CE9F8E8EDB3502C4B779D9C | SHA256:57951F7E48AAF4E245A4098863B00F787F49502498BA23094949286C3170CC06 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | der | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 4000 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\style[1].css | text | |
MD5:177CE3195E063DF497ABEF93F207A317 | SHA256:60CA9C0B9E446CA209D558F3793F84EA10CFFE6C9B10FAAB41D4F15400013048 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
40
TCP/UDP connections
195
DNS requests
99
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4000 | iexplore.exe | GET | 304 | 88.221.110.65:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b150b552b216e1f4 | unknown | — | — | unknown |
4000 | iexplore.exe | GET | 304 | 88.221.110.104:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?36ca310eb28aaa33 | unknown | — | — | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC%2BP0iGO7o7nQoIudW3BwdU | unknown | binary | 472 b | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCRd4hKrA6aBAnnS3UYBsso | unknown | binary | 472 b | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCimReIRyQtphKmdTNhBzaE | unknown | binary | 472 b | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCimReIRyQtphKmdTNhBzaE | unknown | binary | 472 b | unknown |
4000 | iexplore.exe | GET | 200 | 216.58.206.67:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCGXFtW%2BmD7fgro46rB%2F0k5 | unknown | binary | 472 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4000 | iexplore.exe | 188.114.97.3:443 | managerplus.pl | CLOUDFLARENET | NL | unknown |
4000 | iexplore.exe | 88.221.110.104:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4000 | iexplore.exe | 88.221.110.65:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
4000 | iexplore.exe | 216.58.206.67:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4000 | iexplore.exe | 142.250.184.226:443 | pagead2.googlesyndication.com | GOOGLE | US | whitelisted |
4000 | iexplore.exe | 142.250.186.142:443 | fundingchoicesmessages.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
managerplus.pl |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
pagead2.googlesyndication.com |
| whitelisted |
fundingchoicesmessages.google.com |
| whitelisted |
region1.analytics.google.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
www.google.dk |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Misc activity | ET INFO File Sharing Related Domain in DNS Lookup (mega .nz) |
124 | iexplore.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
124 | iexplore.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
1080 | svchost.exe | Misc activity | ET INFO Observed DNS Query to Filesharing Service (mega .co .nz) |
1696 | iexplore.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |
1696 | iexplore.exe | Misc activity | ET INFO File Sharing Domain Observed in TLS SNI (mega .nz) |