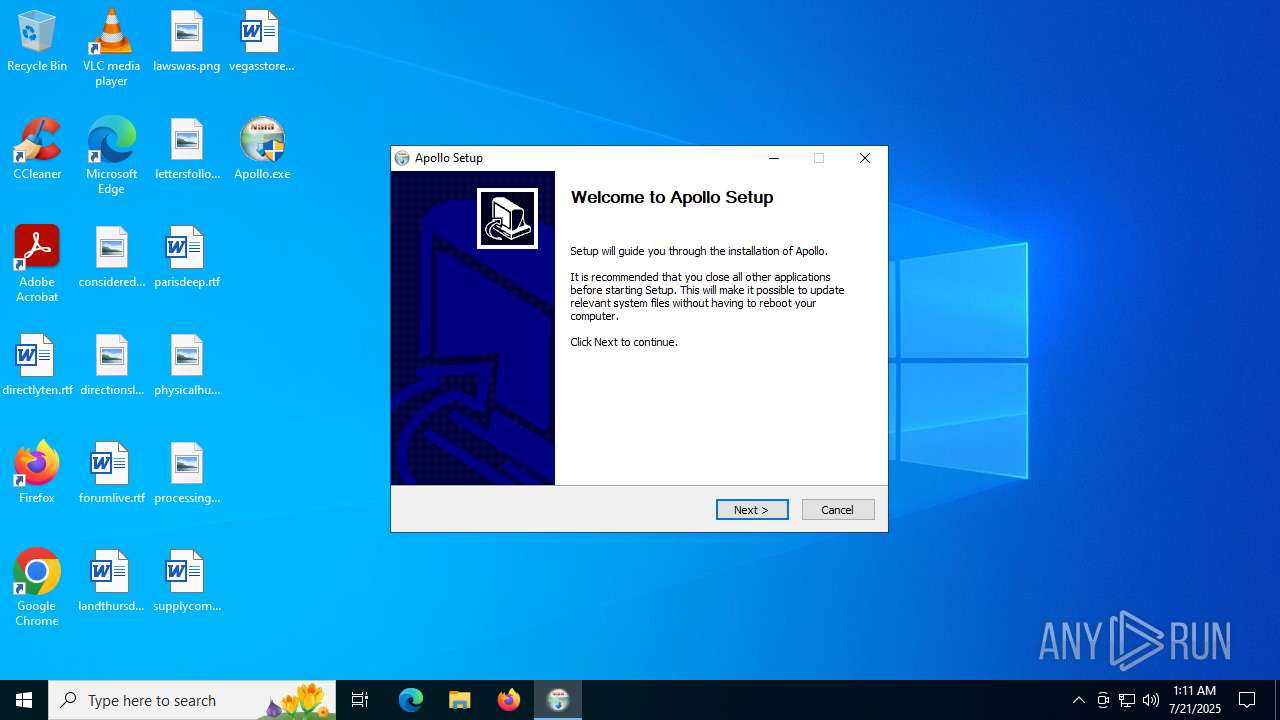
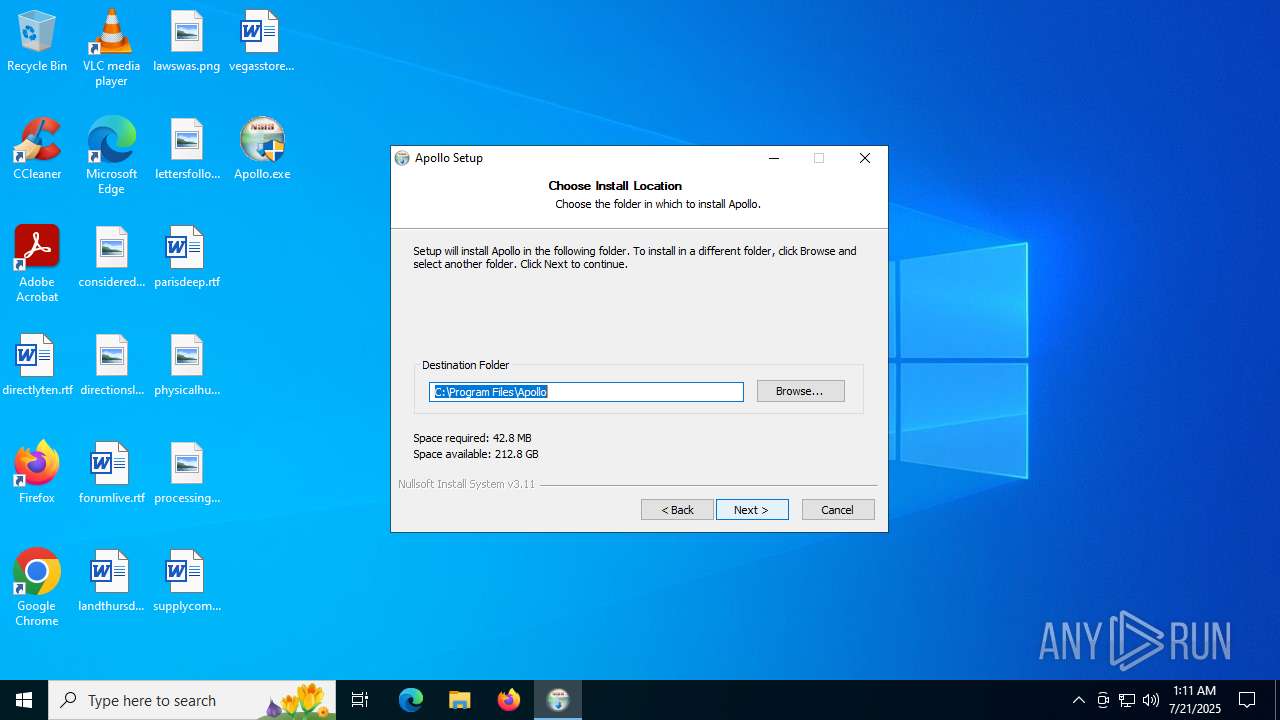
| File name: | Apollo.exe |
| Full analysis: | https://app.any.run/tasks/f88f0c7c-b6b4-46a7-8834-82ff1c102ad3 |
| Verdict: | Malicious activity |
| Analysis date: | July 21, 2025, 01:11:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows, 9 sections |
| MD5: | 0FF951E3173AF3E9E440DA91526148C2 |
| SHA1: | 4195DA2704E14954493490177C3D13053D2B5C59 |
| SHA256: | 13C406840A973E4087848541907C29E07FD9C7DB7A6E0E4A96CE87DB01BE4956 |
| SSDEEP: | 98304:/epSdvd56xTP61+B/OEqs6nB4rS/CdA93+ZArzN7P3r7zcBue0fwkIWGtqoAw3eu:6VXG3DxuLaNXzFjkbnakR |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 6852)
- cmd.exe (PID: 1488)
- net.exe (PID: 1244)
SUSPICIOUS
Adds/modifies Windows certificates
- certutil.exe (PID: 4456)
- powershell.exe (PID: 5288)
- certutil.exe (PID: 2612)
Executable content was dropped or overwritten
- Apollo.exe (PID: 2716)
- drvinst.exe (PID: 72)
- nefconc.exe (PID: 1488)
Uses ICACLS.EXE to modify access control lists
- Apollo.exe (PID: 2716)
- cmd.exe (PID: 1232)
There is functionality for taking screenshot (YARA)
- Apollo.exe (PID: 2716)
Starts CMD.EXE for commands execution
- Apollo.exe (PID: 2716)
- cmd.exe (PID: 856)
- cmd.exe (PID: 2188)
Executing commands from a ".bat" file
- Apollo.exe (PID: 2716)
Creates a software uninstall entry
- Apollo.exe (PID: 2716)
Application launched itself
- cmd.exe (PID: 2188)
- cmd.exe (PID: 856)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 2188)
- cmd.exe (PID: 6756)
Executes as Windows Service
- WUDFHost.exe (PID: 4032)
- sunshinesvc.exe (PID: 6636)
Creates or modifies Windows services
- drvinst.exe (PID: 4888)
Creates files in the driver directory
- drvinst.exe (PID: 72)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 4832)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 856)
Manipulates environment variables
- powershell.exe (PID: 5288)
Execution of CURL command
- cmd.exe (PID: 856)
Windows service management via SC.EXE
- sc.exe (PID: 4412)
- sc.exe (PID: 2312)
- sc.exe (PID: 6748)
Starts SC.EXE for service management
- cmd.exe (PID: 1488)
- cmd.exe (PID: 5244)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 2188)
Creates a new Windows service
- sc.exe (PID: 4232)
Sets the service to start on system boot
- sc.exe (PID: 4112)
The process creates files with name similar to system file names
- Apollo.exe (PID: 2716)
Malware-specific behavior (creating "System.dll" in Temp)
- Apollo.exe (PID: 2716)
INFO
Checks supported languages
- Apollo.exe (PID: 2716)
- nefconc.exe (PID: 7064)
- nefconc.exe (PID: 1488)
- drvinst.exe (PID: 4888)
- drvinst.exe (PID: 72)
- curl.exe (PID: 4072)
- nefconc.exe (PID: 6820)
- curl.exe (PID: 644)
- sunshinesvc.exe (PID: 6636)
- sunshine.exe (PID: 4512)
Creates files in the program directory
- Apollo.exe (PID: 2716)
- cmd.exe (PID: 1232)
- sunshine.exe (PID: 4512)
Reads the computer name
- Apollo.exe (PID: 2716)
- drvinst.exe (PID: 72)
- drvinst.exe (PID: 4888)
- nefconc.exe (PID: 1488)
- curl.exe (PID: 644)
- nefconc.exe (PID: 7064)
- nefconc.exe (PID: 6820)
- sunshinesvc.exe (PID: 6636)
- sunshine.exe (PID: 4512)
Create files in a temporary directory
- Apollo.exe (PID: 2716)
- nefconc.exe (PID: 1488)
The sample compiled with english language support
- Apollo.exe (PID: 2716)
Reads the machine GUID from the registry
- drvinst.exe (PID: 72)
- sunshine.exe (PID: 4512)
Reads the software policy settings
- drvinst.exe (PID: 72)
- slui.exe (PID: 3108)
Adds/modifies Windows certificates
- drvinst.exe (PID: 72)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5288)
Checks proxy server information
- reg.exe (PID: 4164)
- slui.exe (PID: 3108)
Execution of CURL command
- cmd.exe (PID: 6756)
- cmd.exe (PID: 856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:04:30 18:11:53+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.44 |
| CodeSize: | 35328 |
| InitializedDataSize: | 103936 |
| UninitializedDataSize: | 402432 |
| EntryPoint: | 0x42bd |
| OSVersion: | 5.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
198
Monitored processes
61
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 72 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{e2db3f13-3376-3b4e-be75-a5bba9902e73}\SudoVDA.inf" "9" "4fbf0c1f7" "00000000000001DC" "WinSta0\Default" "00000000000001C8" "208" "C:\Program Files\Apollo\drivers\sudovda" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 644 | curl -s -L https://api.github.com/repos/nefarius/vigembus/releases/latest | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 35 Version: 8.4.0 Modules
| |||||||||||||||
| 856 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Apollo\scripts\install-gamepad.bat"" | C:\Windows\System32\cmd.exe | — | Apollo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sunshine.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Apollo\drivers\sudovda\install.bat"" | C:\Windows\System32\cmd.exe | — | Apollo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1160 | netsh advfirewall firewall add rule name=Apollo dir=in action=allow protocol=udp program="C:\Program Files\Apollo\sunshine.exe" enable=yes | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1232 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Apollo\scripts\migrate-config.bat"" | C:\Windows\System32\cmd.exe | — | Apollo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1244 | net start ApolloService | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | nefconc.exe --install-driver --inf-path "SudoVDA.inf" | C:\Program Files\Apollo\drivers\sudovda\nefconc.exe | cmd.exe | ||||||||||||
User: admin Company: Nefarius Software Solutions e.U. Integrity Level: HIGH Description: Nefarius' Device Console Utility Exit code: 0 Version: 1.12.0.0 Modules
| |||||||||||||||
| 1488 | C:\WINDOWS\system32\cmd.exe /c ""C:\Program Files\Apollo\scripts\install-service.bat"" | C:\Windows\System32\cmd.exe | — | Apollo.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 299
Read events
15 237
Write events
52
Delete events
10
Modification events
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Apollo\sunshine.exe | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | DisplayName |
Value: Apollo | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | DisplayVersion |
Value: 0.4.1 | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | Publisher |
Value: SudoMaker | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Apollo\Uninstall.exe" | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\Apollo |
| Operation: | write | Name: | StartMenu |
Value: Apollo | |||
| (PID) Process: | (2716) Apollo.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\SudoMaker\Apollo |
| Operation: | write | Name: | Start Menu Folder |
Value: Apollo | |||
| (PID) Process: | (2612) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
Executable files
18
Suspicious files
47
Text files
105
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2716 | Apollo.exe | C:\Program Files\Apollo\sunshine.exe | — | |
MD5:— | SHA256:— | |||
| 2716 | Apollo.exe | C:\Users\admin\AppData\Local\Temp\nsxDDBA.tmp\ioSpecial.ini | text | |
MD5:E2D5070BC28DB1AC745613689FF86067 | SHA256:D95AED234F932A1C48A2B1B0D98C60CA31F962310C03158E2884AB4DDD3EA1E0 | |||
| 2716 | Apollo.exe | C:\Users\admin\AppData\Local\Temp\nsxDDBA.tmp\UserInfo.dll | executable | |
MD5:7357838AC641996018FEF63B2F30E085 | SHA256:B12B4A4BA795356E4112F51986A329BE29929FD7CC533984F55BF6AFE5E3F2FD | |||
| 2716 | Apollo.exe | C:\Users\admin\AppData\Local\Temp\nsxDDBA.tmp\InstallOptions.dll | executable | |
MD5:79C985EA58A63ADF00D79D5D9BEDE11C | SHA256:FE1D0728BCFB370048F1738259CAC8835B5E41DAFEADD5D80486C8ECC3C1577B | |||
| 2716 | Apollo.exe | C:\Users\admin\AppData\Local\Temp\nsxDDBA.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 2716 | Apollo.exe | C:\Program Files\Apollo\zlib1.dll | executable | |
MD5:EE01439A96E6C269C5D3D42C46C4516E | SHA256:1DC85208162EE57FE97E892BB5160FE9588903992995F90ADC3A3A358DAC6FC6 | |||
| 2716 | Apollo.exe | C:\Program Files\Apollo\assets\shaders\directx\convert_yuv420_packed_uv_type0_ps.hlsl | text | |
MD5:920BFD762632909D51768DF25483356C | SHA256:897BC37D0319B5400E142EE5D04C7DD260AF1071040B4D8F0BB6DCA90C510A3E | |||
| 2716 | Apollo.exe | C:\Program Files\Apollo\assets\shaders\directx\convert_yuv420_packed_uv_type0_ps_linear.hlsl | text | |
MD5:7BA99F704E3D336B7DA19EC698373F18 | SHA256:C0A67152C118E59C7B19BB55D180B3DBC7FC5841FC93688D799BD572F62997B8 | |||
| 2716 | Apollo.exe | C:\Program Files\Apollo\assets\shaders\directx\convert_yuv420_packed_uv_type0_ps_perceptual_quantizer.hlsl | text | |
MD5:770E5F40434C5B20DC0E4684A3869044 | SHA256:D5F937713422D2122BF57F482CF14C9B7CF70DBDB2E7A881742334E22FD951F2 | |||
| 2716 | Apollo.exe | C:\Users\admin\AppData\Local\Temp\nsxDDBA.tmp\StartMenu.dll | executable | |
MD5:24ED78F875EBD2F412ABBD53820350EC | SHA256:643F52F1341EACE7D8FB2FD2BA54A41B8863F0AC435F2FA0918E2971A1B4BA1B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
67
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.4:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.73:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.4:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.68:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.31.3:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3112 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
api.github.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |