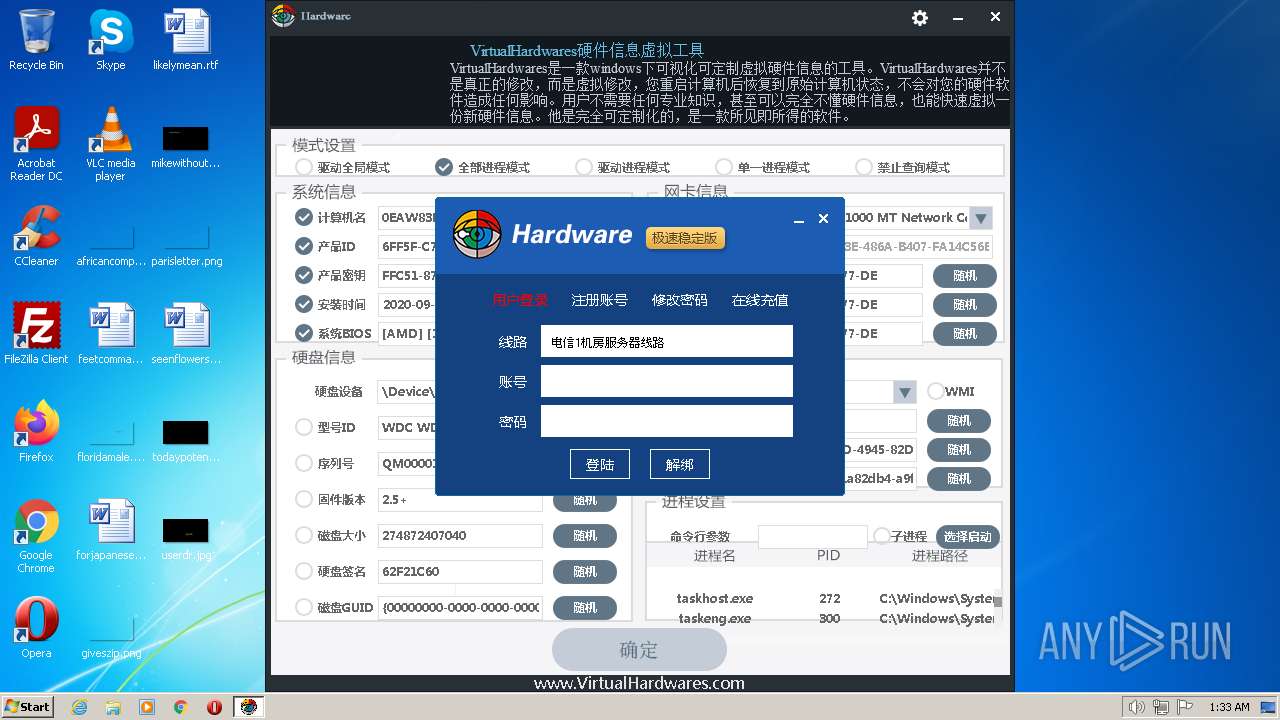
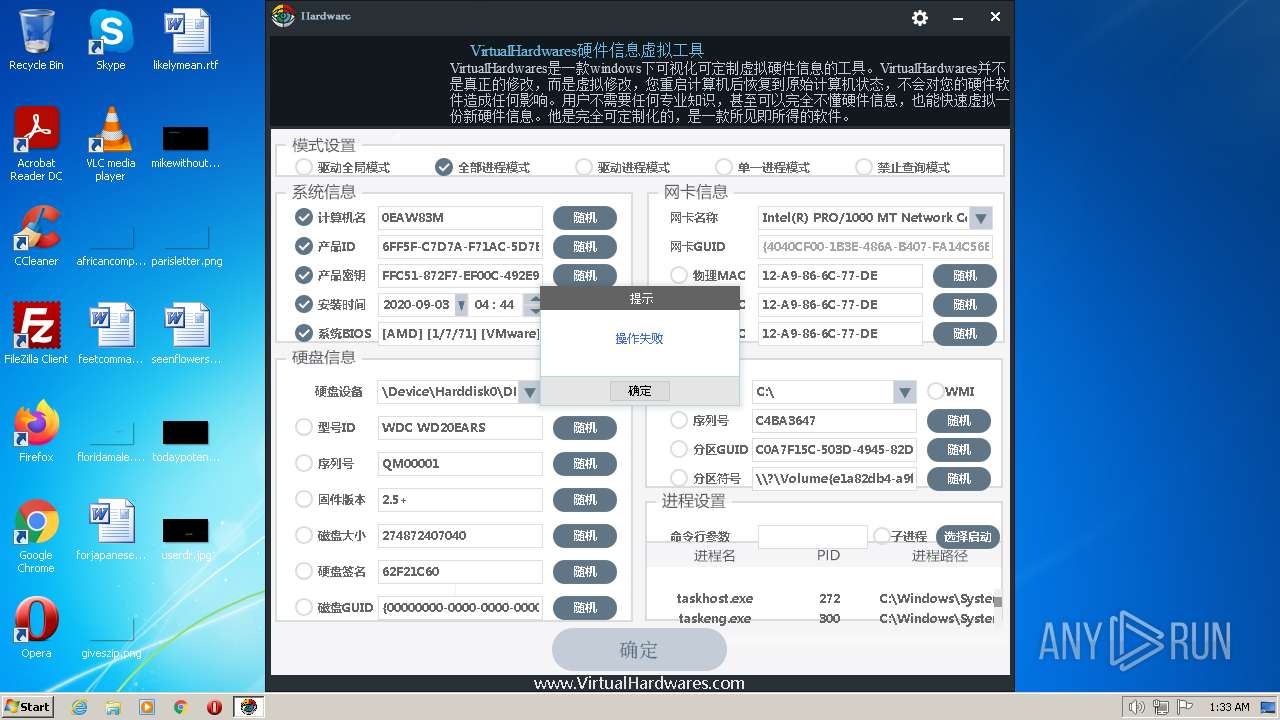
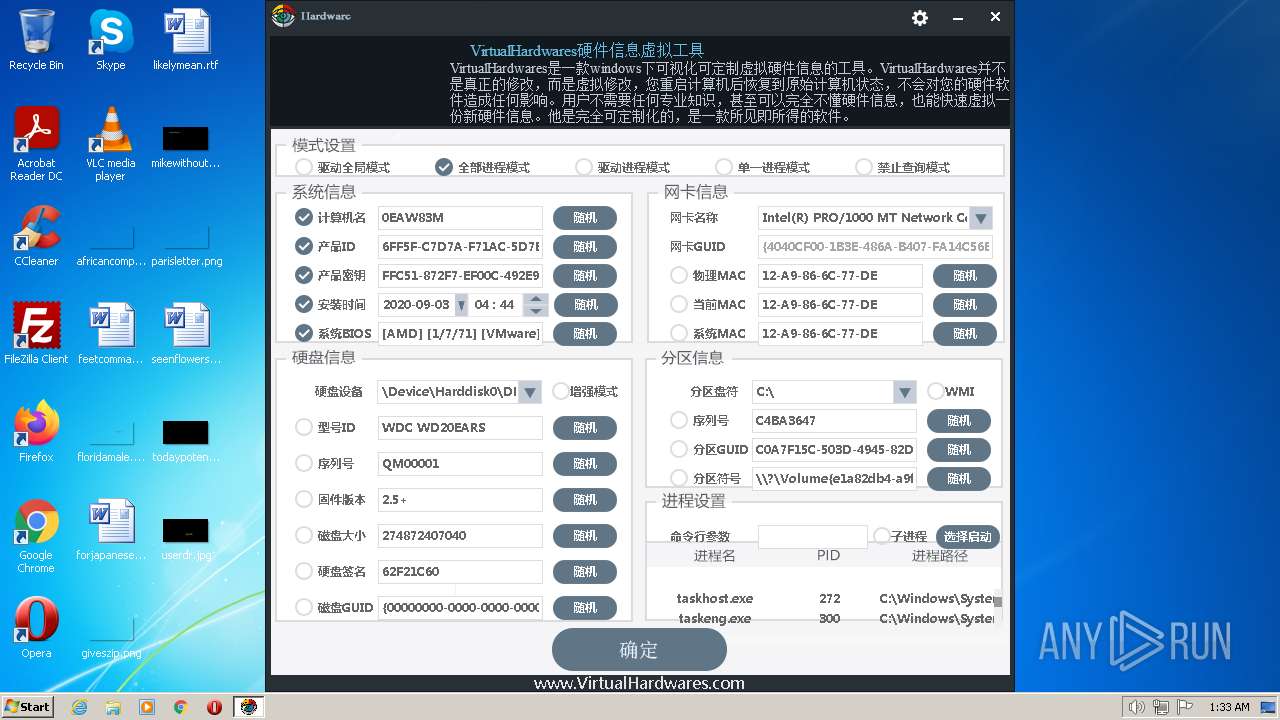
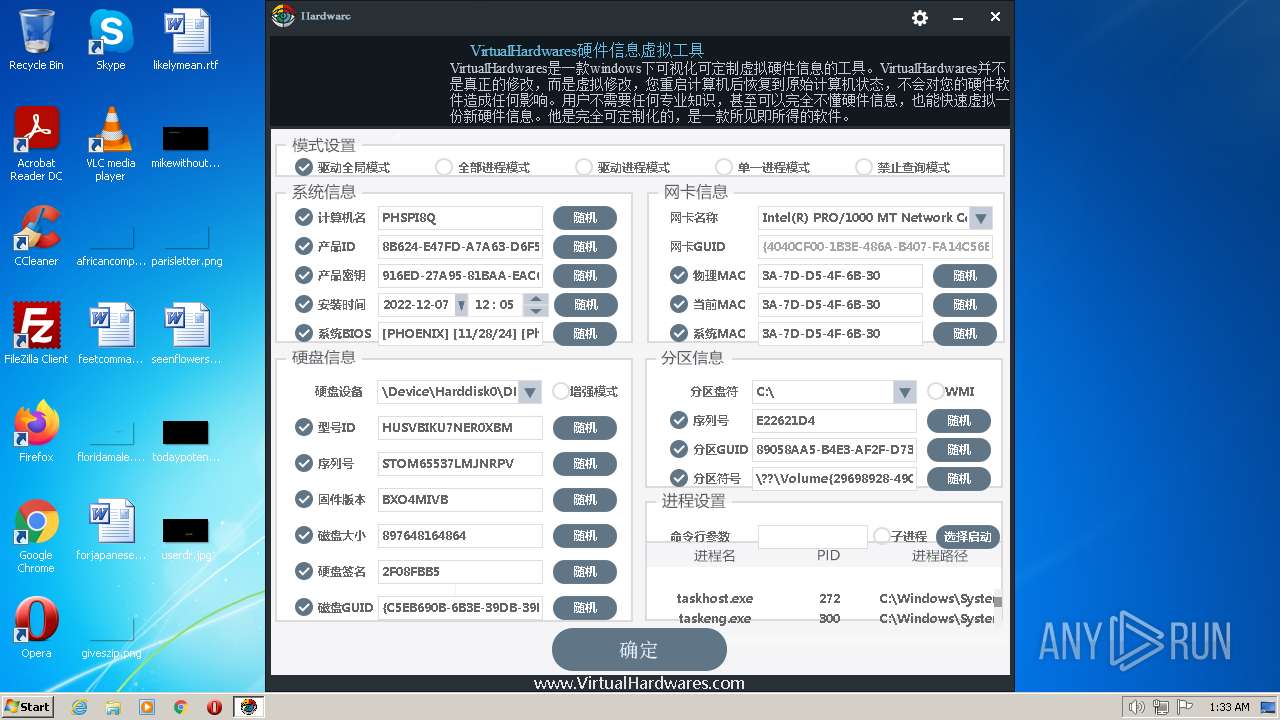
| File name: | hardware.exe |
| Full analysis: | https://app.any.run/tasks/3e73ebee-123a-47a9-8ba6-56054d77dc53 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 01:32:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 28260A35DEADF16EB01FA64EB7901F38 |
| SHA1: | 014D9FF8BB00F65D5B81E4F38951D447578CBA13 |
| SHA256: | 13BD765E29280E0DA7F6F4CB6498ADCB777A28266A513DEB4998B2E0C3AB3461 |
| SSDEEP: | 98304:S4GqXn/oOWMvX++y8GHEvsiWyERiS7I4qaF9fOgx:SeX/oOWMvXxCGPYRiS7IzaF9fOg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- hardware.exe (PID: 2988)
Reads Microsoft Outlook installation path
- hardware.exe (PID: 2988)
Reads security settings of Internet Explorer
- hardware.exe (PID: 2988)
Reads Internet Explorer settings
- hardware.exe (PID: 2988)
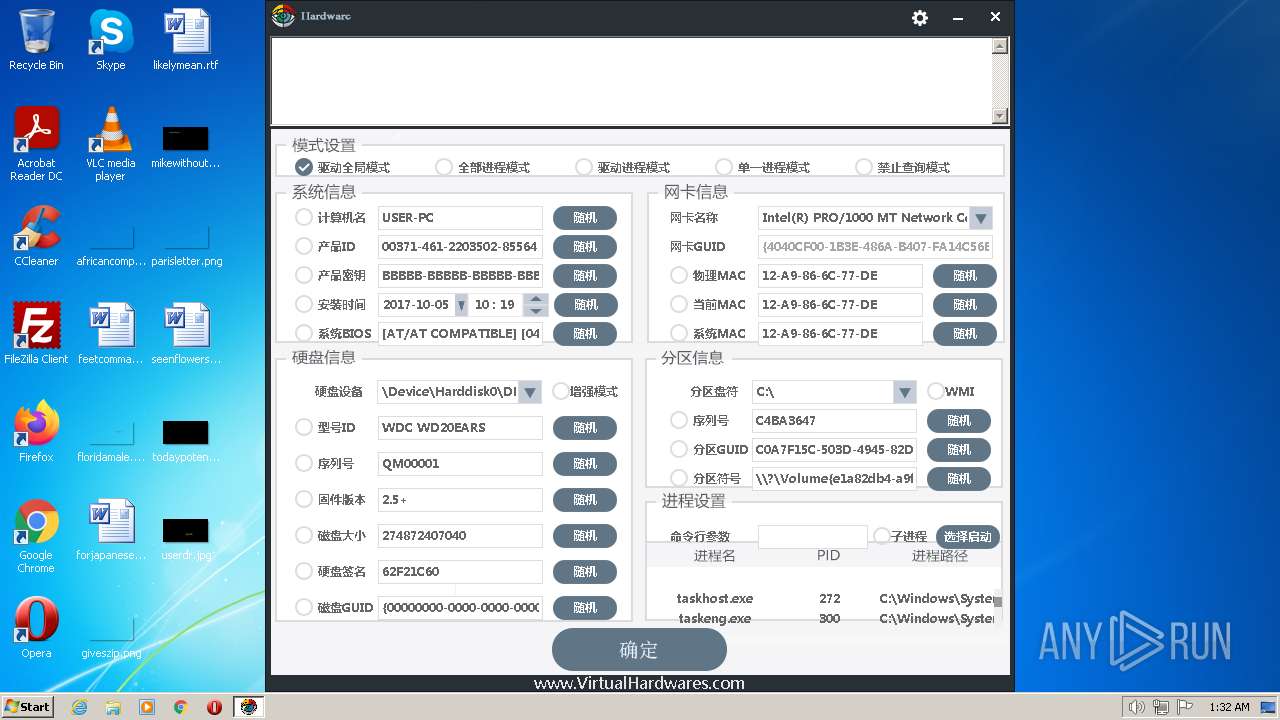
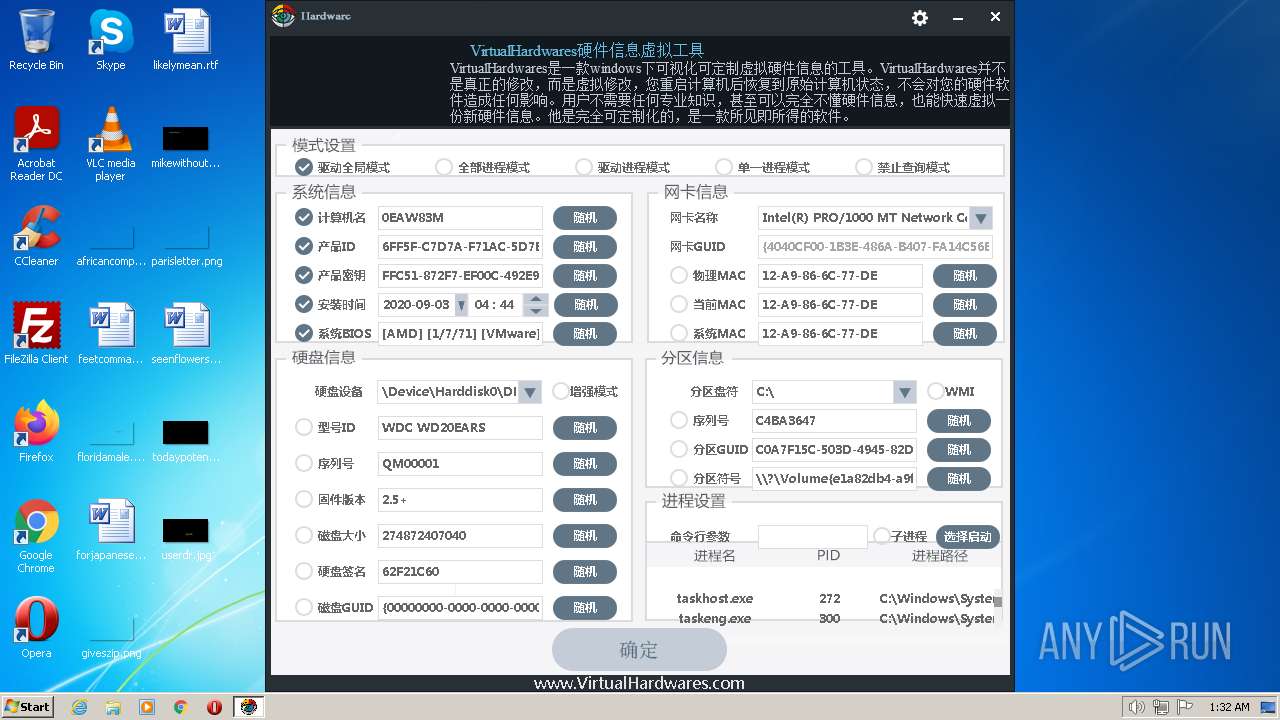
Reads the BIOS version
- hardware.exe (PID: 2988)
Adds/modifies Windows certificates
- hardware.exe (PID: 2988)
Checks Windows Trust Settings
- hardware.exe (PID: 2988)
Reads settings of System Certificates
- hardware.exe (PID: 2988)
Reads the date of Windows installation
- hardware.exe (PID: 2988)
INFO
Checks proxy server information
- hardware.exe (PID: 2988)
Reads Windows Product ID
- hardware.exe (PID: 2988)
Checks supported languages
- hardware.exe (PID: 2988)
Reads the computer name
- hardware.exe (PID: 2988)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2022-Oct-13 06:40:39 |
| Detected languages: |
|
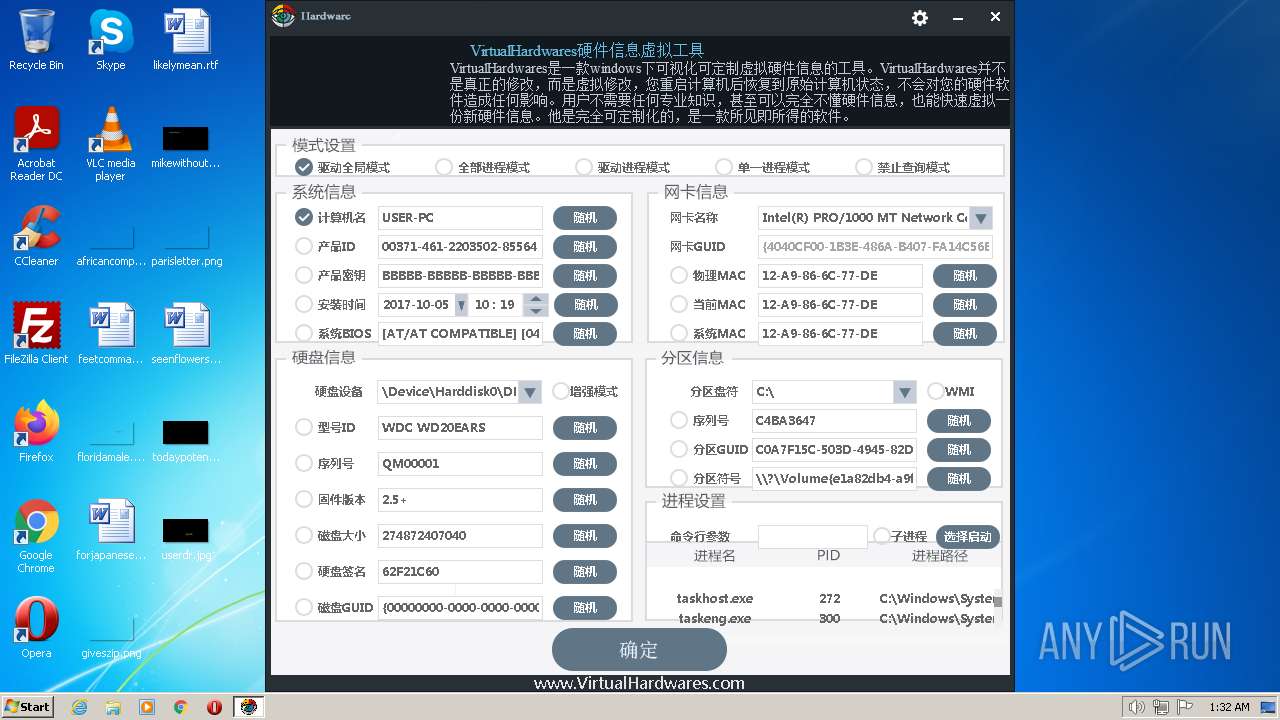
| CompanyName: | virtualhardwares |
| FileDescription: | virtualhardwares |
| FileVersion: | 1, 0, 0, 0 |
| InternalName: | virtualhardwares.exe |
| LegalCopyright: | (C) virtualhardwares All Rights Reserved |
| OriginalFilename: | virtualhardwares |
| ProductName: | virtualhardwares |
| ProductVersion: | 1, 0, 0, 0 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 256 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 7 |
| TimeDateStamp: | 2022-Oct-13 06:40:39 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 681294 | 0 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | |
.rdata | 688128 | 108054 | 0 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | |
.data | 798720 | 112900 | 0 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.vmp0 | 913408 | 2095117 | 0 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.vmp1 | 3010560 | 4383661 | 4383744 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.88718 |
.reloc | 7397376 | 288 | 512 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 2.65815 |
.rsrc | 7401472 | 1685093 | 20992 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.21773 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.34507 | 16936 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
5 | 1.91924 | 20 | Latin 1 / Western European | Chinese - PRC | RT_GROUP_ICON |
10 | 0 | 21895 | Latin 1 / Western European | Chinese - PRC | XML |
11 | 0 | 463 | Latin 1 / Western European | Chinese - PRC | XML |
13 | 0 | 1302 | Latin 1 / Western European | Chinese - PRC | XML |
14 | 0 | 772 | Latin 1 / Western European | Chinese - PRC | XML |
15 | 0 | 8361 | Latin 1 / Western European | Chinese - PRC | XML |
100 | 0 | 17212 | Latin 1 / Western European | Chinese - PRC | PNG |
106 | 0 | 225280 | Latin 1 / Western European | Chinese - PRC | RC_DATA |
107 | 0 | 238592 | Latin 1 / Western European | Chinese - PRC | RC_DATA |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.dll |
GDI32.dll |
IMM32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
KERNEL32.dll (#2) |
KERNEL32.dll (#3) |
OLEAUT32.dll |
Total processes
38
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1756 | "C:\Users\admin\AppData\Local\Temp\hardware.exe" | C:\Users\admin\AppData\Local\Temp\hardware.exe | — | Explorer.EXE | |||||||||||
User: admin Company: virtualhardwares Integrity Level: MEDIUM Description: virtualhardwares Exit code: 3221226540 Version: 1, 0, 0, 0 Modules
| |||||||||||||||
| 2988 | "C:\Users\admin\AppData\Local\Temp\hardware.exe" | C:\Users\admin\AppData\Local\Temp\hardware.exe | Explorer.EXE | ||||||||||||
User: admin Company: virtualhardwares Integrity Level: HIGH Description: virtualhardwares Exit code: 0 Version: 1, 0, 0, 0 Modules
| |||||||||||||||
Total events
5 063
Read events
4 998
Write events
64
Delete events
1
Modification events
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2988) hardware.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\{FCC67766-6201-4AD1-A6B8-2F4553C93D47} |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
Executable files
0
Suspicious files
5
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2988 | hardware.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\hardware[1].htm | html | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | der | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_4136D3715888E22D65EBE484B233D81B | binary | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\349D186F1CB5682FA0194D4F3754EF36_97A2CB43E01F27293633B7B57353C80B | der | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\TEKNOAPG.txt | text | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\hm[1].js | text | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\E1C7BUEG.txt | text | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\Local\Temp\GameHardware.ini | text | |
MD5:— | SHA256:— | |||
| 2988 | hardware.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\349D186F1CB5682FA0194D4F3754EF36_97A2CB43E01F27293633B7B57353C80B | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
12
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2988 | hardware.exe | HEAD | 301 | 47.74.138.66:80 | http://www.aliyun.com/ | US | — | — | suspicious |
2988 | hardware.exe | GET | 200 | 43.129.214.10:80 | http://www.virtualhardwares.com/2022/hardware.html | JP | html | 1.44 Kb | unknown |
2988 | hardware.exe | HEAD | 301 | 47.74.138.66:80 | http://www.aliyun.com/ | US | — | — | suspicious |
2988 | hardware.exe | HEAD | 301 | 47.74.138.66:80 | http://www.aliyun.com/ | US | — | — | suspicious |
2988 | hardware.exe | GET | 404 | 43.129.214.10:80 | http://www.virtualhardwares.com/2022/hardware.png | JP | html | 555 b | unknown |
2988 | hardware.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | US | der | 1.40 Kb | whitelisted |
2988 | hardware.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDEQXzobvguxpIcxvaA%3D%3D | US | der | 1.40 Kb | whitelisted |
2988 | hardware.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCDQHuXxad%2F5c1K2Rl1mo%3D | US | der | 1.41 Kb | whitelisted |
2988 | hardware.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?19988b11ef01e9e3 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2988 | hardware.exe | 43.129.214.10:80 | www.qqgamegroup.com | Tencent Building, Kejizhongyi Avenue | HK | unknown |
2988 | hardware.exe | 103.235.46.191:443 | hm.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | suspicious |
2988 | hardware.exe | 47.74.138.66:80 | www.aliyun.com | Alibaba US Technology Co., Ltd. | SG | unknown |
2988 | hardware.exe | 8.210.51.125:80 | www.qqgamegroup.com | Alibaba US Technology Co., Ltd. | HK | malicious |
2988 | hardware.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
2988 | hardware.exe | 104.18.21.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
2988 | hardware.exe | 104.18.20.226:80 | ocsp.globalsign.com | CLOUDFLARENET | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.qqgamegroup.com |
| malicious |
www.virtualhardwares.com |
| unknown |
hm.baidu.com |
| whitelisted |
www.aliyun.com |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |