| File name: | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe |
| Full analysis: | https://app.any.run/tasks/24eccde2-7312-4dc4-95fb-9f096d39cb85 |
| Verdict: | Malicious activity |
| Analysis date: | March 04, 2024, 02:29:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3D716D8C6114533BBE1FDA6938B84092 |
| SHA1: | C918F6FC8ECA08C330C5434D46344AC63D31A3E7 |
| SHA256: | 13902861132376C808E304074E537F22435976567BD3E48B959363108AB79389 |
| SSDEEP: | 98304:G+cD4dnHh0N1nb0ZwL0egN9P8YW+HyeY4E9w11TwjyxviGZfeTw4ug4Dr1j1ZfUE:WR8tdT |
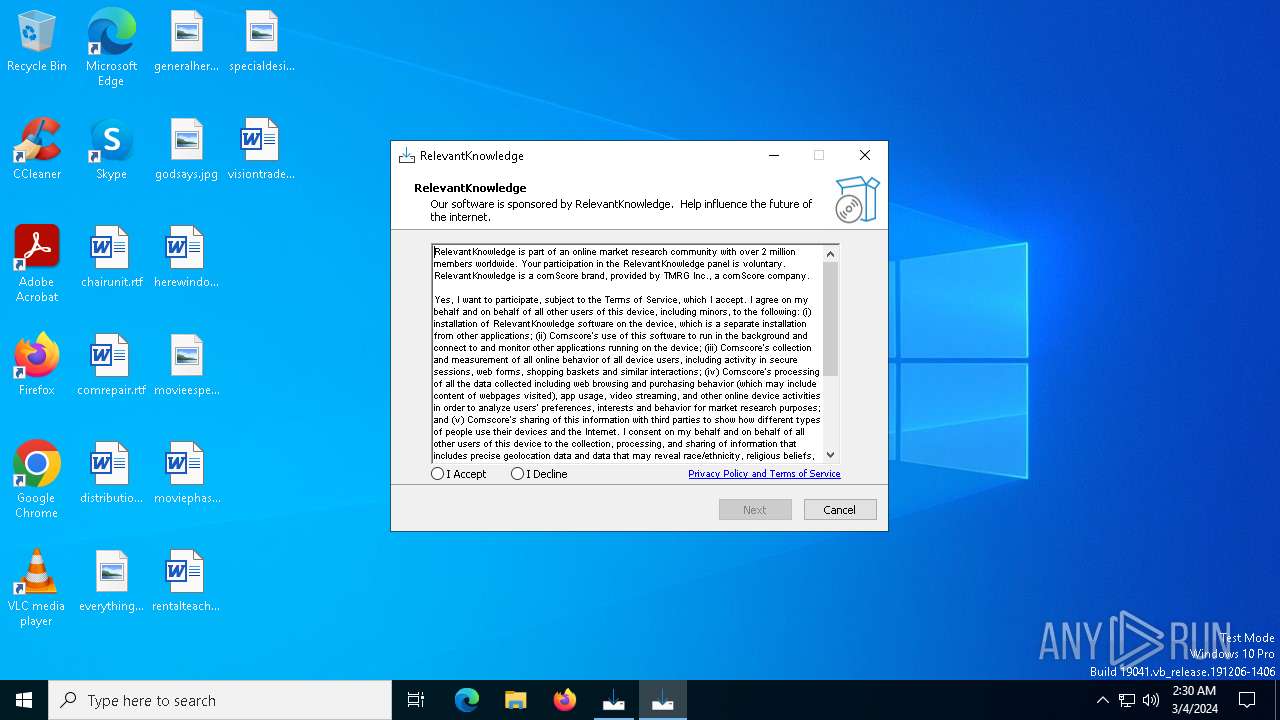
MALICIOUS
Drops the executable file immediately after the start
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 6056)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 2664)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- rk_setup.exe (PID: 1816)
- rk_setup.tmp (PID: 2168)
SUSPICIOUS
Reads security settings of Internet Explorer
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 2696)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
Executable content was dropped or overwritten
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 2664)
- rk_setup.exe (PID: 1816)
- rk_setup.tmp (PID: 2168)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 6056)
Reads the Windows owner or organization settings
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- rk_setup.tmp (PID: 2168)
Checks Windows Trust Settings
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
Reads the date of Windows installation
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 2696)
INFO
Create files in a temporary directory
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 6056)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 2664)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- rk_setup.exe (PID: 1816)
- rk_setup.tmp (PID: 2168)
Checks supported languages
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 6056)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe (PID: 2664)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- rk_setup.exe (PID: 1816)
- rk_setup.tmp (PID: 2168)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 2696)
Reads the computer name
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 2696)
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- rk_setup.tmp (PID: 2168)
Checks proxy server information
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- slui.exe (PID: 5456)
Reads the machine GUID from the registry
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- rk_setup.tmp (PID: 2168)
Reads the software policy settings
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
- slui.exe (PID: 5456)
Creates files or folders in the user directory
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 6660)
Process checks computer location settings
- 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp (PID: 2696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 89600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.1 |
| ProductVersionNumber: | 1.0.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
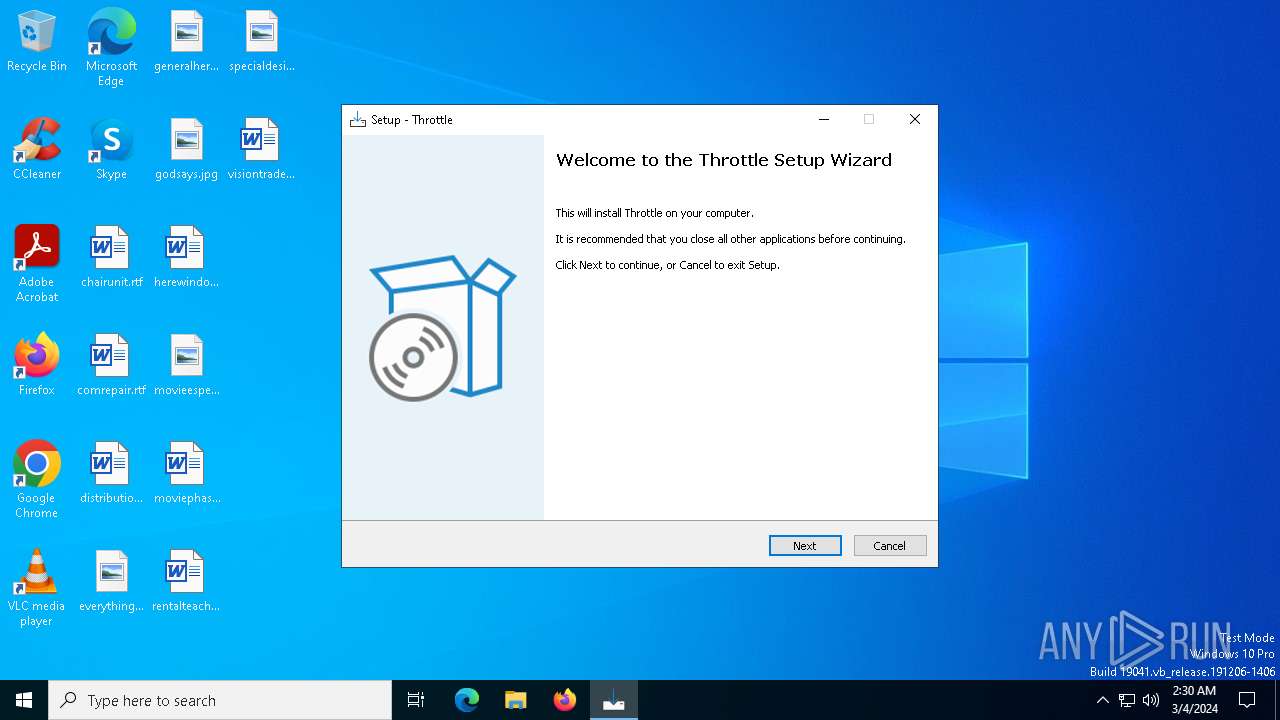
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | PGWARE LLC |
| FileDescription: | Throttle Setup |
| FileVersion: | 1.0.0.1 |
| LegalCopyright: | Copyright © 2001-2022 PGWARE LLC |
| OriginalFileName: | |
| ProductName: | Throttle |
| ProductVersion: | 1.0.0.1 |
Total processes
139
Monitored processes
7
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
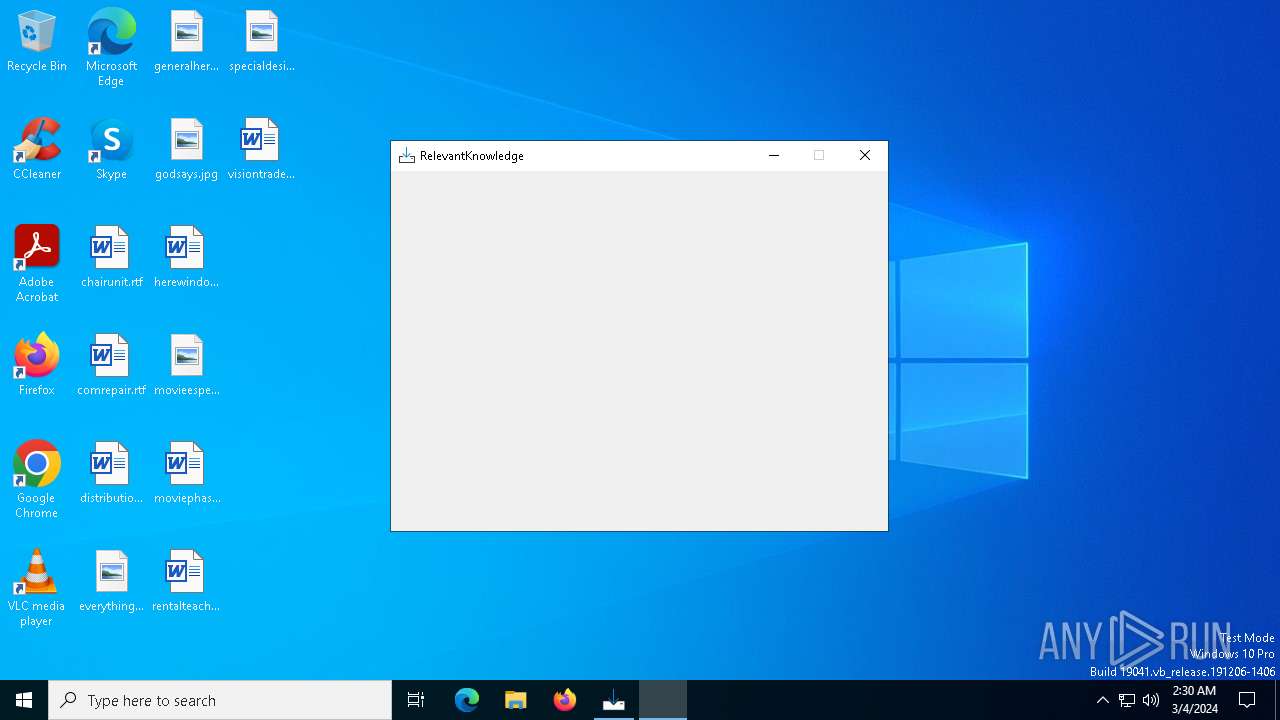
| 1816 | "C:\Users\admin\AppData\Local\Temp\is-ARVI9.tmp\rk_setup.exe" -c: 3033 -lang: 1 -tpi: PGWARE_THROTTLE | C:\Users\admin\AppData\Local\Temp\is-ARVI9.tmp\rk_setup.exe | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | ||||||||||||
User: admin Company: TMRG Integrity Level: HIGH Description: RelevantKnowledge Setup Setup Exit code: 0 Version: 1.1.0 Modules
| |||||||||||||||
| 2168 | "C:\Users\admin\AppData\Local\Temp\is-BQOJR.tmp\rk_setup.tmp" /SL5="$80158,2145894,832512,C:\Users\admin\AppData\Local\Temp\is-ARVI9.tmp\rk_setup.exe" -c: 3033 -lang: 1 -tpi: PGWARE_THROTTLE | C:\Users\admin\AppData\Local\Temp\is-BQOJR.tmp\rk_setup.tmp | rk_setup.exe | ||||||||||||
User: admin Company: TMRG Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2664 | "C:\Users\admin\AppData\Local\Temp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe" /SPAWNWND=$90272 /NOTIFYWND=$11004C | C:\Users\admin\AppData\Local\Temp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | ||||||||||||
User: admin Company: PGWARE LLC Integrity Level: HIGH Description: Throttle Setup Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2696 | "C:\Users\admin\AppData\Local\Temp\is-K87LT.tmp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp" /SL5="$11004C,4523637,832512,C:\Users\admin\AppData\Local\Temp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe" | C:\Users\admin\AppData\Local\Temp\is-K87LT.tmp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | — | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe | |||||||||||
User: admin Company: PGWARE LLC Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 5456 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6056 | "C:\Users\admin\AppData\Local\Temp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe" | C:\Users\admin\AppData\Local\Temp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe | explorer.exe | ||||||||||||
User: admin Company: PGWARE LLC Integrity Level: MEDIUM Description: Throttle Setup Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 6660 | "C:\Users\admin\AppData\Local\Temp\is-OB6UM.tmp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp" /SL5="$8013C,4523637,832512,C:\Users\admin\AppData\Local\Temp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe" /SPAWNWND=$90272 /NOTIFYWND=$11004C | C:\Users\admin\AppData\Local\Temp\is-OB6UM.tmp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe | ||||||||||||
User: admin Company: PGWARE LLC Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
5 646
Read events
5 632
Write events
14
Delete events
0
Modification events
| (PID) Process: | (6660) 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 041A0000D13EBCD9DB6DDA01 | |||
| (PID) Process: | (6660) 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 7A7B65A6DFF8C983C739831ABFE3935134A43A32547A372AFD45CAADB1DC5428 | |||
| (PID) Process: | (6660) 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6660) 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6660) 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6660) 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6660) 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2168) rk_setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: 78080000EDF269DCDB6DDA01 | |||
| (PID) Process: | (2168) rk_setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: DDB13A88161E5DC477AA583A75EB6744AD8225CE75E5E9A01F27C44DE8D749AD | |||
| (PID) Process: | (2168) rk_setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
Executable files
11
Suspicious files
2
Text files
0
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6660 | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:2217DC59D985360607D7B1039D8E614D | SHA256:BE00F5005B9E1A9033927FA9B83CB1C981C246C2F91B8F5AE048D6E8C858D5A3 | |||
| 6056 | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.exe | C:\Users\admin\AppData\Local\Temp\is-K87LT.tmp\13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | executable | |
MD5:034372FA86E28E4DCF1A1D44A9CFCECD | SHA256:F399902F50EECA069DCBCB9F528BA159BCA0EC6072B1216D53BAA6062A38810C | |||
| 2168 | rk_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-EKEO6.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 1816 | rk_setup.exe | C:\Users\admin\AppData\Local\Temp\is-BQOJR.tmp\rk_setup.tmp | executable | |
MD5:63B305BAA9994EA2A53AD5BD640F3494 | SHA256:A2BDFFBE67FAE5656019BB2ECC2EF708599BF0F10E75FEB64060EBB6553A5352 | |||
| 2168 | rk_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-EKEO6.tmp\libssl-1_1.dll | executable | |
MD5:8B15CE1C87750425A63C8CD6EAE55563 | SHA256:149291BF3C739B11AE425C6611786D36D74FDCBC60BCD7B2C555B59AA0C7017D | |||
| 2168 | rk_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-EKEO6.tmp\libcrypto-1_1.dll | executable | |
MD5:B7AFBC5E66B68D3AD0336DC3A8382E7C | SHA256:64D0C2B6ED879509F5E861B97A0CF5E6F9A6763032D9E5C53F39AF08B0951AAE | |||
| 2168 | rk_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-EKEO6.tmp\CallbackAdapter.dll | executable | |
MD5:94FA1BDAEB995239E459ACA68B5FCD39 | SHA256:F6A85D1DBD81D7796386CA058086147898782A156662EDE5C57377F5CFD1F5F7 | |||
| 2168 | rk_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-EKEO6.tmp\curl-ca-bundle.crt | binary | |
MD5:D8771605855EF563748A3D599854B8DF | SHA256:9FA396BA8B6FDB0A1D5350408A1814CB7658BC08B34F70423939709FAD8480FB | |||
| 2168 | rk_setup.tmp | C:\Users\admin\AppData\Local\Temp\is-EKEO6.tmp\libcurl.dll | executable | |
MD5:454C6F6641125F8D0D95496F0A27D932 | SHA256:279D32802C5613928239D5E743362E36FA4AA719A8A07805CDC3B8A9D6665AEC | |||
| 6660 | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | C:\Users\admin\AppData\Local\Temp\is-ARVI9.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
32
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5928 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
6748 | svchost.exe | GET | 200 | 23.53.41.88:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.01 Kb | unknown |
2052 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2464 | svchost.exe | GET | 200 | 104.115.228.157:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
6660 | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | binary | 1.37 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3848 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
6748 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6896 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5928 | svchost.exe | 40.126.32.72:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6660 | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | 13.32.121.51:443 | dpd.securestudies.com | AMAZON-02 | US | unknown |
6660 | 13902861132376c808e304074e537f22435976567bd3e48b959363108ab79389.tmp | 18.66.142.79:80 | ocsp.rootca1.amazontrust.com | AMAZON-02 | US | unknown |
5928 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
6748 | svchost.exe | 23.53.41.88:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
2168 | rk_setup.tmp | 13.32.121.51:443 | dpd.securestudies.com | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dpd.securestudies.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |