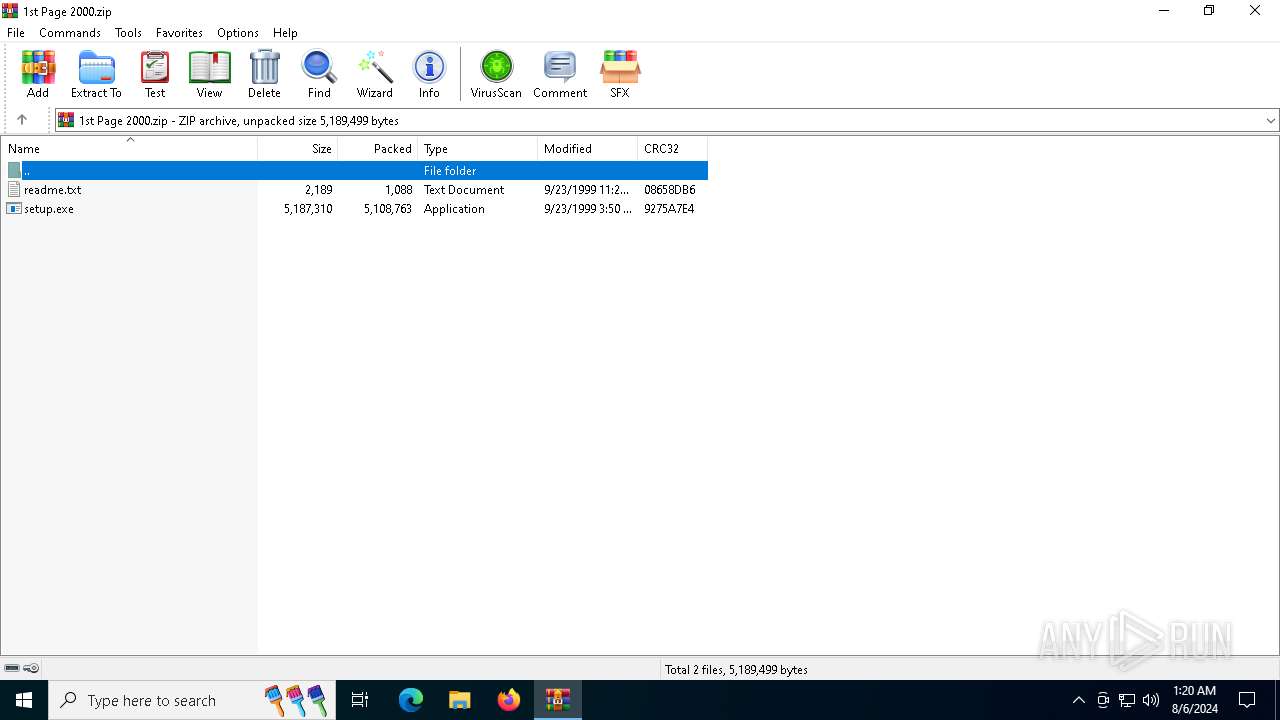
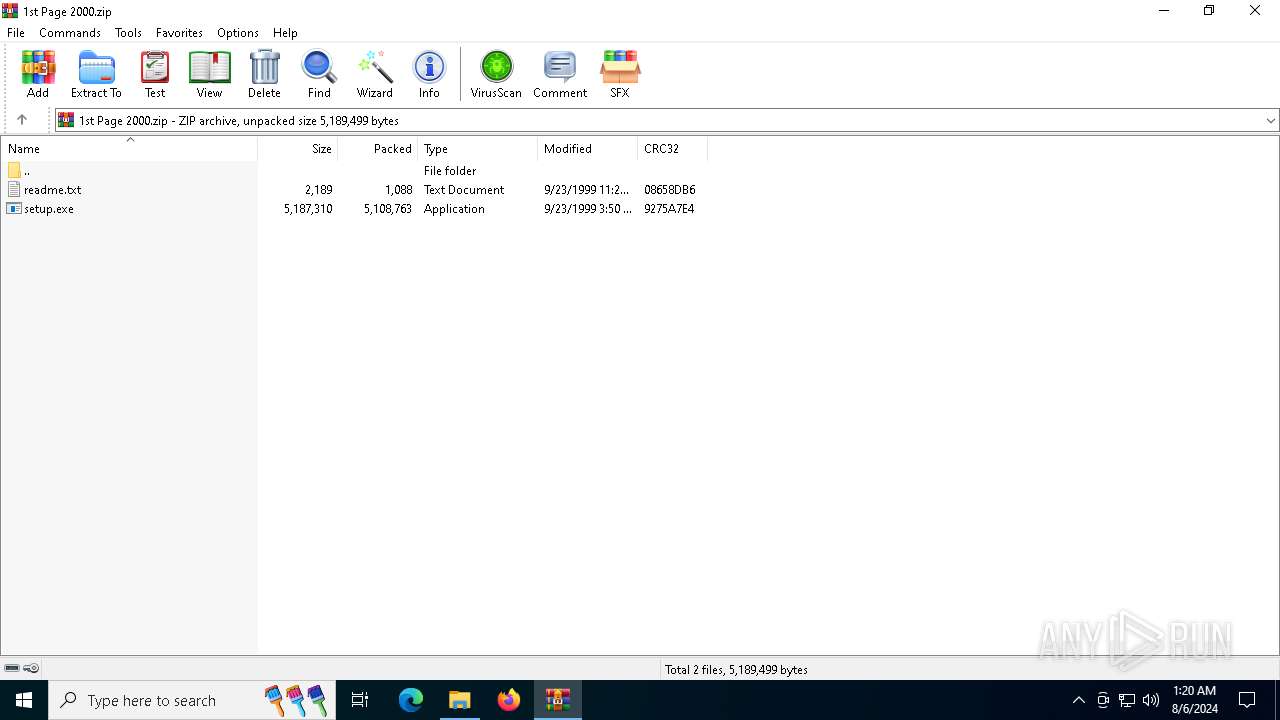
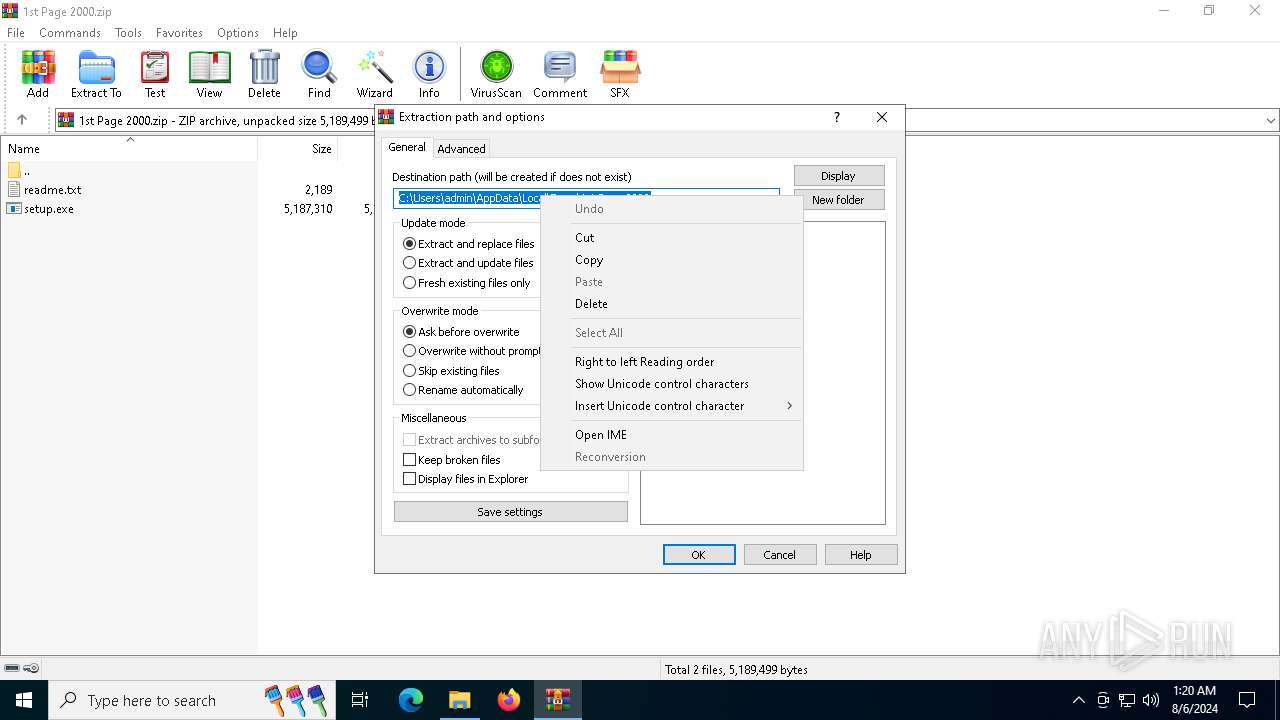
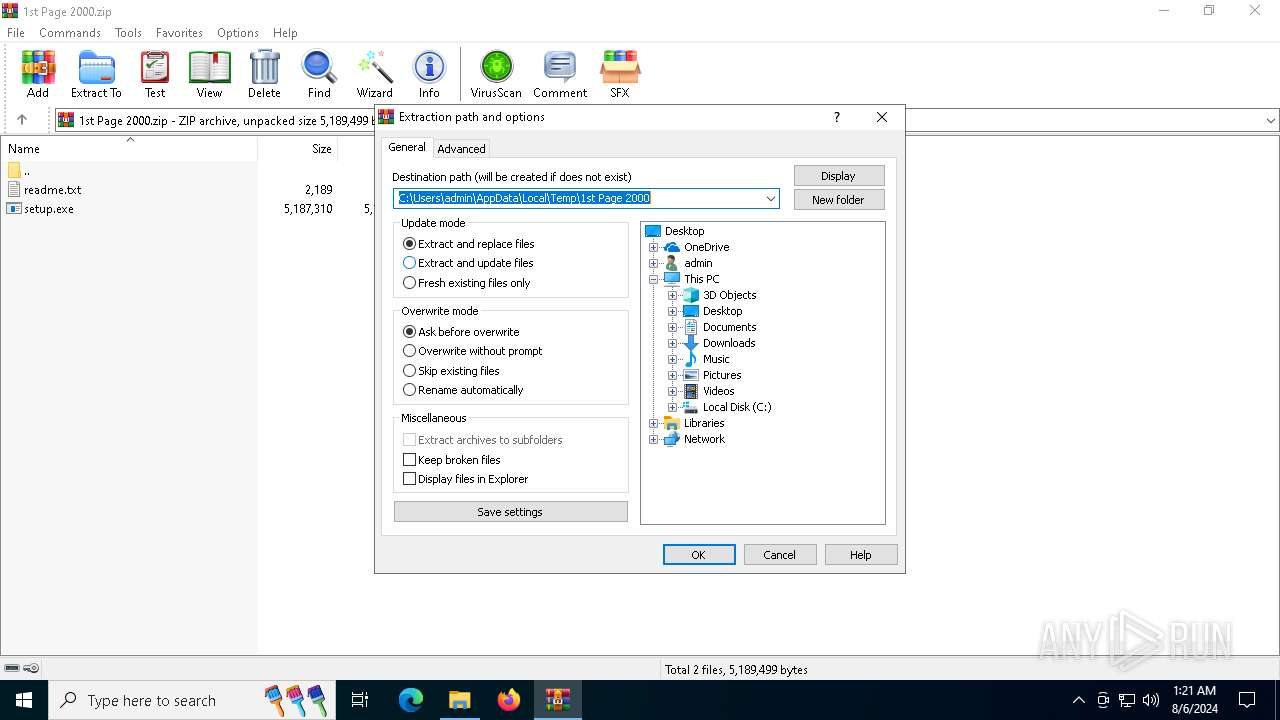
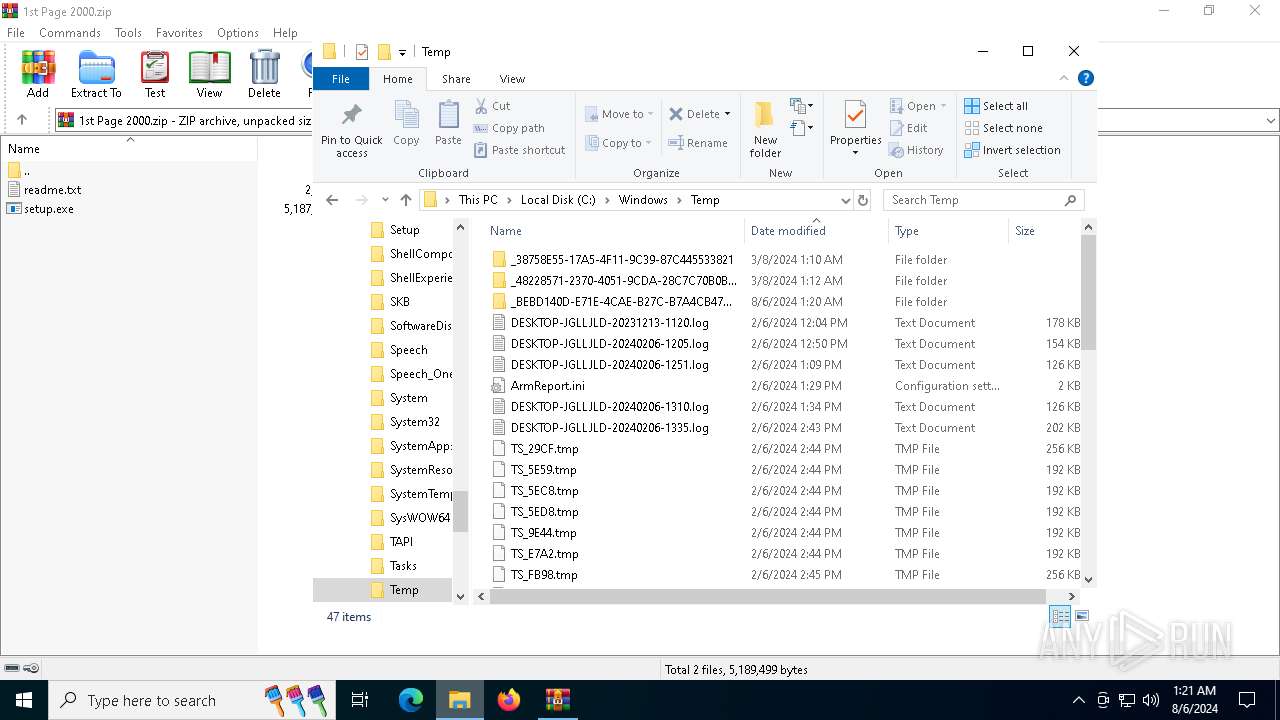
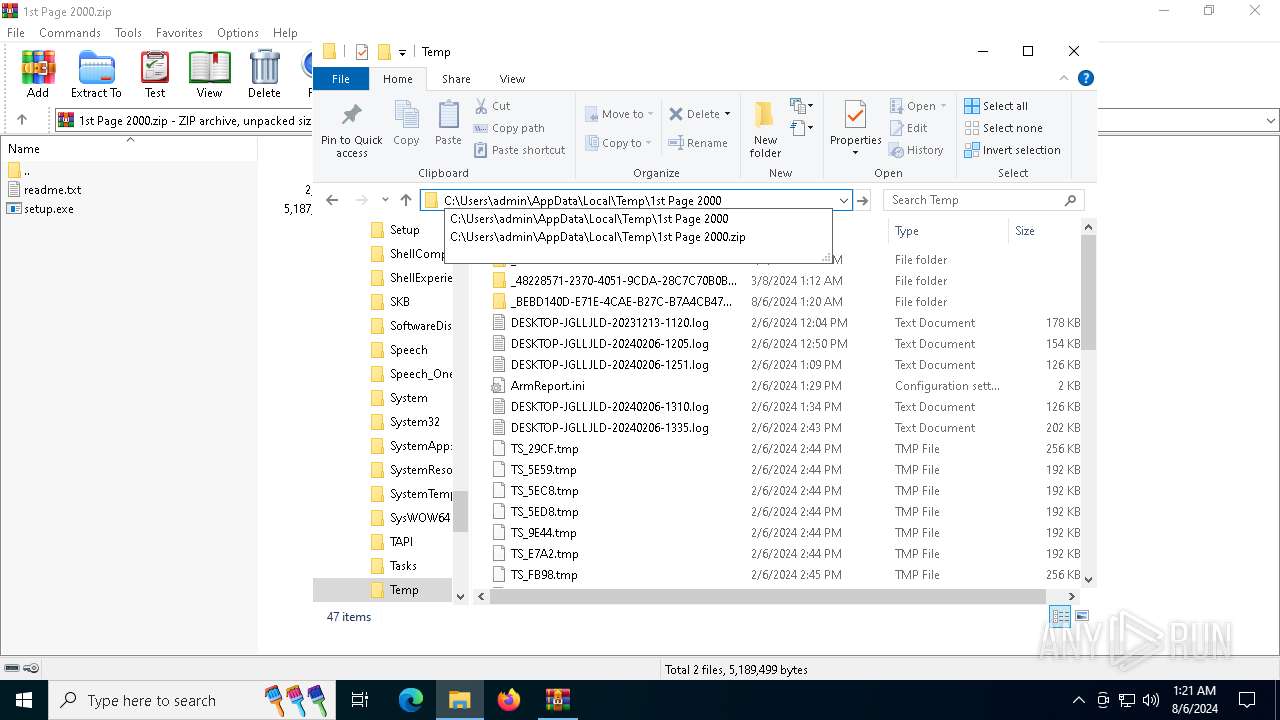
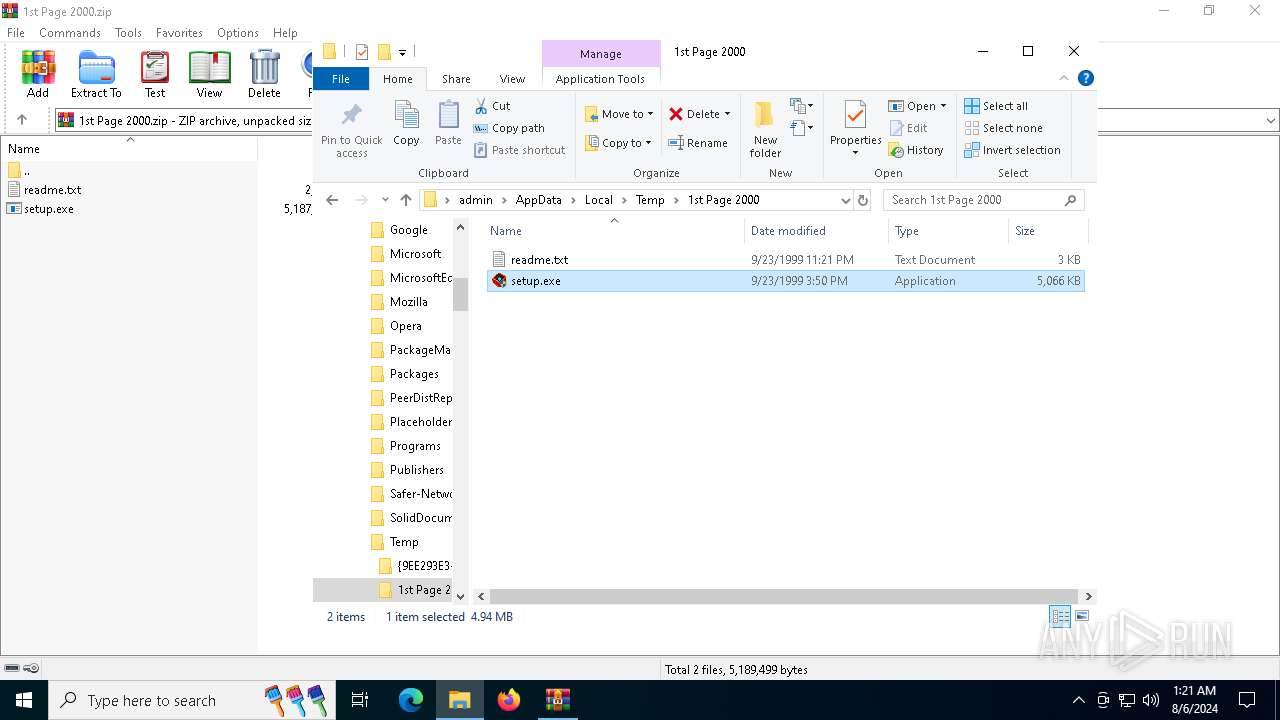
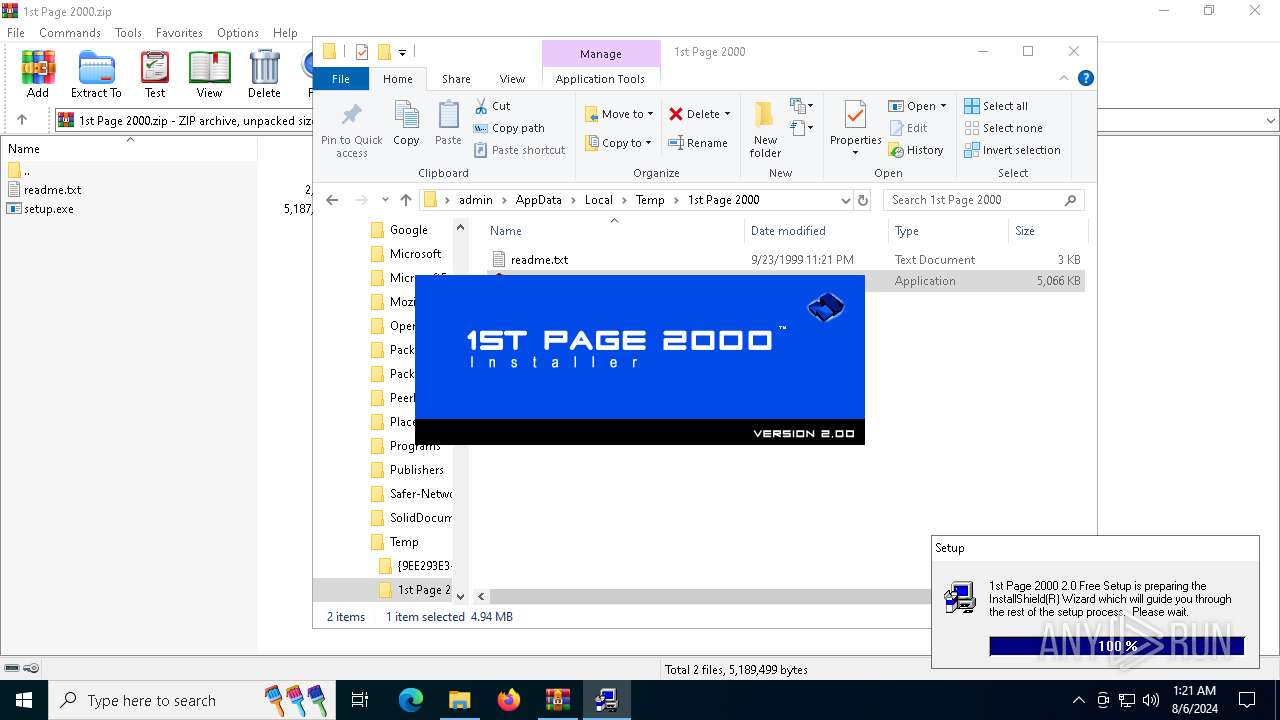
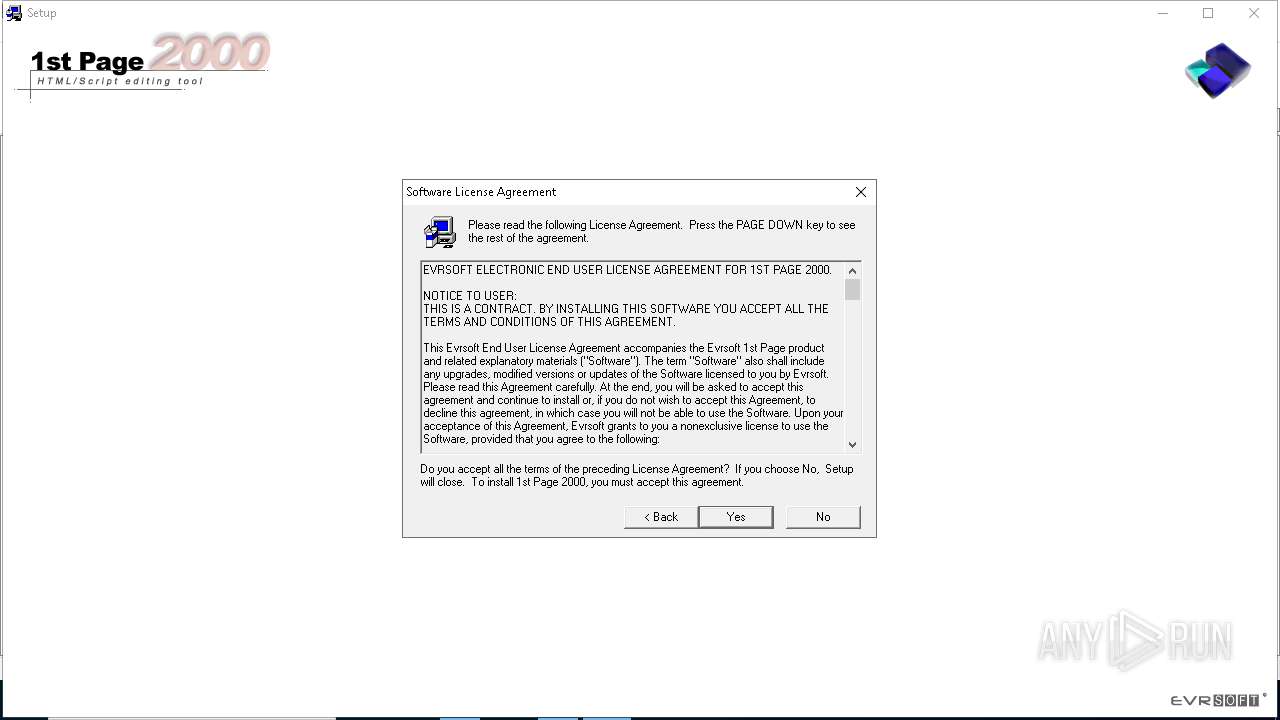
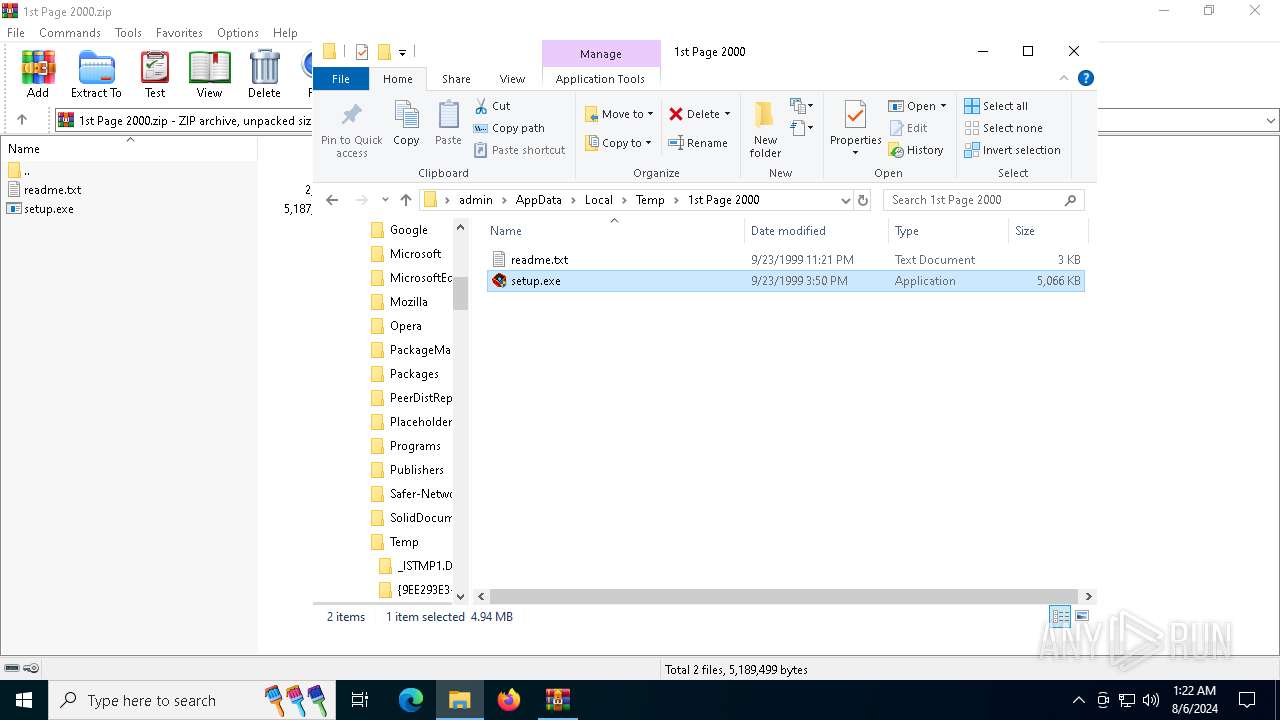
| File name: | 1st Page 2000.zip |
| Full analysis: | https://app.any.run/tasks/97a948c6-b48a-40d3-a095-0a5e52937bae |
| Verdict: | Malicious activity |
| Analysis date: | August 06, 2024, 01:19:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 382A8160A90E45E37BF5E3E75849933F |
| SHA1: | F416A64C3CADF52A2E4EA8C5B3A552D48A885137 |
| SHA256: | 137BD412FEFE2B3C63C815F1B14729979C9E51253227BC3CCA6B9387C55F00EA |
| SSDEEP: | 98304:Wzf0Kgh2dNSlnJitHHhuXg4IhsHg3ldidPXRGgmKpbiZRfikYHreiyoHBxU9R:WzcTWSzQBuXpggg3loIgmQbERfpYyidS |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 7056)
- setup.exe (PID: 6840)
- setup.exe (PID: 1680)
- _INS5176._MP (PID: 5500)
SUSPICIOUS
Creates file in the systems drive root
- setup.exe (PID: 6840)
- _isdel.exe (PID: 6968)
Executable content was dropped or overwritten
- setup.exe (PID: 6840)
- setup.exe (PID: 1680)
- _INS5176._MP (PID: 5500)
Starts application with an unusual extension
- setup.exe (PID: 1680)
Creates a software uninstall entry
- _INS5176._MP (PID: 5500)
Reads the Windows owner or organization settings
- _INS5176._MP (PID: 5500)
Process drops legitimate windows executable
- _INS5176._MP (PID: 5500)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7056)
Checks supported languages
- setup.exe (PID: 6840)
- setup.exe (PID: 1680)
- _INS5176._MP (PID: 5500)
- _isdel.exe (PID: 6968)
- TextInputHost.exe (PID: 6484)
Reads the computer name
- setup.exe (PID: 6840)
- setup.exe (PID: 1680)
- _INS5176._MP (PID: 5500)
- TextInputHost.exe (PID: 6484)
Manual execution by a user
- setup.exe (PID: 6840)
- setup.exe (PID: 888)
Create files in a temporary directory
- setup.exe (PID: 6840)
- setup.exe (PID: 1680)
- _INS5176._MP (PID: 5500)
Creates files in the program directory
- _INS5176._MP (PID: 5500)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1999:09:23 23:21:16 |
| ZipCRC: | 0x08658db6 |
| ZipCompressedSize: | 1088 |
| ZipUncompressedSize: | 2189 |
| ZipFileName: | readme.txt |
Total processes
146
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\Users\admin\AppData\Local\Temp\1st Page 2000\setup.exe" | C:\Users\admin\AppData\Local\Temp\1st Page 2000\setup.exe | — | explorer.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: MEDIUM Description: PackageForTheWeb Stub Exit code: 3221226540 Version: 2.02.001 Modules
| |||||||||||||||
| 1680 | "C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\SETUP.EXE" -isw64"C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\SETUP.EXE" /SMS | C:\Windows\SysWOW64\InstallShield\setup.exe | setup.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: 32-bit Setup Launcher Exit code: 0 Version: 5, 54, 001, 0 Modules
| |||||||||||||||
| 1884 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3044 | C:\WINDOWS\system32\DllHost.exe /Processid:{4D111E08-CBF7-4F12-A926-2C7920AF52FC} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5500 | C:\Users\admin\AppData\Local\Temp\_ISTMP1.DIR\_INS5176._MP | C:\Users\admin\AppData\Local\Temp\_ISTMP1.DIR\_INS5176._MP | setup.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: InstallShield Engine Exit code: 0 Version: 5.10.145.0 Modules
| |||||||||||||||
| 6484 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6840 | "C:\Users\admin\AppData\Local\Temp\1st Page 2000\setup.exe" | C:\Users\admin\AppData\Local\Temp\1st Page 2000\setup.exe | explorer.exe | ||||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: PackageForTheWeb Stub Exit code: 0 Version: 2.02.001 Modules
| |||||||||||||||
| 6968 | C:\Windows\SysWOW64\InstallShield\_ISDEL.EXE | C:\Windows\SysWOW64\InstallShield\_isdel.exe | — | setup.exe | |||||||||||
User: admin Company: InstallShield Software Corporation Integrity Level: HIGH Description: 32-bit InstallShield Deleter. Exit code: 0 Version: 5, 51, 138, 0 Modules
| |||||||||||||||
| 7056 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1st Page 2000.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
9 593
Read events
9 580
Write events
13
Delete events
0
Modification events
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1st Page 2000.zip | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7056) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1st Page 2000 | |||
| (PID) Process: | (5500) _INS5176._MP | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\1st Page 2000 2.00 Free |
| Operation: | write | Name: | UninstallString |
Value: C:\WINDOWS\IsUninst.exe -f"C:\Program Files (x86)\Evrsoft\1st Page 2000\Uninst.isu" | |||
Executable files
24
Suspicious files
18
Text files
915
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\pftw1.pkg | — | |
MD5:— | SHA256:— | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\data1.cab | — | |
MD5:— | SHA256:— | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\lang.dat | text | |
MD5:90E64689804B4F4B0197C07290965A3C | SHA256:EB1E8EA9707BC2F6EB4B4CC4D022E6ACF0B79E0C66F8406478269EEAB05693B8 | |||
| 7056 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\1st Page 2000\readme.txt | text | |
MD5:6E39CD6A1F6F3F3B794D0B357ABC7470 | SHA256:E5959028EB324D8931FB755AE9758F9EB60A8EB1DF35B60A09734D4AE9966DEC | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\setup.ins | ins | |
MD5:6DB07FD6D02F852ABF510D889EF5DF44 | SHA256:1F739CC7E8DAA6A3E3579CC5EC1522BDEB6BB13269B17858A3AADAFFC9CD0FE6 | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\os.dat | text | |
MD5:AF1D8D9435CB10FE2F4B4215EAF6BEC4 | SHA256:2F148CB3D32AB70A315B5A853761C2702B6DEEF6FFAFF6AA76D513B945CE7EF7 | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\_user1.cab | compressed | |
MD5:AFC16881FE36055865E4EE791D13C845 | SHA256:0486214420B0CEAC407E99844BAFC215735651455C3EDF46F1E9BB9A29E3B7BE | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\_INST32I.EX_ | binary | |
MD5:4251C8E7962CE3CA98FDCBE096C1D270 | SHA256:065443568C396564EC51C72F54F81990C49E4B0CECE780ACBFC6A7494B65A3E0 | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\SETUP.EXE | executable | |
MD5:AFE10D250B2C1850B37827C1D4E01EEF | SHA256:26ADEA53490125FD31E300DA97EF48B9DDC583753789051746B9A31406B418CF | |||
| 6840 | setup.exe | C:\Users\admin\AppData\Local\Temp\pftC0F5~tmp\SETUP.BMP | image | |
MD5:4A8D4DC0885AFEE94CE27FA3DF1F0CFE | SHA256:4C03646DA2C18AC70BD95A4E3C33DAAB1BEDEA10A03FAFF6CF92117B27A2EA78 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
54
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6420 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6384 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6140 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6444 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5600 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5336 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
6140 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6384 | backgroundTaskHost.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |