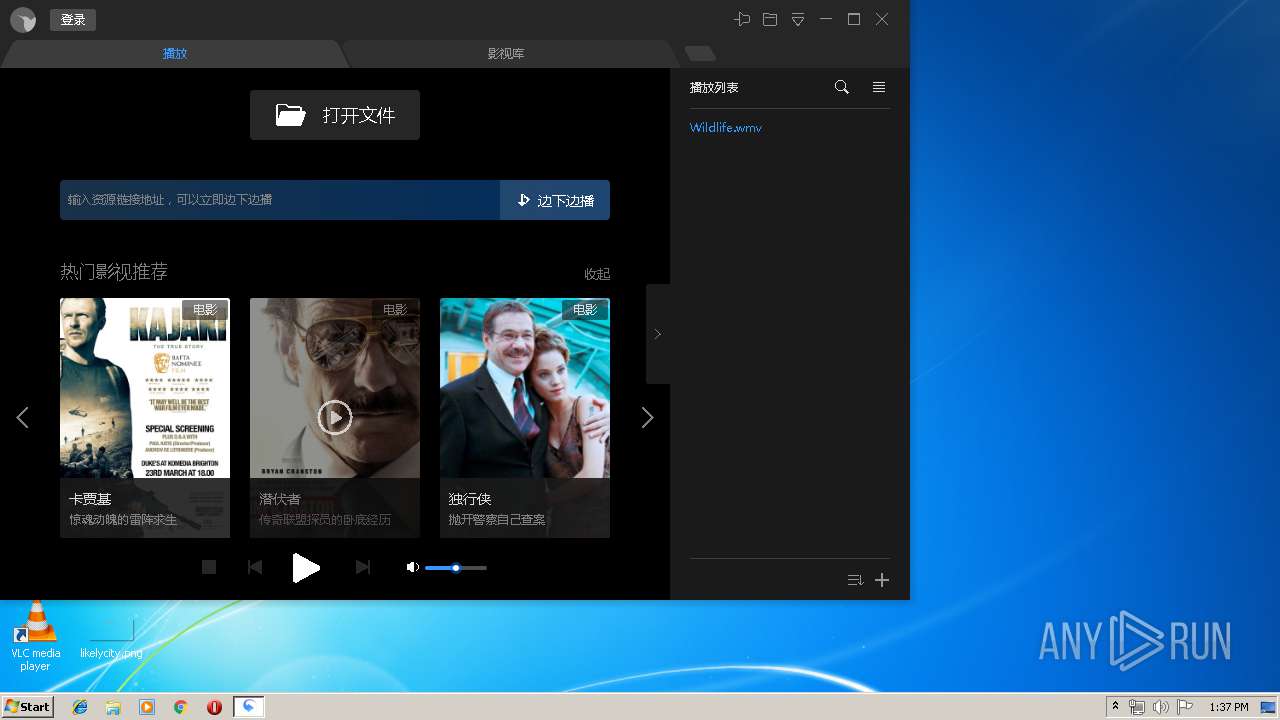
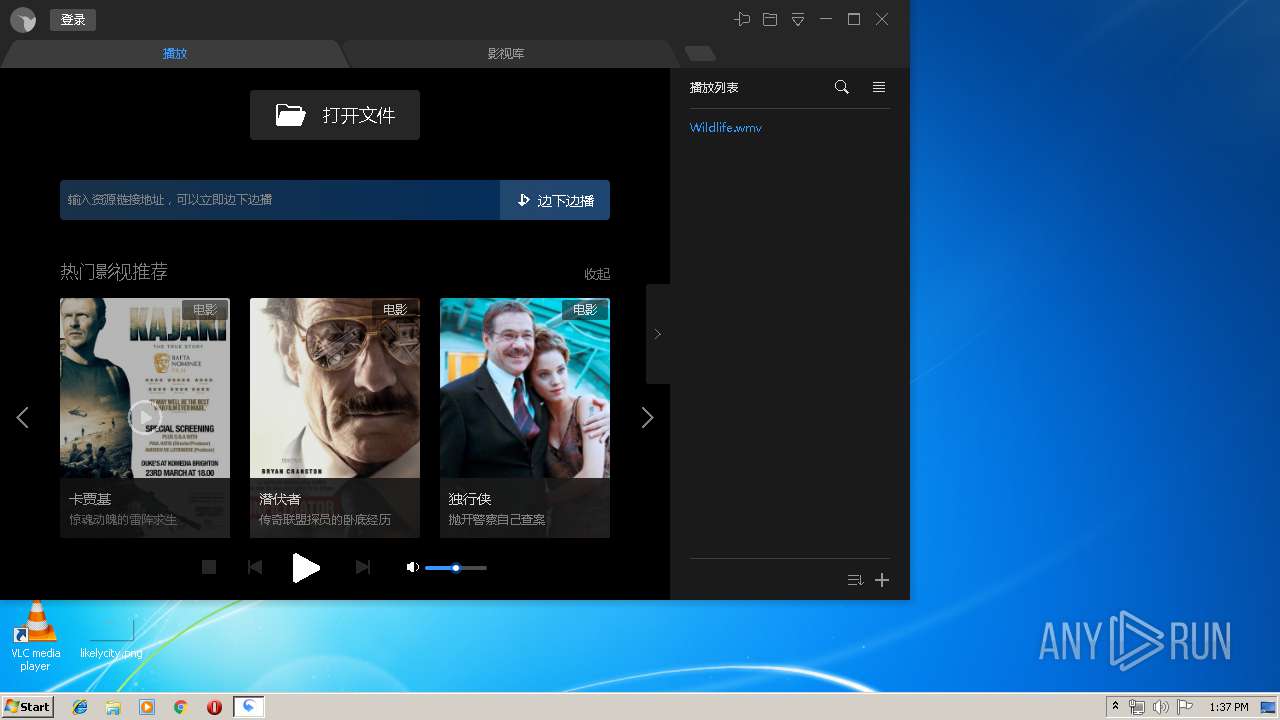
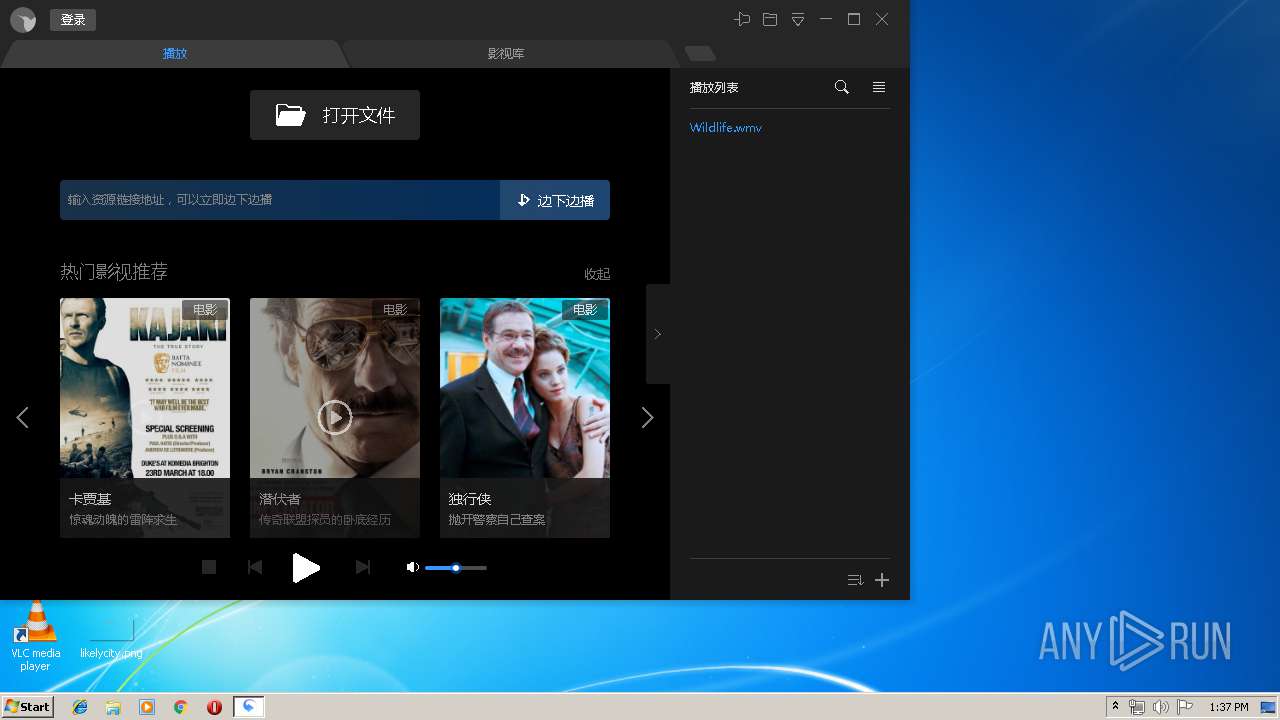
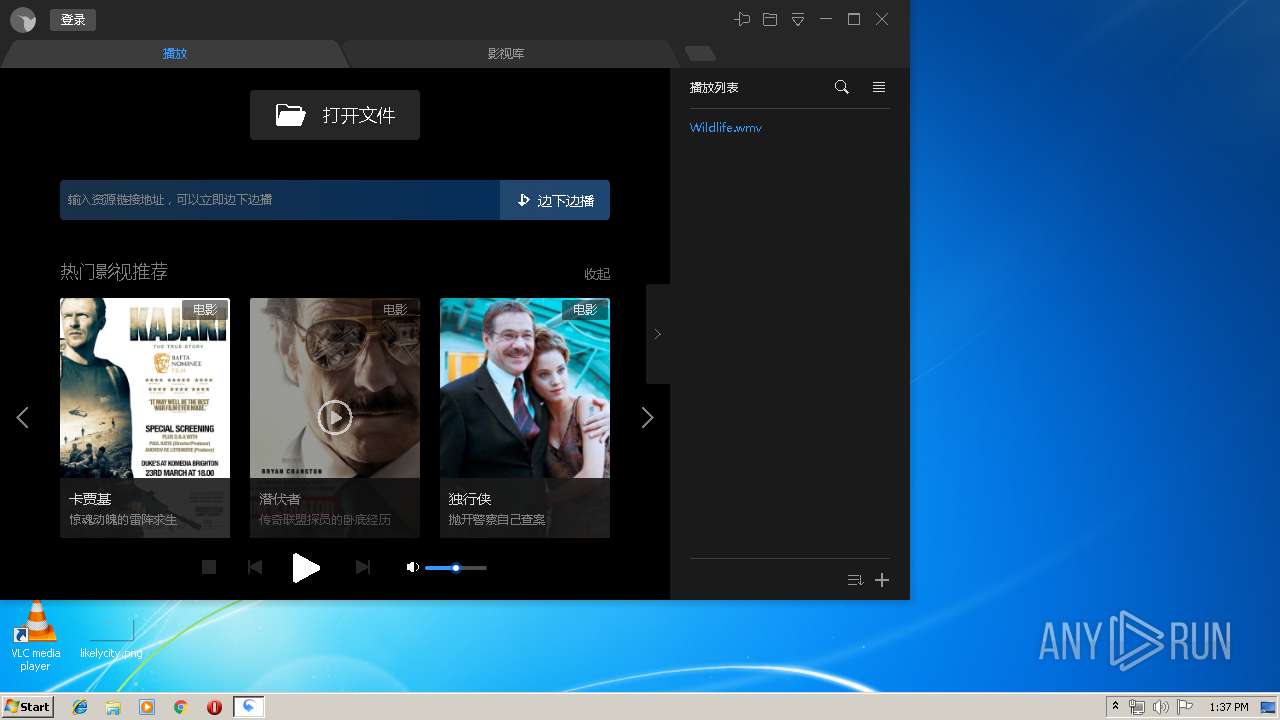
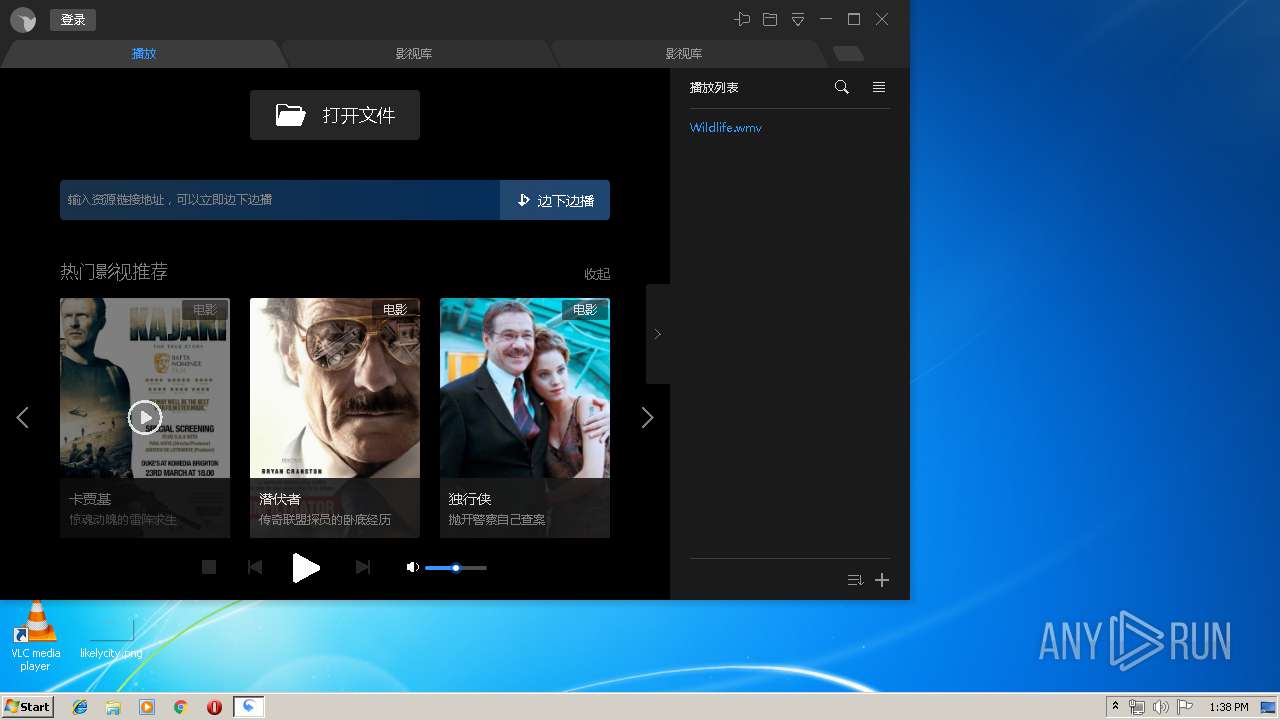
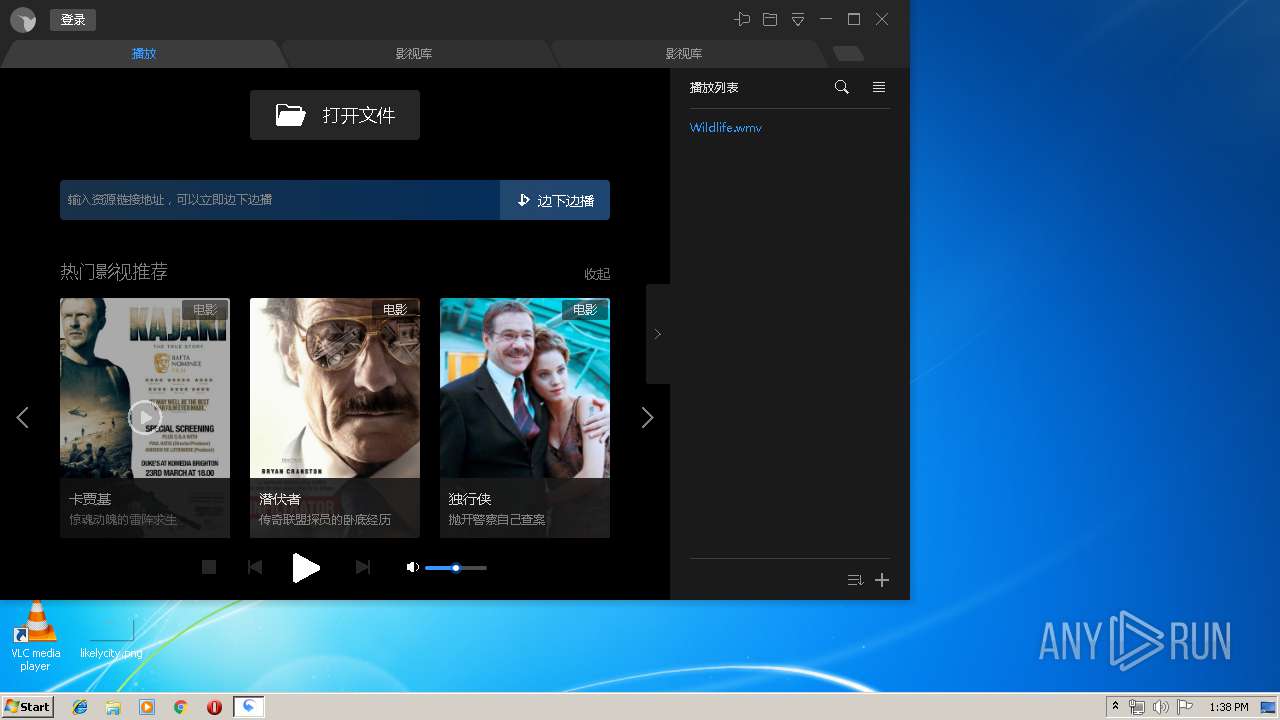
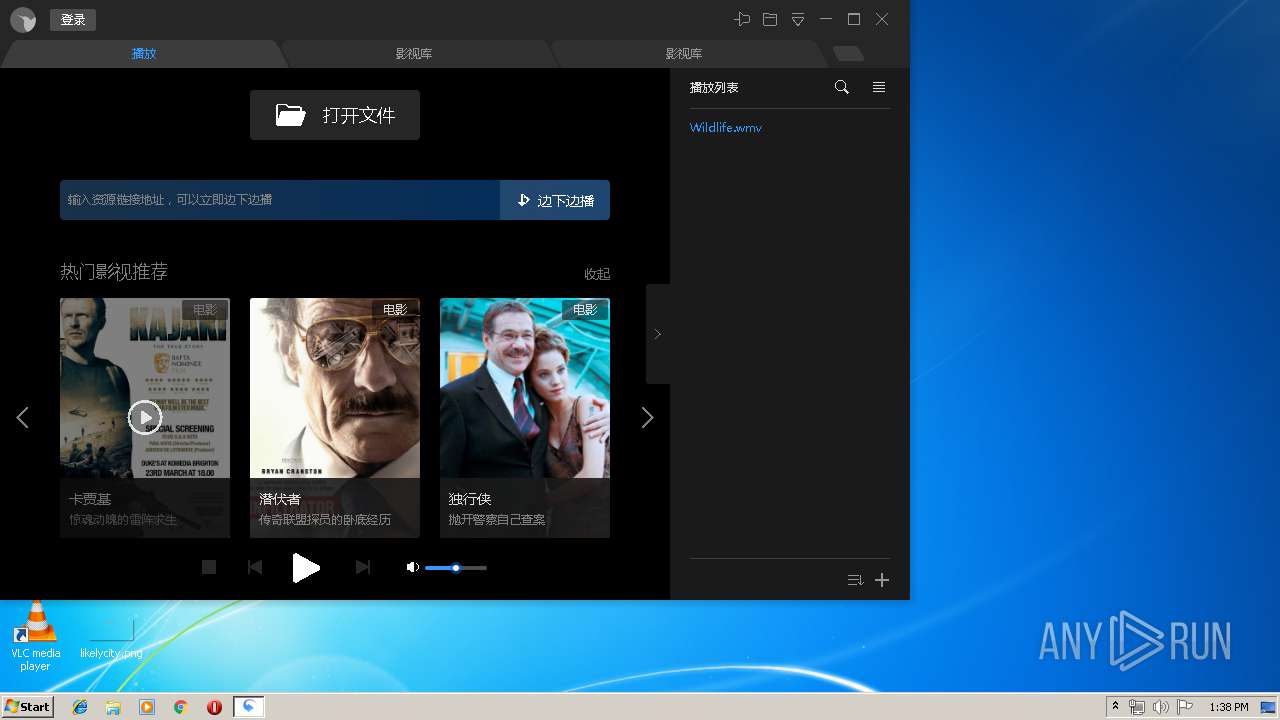
| URL: | http://xmp.down.sandai.net/xmp/XMPSetup6.0.6.304xl.exe |
| Full analysis: | https://app.any.run/tasks/8c2d5044-8728-44f0-ab00-830bc5046e85 |
| Verdict: | Malicious activity |
| Analysis date: | September 17, 2019, 12:34:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | BD47AC7E49714C3A04C7C6FD17873601 |
| SHA1: | D0DC514710B8FE5406EDD118A322D6092B41A7B9 |
| SHA256: | 135F252FA7CD67ED916D2BF5EB93A462DB0375DC5FE3DB04486600F7FB881F82 |
| SSDEEP: | 3:N1KGIXK4njLNIWFLWZn:CGd4njGPZn |
MALICIOUS
Application was dropped or rewritten from another process
- DownloadSDKServer.exe (PID: 3380)
- Win7AppId.exe (PID: 3284)
- Win7AppId.exe (PID: 2328)
- Win7AppId.exe (PID: 2556)
- Win7AppId.exe (PID: 2008)
- Win7AppId.exe (PID: 2388)
- Win7AppId.exe (PID: 1080)
- Xmp.exe (PID: 2340)
- Xmp.exe (PID: 3636)
- XmpLiveUD.exe (PID: 3544)
- DownloadSDKServer.exe (PID: 4000)
- Xmp.exe (PID: 3712)
- XmpLiveUD.exe (PID: 1508)
- Xmp.exe (PID: 392)
- Xmp.exe (PID: 3596)
- Xmp.exe (PID: 460)
- XmpLiveUD.exe (PID: 2760)
- XmpLiveUD.exe (PID: 2512)
Loads dropped or rewritten executable
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
- DownloadSDKServer.exe (PID: 3380)
- Xmp.exe (PID: 2340)
- SearchProtocolHost.exe (PID: 2860)
- regsvr32.exe (PID: 3204)
- Xmp.exe (PID: 3636)
- DownloadSDKServer.exe (PID: 4000)
- XmpLiveUD.exe (PID: 3544)
- Xmp.exe (PID: 3712)
- XmpLiveUD.exe (PID: 1508)
- Xmp.exe (PID: 392)
- Xmp.exe (PID: 460)
- xlbrowsershell.exe (PID: 2056)
- Xmp.exe (PID: 3596)
- xlbrowsershell.exe (PID: 3136)
- xlbrowsershell.exe (PID: 3012)
- XmpLiveUD.exe (PID: 2760)
- XmpLiveUD.exe (PID: 2512)
- xlbrowsershell.exe (PID: 2364)
- xlbrowsershell.exe (PID: 3412)
Registers / Runs the DLL via REGSVR32.EXE
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
Changes the autorun value in the registry
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
Changes settings of System certificates
- Xmp.exe (PID: 2340)
SUSPICIOUS
Uses NETSH.EXE for network configuration
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
Low-level read access rights to disk partition
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
- DownloadSDKServer.exe (PID: 3380)
- Xmp.exe (PID: 2340)
- DownloadSDKServer.exe (PID: 4000)
- XmpLiveUD.exe (PID: 3544)
- Xmp.exe (PID: 3712)
- XmpLiveUD.exe (PID: 1508)
- Xmp.exe (PID: 3636)
- Xmp.exe (PID: 392)
- XmpLiveUD.exe (PID: 2760)
- XmpLiveUD.exe (PID: 2512)
- Xmp.exe (PID: 3596)
Creates a software uninstall entry
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
Reads CPU info
- DownloadSDKServer.exe (PID: 3380)
- DownloadSDKServer.exe (PID: 4000)
Creates files in the user directory
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
- Xmp.exe (PID: 2340)
Executable content was dropped or overwritten
- regsvr32.exe (PID: 3204)
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
- XmpLiveUD.exe (PID: 3544)
- XmpLiveUD.exe (PID: 2760)
Creates COM task schedule object
- regsvr32.exe (PID: 3204)
Modifies the open verb of a shell class
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
- Xmp.exe (PID: 3636)
Application launched itself
- Xmp.exe (PID: 2340)
- Xmp.exe (PID: 3636)
- xlbrowsershell.exe (PID: 2056)
Creates files in the program directory
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
- Xmp.exe (PID: 3636)
- DownloadSDKServer.exe (PID: 4000)
- Xmp.exe (PID: 2340)
- xlbrowsershell.exe (PID: 2056)
Starts itself from another location
- XmpLiveUD.exe (PID: 3544)
- XmpLiveUD.exe (PID: 2760)
Adds / modifies Windows certificates
- Xmp.exe (PID: 2340)
INFO
Application launched itself
- iexplore.exe (PID: 3416)
Reads Internet Cache Settings
- iexplore.exe (PID: 3416)
- iexplore.exe (PID: 3920)
Changes internet zones settings
- iexplore.exe (PID: 3416)
Dropped object may contain Bitcoin addresses
- XMPSetup6.0.6.304xl[1].exe (PID: 3568)
Reads the hosts file
- Xmp.exe (PID: 2340)
- xlbrowsershell.exe (PID: 2056)
Reads settings of System Certificates
- Xmp.exe (PID: 2340)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
86
Monitored processes
37
Malicious processes
18
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe" --type=renderer --no-sandbox --primordial-pipe-token=84EC2DA86B49F0F4ACAF33B9B36CA040 --lang=en-US --app-user-model-id="C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe" --app-path="C:\Program Files\Thunder Network\Xmp\Program\resources\app" --node-integration=true --webview-tag=true --no-sandbox --preload="C:\Program Files\Thunder Network\Xmp\Program\resources\app/out/common-preload.js" --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553 --disable-accelerated-video-decode --disable-gpu-compositing --service-request-channel-token=84EC2DA86B49F0F4ACAF33B9B36CA040 --renderer-client-id=5 --mojo-platform-channel-handle=2592 /prefetch:1 | C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe | — | Xmp.exe | |||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: MEDIUM Description: 迅雷影音 Exit code: 0 Version: 6,0,6,304 Modules
| |||||||||||||||
| 460 | "C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe" --type=renderer --no-sandbox --primordial-pipe-token=D5278D3ED649CB10DEC69811A36772B2 --lang=en-US --app-user-model-id="C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe" --app-path="C:\Program Files\Thunder Network\Xmp\Program\resources\app" --node-integration=true --webview-tag=true --no-sandbox --preload="C:\Program Files\Thunder Network\Xmp\Program\resources\app/out/common-preload.js" --background-color=#000 --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553 --disable-accelerated-video-decode --disable-gpu-compositing --service-request-channel-token=D5278D3ED649CB10DEC69811A36772B2 --renderer-client-id=9 --mojo-platform-channel-handle=3000 /prefetch:1 | C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe | — | Xmp.exe | |||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: MEDIUM Description: 迅雷影音 Exit code: 0 Version: 6,0,6,304 Modules
| |||||||||||||||
| 1080 | "C:\Program Files\Thunder Network\Xmp\Program\Win7AppId.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\迅雷影音.lnk" "C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe" | C:\Program Files\Thunder Network\Xmp\Program\Win7AppId.exe | — | XMPSetup6.0.6.304xl[1].exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1508 | "C:\Users\admin\AppData\Local\Temp\XLLiveUD\XMP_6.0.6.304\XmpLiveUD.exe" -UpdateMode:l -RestartToInstall | C:\Users\admin\AppData\Local\Temp\XLLiveUD\XMP_6.0.6.304\XmpLiveUD.exe | — | XmpLiveUD.exe | |||||||||||
User: admin Company: 深圳市迅雷网络技术有限公司 Integrity Level: MEDIUM Description: 迅雷影音升级程序 Exit code: 0 Version: 1.2.5.68 Modules
| |||||||||||||||
| 1684 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files\Thunder Network\Xmp\Program\ShlExt_x64.dll" | C:\Windows\System32\regsvr32.exe | — | XMPSetup6.0.6.304xl[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 3 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Thunder Network\Xmp\Program\Win7AppId.exe" "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\迅雷软件\迅雷影音\迅雷影音.lnk" "C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe" | C:\Program Files\Thunder Network\Xmp\Program\Win7AppId.exe | — | XMPSetup6.0.6.304xl[1].exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2056 | --parent_id=3636 --user_agent=Mozilla/5.0 (Windows NT 6.2; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/72.0.3626.121 Safari/537.36 TBC/1.2.8.120 XMP/6.0.6.304 --data_path=C:\Program Files\Thunder Network\Xmp\Program\resources\bin\TBC\Data --enable_sandbox=0 --product_version=6.0.6.304 --peer_id=5254004A04AF038E --launch-start-tick=1661625 | C:\Program Files\Thunder Network\Xmp\Program\resources\bin\TBC\xlbrowsershell.exe | Xmp.exe | ||||||||||||
User: admin Company: ShenZhen Thunder Networking Technologies Ltd. Integrity Level: MEDIUM Description: Xunlei Browser Process Shell Exit code: 0 Version: 1.2.8.120 Modules
| |||||||||||||||
| 2064 | C:\Windows\system32\netsh.exe advfirewall firewall delete rule name="DownloadSDKServer" dir=in action=allow program="C:\Users\admin\AppData\Local\Temp\XmpInstall\6.0.6.304\SDK\DownloadSDKServer.exe" | C:\Windows\system32\netsh.exe | — | XMPSetup6.0.6.304xl[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2164 | C:\Windows\system32\netsh.exe advfirewall firewall delete rule name="DownloadSDKServer" dir=in action=allow program="C:\Users\admin\AppData\Local\Temp\XmpInstall\6.0.6.304\SDK\DownloadSDKServer.exe" | C:\Windows\system32\netsh.exe | — | XMPSetup6.0.6.304xl[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2328 | "C:\Program Files\Thunder Network\Xmp\Program\Win7AppId.exe" "C:\Users\admin\Desktop\迅雷影音.lnk" "C:\Program Files\Thunder Network\Xmp\Program\Xmp.exe" | C:\Program Files\Thunder Network\Xmp\Program\Win7AppId.exe | — | XMPSetup6.0.6.304xl[1].exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
7 310
Read events
3 227
Write events
4 077
Delete events
6
Modification events
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {8594B897-D947-11E9-B86F-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 2 | |||
| (PID) Process: | (3416) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E3070900020011000C0022002B006700 | |||
Executable files
514
Suspicious files
115
Text files
1 416
Unknown types
56
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFFD755B0C11D53970.TMP | — | |
MD5:— | SHA256:— | |||
| 3920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\XY53GTAS\XMPSetup6.0.6.304xl[1].exe | — | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\XMPSetup6.0.6.304xl[1].exe | — | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{8594B898-D947-11E9-B86F-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 3920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019091720190918\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3920 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019091720190918\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
148
DNS requests
94
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3380 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
3380 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
3380 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
3380 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
3920 | iexplore.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/XMPSetup6.0.6.304xl.exe | CN | — | — | malicious |
3380 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
3380 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
4000 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
2340 | Xmp.exe | GET | — | 47.102.50.0:80 | http://xmlconf.rcv.sandai.net/?appid=76 | CN | — | — | unknown |
3380 | DownloadSDKServer.exe | GET | — | 153.35.132.238:80 | http://xmp.down.sandai.net/xmp/tbc_1.2.8.120.zip | CN | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3416 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3920 | iexplore.exe | 153.35.132.238:80 | xmp.down.sandai.net | CHINA UNICOM China169 Backbone | CN | suspicious |
3568 | XMPSetup6.0.6.304xl[1].exe | 140.206.225.241:8099 | stat.download.xunlei.com | China Unicom Shanghai network | CN | suspicious |
3380 | DownloadSDKServer.exe | 47.101.213.251:80 | dconf.xcloud.sandai.net | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3380 | DownloadSDKServer.exe | 47.92.75.245:8000 | hub5u.wap.sandai.net | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
— | — | 47.92.99.221:8000 | hub5pnc.sandai.net | Hangzhou Alibaba Advertising Co.,Ltd. | CN | malicious |
3380 | DownloadSDKServer.exe | 47.92.100.53:8000 | hub5pnc.sandai.net | Hangzhou Alibaba Advertising Co.,Ltd. | CN | malicious |
3380 | DownloadSDKServer.exe | 47.102.63.100:80 | pc.gw.xnet.sandai.net | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3380 | DownloadSDKServer.exe | 123.129.242.221:80 | hub5idx.v6.shub.sandai.net | CHINA UNICOM China169 Backbone | CN | malicious |
3380 | DownloadSDKServer.exe | 153.35.132.238:80 | xmp.down.sandai.net | CHINA UNICOM China169 Backbone | CN | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xmp.down.sandai.net |
| malicious |
www.bing.com |
| whitelisted |
stat.download.xunlei.com |
| malicious |
dconf.xcloud.sandai.net |
| unknown |
hub5pnc.sandai.net |
| malicious |
hub5pn.wap.sandai.net |
| malicious |
hub5u.wap.sandai.net |
| unknown |
hub5pn.sandai.net |
| unknown |
hubciddata.sandai.net |
| malicious |
master.dphub.sandai.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3920 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
— | — | Potential Corporate Privacy Violation | ET P2P BitTorrent DHT ping request |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
3636 | Xmp.exe | Misc activity | SUSPICIOUS [PTsecurity] HTTP GET method with http_client_body (RFC7231) |
Process | Message |
|---|---|
Xmp.exe | BaseFilter(1dbba824): EnumWindows cost time = 0 |
Xmp.exe | BaseFilter(138c5314): EnumWindows cost time = 0 |
Xmp.exe | BaseFilter(1497107c): EnumWindows cost time = 0 |
Xmp.exe | BaseFilter(0f225954): EnumWindows cost time = 0 |
Xmp.exe | BaseFilter(0f522af4): EnumWindows cost time = 0 |
Xmp.exe | BaseFilter(049edcf4): EnumWindows cost time = 0 |
Xmp.exe | BaseFilter(1dbba80c): EnumWindows cost time = 0 |
Xmp.exe | Subtitle: ClearStreams |