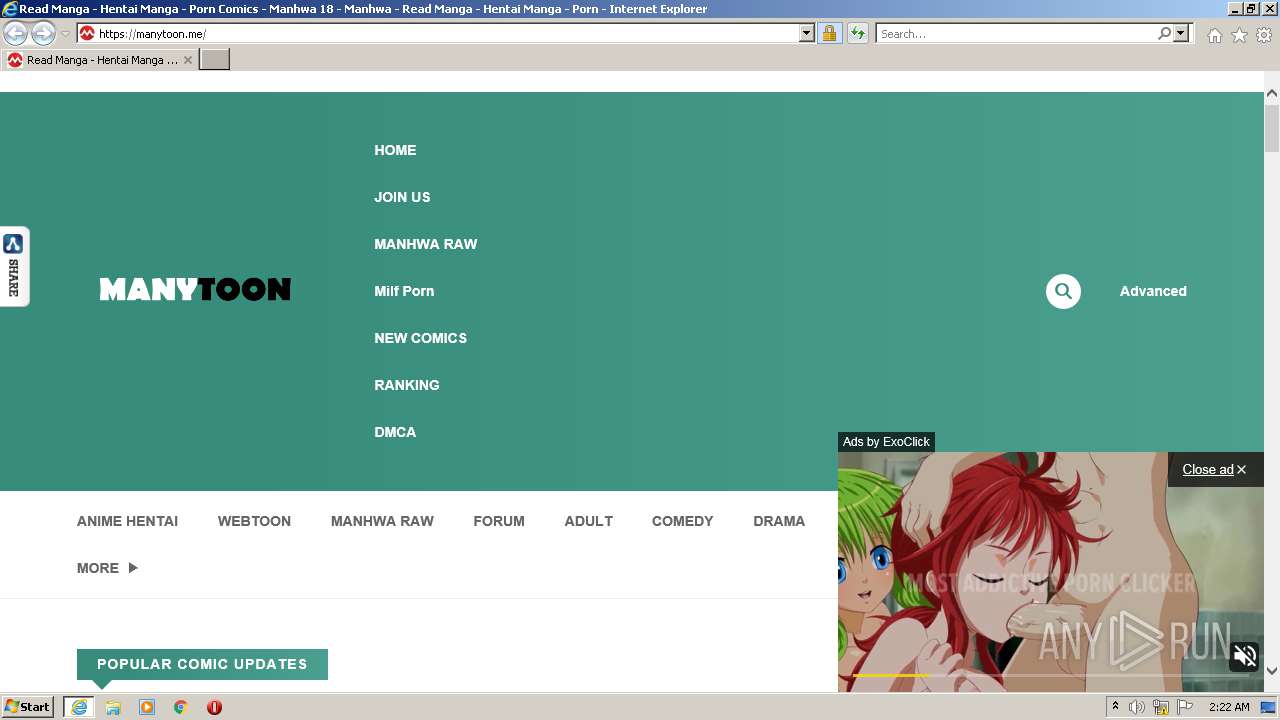
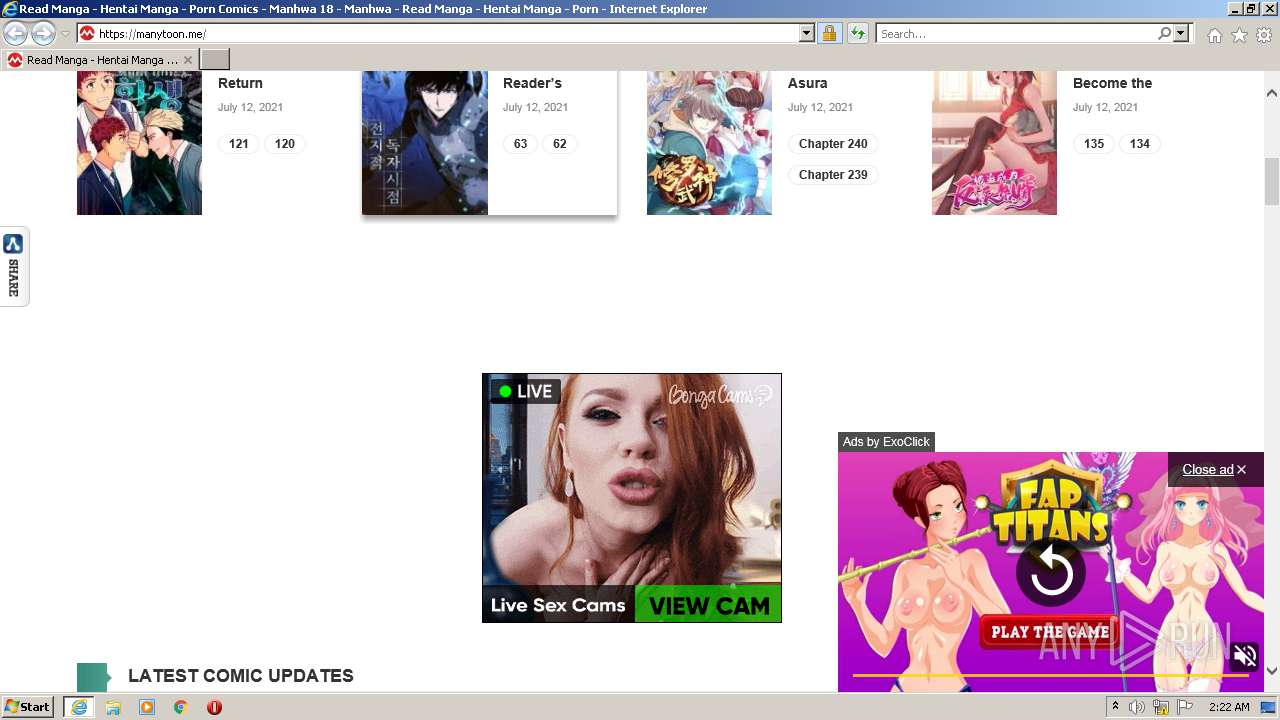
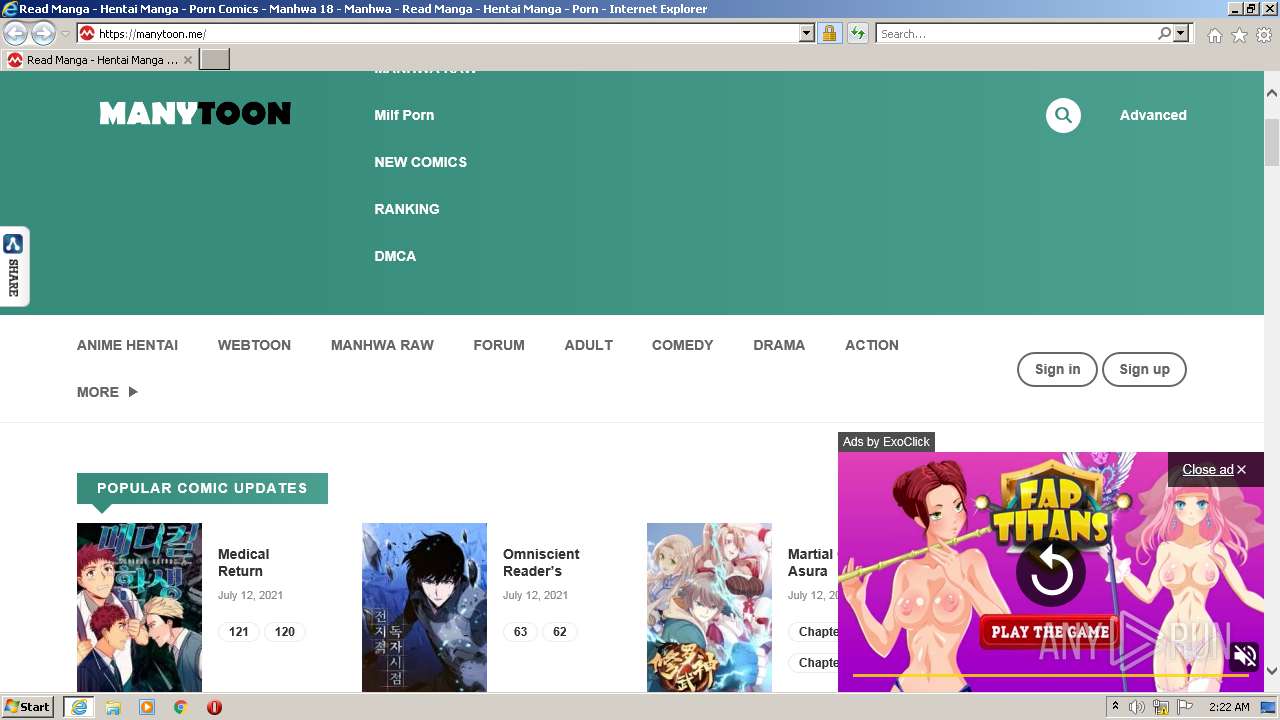
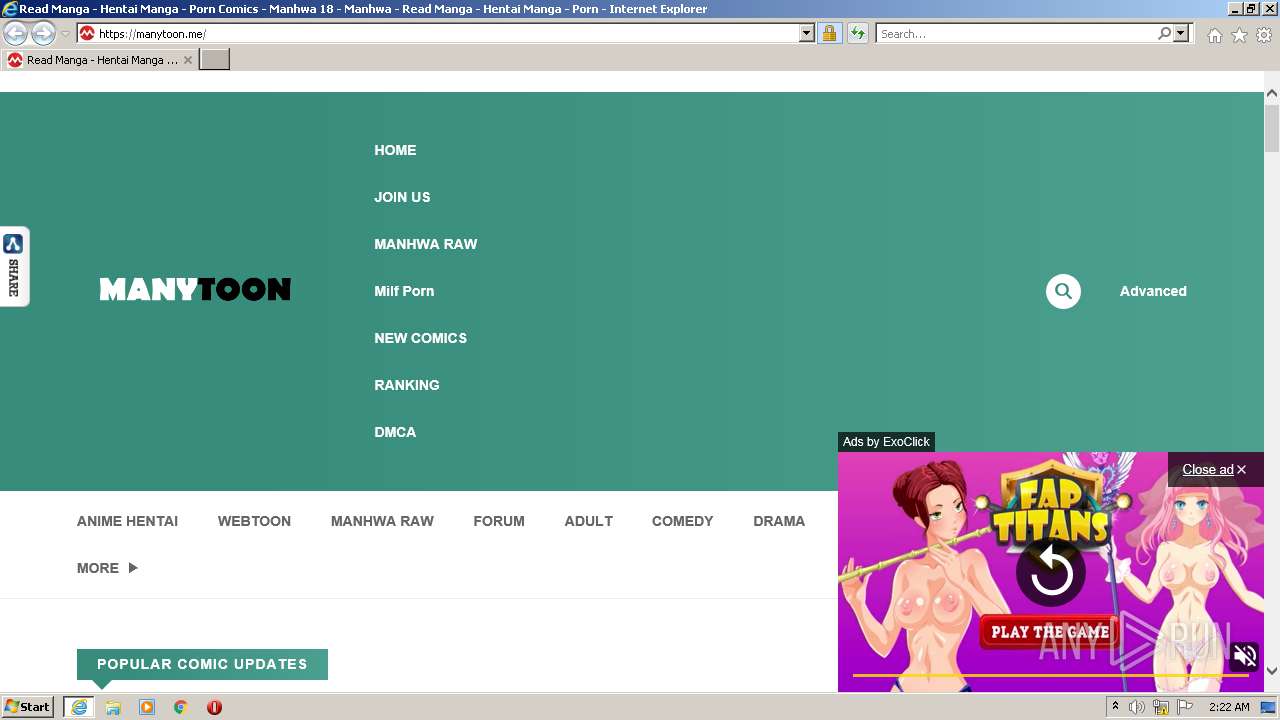
| URL: | https://manytoon.me |
| Full analysis: | https://app.any.run/tasks/09ecc9f2-96aa-4e7a-ba32-7aaf670b96d2 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2021, 01:21:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | D76DCC149EA113C9084AB6DCC35E29B8 |
| SHA1: | D0CEE22442420D4A8E6AC2DAE4AA8F3733555C21 |
| SHA256: | 1345BEE6C68B9D54BCE04799F5CFA8F9867519706EFB22061A574D35240EA47D |
| SSDEEP: | 3:N8cf8An:2cfRn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3924)
INFO
Application launched itself
- iexplore.exe (PID: 352)
Checks supported languages
- iexplore.exe (PID: 352)
- iexplore.exe (PID: 3924)
Reads the computer name
- iexplore.exe (PID: 352)
- iexplore.exe (PID: 3924)
Reads settings of System Certificates
- iexplore.exe (PID: 3924)
- iexplore.exe (PID: 352)
Reads internet explorer settings
- iexplore.exe (PID: 3924)
Checks Windows Trust Settings
- iexplore.exe (PID: 352)
- iexplore.exe (PID: 3924)
Changes internet zones settings
- iexplore.exe (PID: 352)
Creates files in the user directory
- iexplore.exe (PID: 3924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 352 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://manytoon.me" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3924 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:352 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
17 318
Read events
17 190
Write events
128
Delete events
0
Modification events
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30898254 | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30898254 | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (352) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
20
Text files
175
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\QDIZTL2E.htm | html | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\style[1].css | text | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\loaders.min[1].css | text | |
MD5:09917E843F2C87D1B18EC859F7B1B7F9 | SHA256:E90232FA519C3B428277755817C64D59056677920763465A851275ED53CD4D0B | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\style.min[1].css | text | |
MD5:B5D1E2C87B60CE71C3FD90CA27073250 | SHA256:2CD9DE3DD26246204749CFF259BC34E8E6A47AE5D6E4528B9B28C75D68D50CDE | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\bootstrap.min[1].css | text | |
MD5:7CC40C199D128AF6B01E74A28C5900B0 | SHA256:2FF5B959FA9F6B4B1D04D20A37D706E90039176AB1E2A202994D9580BAEEBFD6 | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\csbwfs[1].css | text | |
MD5:D97757223495B1E91B6890474BE6866E | SHA256:27787B47239DF2EF92EC97A31B49A2945640B92E2B3A3379DF66F79B395CD36F | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\slick[1].css | text | |
MD5:D5ADC4DC64F673CE6A0D5801E5339622 | SHA256:21061765237C66C10B48E236063A3497C22D33629E98F8654D1A3B860FA48700 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
73
DNS requests
35
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3924 | iexplore.exe | GET | 200 | 23.55.163.57:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 1.16 Kb | whitelisted |
3924 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
3924 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3924 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3924 | iexplore.exe | GET | 200 | 104.117.200.9:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
3924 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQDGabZ4cXRe1CWOGetVwTBc | US | der | 472 b | whitelisted |
3924 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCECxnvN4MUipXCgAAAADoMbo%3D | US | der | 471 b | whitelisted |
3924 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
3924 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECECAIqYlXEzq2KDLPucq1%2B4M%3D | US | der | 471 b | whitelisted |
3924 | iexplore.exe | GET | 200 | 23.55.163.58:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgMuSalu3Fv4sf7uWd%2B3eOddrA%3D%3D | US | der | 503 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3924 | iexplore.exe | 88.208.59.103:443 | 8016.dendrito.name | DataWeb Global Group B.V. | NL | suspicious |
3924 | iexplore.exe | 142.250.186.72:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3924 | iexplore.exe | 205.185.216.10:443 | a.realsrv.com | Highwinds Network Group, Inc. | US | whitelisted |
3924 | iexplore.exe | 172.67.74.121:443 | manytoon.com | — | US | unknown |
3924 | iexplore.exe | 172.67.171.120:443 | y8z5nv0slz06vj2k5vh6akv7dj2c8aj62zhj2v7zj8vp0zq7fj2gf4mv6zsb.me | — | US | unknown |
3924 | iexplore.exe | 104.16.95.65:443 | static.cloudflareinsights.com | Cloudflare Inc | US | shared |
3924 | iexplore.exe | 23.55.163.57:80 | crl.identrust.com | Akamai International B.V. | US | unknown |
3924 | iexplore.exe | 142.250.185.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3924 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
3924 | iexplore.exe | 104.117.200.9:80 | x1.c.lencr.org | TPG Telecom Limited | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
manytoon.me |
| suspicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
8016.dendrito.name |
| suspicious |
www.googletagmanager.com |
| whitelisted |
manytoon.com |
| malicious |
y8z5nv0slz06vj2k5vh6akv7dj2c8aj62zhj2v7zj8vp0zq7fj2gf4mv6zsb.me |
| unknown |
a.realsrv.com |
| whitelisted |
cdn.tsyndicate.com |
| unknown |
static.cloudflareinsights.com |
| whitelisted |