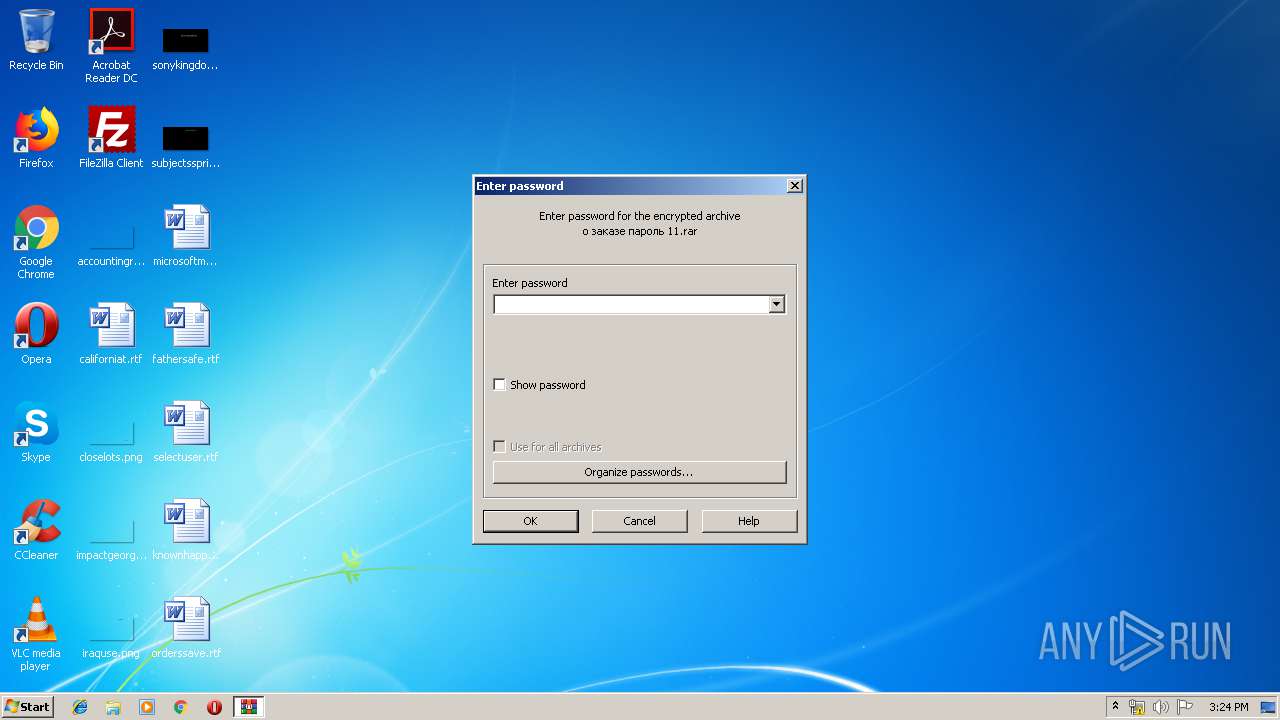
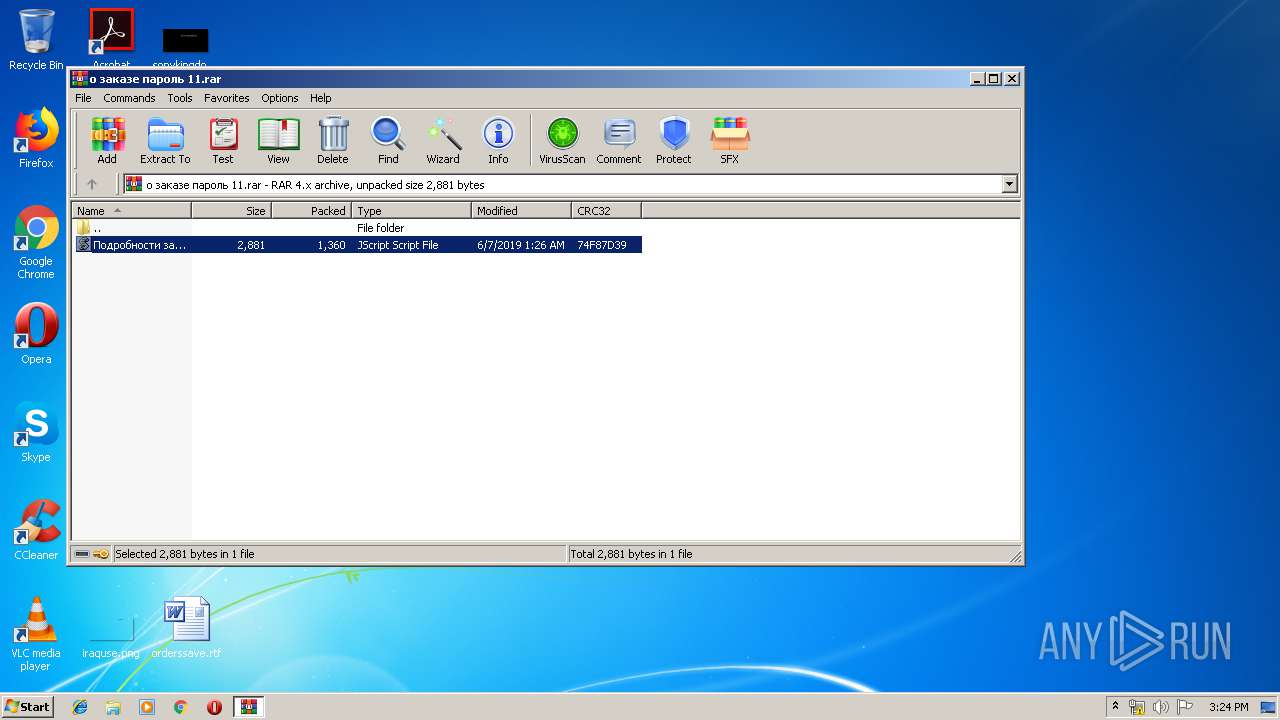
| File name: | о заказе пароль 11.rar |
| Full analysis: | https://app.any.run/tasks/c7bfa294-4213-494f-8529-68876c9fed9a |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 14:23:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, flags: EncryptedBlockHeader |
| MD5: | 1257822B6D3813F981348D07536DE65B |
| SHA1: | 57CBF15E45C5B649B6616519D1930E57E9B0B9CB |
| SHA256: | 133C66B369A3A93F041D6D7FD5C651371CD425552B1E575B58B17A853EC050A6 |
| SSDEEP: | 24:H4FNNHFeUvc+6JNJVzXg6+8XaIVkPnWltuLfFwm3v4kz70Kzg/uP4AWqiEDM5Arl:CNNlNvwM63qIGnWl4LdpzJw1AWqBD4+l |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 1028)
- WScript.exe (PID: 3240)
SUSPICIOUS
Creates files in the user directory
- WScript.exe (PID: 3240)
Executes scripts
- WinRAR.exe (PID: 3144)
Adds / modifies Windows certificates
- WScript.exe (PID: 1028)
- WScript.exe (PID: 3240)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
Total processes
34
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
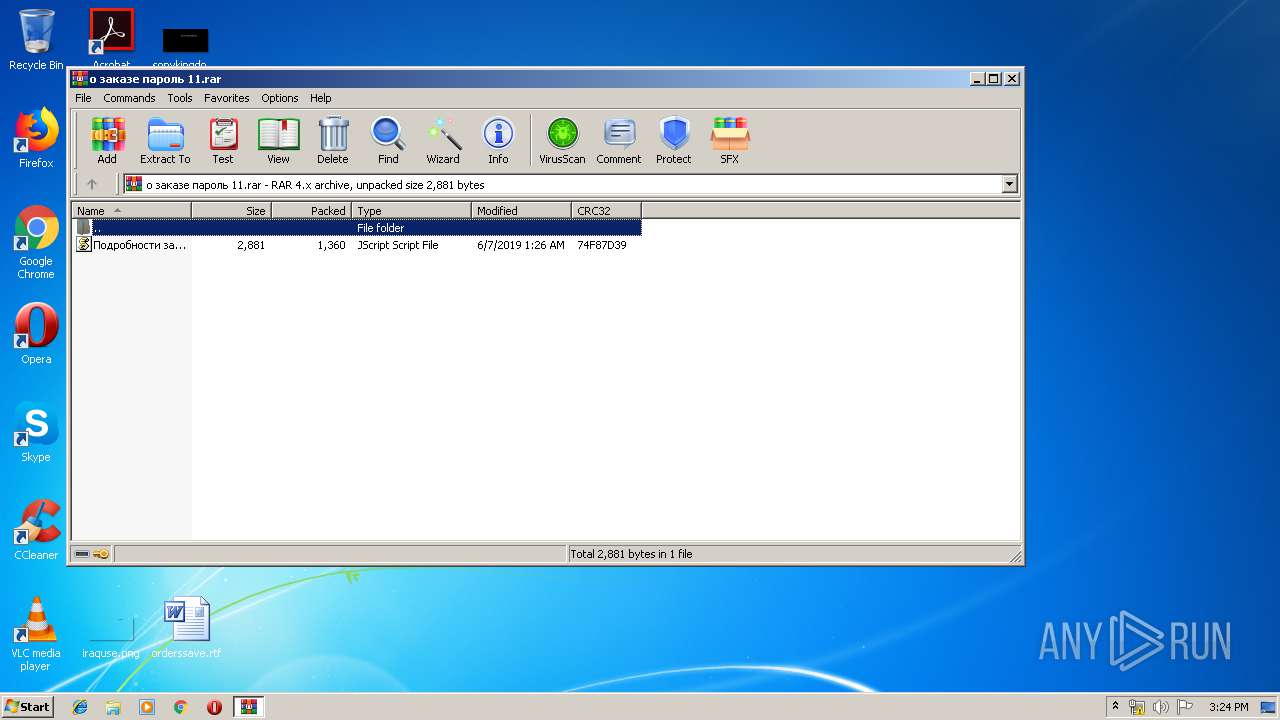
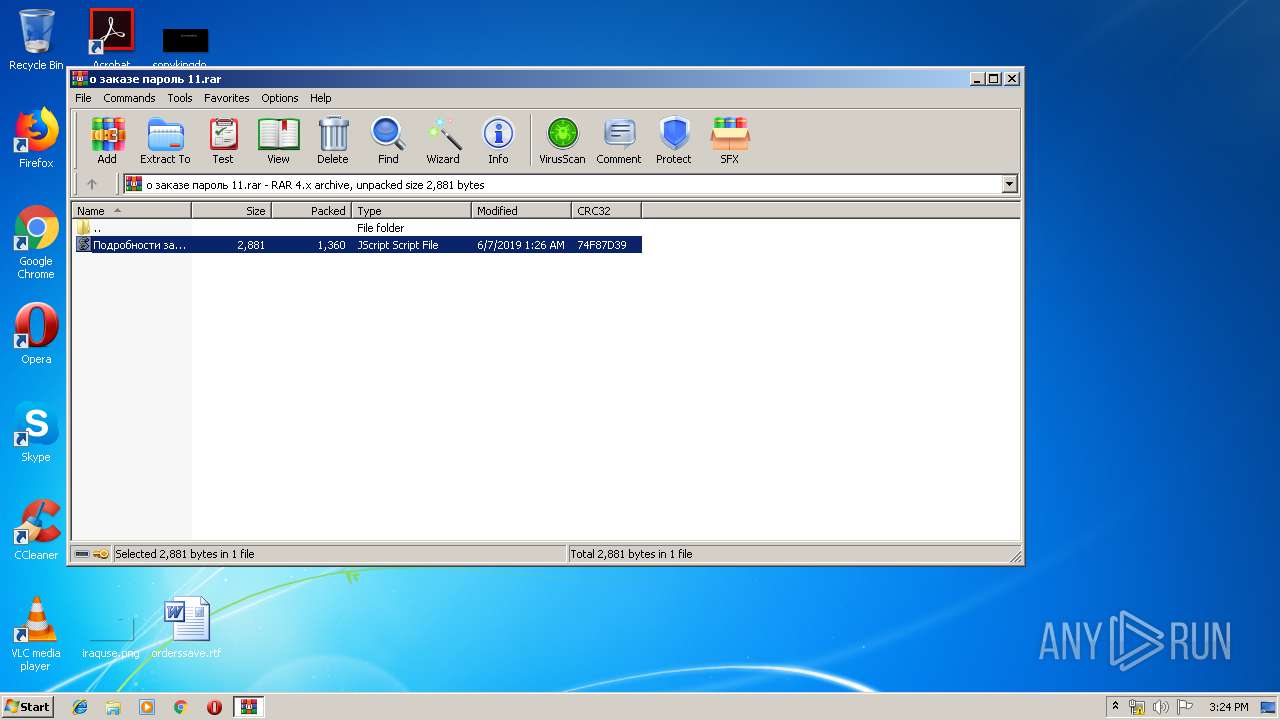
| 1028 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb3144.27686\Подробности заказа.js" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3144 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\о заказе пароль 11.rar" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3240 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb3144.27445\Подробности заказа.js" | C:\Windows\System32\WScript.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
588
Read events
511
Write events
71
Delete events
6
Modification events
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\о заказе пароль 11.rar | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3144) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\wshext.dll,-4804 |
Value: JScript Script File | |||
Executable files
0
Suspicious files
0
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3144.27445\Подробности заказа.js | text | |
MD5:— | SHA256:— | |||
| 3144 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3144.27686\Подробности заказа.js | text | |
MD5:— | SHA256:— | |||
| 3240 | WScript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\IETldCache\index.dat | dat | |
MD5:D7A950FEFD60DBAA01DF2D85FEFB3862 | SHA256:75D0B1743F61B76A35B1FEDD32378837805DE58D79FA950CB6E8164BFA72073A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3240 | WScript.exe | GET | 404 | 109.234.165.77:80 | http://mboavision.rodevdesign.com/.well-known/acme-challenge/1c.jpg | FR | html | 350 b | malicious |
1028 | WScript.exe | GET | 404 | 109.234.165.77:80 | http://mboavision.rodevdesign.com/.well-known/acme-challenge/1c.jpg | FR | html | 350 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3240 | WScript.exe | 62.173.145.104:443 | easyplay.io | JSC Internet-Cosmos | RU | malicious |
1028 | WScript.exe | 62.173.145.104:443 | easyplay.io | JSC Internet-Cosmos | RU | malicious |
3240 | WScript.exe | 109.234.165.77:80 | mboavision.rodevdesign.com | o2switch SARL | FR | suspicious |
1028 | WScript.exe | 109.234.165.77:80 | mboavision.rodevdesign.com | o2switch SARL | FR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
easyplay.io |
| malicious |
mboavision.rodevdesign.com |
| malicious |