| File name: | terminal.exe |
| Full analysis: | https://app.any.run/tasks/5a9fa701-d671-44c2-bcd3-5c40c1672a24 |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2018, 21:07:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 2AA9985EAC6FFDBA057EBD70777E248D |
| SHA1: | D605BBC5B2D65097E4BB51BCA96097C3D28262C9 |
| SHA256: | 131D0E531F0C7557D5D55F76F03873DED962782B5481522314781894E76374A5 |
| SSDEEP: | 393216:ivLb6mjJi6NwXuJYraA/VLkdHjXQGQeV9QH:qLfFiZX2Yr/VLk/n3a |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads internet explorer settings
- terminal.exe (PID: 2216)
Reads Internet Cache Settings
- terminal.exe (PID: 2216)
Changes IE settings (feature browser emulation)
- terminal.exe (PID: 2216)
Reads the cookies of Google Chrome
- terminal.exe (PID: 2216)
Executable content was dropped or overwritten
- terminal.exe (PID: 2216)
Reads the cookies of Mozilla Firefox
- terminal.exe (PID: 2216)
Creates files in the user directory
- terminal.exe (PID: 2216)
INFO
Reads settings of System Certificates
- terminal.exe (PID: 2216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1970:06:09 20:18:24+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 6497792 |
| InitializedDataSize: | 12629504 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xde0423 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.0.0.1147 |
| ProductVersionNumber: | 4.0.0.1147 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | https://www.metaquotes.net |
| CompanyName: | MetaQuotes Software Corp. |
| FileDescription: | MetaTrader |
| FileVersion: | 4.0.0.1147 |
| InternalName: | MetaTrader |
| LegalCopyright: | © 2000-2018, MetaQuotes Software Corp. |
| LegalTrademarks: | MetaTrader® |
| ProductName: | MetaTrader |
| ProductVersion: | 4.0.0.1147 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 09-Jun-1970 19:18:24 |
| Detected languages: |
|
| Debug artifacts: |
|
| Comments: | https://www.metaquotes.net |
| CompanyName: | MetaQuotes Software Corp. |
| FileDescription: | MetaTrader |
| FileVersion: | 4.0.0.1147 |
| InternalName: | MetaTrader |
| LegalCopyright: | © 2000-2018, MetaQuotes Software Corp. |
| LegalTrademarks: | MetaTrader® |
| ProductName: | MetaTrader |
| ProductVersion: | 4.0.0.1147 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000138 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 8 |
| Time date stamp: | 09-Jun-1970 19:18:24 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0063244C | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.rdata | 0x00634000 | 0x000FA19E | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.data | 0x0072F000 | 0x000B241C | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
_RDATA | 0x007E2000 | 0x000005E0 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.cod0 | 0x007E3000 | 0x0059664A | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.cod1 | 0x00D7A000 | 0x00C02EA0 | 0x00C03000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.98315 |
.reloc | 0x0197D000 | 0x00000624 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.72396 |
.rsrc | 0x0197E000 | 0x00A826D6 | 0x00127200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.53205 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.18261 | 2150 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 4.62163 | 2216 | Latin 1 / Western European | UNKNOWN | RT_ICON |
3 | 3.79688 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
4 | 3.31633 | 7336 | Latin 1 / Western European | UNKNOWN | RT_ICON |
5 | 3.94507 | 3240 | Latin 1 / Western European | UNKNOWN | RT_ICON |
6 | 2.81563 | 872 | Latin 1 / Western European | UNKNOWN | RT_ICON |
7 | 0 | 52 | Latin 1 / Western European | UNKNOWN | RT_STRING |
8 | 5.26905 | 4264 | Latin 1 / Western European | UNKNOWN | RT_ICON |
9 | 2.78683 | 1128 | Latin 1 / Western European | UNKNOWN | RT_ICON |
10 | 3.65502 | 1384 | Latin 1 / Western European | UNKNOWN | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
CRYPT32.dll |
GDI32.dll |
IMM32.dll |
IPHLPAPI.DLL |
KERNEL32.dll |
MSIMG32.dll |
OLEACC.dll |
OLEAUT32.dll |
Total processes
32
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
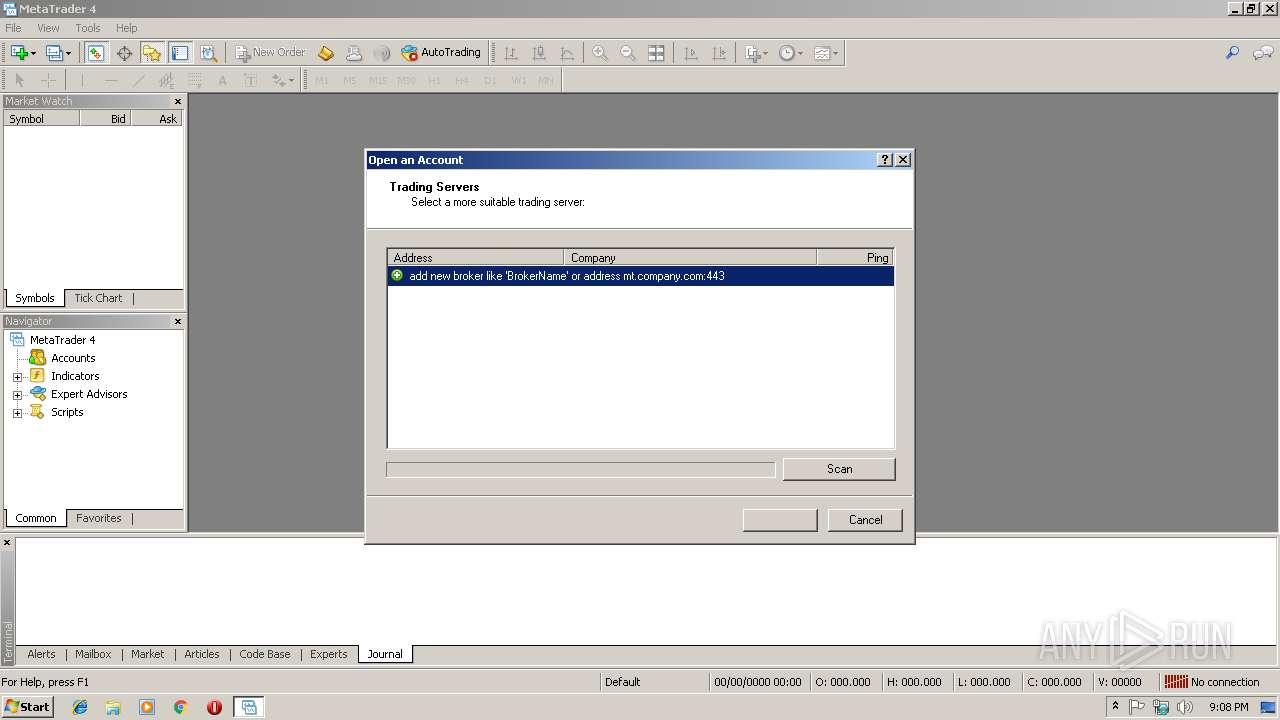
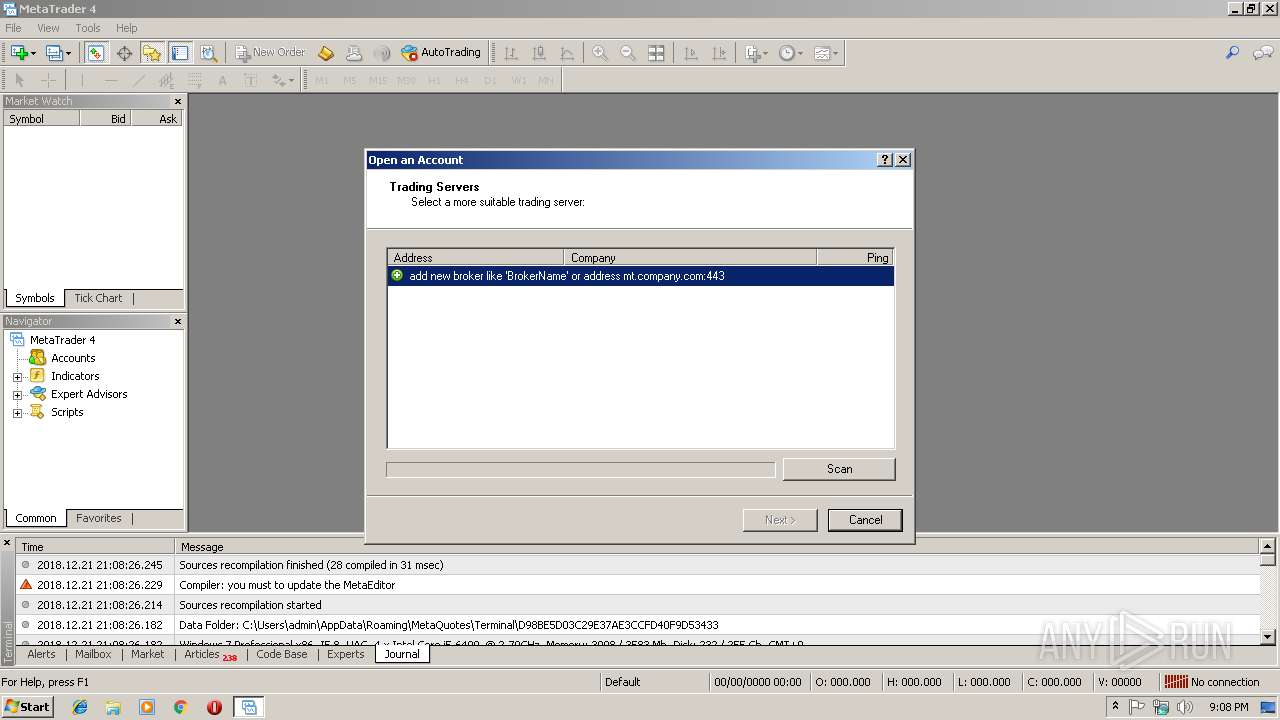
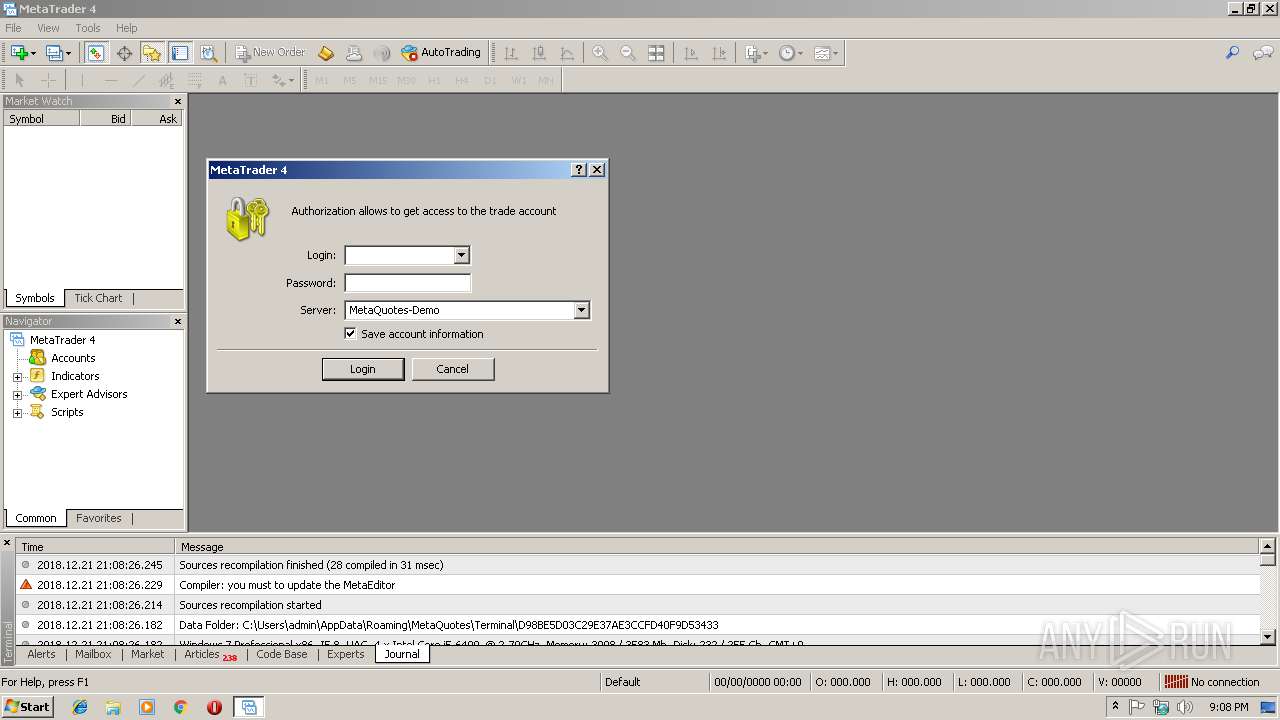
| 2216 | "C:\Users\admin\Desktop\terminal.exe" | C:\Users\admin\Desktop\terminal.exe | explorer.exe | ||||||||||||
User: admin Company: MetaQuotes Software Corp. Integrity Level: MEDIUM Description: MetaTrader Exit code: 0 Version: 4.0.0.1147 Modules
| |||||||||||||||
Total events
93
Read events
70
Write events
23
Delete events
0
Modification events
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\MetaQuotes Software |
| Operation: | write | Name: | ID |
Value: E64797E1-79F9-T-181221 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\MetaQuotes Software |
| Operation: | write | Name: | Install.Time |
Value: 1545426506 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | terminal.exe |
Value: 8000 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\MetaQuotes Software |
| Operation: | write | Name: | IDD |
Value: 8880880657844574249 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\MetaQuotes Software |
| Operation: | write | Name: | API |
Value: api4.mql5.com=190;api1.mql5.com=201;api13.mql5.com=204;api3.mql5.com=470;api11.mql5.com=556;api9.mql5.com=724;api8.mql5.com=771;api2.mql5.com=795;api6.mql5.com=924;api5.mql5.com=981;api12.mql5.com=1070 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\MetaQuotes Software |
| Operation: | write | Name: | API.Time |
Value: 1545426557 | |||
| (PID) Process: | (2216) terminal.exe | Key: | HKEY_CURRENT_USER\Software\MetaQuotes Software\Settings |
| Operation: | write | Name: | IP |
Value: 85.206.175.219 | |||
Executable files
1
Suspicious files
10
Text files
171
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\mql4.zip | — | |
MD5:— | SHA256:— | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\config\terminal.ini | text | |
MD5:— | SHA256:— | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\ArrayInt.mqh | text | |
MD5:B9A328A4E38A5152B93FE25C64C1DFBC | SHA256:7BB3A442630411746D43D4EC0DF18B1B2B3D56965CF29876228375E391997DEA | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Experts\MACD Sample.mq4 | text | |
MD5:76336FF9B38FBEBBFBAEFF0B2DE320FC | SHA256:4B9B0837BE9A580444A15513E02DBBFC4E3FBA7321133AEFE5CFB1CC7C34FD5F | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\templates\StrategyTester.htm | html | |
MD5:26B2D851BC754CE6F01893DF04C64090 | SHA256:E68AF34BA74F7AEFD077FE6147C6E2F40F91B90188E000656CAB533FFB419A04 | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\templates\Statement.htm | html | |
MD5:2D2466B92A18E19823B379DB53D4E114 | SHA256:8D1078534622984D2773FCD2584D41E2FAA76D453AE4868C594490B7501069CB | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\ArrayChar.mqh | text | |
MD5:A6D32CEDC7FD7E24D82F36039A1220AC | SHA256:595C4CB02C29CE99495ABB37E1BC93CB9384B05CE1A089A3ADE7E90090C27AF5 | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\Array.mqh | text | |
MD5:D8CD709D6263676AED5398D602EBEB19 | SHA256:E0A9C33C7F48E8F3568493A6A5C0F73CFC0CA67F244C98DB537197E33EF353F4 | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\ArrayFloat.mqh | text | |
MD5:82EFD278D622ABF0AC3AFB98C1900D4B | SHA256:331E4B985BDFC45674F67A6EEADBA3848913359132DBCCE986052C7EF6A04F0D | |||
| 2216 | terminal.exe | C:\Users\admin\AppData\Roaming\MetaQuotes\Terminal\D98BE5D03C29E37AE3CCFD40F9D53433\MQL4\Include\Arrays\Tree.mqh | text | |
MD5:76CB57572F055249A78AF710D0B2ABEE | SHA256:4D4DD2007FA4D4577C9E40C28CF8544F8B154C15861B096BD1A840924D495500 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
54
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2216 | terminal.exe | GET | 200 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/47BEABC922EAE80E78783462A79F45C254FDE68B.crt | unknown | der | 969 b | whitelisted |
2216 | terminal.exe | GET | 200 | 2.16.186.56:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2216 | terminal.exe | 138.201.201.91:443 | download.mql5.com | Hetzner Online GmbH | DE | unknown |
2216 | terminal.exe | 78.140.180.86:443 | content.mql5.com | Webzilla B.V. | NL | suspicious |
2216 | terminal.exe | 2.16.186.56:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
2216 | terminal.exe | 78.140.180.43:443 | download.mql5.com | Webzilla B.V. | NL | suspicious |
2216 | terminal.exe | 206.221.189.58:443 | api3.mql5.com | Choopa, LLC | US | unknown |
2216 | terminal.exe | 40.83.76.58:443 | api2.mql5.com | Microsoft Corporation | HK | unknown |
2216 | terminal.exe | 88.212.244.84:443 | api4.mql5.com | Servers.com, Inc. | RU | unknown |
2216 | terminal.exe | 47.52.161.165:443 | api5.mql5.com | Alibaba (China) Technology Co., Ltd. | HK | unknown |
2216 | terminal.exe | 47.74.14.49:443 | api6.mql5.com | Alibaba (China) Technology Co., Ltd. | JP | unknown |
2216 | terminal.exe | 47.95.9.170:443 | api7.mql5.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.mql5.com |
| whitelisted |
api1.mql5.com |
| suspicious |
content.mql5.com |
| suspicious |
www.download.windowsupdate.com |
| whitelisted |
api2.mql5.com |
| unknown |
api3.mql5.com |
| unknown |
api4.mql5.com |
| unknown |
api5.mql5.com |
| unknown |
api6.mql5.com |
| suspicious |
api7.mql5.com |
| unknown |