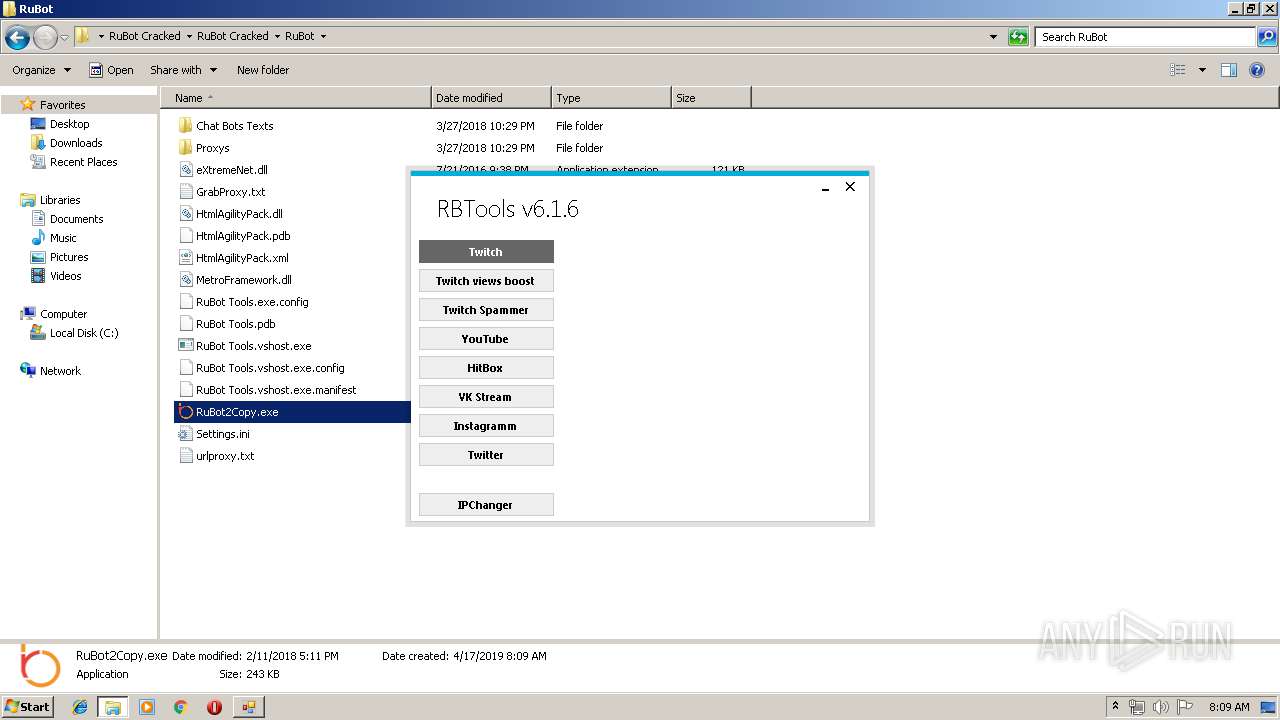
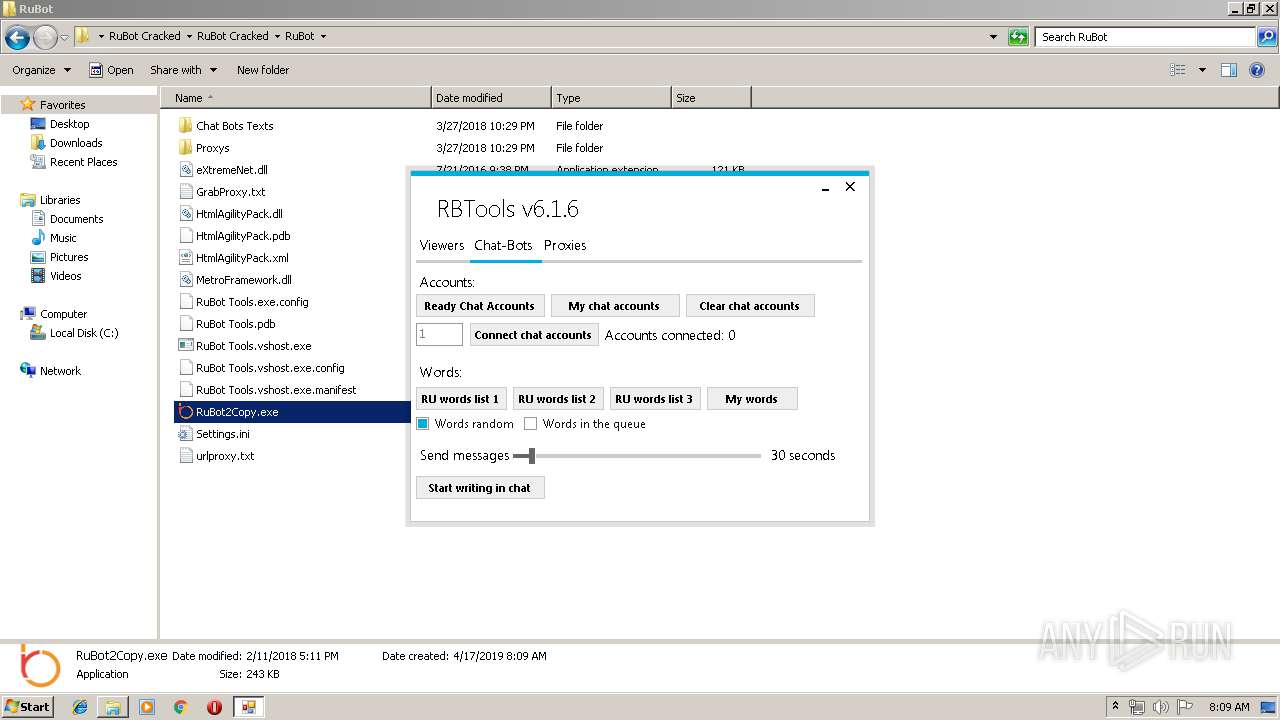
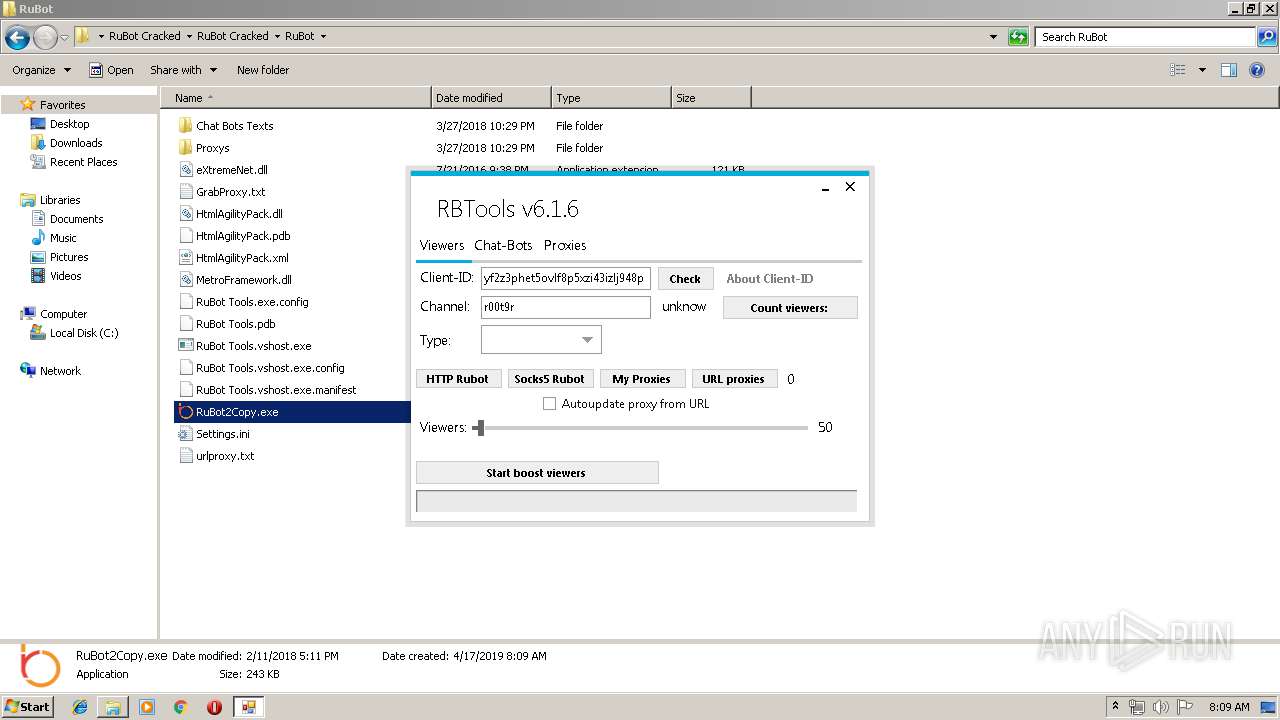
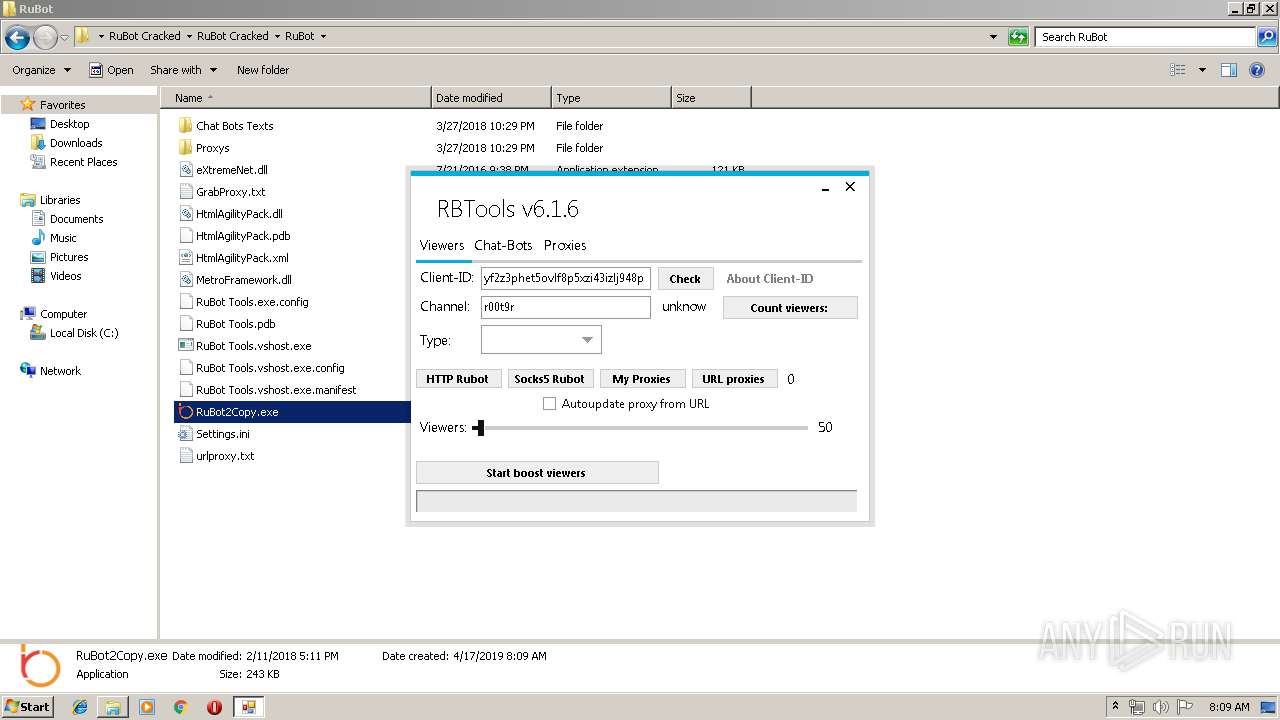
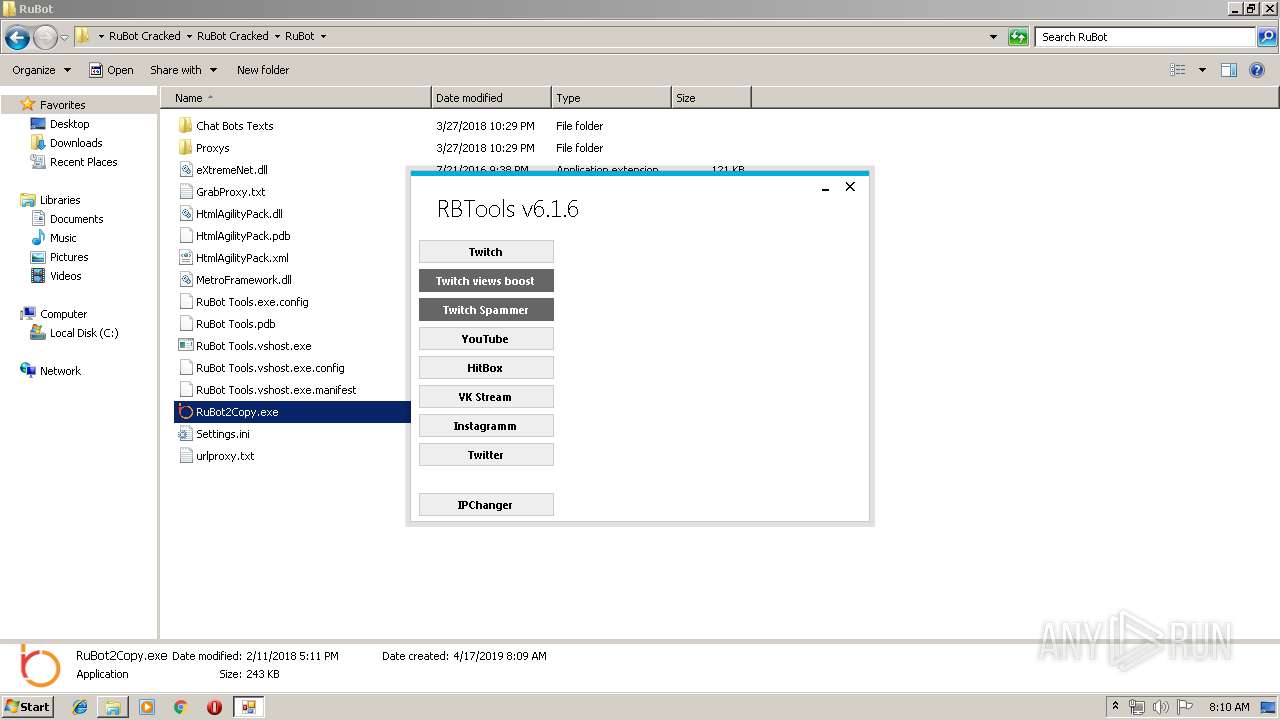
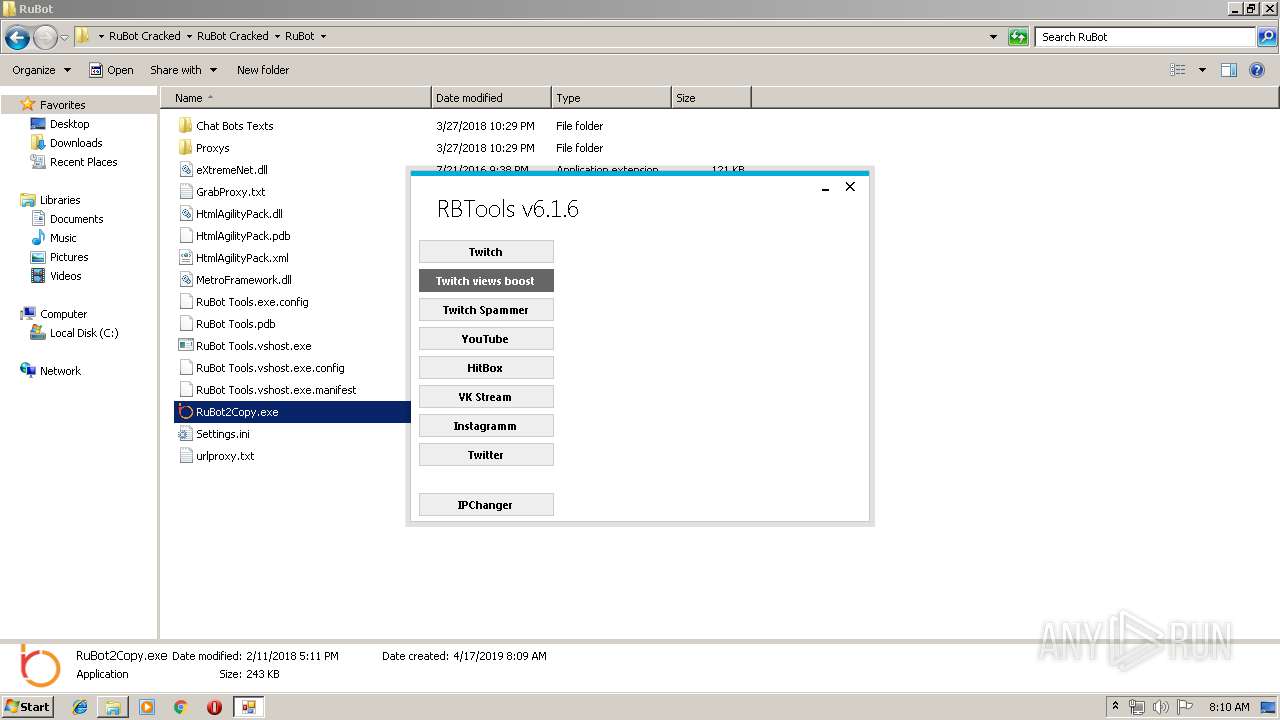
| File name: | RuBot Cracked.rar |
| Full analysis: | https://app.any.run/tasks/18d41c19-5036-4ffb-823c-5019311bdc98 |
| Verdict: | Malicious activity |
| Analysis date: | April 17, 2019, 07:09:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 8F0B5447578B4C90EE8953C695FF122F |
| SHA1: | B844DDEB525F7AC839758FCDBBCE9707C2AEEA39 |
| SHA256: | 13007DC37C11271A76D91CE5906EDF31393AA3E26BB8AC4B7FBD0D8690EBCE88 |
| SSDEEP: | 12288:Upg8WvATyzehAgYKcs80G5zmRWS4l6vBb+sjbVFDUslBrbNz4MvWgS2:SgKfA6cBfEWS4DsjbVF1BFzMa |
MALICIOUS
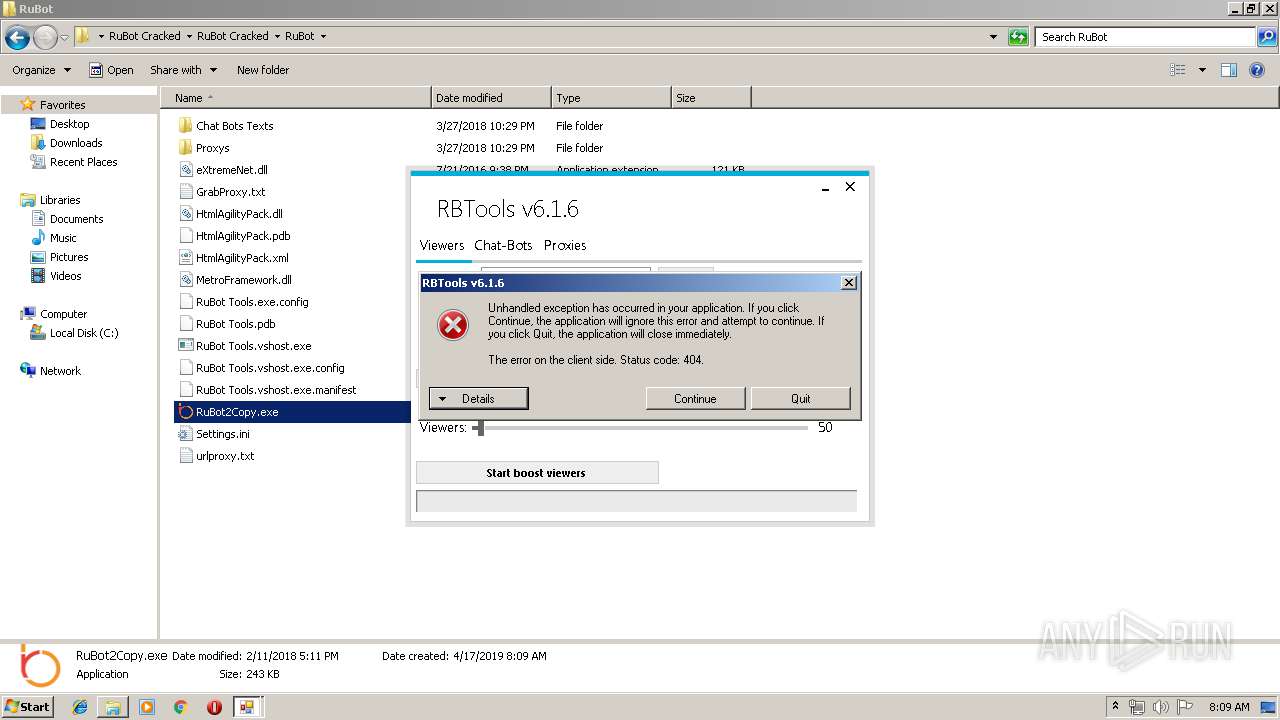
Loads dropped or rewritten executable
- RuBot2Copy.exe (PID: 3872)
- SearchProtocolHost.exe (PID: 3216)
- RuBot2Copy.exe (PID: 388)
Application was dropped or rewritten from another process
- RuBot2Copy.exe (PID: 3872)
- RuBot2Copy.exe (PID: 388)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2172)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
35
Monitored processes
4
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Users\admin\Desktop\RuBot Cracked\RuBot Cracked\RuBot\RuBot2Copy.exe" | C:\Users\admin\Desktop\RuBot Cracked\RuBot Cracked\RuBot\RuBot2Copy.exe | — | explorer.exe | |||||||||||
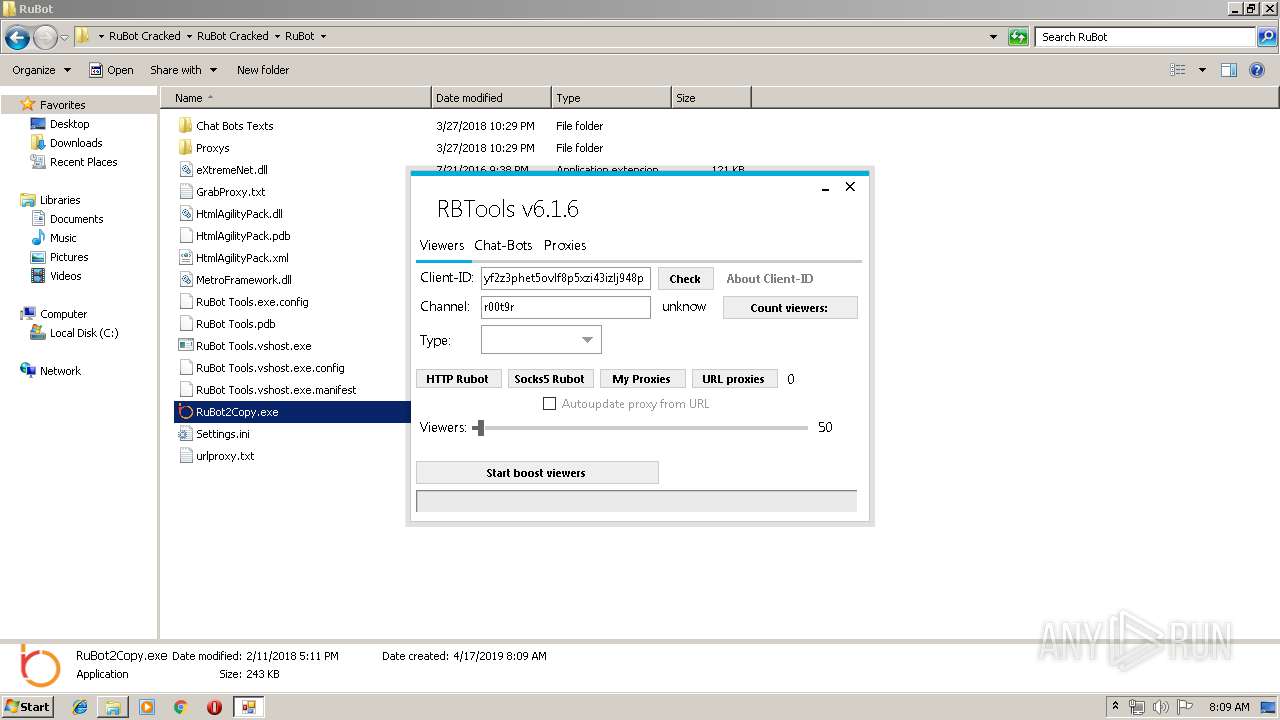
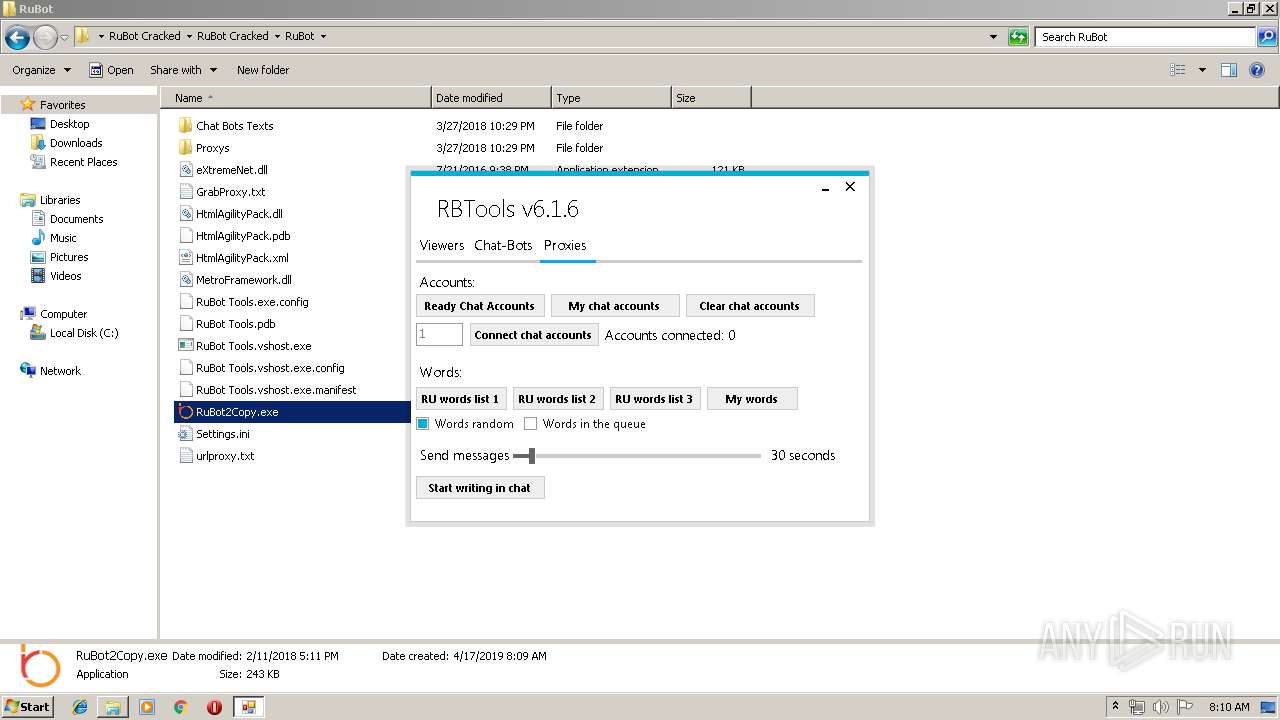
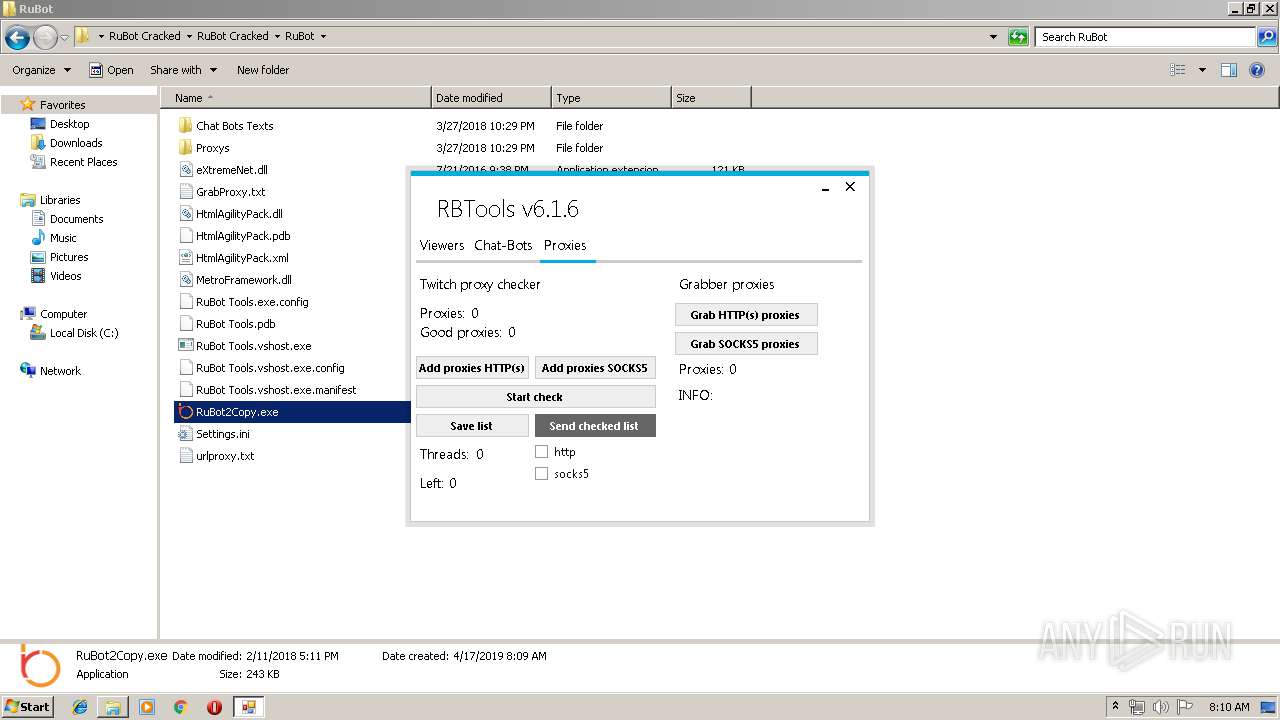
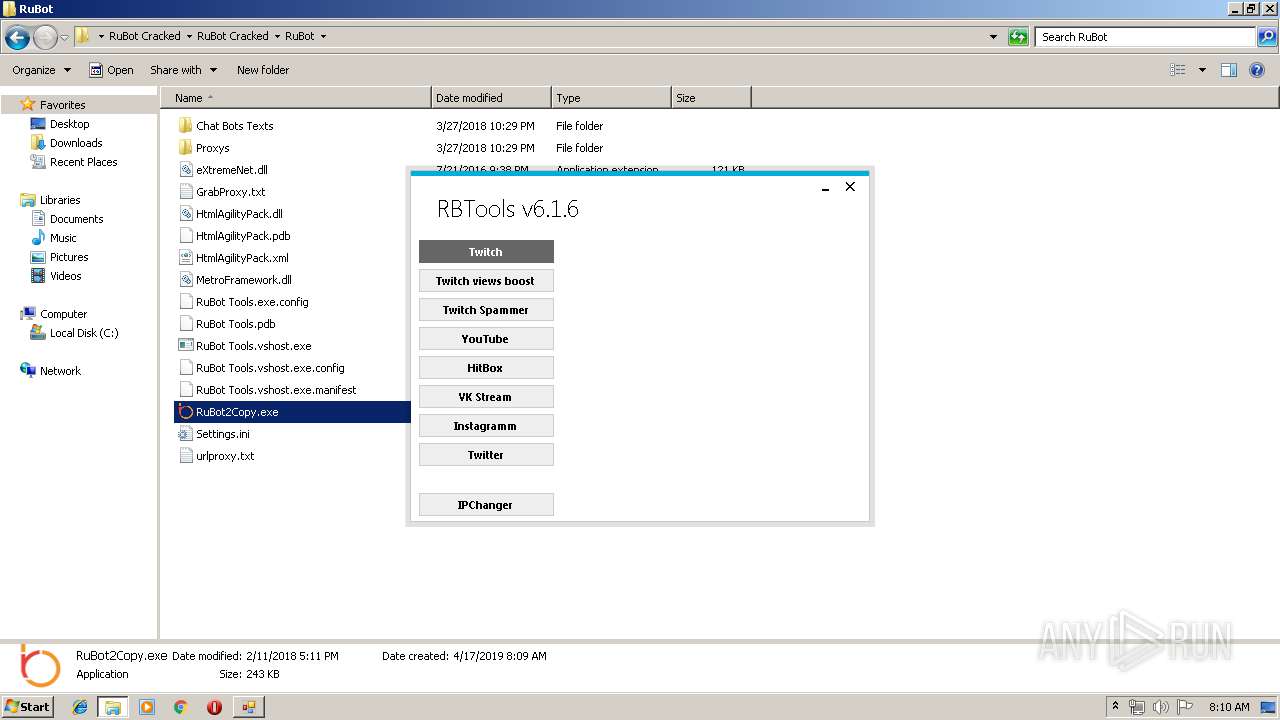
User: admin Company: RuBot.OVH Integrity Level: MEDIUM Description: RuBot_Tools Exit code: 0 Version: 6.1.0.0 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\RuBot Cracked.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3216 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3872 | "C:\Users\admin\Desktop\RuBot Cracked\RuBot Cracked\RuBot\RuBot2Copy.exe" | C:\Users\admin\Desktop\RuBot Cracked\RuBot Cracked\RuBot\RuBot2Copy.exe | explorer.exe | ||||||||||||
User: admin Company: RuBot.OVH Integrity Level: MEDIUM Description: RuBot_Tools Exit code: 4294967295 Version: 6.1.0.0 Modules
| |||||||||||||||
Total events
824
Read events
791
Write events
33
Delete events
0
Modification events
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RuBot Cracked.rar | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2172) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
5
Suspicious files
1
Text files
12
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\.vs\RuBot Tools\v15\.suo | binary | |
MD5:72047AF58DB7B8A1FEE383AA420C6779 | SHA256:F508439301484AA31277BB4C49BC0A14AD95235F8E96C6FFBB0422DEC737A8B6 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\HtmlAgilityPack.pdb | pdb | |
MD5:A62E283F655F6C8D13C2157DECC6D526 | SHA256:76209CD7521A86B41E27242F6BBB4FB48715840809D4E932351F33AE7C07D19F | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\GrabProxy.txt | text | |
MD5:CF3A4E0E92709928AB2440331F5EBB9B | SHA256:8C47FC94301C20A33FA3DE4E9F301893BA747384BB13C004111A4ED14FD4C084 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\eXtremeNet.dll | executable | |
MD5:613E35243D0F608D7A03A5500CF2F08B | SHA256:91F6647B19613C3F58CF5D75B320CC4F794318906C24D095C78964AA004CE844 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\HtmlAgilityPack.dll | executable | |
MD5:433645B4A51EE5D2A2E48114BE461052 | SHA256:129288252BEED0824C8436F3C595BD8E200A2182A229DEC85A2CA722F0CF1A05 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\Proxys\proxies.txt | text | |
MD5:C6EC62612DC9E7261AD57F780D38D4EA | SHA256:A54A5BF6BFD8B524E763F4AF856DE8E991090DA6471B85C1E67F9CD83B1E93D3 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\RuBot Tools.exe.config | xml | |
MD5:CEBFE157098995082112604CA8730110 | SHA256:DFDF5ECD6291CB0D74B89746B733BC8B1F6E74F00A253DEE15D14891A2CF5BA0 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\RuBot Tools.pdb | pdb | |
MD5:487E7DB9AD6CA6F987E78FD1B6DDEA30 | SHA256:340B8976BC3FBAD5CBFB9F6A415B5A2BAA867153A6C157D5335E63F31CDE27F3 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\MetroFramework.dll | executable | |
MD5:34EA7F7D66563F724318E322FF08F4DB | SHA256:C2C12D31B4844E29DE31594FC9632A372A553631DE0A0A04C8AF91668E37CF49 | |||
| 2172 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2172.47666\RuBot Cracked\RuBot Cracked\RuBot\Chat Bots Texts\GERMAN CHATBOT.txt | text | |
MD5:10988A198328FC7AF11DD9CDBDB4C52D | SHA256:942C78CF9CA4423E62EA1B6F5D0FD88D955BBAC39F8A52519A54F1C99E734C31 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
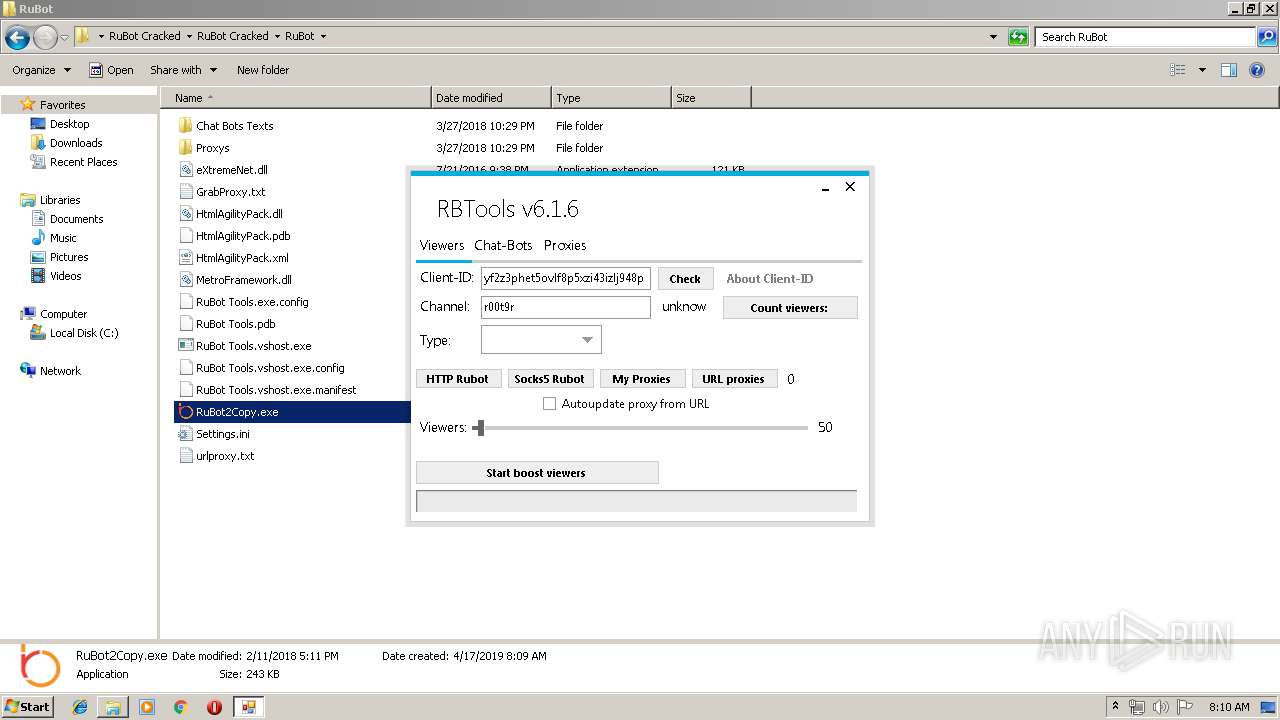
3872 | RuBot2Copy.exe | 54.37.207.219:443 | rubot.ovh | OVH SAS | FR | unknown |
— | — | 104.111.249.198:443 | api.twitch.tv | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rubot.ovh |
| suspicious |
api.twitch.tv |
| whitelisted |