| File name: | MSTeams.exe |
| Full analysis: | https://app.any.run/tasks/197d6479-39c0-4741-a990-f8c498e3a422 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2023, 15:53:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F042063023FE12546BC13C87BA5BFA25 |
| SHA1: | 650D23339AAC99447796344248328E7743C9628C |
| SHA256: | 12E4124BF790BCED8B0CFF6506511BC15E8B65FD31FC2F13697CE899F6AD9B69 |
| SSDEEP: | 98304:Jyi3Kt2pSbQnxd545HXGUHRyCXt870aszNVdYgqhTMbwJZadD5DMQBt2pSbQnxdH:sbEjF |
MALICIOUS
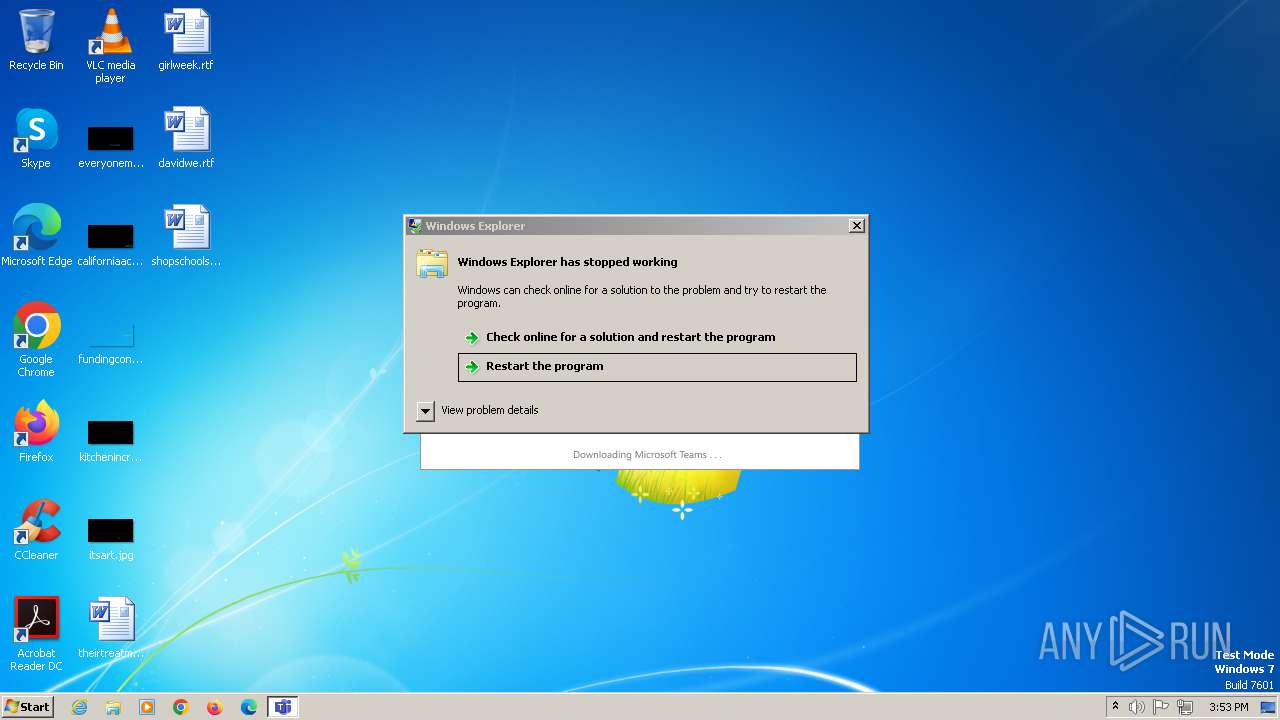
Drops the executable file immediately after the start
- MSTeamsSetup.exe (PID: 2064)
- MSTeams.exe (PID: 648)
- Update.exe (PID: 684)
The DLL Hijacking
- Teams.exe (PID: 2560)
- Teams.exe (PID: 2764)
- Teams.exe (PID: 1936)
Registers / Runs the DLL via REGSVR32.EXE
- Update.exe (PID: 684)
SUSPICIOUS
Reads the Internet Settings
- MSTeams.exe (PID: 648)
- Update.exe (PID: 684)
- Update.exe (PID: 1612)
- Teams.exe (PID: 1968)
- Teams.exe (PID: 2476)
- Squirrel.exe (PID: 584)
Uses RUNDLL32.EXE to load library
- MSTeamsSetup.exe (PID: 2064)
Process drops legitimate windows executable
- MSTeamsSetup.exe (PID: 2064)
- Update.exe (PID: 684)
Reads settings of System Certificates
- Update.exe (PID: 684)
- Update.exe (PID: 1612)
- Squirrel.exe (PID: 584)
The process drops C-runtime libraries
- Update.exe (PID: 684)
Process requests binary or script from the Internet
- explorer.exe (PID: 1944)
Application launched itself
- Teams.exe (PID: 1968)
- Teams.exe (PID: 2476)
INFO
Reads the computer name
- MSTeams.exe (PID: 648)
- Update.exe (PID: 684)
- Squirrel.exe (PID: 584)
- Teams.exe (PID: 1968)
- Teams.exe (PID: 2560)
- Teams.exe (PID: 2868)
- Teams.exe (PID: 2764)
- Update.exe (PID: 1612)
- Teams.exe (PID: 2476)
- Teams.exe (PID: 1936)
- Teams.exe (PID: 872)
Checks supported languages
- MSTeams.exe (PID: 648)
- MSTeamsSetup.exe (PID: 2064)
- Update.exe (PID: 684)
- Squirrel.exe (PID: 584)
- Teams.exe (PID: 1968)
- Update.exe (PID: 1612)
- Teams.exe (PID: 2560)
- Teams.exe (PID: 2868)
- Teams.exe (PID: 2764)
- Teams.exe (PID: 872)
- Teams.exe (PID: 1936)
- Teams.exe (PID: 2108)
- Teams.exe (PID: 2476)
Create files in a temporary directory
- MSTeams.exe (PID: 648)
- Update.exe (PID: 684)
- Teams.exe (PID: 1968)
Creates files or folders in the user directory
- MSTeamsSetup.exe (PID: 2064)
- Update.exe (PID: 684)
- explorer.exe (PID: 1944)
- Squirrel.exe (PID: 584)
- Teams.exe (PID: 1968)
- Update.exe (PID: 1612)
- Teams.exe (PID: 2476)
Reads the machine GUID from the registry
- Update.exe (PID: 684)
- Squirrel.exe (PID: 584)
- Update.exe (PID: 1612)
- Teams.exe (PID: 2476)
Reads Environment values
- Update.exe (PID: 684)
- Teams.exe (PID: 1968)
- Squirrel.exe (PID: 584)
- Update.exe (PID: 1612)
- Teams.exe (PID: 2476)
Reads Microsoft Office registry keys
- Update.exe (PID: 684)
- Update.exe (PID: 1612)
- Squirrel.exe (PID: 584)
Drops the executable file immediately after the start
- explorer.exe (PID: 1944)
Reads the Internet Settings
- explorer.exe (PID: 1944)
Reads product name
- Teams.exe (PID: 1968)
- Teams.exe (PID: 2476)
Process checks computer location settings
- Teams.exe (PID: 1968)
- Teams.exe (PID: 2108)
- Teams.exe (PID: 2476)
Reads CPU info
- Teams.exe (PID: 1968)
- Teams.exe (PID: 2476)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:03:03 14:15:57+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.3 |
| CodeSize: | 203776 |
| InitializedDataSize: | 250880 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f530 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
52
Monitored processes
18
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | "C:\Users\admin\AppData\Local\Microsoft\Teams\current\Squirrel.exe" --updateSelf=C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe | C:\Users\admin\AppData\Local\Microsoft\Teams\current\Squirrel.exe | Update.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams classic Exit code: 0 Version: 3.3.5.0 Modules
| |||||||||||||||
| 648 | "C:\Users\admin\AppData\Local\Temp\MSTeams.exe" | C:\Users\admin\AppData\Local\Temp\MSTeams.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 684 | "C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe" --install . --exeName=MSTeamsSetup.exe --bootstrapperMode | C:\Users\admin\AppData\Local\SquirrelTemp\Update.exe | MSTeamsSetup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams Exit code: 0 Version: 3.1.2.0 Modules
| |||||||||||||||
| 872 | "C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --enable-wer --user-data-dir="C:\Users\admin\AppData\Roaming\Microsoft\Teams" --mojo-platform-channel-handle=1448 --field-trial-handle=1140,i,9307248539490673987,1939988095173654683,131072 --enable-features=ContextBridgeMutability,SharedArrayBuffer,WinUseBrowserSpellChecker,WinUseHybridSpellChecker --disable-features=CalculateNativeWinOcclusion,ExtraCookieValidityChecks,ForcedColors,SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:8 | C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe | — | Teams.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams Exit code: 0 Version: 1.6.00.29964 Modules
| |||||||||||||||
| 1612 | C:\Users\admin\AppData\Local\Microsoft\Teams\Update.exe --createShortcut=Teams.exe -l=StartMenu | C:\Users\admin\AppData\Local\Microsoft\Teams\Update.exe | Teams.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams Exit code: 0 Version: 3.1.2.0 Modules
| |||||||||||||||
| 1620 | C:\Windows\system32\rundll32.exe cleanhelper.dll T34 /k fugas144 /auto 0 | C:\Windows\System32\rundll32.exe | — | MSTeamsSetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1936 | "C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe" --type=gpu-process --user-data-dir="C:\Users\admin\AppData\Roaming\Microsoft\Teams" --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1116 --field-trial-handle=1140,i,9307248539490673987,1939988095173654683,131072 --enable-features=ContextBridgeMutability,SharedArrayBuffer,WinUseBrowserSpellChecker,WinUseHybridSpellChecker --disable-features=CalculateNativeWinOcclusion,ExtraCookieValidityChecks,ForcedColors,SpareRendererForSitePerProcess,WinRetrieveSuggestionsOnlyOnDemand /prefetch:2 | C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe | — | Teams.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Teams Exit code: 0 Version: 1.6.00.29964 Modules
| |||||||||||||||
| 1944 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1968 | "C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe" --squirrel-install 1.6.00.29964 | C:\Users\admin\AppData\Local\Microsoft\Teams\current\Teams.exe | — | Update.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Teams Exit code: 0 Version: 1.6.00.29964 Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\MSTeamsSetup.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\MSTeamsSetup.exe | — | MSTeams.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Installer for Squirrel-based applications Exit code: 0 Version: 1.4.4.0 Modules
| |||||||||||||||
Total events
8 076
Read events
8 036
Write events
40
Delete events
0
Modification events
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000088AF72B0747534094337F63DE35C94A000000000200000000001066000000010000200000003A7AE26404D75DF41C31FF40C5EA8CE90BAF74FA9E9BD7A9ACA34C7048350C1E000000000E8000000002000020000000BD2D56D46506C12C41A6A70B10E79EE53CB79EF36FD2BA8CDD2460CB8F4BE86A300000009B5D1418CBF2EB49F3C4BD4C21D58CA55B82FA3D3ED08AF0EF59D6C7ECAFC1055FA323A80FF7C154B1C9B60253392B6640000000DED9FDCC168073324C3013F1BB125E066EB1A2F09FD2C8E7CC7A793AA992E21EF1C942BF7294D04E036428704009B863B1CB981B97312E2530E3E816780CF7C9 | |||
| (PID) Process: | (648) MSTeams.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (648) MSTeams.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (648) MSTeams.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (648) MSTeams.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (684) Update.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\15A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (684) Update.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Skype.exe | |||
| (PID) Process: | (1944) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{CEBFF5CD-ACE2-4F4F-9178-9926F41749EA}\Count |
| Operation: | write | Name: | HRZR_PGYFRFFVBA |
Value: 00000000CC0000000101000073456B001500000007000000DD2706007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E0065007800650000005DFEFE0700007DDBCB529EC50000D0C78A09000000001054C5030000000098835CFEFE070000B8DF1003000000001054C50300000000A0DF1003000000002C5E1DFEFE07000005400080000000001054C5030000000030C730000000000048DE20FEFE070000B8DF100300000000A0DF100300000000070000000000000002000000000000000000000000000000D0C78A0900000000000000000000000016611DFEFE07000000000000000000001054C5030000000098835CFEFE0700008097960700000000B8DF100300000000A0DF1003000000000000000000000000DF5C0BFFFE07000000000000000000000100000000000000A034CF0300000000280CBF77000000000000000000000000DF5C0BFFFE07000000C88A090000000001000000000000001054C5030000000001000000000000002094750900000000AFBD1FFEFE070000000000000000000001000000000000001054C50300000000207D2B000000000000000000000000001C7F2B0000000000D0242E000000000000000000000000008097960700000000751927FFFE070000000000000000000028595DFEFE070000C803CE7707000000250000004B7A0B004D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E0043006F006E00740072006F006C00500061006E0065006C00000075006C0074000000000000000000010000000000000088E2EA0200000000000000000000000030E0EA020000000028E0EA020000000020E0EA0200000000586705FCFE070000000000000000000040E0EA0200000000000000000000000000000000000000003E00400000000000B0E8EA02000000003053A203000000000000000000000000000000000000000022BBD2FF0000000000003D4A62B00000E000070000000000A210000000000000E0F1EA02000000000000000000000000300B8B0200000000A4768F0200000000D4AF17FEFE070000B0E3EA0200000000200C9C0A000000000100000000000000D46905FCFE0700001500000007000000790E06007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C0063006D0064002E006500780065000000EA02000000000540008000000000542D8CFFFE070000000000000000000068006C02000000005C0001000000000000000000000000000000280000000000EB1A6E770000000068006C020000000000000000FE070000282595FFFE070000A00D33000000000018006C02000000001B000000E8261C007B00310041004300310034004500370037002D0030003200450037002D0034004500350044002D0042003700340034002D003200450042003100410045003500310039003800420037007D005C007400610073006B006D00670072002E006500780065000000008000000000542DC9FDFE070000000000000000000068009902000000005800010000000000000000000000000000002B0000000000EB1AC07700000000680099020000000000000000FE0700002825D2FDFE070000F099A90200000000180099020000000000000000000000000100000000000000BF1DC9FDFE07000030E010030000000010D1AB020000000000000000000000003B94B8FDFE070000B04EAB020000000008009902000000005800010000000000869AAE7700000000C7F7CF529EC5000082020000000000000000000000000000580001000000000000000000000000008202000000000000020000000000000058000100000000000000000000000000820200000000000080A630FF00000000C81222FF00000000B04EAB020000000001000000000000000F0000C00000000090DFDD0300000000820200000000000001000000000000008202000000000000DB9BAE77000000005800010000000000000000000000000000000000000000000100000000000000000000000000000081020000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (684) Update.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
343
Suspicious files
153
Text files
138
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 684 | Update.exe | C:\Users\admin\AppData\Local\Microsoft\Teams\packages\Teams-1.6.00.29964-full.nupkg | — | |
MD5:— | SHA256:— | |||
| 684 | Update.exe | C:\Users\admin\AppData\Roaming\Microsoft\Teams\teams_install_session.json | binary | |
MD5:BAED68CACBF59C9039DEEC9AEFCFC756 | SHA256:E106412ACE17B0F2AE05746847D22A6C3BF0BB86466A0CB11E5FDC99B7668D70 | |||
| 648 | MSTeams.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\README.txt | binary | |
MD5:C81E728D9D4C2F636F067F89CC14862C | SHA256:— | |||
| 684 | Update.exe | C:\Users\admin\AppData\Roaming\Microsoft\Teams\SquirrelTelemetry.log | text | |
MD5:8634EA26B3A64B53E2788E420D99E097 | SHA256:B5CB1F6AA529D5F1437FBF990B7232B877881A25FB9EF744D2E4B19E309F10CF | |||
| 1944 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\WindowsApps\cleanhelper.dll | executable | |
MD5:3B1FA7C1272F4208606A1848DE23D261 | SHA256:FD8BC352E66344AD3E04D1437A068F645A17675EC87EED830478586B3B1AE5E9 | |||
| 648 | MSTeams.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\payload\cleanhelper.dll | executable | |
MD5:3B1FA7C1272F4208606A1848DE23D261 | SHA256:FD8BC352E66344AD3E04D1437A068F645A17675EC87EED830478586B3B1AE5E9 | |||
| 2064 | MSTeamsSetup.exe | C:\Users\admin\AppData\Local\SquirrelTemp\downloading.gif | image | |
MD5:3488A1749B859E969C01BA981036FAB6 | SHA256:C3FA333FDBCE95D504AEE31912993DC17AB31324428F557AC774F7E98B049B99 | |||
| 2064 | MSTeamsSetup.exe | C:\Users\admin\AppData\Local\SquirrelTemp\background.gif | image | |
MD5:FF1F29DCA0451246C3CA6CB7B023434F | SHA256:753D7D351E427246E2B6CC86C45E21F952939E306C3EB2FDB1BD7D67842C64B8 | |||
| 684 | Update.exe | C:\Users\admin\AppData\Local\SquirrelTemp\setup.json | binary | |
MD5:5578707EF7B9BF6B84A7AD0467CE7001 | SHA256:9987CC47BA8429D9044663C1482180BD38495511A0FB4C343E50A3721F269F8C | |||
| 648 | MSTeams.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\MSTeamsSetup.exe | executable | |
MD5:62240738F62DE01BD15356D8AB6B2DBC | SHA256:F584BD6C77B91D942D866A524A8881B677F22F402A57D206504B622ABCEC9931 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
16
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 194.87.218.3:80 | http://superxxl-cdn.com/jkdjkekhu/json.php | unknown | binary | 195 b | unknown |
1944 | explorer.exe | GET | 200 | 194.87.218.3:80 | http://superxxl-cdn.com/jkdjkekhu/payloads/rh_0.5.0.exe.cipher | unknown | binary | 539 Kb | unknown |
1944 | explorer.exe | POST | 200 | 194.87.218.3:80 | http://superxxl-cdn.com/jkdjkekhu/json.php | unknown | text | 5 b | unknown |
1944 | explorer.exe | GET | 200 | 194.87.218.3:80 | http://superxxl-cdn.com/jkdjkekhu/payloads/rh_0.5.0.exe.key | unknown | binary | 16 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
684 | Update.exe | 52.113.194.132:443 | teams.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
684 | Update.exe | 52.123.128.14:443 | teams.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1944 | explorer.exe | 37.220.86.131:443 | coliquoi.com | Datacamp Limited | RU | unknown |
1944 | explorer.exe | 194.87.218.3:80 | superxxl-cdn.com | Partner LLC | CZ | unknown |
684 | Update.exe | 52.182.143.208:443 | mobile.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1612 | Update.exe | 104.208.16.88:443 | mobile.pipe.aria.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
teams.live.com |
| unknown |
teams.microsoft.com |
| whitelisted |
statics.teams.cdn.office.net |
| whitelisted |
coliquoi.com |
| unknown |
superxxl-cdn.com |
| unknown |
mobile.pipe.aria.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Update.exe | Performance counters are disabled. Skipping creation of counters category.
|
Update.exe | Update.exe Information: 0 : |
Update.exe | TelemetryManagerImpl creation started
|
Update.exe | Starting TelemetryManager constructor
|
Update.exe | Update.exe Information: 0 : |
Update.exe | Update.exe Information: 0 : |
Update.exe | Update.exe Information: 0 : |
Update.exe | RecordBatcherTask with ID 4 started.
|
Update.exe | TelemetryManagerImpl creation finished
|
Update.exe | Update.exe Information: 0 : |