| File name: | VpnClientSetupX86.exe |
| Full analysis: | https://app.any.run/tasks/8948a380-17db-42fc-93b3-4ec6f0942e59 |
| Verdict: | Malicious activity |
| Analysis date: | December 23, 2024, 17:18:56 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 7A0C943FC3A9092AE160EE3018986205 |
| SHA1: | F6D581B39D5C059A448C2F1817523CECB3CF0061 |
| SHA256: | 12A035BC7DD79F3CD2A95A38C28FC9C02872C8F383057F5842334F5A93535E15 |
| SSDEEP: | 3072:PCCJ1I5W2PScVgkl7T25Tz7unJrOXjmOVVpFNVrzg4Uu9R7dF:Nz2LnT25qndIjjVVbXJUu77 |
MALICIOUS
Changes the autorun value in the registry
- VpnClientSetupX86.exe (PID: 6268)
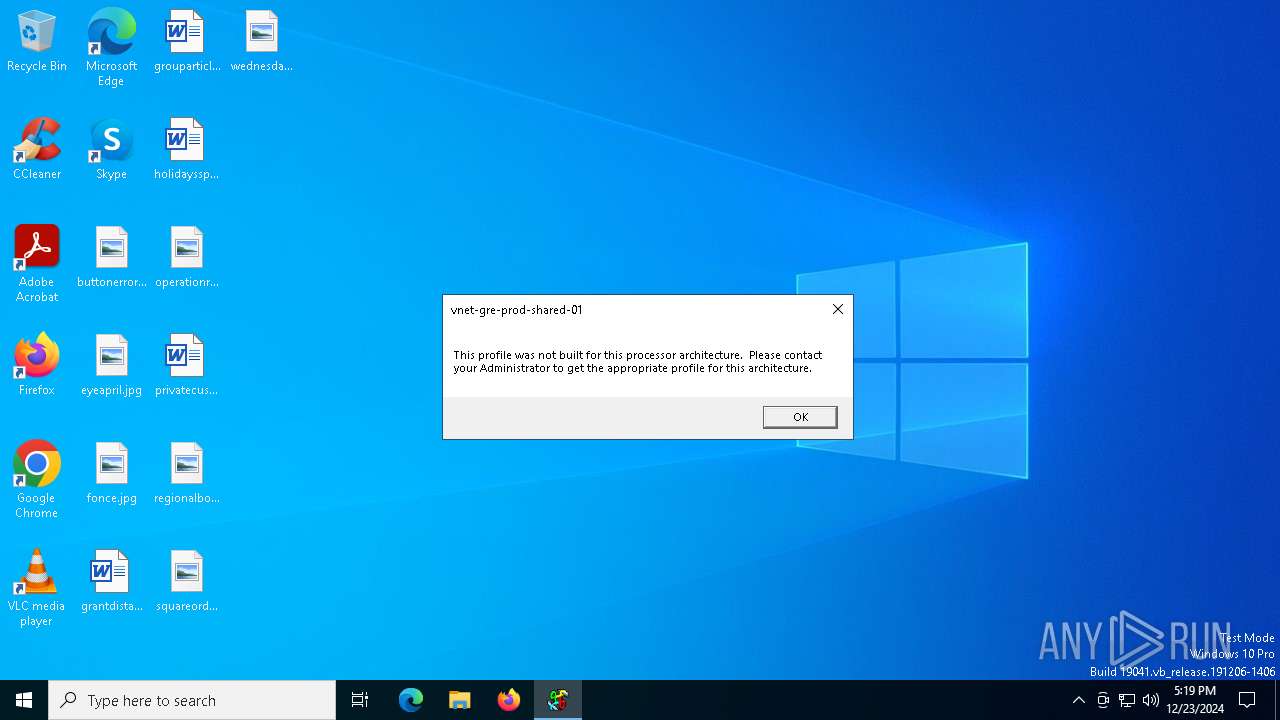
UAC Bypass using CMSTP.exe (Connection Manager service profile)
- VpnClientSetupX86.exe (PID: 6268)
SUSPICIOUS
Starts a Microsoft application from unusual location
- VpnClientSetupX86.exe (PID: 6268)
- VpnClientSetupX86.exe (PID: 3608)
The process creates files with name similar to system file names
- VpnClientSetupX86.exe (PID: 6268)
Process drops legitimate windows executable
- VpnClientSetupX86.exe (PID: 6268)
Executable content was dropped or overwritten
- VpnClientSetupX86.exe (PID: 6268)
INFO
The sample compiled with english language support
- VpnClientSetupX86.exe (PID: 6268)
Reads the computer name
- VpnClientSetupX86.exe (PID: 6268)
Checks supported languages
- VpnClientSetupX86.exe (PID: 6268)
Create files in a temporary directory
- VpnClientSetupX86.exe (PID: 6268)
Disables trace logs
- cmstp.exe (PID: 6504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2040:03:15 19:34:43+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.26 |
| CodeSize: | 26624 |
| InitializedDataSize: | 164864 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6ce0 |
| OSVersion: | 10 |
| ImageVersion: | 10 |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.20348.1 |
| ProductVersionNumber: | 11.0.20348.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Win32 Cabinet Self-Extractor |
| FileVersion: | 11.00.20348.1 (WinBuild.160101.0800) |
| InternalName: | Wextract |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | WEXTRACT.EXE .MUI |
| ProductName: | Internet Explorer |
| ProductVersion: | 11.00.20348.1 |
Total processes
134
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3608 | "C:\Users\admin\AppData\Local\Temp\VpnClientSetupX86.exe" | C:\Users\admin\AppData\Local\Temp\VpnClientSetupX86.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 3221226540 Version: 11.00.20348.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6268 | "C:\Users\admin\AppData\Local\Temp\VpnClientSetupX86.exe" | C:\Users\admin\AppData\Local\Temp\VpnClientSetupX86.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Exit code: 0 Version: 11.00.20348.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6504 | cmstp.exe /s /su /ns fa010069-15bb-4d12-8d7a-c1fcde134ea9.inf | C:\Windows\SysWOW64\cmstp.exe | — | VpnClientSetupX86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Connection Manager Profile Installer Exit code: 1 Version: 7.2.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
66
Read events
57
Write events
8
Delete events
1
Modification events
| (PID) Process: | (6268) VpnClientSetupX86.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | write | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
| (PID) Process: | (6504) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6504) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6504) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6504) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6504) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (6504) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (6504) cmstp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\CMSTP |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (6268) VpnClientSetupX86.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | wextract_cleanup0 |
Value: rundll32.exe C:\WINDOWS\system32\advpack.dll,DelNodeRunDLL32 "C:\Users\admin\AppData\Local\Temp\IXP000.TMP\" | |||
Executable files
2
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\cmroute.dll | executable | |
MD5:344BE7745270300442F2472DDD96DDCD | SHA256:8298F20DF9AD412EEEE453EA989D6CAC3B7734A468A2B868499E80E7D3C69BF3 | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\azurebox32.ico | image | |
MD5:1E633EC56EEE97F7CD80316388F0B769 | SHA256:04AAB375E08F56CF4BE4CA7E148969FA93789886EFF1B13AB85F00A76CEA238E | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\fa010069-15bb-4d12-8d7a-c1fcde134ea9.pbk | text | |
MD5:DD68BFA5F0A3344A09384964C84B76F3 | SHA256:891D7E3D577B558D17656F3160F3D671B729D1E5948BBAEA514D459FD4897BB7 | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\fa010069-15bb-4d12-8d7a-c1fcde134ea9.cms | text | |
MD5:C31E8CBBEA66807BF4027857ADDEBC4E | SHA256:5711F1F6DD5D444954E3014E333D91B907C526B630D101EA76ADAFBE5206450E | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\azurevpnbanner.bmp | image | |
MD5:82CC9A24C36D676E0537156B17F324B0 | SHA256:FD18BC07A577C5F155FF5A188D41358DC01E6C12FC0152756B6ECE9E99A93558 | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\fa010069-15bb-4d12-8d7a-c1fcde134ea9.inf | binary | |
MD5:42BAA0597FE6D3F474CE5BF694E2D87C | SHA256:4A3C6D7206EA328B48B2406F98553B1CE395A40583107FA264630F341CDB877C | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\fa010069-15bb-4d12-8d7a-c1fcde134ea9.cer | binary | |
MD5:E4A68AC854AC5242460AFD72481B2A44 | SHA256:CB3CCBB76031E5E0138F8DD39A23F9DE47FFC35E43C1144CEA27D46A5AB1CB5F | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\fa010069-15bb-4d12-8d7a-c1fcde134ea9.cmp | ini | |
MD5:F5366377F7A4CACEB4E23A39AE9337F6 | SHA256:AF5CF3CA10747D8FB561C73CC7D3CD81D7A1BC5D90E9F0044AB225BAD90927BF | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\routes.txt | text | |
MD5:DE6E7A9C42542B6437349BFF98803D1B | SHA256:A2B2FC24F90D06638166A546D824589A6739E7F76B41423A094F5CB71C7E37A9 | |||
| 6268 | VpnClientSetupX86.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\azurebox16.ico | image | |
MD5:F4210677849C93E4550B23C038B251F8 | SHA256:1EBDCE9E839099060B4A68DAD683BD77CCB398280CE6CEADE6297D50DF1001E0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4024 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4024 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6584 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5696 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 2.23.209.135:443 | — | Akamai International B.V. | GB | unknown |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4024 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4024 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4024 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4024 | svchost.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 2.23.209.133:443 | — | Akamai International B.V. | GB | unknown |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |