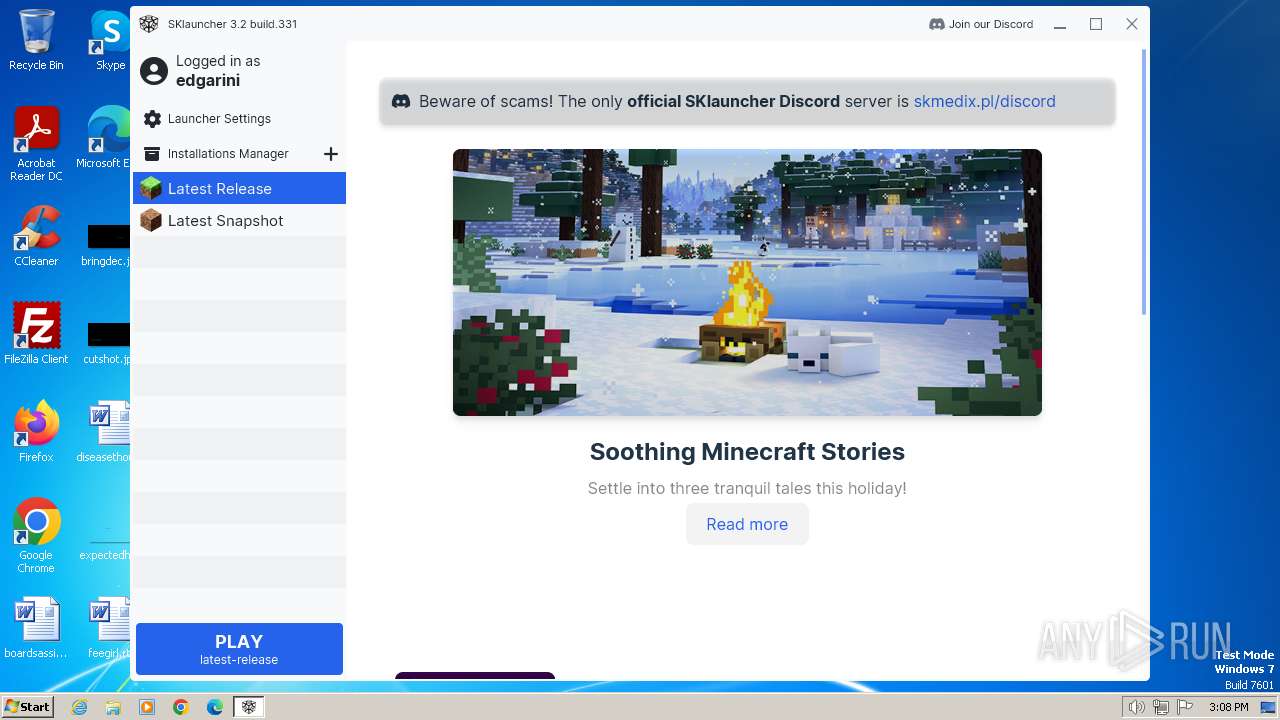
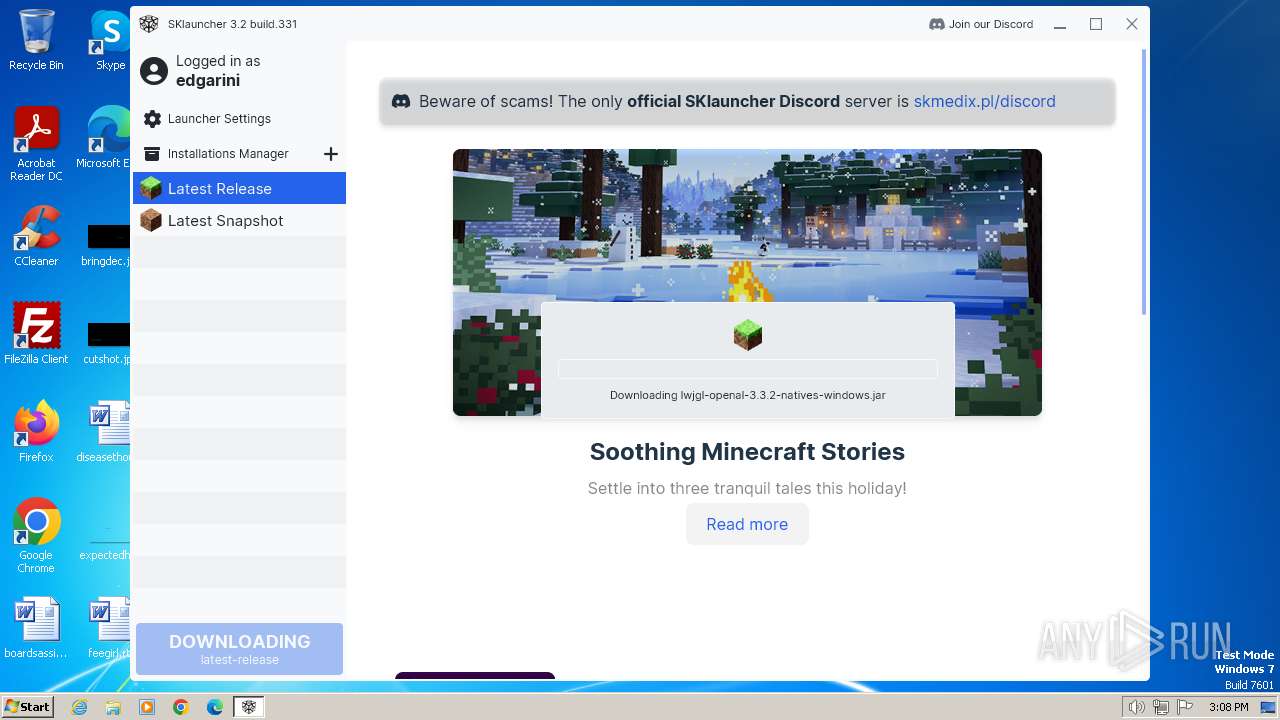
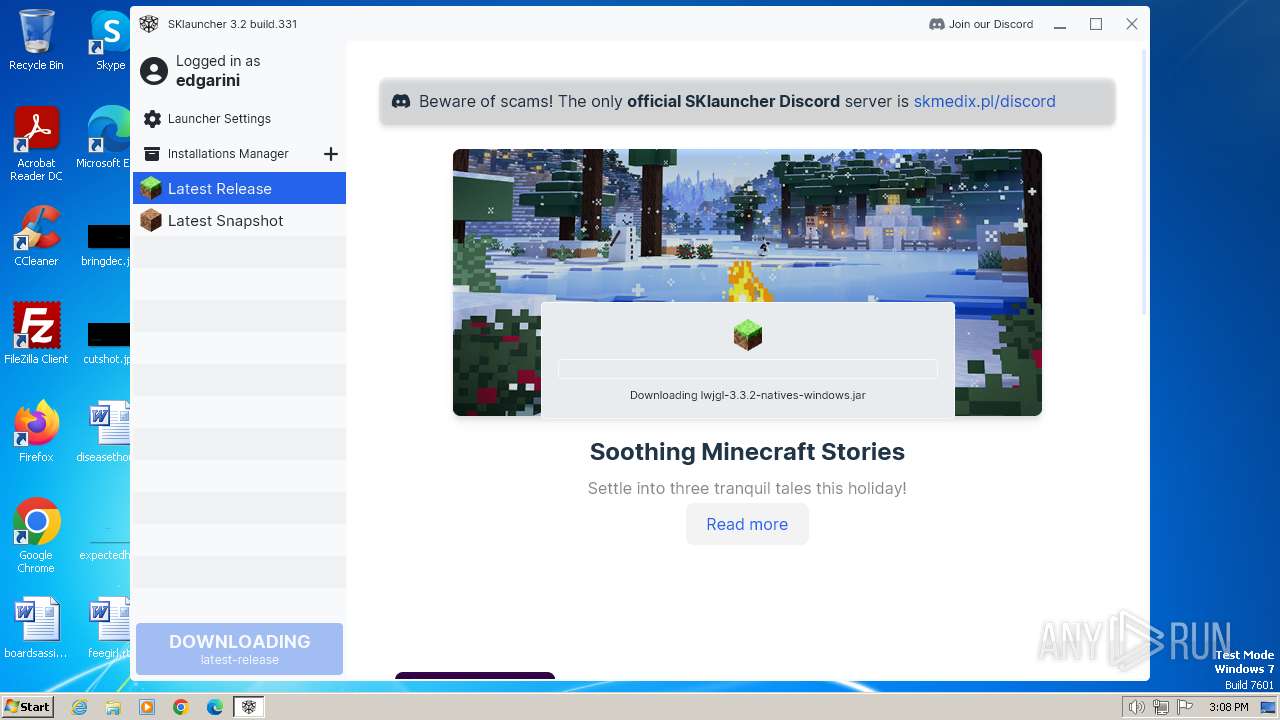
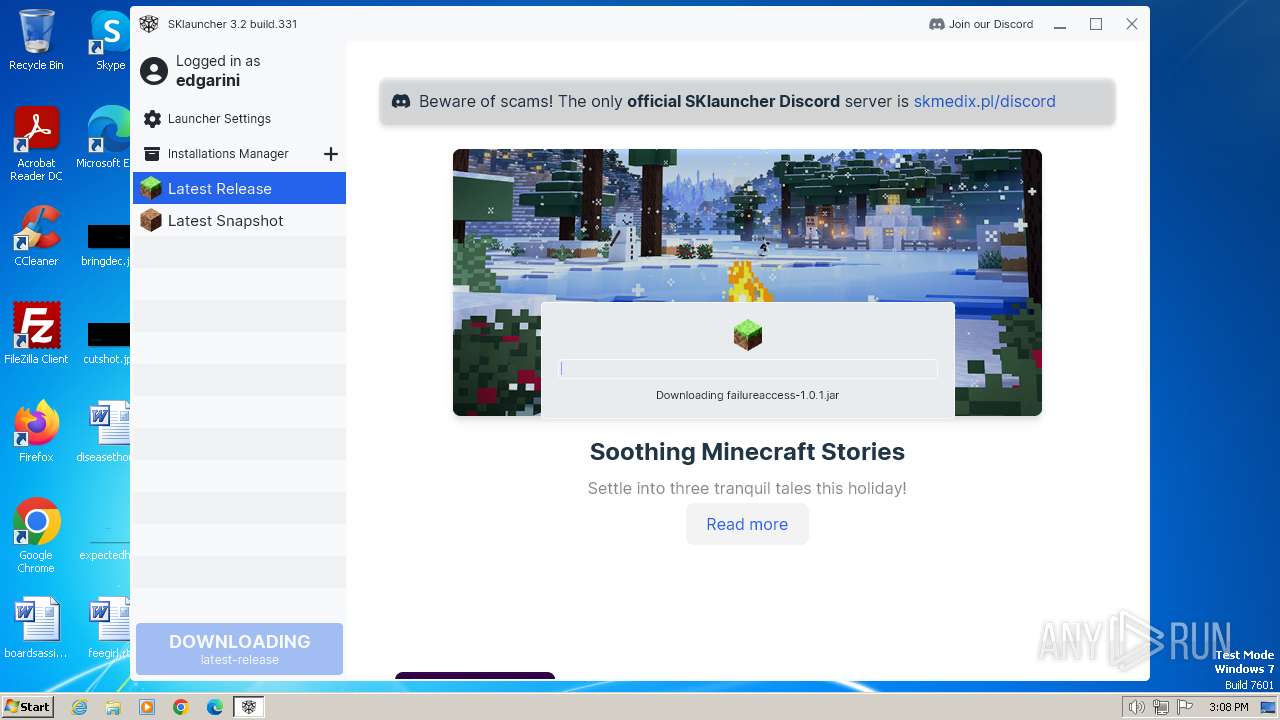
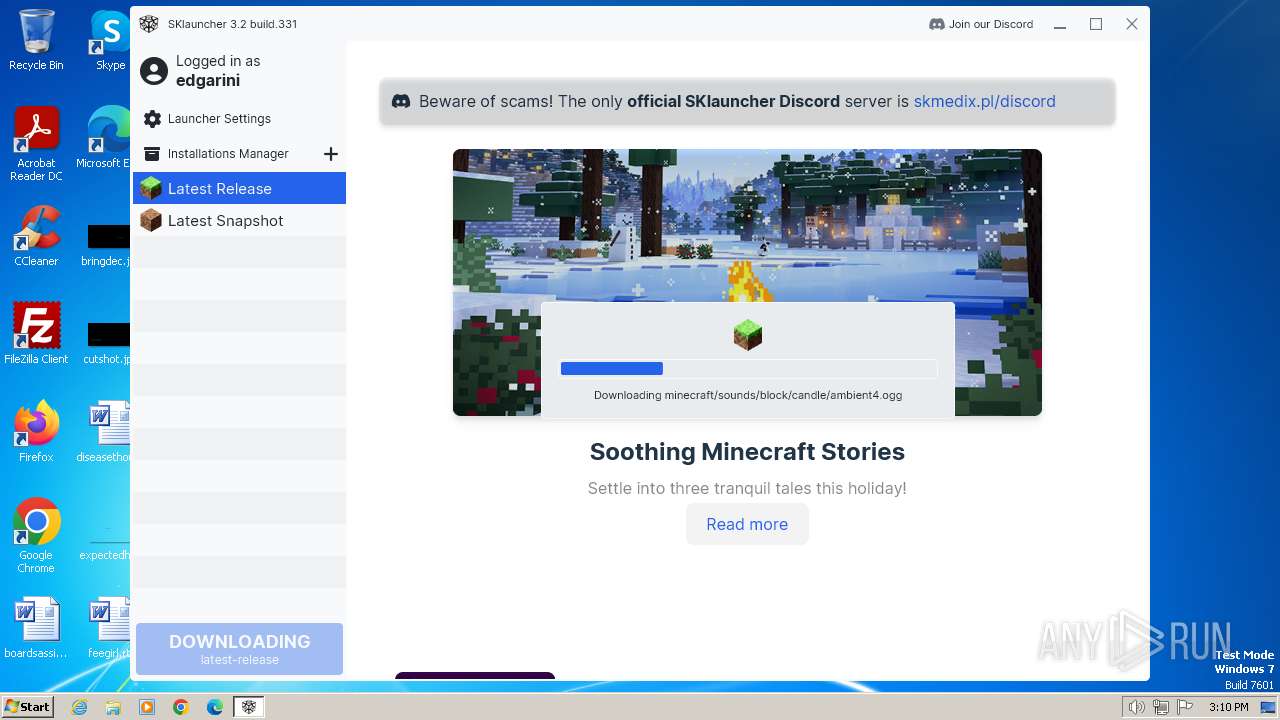
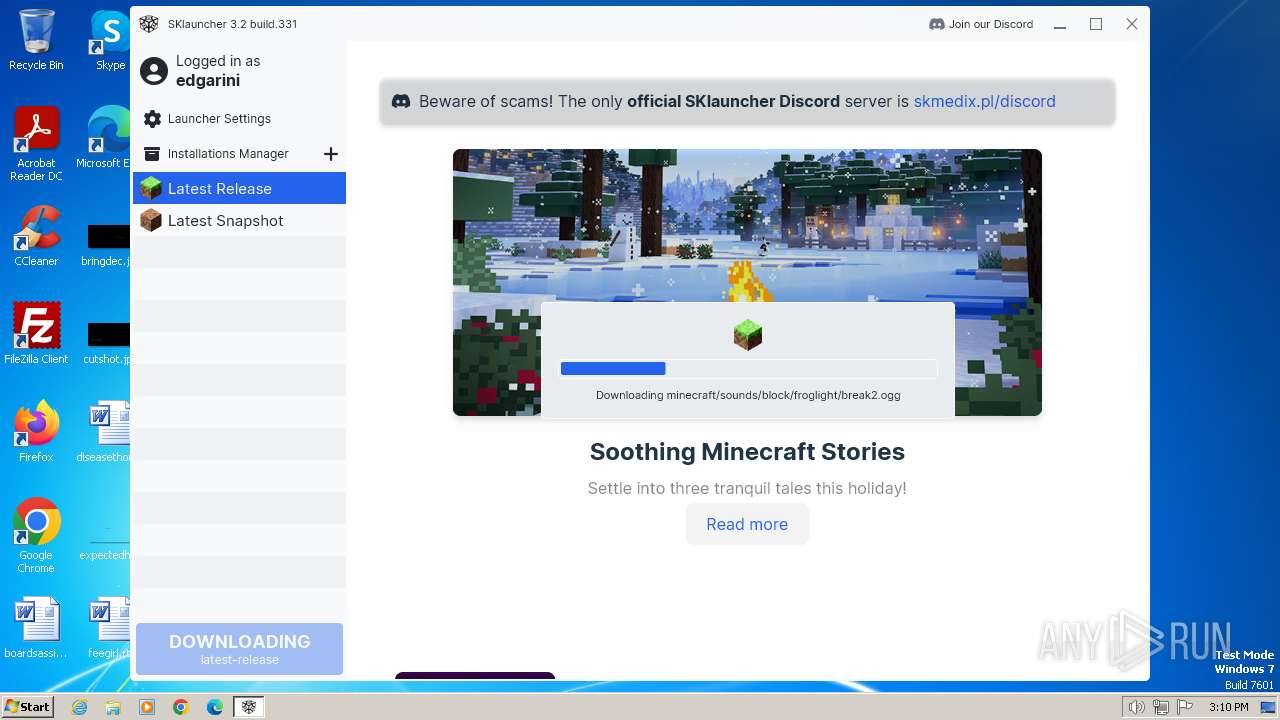
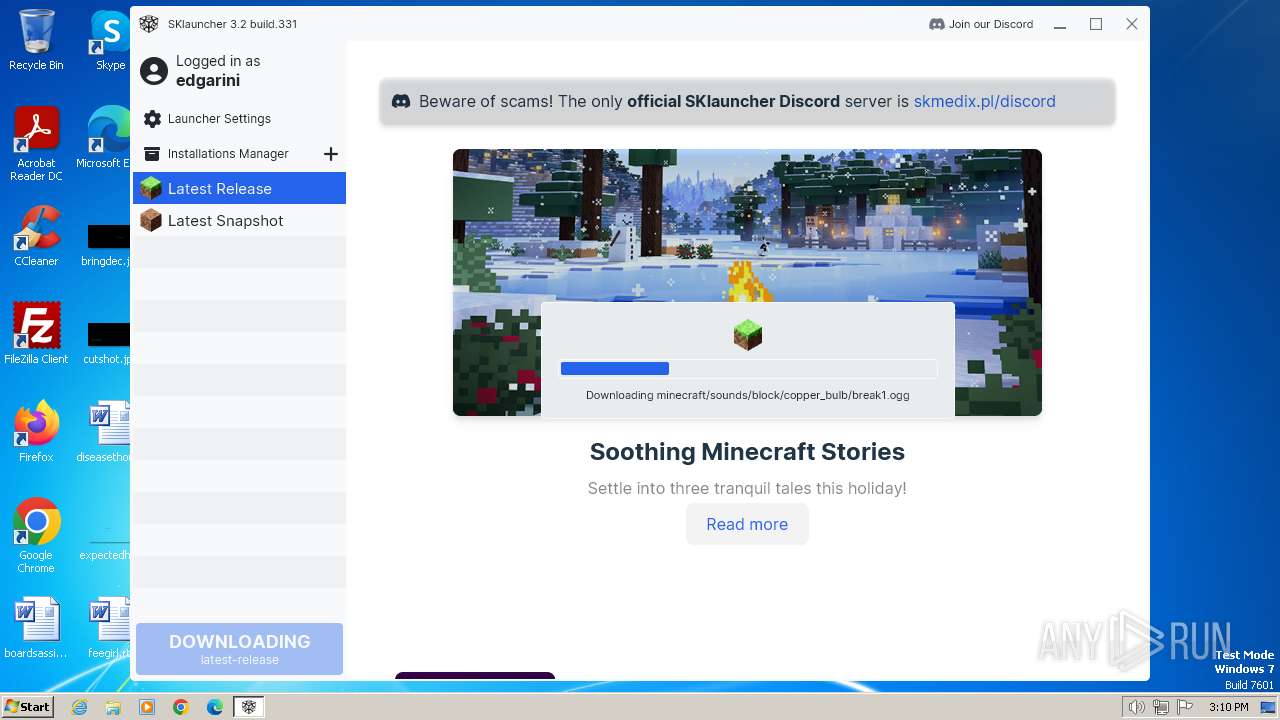
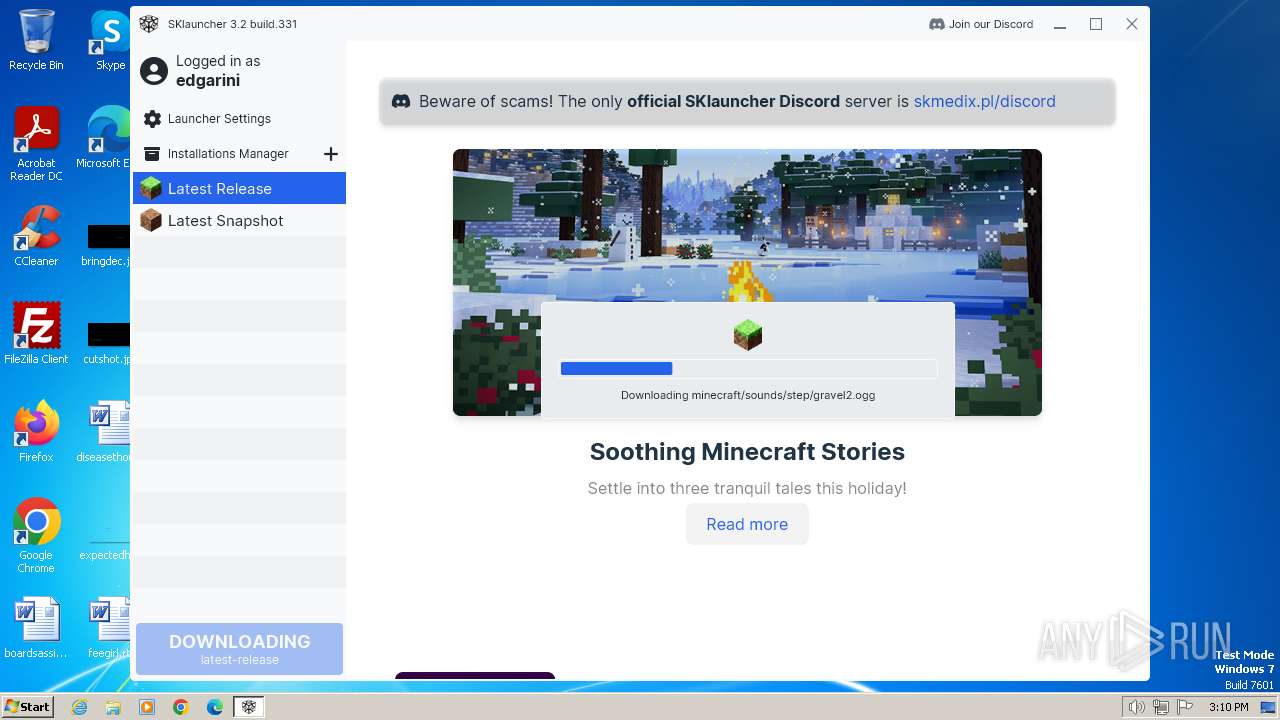
| File name: | SKlauncher-3.2.5.jar |
| Full analysis: | https://app.any.run/tasks/94ba584c-23aa-4f4f-a69f-b9701ec1a376 |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2024, 15:05:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 7454D24AE19035309AB3EEA108FBB777 |
| SHA1: | CE3DBBC97A10CB7D08D4D8AF4A245F148EFD5B11 |
| SHA256: | 1293A729057DEDB90D5271621AFBCD14B38BE19B2A31570A330E2EBCB3EB1BB3 |
| SSDEEP: | 49152:hlXnFEjAibAqXmneqj+jM3iyvr0H7XcvL5zz6m8rnFCMHxjWSidSNrwHfz26JOd/:hxFxibAEmLj2BorI7XqL5zzlkLidSOrK |
MALICIOUS
Drops the executable file immediately after the start
- javaw.exe (PID: 1380)
SUSPICIOUS
Process drops legitimate windows executable
- javaw.exe (PID: 1380)
Executable content was dropped or overwritten
- javaw.exe (PID: 1380)
The process creates files with name similar to system file names
- javaw.exe (PID: 1380)
The process drops C-runtime libraries
- javaw.exe (PID: 1380)
INFO
Checks supported languages
- javaw.exe (PID: 1380)
Creates files in the program directory
- javaw.exe (PID: 1380)
Reads the computer name
- javaw.exe (PID: 1380)
Reads the machine GUID from the registry
- javaw.exe (PID: 1380)
Create files in a temporary directory
- javaw.exe (PID: 1380)
Creates files or folders in the user directory
- javaw.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .jar | | | Java Archive (78.3) |
|---|---|---|
| .zip | | | ZIP compressed archive (21.6) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | 0x0800 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:20 05:57:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | META-INF/ |
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1380 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Local\Temp\SKlauncher-3.2.5.jar" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3052 | reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize" /v AppsUseLightTheme | C:\Windows\System32\reg.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3468 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
655
Read events
653
Write events
2
Delete events
0
Modification events
| (PID) Process: | (1380) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1380) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: javaw.exe | |||
Executable files
165
Suspicious files
1 405
Text files
279
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1380 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\sklauncher\sklauncher-fx.jar.xz | — | |
MD5:— | SHA256:— | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Roaming\.minecraft\sklauncher\sklauncher_data.bin | text | |
MD5:3789F58E903CE39A8D54ED1C32C9E437 | SHA256:F5DF9A5B3B92A6228A4CEB46C73A8BF4A35C1E0D1DD238E1AEC85BA2E3946552 | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8366434477965390366.tmp | image | |
MD5:4BC22D05B225A34A3DDB4F17D2469B77 | SHA256:FACE76C9C4FAD9476A1D80483D41772C805808A1383012B1C22065E30D32EDE6 | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF6339662341249576452.tmp | binary | |
MD5:52355593E805F6C172BFDC156A39A031 | SHA256:529BE850E06F62F8904F22BDA77E45BDE4834498FDBEC4FF4201FA3177447A3A | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF4516168249872124684.tmp | binary | |
MD5:250894A9A597C4362471DCB111934943 | SHA256:E6C172FD8A2F957414A7A63EC8DEB7F2AA239182394CFA5EE2EA6927C6194389 | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF7555366599865503472.tmp | binary | |
MD5:F2684BCE39D701EF54F3C9A717508162 | SHA256:53A941C664BBA47E36A20FE71E89EAE3CC92C47B5ACB85D7436C39758DDAF530 | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF6035783106675431335.tmp | binary | |
MD5:C10484D6B9BE5C545CF20FFDBE27ECB2 | SHA256:D253C410F4D0FD7F16D7B2ECAEA19B60FB877CB94F5B2752FDA272A3A86FA908 | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF6727307283388714286.tmp | binary | |
MD5:6C4504A7E86D43437C3805A9111F57EF | SHA256:858EFF8227A495097364AD2B90FB4602C4F55DDEC01663B61D7391FE51266322 | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\imageio8487193712412136840.tmp | image | |
MD5:4BC22D05B225A34A3DDB4F17D2469B77 | SHA256:FACE76C9C4FAD9476A1D80483D41772C805808A1383012B1C22065E30D32EDE6 | |||
| 1380 | javaw.exe | C:\Users\admin\AppData\Local\Temp\+JXF7966238292452037075.tmp | binary | |
MD5:52355593E805F6C172BFDC156A39A031 | SHA256:529BE850E06F62F8904F22BDA77E45BDE4834498FDBEC4FF4201FA3177447A3A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
84
DNS requests
23
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1380 | javaw.exe | 188.114.97.3:443 | files.skmedix.pl | CLOUDFLARENET | NL | unknown |
1380 | javaw.exe | 13.107.246.45:443 | launchermeta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1380 | javaw.exe | 13.107.246.62:443 | piston-meta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1380 | javaw.exe | 13.107.213.62:443 | piston-meta.mojang.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1380 | javaw.exe | 188.114.96.3:443 | files.skmedix.pl | CLOUDFLARENET | NL | unknown |
1380 | javaw.exe | 185.199.111.153:443 | meta.skmedix.pl | FASTLY | US | shared |
1380 | javaw.exe | 142.250.186.168:443 | www.googletagmanager.com | GOOGLE | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
files.skmedix.pl |
| unknown |
launchermeta.mojang.com |
| whitelisted |
piston-meta.mojang.com |
| unknown |
resources.download.minecraft.net |
| shared |
libraries.minecraft.net |
| shared |
sessionserver.skmedix.pl |
| unknown |
textures.skmedix.pl |
| unknown |
beta.skmedix.pl |
| unknown |
meta.skmedix.pl |
| unknown |
rsms.me |
| whitelisted |